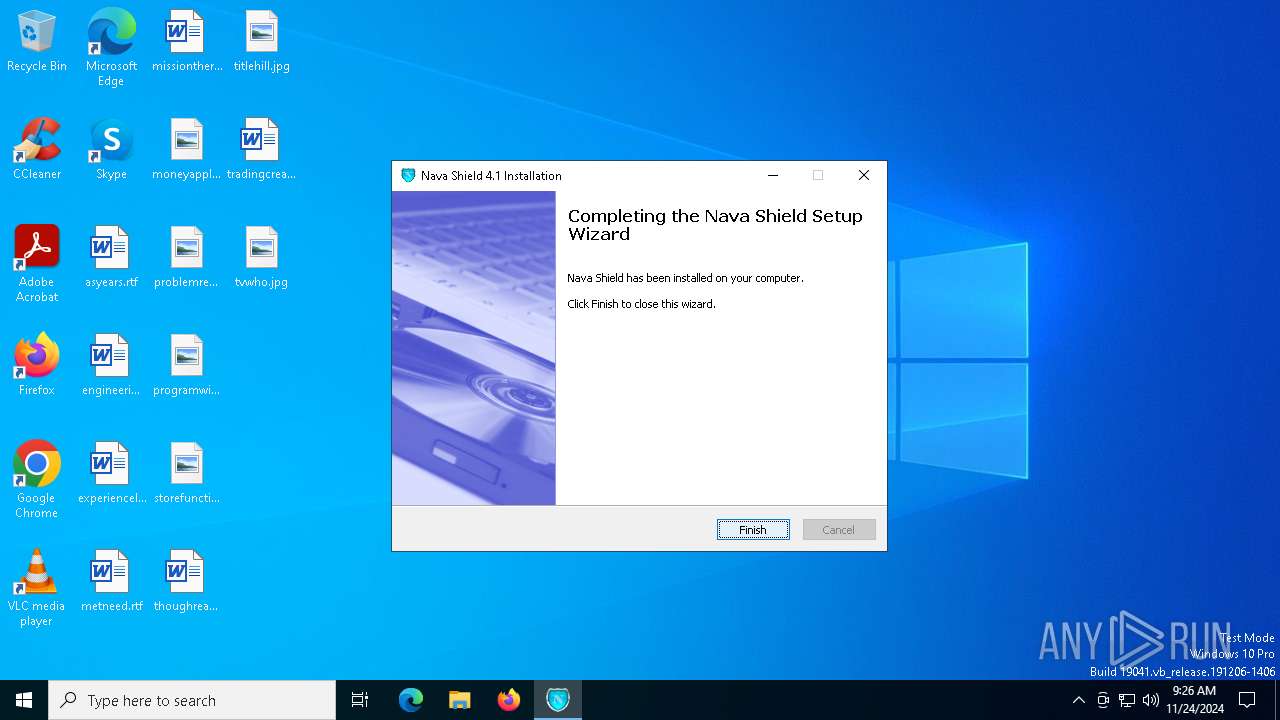
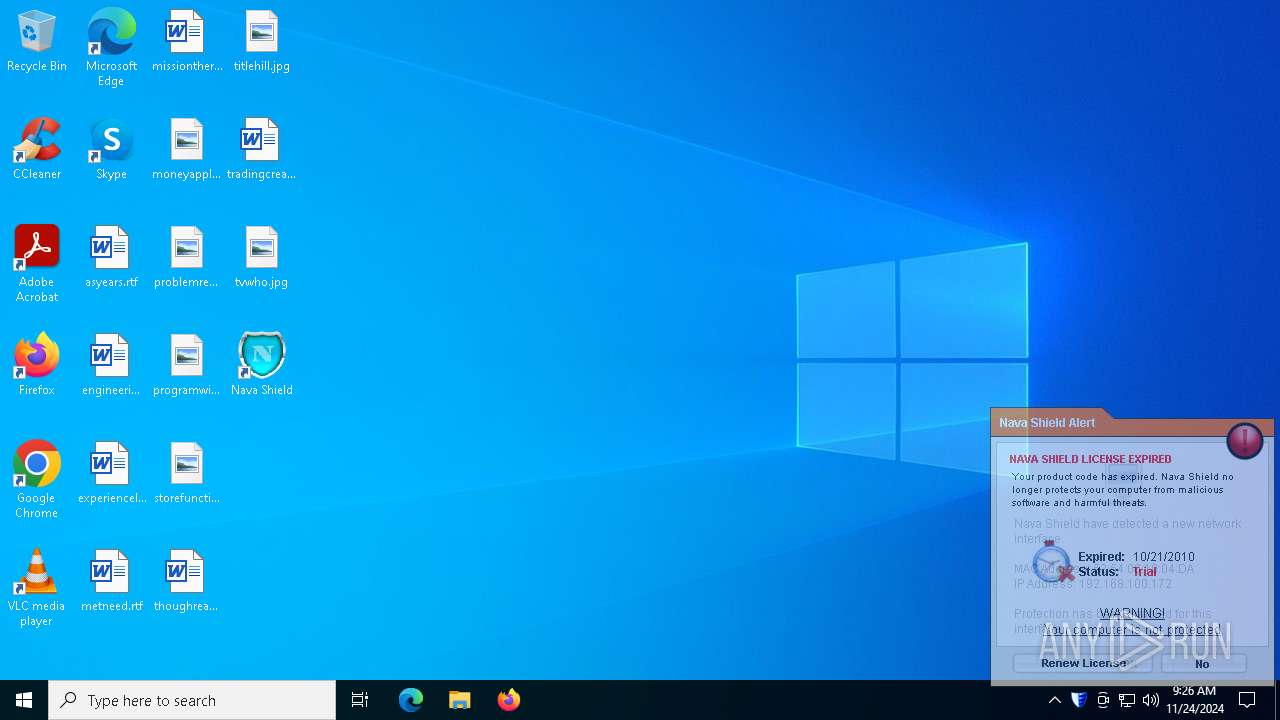
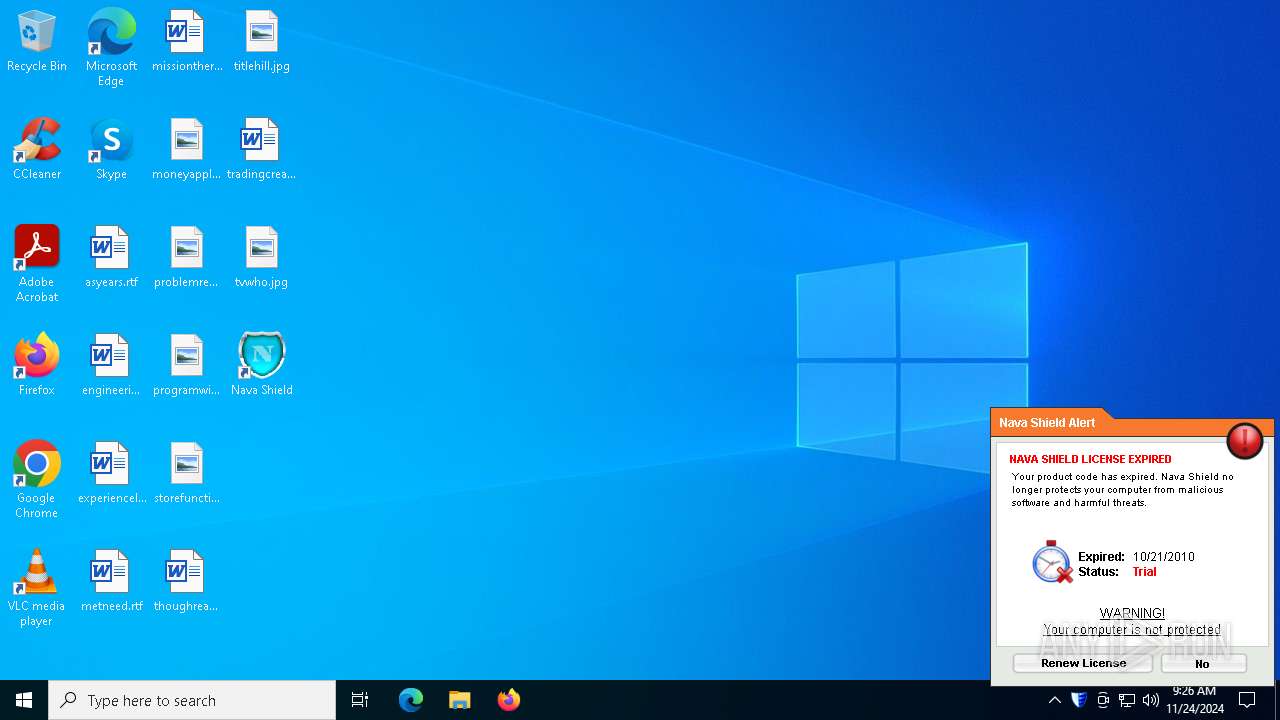
| File name: | Endermanch@NavaShield.exe |
| Full analysis: | https://app.any.run/tasks/8b52778b-7191-4cdc-b095-87186fc341f9 |
| Verdict: | Malicious activity |
| Analysis date: | November 24, 2024, 09:26:25 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows, 8 sections |
| MD5: | 1F13396FA59D38EBE76CCC587CCB11BB |
| SHA1: | 867ADB3076C0D335B9BFA64594EF37A7E2C951FF |
| SHA256: | 83ECB875F87150A88F4C3D496EB3CB5388CD8BAFDFF4879884ECECDBD1896E1D |
| SSDEEP: | 196608:CtbTP1ErBwMQjd1YTHdmpCP2PVgP/acIE/xQ0zyZejVk+YzbRdTZ:C1E1+dYx6OP9hdyZwV4zd |
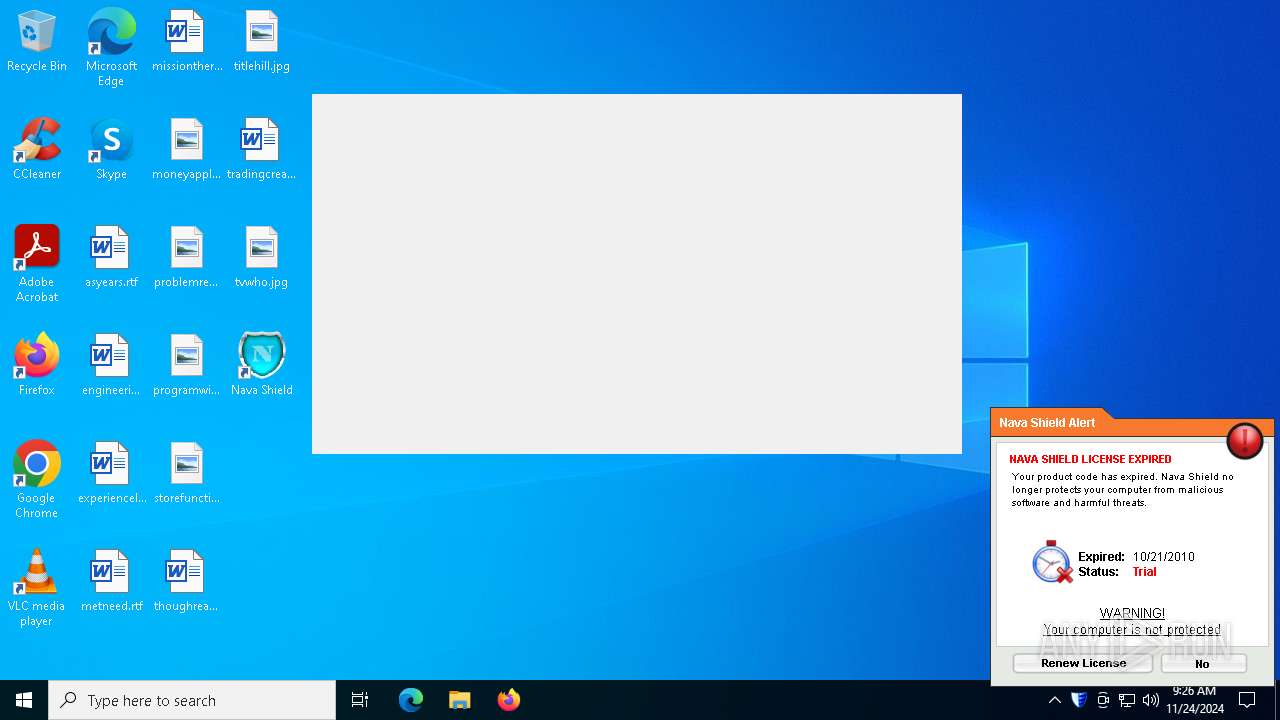
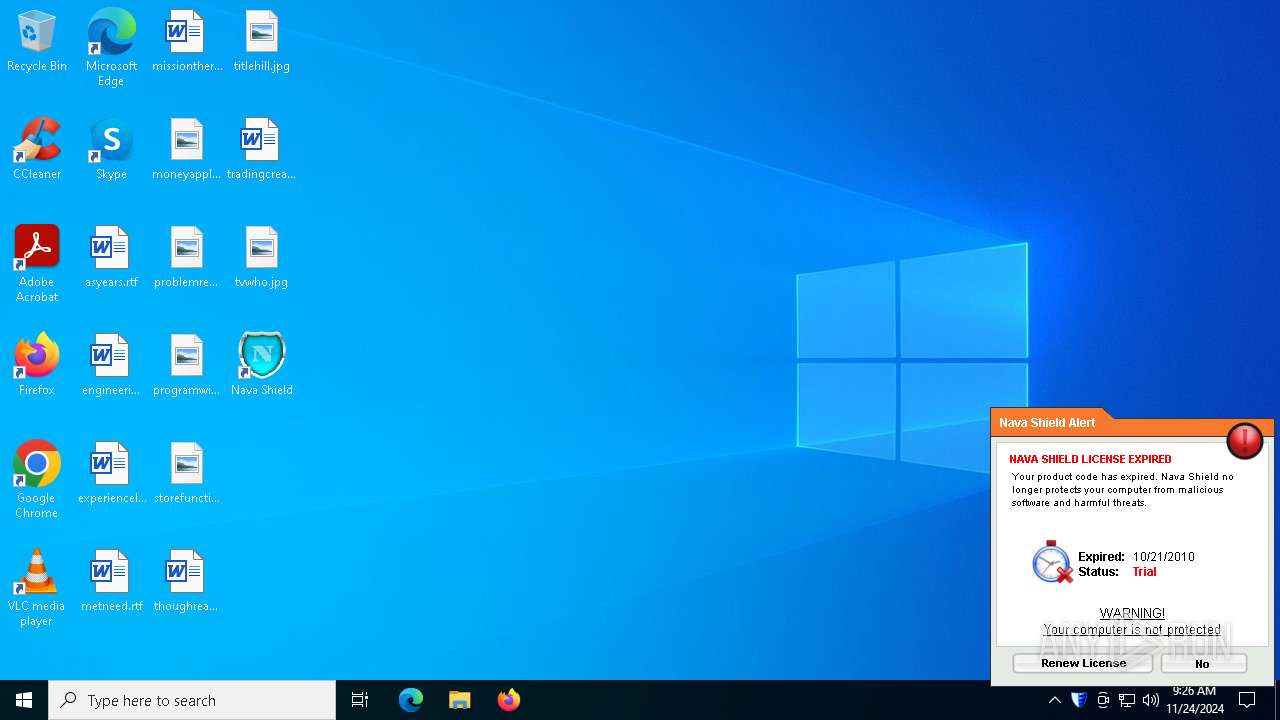
MALICIOUS
Changes the autorun value in the registry
- Endermanch@NavaShield.exe (PID: 2928)
XORed URL has been found (YARA)
- NavaDebugger.exe (PID: 6436)
SUSPICIOUS
Executable content was dropped or overwritten
- Endermanch@NavaShield.exe (PID: 2928)
Reads security settings of Internet Explorer
- Endermanch@NavaShield.exe (PID: 2928)
- NavaShield.exe (PID: 3092)
Creates a software uninstall entry
- Endermanch@NavaShield.exe (PID: 2928)
Starts itself from another location
- NavaShield.exe (PID: 3092)
There is functionality for communication over UDP network (YARA)
- NavaShield.exe (PID: 3092)
- NavaBridge.exe (PID: 6416)
- NavaDebugger.exe (PID: 6436)
INFO
Checks supported languages
- Endermanch@NavaShield.exe (PID: 2928)
- NavaShield.exe (PID: 3092)
- NavaBridge.exe (PID: 6416)
- NavaDebugger.exe (PID: 6436)
Creates files or folders in the user directory
- Endermanch@NavaShield.exe (PID: 2928)
Create files in a temporary directory
- Endermanch@NavaShield.exe (PID: 2928)
- NavaShield.exe (PID: 3092)
- NavaBridge.exe (PID: 6416)
- NavaDebugger.exe (PID: 6436)
Reads the computer name
- Endermanch@NavaShield.exe (PID: 2928)
- NavaShield.exe (PID: 3092)
The process uses the downloaded file
- Endermanch@NavaShield.exe (PID: 2928)
- NavaShield.exe (PID: 3092)
Process checks computer location settings
- Endermanch@NavaShield.exe (PID: 2928)
- NavaShield.exe (PID: 3092)
Reads CPU info
- NavaShield.exe (PID: 3092)
Manual execution by a user
- NavaShield.exe (PID: 6688)
- NavaShield.exe (PID: 7116)
- NavaShield.exe (PID: 6740)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
xor-url
(PID) Process(6436) NavaDebugger.exe
Decrypted-URLs (34)http://www.adultmovienetwork.com
http://www.analcravings.com
http://www.analsexlessons.com
http://www.asiancream.com
http://www.bigdickacademy.com
http://www.blackdickroundass.com
http://www.clubsapphic.com
http://www.cocksusa.com
http://www.collegefucktour.com
http://www.fetishview.com
http://www.firstsexvideo.com
http://www.gaythrills.com
http://www.google.com/#hl=en&source=hp&q=gay+porn&fp=
http://www.hentaixxxsex.com
http://www.hugedickslittlechicks.com
http://www.interracialtv.com
http://www.jizzmouthwash.com
http://www.lesbianrecruiters.com
http://www.lubemytits.com
http://www.manuelferrara.com
http://www.maturehotel.com
http://www.momsneedcash.com
http://www.mymilfstory.com
http://www.orgyfantasy.com
http://www.petitebeaver.com
http://www.realtrannies.com
http://www.shemaleseduction.com
http://www.sluttoons.com
http://www.spermglazed.comhcduc
http://www.studtoons.com
http://www.teenagetwinks.com
http://www.teenslutsgonewild.com
http://www.teenthrills.com
http://www.wildlatinagirls.com
TRiD
| .exe | | | Win32 Executable Delphi generic (37.4) |
|---|---|---|
| .scr | | | Windows screen saver (34.5) |
| .exe | | | Win32 Executable (generic) (11.9) |
| .exe | | | Win16/32 Executable Delphi generic (5.4) |
| .exe | | | Generic Win/DOS Executable (5.2) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 1992:06:19 22:22:17+00:00 |
| ImageFileCharacteristics: | Executable, No line numbers, No symbols, Bytes reversed lo, 32-bit, Bytes reversed hi |
| PEType: | PE32 |
| LinkerVersion: | 2.25 |
| CodeSize: | 148992 |
| InitializedDataSize: | 320000 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x25468 |
| OSVersion: | 4 |
| ImageVersion: | - |
| SubsystemVersion: | 4 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 4.1.0.0 |
| ProductVersionNumber: | 0.0.0.0 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | English (U.S.) |
| CharacterSet: | Windows, Latin1 |
| Comments: | - |
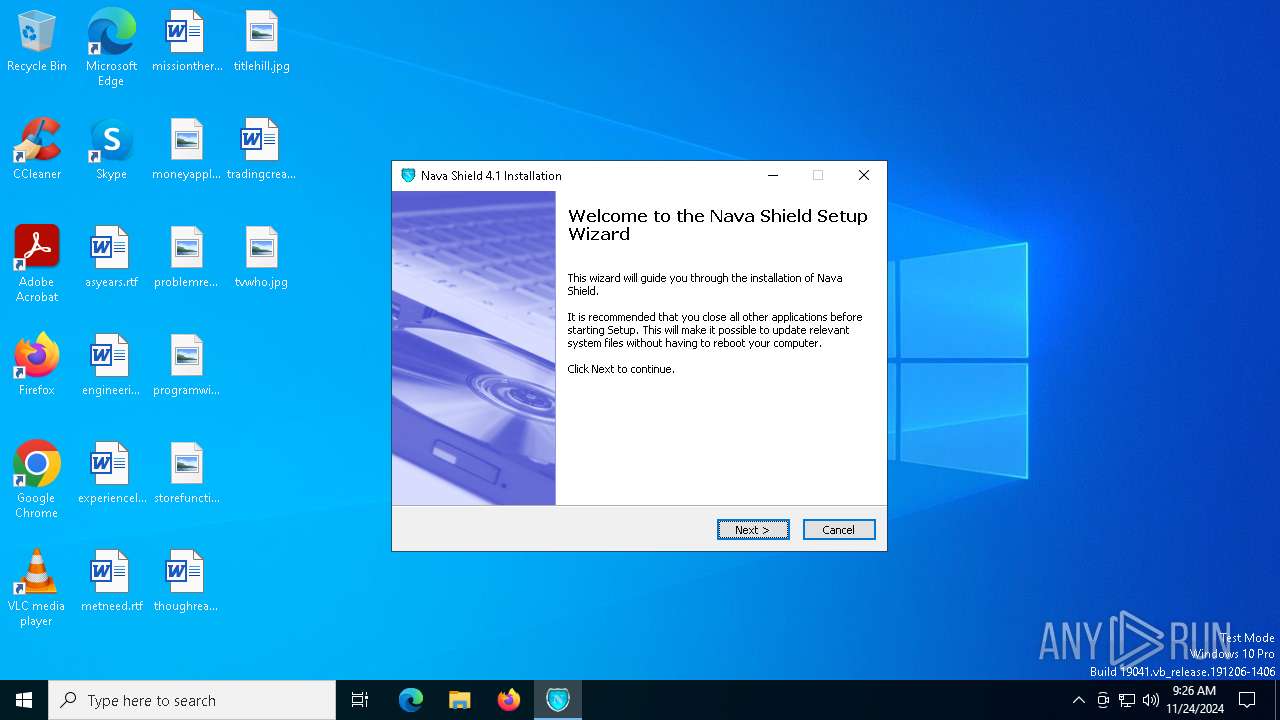
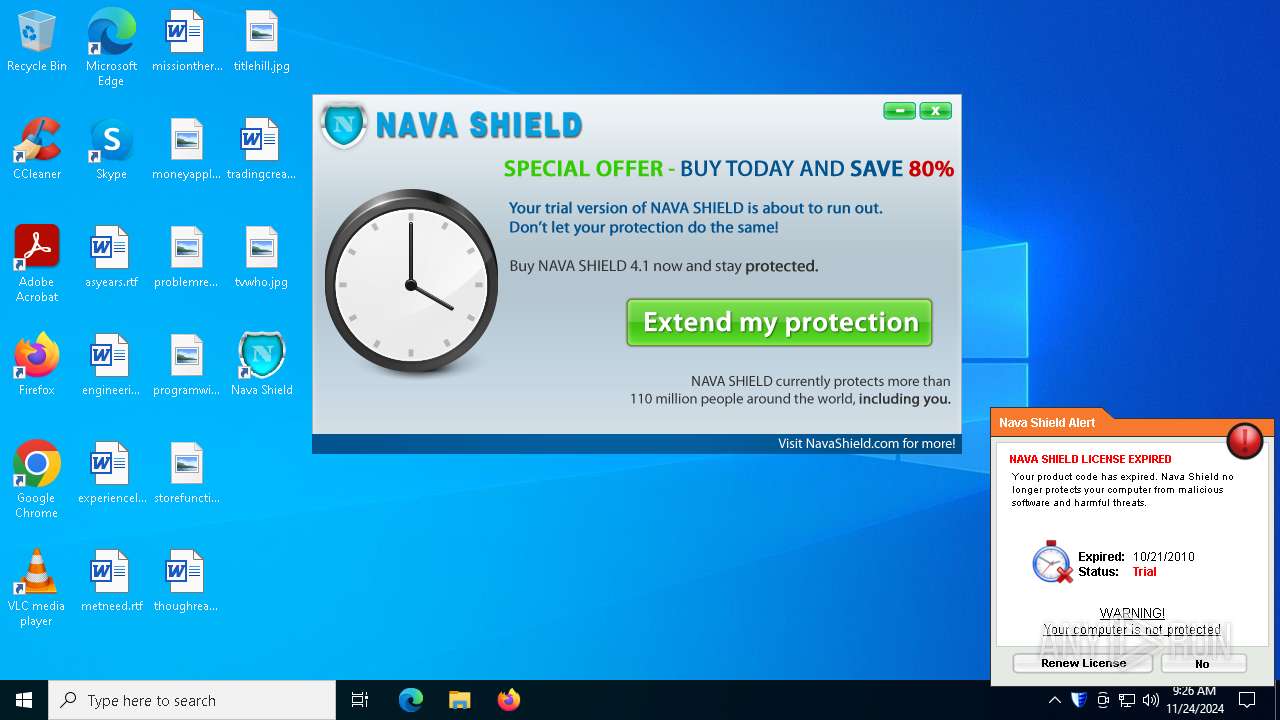
| CompanyName: | Nava Labs |
| FileDescription: | Nava Shield 4.1 Installation |
| FileVersion: | 4.1 |
| LegalCopyright: | Nava Labs |
Total processes
135
Monitored processes
8
Malicious processes
2
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 2928 | "C:\Users\admin\AppData\Local\Temp\Endermanch@NavaShield.exe" | C:\Users\admin\AppData\Local\Temp\Endermanch@NavaShield.exe | explorer.exe | ||||||||||||
User: admin Company: Nava Labs Integrity Level: HIGH Description: Nava Shield 4.1 Installation Exit code: 0 Version: 4.1 Modules
| |||||||||||||||
| 3092 | "C:\Nava Labs\Nava Shield\NavaShield.exe" | C:\Nava Labs\Nava Shield\NavaShield.exe | — | Endermanch@NavaShield.exe | |||||||||||
User: admin Integrity Level: HIGH Modules
| |||||||||||||||
| 5096 | "C:\Users\admin\AppData\Local\Temp\Endermanch@NavaShield.exe" | C:\Users\admin\AppData\Local\Temp\Endermanch@NavaShield.exe | — | explorer.exe | |||||||||||
User: admin Company: Nava Labs Integrity Level: MEDIUM Description: Nava Shield 4.1 Installation Exit code: 3221226540 Version: 4.1 Modules
| |||||||||||||||
| 6416 | "C:\Nava Labs\Nava Shield\NavaBridge.exe" | C:\Nava Labs\Nava Shield\NavaBridge.exe | NavaShield.exe | ||||||||||||
User: admin Integrity Level: HIGH Modules
| |||||||||||||||
| 6436 | "C:\Nava Labs\Nava Shield\NavaDebugger.exe" | C:\Nava Labs\Nava Shield\NavaDebugger.exe | NavaShield.exe | ||||||||||||
User: admin Integrity Level: HIGH Modules
xor-url(PID) Process(6436) NavaDebugger.exe Decrypted-URLs (34)http://www.adultmovienetwork.com http://www.analcravings.com http://www.analsexlessons.com http://www.asiancream.com http://www.bigdickacademy.com http://www.blackdickroundass.com http://www.clubsapphic.com http://www.cocksusa.com http://www.collegefucktour.com http://www.fetishview.com http://www.firstsexvideo.com http://www.gaythrills.com http://www.google.com/#hl=en&source=hp&q=gay+porn&fp= http://www.hentaixxxsex.com http://www.hugedickslittlechicks.com http://www.interracialtv.com http://www.jizzmouthwash.com http://www.lesbianrecruiters.com http://www.lubemytits.com http://www.manuelferrara.com http://www.maturehotel.com http://www.momsneedcash.com http://www.mymilfstory.com http://www.orgyfantasy.com http://www.petitebeaver.com http://www.realtrannies.com http://www.shemaleseduction.com http://www.sluttoons.com http://www.spermglazed.comhcduc http://www.studtoons.com http://www.teenagetwinks.com http://www.teenslutsgonewild.com http://www.teenthrills.com http://www.wildlatinagirls.com | |||||||||||||||
| 6688 | "C:\Nava Labs\Nava Shield\NavaShield.exe" | C:\Nava Labs\Nava Shield\NavaShield.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 6740 | "C:\Nava Labs\Nava Shield\NavaShield.exe" | C:\Nava Labs\Nava Shield\NavaShield.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 7116 | "C:\Nava Labs\Nava Shield\NavaShield.exe" | C:\Nava Labs\Nava Shield\NavaShield.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
Total events
2 022
Read events
2 004
Write events
18
Delete events
0
Modification events
| (PID) Process: | (2928) Endermanch@NavaShield.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Run |
| Operation: | write | Name: | NavaShield |
Value: c:\Nava Labs\Nava Shield\navashield.exe | |||
| (PID) Process: | (2928) Endermanch@NavaShield.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\Uninstall\Nava Shield 4.1 |
| Operation: | write | Name: | DisplayName |
Value: Nava Shield 4.1 | |||
| (PID) Process: | (2928) Endermanch@NavaShield.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\Uninstall\Nava Shield 4.1 |
| Operation: | write | Name: | DisplayVersion |
Value: 4.1 | |||
| (PID) Process: | (2928) Endermanch@NavaShield.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\Uninstall\Nava Shield 4.1 |
| Operation: | write | Name: | VersionMajor |
Value: 4 | |||
| (PID) Process: | (2928) Endermanch@NavaShield.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\Uninstall\Nava Shield 4.1 |
| Operation: | write | Name: | VersionMinor |
Value: 1 | |||
| (PID) Process: | (2928) Endermanch@NavaShield.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\Uninstall\Nava Shield 4.1 |
| Operation: | write | Name: | Publisher |
Value: Nava Labs | |||
| (PID) Process: | (2928) Endermanch@NavaShield.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\Uninstall\Nava Shield 4.1 |
| Operation: | write | Name: | DisplayIcon |
Value: c:\Nava Labs\Nava Shield\UninstallNava.exe | |||
| (PID) Process: | (2928) Endermanch@NavaShield.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\Uninstall\Nava Shield 4.1 |
| Operation: | write | Name: | UninstallString |
Value: c:\Nava Labs\Nava Shield\UninstallNava.exe | |||
| (PID) Process: | (2928) Endermanch@NavaShield.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\Uninstall\Nava Shield 4.1 |
| Operation: | write | Name: | URLInfoAbout |
Value: http://www.navashield.com/ | |||
| (PID) Process: | (2928) Endermanch@NavaShield.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\Uninstall\Nava Shield 4.1 |
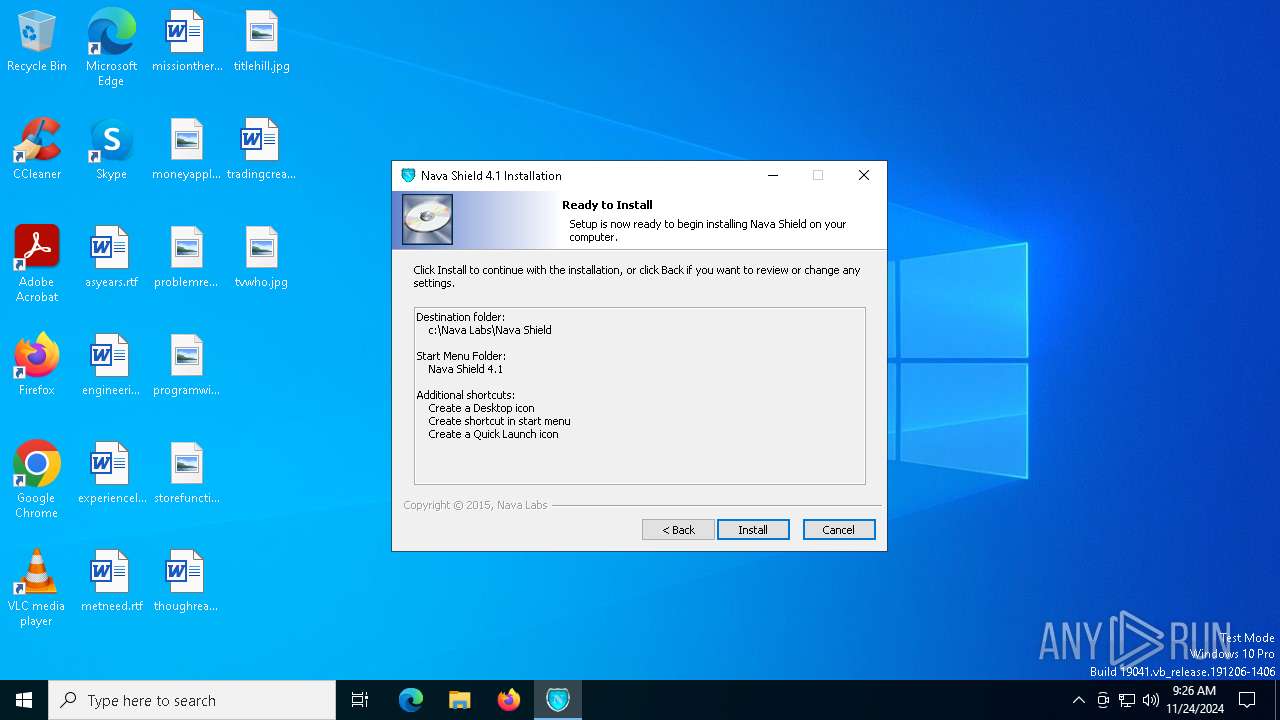
| Operation: | write | Name: | InstallLocation |
Value: c:\Nava Labs\Nava Shield\ | |||
Executable files
12
Suspicious files
11
Text files
5
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2928 | Endermanch@NavaShield.exe | C:\Users\admin\AppData\Local\Temp\$inst\temp_0.tmp | — | |
MD5:— | SHA256:— | |||
| 2928 | Endermanch@NavaShield.exe | C:\Nava Labs\Nava Shield\NavaBridge Libs\Browser Plugin.dll | executable | |
MD5:912924F628E277BE9CC28A5F2A990CB9 | SHA256:BD474C5AAFCAA12F20DA5ECB29E17555B953ECA46B4F56588A72672A36D4A8EB | |||
| 2928 | Endermanch@NavaShield.exe | C:\Nava Labs\Nava Shield\freeset.dat | text | |
MD5:2C66614915A2EDAC8BD5489C957A2879 | SHA256:FD242B6EAED612C71FF90B17D10D129FF9B4B4969291303458EE817FE2FB3F06 | |||
| 2928 | Endermanch@NavaShield.exe | C:\Nava Labs\Nava Shield\install.log | text | |
MD5:33836EF8621FC8D2E5F3302FD3BFBC8C | SHA256:FE219EB5CC7DA3F928E816D65DCEC5FD8A727F34B026F681810DFCC2B9F395DA | |||
| 2928 | Endermanch@NavaShield.exe | C:\Users\admin\AppData\Local\Temp\$inst\5.tmp | image | |
MD5:110B42B9AA84606C7FF6177535D9ED77 | SHA256:DDCD070A764F83C367631A205C833C4901293FE0A64C59916C82393F9AEE99AD | |||
| 2928 | Endermanch@NavaShield.exe | C:\Nava Labs\Nava Shield\config.dat | binary | |
MD5:389BF6E15AE0A7250F454DA52AA7CED5 | SHA256:5993325ACFE309946C176737A019AA16E22B921FA6387B766BF8BC8A504E220D | |||
| 2928 | Endermanch@NavaShield.exe | C:\Nava Labs\Nava Shield\NavaDebugger Libs\MD5.dll | executable | |
MD5:831295342C47B770BF7CC591A6916FA7 | SHA256:8341ECC0938CA6D90B7E0F02AF2D7E6B571C948A03A99D54AF61C4557C78D656 | |||
| 2928 | Endermanch@NavaShield.exe | C:\Nava Labs\Nava Shield\NavaBridge Libs\MD5.dll | executable | |
MD5:831295342C47B770BF7CC591A6916FA7 | SHA256:8341ECC0938CA6D90B7E0F02AF2D7E6B571C948A03A99D54AF61C4557C78D656 | |||
| 2928 | Endermanch@NavaShield.exe | C:\Users\admin\AppData\Local\Temp\$inst\2.tmp | compressed | |
MD5:37A639FC899D0C312AF607BE808B5E4D | SHA256:8ECAD2A44EBB53CEF96FDF4D6A695B729FC2027408421A194F290A31E28B9790 | |||
| 2928 | Endermanch@NavaShield.exe | C:\Users\admin\AppData\Local\Temp\$inst\4.tmp | image | |
MD5:5252FE76395E49A85C435D3431EE3927 | SHA256:5CA7C69BA0AA28276A718706CAE4E61520CB45FB34F32DE9FAC019B0574B2C1C | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
9
TCP/UDP connections
44
DNS requests
24
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
5576 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
— | — | GET | 200 | 23.48.23.156:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
6468 | SIHClient.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
5064 | SearchApp.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
— | — | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
6416 | NavaBridge.exe | GET | 403 | 64.190.63.222:80 | http://navashield.com/nava/offers?a=TNEQ7W7U4W&v=1&b=cKDXlwzUVy1zTbIUPjKvKg== | unknown | — | — | unknown |
5064 | SearchApp.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAUZZSZEml49Gjh0j13P68w%3D | unknown | — | — | whitelisted |
6468 | SIHClient.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4712 | MoUsoCoreWorker.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
3560 | svchost.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
5064 | SearchApp.exe | 92.123.104.58:443 | www.bing.com | Akamai International B.V. | DE | whitelisted |
5064 | SearchApp.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
— | — | 23.48.23.156:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
— | — | 23.35.229.160:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1176 | svchost.exe | 20.190.159.2:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
www.bing.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
login.live.com |
| whitelisted |
go.microsoft.com |
| whitelisted |
arc.msn.com |
| whitelisted |
fd.api.iris.microsoft.com |
| whitelisted |