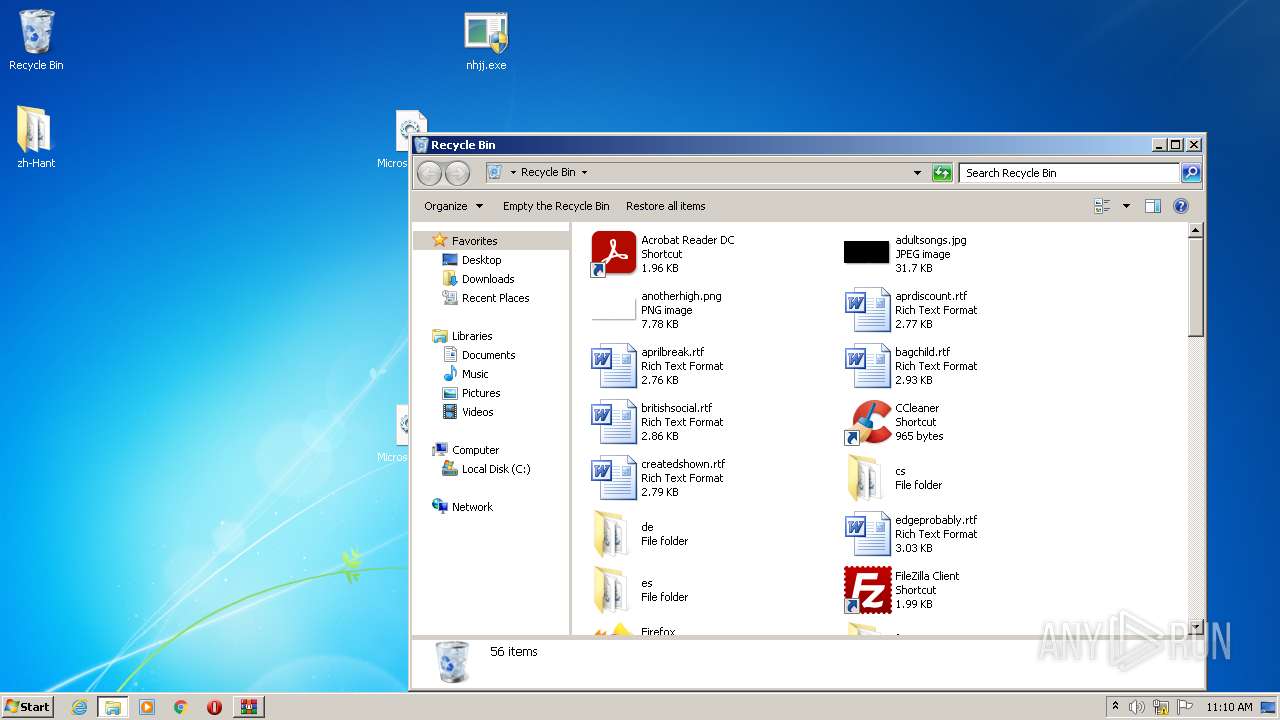
| File name: | Debug.7z |
| Full analysis: | https://app.any.run/tasks/cce75404-beb7-4e61-94fe-9ce85131176b |
| Verdict: | Malicious activity |
| Analysis date: | June 27, 2022, 10:09:53 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/x-7z-compressed |
| File info: | 7-zip archive data, version 0.4 |
| MD5: | 6D4FA8AB3B7C2D9433C92141D1897608 |
| SHA1: | 88DA8EE0C7E27DF69103B0719BDE71804A6714FB |
| SHA256: | 83DFA333E40CAFC2C7E62FECDDC9F66A3441498C1EB5D5E36B31C469BC6E8506 |
| SSDEEP: | 98304:LuLx3GvI4FtQJIgtVAu02ZBzJE66S3AEO9J+wSAq0iujUvR4bEQP+mM2y8CIHr:sx3GvI4F2JIsAUL6wAEMAzADiuo2V+X4 |
MALICIOUS
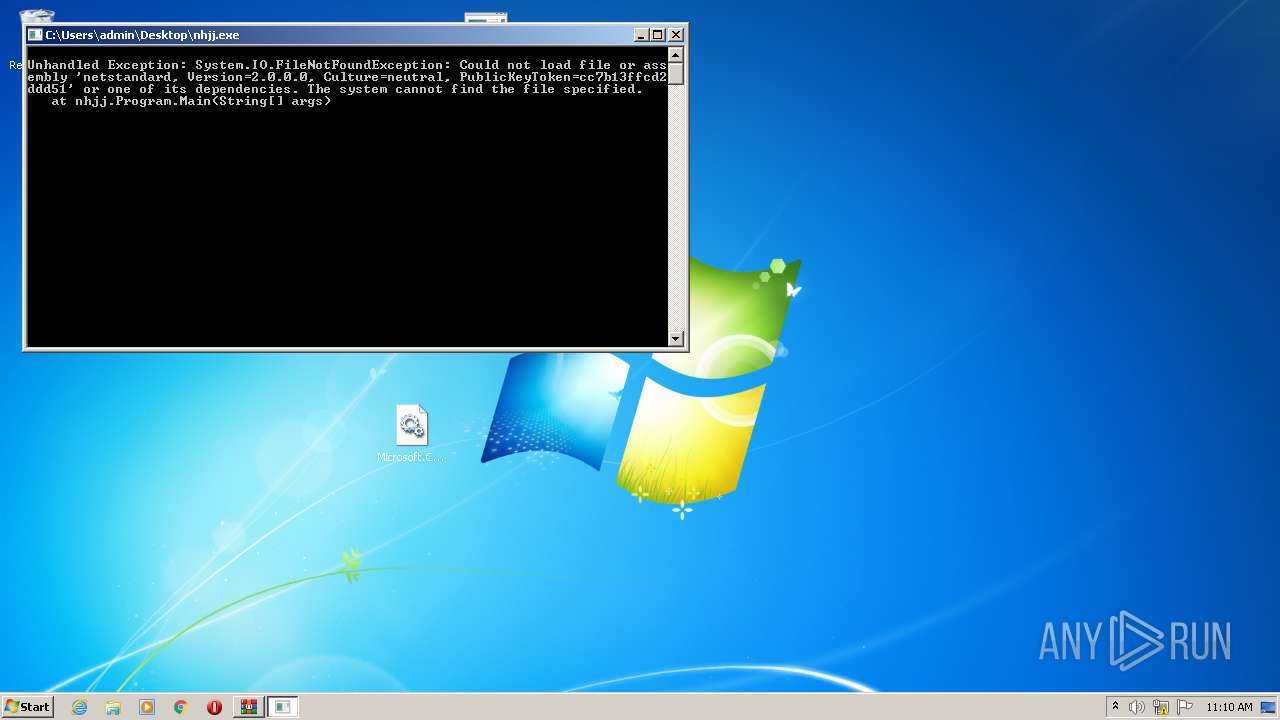
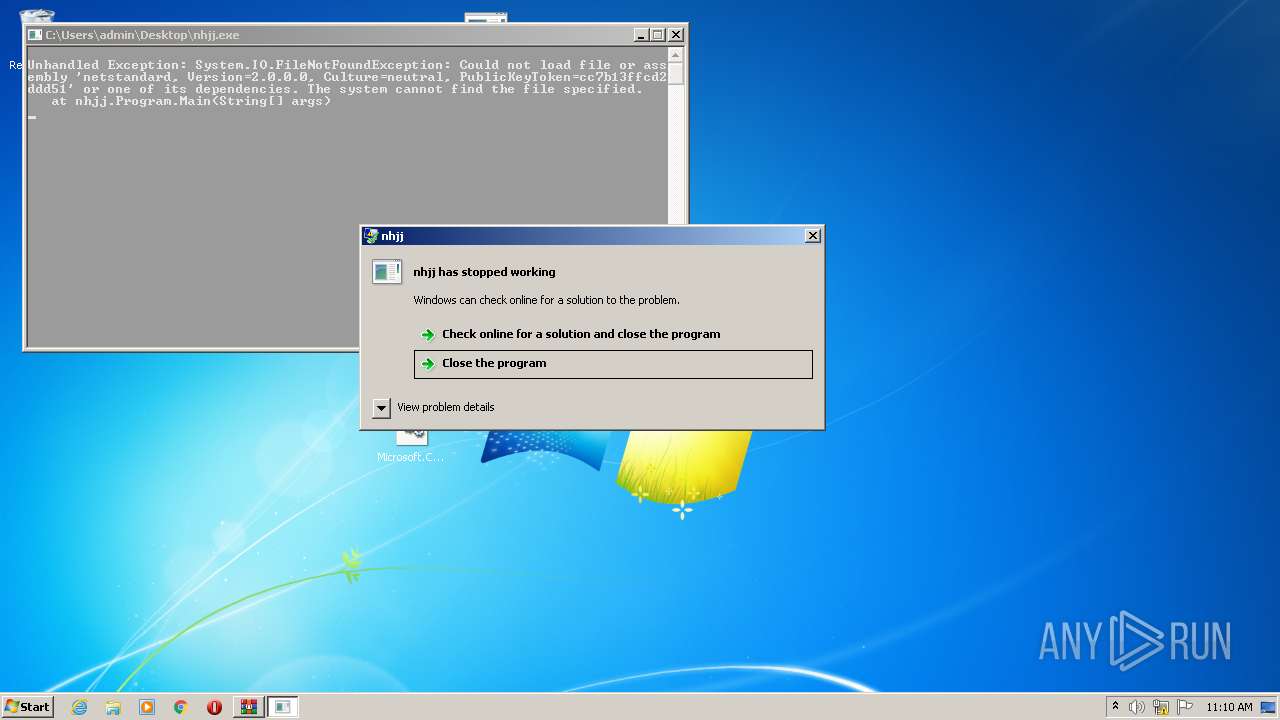
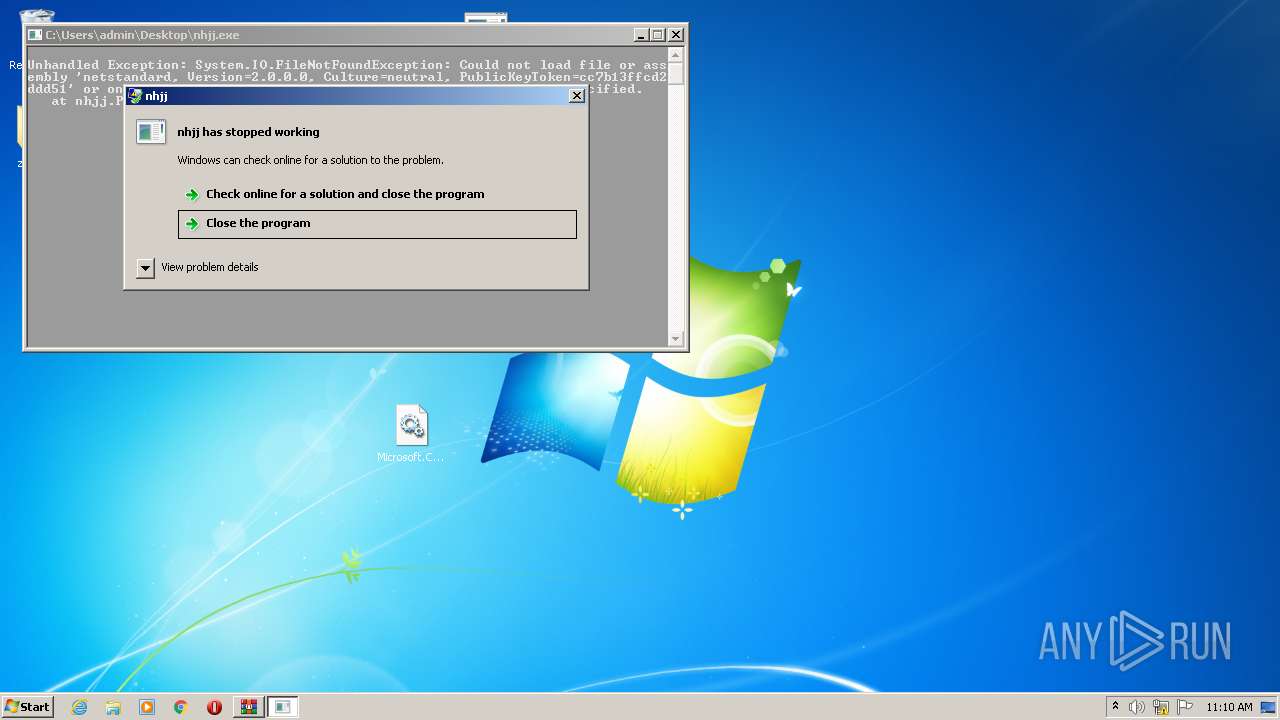
Drops executable file immediately after starts
- Explorer.EXE (PID: 1172)
- WinRAR.exe (PID: 3740)
Loads dropped or rewritten executable
- SearchProtocolHost.exe (PID: 2484)
- Explorer.EXE (PID: 1172)
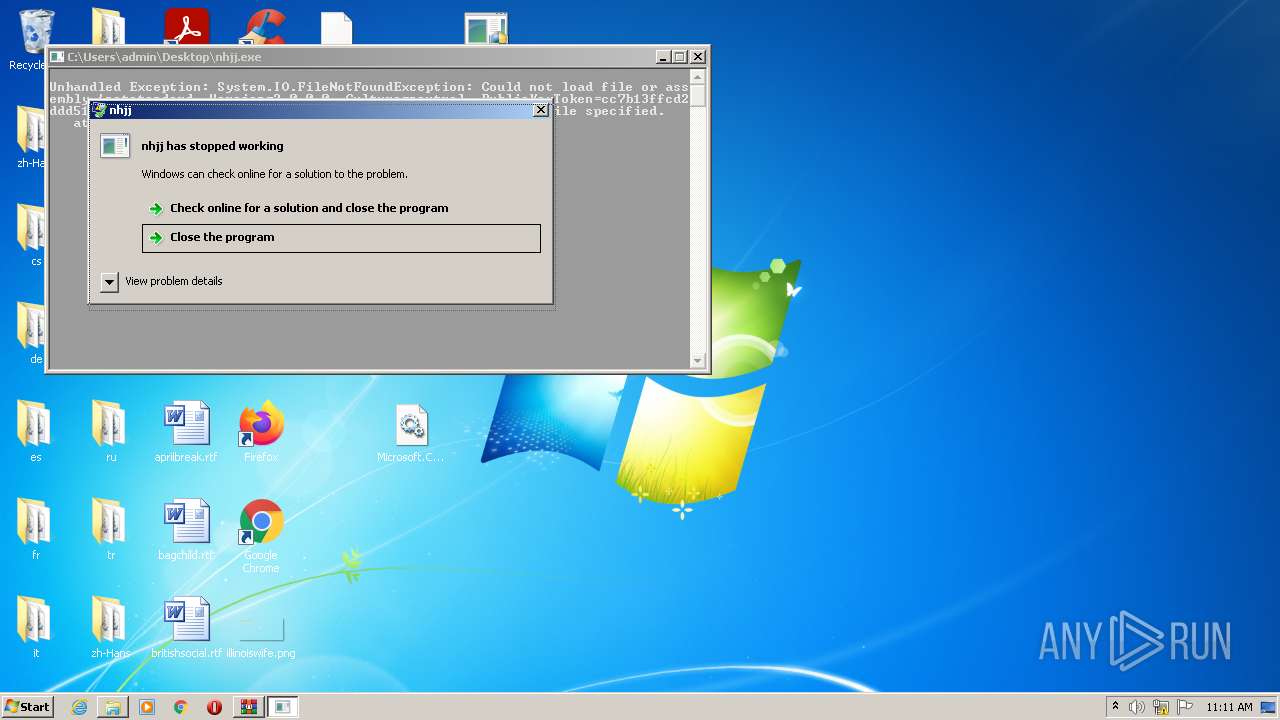
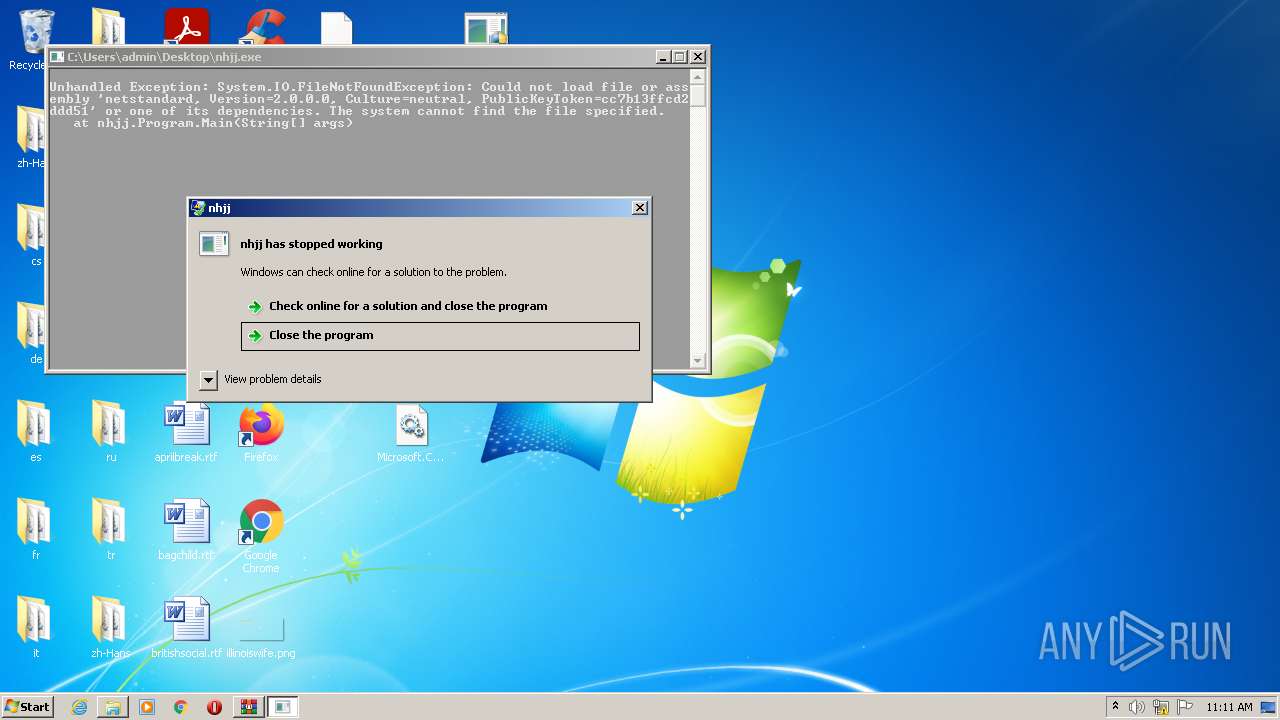
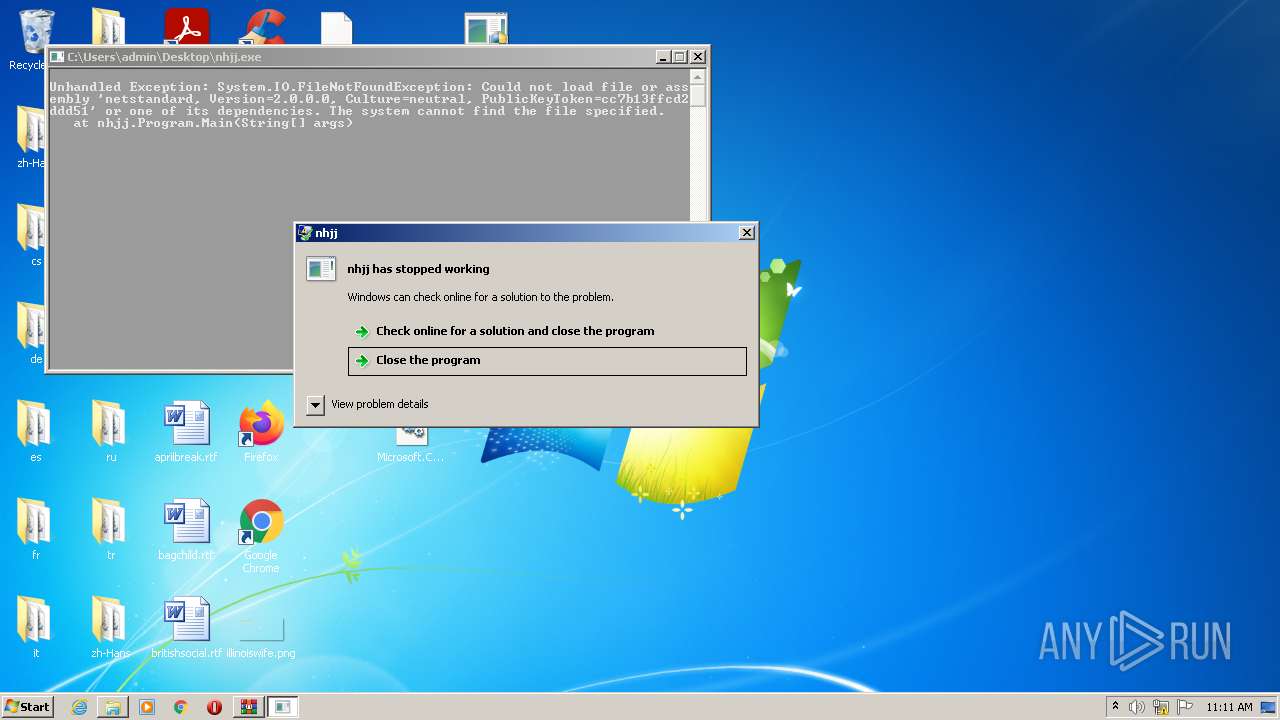
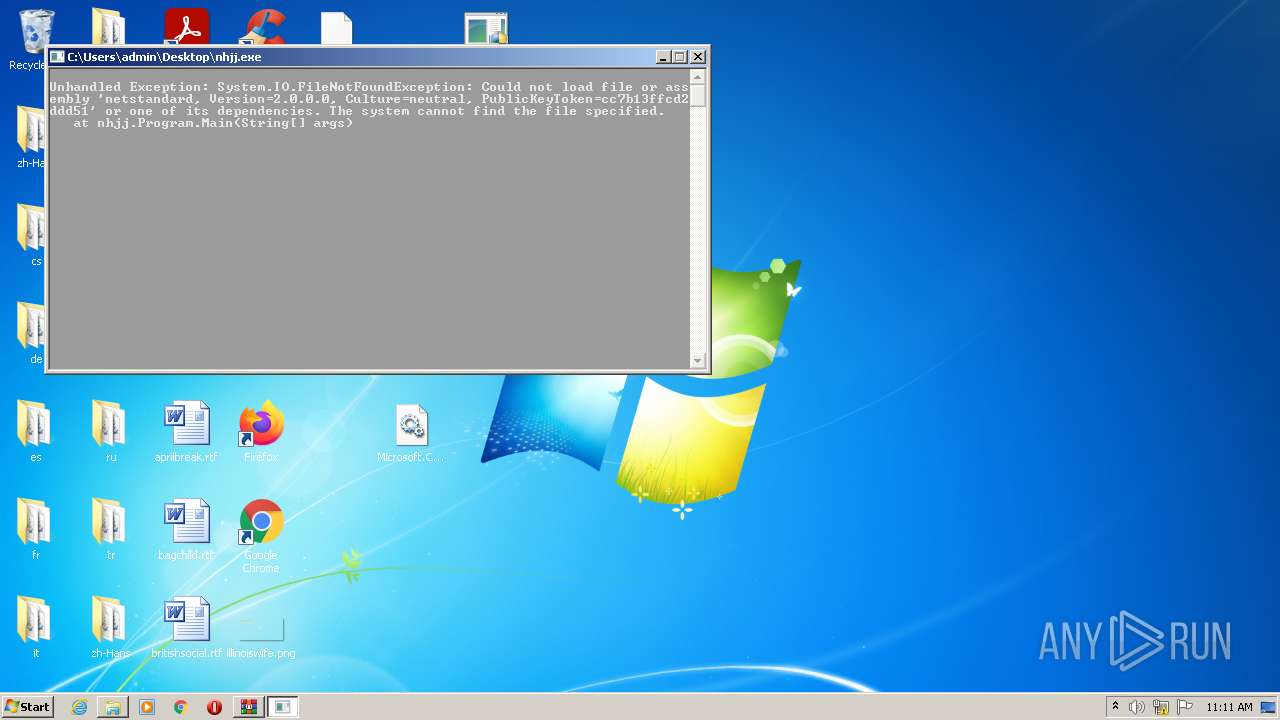
- nhjj.exe (PID: 2488)
- nhjj.exe (PID: 2532)
- nhjj.exe (PID: 3056)
Application was dropped or rewritten from another process
- nhjj.exe (PID: 2200)
- nhjj.exe (PID: 2488)
- nhjj.exe (PID: 568)
- nhjj.exe (PID: 2532)
- nhjj.exe (PID: 3228)
- nhjj.exe (PID: 3056)
SUSPICIOUS
Reads the computer name
- WinRAR.exe (PID: 3740)
- nhjj.exe (PID: 2488)
- nhjj.exe (PID: 2532)
- nhjj.exe (PID: 3056)
Checks supported languages
- WinRAR.exe (PID: 3740)
- nhjj.exe (PID: 2488)
- nhjj.exe (PID: 2532)
- nhjj.exe (PID: 3056)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 3740)
- Explorer.EXE (PID: 1172)
Drops a file with a compile date too recent
- WinRAR.exe (PID: 3740)
- Explorer.EXE (PID: 1172)
Reads default file associations for system extensions
- Explorer.EXE (PID: 1172)
INFO
Dropped object may contain Bitcoin addresses
- WinRAR.exe (PID: 3740)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .7z | | | 7-Zip compressed archive (v0.4) (57.1) |
|---|---|---|
| .7z | | | 7-Zip compressed archive (gen) (42.8) |
Total processes
57
Monitored processes
9
Malicious processes
6
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 568 | "C:\Users\admin\Desktop\nhjj.exe" | C:\Users\admin\Desktop\nhjj.exe | — | Explorer.EXE | |||||||||||
User: admin Integrity Level: MEDIUM Description: nhjj Exit code: 3221226540 Version: 1.0.0.0 Modules
| |||||||||||||||
| 1172 | C:\Windows\Explorer.EXE | C:\Windows\Explorer.EXE | — | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Explorer Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2200 | "C:\Users\admin\Desktop\nhjj.exe" | C:\Users\admin\Desktop\nhjj.exe | — | Explorer.EXE | |||||||||||
User: admin Integrity Level: MEDIUM Description: nhjj Exit code: 3221226540 Version: 1.0.0.0 Modules
| |||||||||||||||
| 2484 | "C:\Windows\system32\SearchProtocolHost.exe" Global\UsGthrFltPipeMssGthrPipe2_ Global\UsGthrCtrlFltPipeMssGthrPipe2 1 -2147483646 "Software\Microsoft\Windows Search" "Mozilla/4.0 (compatible; MSIE 6.0; Windows NT; MS Search 4.0 Robot)" "C:\ProgramData\Microsoft\Search\Data\Temp\usgthrsvc" "DownLevelDaemon" | C:\Windows\system32\SearchProtocolHost.exe | — | SearchIndexer.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Microsoft Windows Search Protocol Host Exit code: 0 Version: 7.00.7601.24542 (win7sp1_ldr_escrow.191209-2211) Modules
| |||||||||||||||
| 2488 | "C:\Users\admin\Desktop\nhjj.exe" | C:\Users\admin\Desktop\nhjj.exe | Explorer.EXE | ||||||||||||
User: admin Integrity Level: HIGH Description: nhjj Exit code: 3762504530 Version: 1.0.0.0 Modules
| |||||||||||||||
| 2532 | "C:\Users\admin\Desktop\nhjj.exe" | C:\Users\admin\Desktop\nhjj.exe | Explorer.EXE | ||||||||||||
User: admin Integrity Level: HIGH Description: nhjj Exit code: 3762504530 Version: 1.0.0.0 Modules
| |||||||||||||||
| 3056 | "C:\Users\admin\Desktop\nhjj.exe" | C:\Users\admin\Desktop\nhjj.exe | Explorer.EXE | ||||||||||||
User: admin Integrity Level: HIGH Description: nhjj Exit code: 3762504530 Version: 1.0.0.0 Modules
| |||||||||||||||
| 3228 | "C:\Users\admin\Desktop\nhjj.exe" | C:\Users\admin\Desktop\nhjj.exe | — | Explorer.EXE | |||||||||||
User: admin Integrity Level: MEDIUM Description: nhjj Exit code: 3221226540 Version: 1.0.0.0 Modules
| |||||||||||||||
| 3740 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Temp\Debug.7z" | C:\Program Files\WinRAR\WinRAR.exe | Explorer.EXE | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
Total events
22 304
Read events
22 034
Write events
254
Delete events
16
Modification events
| (PID) Process: | (3740) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (3740) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (3740) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\16C\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (3740) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\virtio_ivshmem_master_build.zip | |||
| (PID) Process: | (3740) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\Win7-KB3191566-x86.zip | |||
| (PID) Process: | (3740) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\Debug.7z | |||
| (PID) Process: | (3740) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (3740) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (3740) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (3740) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
Executable files
64
Suspicious files
87
Text files
75
Unknown types
21
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3740 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3740.26688\Microsoft.CodeAnalysis.CSharp.xml | xml | |
MD5:— | SHA256:— | |||
| 3740 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3740.26688\Microsoft.CodeAnalysis.xml | xml | |
MD5:— | SHA256:— | |||
| 3740 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3740.26688\Microsoft.CodeAnalysis.pdb | binary | |
MD5:— | SHA256:— | |||
| 3740 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3740.26688\Microsoft.CodeAnalysis.CSharp.pdb | binary | |
MD5:— | SHA256:— | |||
| 3740 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3740.26688\cs\Microsoft.CodeAnalysis.CSharp.resources.dll | executable | |
MD5:— | SHA256:— | |||
| 3740 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3740.26688\System.Buffers.xml | xml | |
MD5:1C55860DD93297A6EA2FAD2974834C3A | SHA256:2EC7FB12E11F9831E40524427F6D88A3C9FFDD56CCFA81D373467B75B479A578 | |||
| 3740 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3740.26688\System.Collections.Immutable.xml | xml | |
MD5:E0A26EA286158273C31993DC98F0C8F1 | SHA256:8E638BE0C97F677B2E9E99358E8FBBC5200FCA5B99CEAB52F4CBA13C62AA9973 | |||
| 3740 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3740.26688\de\Microsoft.CodeAnalysis.resources.dll | executable | |
MD5:— | SHA256:— | |||
| 3740 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3740.26688\es\Microsoft.CodeAnalysis.resources.dll | executable | |
MD5:— | SHA256:— | |||
| 3740 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3740.26688\de\Microsoft.CodeAnalysis.CSharp.resources.dll | executable | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
0
DNS requests
0
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report