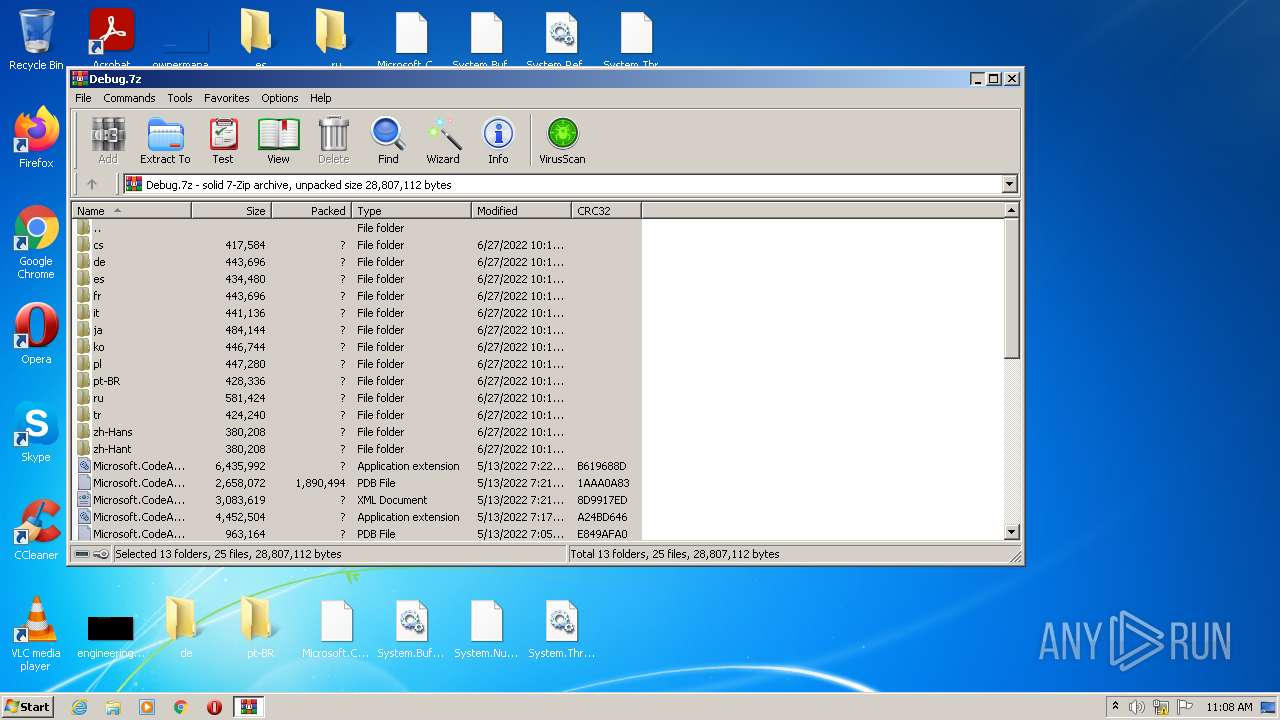
| File name: | Debug.7z |
| Full analysis: | https://app.any.run/tasks/72d4b0c6-dfb4-4e6d-aec0-5039476d3583 |
| Verdict: | Malicious activity |
| Analysis date: | June 27, 2022, 10:08:22 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/x-7z-compressed |
| File info: | 7-zip archive data, version 0.4 |
| MD5: | 6D4FA8AB3B7C2D9433C92141D1897608 |
| SHA1: | 88DA8EE0C7E27DF69103B0719BDE71804A6714FB |
| SHA256: | 83DFA333E40CAFC2C7E62FECDDC9F66A3441498C1EB5D5E36B31C469BC6E8506 |
| SSDEEP: | 98304:LuLx3GvI4FtQJIgtVAu02ZBzJE66S3AEO9J+wSAq0iujUvR4bEQP+mM2y8CIHr:sx3GvI4F2JIsAUL6wAEMAzADiuo2V+X4 |
MALICIOUS
Drops executable file immediately after starts
- WinRAR.exe (PID: 3212)
- Explorer.EXE (PID: 764)
Application was dropped or rewritten from another process
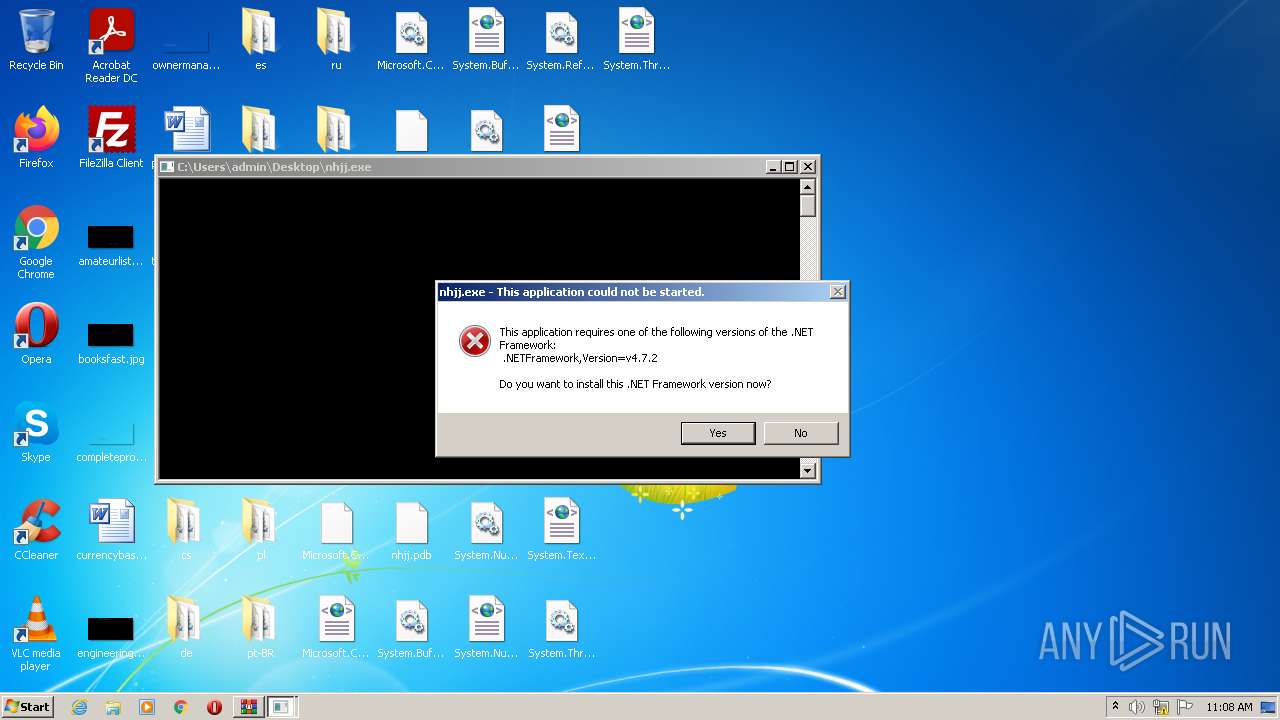
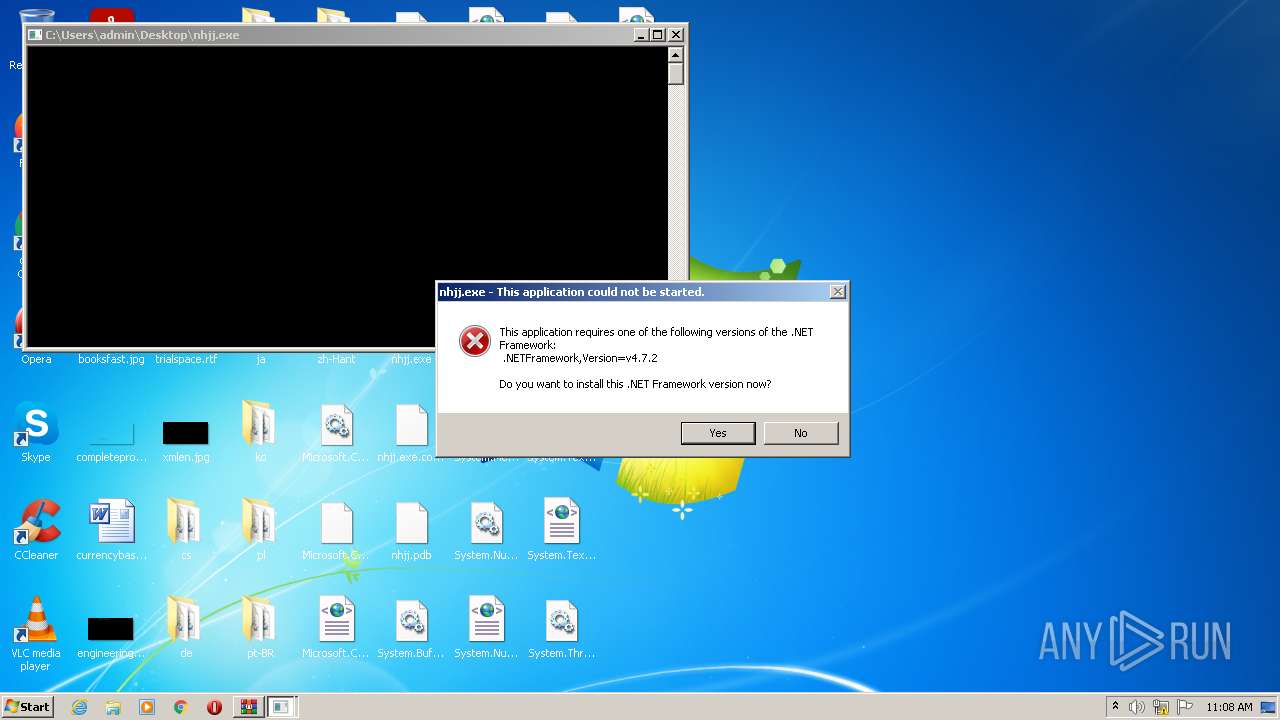
- nhjj.exe (PID: 4024)
- nhjj.exe (PID: 3176)
- nhjj.exe (PID: 2152)
- nhjj.exe (PID: 2804)
- nhjj.exe (PID: 2360)
- nhjj.exe (PID: 2068)
Loads dropped or rewritten executable
- SearchProtocolHost.exe (PID: 3604)
- Explorer.EXE (PID: 764)
SUSPICIOUS
Checks supported languages
- WinRAR.exe (PID: 3212)
- nhjj.exe (PID: 4024)
- nhjj.exe (PID: 2804)
- nhjj.exe (PID: 2068)
Reads the computer name
- WinRAR.exe (PID: 3212)
- nhjj.exe (PID: 4024)
- nhjj.exe (PID: 2804)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 3212)
- Explorer.EXE (PID: 764)
Drops a file with a compile date too recent
- WinRAR.exe (PID: 3212)
- Explorer.EXE (PID: 764)
Reads Microsoft Outlook installation path
- iexplore.exe (PID: 3380)
- iexplore.exe (PID: 3948)
Starts Internet Explorer
- nhjj.exe (PID: 4024)
- nhjj.exe (PID: 2804)
INFO
Dropped object may contain Bitcoin addresses
- WinRAR.exe (PID: 3212)
Reads the computer name
- iexplore.exe (PID: 3380)
- iexplore.exe (PID: 2520)
- iexplore.exe (PID: 3520)
- iexplore.exe (PID: 3948)
Checks supported languages
- iexplore.exe (PID: 3380)
- iexplore.exe (PID: 2520)
- iexplore.exe (PID: 3948)
- iexplore.exe (PID: 3520)
Manual execution by user
- nhjj.exe (PID: 3176)
- nhjj.exe (PID: 4024)
- nhjj.exe (PID: 2152)
- nhjj.exe (PID: 2804)
Changes internet zones settings
- iexplore.exe (PID: 2520)
- iexplore.exe (PID: 3520)
Application launched itself
- iexplore.exe (PID: 2520)
- iexplore.exe (PID: 3520)
Checks Windows Trust Settings
- iexplore.exe (PID: 3948)
- iexplore.exe (PID: 3380)
Reads settings of System Certificates
- iexplore.exe (PID: 3380)
- iexplore.exe (PID: 3948)
Reads the date of Windows installation
- iexplore.exe (PID: 2520)
- iexplore.exe (PID: 3520)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .7z | | | 7-Zip compressed archive (v0.4) (57.1) |
|---|---|---|
| .7z | | | 7-Zip compressed archive (gen) (42.8) |
Total processes
61
Monitored processes
13
Malicious processes
4
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 764 | C:\Windows\Explorer.EXE | C:\Windows\Explorer.EXE | — | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Explorer Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2068 | "C:\Users\admin\Desktop\nhjj.exe" | C:\Users\admin\Desktop\nhjj.exe | Explorer.EXE | ||||||||||||
User: admin Integrity Level: HIGH Description: nhjj Exit code: 2148734720 Version: 1.0.0.0 Modules
| |||||||||||||||
| 2152 | "C:\Users\admin\Desktop\nhjj.exe" | C:\Users\admin\Desktop\nhjj.exe | — | Explorer.EXE | |||||||||||
User: admin Integrity Level: MEDIUM Description: nhjj Exit code: 3221226540 Version: 1.0.0.0 Modules
| |||||||||||||||
| 2360 | "C:\Users\admin\Desktop\nhjj.exe" | C:\Users\admin\Desktop\nhjj.exe | — | Explorer.EXE | |||||||||||
User: admin Integrity Level: MEDIUM Description: nhjj Exit code: 3221226540 Version: 1.0.0.0 Modules
| |||||||||||||||
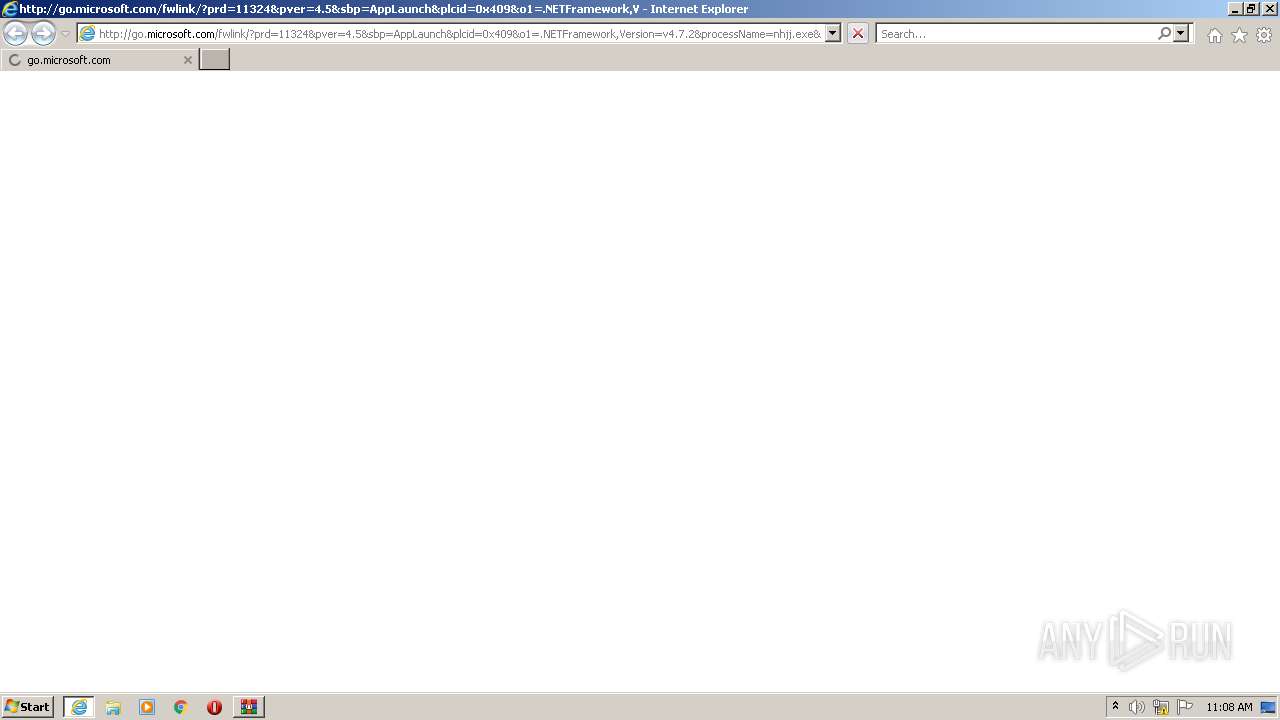
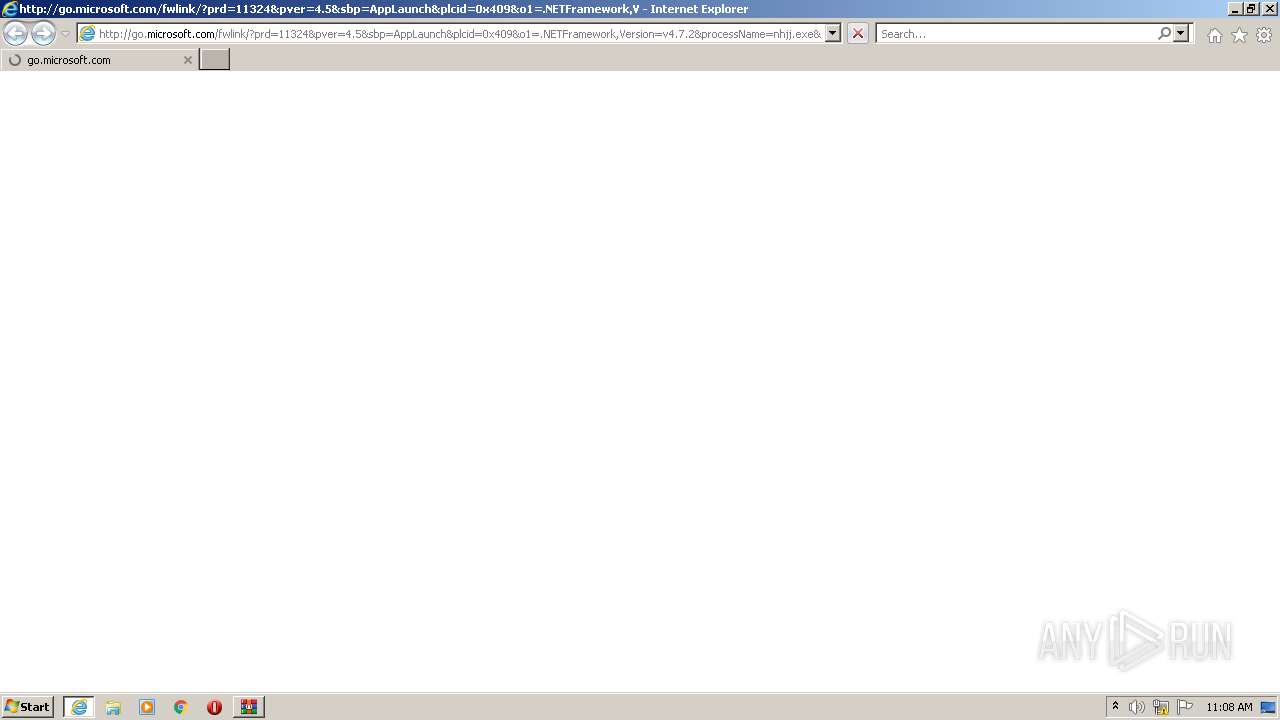
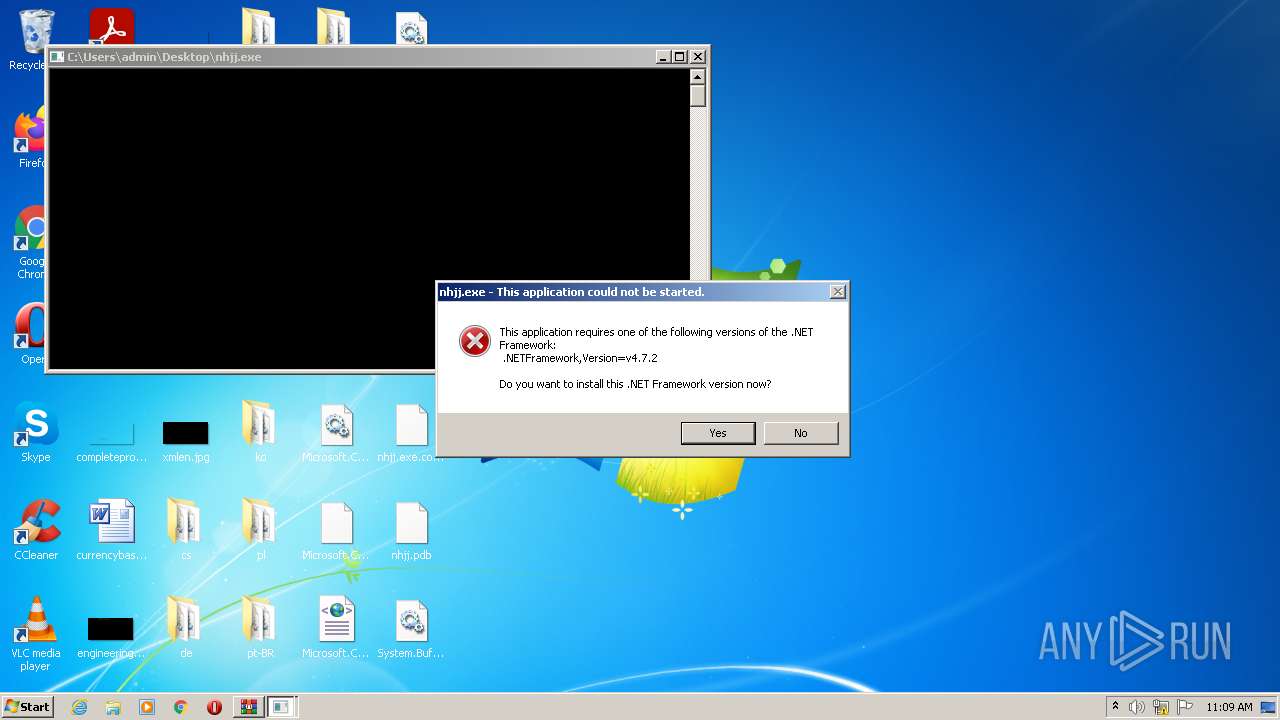
| 2520 | "C:\Program Files\Internet Explorer\iexplore.exe" http://go.microsoft.com/fwlink/?prd=11324&pver=4.5&sbp=AppLaunch&plcid=0x409&o1=.NETFramework,Version=v4.7.2&processName=nhjj.exe&platform=0000&osver=5&isServer=0&shimver=4.0.30319.34209 | C:\Program Files\Internet Explorer\iexplore.exe | — | nhjj.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Internet Explorer Exit code: 1 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 2804 | "C:\Users\admin\Desktop\nhjj.exe" | C:\Users\admin\Desktop\nhjj.exe | Explorer.EXE | ||||||||||||
User: admin Integrity Level: HIGH Description: nhjj Exit code: 2148734720 Version: 1.0.0.0 Modules
| |||||||||||||||
| 3176 | "C:\Users\admin\Desktop\nhjj.exe" | C:\Users\admin\Desktop\nhjj.exe | — | Explorer.EXE | |||||||||||
User: admin Integrity Level: MEDIUM Description: nhjj Exit code: 3221226540 Version: 1.0.0.0 Modules
| |||||||||||||||
| 3212 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Temp\Debug.7z" | C:\Program Files\WinRAR\WinRAR.exe | Explorer.EXE | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
| 3380 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:2520 CREDAT:275457 /prefetch:2 | C:\Program Files\Internet Explorer\iexplore.exe | iexplore.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 3520 | "C:\Program Files\Internet Explorer\iexplore.exe" http://go.microsoft.com/fwlink/?prd=11324&pver=4.5&sbp=AppLaunch&plcid=0x409&o1=.NETFramework,Version=v4.7.2&processName=nhjj.exe&platform=0000&osver=5&isServer=0&shimver=4.0.30319.34209 | C:\Program Files\Internet Explorer\iexplore.exe | — | nhjj.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Internet Explorer Exit code: 1 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
Total events
21 811
Read events
21 440
Write events
365
Delete events
6
Modification events
| (PID) Process: | (3212) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (3212) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (3212) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\16C\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (3212) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\virtio_ivshmem_master_build.zip | |||
| (PID) Process: | (3212) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\Win7-KB3191566-x86.zip | |||
| (PID) Process: | (3212) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\Debug.7z | |||
| (PID) Process: | (3212) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (3212) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (3212) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (3212) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
Executable files
56
Suspicious files
32
Text files
31
Unknown types
12
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3212 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3212.17101\Microsoft.CodeAnalysis.CSharp.xml | xml | |
MD5:— | SHA256:— | |||
| 3212 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3212.17101\Microsoft.CodeAnalysis.xml | xml | |
MD5:— | SHA256:— | |||
| 3212 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3212.17101\Microsoft.CodeAnalysis.CSharp.pdb | binary | |
MD5:— | SHA256:— | |||
| 3212 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3212.17101\cs\Microsoft.CodeAnalysis.CSharp.resources.dll | executable | |
MD5:— | SHA256:— | |||
| 3212 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3212.17101\nhjj.pdb | pdb | |
MD5:— | SHA256:— | |||
| 3212 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3212.17101\Microsoft.CodeAnalysis.pdb | binary | |
MD5:— | SHA256:— | |||
| 3212 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3212.17101\de\Microsoft.CodeAnalysis.resources.dll | executable | |
MD5:— | SHA256:— | |||
| 3212 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3212.17101\es\Microsoft.CodeAnalysis.resources.dll | executable | |
MD5:— | SHA256:— | |||
| 3212 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3212.17101\de\Microsoft.CodeAnalysis.CSharp.resources.dll | executable | |
MD5:— | SHA256:— | |||
| 3212 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3212.17101\cs\Microsoft.CodeAnalysis.resources.dll | executable | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
2
TCP/UDP connections
9
DNS requests
7
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3948 | iexplore.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTBL0V27RVZ7LBduom%2FnYB45SPUEwQU5Z1ZMIJHWMys%2BghUNoZ7OrUETfACEA8Ull8gIGmZT9XHrHiJQeI%3D | US | der | 1.47 Kb | whitelisted |
3380 | iexplore.exe | GET | 200 | 178.79.242.128:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?19a1f92e954799a8 | DE | compressed | 4.70 Kb | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
3380 | iexplore.exe | 178.79.242.128:80 | ctldl.windowsupdate.com | Limelight Networks, Inc. | DE | malicious |
3380 | iexplore.exe | 93.184.220.29:80 | ocsp.digicert.com | MCI Communications Services, Inc. d/b/a Verizon Business | US | whitelisted |
3948 | iexplore.exe | 93.184.220.29:80 | ocsp.digicert.com | MCI Communications Services, Inc. d/b/a Verizon Business | US | whitelisted |
3948 | iexplore.exe | 104.89.38.104:443 | go.microsoft.com | Akamai Technologies, Inc. | NL | malicious |
3380 | iexplore.exe | 104.89.38.104:443 | go.microsoft.com | Akamai Technologies, Inc. | NL | malicious |
— | — | 192.168.100.2:53 | — | — | — | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
www.microsoft.com |
| whitelisted |
go.microsoft.com |
| whitelisted |
ctldl.windowsupdate.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
dotnet.microsoft.com |
| whitelisted |