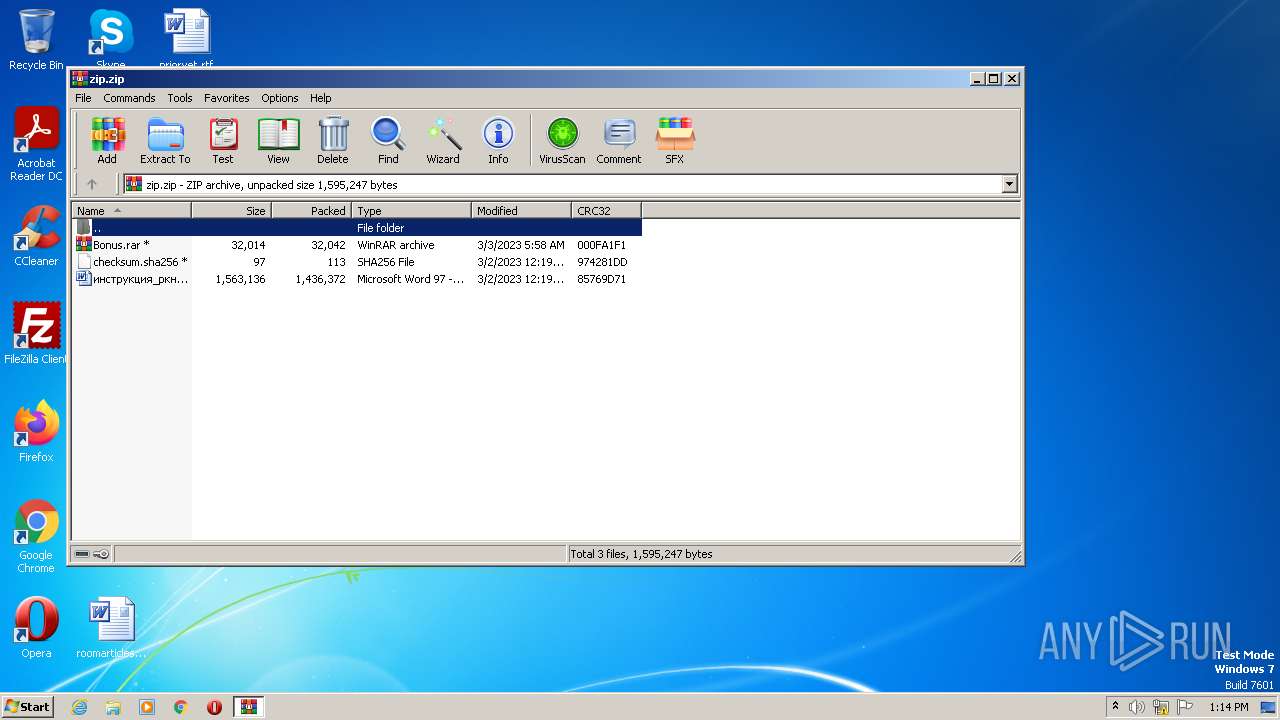
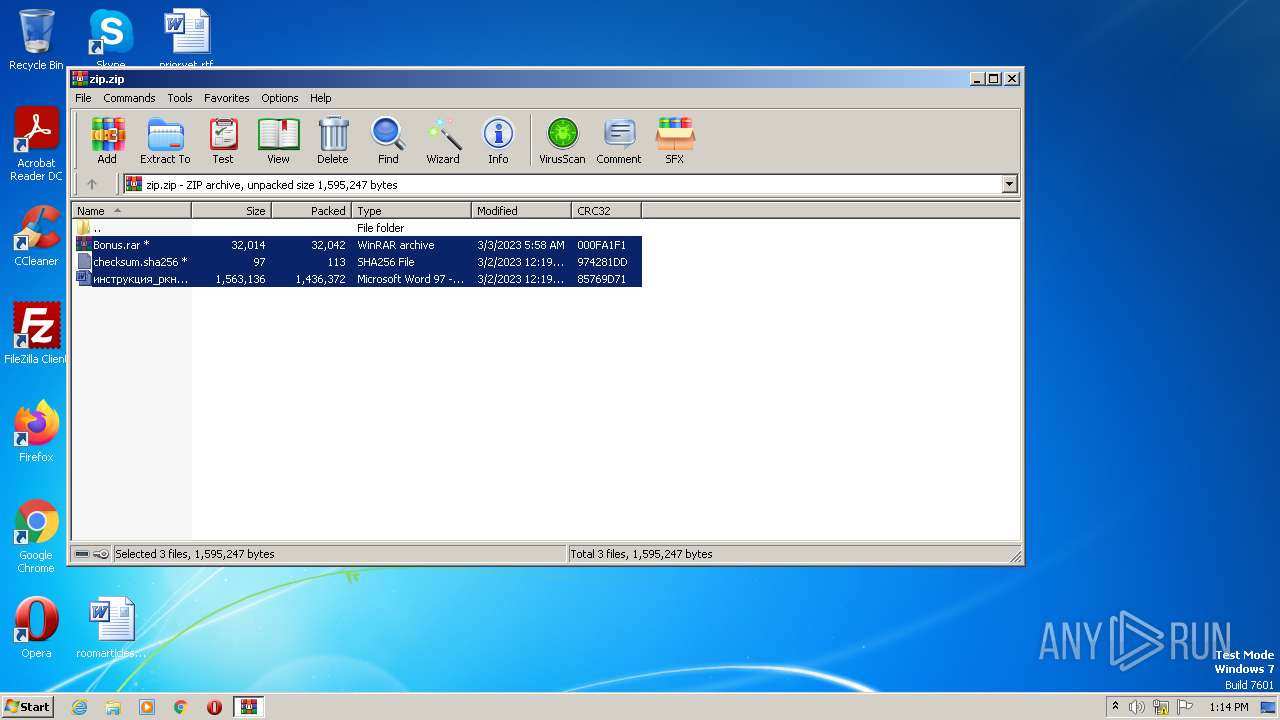
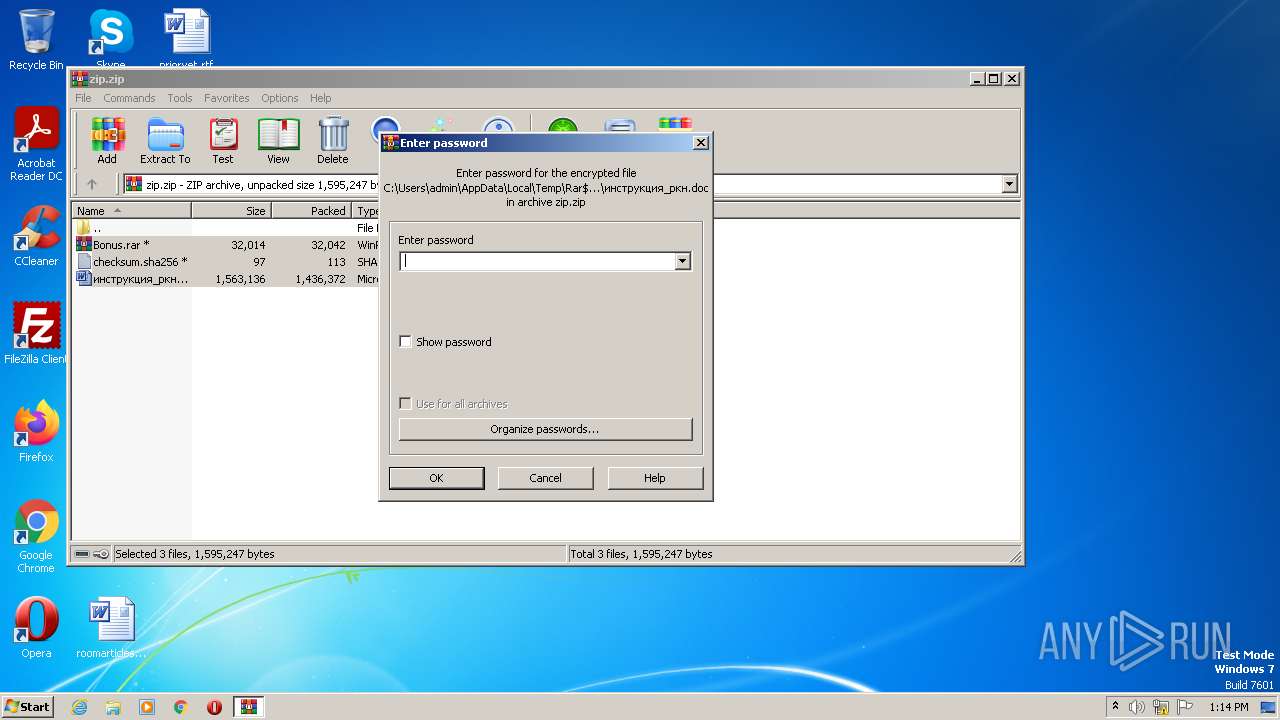
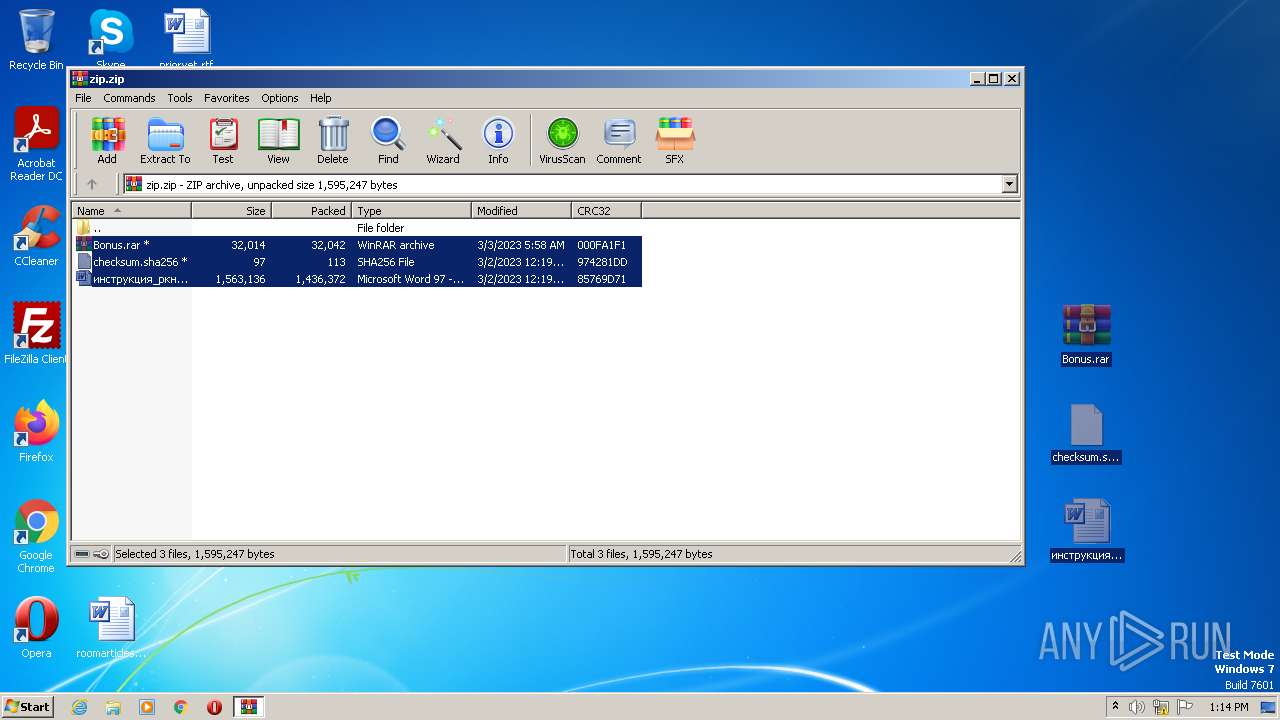
| File name: | zip |
| Full analysis: | https://app.any.run/tasks/bdf6b832-b6f9-40ee-a889-ea405cf1cc96 |
| Verdict: | Malicious activity |
| Analysis date: | April 01, 2023, 12:14:02 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract |
| MD5: | 7F7BA3D6DA851D654037FE94E5442ACE |
| SHA1: | 72ED47050B07CB27603F9CE2DCA7F5204A35D2F9 |
| SHA256: | 83D5AD1F70CBE68C591E97E5AB7491D4E308A8BC931263CC4B937A433F02A2A4 |
| SSDEEP: | 24576:cJYtjyYU1juGMC72LHa+UdEnL6bc3hRAwLdhN4e0M/uWKrz8SZWep5nysp2bT1vO:ltjyZZue7J+UanLzvhD/ut0vep5ysQFm |
MALICIOUS
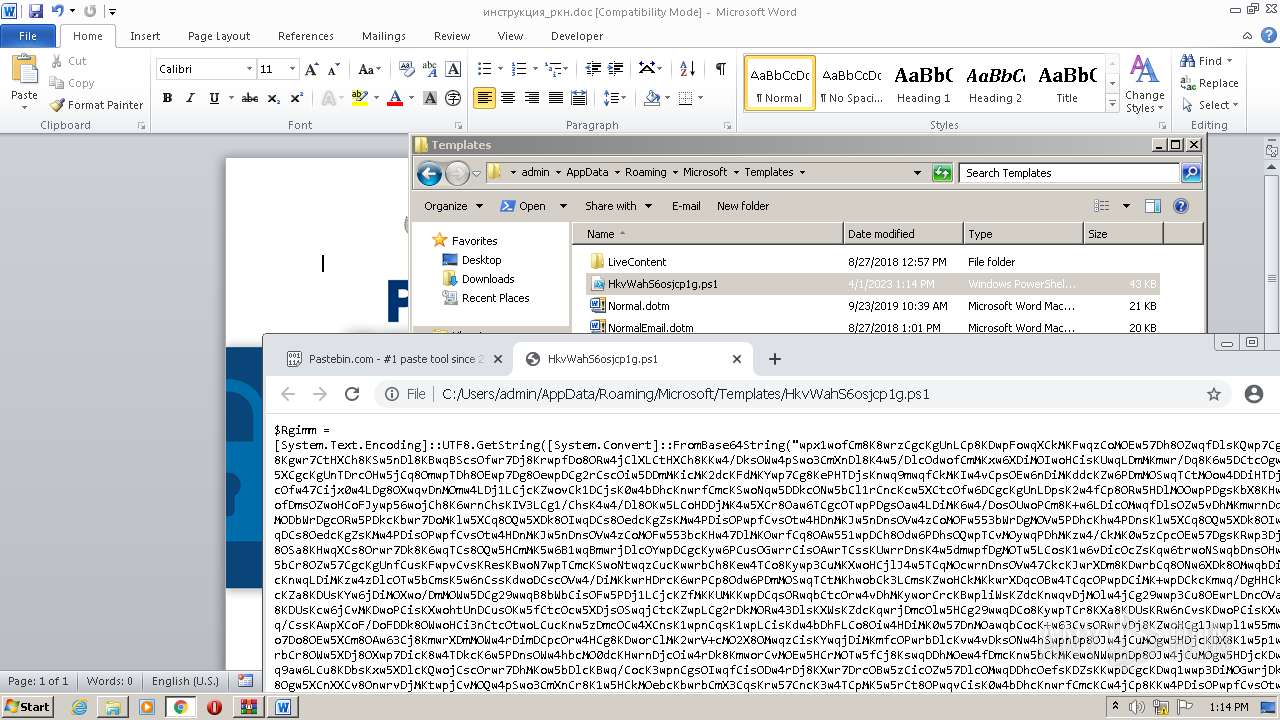
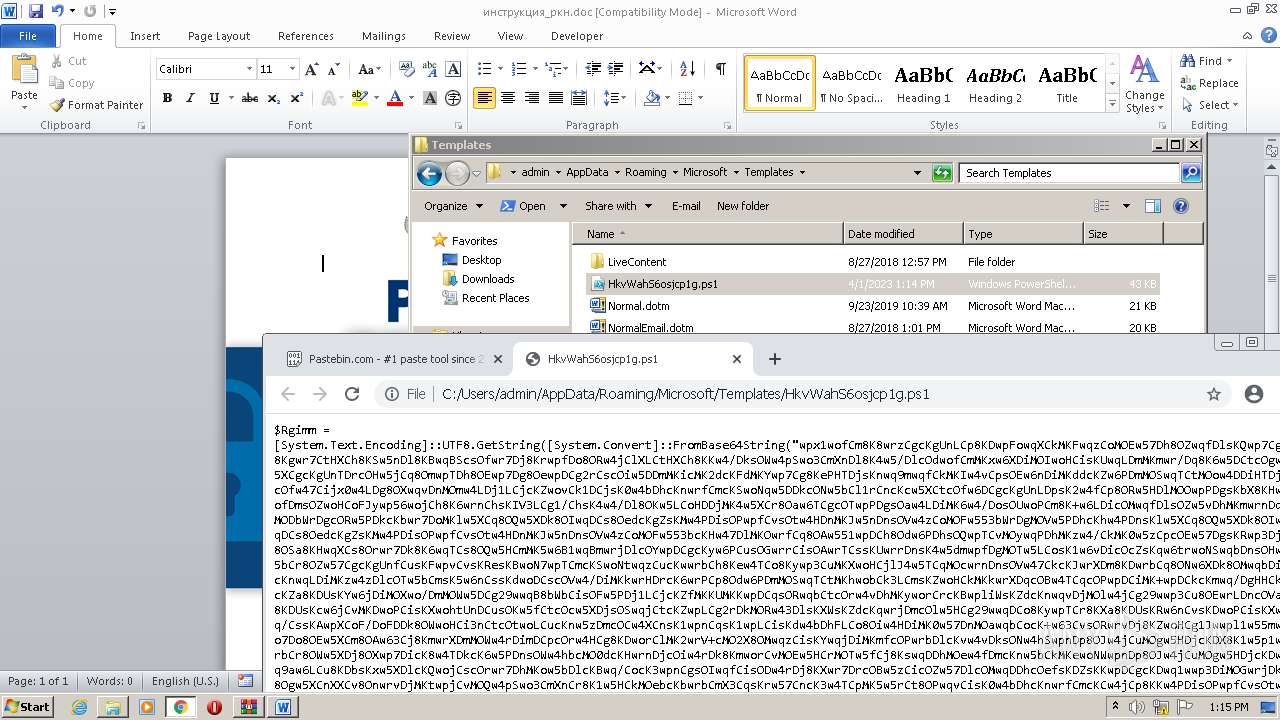
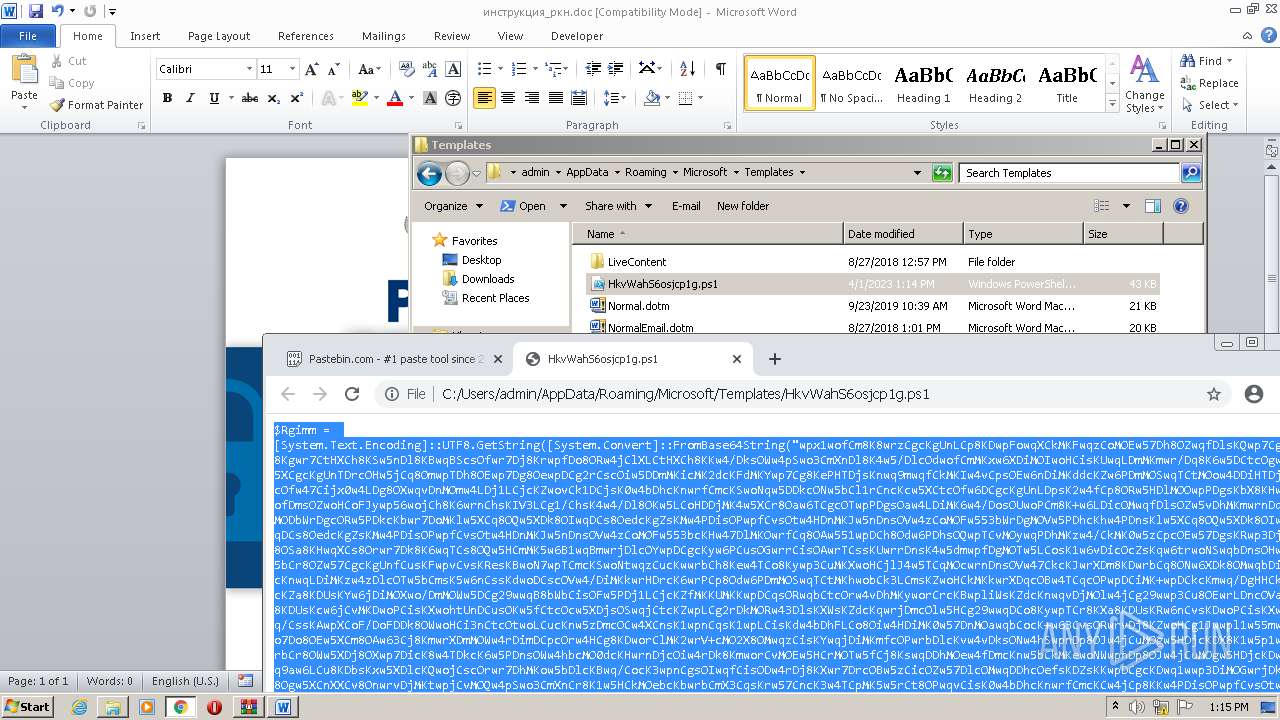
Run PowerShell with an invisible window
- powershell.exe (PID: 4064)
Starts POWERSHELL.EXE for commands execution
- WINWORD.EXE (PID: 3480)
Bypass execution policy to execute commands
- powershell.exe (PID: 4064)
Microsoft Office executes commands via PowerShell or Cmd
- WINWORD.EXE (PID: 3480)
Unusual execution from MS Office
- WINWORD.EXE (PID: 3480)
SUSPICIOUS
The process executes Powershell scripts
- WINWORD.EXE (PID: 3480)
The process hide an interactive prompt from the user
- WINWORD.EXE (PID: 3480)
The process hides Powershell's copyright startup banner
- WINWORD.EXE (PID: 3480)
Reads the Internet Settings
- powershell.exe (PID: 4064)
Unusual connection from system programs
- powershell.exe (PID: 4064)
INFO
Manual execution by a user
- WINWORD.EXE (PID: 3480)
- chrome.exe (PID: 3468)
- explorer.exe (PID: 2892)
The process checks LSA protection
- explorer.exe (PID: 2892)
- powershell.exe (PID: 4064)
The process uses the downloaded file
- WINWORD.EXE (PID: 3480)
Application launched itself
- chrome.exe (PID: 3468)
Create files in a temporary directory
- powershell.exe (PID: 4064)
- chrome.exe (PID: 3468)
Reads security settings of Internet Explorer
- powershell.exe (PID: 4064)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipFileName: | - |
|---|---|
| ZipUncompressedSize: | 1563136 |
| ZipCompressedSize: | 1436372 |
| ZipCRC: | 0x85769d71 |
| ZipModifyDate: | 2023:03:02 12:19:00 |
| ZipCompression: | Unknown (99) |
| ZipBitFlag: | 0x0809 |
| ZipRequiredVersion: | 20 |
Total processes
68
Monitored processes
27
Malicious processes
1
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 128 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --field-trial-handle=1036,5261105055207911919,11698394732358019821,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=utility --mojo-platform-channel-handle=3044 /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 Modules
| |||||||||||||||
| 852 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=1036,5261105055207911919,11698394732358019821,131072 --enable-features=PasswordImport --disable-gpu-compositing --lang=en-US --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=11 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=2792 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 Modules
| |||||||||||||||
| 1012 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=chrome.mojom.UtilWin --field-trial-handle=1036,5261105055207911919,11698394732358019821,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=none --mojo-platform-channel-handle=3664 /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 Modules
| |||||||||||||||
| 1416 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=1036,5261105055207911919,11698394732358019821,131072 --enable-features=PasswordImport --lang=en-US --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=6 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=1936 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 Modules
| |||||||||||||||
| 2120 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=network.mojom.NetworkService --field-trial-handle=1036,5261105055207911919,11698394732358019821,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=network --mojo-platform-channel-handle=1288 /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | chrome.exe | ||||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 Modules
| |||||||||||||||
| 2356 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=1036,5261105055207911919,11698394732358019821,131072 --enable-features=PasswordImport --disable-gpu-compositing --lang=en-US --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=10 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=3000 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 Modules
| |||||||||||||||
| 2392 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=1036,5261105055207911919,11698394732358019821,131072 --enable-features=PasswordImport --disable-gpu-compositing --lang=en-US --extension-process --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=19 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=3076 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 Modules
| |||||||||||||||
| 2432 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --field-trial-handle=1036,5261105055207911919,11698394732358019821,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=utility --mojo-platform-channel-handle=3624 /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 Modules
| |||||||||||||||
| 2512 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\Desktop\zip.zip" | C:\Program Files\WinRAR\WinRAR.exe | — | explorer.exe | |||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
| 2672 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=gpu-process --field-trial-handle=1036,5261105055207911919,11698394732358019821,131072 --enable-features=PasswordImport --gpu-preferences=MAAAAAAAAADgAAAwAAAAAAAAAAAAAAAAAABgAAAAAAAQAAAAAAAAAAAAAAAAAAAAKAAAAAQAAAAgAAAAAAAAACgAAAAAAAAAMAAAAAAAAAA4AAAAAAAAABAAAAAAAAAAAAAAAAUAAAAQAAAAAAAAAAAAAAAGAAAAEAAAAAAAAAABAAAABQAAABAAAAAAAAAAAQAAAAYAAAA= --use-gl=swiftshader-webgl --mojo-platform-channel-handle=2404 /prefetch:2 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 Modules
| |||||||||||||||
Total events
33 128
Read events
31 954
Write events
830
Delete events
344
Modification events
| (PID) Process: | (2512) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\16D\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (2512) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\virtio_ivshmem_master_build.zip | |||
| (PID) Process: | (2512) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\Win7-KB3191566-x86.zip | |||
| (PID) Process: | (2512) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\phacker.zip | |||
| (PID) Process: | (2512) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (2512) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (2512) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (2512) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (3468) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BLBeacon |
| Operation: | write | Name: | failed_count |
Value: 0 | |||
| (PID) Process: | (3468) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BLBeacon |
| Operation: | write | Name: | state |
Value: 1 | |||
Executable files
0
Suspicious files
350
Text files
264
Unknown types
28
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3468 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\BrowserMetrics\BrowserMetrics-6428201D-D8C.pma | — | |
MD5:— | SHA256:— | |||
| 2512 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRb2512.23641\Bonus.rar | compressed | |
MD5:— | SHA256:— | |||
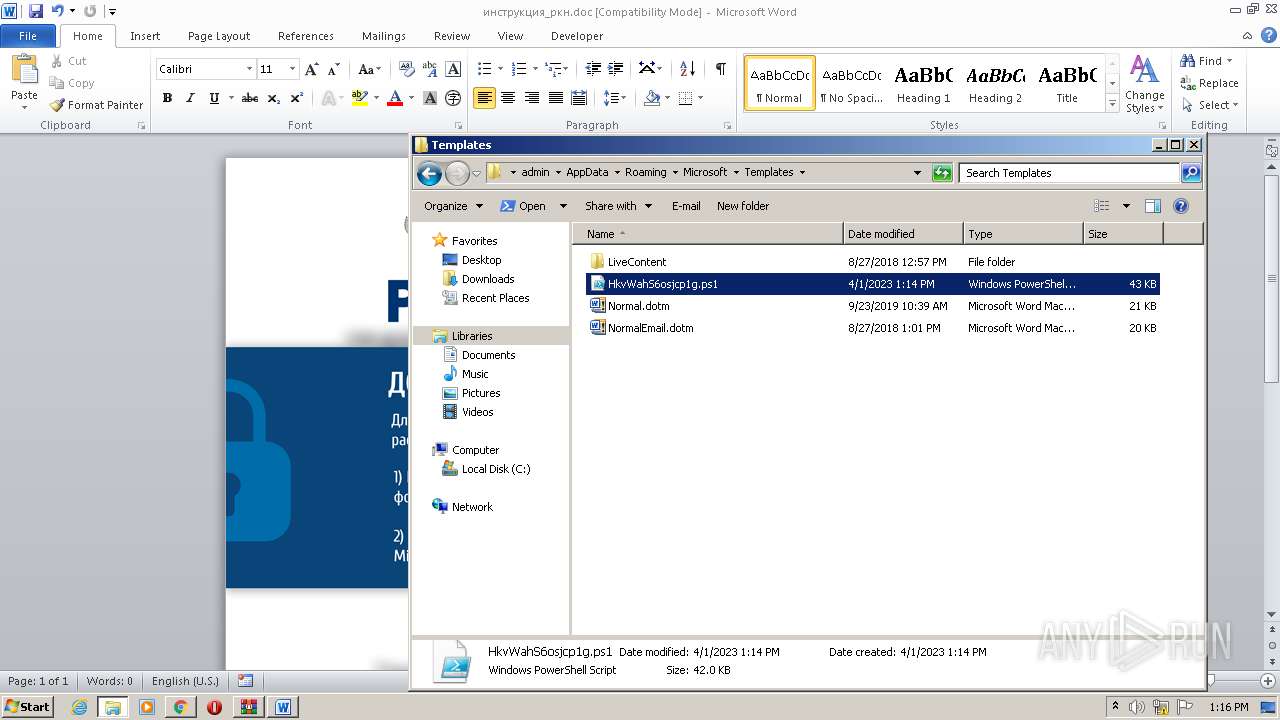
| 2512 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRb2512.23641\инструкция_ркн.doc | document | |
MD5:— | SHA256:— | |||
| 3468 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\043e054a-415e-4a52-9c55-12d96083b4c3.tmp | text | |
MD5:— | SHA256:— | |||
| 2512 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRb2512.23641\checksum.sha256 | text | |
MD5:— | SHA256:— | |||
| 3468 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Preferences | text | |
MD5:— | SHA256:— | |||
| 3468 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Platform Notifications\LOG.old | text | |
MD5:EF1D5606A483BB6C72C81A3F649BEB18 | SHA256:BA083E7585ADA9936944FE56BC0141A544F18A01C3424E5C9F02375B34FE3D45 | |||
| 3468 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\083f1915-5c85-4cbb-9864-257e1ec3a58e.tmp | binary | |
MD5:5058F1AF8388633F609CADB75A75DC9D | SHA256:— | |||
| 3956 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\CrashpadMetrics.pma | binary | |
MD5:03C4F648043A88675A920425D824E1B3 | SHA256:F91DBB7C64B4582F529C968C480D2DCE1C8727390482F31E4355A27BB3D9B450 | |||
| 3468 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Sync Data\LevelDB\LOG.old~RF253033.TMP | text | |
MD5:64AD8ED3E666540337BA541C549F72F7 | SHA256:BECBDB08B5B37D203A85F2E974407334053BB1D2270F0B3C9A4DB963896F2206 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
13
TCP/UDP connections
37
DNS requests
22
Threats
2
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
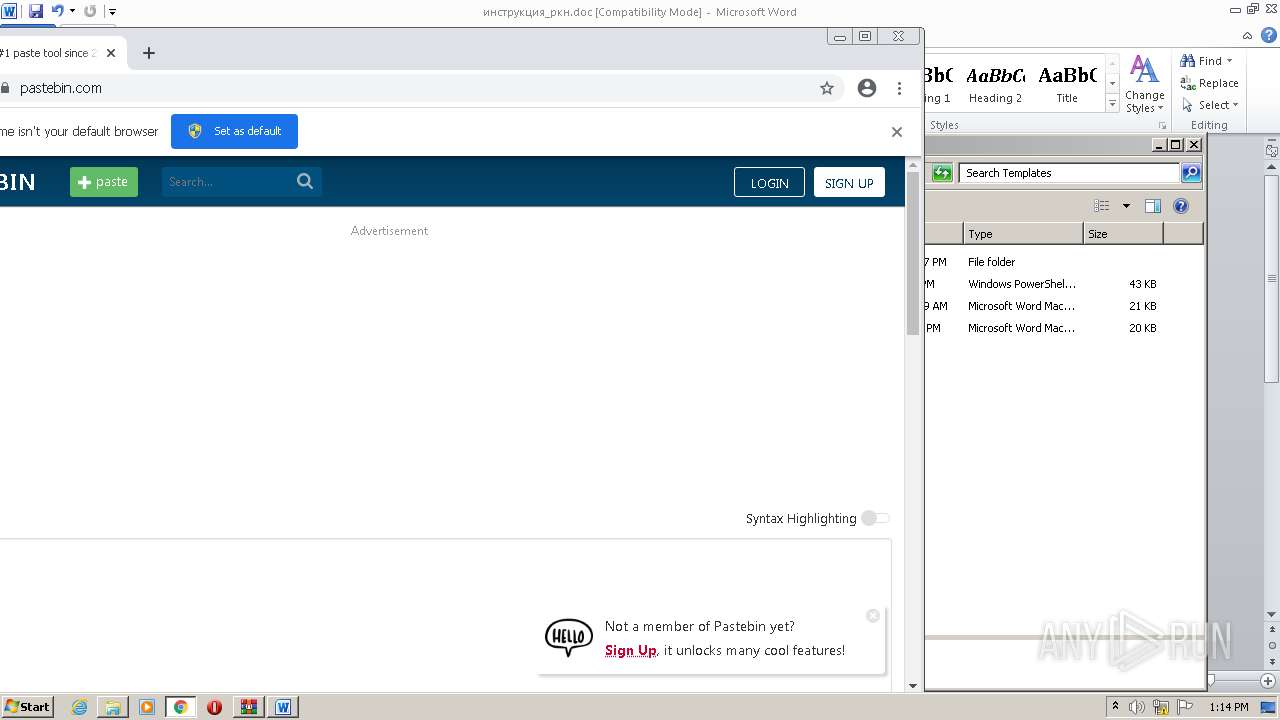
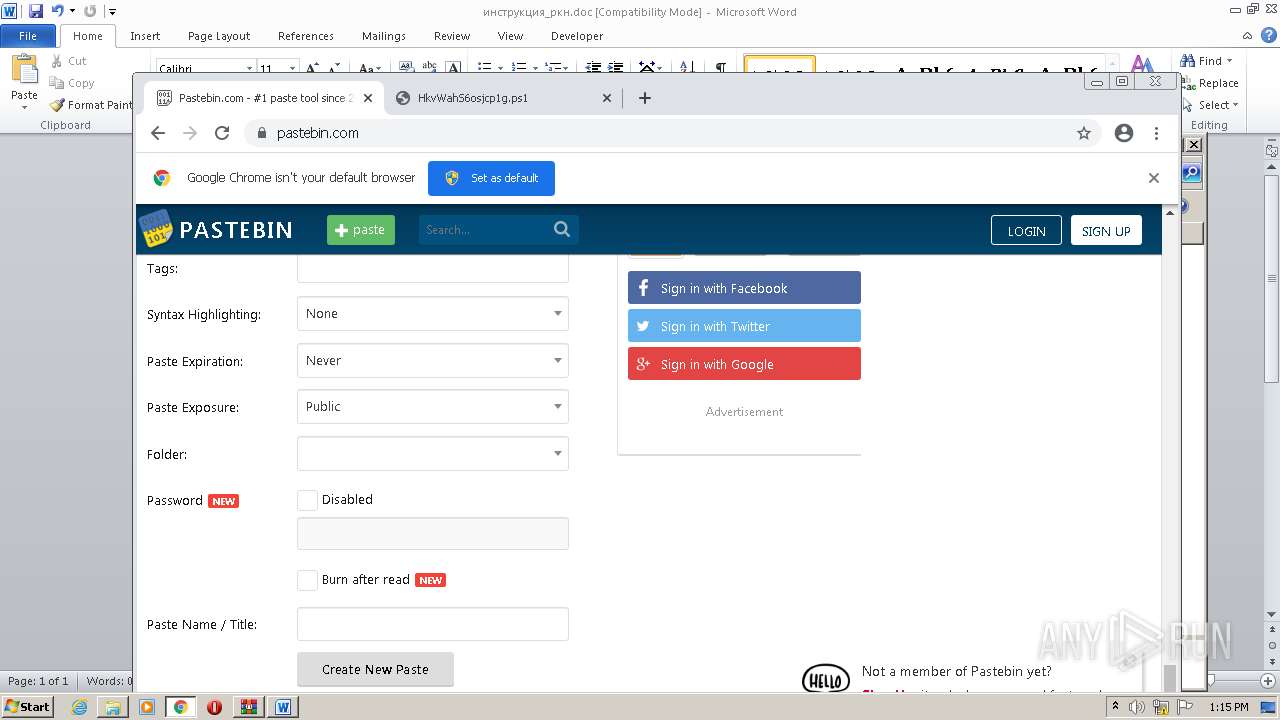
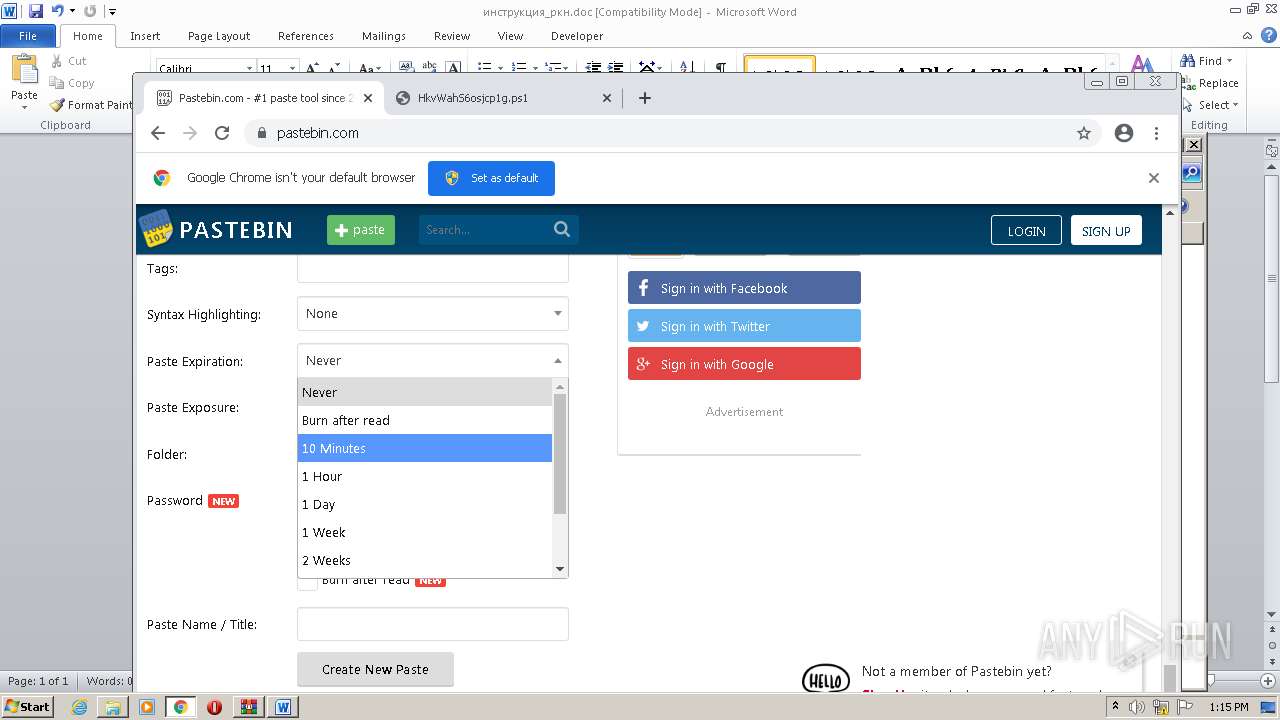
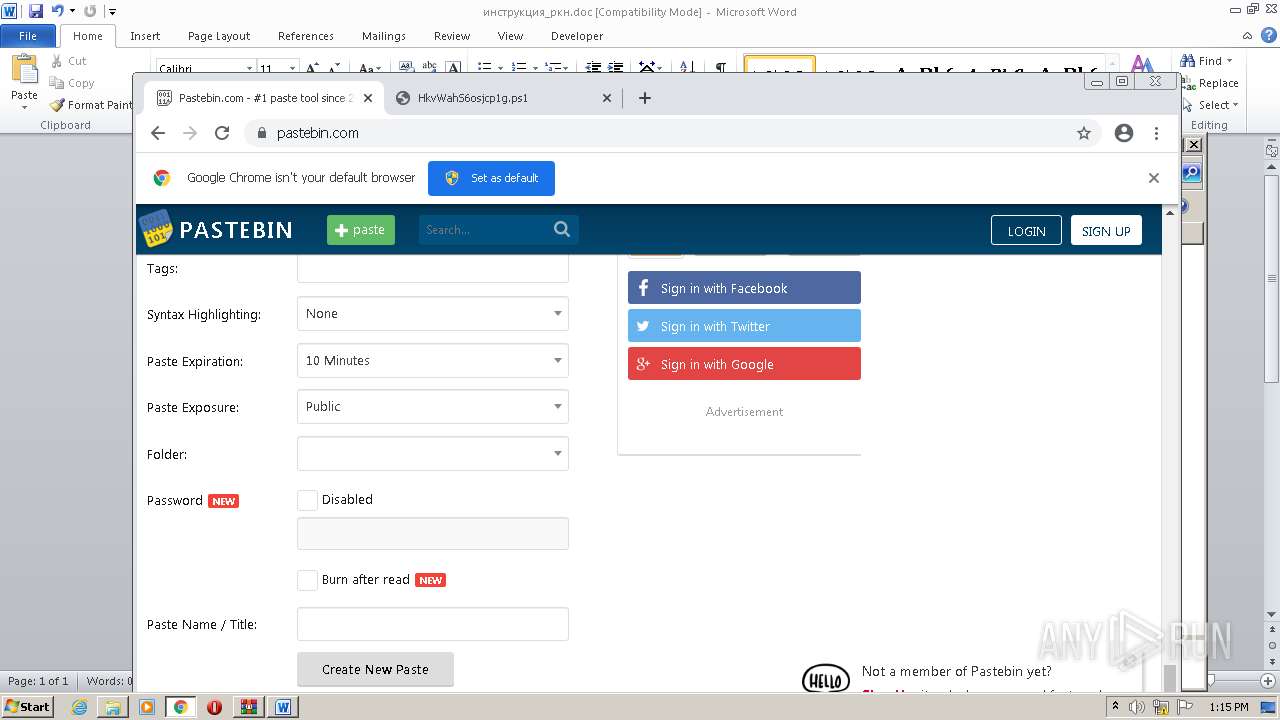
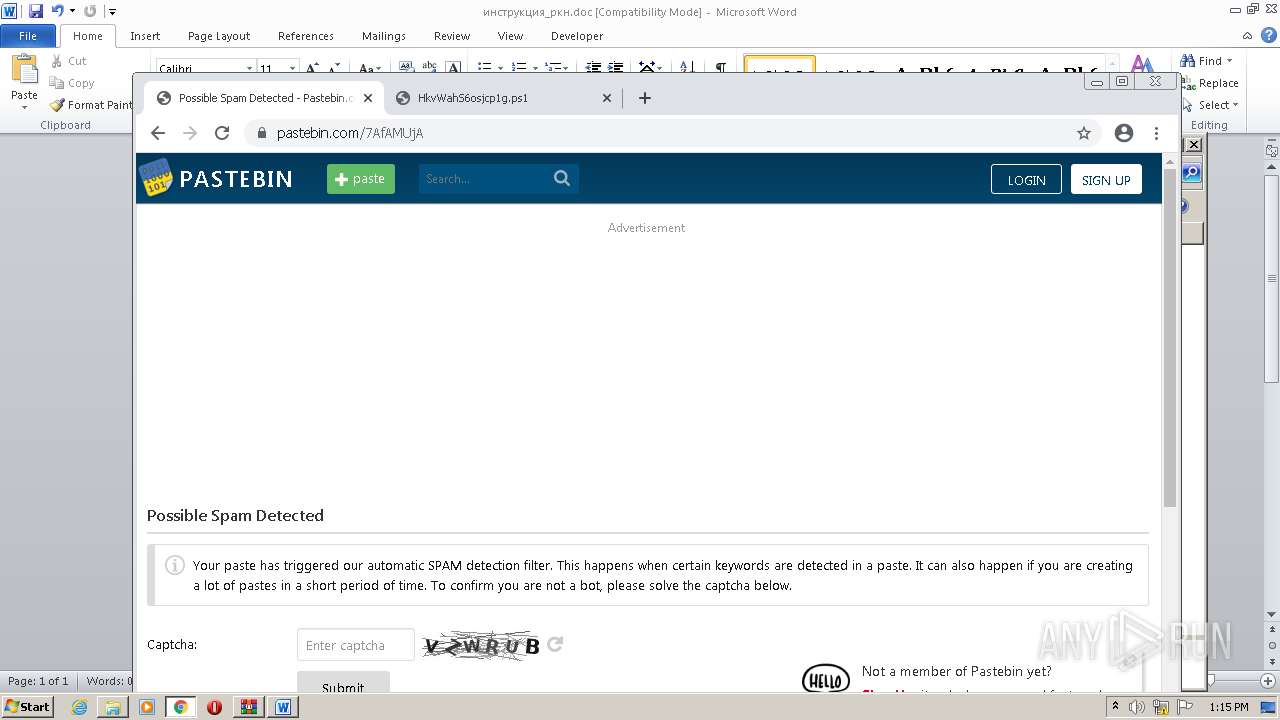
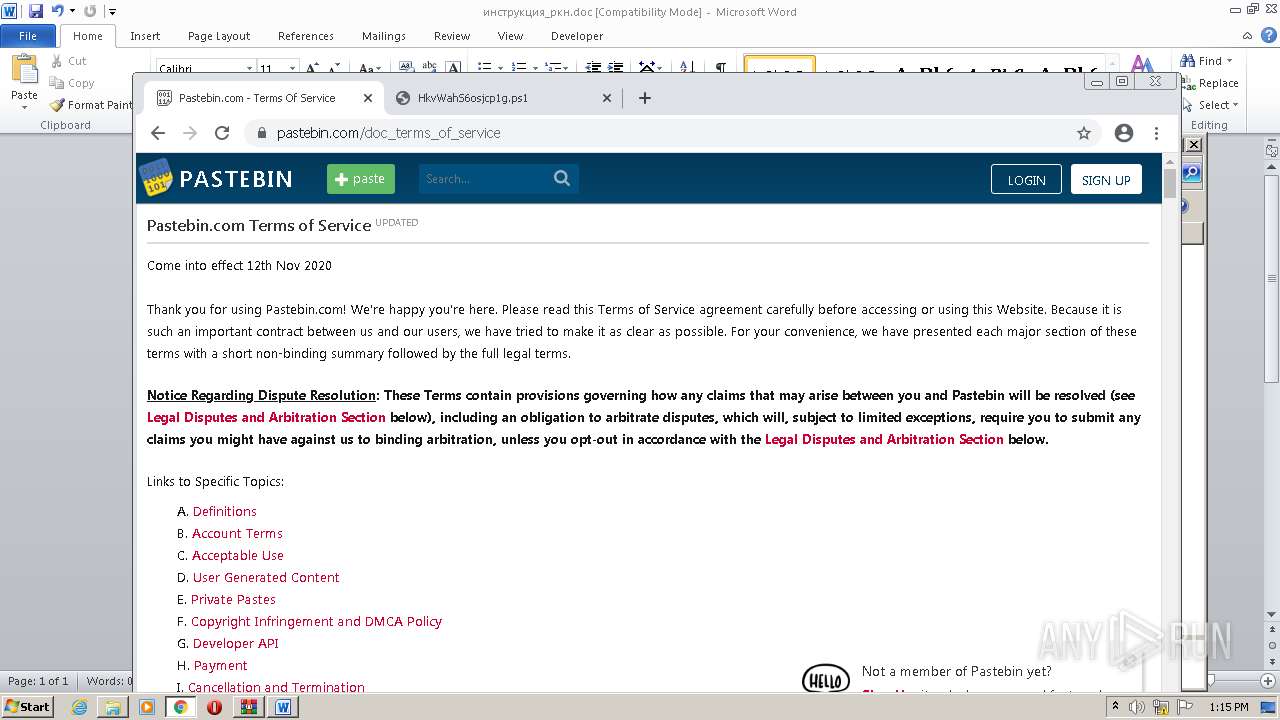
2120 | chrome.exe | GET | 301 | 104.20.68.143:80 | http://pastebin.com/ | US | — | — | malicious |
860 | svchost.exe | GET | 206 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/j2hxfei2occ5siitujtlwgp6xi_3/ojhpjlocmbogdgmfpkhlaaeamibhnphh_3_all_gplutbkdljxxbjolk3siq7kive.crx3 | US | binary | 9.70 Kb | whitelisted |
860 | svchost.exe | GET | 206 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/j2hxfei2occ5siitujtlwgp6xi_3/ojhpjlocmbogdgmfpkhlaaeamibhnphh_3_all_gplutbkdljxxbjolk3siq7kive.crx3 | US | binary | 9.65 Kb | whitelisted |
860 | svchost.exe | GET | 206 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/j2hxfei2occ5siitujtlwgp6xi_3/ojhpjlocmbogdgmfpkhlaaeamibhnphh_3_all_gplutbkdljxxbjolk3siq7kive.crx3 | US | binary | 42.6 Kb | whitelisted |
860 | svchost.exe | GET | 206 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/j2hxfei2occ5siitujtlwgp6xi_3/ojhpjlocmbogdgmfpkhlaaeamibhnphh_3_all_gplutbkdljxxbjolk3siq7kive.crx3 | US | binary | 20.7 Kb | whitelisted |
860 | svchost.exe | GET | 206 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/j2hxfei2occ5siitujtlwgp6xi_3/ojhpjlocmbogdgmfpkhlaaeamibhnphh_3_all_gplutbkdljxxbjolk3siq7kive.crx3 | US | binary | 9.70 Kb | whitelisted |
860 | svchost.exe | GET | 206 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/j2hxfei2occ5siitujtlwgp6xi_3/ojhpjlocmbogdgmfpkhlaaeamibhnphh_3_all_gplutbkdljxxbjolk3siq7kive.crx3 | US | binary | 86.2 Kb | whitelisted |
860 | svchost.exe | GET | 206 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/j2hxfei2occ5siitujtlwgp6xi_3/ojhpjlocmbogdgmfpkhlaaeamibhnphh_3_all_gplutbkdljxxbjolk3siq7kive.crx3 | US | binary | 152 Kb | whitelisted |
860 | svchost.exe | GET | 206 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/j2hxfei2occ5siitujtlwgp6xi_3/ojhpjlocmbogdgmfpkhlaaeamibhnphh_3_all_gplutbkdljxxbjolk3siq7kive.crx3 | US | binary | 174 Kb | whitelisted |
860 | svchost.exe | GET | 206 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/j2hxfei2occ5siitujtlwgp6xi_3/ojhpjlocmbogdgmfpkhlaaeamibhnphh_3_all_gplutbkdljxxbjolk3siq7kive.crx3 | US | binary | 346 Kb | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2120 | chrome.exe | 142.250.179.238:443 | clients2.google.com | GOOGLE | US | whitelisted |
2120 | chrome.exe | 142.250.179.228:443 | www.google.com | GOOGLE | US | suspicious |
2120 | chrome.exe | 172.217.169.3:443 | clientservices.googleapis.com | GOOGLE | US | whitelisted |
2120 | chrome.exe | 142.250.200.42:443 | fonts.googleapis.com | GOOGLE | US | whitelisted |
2120 | chrome.exe | 142.250.178.1:443 | clients2.googleusercontent.com | GOOGLE | US | whitelisted |
2120 | chrome.exe | 142.250.200.35:443 | www.gstatic.com | GOOGLE | US | whitelisted |
2120 | chrome.exe | 172.217.16.238:443 | apis.google.com | GOOGLE | US | whitelisted |
2120 | chrome.exe | 104.20.68.143:443 | pastebin.com | CLOUDFLARENET | — | malicious |
2120 | chrome.exe | 104.17.25.14:443 | cdnjs.cloudflare.com | CLOUDFLARENET | — | suspicious |
2120 | chrome.exe | 216.239.34.36:443 | region1.google-analytics.com | GOOGLE | US | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
clients2.google.com |
| whitelisted |
www.google.com |
| malicious |
clientservices.googleapis.com |
| whitelisted |
accounts.google.com |
| shared |
clients2.googleusercontent.com |
| whitelisted |
fonts.googleapis.com |
| whitelisted |
www.gstatic.com |
| whitelisted |
apis.google.com |
| whitelisted |
fonts.gstatic.com |
| whitelisted |
pastebin.com |
| malicious |
Threats
PID | Process | Class | Message |
|---|---|---|---|
— | — | Domain Observed Used for C2 Detected | ET MALWARE Win32/Backdoor Related Domain in DNS Lookup (swordoke .com) |
4064 | powershell.exe | Domain Observed Used for C2 Detected | ET MALWARE Observed Win32/Backdoor Related Domain (swordoke .com in TLS SNI) |