| URL: | https://download.lenovo.com/ibmdl/pub/pc/pccbbs/agent/SSClientCommon/UTS/systemupdate507-2019-01-25.exe |
| Full analysis: | https://app.any.run/tasks/779a2b1c-3c60-4d44-bae1-cf69b860cdbf |
| Verdict: | Malicious activity |
| Analysis date: | March 18, 2019, 17:01:16 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MD5: | 40CED23CDA25CE86792573A8F7968800 |
| SHA1: | FC0FD891E4A820442ACF057A6A9E13DDCD7FD221 |
| SHA256: | 83D4879E2929F51AEC0884AE748B422A131D66280B7CCBD1A3830FAC43D72617 |
| SSDEEP: | 3:N8SElDcd3nOSKsMWKEDjBDlmT7KEVocASZQLAC:2SKDcBO5saEDjBg7KpSuJ |
MALICIOUS
Application was dropped or rewritten from another process
- systemupdate507-2019-01-25.exe (PID: 3908)
- systemupdate507-2019-01-25.exe (PID: 2284)
- SUService.exe (PID: 3404)
- ConfigService.exe (PID: 2256)
- susetsched.exe (PID: 3844)
- uncsetting.exe (PID: 2732)
- ConfigScheduledTask.exe (PID: 2804)
- StartSuService.exe (PID: 3944)
- tvsu.exe (PID: 2724)
- ConfigService.exe (PID: 128)
- TvsuCommandLauncher.exe (PID: 2504)
- TVSU2DirAllowWriting.exe (PID: 1816)
- uncserver.exe (PID: 3156)
- UACSdk.exe (PID: 3860)
- uncsetting.exe (PID: 3492)
- Tvsukernel.exe (PID: 2836)
- TvsuCommandLauncher.exe (PID: 3668)
- ia.exe (PID: 2584)
- ConfigService.exe (PID: 3500)
- ia.exe (PID: 996)
Loads dropped or rewritten executable
- SUService.exe (PID: 3404)
- InstallUtil.exe (PID: 2652)
- ConfigScheduledTask.exe (PID: 2804)
- TvsuCommandLauncher.exe (PID: 3668)
- uncserver.exe (PID: 3156)
- Tvsukernel.exe (PID: 2836)
- TvsuCommandLauncher.exe (PID: 2504)
- ia.exe (PID: 996)
- ia.exe (PID: 2584)
Loads the Task Scheduler COM API
- susetsched.exe (PID: 3844)
- schtasks.exe (PID: 3004)
- schtasks.exe (PID: 3504)
Changes settings of System certificates
- certutil.exe (PID: 3600)
- certutil.exe (PID: 2904)
- SUService.exe (PID: 3404)
Uses Task Scheduler to run other applications
- ConfigScheduledTask.exe (PID: 2804)
SUSPICIOUS
Executable content was dropped or overwritten
- chrome.exe (PID: 2876)
- systemupdate507-2019-01-25.tmp (PID: 2664)
- systemupdate507-2019-01-25.exe (PID: 2284)
- systemupdate507-2019-01-25.exe (PID: 3908)
Reads Environment values
- systemupdate507-2019-01-25.tmp (PID: 2664)
- Tvsukernel.exe (PID: 2836)
Starts CMD.EXE for commands execution
- systemupdate507-2019-01-25.tmp (PID: 2664)
- cmd.exe (PID: 2928)
Reads the Windows organization settings
- systemupdate507-2019-01-25.tmp (PID: 2664)
Creates files in the Windows directory
- systemupdate507-2019-01-25.tmp (PID: 2664)
- InstallUtil.exe (PID: 2652)
- certutil.exe (PID: 2904)
- certutil.exe (PID: 3600)
- SUService.exe (PID: 3404)
- ia.exe (PID: 996)
Modifies the open verb of a shell class
- systemupdate507-2019-01-25.tmp (PID: 2664)
Reads Windows owner or organization settings
- systemupdate507-2019-01-25.tmp (PID: 2664)
Creates files in the program directory
- InstallUtil.exe (PID: 2652)
- StartSuService.exe (PID: 3944)
- ConfigScheduledTask.exe (PID: 2804)
- SUService.exe (PID: 3404)
- UACSdk.exe (PID: 3860)
- Tvsukernel.exe (PID: 2836)
- TvsuCommandLauncher.exe (PID: 2504)
- tvsu.exe (PID: 2724)
- TvsuCommandLauncher.exe (PID: 3668)
- ia.exe (PID: 996)
- ia.exe (PID: 2584)
Creates or modifies windows services
- InstallUtil.exe (PID: 2652)
Removes files from Windows directory
- certutil.exe (PID: 3600)
- systemupdate507-2019-01-25.tmp (PID: 2664)
- certutil.exe (PID: 2904)
- SUService.exe (PID: 3404)
Uses NETSH.EXE for network configuration
- uncsetting.exe (PID: 2732)
Uses ICACLS.EXE to modify access control list
- ConfigScheduledTask.exe (PID: 2804)
- Tvsukernel.exe (PID: 2836)
Checks supported languages
- Tvsukernel.exe (PID: 2836)
Low-level read access rights to disk partition
- ia.exe (PID: 2584)
Creates files in the user directory
- ia.exe (PID: 2584)
Reads Internet Cache Settings
- Tvsukernel.exe (PID: 2836)
INFO
Application was dropped or rewritten from another process
- systemupdate507-2019-01-25.tmp (PID: 2664)
- systemupdate507-2019-01-25.tmp (PID: 3364)
Reads settings of System Certificates
- chrome.exe (PID: 2876)
Application launched itself
- chrome.exe (PID: 2876)
Creates a software uninstall entry
- systemupdate507-2019-01-25.tmp (PID: 2664)
Reads Internet Cache Settings
- chrome.exe (PID: 2876)
Creates files in the program directory
- systemupdate507-2019-01-25.tmp (PID: 2664)
Dropped object may contain Bitcoin addresses
- ia.exe (PID: 2584)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
92
Monitored processes
45
Malicious processes
14
Suspicious processes
3
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 128 | "C:\Program Files\Lenovo\System Update\ConfigService.exe" start | C:\Program Files\Lenovo\System Update\ConfigService.exe | — | tvsu.exe | |||||||||||
User: admin Integrity Level: MEDIUM Description: ConfigService Application Exit code: 0 Version: 5, 7, 0, 78 Modules
| |||||||||||||||
| 996 | "C:\Program Files\Lenovo\System Update\egather\\ia.exe" -filename"C:\Program Files\Lenovo\System Update\egather\sysrecomin" -probes REGIONAL_SETTINGS GATHERER_INFORMATION SYSTEM_SUMMARY -local | C:\Program Files\Lenovo\System Update\egather\ia.exe | — | Tvsukernel.exe | |||||||||||
User: admin Integrity Level: HIGH Description: IA Exit code: 0 Version: 1.0.0.1 Modules
| |||||||||||||||
| 1620 | "C:\Windows\system32\cmd.exe" /c call "C:\Program Files\Lenovo\System Update\detectpm.cmd" | C:\Windows\system32\cmd.exe | — | systemupdate507-2019-01-25.tmp | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 1 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 1816 | "C:\Windows\TVSU2DirAllowWriting.exe" | C:\Windows\TVSU2DirAllowWriting.exe | — | systemupdate507-2019-01-25.tmp | |||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 2256 | "C:\Program Files\Lenovo\System Update\ConfigService.exe" settrigger | C:\Program Files\Lenovo\System Update\ConfigService.exe | — | systemupdate507-2019-01-25.tmp | |||||||||||
User: admin Integrity Level: HIGH Description: ConfigService Application Exit code: 0 Version: 5, 7, 0, 78 Modules
| |||||||||||||||
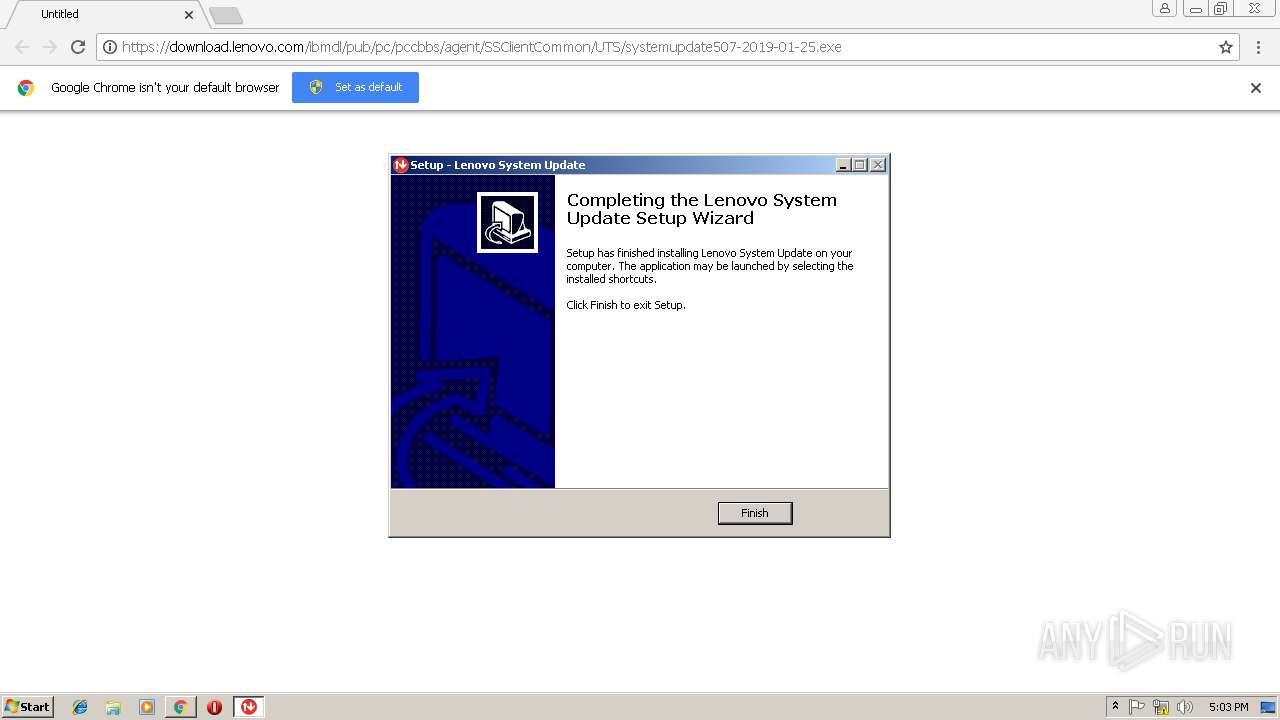
| 2284 | "C:\Users\admin\Downloads\systemupdate507-2019-01-25.exe" | C:\Users\admin\Downloads\systemupdate507-2019-01-25.exe | chrome.exe | ||||||||||||
User: admin Company: Lenovo Integrity Level: MEDIUM Description: Lenovo System Update Setup Exit code: 0 Version: 5.07.0078 Modules
| |||||||||||||||
| 2404 | "C:\Windows\system32\netsh.exe" advfirewall firewall add rule name="TvsuUNCServer" dir=out action=allow program="C:\Program Files\Lenovo\System Update\uncserver.exe" enable=yes profile=any protocol=UDP | C:\Windows\system32\netsh.exe | — | uncsetting.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Network Command Shell Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2476 | "C:\Windows\system32\netsh.exe" advfirewall firewall add rule name="TvsuUNCServer" dir=out action=allow program="C:\Program Files\Lenovo\System Update\uncserver.exe" enable=yes profile=any protocol=TCP | C:\Windows\system32\netsh.exe | — | uncsetting.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Network Command Shell Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2504 | "C:\Program Files\Lenovo\System Update\TvsuCommandLauncher.exe" 6 | C:\Program Files\Lenovo\System Update\TvsuCommandLauncher.exe | — | tvsu.exe | |||||||||||
User: admin Integrity Level: MEDIUM Description: Lenovo System Update TvsuCommandLauncher Exit code: 2147483648 Version: 5.7.0.78 Modules
| |||||||||||||||
| 2548 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=936,1118884064671851102,3336870485949245273,131072 --enable-features=PasswordImport --service-pipe-token=7D54F1FD2EBDA03F550594F9872F4BC4 --lang=en-US --enable-offline-auto-reload --enable-offline-auto-reload-visible-only --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --service-request-channel-token=7D54F1FD2EBDA03F550594F9872F4BC4 --renderer-client-id=4 --mojo-platform-channel-handle=1904 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google Inc. Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 68.0.3440.106 Modules
| |||||||||||||||
Total events
2 258
Read events
1 874
Write events
375
Delete events
9
Modification events
| (PID) Process: | (2876) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BLBeacon |
| Operation: | write | Name: | failed_count |
Value: 0 | |||
| (PID) Process: | (2876) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BLBeacon |
| Operation: | write | Name: | state |
Value: 2 | |||
| (PID) Process: | (2876) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BLBeacon |
| Operation: | write | Name: | state |
Value: 1 | |||
| (PID) Process: | (2868) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BrowserExitCodes |
| Operation: | write | Name: | 2876-13197402106539375 |
Value: 259 | |||
| (PID) Process: | (2876) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Update\ClientState\{8A69D345-D564-463c-AFF1-A69D9E530F96} |
| Operation: | write | Name: | dr |
Value: 1 | |||
| (PID) Process: | (2876) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome |
| Operation: | write | Name: | UsageStatsInSample |
Value: 0 | |||
| (PID) Process: | (2876) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BrowserExitCodes |
| Operation: | delete value | Name: | 3516-13180984670829101 |
Value: 0 | |||
| (PID) Process: | (2876) chrome.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Google\Update\ClientStateMedium\{8A69D345-D564-463C-AFF1-A69D9E530F96} |
| Operation: | write | Name: | usagestats |
Value: 0 | |||
| (PID) Process: | (2876) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BrowserExitCodes |
| Operation: | delete value | Name: | 2876-13197402106539375 |
Value: 259 | |||
| (PID) Process: | (2876) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Update\ClientState\{8A69D345-D564-463c-AFF1-A69D9E530F96} |
| Operation: | write | Name: | metricsid |
Value: | |||
Executable files
103
Suspicious files
49
Text files
291
Unknown types
28
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2876 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\1f26b8eb-87d5-4a32-b245-296b04b7c2a1.tmp | — | |
MD5:— | SHA256:— | |||
| 2876 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Download Service\EntryDB\000016.dbtmp | — | |
MD5:— | SHA256:— | |||
| 2876 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Download Service\EntryDB\CURRENT | — | |
MD5:— | SHA256:— | |||
| 2876 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\data_reduction_proxy_leveldb\000016.dbtmp | — | |
MD5:— | SHA256:— | |||
| 2876 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\155b0dc1-50b2-40f4-bf9b-a0948dd4d96b.tmp | — | |
MD5:— | SHA256:— | |||
| 2876 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\f12e8477-5ad9-4ed2-90c9-9c6fef411866.tmp | — | |
MD5:— | SHA256:— | |||
| 2876 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Last Version | text | |
MD5:— | SHA256:— | |||
| 2876 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\data_reduction_proxy_leveldb\LOG.old | text | |
MD5:— | SHA256:— | |||
| 2876 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\in_progress_download_metadata_store | binary | |
MD5:— | SHA256:— | |||
| 2876 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\data_reduction_proxy_leveldb\LOG.old~RF19a6a6.TMP | text | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
9
TCP/UDP connections
21
DNS requests
18
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3404 | SUService.exe | GET | 200 | 23.51.123.27:80 | http://s.symcd.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ%2FYHKj6JjF6UBieQioTYpFsuEriQQUtnf6aUhHn1MS1cLqBzJ2B9GXBxkCEHwbNTVK59t050FfEWnKa6g%3D | NL | der | 1.68 Kb | shared |
2836 | Tvsukernel.exe | GET | 200 | 23.51.123.27:80 | http://rb.symcd.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTDRSYViRCZTxmZjLENmnwVjLly9QQU1MAGIknrOUvdk%2BJcobhHdglyA1gCEGZYxb%2BG6ZEk%2BZdIsKegFUw%3D | NL | der | 1.58 Kb | whitelisted |
3404 | SUService.exe | GET | 200 | 23.51.123.27:80 | http://s.symcd.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ%2FYHKj6JjF6UBieQioTYpFsuEriQQUtnf6aUhHn1MS1cLqBzJ2B9GXBxkCEHsFsdRJaFFE98mJ0pwZnRI%3D | NL | der | 1.68 Kb | shared |
3404 | SUService.exe | GET | 200 | 23.51.123.27:80 | http://rb.symcd.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTDRSYViRCZTxmZjLENmnwVjLly9QQU1MAGIknrOUvdk%2BJcobhHdglyA1gCEGZYxb%2BG6ZEk%2BZdIsKegFUw%3D | NL | der | 1.58 Kb | whitelisted |
3404 | SUService.exe | GET | 200 | 23.51.123.27:80 | http://ts-ocsp.ws.symantec.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQd11mpyHEqFCSocj4SCu93CBydHAQUr2PWyqNOhXLgp7xB8ymiOH%2BAdWICEHvU5a%2B6zAc%2FoQEjBCJBTRI%3D | NL | der | 1.55 Kb | whitelisted |
3404 | SUService.exe | GET | 200 | 23.51.123.27:80 | http://ts-ocsp.ws.symantec.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQd11mpyHEqFCSocj4SCu93CBydHAQUr2PWyqNOhXLgp7xB8ymiOH%2BAdWICEFRY8qrXQdZEvISpe6CWUuY%3D | NL | der | 1.55 Kb | whitelisted |
2836 | Tvsukernel.exe | GET | 200 | 23.51.123.27:80 | http://s.symcd.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ%2FYHKj6JjF6UBieQioTYpFsuEriQQUtnf6aUhHn1MS1cLqBzJ2B9GXBxkCEHwbNTVK59t050FfEWnKa6g%3D | NL | der | 1.68 Kb | shared |
2836 | Tvsukernel.exe | GET | 200 | 23.51.123.27:80 | http://s.symcd.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ%2FYHKj6JjF6UBieQioTYpFsuEriQQUtnf6aUhHn1MS1cLqBzJ2B9GXBxkCEHsFsdRJaFFE98mJ0pwZnRI%3D | NL | der | 1.68 Kb | shared |
2836 | Tvsukernel.exe | GET | 200 | 23.51.123.27:80 | http://ts-ocsp.ws.symantec.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQd11mpyHEqFCSocj4SCu93CBydHAQUr2PWyqNOhXLgp7xB8ymiOH%2BAdWICEFRY8qrXQdZEvISpe6CWUuY%3D | NL | der | 1.55 Kb | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2876 | chrome.exe | 216.58.210.3:443 | clientservices.googleapis.com | Google Inc. | US | whitelisted |
2876 | chrome.exe | 184.51.8.76:443 | download.lenovo.com | Akamai Technologies, Inc. | US | whitelisted |
2876 | chrome.exe | 172.217.18.173:443 | accounts.google.com | Google Inc. | US | whitelisted |
2876 | chrome.exe | 216.58.207.35:443 | ssl.gstatic.com | Google Inc. | US | whitelisted |
2836 | Tvsukernel.exe | 184.51.8.76:443 | download.lenovo.com | Akamai Technologies, Inc. | US | whitelisted |
2876 | chrome.exe | 172.217.23.138:443 | safebrowsing.googleapis.com | Google Inc. | US | whitelisted |
2836 | Tvsukernel.exe | 2.18.232.126:443 | download.lenovo.com | Akamai International B.V. | — | whitelisted |
2836 | Tvsukernel.exe | 38.106.231.204:443 | chifsr.lenovomm.com | Cogent Communications | US | unknown |
2836 | Tvsukernel.exe | 23.51.123.27:80 | s.symcd.com | Akamai Technologies, Inc. | NL | whitelisted |
3404 | SUService.exe | 23.51.123.27:80 | s.symcd.com | Akamai Technologies, Inc. | NL | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
download.lenovo.com |
| suspicious |
clientservices.googleapis.com |
| whitelisted |
www.gstatic.com |
| whitelisted |
accounts.google.com |
| shared |
ssl.gstatic.com |
| whitelisted |
clients1.google.com |
| whitelisted |
clients2.google.com |
| whitelisted |
s.symcd.com |
| shared |
rb.symcd.com |
| whitelisted |
ts-ocsp.ws.symantec.com |
| whitelisted |