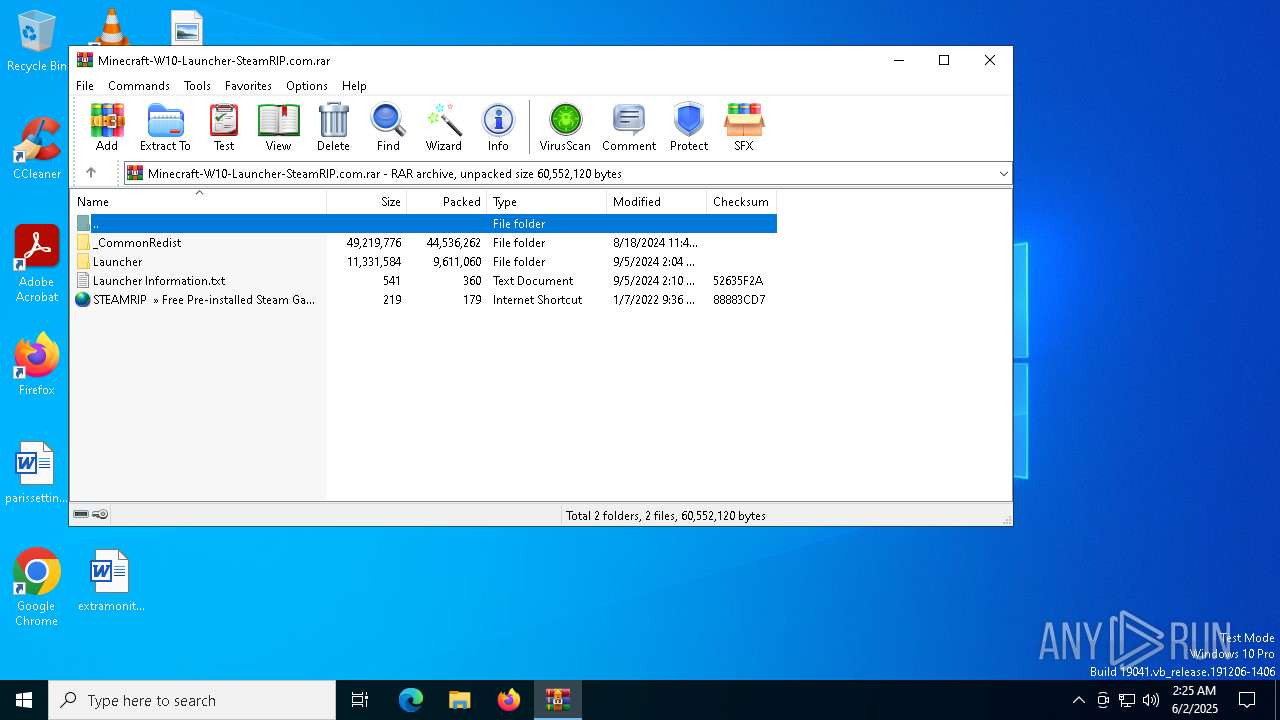
| File name: | Minecraft-W10-Launcher-SteamRIP.com.rar |
| Full analysis: | https://app.any.run/tasks/b0fdee66-0072-4844-8dd6-11e588fa47db |
| Verdict: | Malicious activity |
| Analysis date: | June 02, 2025, 02:24:44 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-rar |
| File info: | RAR archive data, v5 |
| MD5: | 1080CC9D09A7111A5222548DB693D11E |
| SHA1: | 5AB8EA86652B71386885BB50D084DA6FDED7276E |
| SHA256: | 839AF2E4626DEF466FDB115636BE9E5AECCBFBB3CE2883A7119789CBFE3B33D1 |
| SSDEEP: | 393216:qB7PocgBID7JaxKSgYHq29KJ7MoP5S3KeMPdzRf6d3jqccf77YoRwa/iXvJ:U7ocguDeKSHDwZL5+SPdoO/nnWvJ |
MALICIOUS
Executing a file with an untrusted certificate
- oalinst.exe (PID: 5376)
- oalinst.exe (PID: 5624)
- dotNetFx40_Full_setup.exe (PID: 7172)
- dotNetFx40_Full_setup.exe (PID: 7684)
- dxwebsetup.exe (PID: 8000)
- dxwebsetup.exe (PID: 7200)
- Setup.exe (PID: 7756)
- vcredist_x64.exe (PID: 8164)
- vcredist_x64.exe (PID: 7900)
- Setup.exe (PID: 4040)
Changes the autorun value in the registry
- dxwebsetup.exe (PID: 7200)
SUSPICIOUS
Process drops legitimate windows executable
- WinRAR.exe (PID: 2980)
- dotNetFx40_Full_setup.exe (PID: 7684)
- dxwebsetup.exe (PID: 7200)
- dxwsetup.exe (PID: 6184)
- vcredist_x64.exe (PID: 7900)
- msiexec.exe (PID: 8088)
Reads security settings of Internet Explorer
- WinRAR.exe (PID: 2980)
- Setup.exe (PID: 4040)
Starts CMD.EXE for commands execution
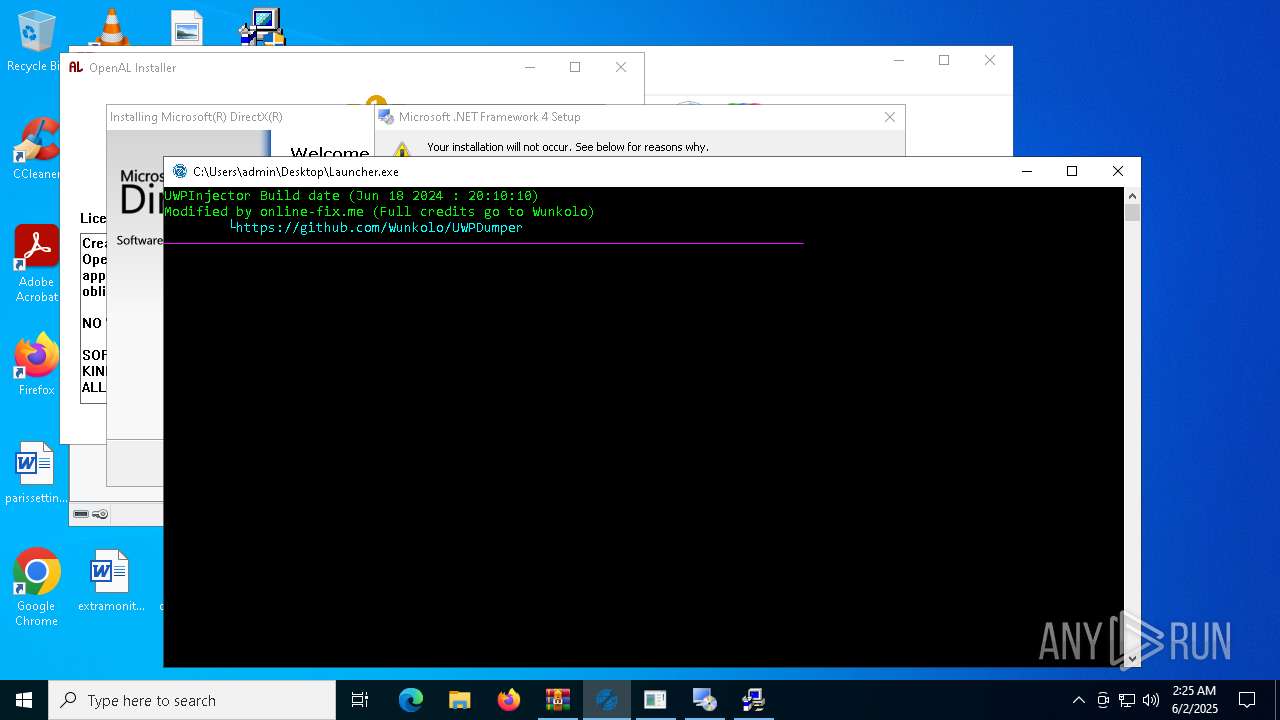
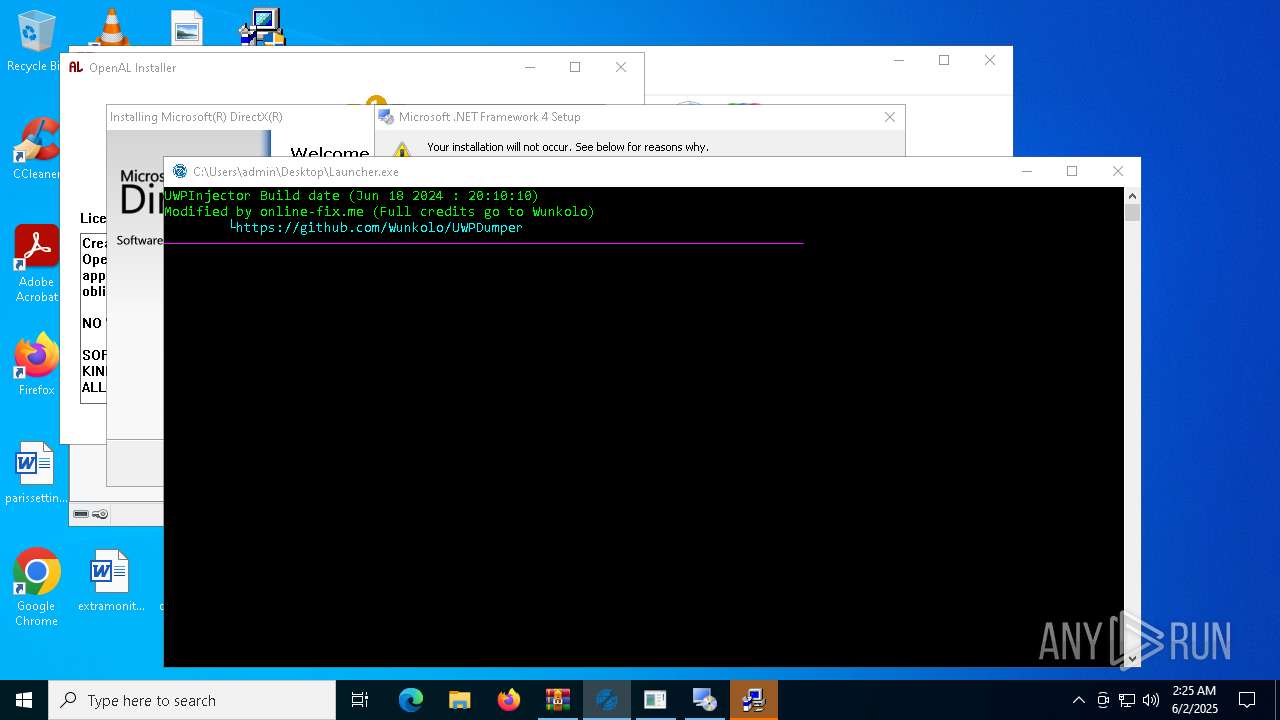
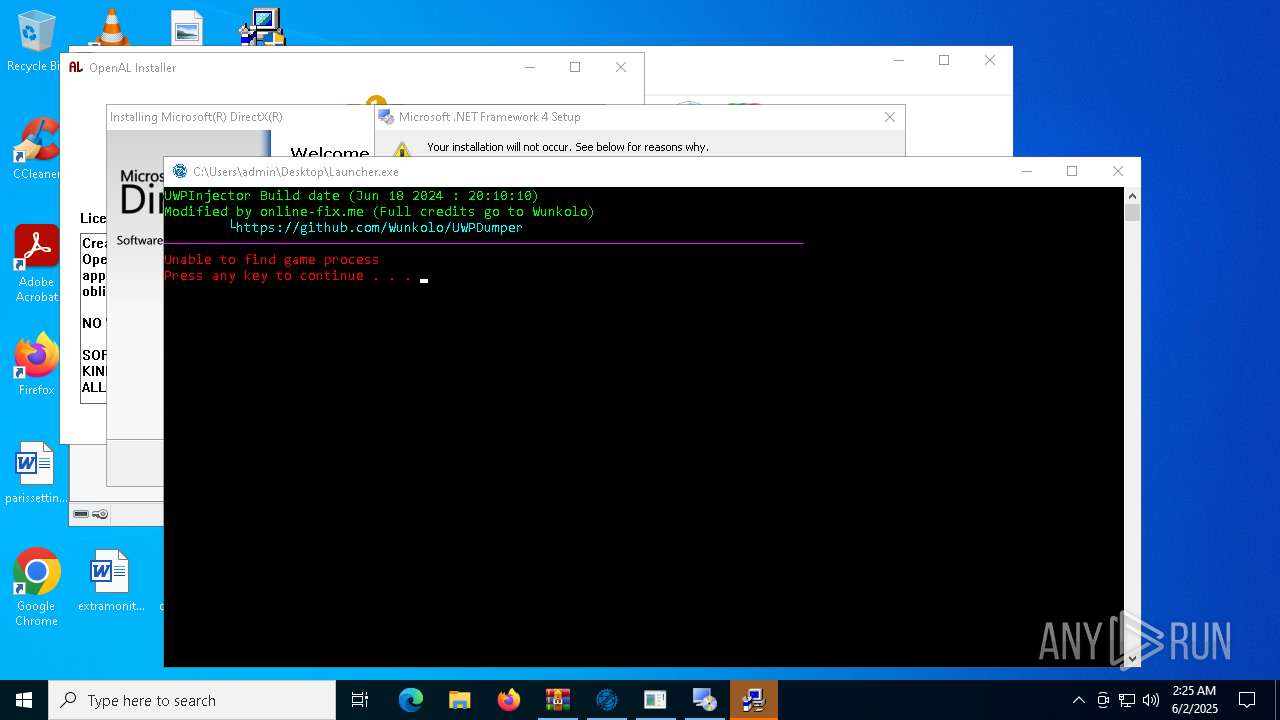
- Launcher.exe (PID: 516)
Starts a Microsoft application from unusual location
- dotNetFx40_Full_setup.exe (PID: 7172)
- dotNetFx40_Full_setup.exe (PID: 7684)
- dxwebsetup.exe (PID: 8000)
- dxwebsetup.exe (PID: 7200)
- dxwsetup.exe (PID: 6184)
- vcredist_x64.exe (PID: 8164)
- vcredist_x64.exe (PID: 7900)
Executable content was dropped or overwritten
- dotNetFx40_Full_setup.exe (PID: 7684)
- dxwsetup.exe (PID: 6184)
- dxwebsetup.exe (PID: 7200)
- vcredist_x64.exe (PID: 7900)
Creates file in the systems drive root
- dotNetFx40_Full_setup.exe (PID: 7684)
- vcredist_x64.exe (PID: 7900)
Reads the Windows owner or organization settings
- msiexec.exe (PID: 8088)
The process drops C-runtime libraries
- msiexec.exe (PID: 8088)
There is functionality for taking screenshot (YARA)
- oalinst.exe (PID: 5376)
INFO
Manual execution by a user
- Launcher.exe (PID: 516)
- oalinst.exe (PID: 5624)
- oalinst.exe (PID: 5376)
- dotNetFx40_Full_setup.exe (PID: 7172)
- dotNetFx40_Full_setup.exe (PID: 7684)
- dxwebsetup.exe (PID: 8000)
- dxwebsetup.exe (PID: 7200)
- rundll32.exe (PID: 7960)
- vcredist_x64.exe (PID: 7900)
- vcredist_x64.exe (PID: 8164)
Checks supported languages
- Launcher.exe (PID: 516)
- oalinst.exe (PID: 5376)
- dotNetFx40_Full_setup.exe (PID: 7684)
- Setup.exe (PID: 7756)
- dxwebsetup.exe (PID: 7200)
- dxwsetup.exe (PID: 6184)
- vcredist_x64.exe (PID: 7900)
- Setup.exe (PID: 4040)
- msiexec.exe (PID: 8088)
Reads security settings of Internet Explorer
- OpenWith.exe (PID: 644)
Reads the computer name
- oalinst.exe (PID: 5376)
- dotNetFx40_Full_setup.exe (PID: 7684)
- Setup.exe (PID: 7756)
- vcredist_x64.exe (PID: 7900)
- dxwsetup.exe (PID: 6184)
- Setup.exe (PID: 4040)
- msiexec.exe (PID: 8088)
Create files in a temporary directory
- dotNetFx40_Full_setup.exe (PID: 7684)
- dxwebsetup.exe (PID: 7200)
- Setup.exe (PID: 7756)
- Setup.exe (PID: 4040)
The sample compiled with german language support
- dotNetFx40_Full_setup.exe (PID: 7684)
- vcredist_x64.exe (PID: 7900)
- msiexec.exe (PID: 8088)
Reads the machine GUID from the registry
- dotNetFx40_Full_setup.exe (PID: 7684)
- vcredist_x64.exe (PID: 7900)
- Setup.exe (PID: 4040)
- msiexec.exe (PID: 8088)
The sample compiled with czech language support
- dotNetFx40_Full_setup.exe (PID: 7684)
The sample compiled with english language support
- dotNetFx40_Full_setup.exe (PID: 7684)
- dxwebsetup.exe (PID: 7200)
- dxwsetup.exe (PID: 6184)
- vcredist_x64.exe (PID: 7900)
- msiexec.exe (PID: 8088)
The sample compiled with arabic language support
- dotNetFx40_Full_setup.exe (PID: 7684)
The sample compiled with turkish language support
- dotNetFx40_Full_setup.exe (PID: 7684)
The sample compiled with chinese language support
- dotNetFx40_Full_setup.exe (PID: 7684)
- vcredist_x64.exe (PID: 7900)
- msiexec.exe (PID: 8088)
The sample compiled with french language support
- dotNetFx40_Full_setup.exe (PID: 7684)
- vcredist_x64.exe (PID: 7900)
- msiexec.exe (PID: 8088)
The sample compiled with swedish language support
- dotNetFx40_Full_setup.exe (PID: 7684)
The sample compiled with korean language support
- dotNetFx40_Full_setup.exe (PID: 7684)
- vcredist_x64.exe (PID: 7900)
- msiexec.exe (PID: 8088)
The sample compiled with japanese language support
- dotNetFx40_Full_setup.exe (PID: 7684)
- vcredist_x64.exe (PID: 7900)
- msiexec.exe (PID: 8088)
The sample compiled with Italian language support
- dotNetFx40_Full_setup.exe (PID: 7684)
- vcredist_x64.exe (PID: 7900)
- msiexec.exe (PID: 8088)
The sample compiled with polish language support
- dotNetFx40_Full_setup.exe (PID: 7684)
The sample compiled with russian language support
- dotNetFx40_Full_setup.exe (PID: 7684)
- vcredist_x64.exe (PID: 7900)
- msiexec.exe (PID: 8088)
The sample compiled with spanish language support
- dotNetFx40_Full_setup.exe (PID: 7684)
- vcredist_x64.exe (PID: 7900)
- msiexec.exe (PID: 8088)
Launch of the file from Registry key
- dxwebsetup.exe (PID: 7200)
The sample compiled with portuguese language support
- dotNetFx40_Full_setup.exe (PID: 7684)
Reads CPU info
- Setup.exe (PID: 7756)
- Setup.exe (PID: 4040)
Reads the software policy settings
- Setup.exe (PID: 4040)
- msiexec.exe (PID: 8088)
- slui.exe (PID: 7268)
Executable content was dropped or overwritten
- msiexec.exe (PID: 8088)
Creates files or folders in the user directory
- msiexec.exe (PID: 8088)
Creates a software uninstall entry
- msiexec.exe (PID: 8088)
Checks proxy server information
- slui.exe (PID: 7268)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .rar | | | RAR compressed archive (v5.0) (61.5) |
|---|---|---|
| .rar | | | RAR compressed archive (gen) (38.4) |
EXIF
ZIP
| FileVersion: | RAR v5 |
|---|---|
| CompressedSize: | 9436797 |
| UncompressedSize: | 10992640 |
| OperatingSystem: | Win32 |
| ArchivedFileName: | Launcher/Custom.dll |
Total processes
143
Monitored processes
20
Malicious processes
4
Suspicious processes
8
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 516 | "C:\Users\admin\Desktop\Launcher.exe" | C:\Users\admin\Desktop\Launcher.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Modules
| |||||||||||||||
| 644 | C:\WINDOWS\system32\OpenWith.exe -Embedding | C:\Windows\System32\OpenWith.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Pick an app Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
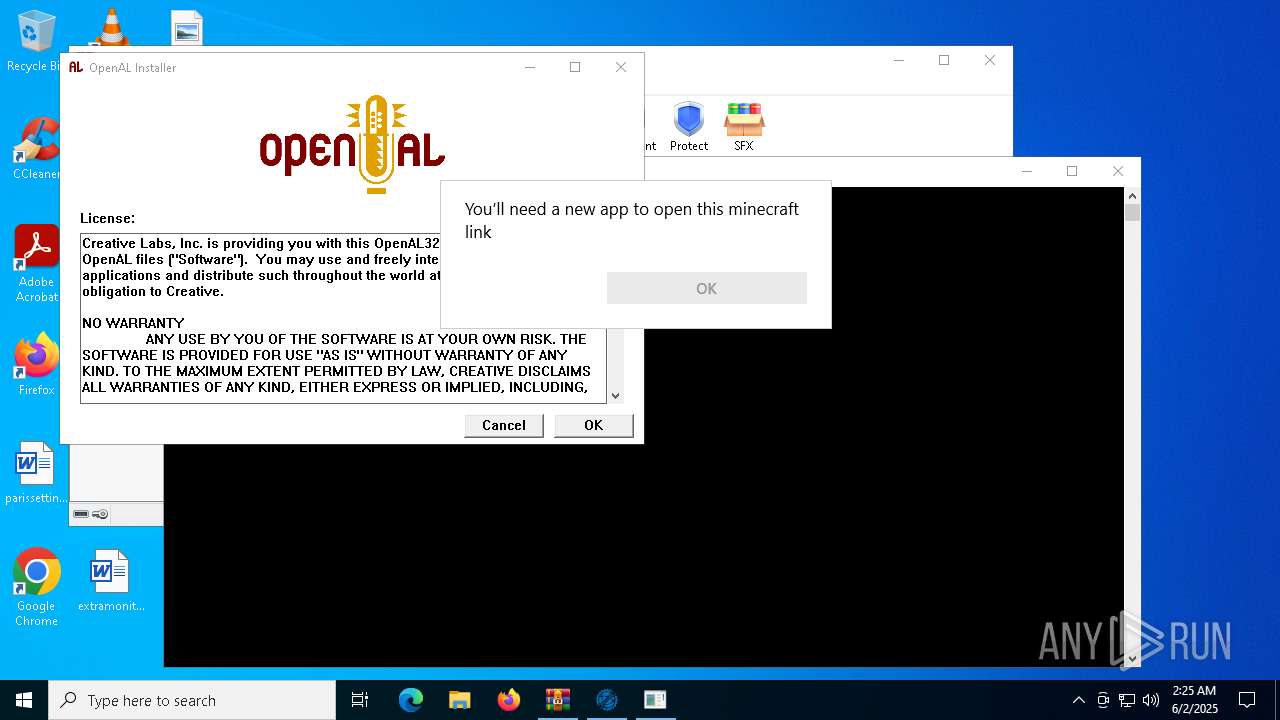
| 2656 | C:\WINDOWS\system32\cmd.exe /c start minecraft: | C:\Windows\System32\cmd.exe | — | Launcher.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2980 | "C:\Program Files\WinRAR\WinRAR.exe" C:\Users\admin\Desktop\Minecraft-W10-Launcher-SteamRIP.com.rar | C:\Program Files\WinRAR\WinRAR.exe | — | explorer.exe | |||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Version: 5.91.0 Modules
| |||||||||||||||
| 3996 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | Launcher.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4040 | c:\da2aa91ccc9651bffed3e3\Setup.exe | C:\da2aa91ccc9651bffed3e3\Setup.exe | — | vcredist_x64.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Setup Installer Exit code: 0 Version: 10.0.30319.1 built by: RTMRel Modules
| |||||||||||||||
| 4724 | C:\WINDOWS\system32\cmd.exe /c pause | C:\Windows\System32\cmd.exe | — | Launcher.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5376 | "C:\Users\admin\Desktop\oalinst.exe" | C:\Users\admin\Desktop\oalinst.exe | explorer.exe | ||||||||||||
User: admin Company: Creative Labs Inc. Integrity Level: HIGH Description: OpenAL Installer Version: 2, 0, 7, 0 Modules
| |||||||||||||||
| 5624 | "C:\Users\admin\Desktop\oalinst.exe" | C:\Users\admin\Desktop\oalinst.exe | — | explorer.exe | |||||||||||
User: admin Company: Creative Labs Inc. Integrity Level: MEDIUM Description: OpenAL Installer Exit code: 3221226540 Version: 2, 0, 7, 0 Modules
| |||||||||||||||
| 6184 | C:\Users\admin\AppData\Local\Temp\IXP000.TMP\dxwsetup.exe | C:\Users\admin\AppData\Local\Temp\IXP000.TMP\dxwsetup.exe | dxwebsetup.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: DirectX Setup Version: 4.9.0.0904 Modules
| |||||||||||||||
Total events
13 613
Read events
13 379
Write events
225
Delete events
9
Modification events
| (PID) Process: | (2980) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\preferences.zip | |||
| (PID) Process: | (2980) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\chromium_ext.zip | |||
| (PID) Process: | (2980) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
| (PID) Process: | (2980) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\Minecraft-W10-Launcher-SteamRIP.com.rar | |||
| (PID) Process: | (2980) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (2980) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (2980) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (2980) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (2656) cmd.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer |
| Operation: | write | Name: | SlowContextMenuEntries |
Value: 6024B221EA3A6910A2DC08002B30309D0A010000BD0E0C47735D584D9CEDE91E22E23282770100000114020000000000C0000000000000468D0000006078A409B011A54DAFA526D86198A780390100009AD298B2EDA6DE11BA8CA68E55D895936E000000 | |||
| (PID) Process: | (2656) cmd.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
Executable files
75
Suspicious files
19
Text files
132
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 7684 | dotNetFx40_Full_setup.exe | C:\159d7f1a7066bd46b3e20afb6c6e\header.bmp | image | |
MD5:514BFCD8DA66722A9639EB41ED3988B7 | SHA256:6B8201ED10CE18FFADE072B77C6D1FCACCF1D29ACB47D86F553D9BEEBD991290 | |||
| 7684 | dotNetFx40_Full_setup.exe | C:\159d7f1a7066bd46b3e20afb6c6e\Graphics\Print.ico | image | |
MD5:7E55DDC6D611176E697D01C90A1212CF | SHA256:FF542E32330B123486797B410621E19EAFB39DF3997E14701AFA4C22096520ED | |||
| 7684 | dotNetFx40_Full_setup.exe | C:\159d7f1a7066bd46b3e20afb6c6e\Graphics\Rotate1.ico | image | |
MD5:26A00597735C5F504CF8B3E7E9A7A4C1 | SHA256:37026C4EA2182D7908B3CF0CEF8A6F72BDDCA5F1CFBC702F35B569AD689CF0AF | |||
| 7684 | dotNetFx40_Full_setup.exe | C:\159d7f1a7066bd46b3e20afb6c6e\Graphics\Rotate6.ico | image | |
MD5:70006BF18A39D258012875AEFB92A3D1 | SHA256:19ABCEDF93D790E19FB3379CB3B46371D3CBFF48FE7E63F4FDCC2AC23A9943E4 | |||
| 7684 | dotNetFx40_Full_setup.exe | C:\159d7f1a7066bd46b3e20afb6c6e\Graphics\Rotate2.ico | image | |
MD5:8419CAA81F2377E09B7F2F6218E505AE | SHA256:DB89D8A45C369303C04988322B2774D2C7888DA5250B4DAB2846DEEF58A7DE22 | |||
| 7684 | dotNetFx40_Full_setup.exe | C:\159d7f1a7066bd46b3e20afb6c6e\Graphics\Rotate7.ico | image | |
MD5:FB4DFEBE83F554FAF1A5CEC033A804D9 | SHA256:4F46A9896DE23A92D2B5F963BCFB3237C3E85DA05B8F7660641B3D1D5AFAAE6F | |||
| 7684 | dotNetFx40_Full_setup.exe | C:\159d7f1a7066bd46b3e20afb6c6e\Graphics\Rotate3.ico | image | |
MD5:924FD539523541D42DAD43290E6C0DB5 | SHA256:02A7FE932029C6FA24D1C7CC06D08A27E84F43A0CBC47B7C43CAC59424B3D1F6 | |||
| 7684 | dotNetFx40_Full_setup.exe | C:\159d7f1a7066bd46b3e20afb6c6e\Graphics\Rotate8.ico | image | |
MD5:D1C53003264DCE4EFFAF462C807E2D96 | SHA256:5FB03593071A99C7B3803FE8424520B8B548B031D02F2A86E8F5412AC519723C | |||
| 7684 | dotNetFx40_Full_setup.exe | C:\159d7f1a7066bd46b3e20afb6c6e\DisplayIcon.ico | image | |
MD5:F9657D290048E169FFABBBB9C7412BE0 | SHA256:B74AD253B9B8F9FCADE725336509143828EE739CC2B24782BE3ECFF26F229160 | |||
| 7684 | dotNetFx40_Full_setup.exe | C:\159d7f1a7066bd46b3e20afb6c6e\Graphics\stop.ico | image | |
MD5:5DFA8D3ABCF4962D9EC41CFC7C0F75E3 | SHA256:B499E1B21091B539D4906E45B6FDF490D5445256B72871AECE2F5B2562C11793 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
25
TCP/UDP connections
40
DNS requests
16
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
6544 | svchost.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
— | — | POST | 200 | 20.190.159.64:443 | https://login.live.com/RST2.srf | unknown | xml | 6.67 Kb | whitelisted |
— | — | POST | 200 | 40.126.32.140:443 | https://login.live.com/RST2.srf | unknown | xml | 11.0 Kb | whitelisted |
5056 | svchost.exe | GET | 200 | 23.216.77.6:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
5056 | svchost.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
— | — | POST | 200 | 40.126.32.140:443 | https://login.live.com/RST2.srf | unknown | xml | 11.1 Kb | whitelisted |
5496 | MoUsoCoreWorker.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
— | — | GET | 304 | 172.202.163.200:443 | https://slscr.update.microsoft.com/SLS/%7B522D76A4-93E1-47F8-B8CE-07C937AD1A1E%7D/x64/10.0.19045.4046/0?CH=686&L=en-US&P=&PT=0x30&WUA=10.0.19041.3996&MK=DELL&MD=DELL | unknown | — | — | unknown |
— | — | GET | 200 | 172.202.163.200:443 | https://slscr.update.microsoft.com/SLS/%7B522D76A4-93E1-47F8-B8CE-07C937AD1A1E%7D/x64/10.0.19045.4046/0?CH=686&L=en-US&P=&PT=0x30&WUA=10.0.19041.3996&MK=DELL&MD=DELL | unknown | compressed | 23.9 Kb | whitelisted |
7704 | SIHClient.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20Update%20Signing%20CA%202.1.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
6544 | svchost.exe | 20.190.160.64:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | NL | unknown |
— | — | 20.190.160.64:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | NL | unknown |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
6544 | svchost.exe | 2.17.190.73:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
5056 | svchost.exe | 23.216.77.6:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
5056 | svchost.exe | 23.35.229.160:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
5496 | MoUsoCoreWorker.exe | 23.35.229.160:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
— | — | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |
activation-v2.sls.microsoft.com |
| whitelisted |
self.events.data.microsoft.com |
| whitelisted |