| File name: | Nicky Romero - Kickstart 2.0 Setup.exe |
| Full analysis: | https://app.any.run/tasks/7afbcdfd-f99c-4278-bdde-23112362a7b5 |
| Verdict: | Malicious activity |
| Analysis date: | August 07, 2024, 10:30:46 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows |
| MD5: | 677852451FD2AC62BD984E36C5BD1EC7 |
| SHA1: | D44FDA95330BA804D4A3530A267405BE131C0942 |
| SHA256: | 8398BDBA68D7520ED4743CD27839EDBF7FB4591986AC6B485CA9308BA7400AB6 |
| SSDEEP: | 98304:xESk+isd1z9zgeyP8L+GR+lRoj+Toy43pKZhrYvDRCZS0x5/ewYo8C4Esgv:XNisnGe39+rZS3pKAQZFrrR8zt6 |
MALICIOUS
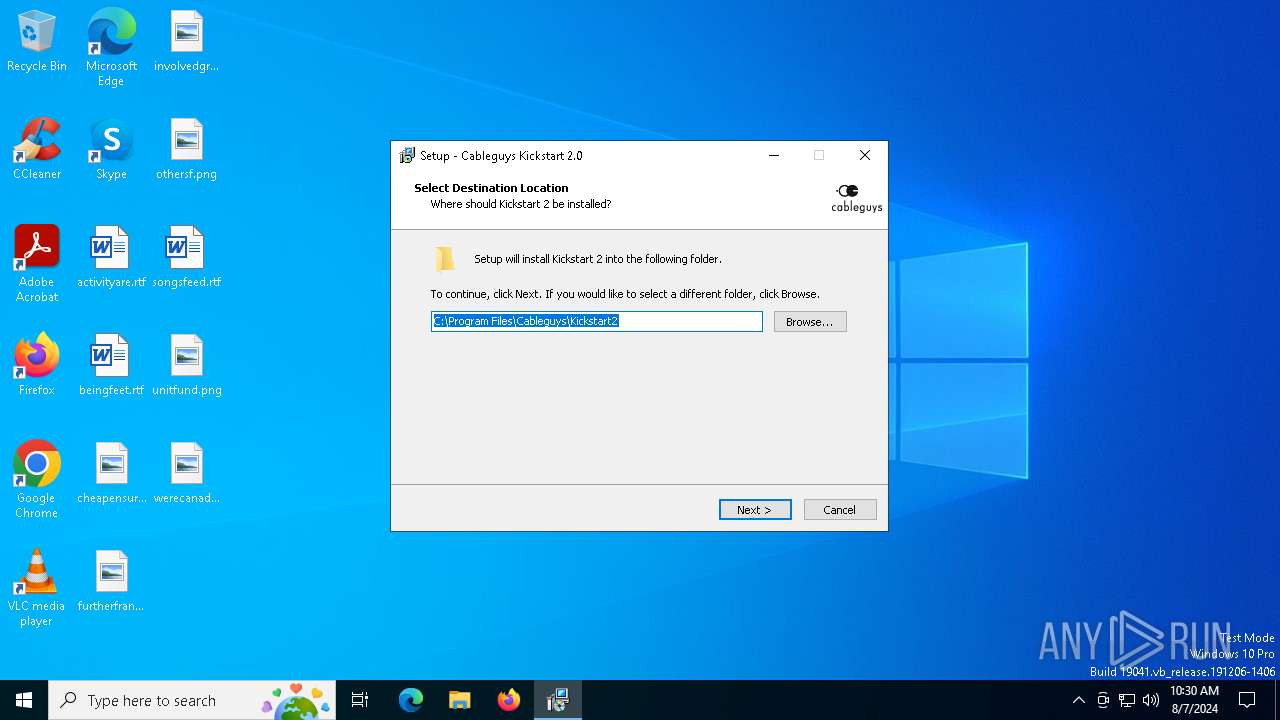
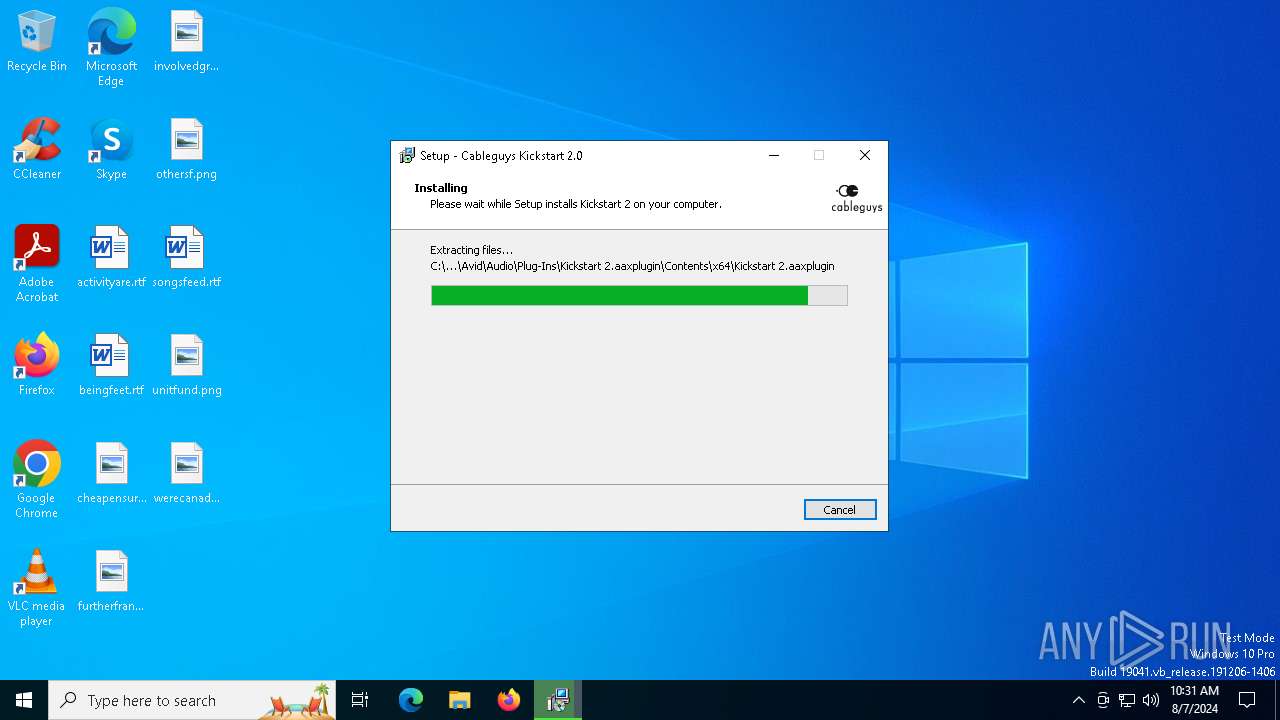
Drops the executable file immediately after the start
- Nicky Romero - Kickstart 2.0 Setup.exe (PID: 6368)
- Nicky Romero - Kickstart 2.0 Setup.exe (PID: 6468)
- Nicky Romero - Kickstart 2.0 Setup.tmp (PID: 6492)
SUSPICIOUS
Executable content was dropped or overwritten
- Nicky Romero - Kickstart 2.0 Setup.exe (PID: 6368)
- Nicky Romero - Kickstart 2.0 Setup.exe (PID: 6468)
- Nicky Romero - Kickstart 2.0 Setup.tmp (PID: 6492)
Reads the date of Windows installation
- Nicky Romero - Kickstart 2.0 Setup.tmp (PID: 6388)
Reads security settings of Internet Explorer
- Nicky Romero - Kickstart 2.0 Setup.tmp (PID: 6388)
Reads the Windows owner or organization settings
- Nicky Romero - Kickstart 2.0 Setup.tmp (PID: 6492)
INFO
Checks supported languages
- Nicky Romero - Kickstart 2.0 Setup.exe (PID: 6368)
- Nicky Romero - Kickstart 2.0 Setup.tmp (PID: 6388)
- Nicky Romero - Kickstart 2.0 Setup.exe (PID: 6468)
- Nicky Romero - Kickstart 2.0 Setup.tmp (PID: 6492)
Create files in a temporary directory
- Nicky Romero - Kickstart 2.0 Setup.exe (PID: 6368)
- Nicky Romero - Kickstart 2.0 Setup.exe (PID: 6468)
- Nicky Romero - Kickstart 2.0 Setup.tmp (PID: 6492)
Reads the computer name
- Nicky Romero - Kickstart 2.0 Setup.tmp (PID: 6388)
- Nicky Romero - Kickstart 2.0 Setup.tmp (PID: 6492)
Process checks computer location settings
- Nicky Romero - Kickstart 2.0 Setup.tmp (PID: 6388)
Creates files in the program directory
- Nicky Romero - Kickstart 2.0 Setup.tmp (PID: 6492)
Creates a software uninstall entry
- Nicky Romero - Kickstart 2.0 Setup.tmp (PID: 6492)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Inno Setup installer (51.8) |
|---|---|---|
| .exe | | | InstallShield setup (20.3) |
| .exe | | | Win32 EXE PECompact compressed (generic) (19.6) |
| .dll | | | Win32 Dynamic Link Library (generic) (3.1) |
| .exe | | | Win32 Executable (generic) (2.1) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2020:05:21 05:56:23+00:00 |
| ImageFileCharacteristics: | No relocs, Executable, No line numbers, No symbols, Bytes reversed lo, 32-bit, Bytes reversed hi |
| PEType: | PE32 |
| LinkerVersion: | 2.25 |
| CodeSize: | 741376 |
| InitializedDataSize: | 38400 |
| UninitializedDataSize: | - |
| EntryPoint: | 0xb5eec |
| OSVersion: | 6 |
| ImageVersion: | 6 |
| SubsystemVersion: | 6 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 0.0.0.0 |
| ProductVersionNumber: | 0.0.0.0 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | Neutral |
| CharacterSet: | Unicode |
| Comments: | This installation was built with Inno Setup. |
| CompanyName: | Cableguys |
| FileDescription: | Kickstart 2 Setup |
| FileVersion: | |
| LegalCopyright: | |
| OriginalFileName: | |
| ProductName: | Kickstart 2 |
| ProductVersion: | 2.0 |
Total processes
135
Monitored processes
4
Malicious processes
4
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 6368 | "C:\Users\admin\AppData\Local\Temp\Nicky Romero - Kickstart 2.0 Setup.exe" | C:\Users\admin\AppData\Local\Temp\Nicky Romero - Kickstart 2.0 Setup.exe | explorer.exe | ||||||||||||
User: admin Company: Cableguys Integrity Level: MEDIUM Description: Kickstart 2 Setup Exit code: 0 Version: Modules
| |||||||||||||||
| 6388 | "C:\Users\admin\AppData\Local\Temp\is-BQCKU.tmp\Nicky Romero - Kickstart 2.0 Setup.tmp" /SL5="$5030C,4910590,780800,C:\Users\admin\AppData\Local\Temp\Nicky Romero - Kickstart 2.0 Setup.exe" | C:\Users\admin\AppData\Local\Temp\is-BQCKU.tmp\Nicky Romero - Kickstart 2.0 Setup.tmp | — | Nicky Romero - Kickstart 2.0 Setup.exe | |||||||||||
User: admin Company: Cableguys Integrity Level: MEDIUM Description: Setup/Uninstall Exit code: 0 Version: 51.1052.0.0 Modules
| |||||||||||||||
| 6468 | "C:\Users\admin\AppData\Local\Temp\Nicky Romero - Kickstart 2.0 Setup.exe" /SPAWNWND=$4028A /NOTIFYWND=$5030C | C:\Users\admin\AppData\Local\Temp\Nicky Romero - Kickstart 2.0 Setup.exe | Nicky Romero - Kickstart 2.0 Setup.tmp | ||||||||||||
User: admin Company: Cableguys Integrity Level: HIGH Description: Kickstart 2 Setup Exit code: 0 Version: Modules
| |||||||||||||||
| 6492 | "C:\Users\admin\AppData\Local\Temp\is-N2PQ0.tmp\Nicky Romero - Kickstart 2.0 Setup.tmp" /SL5="$70118,4910590,780800,C:\Users\admin\AppData\Local\Temp\Nicky Romero - Kickstart 2.0 Setup.exe" /SPAWNWND=$4028A /NOTIFYWND=$5030C | C:\Users\admin\AppData\Local\Temp\is-N2PQ0.tmp\Nicky Romero - Kickstart 2.0 Setup.tmp | Nicky Romero - Kickstart 2.0 Setup.exe | ||||||||||||
User: admin Company: Cableguys Integrity Level: HIGH Description: Setup/Uninstall Exit code: 0 Version: 51.1052.0.0 Modules
| |||||||||||||||
Total events
3 741
Read events
3 708
Write events
27
Delete events
6
Modification events
| (PID) Process: | (6492) Nicky Romero - Kickstart 2.0 Setup.tmp | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\RestartManager\Session0000 |
| Operation: | write | Name: | Owner |
Value: 5C19000064686CE1B4E8DA01 | |||
| (PID) Process: | (6492) Nicky Romero - Kickstart 2.0 Setup.tmp | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\RestartManager\Session0000 |
| Operation: | write | Name: | SessionHash |
Value: CB70A0C8E6651FE24874B1BF0A6E9FA00DD0AC115EC2A15A37A30CFFCEE8781A | |||
| (PID) Process: | (6492) Nicky Romero - Kickstart 2.0 Setup.tmp | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\RestartManager\Session0000 |
| Operation: | write | Name: | Sequence |
Value: 1 | |||
| (PID) Process: | (6492) Nicky Romero - Kickstart 2.0 Setup.tmp | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\RestartManager\Session0000 |
| Operation: | write | Name: | RegFiles0000 |
Value: C:\Program Files\Steinberg\VSTPlugins\Kickstart 2.dll | |||
| (PID) Process: | (6492) Nicky Romero - Kickstart 2.0 Setup.tmp | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\RestartManager\Session0000 |
| Operation: | write | Name: | RegFilesHash |
Value: 47DC42261D0354221633BE2C412AD45B00D8AC890188809543811ACF8CC9448D | |||
| (PID) Process: | (6492) Nicky Romero - Kickstart 2.0 Setup.tmp | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\Kickstart 2_is1 |
| Operation: | write | Name: | Inno Setup: Setup Version |
Value: 6.0.5 (u) | |||
| (PID) Process: | (6492) Nicky Romero - Kickstart 2.0 Setup.tmp | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\Kickstart 2_is1 |
| Operation: | write | Name: | Inno Setup: App Path |
Value: C:\Program Files\Cableguys\Kickstart2 | |||
| (PID) Process: | (6492) Nicky Romero - Kickstart 2.0 Setup.tmp | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\Kickstart 2_is1 |
| Operation: | write | Name: | InstallLocation |
Value: C:\Program Files\Cableguys\Kickstart2\ | |||
| (PID) Process: | (6492) Nicky Romero - Kickstart 2.0 Setup.tmp | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\Kickstart 2_is1 |
| Operation: | write | Name: | Inno Setup: Icon Group |
Value: (Default) | |||
| (PID) Process: | (6492) Nicky Romero - Kickstart 2.0 Setup.tmp | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\Kickstart 2_is1 |
| Operation: | write | Name: | Inno Setup: User |
Value: admin | |||
Executable files
13
Suspicious files
1
Text files
2
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6468 | Nicky Romero - Kickstart 2.0 Setup.exe | C:\Users\admin\AppData\Local\Temp\is-N2PQ0.tmp\Nicky Romero - Kickstart 2.0 Setup.tmp | executable | |
MD5:5DE456A8E1849735565DDED694F45910 | SHA256:BE382CEC639818B7511EC2FF17560257C18584734EE1D8E5978EB9945A71B7B8 | |||
| 6368 | Nicky Romero - Kickstart 2.0 Setup.exe | C:\Users\admin\AppData\Local\Temp\is-BQCKU.tmp\Nicky Romero - Kickstart 2.0 Setup.tmp | executable | |
MD5:5DE456A8E1849735565DDED694F45910 | SHA256:BE382CEC639818B7511EC2FF17560257C18584734EE1D8E5978EB9945A71B7B8 | |||
| 6492 | Nicky Romero - Kickstart 2.0 Setup.tmp | C:\Program Files\Steinberg\VSTPlugins\is-5NV98.tmp | executable | |
MD5:22169B146740FF06DE5F20E8C40905C9 | SHA256:21FE97055E7F25A6FFAB45F71422DC7F0E8439F43DAE4266B5B3982266943265 | |||
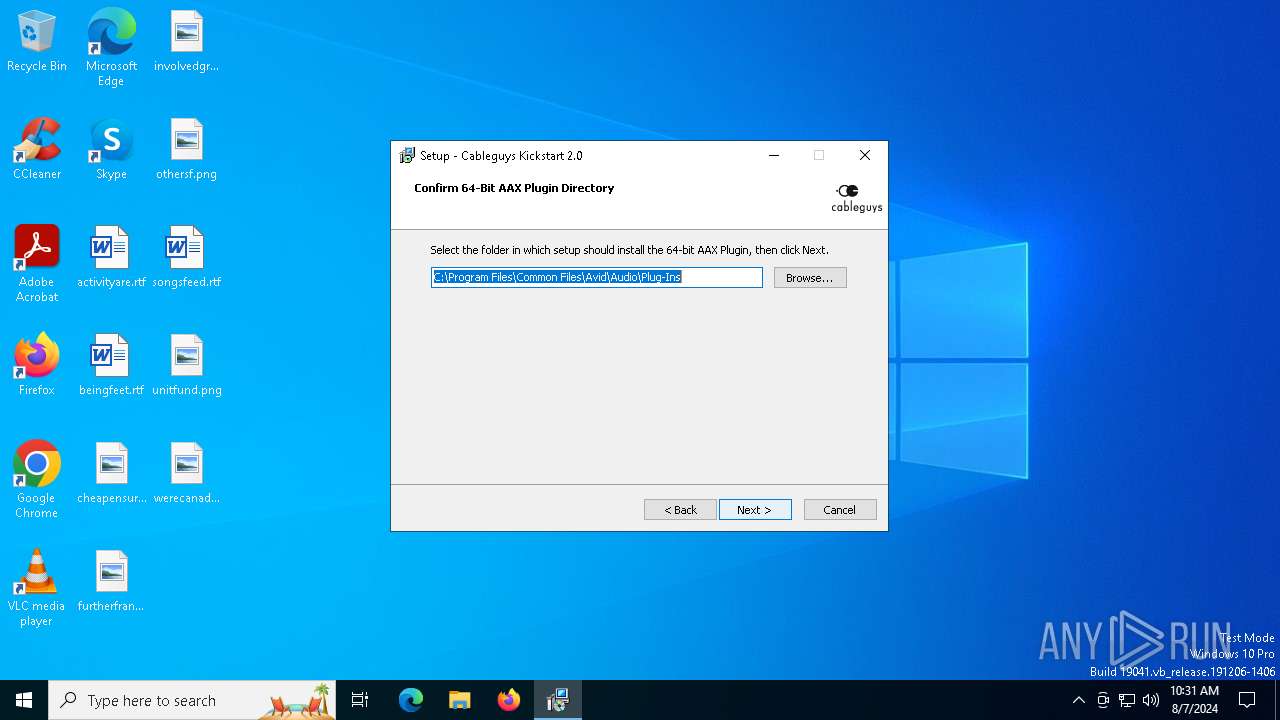
| 6492 | Nicky Romero - Kickstart 2.0 Setup.tmp | C:\Program Files\Common Files\Avid\Audio\Plug-Ins\Kickstart 2.aaxplugin\Contents\x64\Kickstart 2.aaxplugin | executable | |
MD5:6C5340072CB4931F2648D60A0A23EB1F | SHA256:2CEC34BFF356C68386B3876E15DCFD43573A8499D07FBA7E70F9C7D2D09A9B4C | |||
| 6492 | Nicky Romero - Kickstart 2.0 Setup.tmp | C:\Program Files\Cableguys\Kickstart2\is-H0N3Q.tmp | executable | |
MD5:728B1A60EDF28753BFF1FF243B532BFB | SHA256:E48AD294226E317930C3DAA8AFC911AFBB8ED088EECDC2CC329E17FBE53F709F | |||
| 6492 | Nicky Romero - Kickstart 2.0 Setup.tmp | C:\Program Files\Common Files\VST3\is-MS35L.tmp | executable | |
MD5:7CB35247BF9D29A7F1E3E57ED025C30C | SHA256:21C1E192266463BC68A9D0BD4945AB861A1AE06FB6500F4AF165150CB9E961F5 | |||
| 6492 | Nicky Romero - Kickstart 2.0 Setup.tmp | C:\Program Files\Steinberg\VSTPlugins\Kickstart 2.dll | executable | |
MD5:22169B146740FF06DE5F20E8C40905C9 | SHA256:21FE97055E7F25A6FFAB45F71422DC7F0E8439F43DAE4266B5B3982266943265 | |||
| 6492 | Nicky Romero - Kickstart 2.0 Setup.tmp | C:\Program Files\Common Files\Avid\Audio\Plug-Ins\Kickstart 2.aaxplugin\Contents\x64\is-C95PT.tmp | executable | |
MD5:6C5340072CB4931F2648D60A0A23EB1F | SHA256:2CEC34BFF356C68386B3876E15DCFD43573A8499D07FBA7E70F9C7D2D09A9B4C | |||
| 6492 | Nicky Romero - Kickstart 2.0 Setup.tmp | C:\Program Files\Common Files\VST3\Kickstart 2.vst3 | executable | |
MD5:7CB35247BF9D29A7F1E3E57ED025C30C | SHA256:21C1E192266463BC68A9D0BD4945AB861A1AE06FB6500F4AF165150CB9E961F5 | |||
| 6492 | Nicky Romero - Kickstart 2.0 Setup.tmp | C:\Program Files\Common Files\Avid\Audio\Plug-Ins\Kickstart 2.aaxplugin\is-0NOHR.tmp | text | |
MD5:798095CD31340606C8E81D0A5107D57E | SHA256:5526EF6345ADEE7C693E58354DD72B095DF152BE62FF7298B4C6F6D0F91E2F83 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
5
TCP/UDP connections
41
DNS requests
14
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
6768 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
3900 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
6812 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
5336 | SearchApp.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
3900 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2120 | MoUsoCoreWorker.exe | 51.104.136.2:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
3888 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
2532 | RUXIMICS.exe | 51.104.136.2:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
5044 | svchost.exe | 51.104.136.2:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
5044 | svchost.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
5336 | SearchApp.exe | 95.100.146.25:443 | www.bing.com | Akamai International B.V. | CZ | unknown |
3900 | svchost.exe | 40.126.32.134:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
5336 | SearchApp.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
google.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
www.bing.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
login.live.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
fd.api.iris.microsoft.com |
| whitelisted |
th.bing.com |
| whitelisted |
arc.msn.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |