| File name: | peazip-10.4.0.WIN64.exe |
| Full analysis: | https://app.any.run/tasks/aba9c1f2-dad4-49f0-9d7d-e991e8879aae |
| Verdict: | Malicious activity |
| Analysis date: | May 09, 2025, 17:47:46 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows, 8 sections |
| MD5: | B22CCAFC3CA88FF38E42AF4C23B7FE09 |
| SHA1: | C48BF1BC97C7FE7B07350F611C8F23C22B00AE3E |
| SHA256: | 838F3F25D6A03D9C3CF298C3CE6DAF29756AF69524FA608DD92E697669B86C4E |
| SSDEEP: | 98304:xgF0vQL43UbrMxogdSJklSZ6M2spyLc8xG8IgUy9PIh5dHL18mKbdlmSTHjjAri3:s59eHZxllAPO3+j3e2q6A |
MALICIOUS
No malicious indicators.SUSPICIOUS
Executable content was dropped or overwritten
- peazip-10.4.0.WIN64.exe (PID: 7548)
- peazip-10.4.0.WIN64.exe (PID: 7724)
- peazip-10.4.0.WIN64.tmp (PID: 7748)
Reads security settings of Internet Explorer
- peazip-10.4.0.WIN64.tmp (PID: 7576)
- peazip.exe (PID: 6768)
- peazip-10.4.0.WIN64.tmp (PID: 7748)
Reads the Windows owner or organization settings
- peazip-10.4.0.WIN64.tmp (PID: 7748)
Drops 7-zip archiver for unpacking
- peazip-10.4.0.WIN64.tmp (PID: 7748)
The process verifies whether the antivirus software is installed
- peazip.exe (PID: 6768)
- peazip.exe (PID: 6272)
- peazip.exe (PID: 7176)
Reads the date of Windows installation
- peazip.exe (PID: 6768)
There is functionality for taking screenshot (YARA)
- peazip.exe (PID: 7176)
Application launched itself
- peazip.exe (PID: 5156)
The process deletes folder without confirmation
- peazip.exe (PID: 6272)
Starts CMD.EXE for commands execution
- peazip.exe (PID: 6272)
Uses REG/REGEDIT.EXE to modify registry
- peazip.exe (PID: 6768)
INFO
Create files in a temporary directory
- peazip-10.4.0.WIN64.exe (PID: 7548)
- peazip-10.4.0.WIN64.exe (PID: 7724)
- peazip-10.4.0.WIN64.tmp (PID: 7748)
- peazip.exe (PID: 5156)
Reads the computer name
- peazip-10.4.0.WIN64.tmp (PID: 7576)
- peazip-10.4.0.WIN64.tmp (PID: 7748)
- peazip.exe (PID: 6768)
- peazip.exe (PID: 7176)
- peazip.exe (PID: 5156)
- 7z.exe (PID: 4120)
- peazip.exe (PID: 6272)
Checks supported languages
- peazip-10.4.0.WIN64.exe (PID: 7724)
- peazip-10.4.0.WIN64.exe (PID: 7548)
- peazip-10.4.0.WIN64.tmp (PID: 7576)
- peazip-10.4.0.WIN64.tmp (PID: 7748)
- peazip.exe (PID: 6768)
- peazip.exe (PID: 6272)
- peazip.exe (PID: 5156)
- 7z.exe (PID: 4120)
- peazip.exe (PID: 7176)
Process checks computer location settings
- peazip-10.4.0.WIN64.tmp (PID: 7576)
- peazip-10.4.0.WIN64.tmp (PID: 7748)
- peazip.exe (PID: 6768)
Creates files or folders in the user directory
- peazip-10.4.0.WIN64.tmp (PID: 7748)
- peazip.exe (PID: 6768)
- peazip.exe (PID: 7176)
The sample compiled with english language support
- peazip-10.4.0.WIN64.tmp (PID: 7748)
Creates files in the program directory
- peazip-10.4.0.WIN64.tmp (PID: 7748)
Detects InnoSetup installer (YARA)
- peazip-10.4.0.WIN64.exe (PID: 7548)
- peazip-10.4.0.WIN64.tmp (PID: 7576)
- peazip-10.4.0.WIN64.exe (PID: 7724)
- peazip-10.4.0.WIN64.tmp (PID: 7748)
Compiled with Borland Delphi (YARA)
- peazip-10.4.0.WIN64.exe (PID: 7548)
- peazip-10.4.0.WIN64.tmp (PID: 7748)
- peazip-10.4.0.WIN64.tmp (PID: 7576)
- peazip-10.4.0.WIN64.exe (PID: 7724)
- peazip.exe (PID: 7176)
Creates a software uninstall entry
- peazip-10.4.0.WIN64.tmp (PID: 7748)
Manual execution by a user
- peazip.exe (PID: 7176)
- peazip.exe (PID: 5156)
Checks proxy server information
- slui.exe (PID: 7420)
Reads the software policy settings
- slui.exe (PID: 7420)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win32 Executable Delphi generic (57.2) |
|---|---|---|
| .exe | | | Win32 Executable (generic) (18.2) |
| .exe | | | Win16/32 Executable Delphi generic (8.3) |
| .exe | | | Generic Win/DOS Executable (8) |
| .exe | | | DOS Executable Generic (8) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2016:04:06 14:39:04+00:00 |
| ImageFileCharacteristics: | No relocs, Executable, No line numbers, No symbols, Bytes reversed lo, 32-bit, Bytes reversed hi |
| PEType: | PE32 |
| LinkerVersion: | 2.25 |
| CodeSize: | 66560 |
| InitializedDataSize: | 83968 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x117dc |
| OSVersion: | 5 |
| ImageVersion: | 6 |
| SubsystemVersion: | 5 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 0.0.0.0 |
| ProductVersionNumber: | 0.0.0.0 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | Neutral |
| CharacterSet: | Unicode |
| Comments: | This installation was built with Inno Setup. |
| CompanyName: | Giorgio Tani |
| FileDescription: | PeaZip Setup |
| FileVersion: | |
| LegalCopyright: | |
| ProductName: | PeaZip |
| ProductVersion: | 10.4.0 |
Total processes
151
Monitored processes
19
Malicious processes
6
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1056 | cmd /c rmdir "C:\Users\admin\AppData\Local\Temp\peazip-tmp\.pztmp\" /s /q | C:\Windows\System32\cmd.exe | — | peazip.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
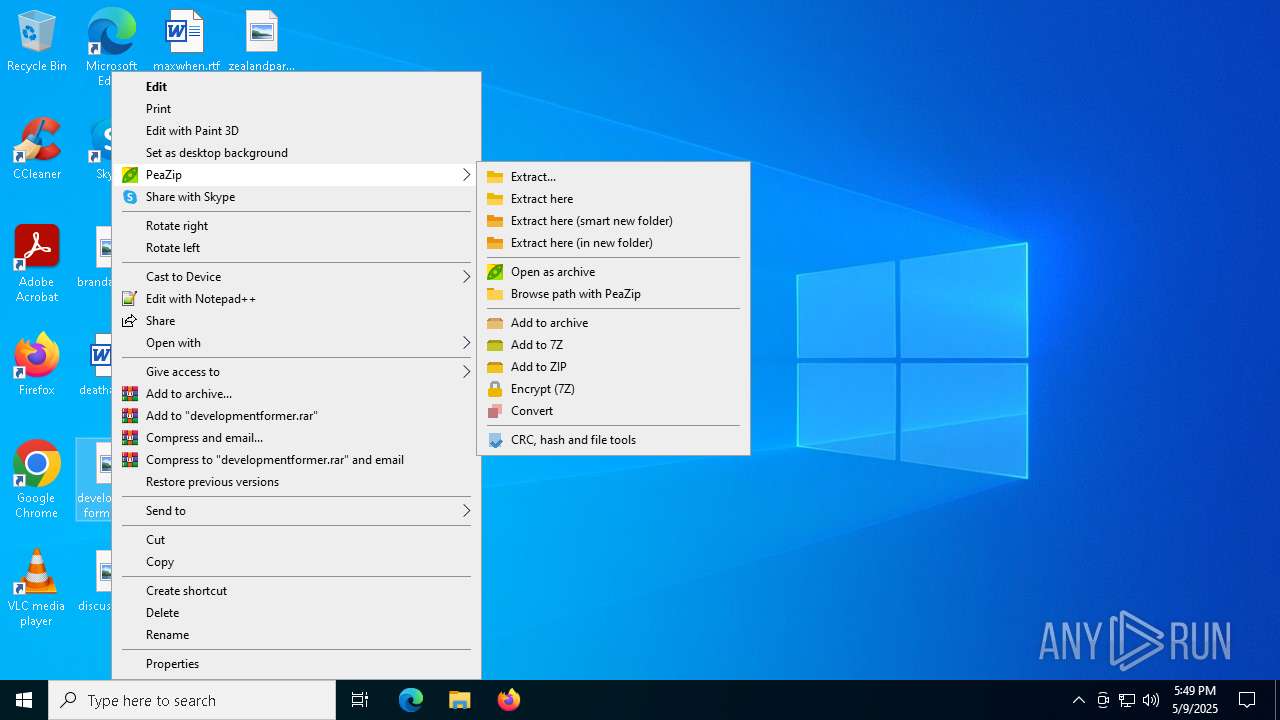
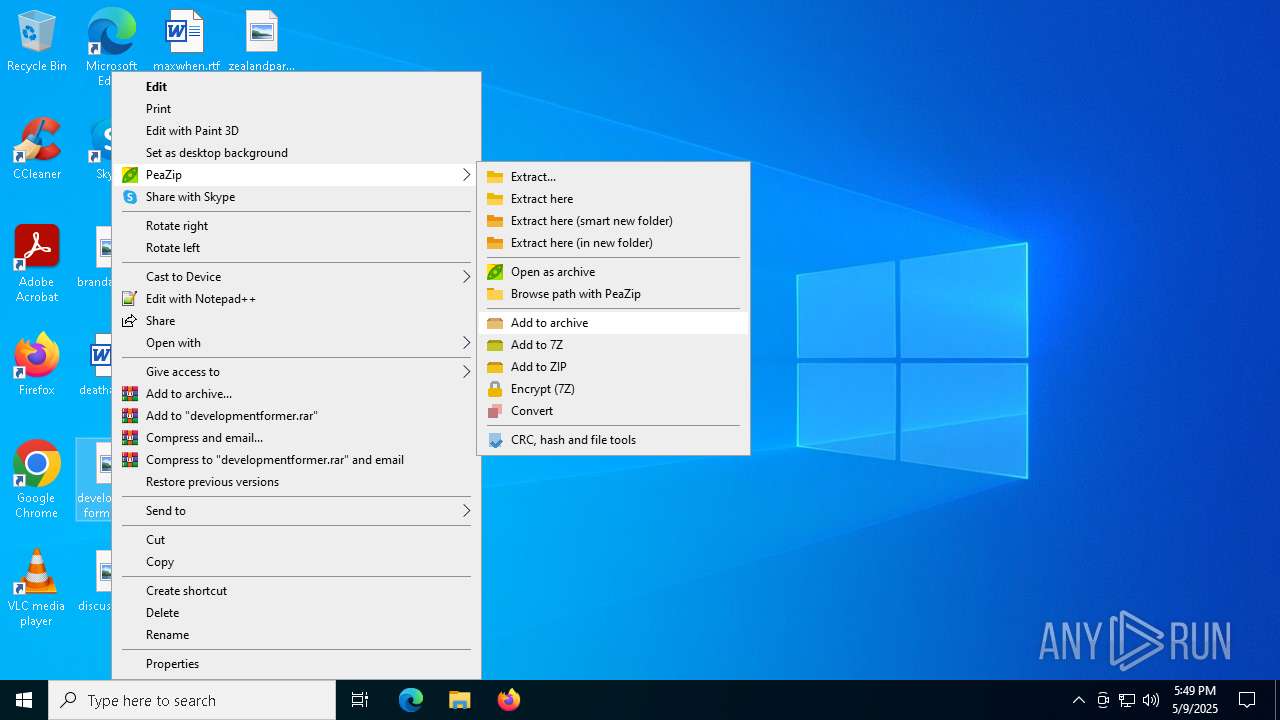
| 4120 | "C:\Program Files\PeaZip\res\bin\7z\7z.exe" a -t7z -m0=LZMA2 -mmt=on -mx3 -md=4m -mfb=32 -ms=1g -mqs=on -sccUTF-8 -bb0 -bse0 -bsp2 "-wC:\Users\admin\Desktop\" -snl -mtc=on -mta=on "C:\Users\admin\Desktop\developmentformer.7z" "C:\Users\admin\Desktop\developmentformer.jpg" | C:\Program Files\PeaZip\res\bin\7z\7z.exe | — | peazip.exe | |||||||||||
User: admin Company: Igor Pavlov Integrity Level: MEDIUM Description: 7-Zip Console Exit code: 0 Version: 24.09 Modules
| |||||||||||||||
| 4408 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | 7z.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4608 | cmd /c rmdir "C:\Users\admin\AppData\Local\Temp\peazip-tmp\.pztmp\add7z250509" /s /q | C:\Windows\System32\cmd.exe | — | peazip.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4976 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5156 | "C:\Program Files\PeaZip\PEAZIP.EXE" "-add2multi7z" "C:\Users\admin\Desktop\developmentformer.jpg" | C:\Program Files\PeaZip\peazip.exe | — | explorer.exe | |||||||||||
User: admin Company: Giorgio Tani Integrity Level: MEDIUM Description: PeaZip, file and archive manager Exit code: 0 Version: 10.4.0 Modules
| |||||||||||||||
| 6272 | "C:\Program Files\PeaZip\peazip.exe" -add2archivemulti7z default "C:\Users\admin\AppData\Local\Temp\peazip-tmp\.pztmp\add7z250509" | C:\Program Files\PeaZip\peazip.exe | — | peazip.exe | |||||||||||
User: admin Company: Giorgio Tani Integrity Level: MEDIUM Description: PeaZip, file and archive manager Exit code: 0 Version: 10.4.0 Modules
| |||||||||||||||
| 6476 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6540 | cmd /c rmdir "C:\Users\admin\AppData\Local\Temp\peazip-tmp\" /s /q | C:\Windows\System32\cmd.exe | — | peazip.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6768 | "C:\Program Files\PeaZip\peazip.exe" -peaziplanguage *nochange | C:\Program Files\PeaZip\peazip.exe | — | peazip-10.4.0.WIN64.tmp | |||||||||||
User: admin Company: Giorgio Tani Integrity Level: HIGH Description: PeaZip, file and archive manager Exit code: 0 Version: 10.4.0 Modules
| |||||||||||||||
Total events
1 934
Read events
1 872
Write events
62
Delete events
0
Modification events
| (PID) Process: | (7748) peazip-10.4.0.WIN64.tmp | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Classes\*\shell\PeaZip |
| Operation: | write | Name: | SubCommands |
Value: PeaZip.ext2main; PeaZip.ext2here; PeaZip.ext2smart; PeaZip.ext2folder; PeaZip.ext2browseasarchive; PeaZip.ext2browsepath; PeaZip.add2separate; PeaZip.add2separate7z; PeaZip.add2separatezip; PeaZip.add2separate7zencrypt; PeaZip.add2convert; PeaZip.analyze; | |||
| (PID) Process: | (7748) peazip-10.4.0.WIN64.tmp | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Classes\*\shell\PeaZip |
| Operation: | write | Name: | MultiSelectModel |
Value: player | |||
| (PID) Process: | (7748) peazip-10.4.0.WIN64.tmp | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Classes\*\shell\PeaZip |
| Operation: | write | Name: | Icon |
Value: "C:\Program Files\PeaZip\peazip.exe",0 | |||
| (PID) Process: | (7748) peazip-10.4.0.WIN64.tmp | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Classes\AllFilesystemObjects\shell\PeaZip |
| Operation: | write | Name: | SubCommands |
Value: PeaZip.ext2main; PeaZip.ext2here; PeaZip.ext2smart; PeaZip.ext2folder; PeaZip.ext2browseasarchive; PeaZip.ext2browsepath; PeaZip.add2separate; PeaZip.add2separate7z; PeaZip.add2separatezip; PeaZip.add2separate7zencrypt; PeaZip.add2convert; PeaZip.analyze; | |||
| (PID) Process: | (7748) peazip-10.4.0.WIN64.tmp | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Classes\AllFilesystemObjects\shell\PeaZip |
| Operation: | write | Name: | MultiSelectModel |
Value: player | |||
| (PID) Process: | (7748) peazip-10.4.0.WIN64.tmp | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Classes\AllFilesystemObjects\shell\PeaZip |
| Operation: | write | Name: | Icon |
Value: "C:\Program Files\PeaZip\peazip.exe",0 | |||
| (PID) Process: | (7748) peazip-10.4.0.WIN64.tmp | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\CommandStore\shell\PeaZip.add2separate |
| Operation: | write | Name: | Icon |
Value: "C:\Program Files\PeaZip\res\share\icons\peazip_seven.icl",2 | |||
| (PID) Process: | (7748) peazip-10.4.0.WIN64.tmp | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\CommandStore\shell\PeaZip.add2separatesingle |
| Operation: | write | Name: | Icon |
Value: "C:\Program Files\PeaZip\res\share\icons\peazip_seven.icl",2 | |||
| (PID) Process: | (7748) peazip-10.4.0.WIN64.tmp | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\CommandStore\shell\PeaZip.add2separategz |
| Operation: | write | Name: | Icon |
Value: "C:\Program Files\PeaZip\res\share\icons\peazip_seven.icl",2 | |||
| (PID) Process: | (7748) peazip-10.4.0.WIN64.tmp | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\CommandStore\shell\PeaZip.add2separatexz |
| Operation: | write | Name: | Icon |
Value: "C:\Program Files\PeaZip\res\share\icons\peazip_seven.icl",2 | |||
Executable files
69
Suspicious files
198
Text files
664
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 7548 | peazip-10.4.0.WIN64.exe | C:\Users\admin\AppData\Local\Temp\is-FD79V.tmp\peazip-10.4.0.WIN64.tmp | executable | |
MD5:889C8EF91AC310544D1539AC3CDC0F07 | SHA256:7BA798767F82812CC3BFBA370B6797FD29ECDCDDC52BAF967A52773EDEE4A0C7 | |||
| 7724 | peazip-10.4.0.WIN64.exe | C:\Users\admin\AppData\Local\Temp\is-ACH15.tmp\peazip-10.4.0.WIN64.tmp | executable | |
MD5:889C8EF91AC310544D1539AC3CDC0F07 | SHA256:7BA798767F82812CC3BFBA370B6797FD29ECDCDDC52BAF967A52773EDEE4A0C7 | |||
| 7748 | peazip-10.4.0.WIN64.tmp | C:\Users\admin\AppData\Roaming\Microsoft\Windows\SendTo\Test archive(s).lnk | binary | |
MD5:913A637F2ECD2D89B6B5397E9EA6DDEA | SHA256:E587CC7C0B7A1B3F9BC1943A03A007004B7B61BD7577ABAECFEBC7524F51B0E2 | |||
| 7748 | peazip-10.4.0.WIN64.tmp | C:\Program Files\PeaZip\is-IE3A8.tmp | executable | |
MD5:1DF1C9AA6D093AEACF0ADEF67952FFF7 | SHA256:4AB51A34DE9D99AECC92DB1B24DB5084E61A8CE2E538C3F98938BD7749868532 | |||
| 7748 | peazip-10.4.0.WIN64.tmp | C:\Program Files\PeaZip\unins000.exe | executable | |
MD5:7119FB3DD7A59E147CF9F7BDAF9FF5F9 | SHA256:8006AD4860F93E301798E7E8B8A8E721EAABBD0A8BD1656C2518F5A5FC36B6B5 | |||
| 7748 | peazip-10.4.0.WIN64.tmp | C:\Users\admin\AppData\Roaming\Microsoft\Windows\SendTo\Browse path with PeaZip.lnk | binary | |
MD5:21EB661E12B3C21FC0654BCEE66260C3 | SHA256:21833B5702FE10BE4AD6A76E1DDE9C05A65E08BF27AABCDCEF81A3747DB26E4B | |||
| 7748 | peazip-10.4.0.WIN64.tmp | C:\Program Files\PeaZip\peazip.exe | executable | |
MD5:C9D546D7776CA2FB2923EA3AA469AC0F | SHA256:CF2B9428E64286E63C881869ED1A145E6C880EB75AB06AE2589AF584BE236678 | |||
| 7748 | peazip-10.4.0.WIN64.tmp | C:\Program Files\PeaZip\is-OG2H7.tmp | executable | |
MD5:A6F5478036F2A15DAA94E280DB0DBE09 | SHA256:84A6FFDB6162CAD5B42B6AB34FB8CB8685791C2E722A548AAE7B69787CF02A34 | |||
| 7748 | peazip-10.4.0.WIN64.tmp | C:\Program Files\PeaZip\is-7M72K.tmp | executable | |
MD5:7119FB3DD7A59E147CF9F7BDAF9FF5F9 | SHA256:8006AD4860F93E301798E7E8B8A8E721EAABBD0A8BD1656C2518F5A5FC36B6B5 | |||
| 7748 | peazip-10.4.0.WIN64.tmp | C:\Program Files\PeaZip\is-T1RTR.tmp | executable | |
MD5:C9D546D7776CA2FB2923EA3AA469AC0F | SHA256:CF2B9428E64286E63C881869ED1A145E6C880EB75AB06AE2589AF584BE236678 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
7
TCP/UDP connections
22
DNS requests
15
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
5496 | MoUsoCoreWorker.exe | GET | 200 | 23.48.23.181:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
5496 | MoUsoCoreWorker.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
2104 | svchost.exe | GET | 200 | 23.48.23.181:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
2104 | svchost.exe | GET | 304 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
6544 | svchost.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
8032 | SIHClient.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
8032 | SIHClient.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
7000 | RUXIMICS.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
5496 | MoUsoCoreWorker.exe | 23.48.23.181:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
2104 | svchost.exe | 23.48.23.181:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
5496 | MoUsoCoreWorker.exe | 95.101.149.131:80 | www.microsoft.com | Akamai International B.V. | NL | whitelisted |
2104 | svchost.exe | 95.101.149.131:80 | www.microsoft.com | Akamai International B.V. | NL | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
2104 | svchost.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
3216 | svchost.exe | 172.211.123.248:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | FR | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |
activation-v2.sls.microsoft.com |
| whitelisted |
nexusrules.officeapps.live.com |
| whitelisted |
login.live.com |
| whitelisted |