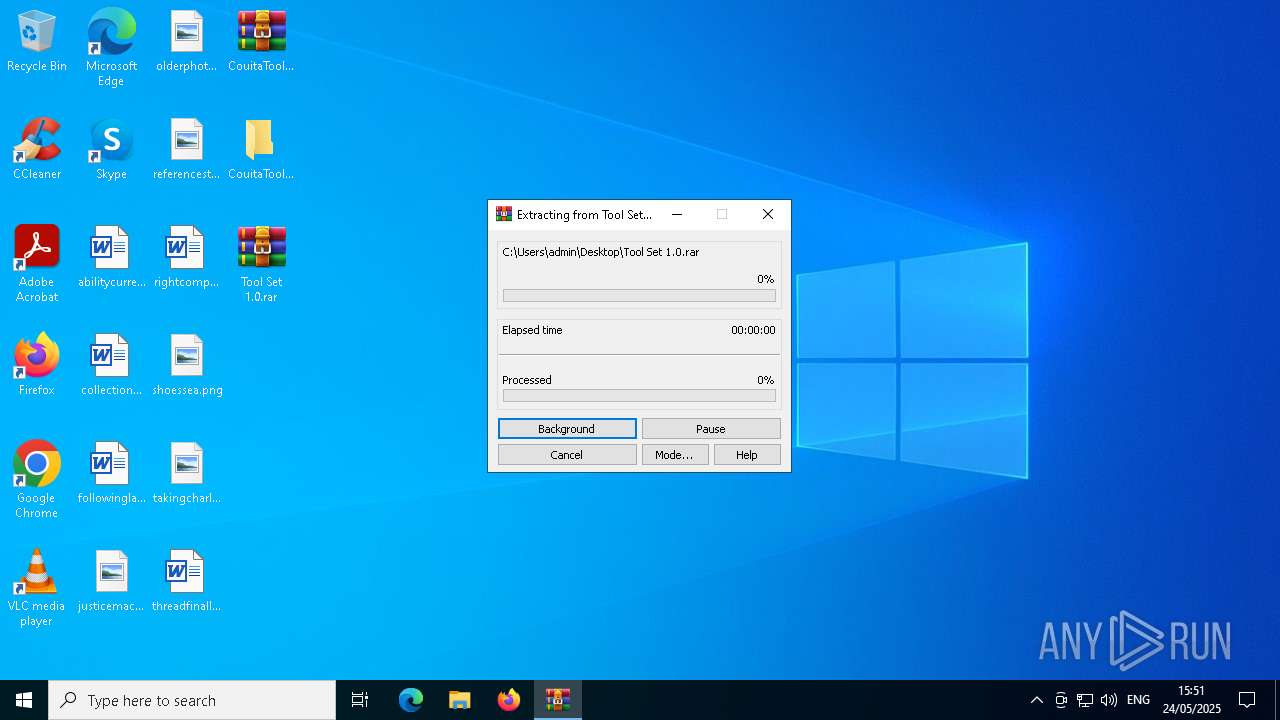
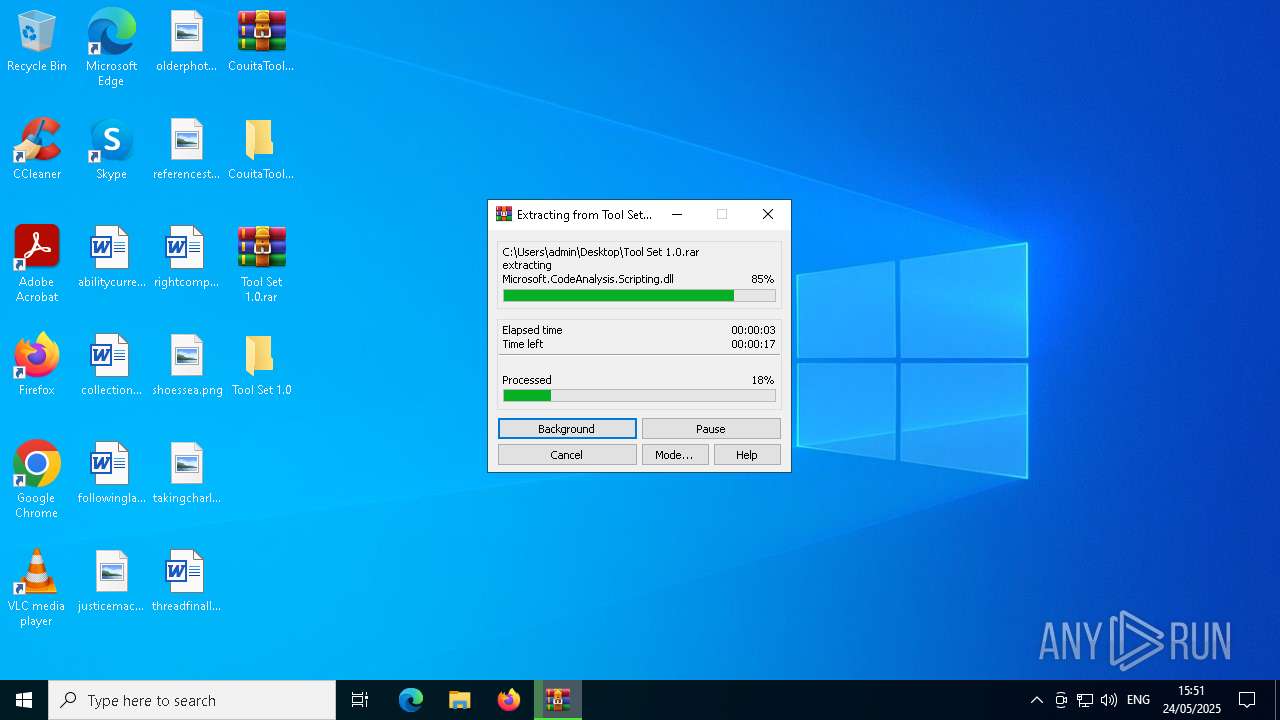
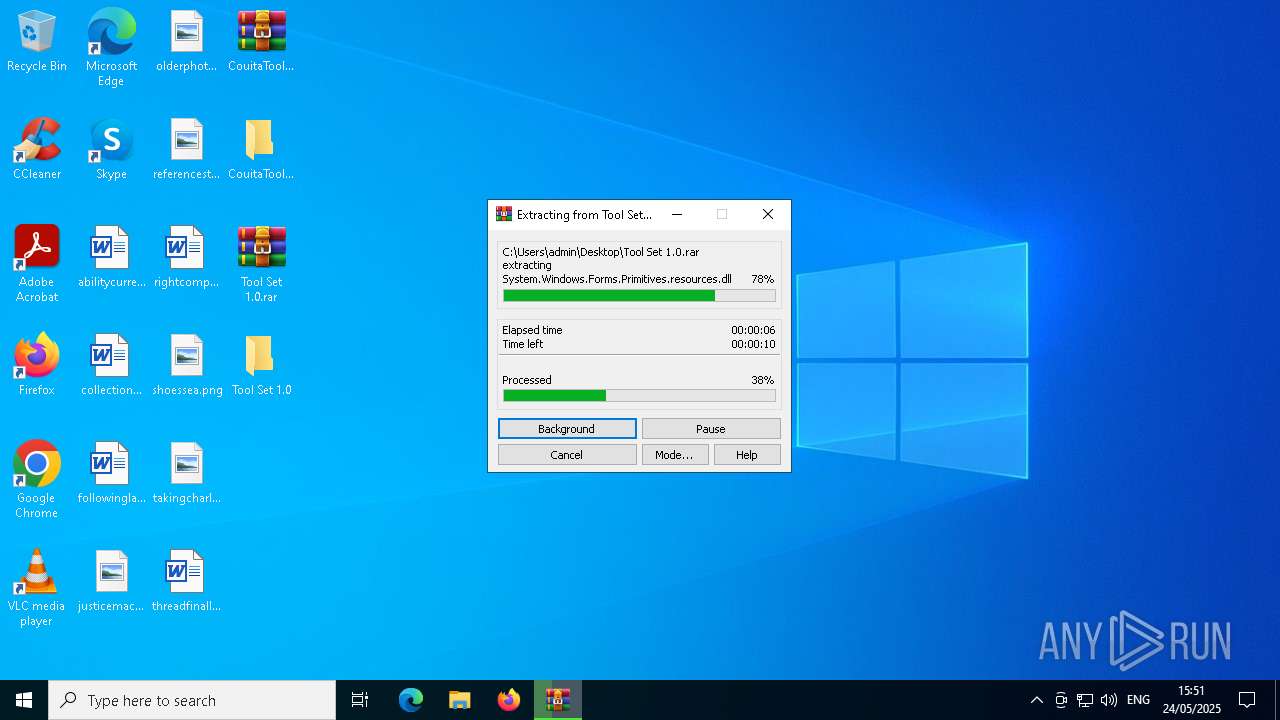
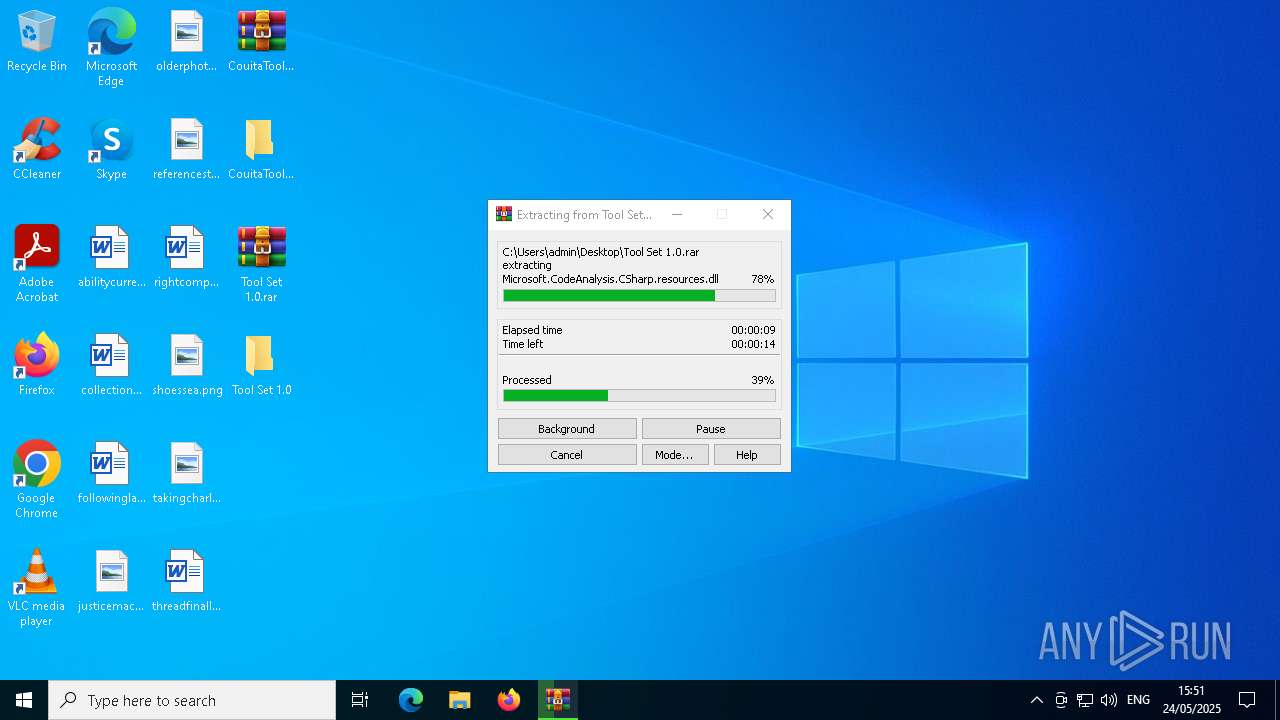
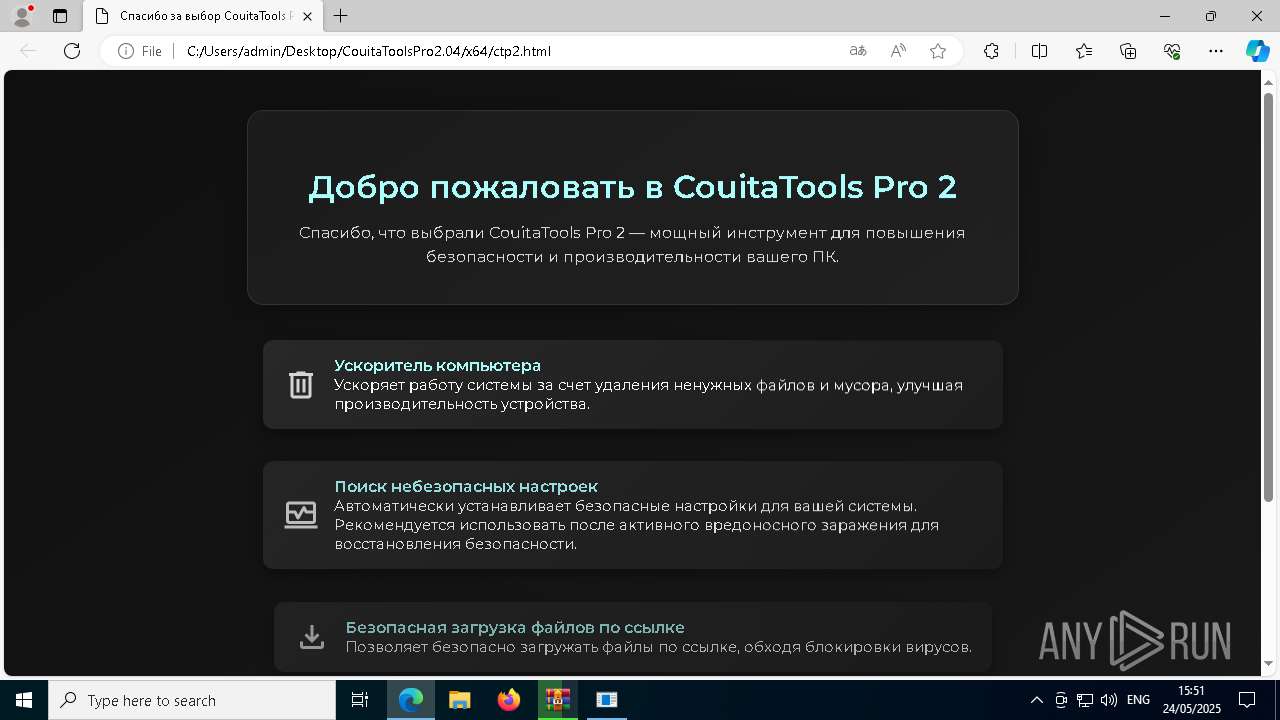
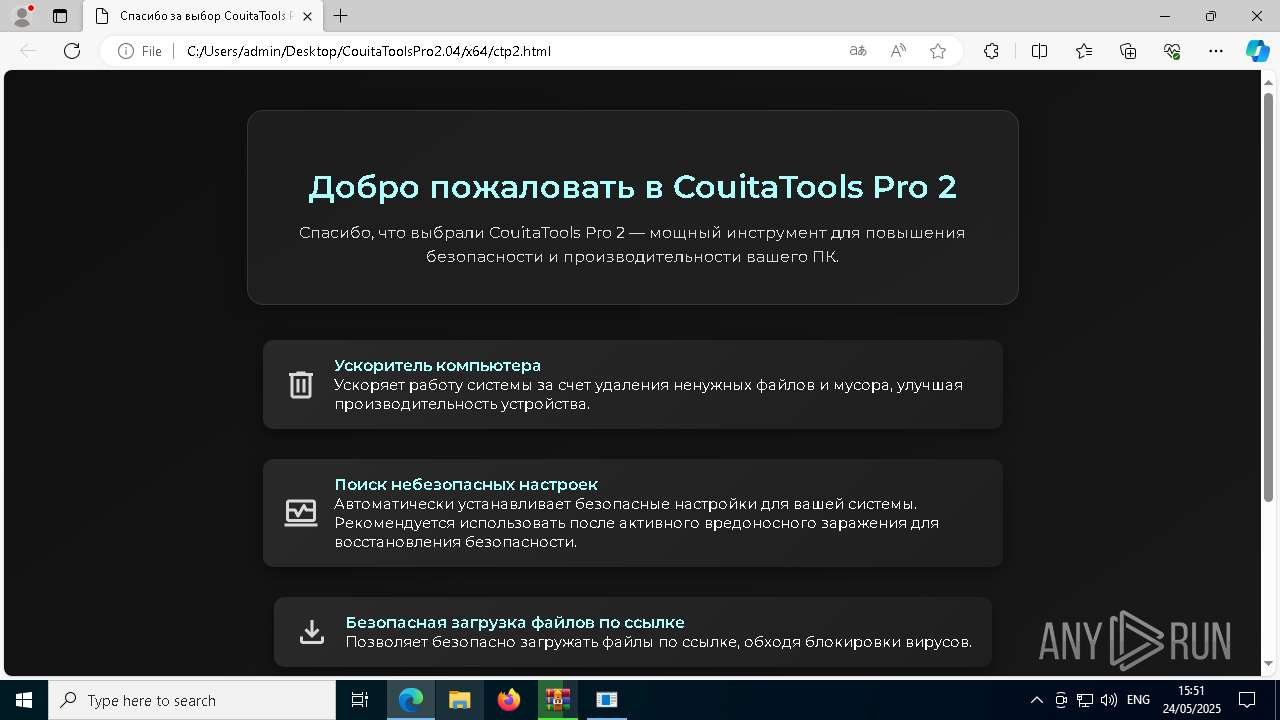
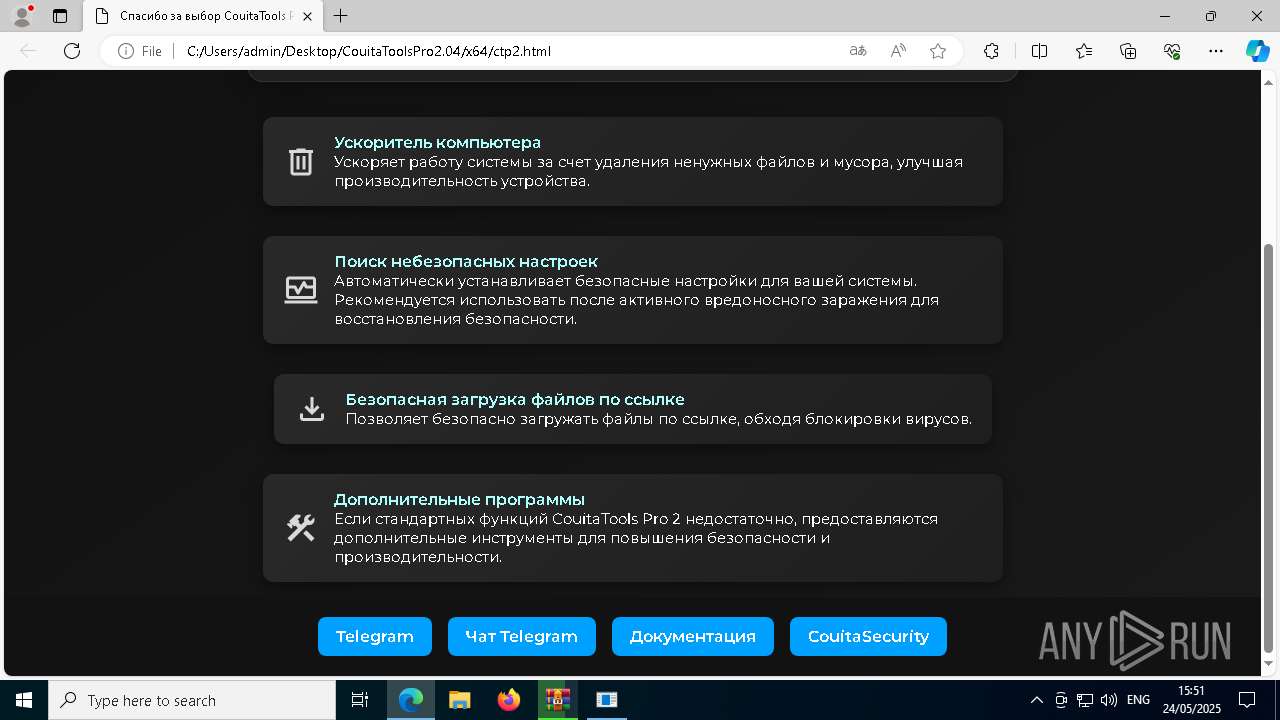
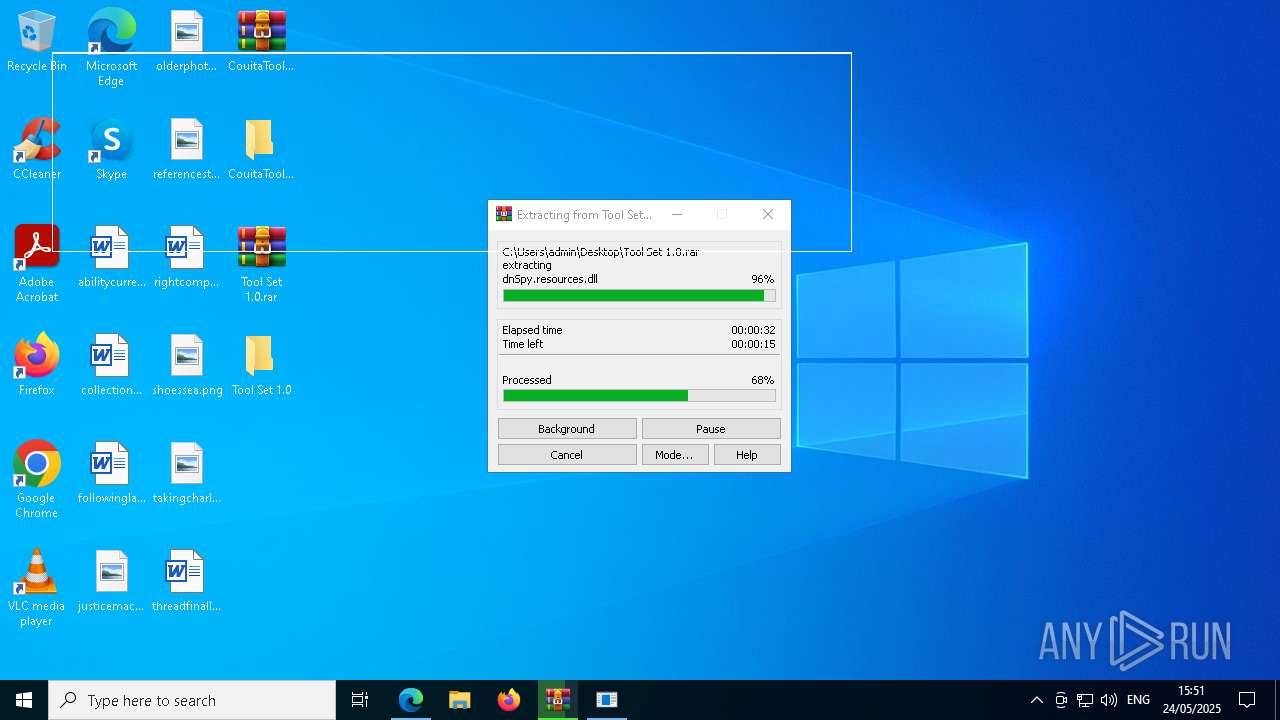
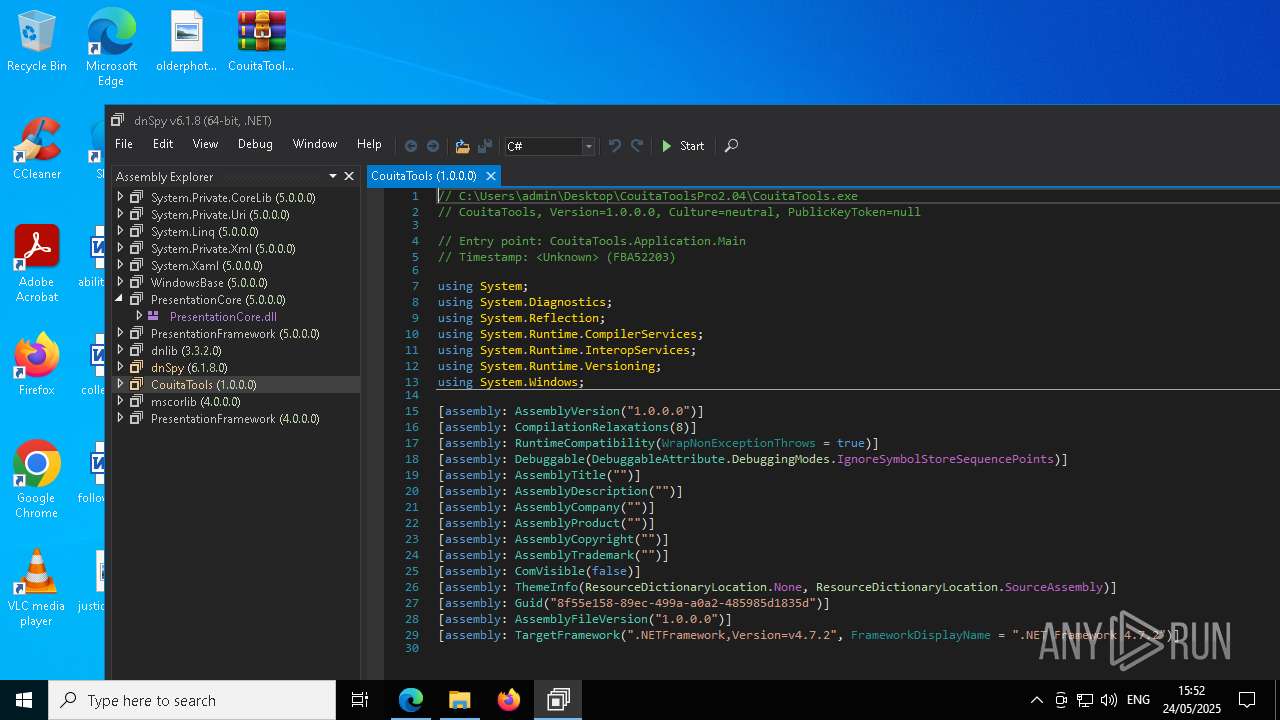
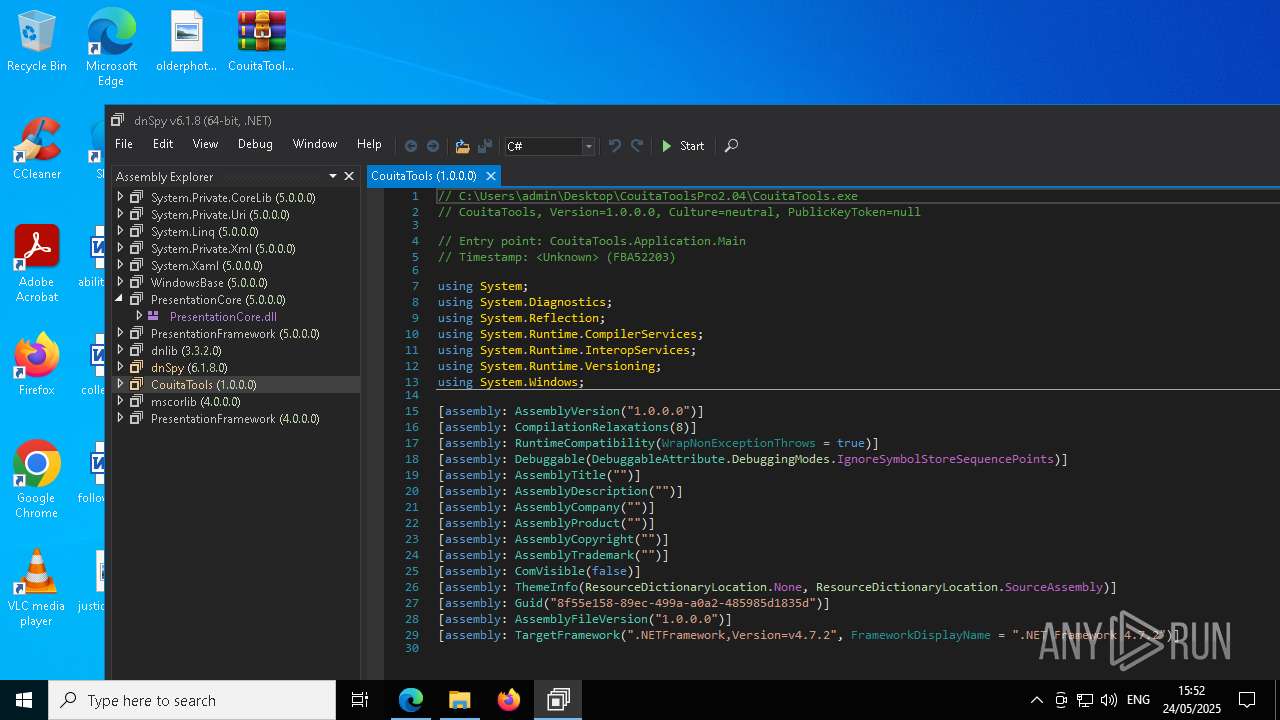
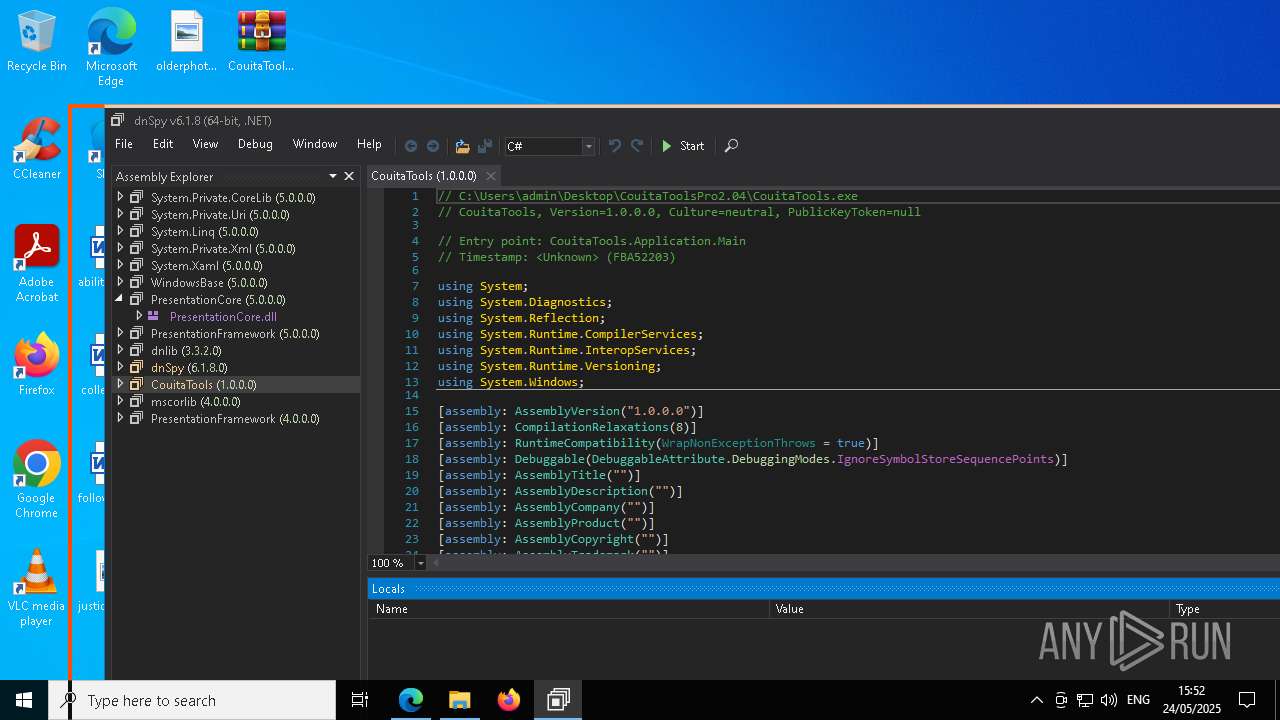
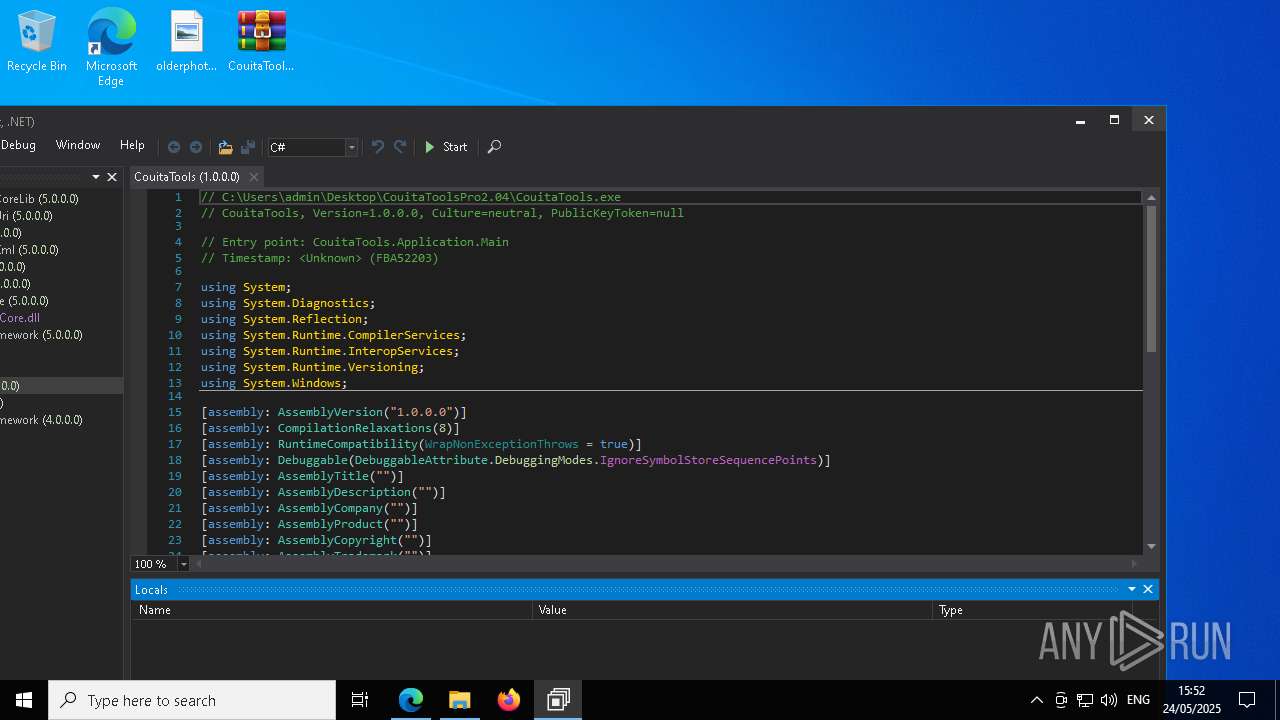
| File name: | CouitaToolsPro2.04.7z |
| Full analysis: | https://app.any.run/tasks/666c7b8c-ff62-4131-b0d5-fa7964f092c8 |
| Verdict: | Malicious activity |
| Analysis date: | May 24, 2025, 14:49:57 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-7z-compressed |
| File info: | 7-zip archive data, version 0.4 |
| MD5: | 2ADB523294F913705CEC28BE24D6A9E6 |
| SHA1: | 795406C390A9C855550B6618E348195D6E507326 |
| SHA256: | 838C1E20E46C8E420CA74015DE734084C239ABEDBD814BF28330380B5EA12BB1 |
| SSDEEP: | 98304:aVXcSIVaMF13FfNuGsV3GLX6XADiWLU81EIX3NMt9rWAlWX8499+XqBzR9enII3E:93d |
MALICIOUS
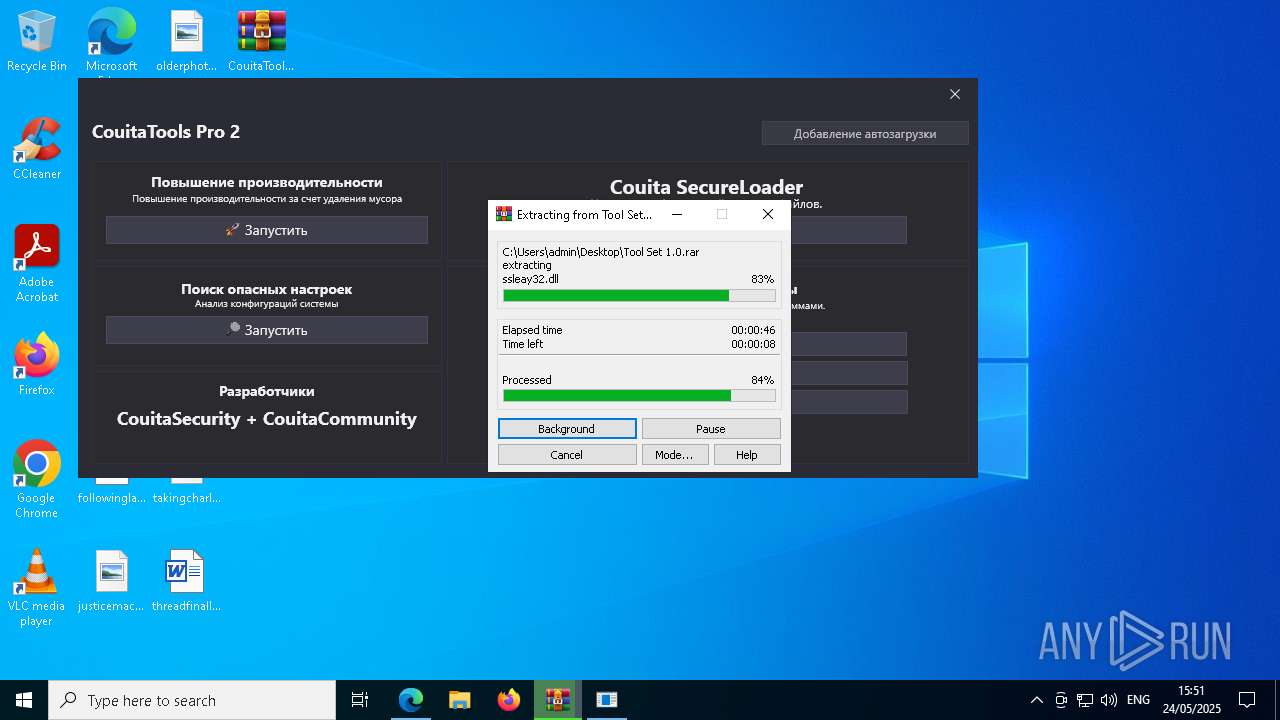
Generic archive extractor
- WinRAR.exe (PID: 5064)
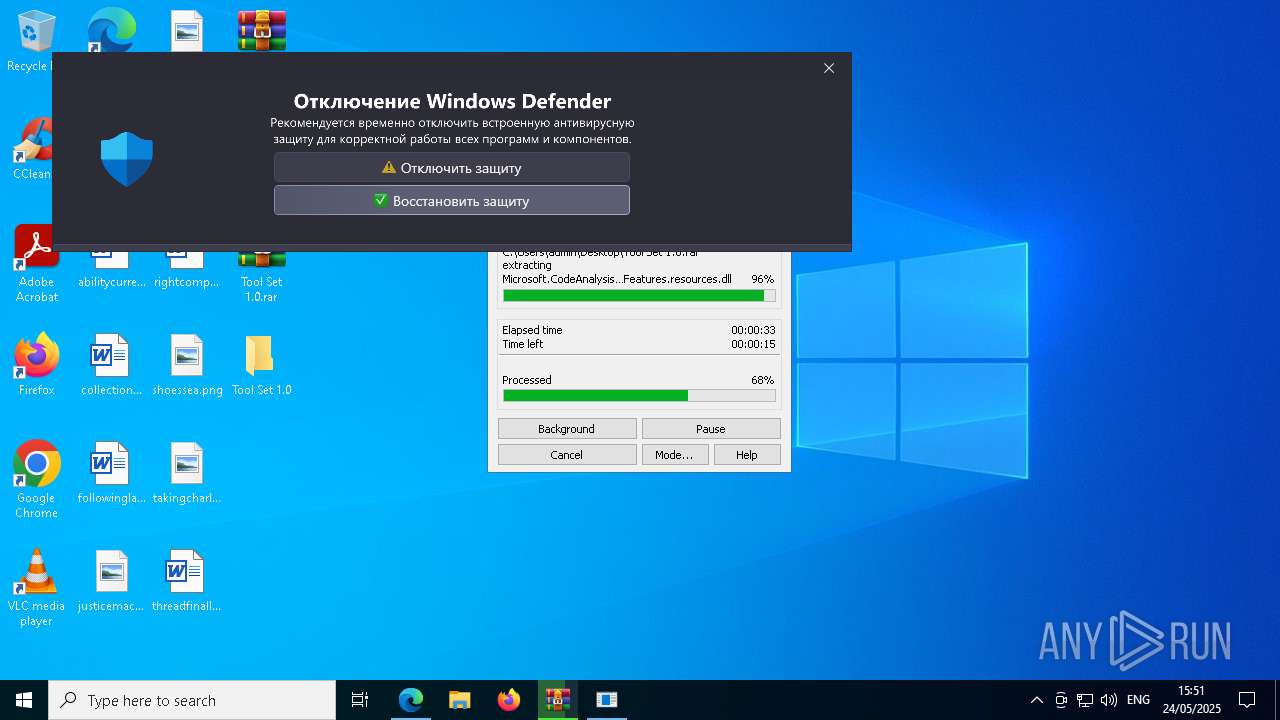
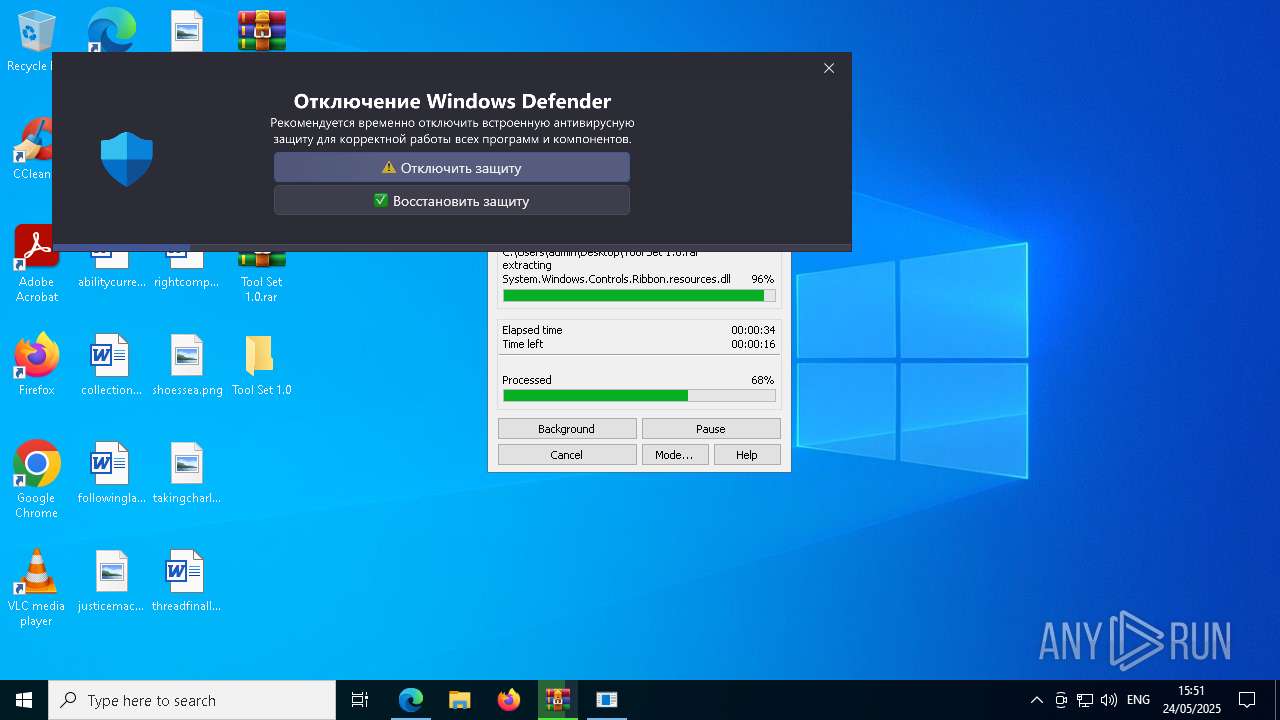
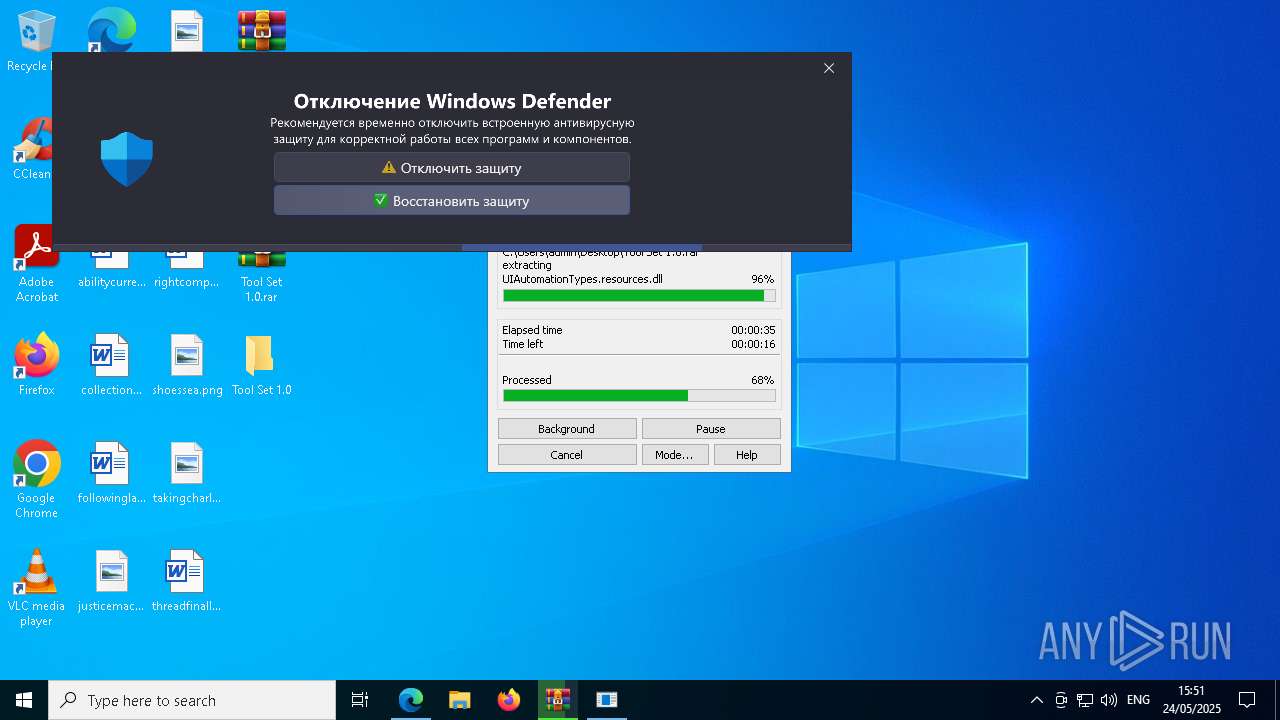
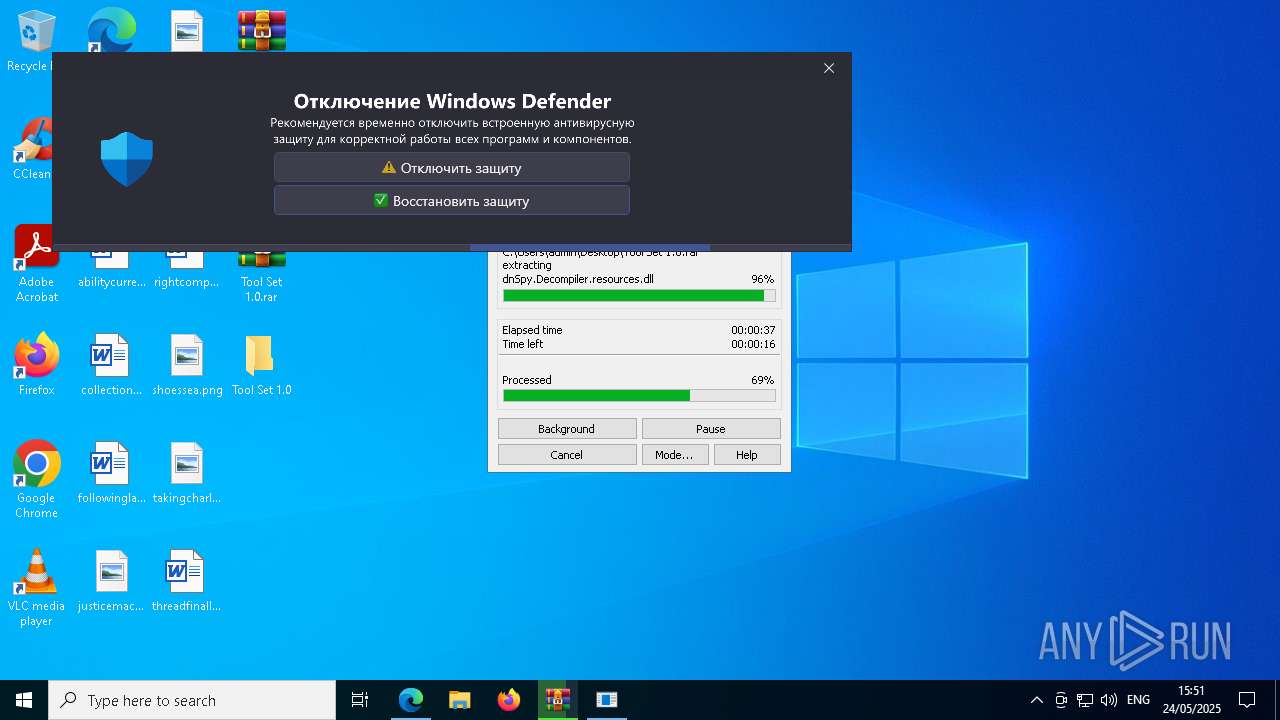
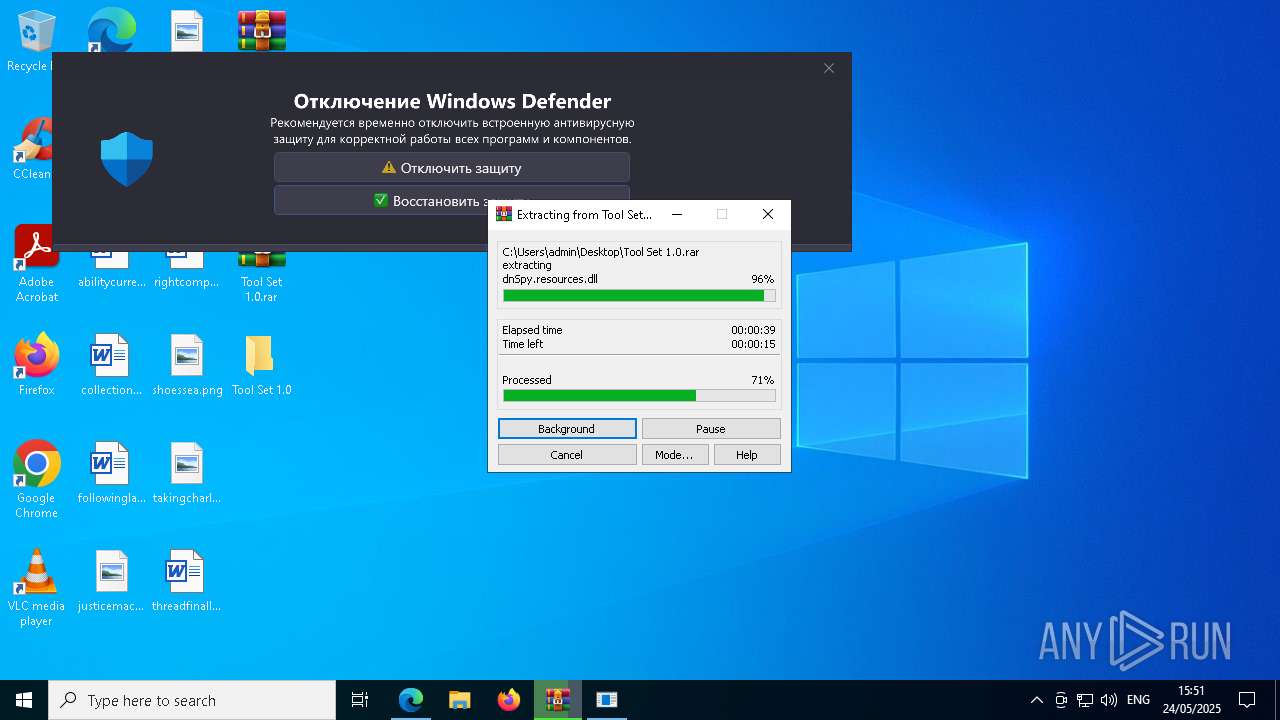
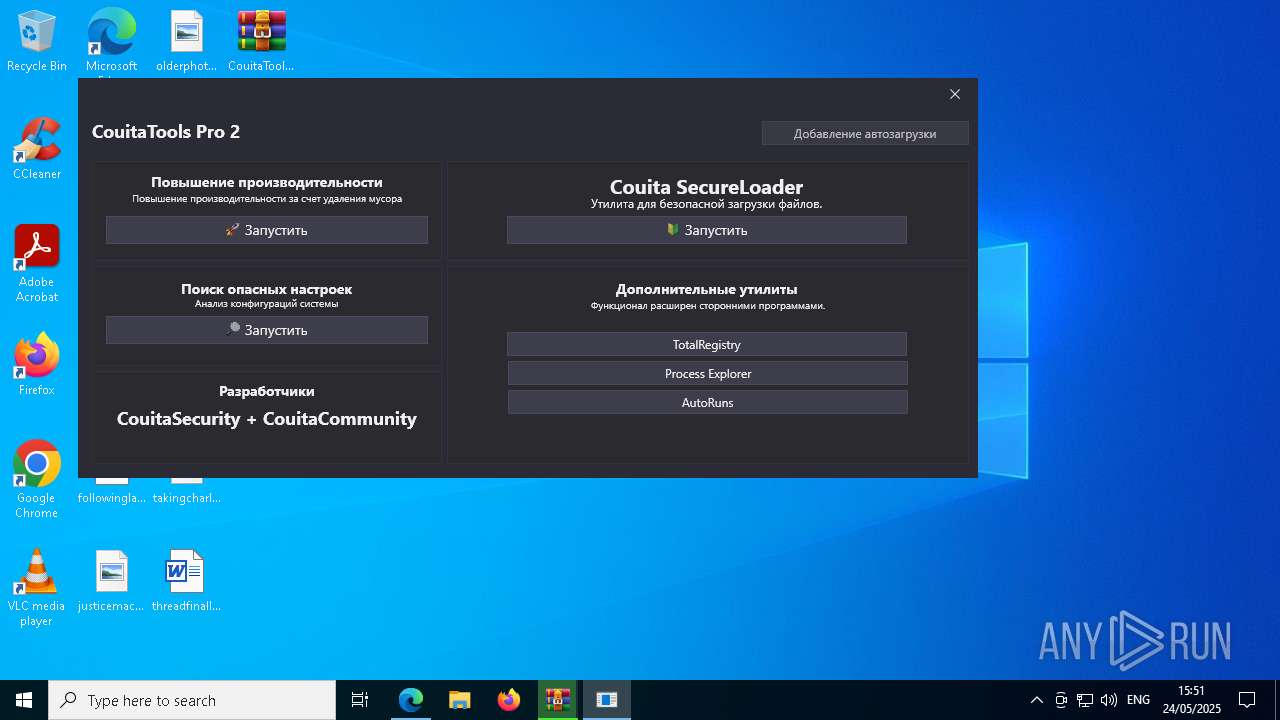
Changes Windows Defender settings
- CouitaTools.exe (PID: 1240)
Vulnerable driver has been detected
- WinRAR.exe (PID: 1348)
Adds path to the Windows Defender exclusion list
- CouitaTools.exe (PID: 1240)
Adds extension to the Windows Defender exclusion list
- CouitaTools.exe (PID: 1240)
SUSPICIOUS
Process drops legitimate windows executable
- WinRAR.exe (PID: 1348)
Reads security settings of Internet Explorer
- CouitaTools.exe (PID: 1240)
The process creates files with name similar to system file names
- WinRAR.exe (PID: 1348)
Starts POWERSHELL.EXE for commands execution
- CouitaTools.exe (PID: 1240)
Uses REG/REGEDIT.EXE to modify registry
- powershell.exe (PID: 6248)
- powershell.exe (PID: 7316)
Script adds exclusion path to Windows Defender
- CouitaTools.exe (PID: 1240)
Script adds exclusion extension to Windows Defender
- CouitaTools.exe (PID: 1240)
Drops a system driver (possible attempt to evade defenses)
- WinRAR.exe (PID: 1348)
INFO
Manual execution by a user
- WinRAR.exe (PID: 5968)
- WinRAR.exe (PID: 1348)
- CouitaTools.exe (PID: 1240)
- CouitaTools.exe (PID: 6752)
- msedge.exe (PID: 2192)
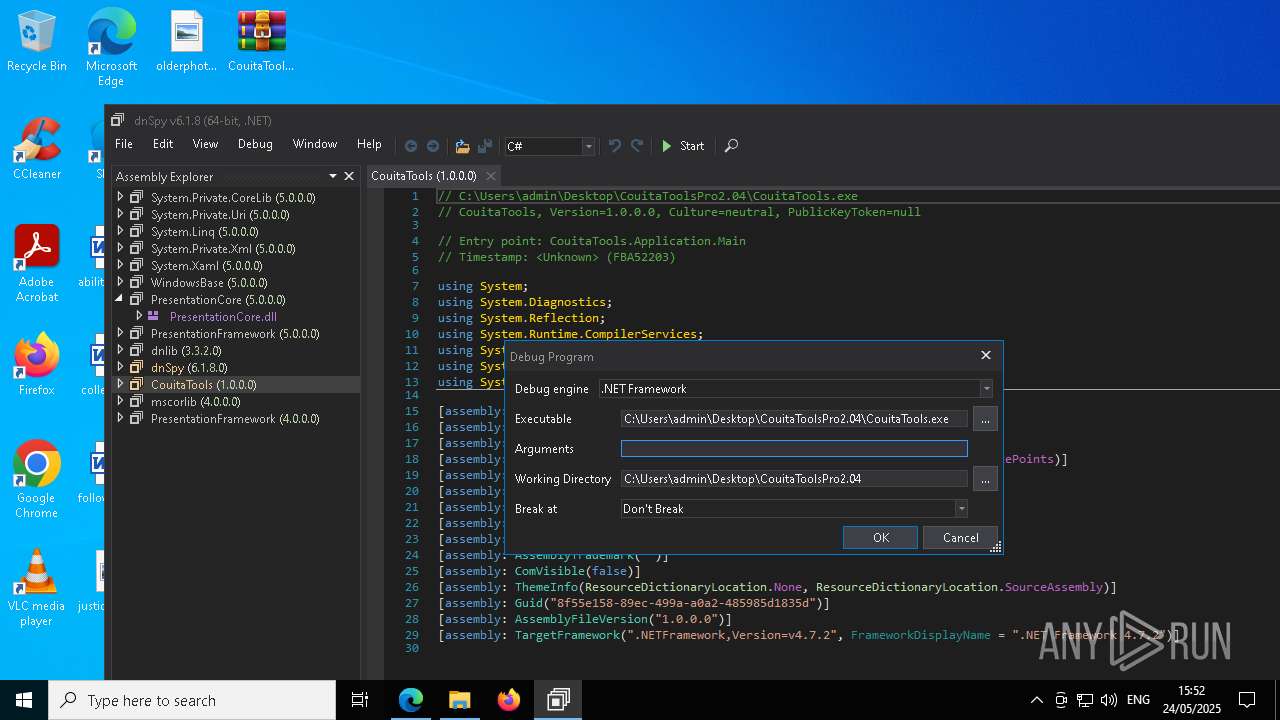
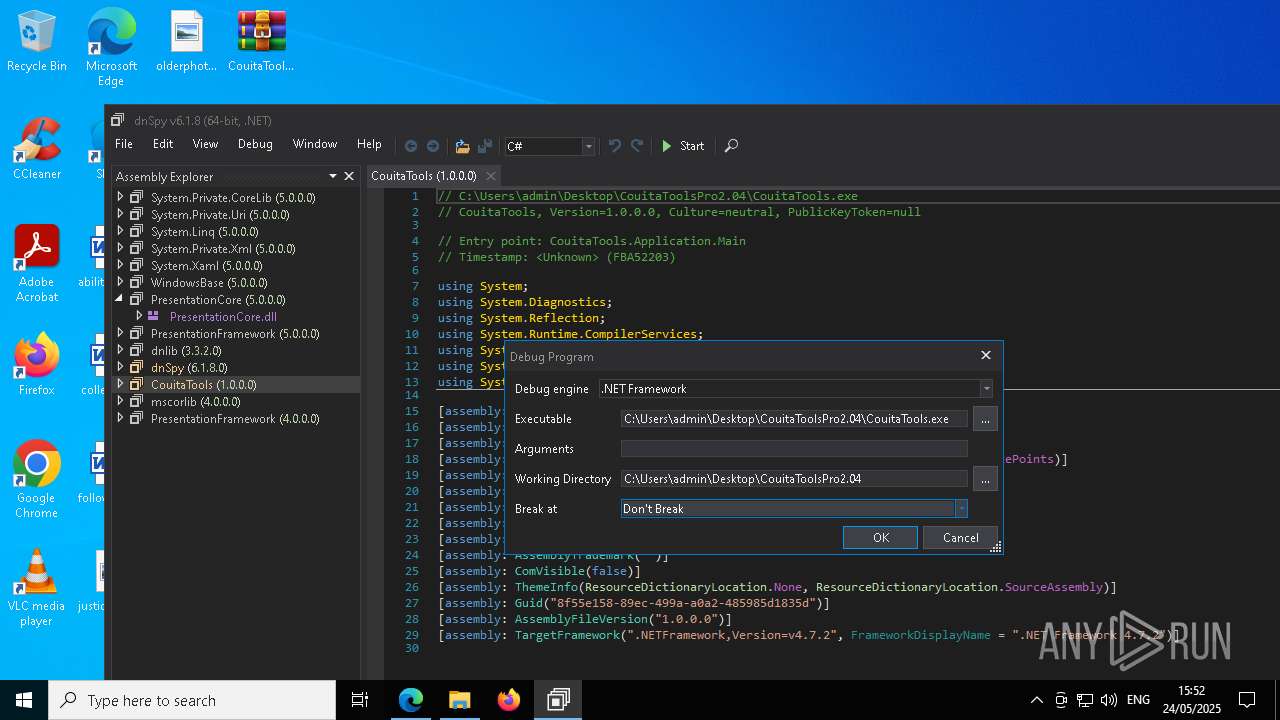
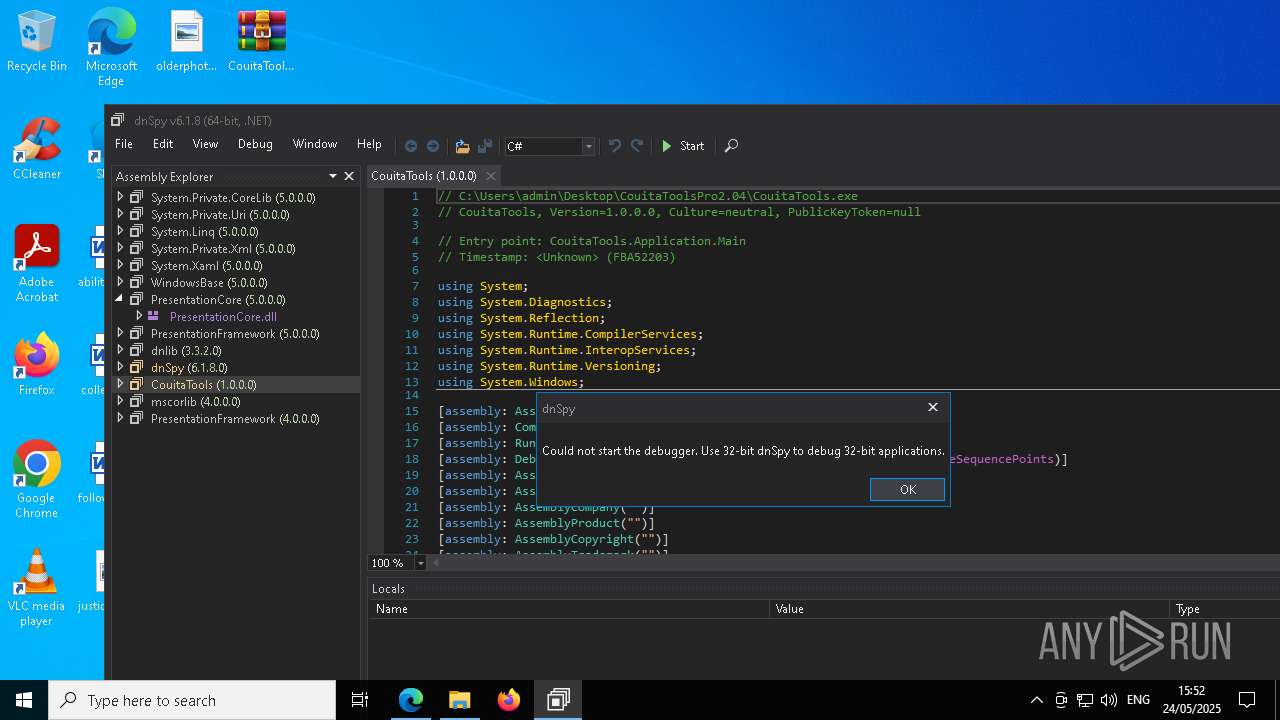
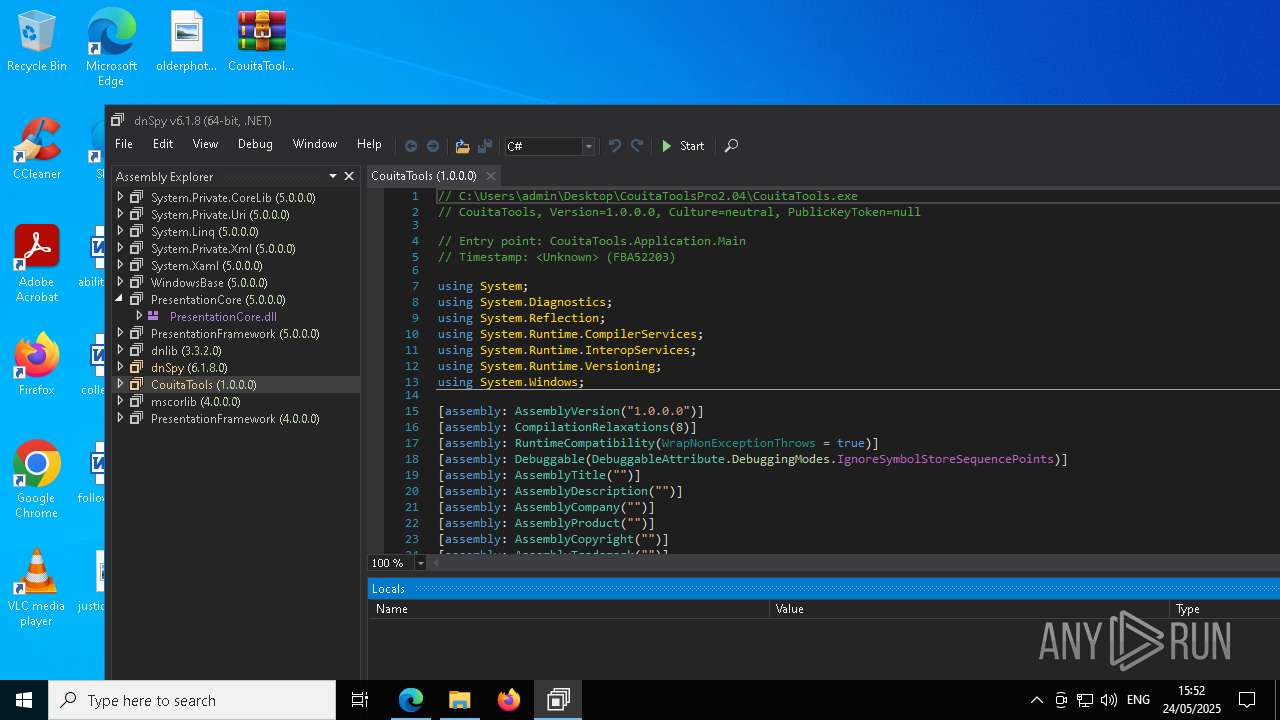
- dnSpy.exe (PID: 8108)
The sample compiled with english language support
- WinRAR.exe (PID: 5968)
- WinRAR.exe (PID: 1348)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 5968)
- WinRAR.exe (PID: 1348)
Checks supported languages
- CouitaTools.exe (PID: 1240)
- identity_helper.exe (PID: 7612)
Reads the computer name
- CouitaTools.exe (PID: 1240)
- identity_helper.exe (PID: 7612)
Application launched itself
- msedge.exe (PID: 4688)
- msedge.exe (PID: 2192)
Reads the machine GUID from the registry
- CouitaTools.exe (PID: 1240)
Reads Environment values
- identity_helper.exe (PID: 7612)
Checks if a key exists in the options dictionary (POWERSHELL)
- powershell.exe (PID: 7904)
- powershell.exe (PID: 8016)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .7z | | | 7-Zip compressed archive (v0.4) (57.1) |
|---|---|---|
| .7z | | | 7-Zip compressed archive (gen) (42.8) |
EXIF
ZIP
| FileVersion: | 7z v0.04 |
|---|---|
| ModifyDate: | 1703:11:17 21:00:00+00:00 |
| ArchivedFileName: | tools |
Total processes
177
Monitored processes
53
Malicious processes
2
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 132 | "powershell" -Command "Add-MpPreference -ExclusionExtension '.exe'" | C:\Windows\SysWOW64\WindowsPowerShell\v1.0\powershell.exe | — | CouitaTools.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows PowerShell Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 672 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=unzip.mojom.Unzipper --lang=en-US --service-sandbox-type=service --no-appcompat-clear --mojo-platform-channel-handle=5352 --field-trial-handle=2384,i,11621624947685144128,16744291792170011463,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 976 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=chrome.mojom.UtilWin --lang=en-US --service-sandbox-type=none --no-appcompat-clear --mojo-platform-channel-handle=6100 --field-trial-handle=2384,i,11621624947685144128,16744291792170011463,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 1240 | "C:\Users\admin\Desktop\CouitaToolsPro2.04\CouitaTools.exe" | C:\Users\admin\Desktop\CouitaToolsPro2.04\CouitaTools.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Version: 1.0.0.0 Modules
| |||||||||||||||
| 1276 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=crashpad-handler "--user-data-dir=C:\Users\admin\AppData\Local\Microsoft\Edge\User Data" /prefetch:4 --monitor-self-annotation=ptype=crashpad-handler "--database=C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Crashpad" --annotation=IsOfficialBuild=1 --annotation=channel= --annotation=chromium-version=122.0.6261.70 "--annotation=exe=C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --annotation=plat=Win64 "--annotation=prod=Microsoft Edge" --annotation=ver=122.0.2365.59 --initial-client-data=0x310,0x314,0x318,0x308,0x320,0x7ffc897f5fd8,0x7ffc897f5fe4,0x7ffc897f5ff0 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
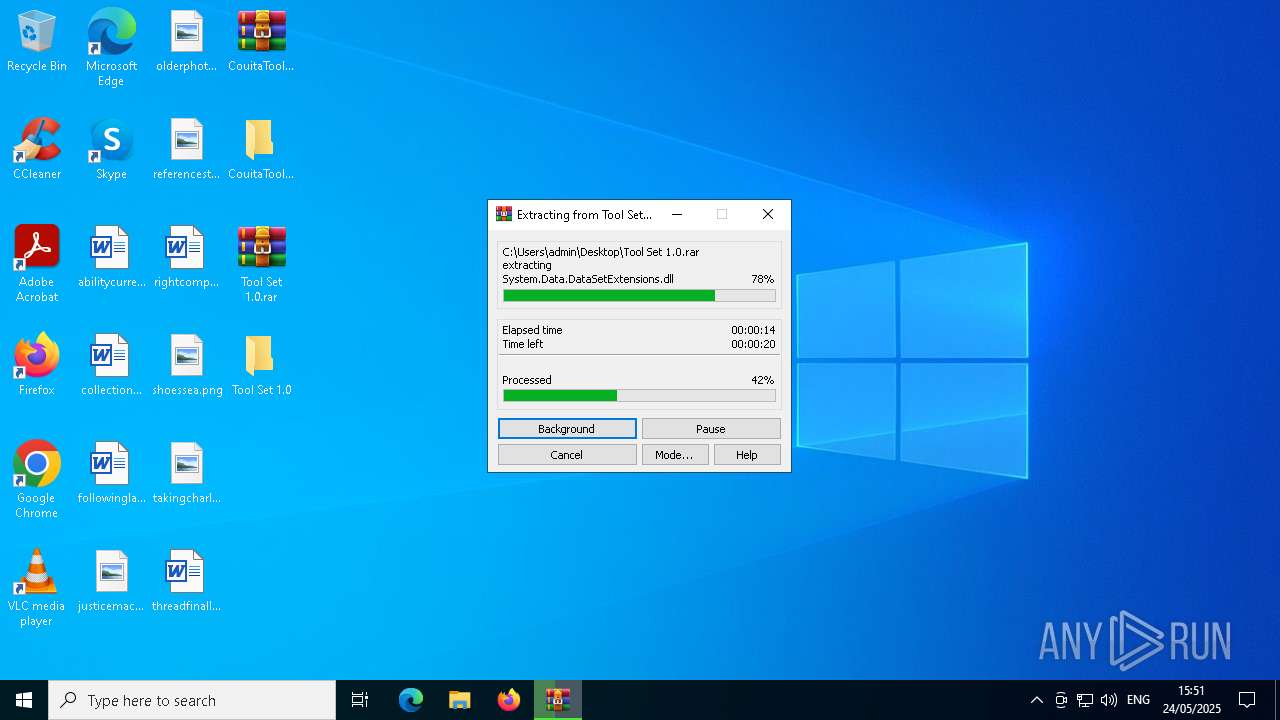
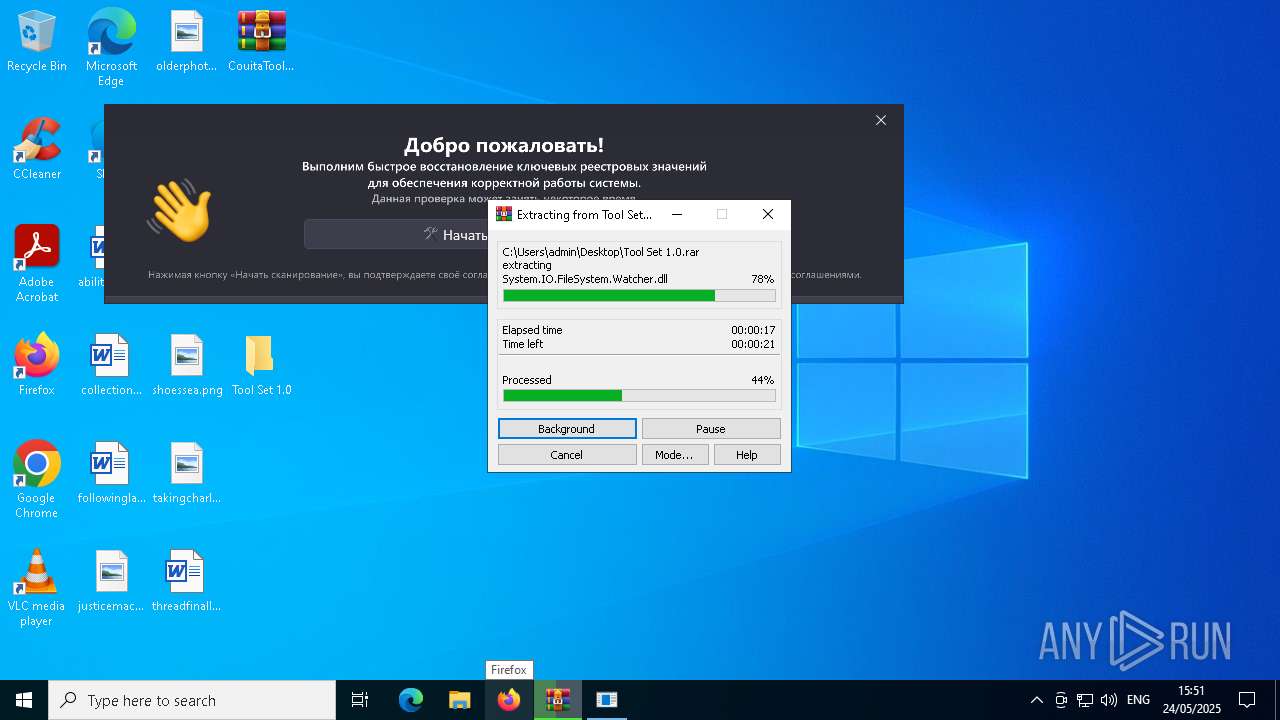
| 1348 | "C:\Program Files\WinRAR\WinRAR.exe" x -iext -ow -ver -- "C:\Users\admin\Desktop\Tool Set 1.0.rar" "C:\Users\admin\Desktop\Tool Set 1.0\" | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
| 1568 | C:\WINDOWS\System32\rundll32.exe C:\WINDOWS\System32\shell32.dll,SHCreateLocalServerRunDll {9aa46009-3ce0-458a-a354-715610a075e6} -Embedding | C:\Windows\System32\rundll32.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1852 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=gpu-process --no-appcompat-clear --gpu-preferences=WAAAAAAAAADgAAAMAAAAAAAAAAAAAAAAAABgAAAAAAA4AAAAAAAAAAAAAAAEAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAGAAAAAAAAAAYAAAAAAAAAAgAAAAAAAAACAAAAAAAAAAIAAAAAAAAAA== --mojo-platform-channel-handle=2380 --field-trial-handle=2384,i,11621624947685144128,16744291792170011463,262144 --variations-seed-version /prefetch:2 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Version: 122.0.2365.59 Modules
| |||||||||||||||
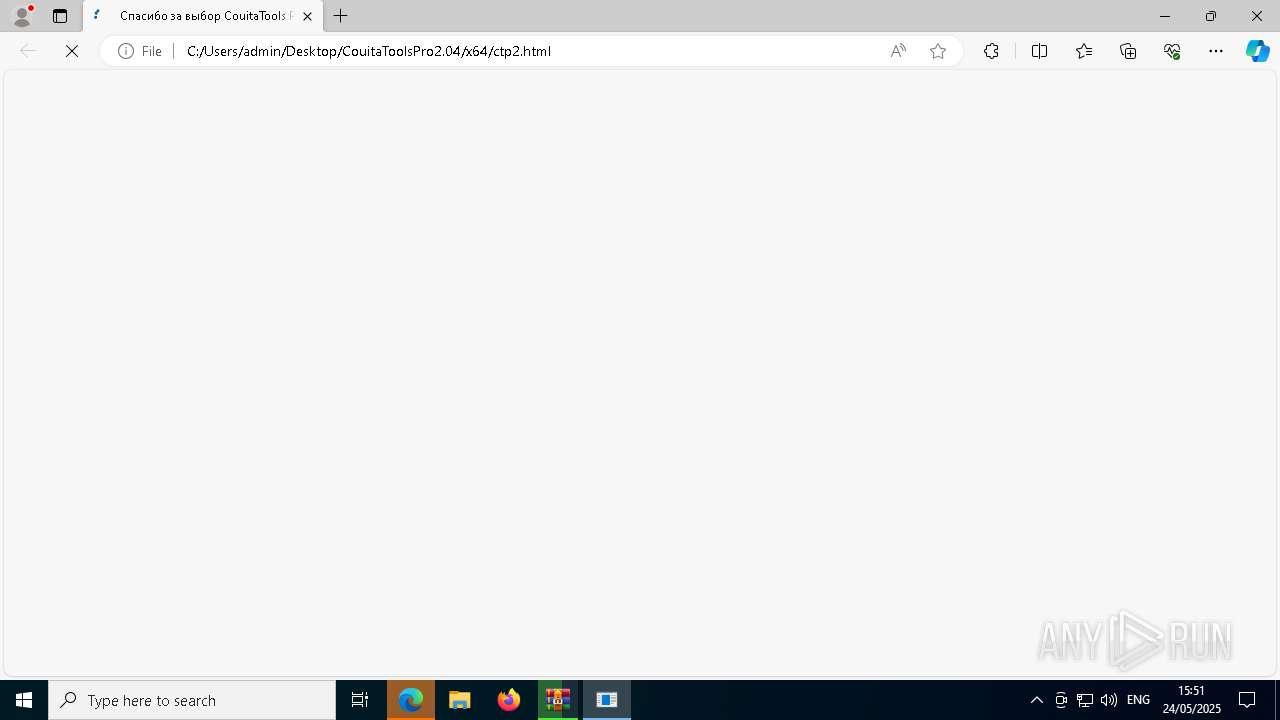
| 2192 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --flag-switches-begin --flag-switches-end --do-not-de-elevate --single-argument C:\Users\admin\Desktop\CouitaToolsPro2.04\x64\ctp2.html | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Edge Version: 122.0.2365.59 Modules
| |||||||||||||||
| 2332 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=crashpad-handler "--user-data-dir=C:\Users\admin\AppData\Local\Microsoft\Edge\User Data" /prefetch:4 --monitor-self-annotation=ptype=crashpad-handler "--database=C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Crashpad" --annotation=IsOfficialBuild=1 --annotation=channel= --annotation=chromium-version=122.0.6261.70 "--annotation=exe=C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --annotation=plat=Win64 "--annotation=prod=Microsoft Edge" --annotation=ver=122.0.2365.59 --initial-client-data=0x1d0,0x16c,0x178,0x298,0x2a0,0x7ffc897f5fd8,0x7ffc897f5fe4,0x7ffc897f5ff0 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Edge Version: 122.0.2365.59 Modules
| |||||||||||||||
Total events
45 212
Read events
44 996
Write events
205
Delete events
11
Modification events
| (PID) Process: | (5064) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\preferences.zip | |||
| (PID) Process: | (5064) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\chromium_ext.zip | |||
| (PID) Process: | (5064) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
| (PID) Process: | (5064) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\CouitaToolsPro2.04.7z | |||
| (PID) Process: | (5064) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (5064) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (5064) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (5064) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (5064) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface\MainWin |
| Operation: | write | Name: | Placement |
Value: 2C0000000000000001000000FFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFF3D0000002D000000FD03000016020000 | |||
| (PID) Process: | (5064) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\ArcColumnWidths |
| Operation: | write | Name: | name |
Value: 256 | |||
Executable files
903
Suspicious files
144
Text files
80
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 5968 | WinRAR.exe | C:\Users\admin\Desktop\CouitaToolsPro2.04\x64\activity.svg | image | |
MD5:E767FA57EAC1DE6866E38492483052AC | SHA256:F43DF660E619A7E163D14258B2CC4A0EC71AA85A99404A813AD0E3537A5B2D6F | |||
| 5968 | WinRAR.exe | C:\Users\admin\Desktop\CouitaToolsPro2.04\x64\download.svg | image | |
MD5:AE6BF304FAEA9A43BD5811B0F7BAA45B | SHA256:6119302B2C4341F168A8460B59ABB14BB9902EF7AAE063BEE969CB99E92BC0FA | |||
| 5968 | WinRAR.exe | C:\Users\admin\Desktop\CouitaToolsPro2.04\x64\ctp2.html | html | |
MD5:1E495FC233B55484BB5814B2F019B0A4 | SHA256:BDE7C04322A69F6AFB76A25E906CB725472E7ACAE7B07140CF86BEFF7936556B | |||
| 5968 | WinRAR.exe | C:\Users\admin\Desktop\CouitaToolsPro2.04\x64\delete.svg | image | |
MD5:ADF7CC21A66F00793BB8B85B4E6F97EA | SHA256:3AE20D2830F14AC764C94B28ECCE0DF440120B939F88ACE1E0F31BAA61BD4CD9 | |||
| 5968 | WinRAR.exe | C:\Users\admin\Desktop\CouitaToolsPro2.04\tools\002.exe | executable | |
MD5:36FBDDDBF5899AC7DF4E760C77486533 | SHA256:C66850426870FCA057E6BF83069CECD9900815AF462C12A3E652A29EA8F8C1E5 | |||
| 1348 | WinRAR.exe | C:\Users\admin\Desktop\Tool Set 1.0\Tool Set 1.0\dnSpy-net-win64\bin\api-ms-win-core-datetime-l1-1-0.dll | executable | |
MD5:6EA580C3387B6F526D311B8755B8B535 | SHA256:275AF628666478FABA0442CB4F2227F6F3D43561EA52ECDEC47E4CBDF5F2ABAC | |||
| 5968 | WinRAR.exe | C:\Users\admin\Desktop\CouitaToolsPro2.04\tools\777.exe | executable | |
MD5:43FE6308AE0DD4DBDE93D8DE34E83D3C | SHA256:E5B603EFAD3138900DF44735E7B430BFD1BC5E34A265C7E92C01E444E848B211 | |||
| 1348 | WinRAR.exe | C:\Users\admin\Desktop\Tool Set 1.0\Tool Set 1.0\dnSpy-net-win64\bin\api-ms-win-core-debug-l1-1-0.dll | executable | |
MD5:B826AC6E0225DB2CFB753D12B527EED3 | SHA256:40F595ADE9F60CA8630870D9122BF5EFC85C1A52AADAD4E4E5ABA3156FA868D5 | |||
| 5968 | WinRAR.exe | C:\Users\admin\Desktop\CouitaToolsPro2.04\tools\999.exe | executable | |
MD5:07F151495C65098FB635D3C95AAFC285 | SHA256:32E268B87130B7B24969718F81534BAFEC92985C2ECE6765A88C20C28C55BCA1 | |||
| 5968 | WinRAR.exe | C:\Users\admin\Desktop\CouitaToolsPro2.04\AdonisUI.ClassicTheme.dll | executable | |
MD5:8A1B183BCA062F48402C74F2DABA7B92 | SHA256:8103F2CCE6A864CEEFE6C5B0C05087AC85AB04A2ABF150E93BC9DB90C54D9D20 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
41
TCP/UDP connections
44
DNS requests
36
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | POST | 500 | 40.91.76.224:443 | https://activation-v2.sls.microsoft.com/SLActivateProduct/SLActivateProduct.asmx?configextension=Retail | unknown | xml | 512 b | whitelisted |
— | — | GET | 200 | 13.107.42.16:443 | https://config.edge.skype.com/config/v1/Edge/122.0.2365.59?clientId=4489578223053569932&agents=EdgeFirstRun%2CEdgeFirstRunConfig&osname=win&client=edge&channel=stable&scpfre=0&osarch=x86_64&osver=10.0.19045&wu=1&devicefamily=desktop&uma=0&sessionid=44&mngd=0&installdate=1661339457&edu=0&bphint=2&soobedate=1504771245&fg=1 | unknown | binary | 768 b | whitelisted |
— | — | GET | 200 | 150.171.27.11:443 | https://edge.microsoft.com/serviceexperimentation/v3/?osname=win&channel=stable&osver=10.0.19045&devicefamily=desktop&installdate=1661339457&clientversion=122.0.2365.59&experimentationmode=2&scpguard=0&scpfull=0&scpver=0 | unknown | binary | 431 b | whitelisted |
— | — | GET | 200 | 142.250.185.170:443 | https://fonts.googleapis.com/css2?family=Montserrat:wght@400;600&display=swap | unknown | text | 3.69 Kb | whitelisted |
— | — | GET | 503 | 13.107.6.158:443 | https://business.bing.com/api/v1/user/token/microsoftgraph?&clienttype=edge-omnibox | unknown | html | 13.7 Kb | whitelisted |
— | — | GET | 503 | 13.107.6.158:443 | https://business.bing.com/work/api/v2/tenant/my/settingswithflights?&clienttype=edge-omnibox | unknown | html | 13.7 Kb | whitelisted |
— | — | GET | 503 | 13.107.6.158:443 | https://business.bing.com/api/v1/user/token/microsoftgraph?&clienttype=edge-omnibox | unknown | html | 13.7 Kb | whitelisted |
— | — | GET | 200 | 13.107.246.45:443 | https://edge-mobile-static.azureedge.net/eccp/get?settenant=edge-config&setplatform=win&setmkt=en-US&setchannel=stable | unknown | binary | 16.0 Kb | whitelisted |
— | — | GET | 200 | 13.107.42.16:443 | https://config.edge.skype.com/config/v1/Edge/122.0.2365.59?clientId=4489578223053569932&agents=Edge%2CEdgeConfig%2CEdgeServices%2CEdgeFirstRun%2CEdgeFirstRunConfig&osname=win&client=edge&channel=stable&scpfre=0&osarch=x86_64&osver=10.0.19045&wu=1&devicefamily=desktop&uma=0&sessionid=44&mngd=0&installdate=1661339457&edu=0&bphint=2&soobedate=1504771245&fg=1 | unknown | binary | 9.11 Kb | whitelisted |
— | — | GET | 503 | 13.107.6.158:443 | https://business.bing.com/api/v1/user/token/microsoftgraph?&clienttype=edge-omnibox | unknown | html | 13.7 Kb | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
— | — | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4896 | slui.exe | 40.91.76.224:443 | activation-v2.sls.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
4996 | msedge.exe | 13.107.42.16:443 | config.edge.skype.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
4996 | msedge.exe | 150.171.28.11:443 | edge.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
2192 | msedge.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
4996 | msedge.exe | 142.250.185.170:443 | fonts.googleapis.com | GOOGLE | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
activation-v2.sls.microsoft.com |
| whitelisted |
config.edge.skype.com |
| whitelisted |
edge.microsoft.com |
| whitelisted |
business.bing.com |
| whitelisted |
fonts.googleapis.com |
| whitelisted |
edge-mobile-static.azureedge.net |
| whitelisted |
fonts.gstatic.com |
| whitelisted |
www.bing.com |
| whitelisted |