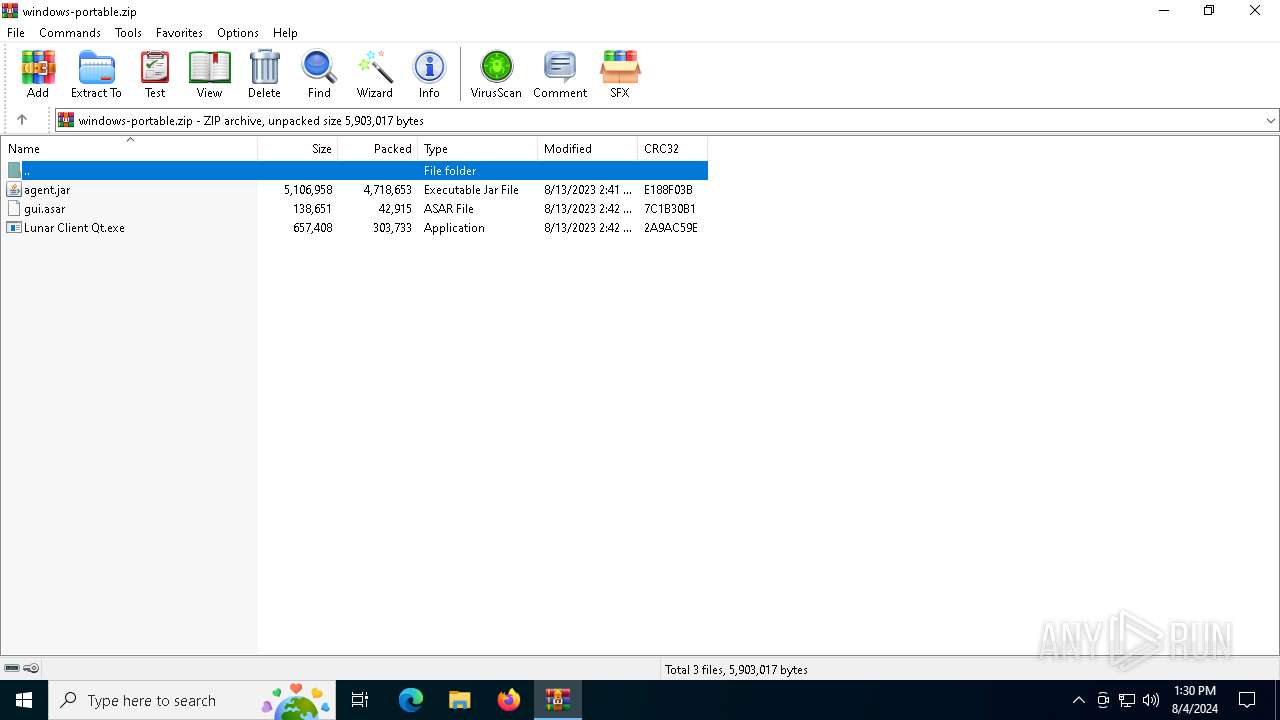
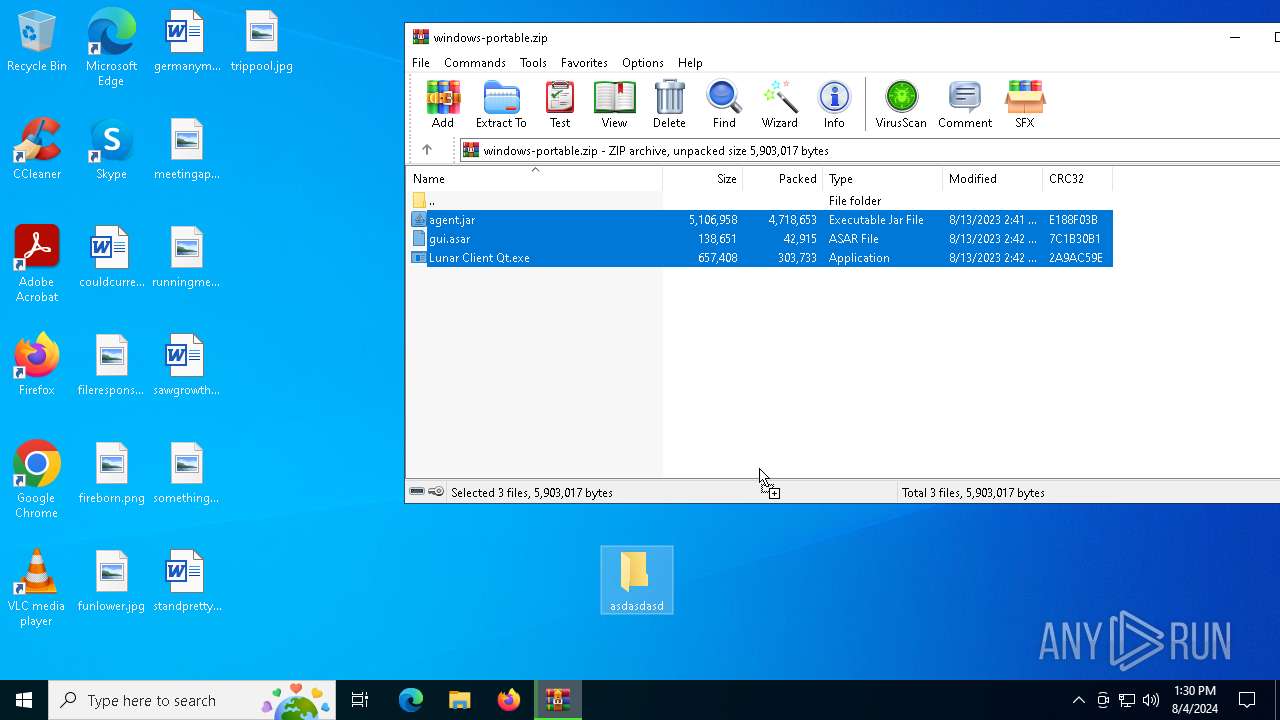
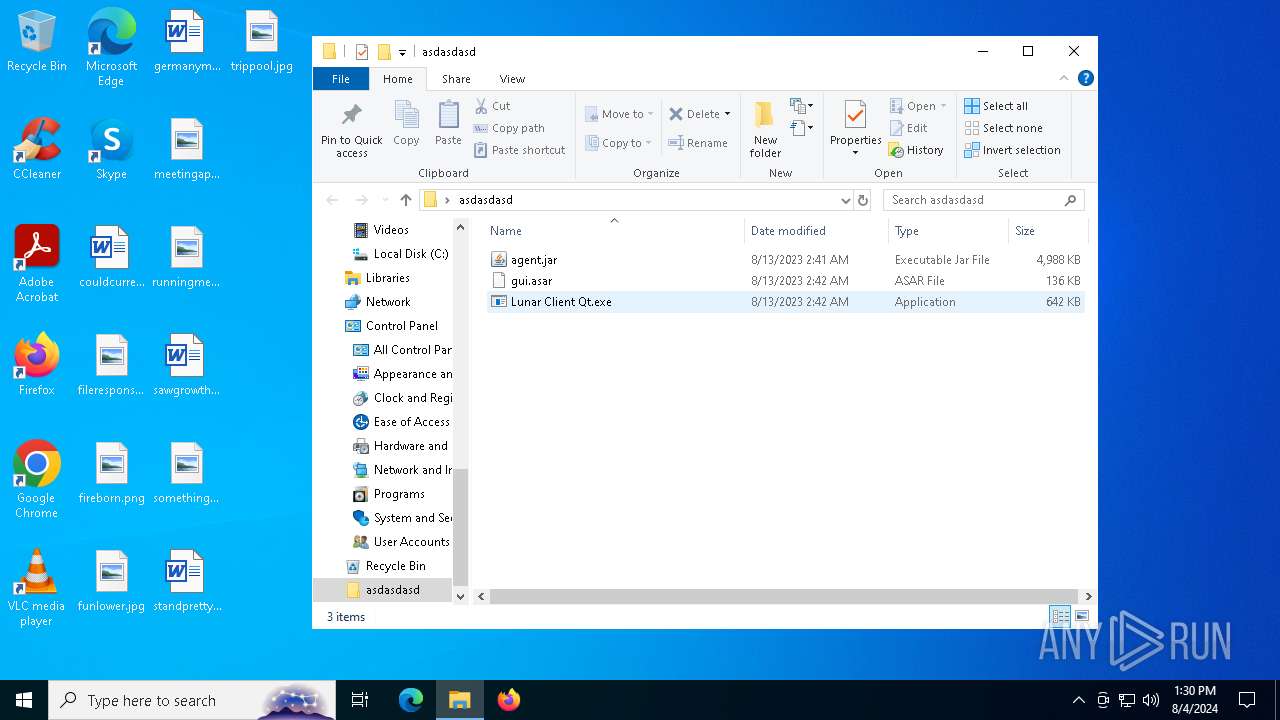
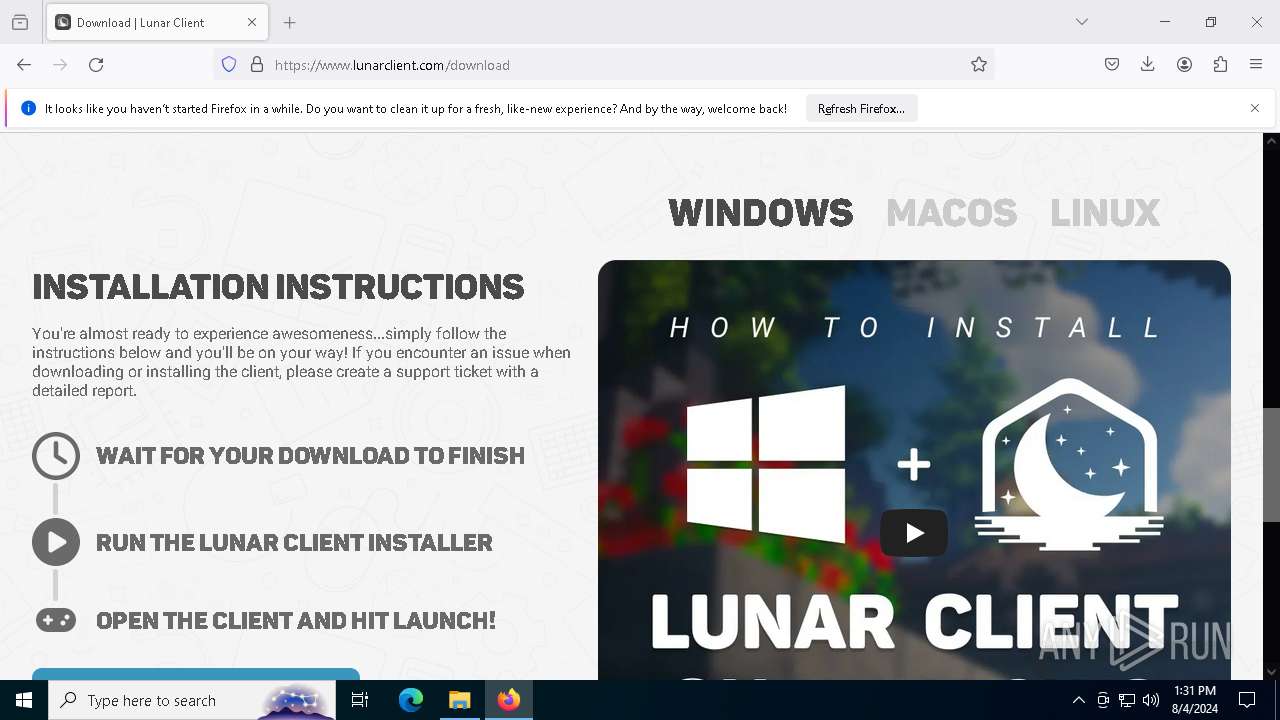
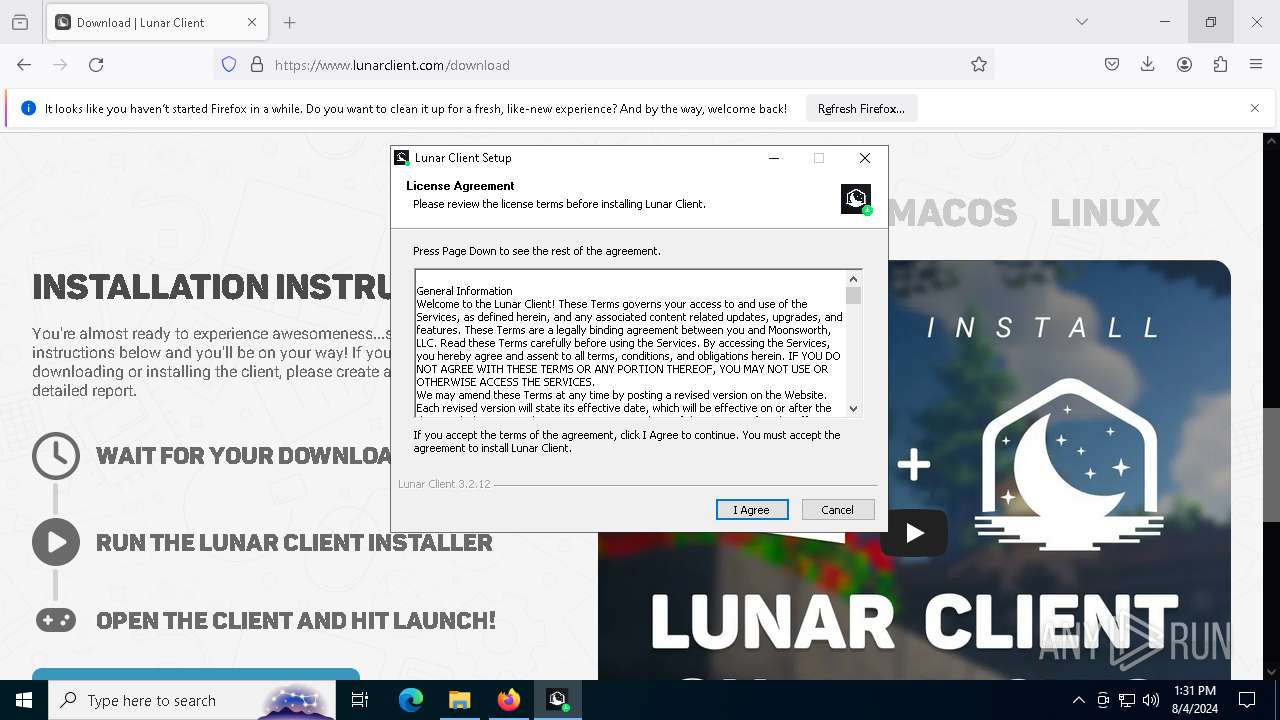
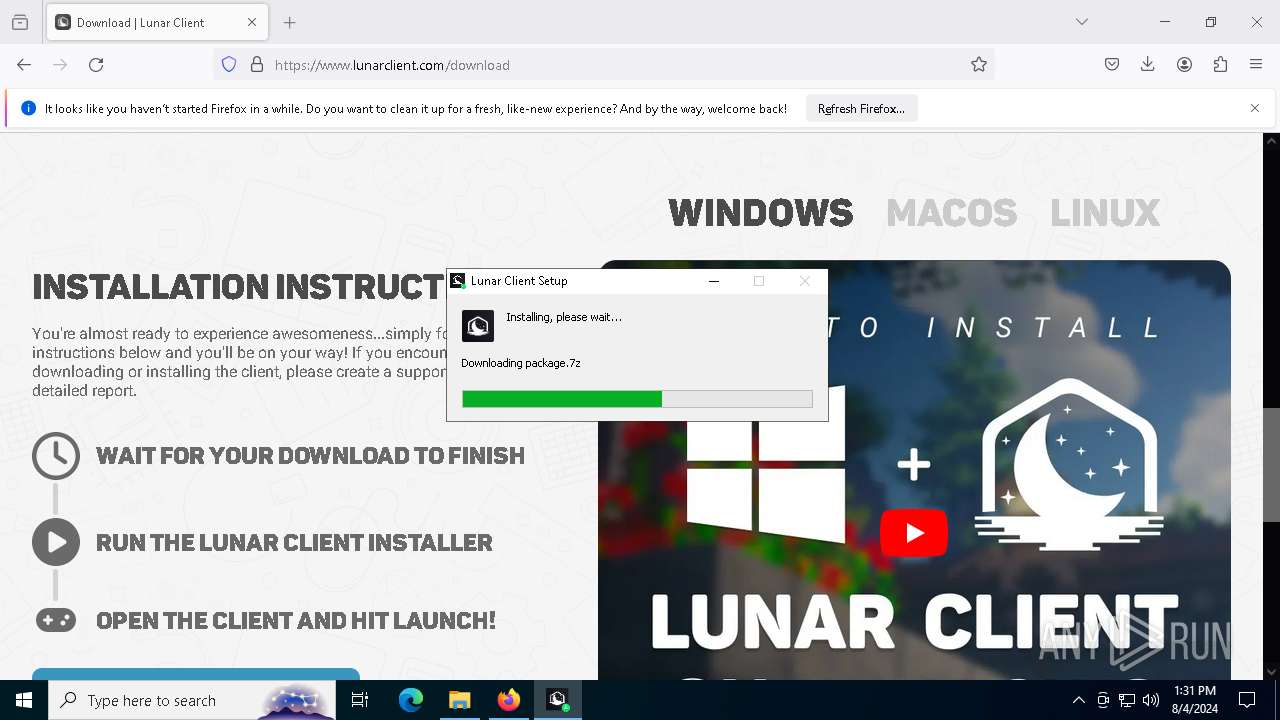
| File name: | windows-portable.zip |
| Full analysis: | https://app.any.run/tasks/8d0a32c4-fe1f-4a97-a821-fa3ad12e7ac6 |
| Verdict: | Malicious activity |
| Analysis date: | August 04, 2024, 13:30:21 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract, compression method=deflate |
| MD5: | AD3F028BBF0159F18C0ED4651F2D1F23 |
| SHA1: | E7B11C65C3D7FECF803889A7A234767DABE1C38D |
| SHA256: | 837FD62CC5C11816CA5302673F9C4028293E73F434E8C86FFDF2721CD65D3B59 |
| SSDEEP: | 98304:pSV90ckQ+PFr6KICznhWbwkvfbL8relM4XA35Vt2T+6304pprP2xv5fm6Y4MUhvh:Vjzn |
MALICIOUS
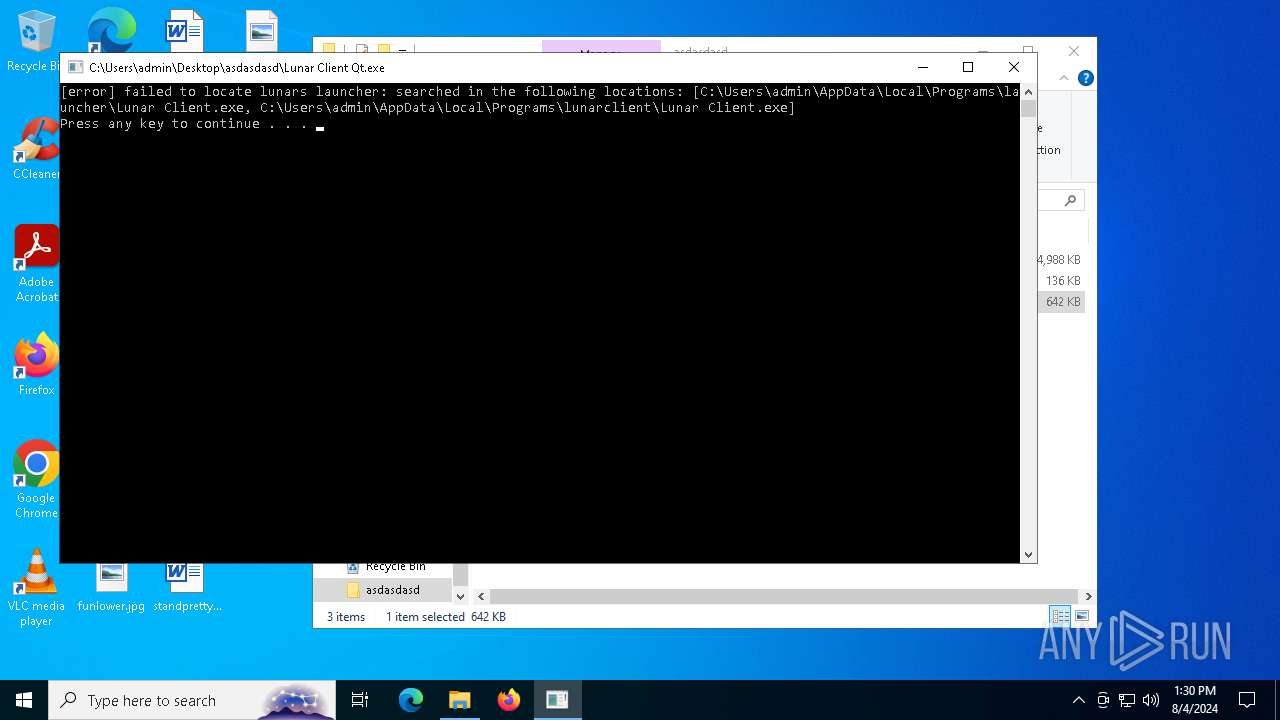
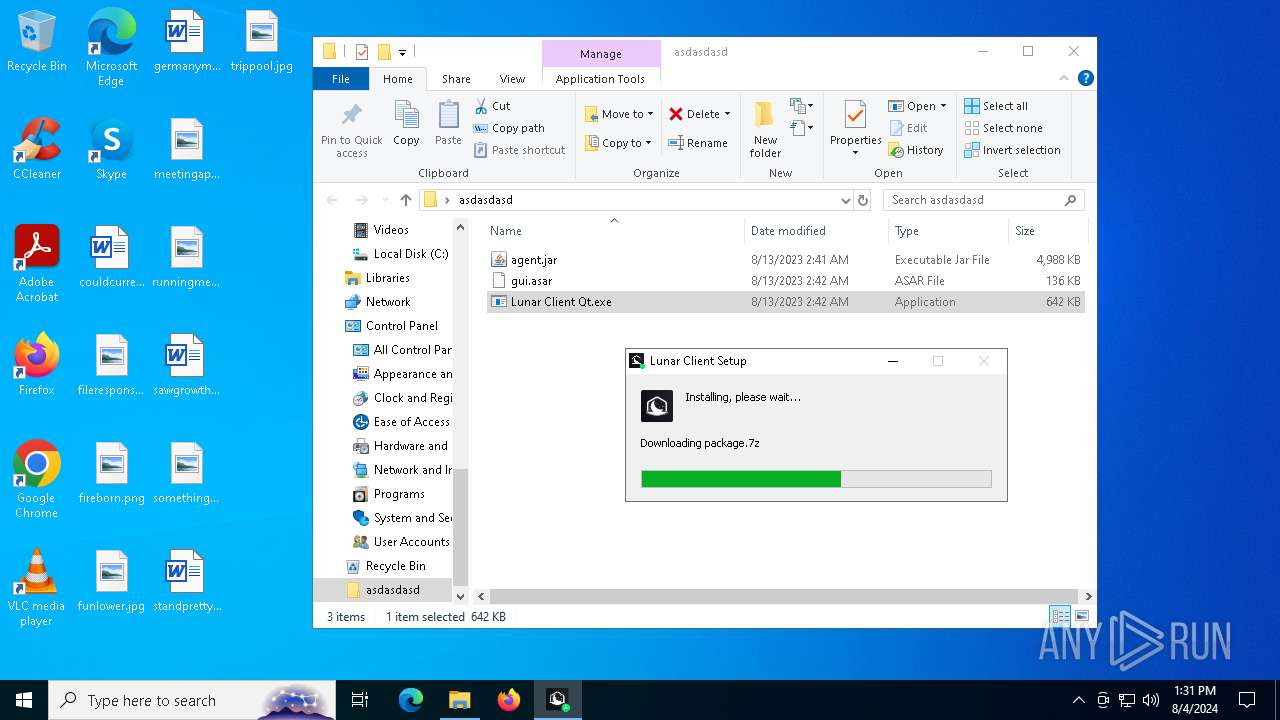
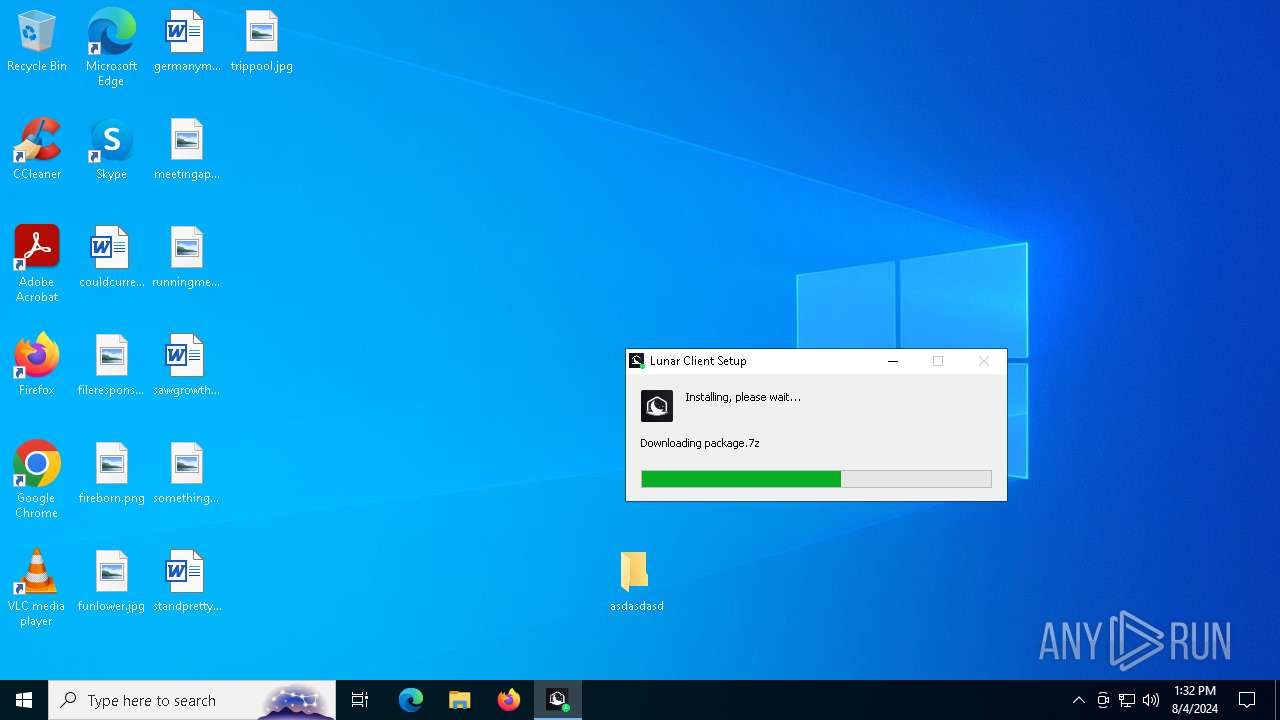
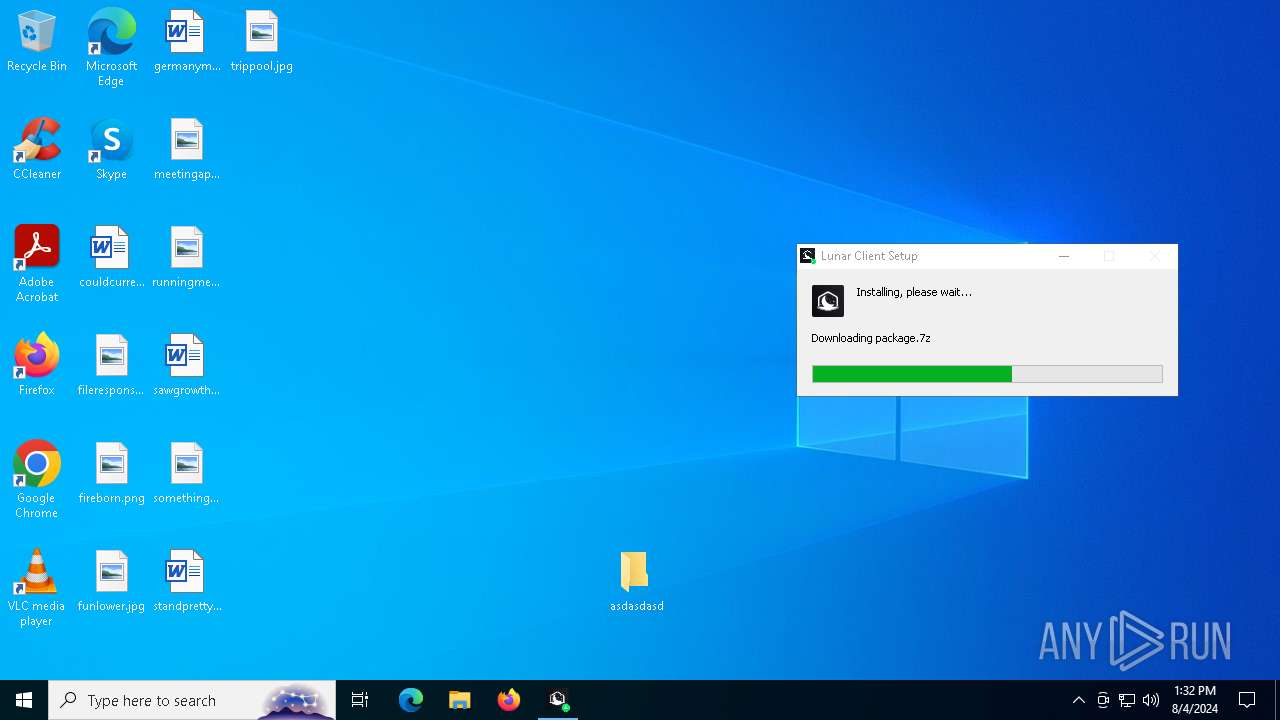
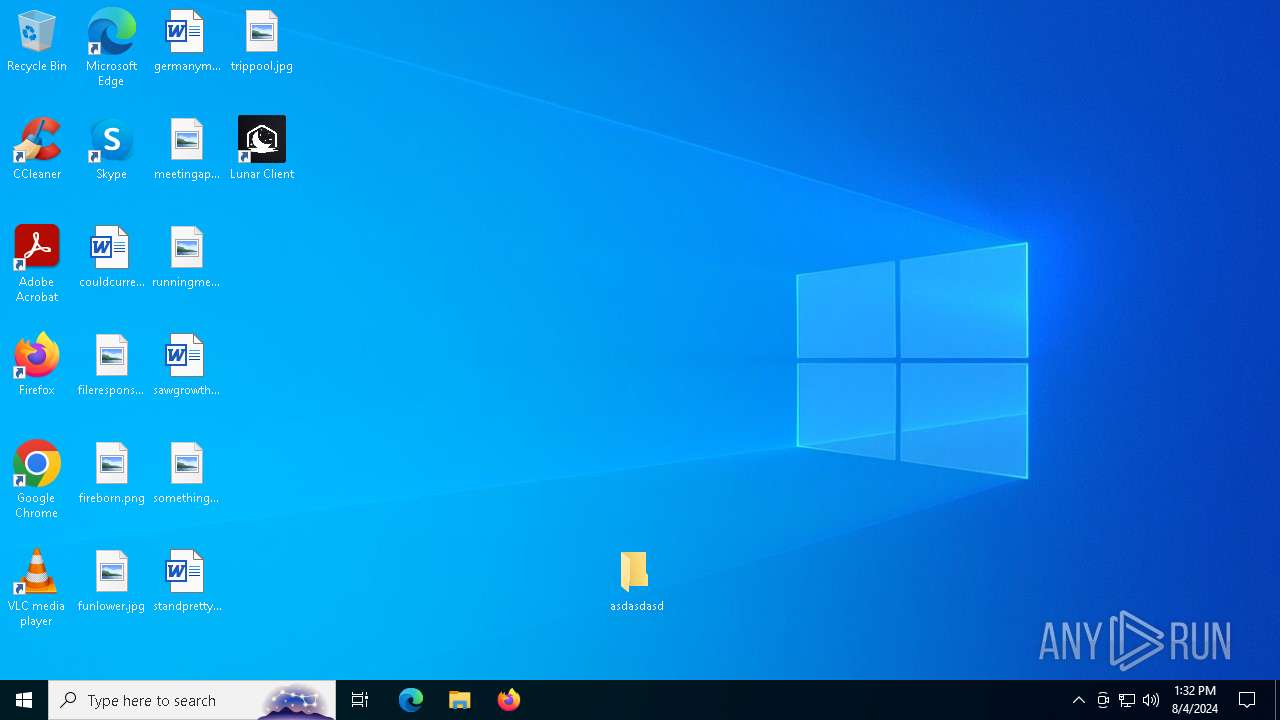
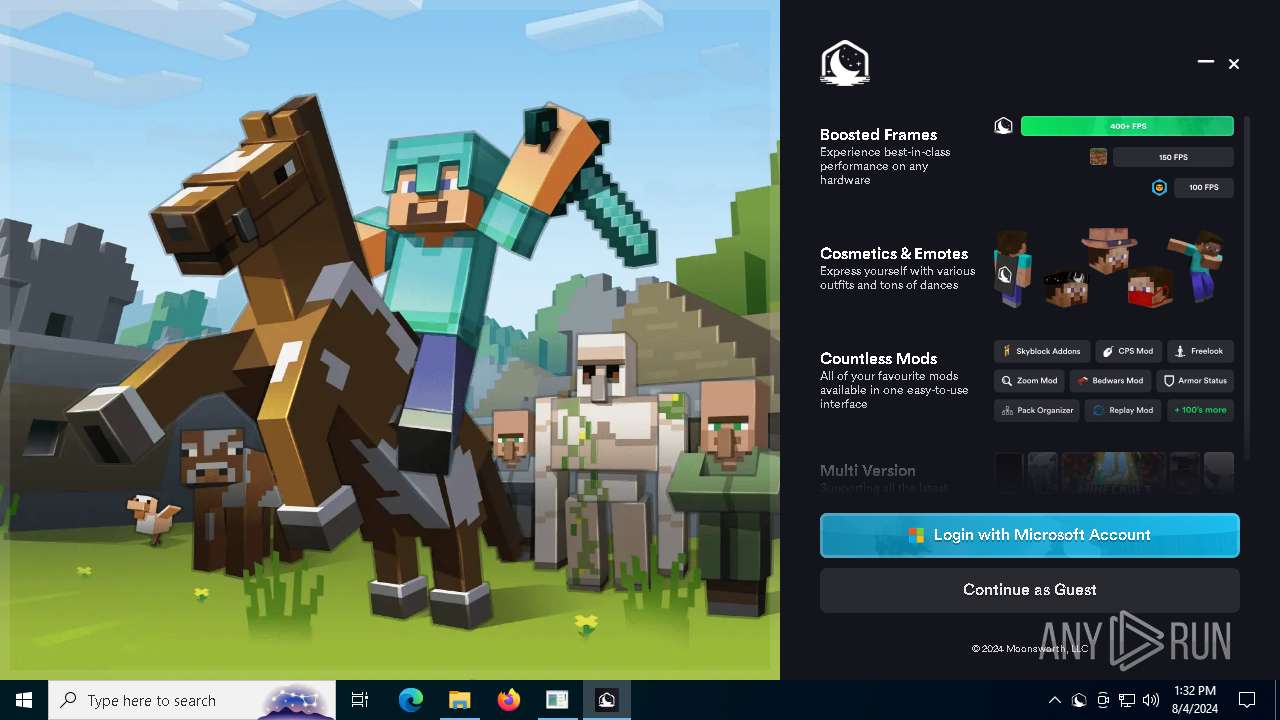
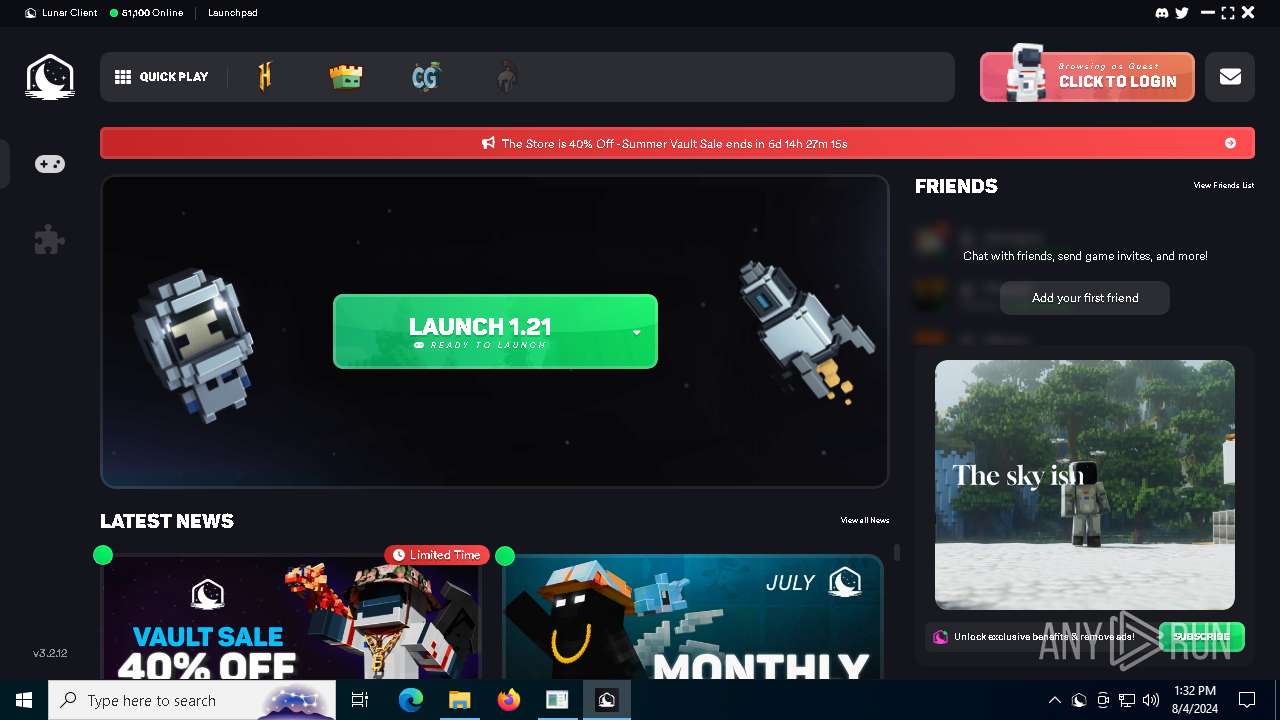
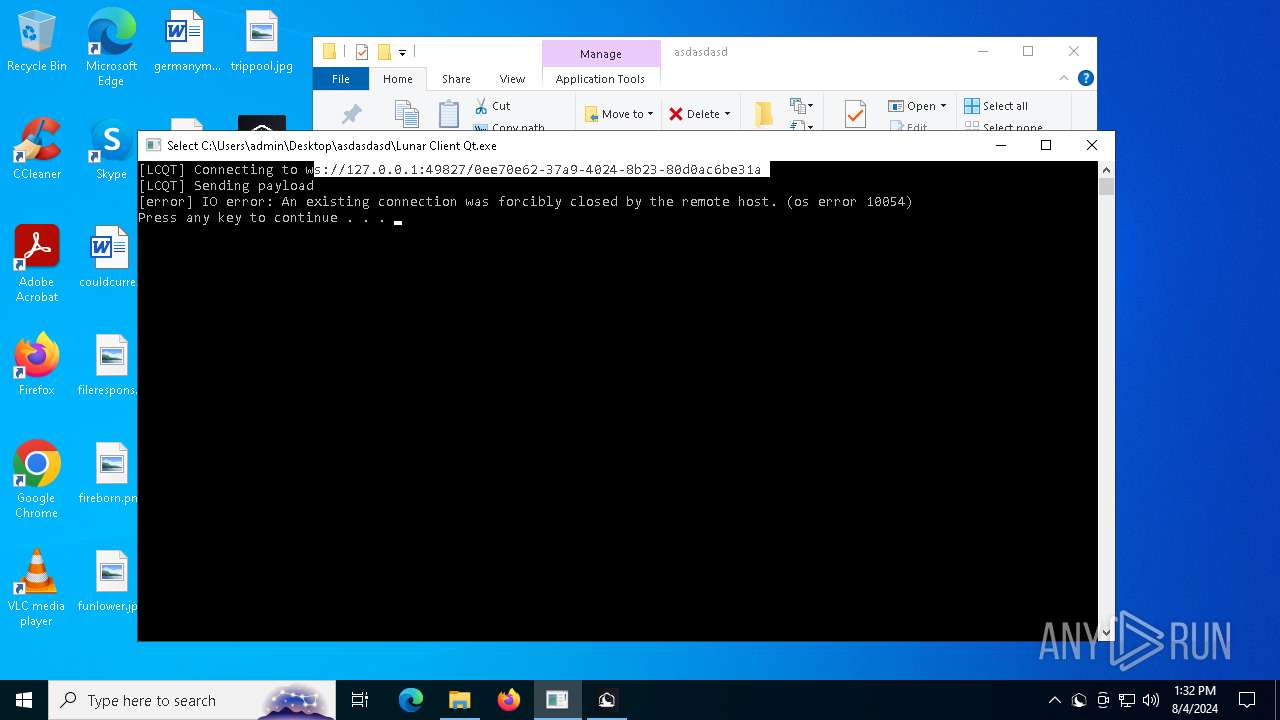
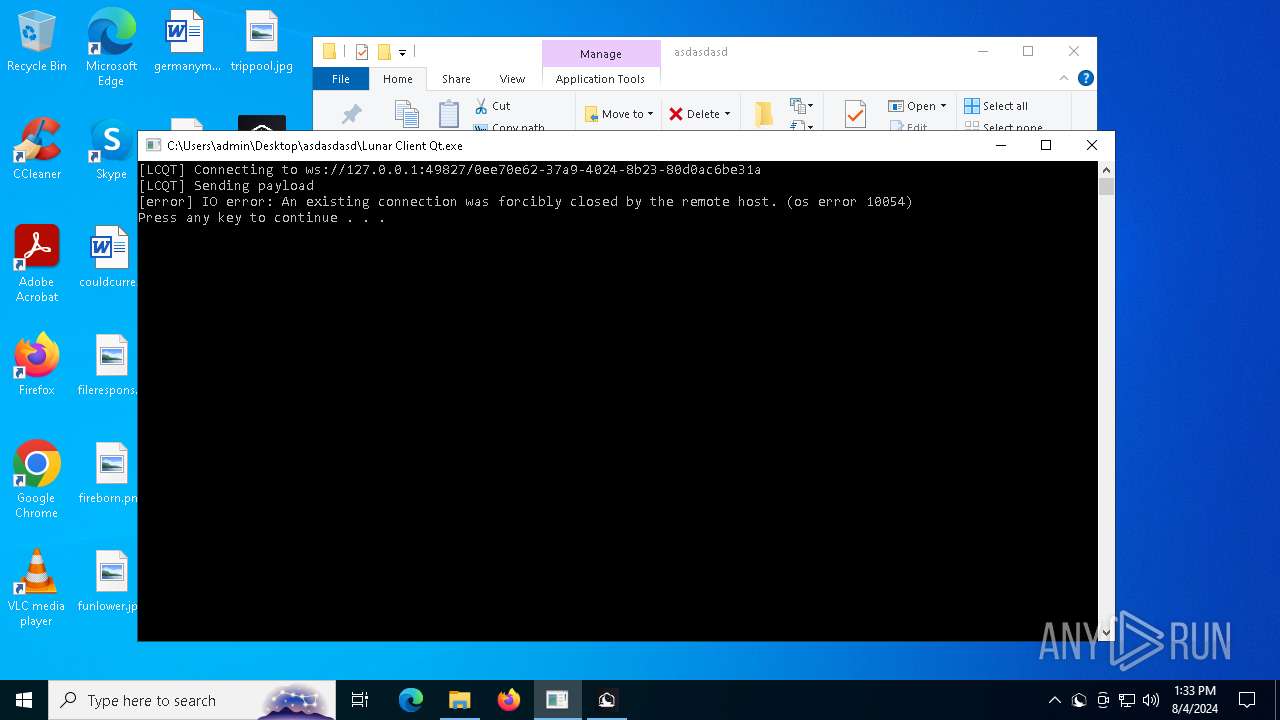
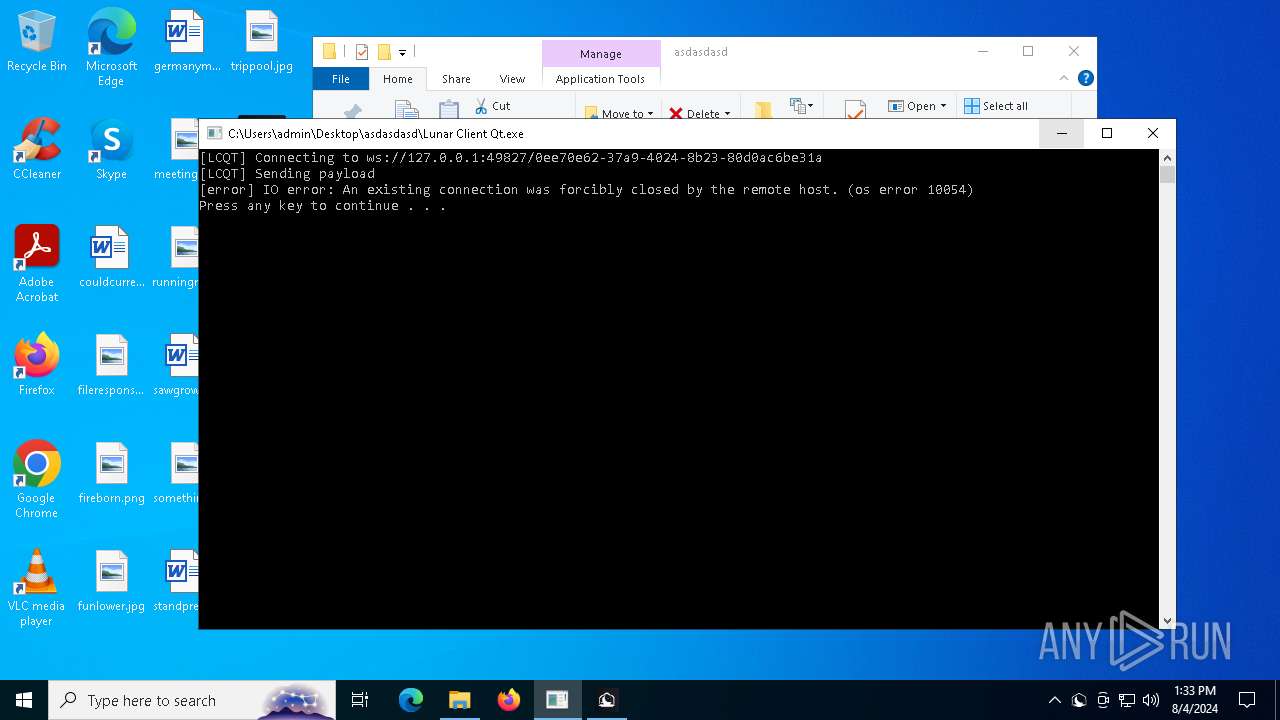
Drops the executable file immediately after the start
- WinRAR.exe (PID: 6452)
- Lunar Client v3.2.12.exe (PID: 7720)
- Lunar Client.exe (PID: 3136)
- Lunar Client.exe (PID: 8052)
Changes the autorun value in the registry
- reg.exe (PID: 7432)
SUSPICIOUS
Executable content was dropped or overwritten
- Lunar Client v3.2.12.exe (PID: 7720)
- Lunar Client.exe (PID: 3136)
- Lunar Client.exe (PID: 8052)
Malware-specific behavior (creating "System.dll" in Temp)
- Lunar Client v3.2.12.exe (PID: 7720)
The process creates files with name similar to system file names
- Lunar Client v3.2.12.exe (PID: 7720)
Reads security settings of Internet Explorer
- Lunar Client v3.2.12.exe (PID: 7720)
Checks Windows Trust Settings
- Lunar Client v3.2.12.exe (PID: 7720)
Process drops legitimate windows executable
- Lunar Client v3.2.12.exe (PID: 7720)
Creates a software uninstall entry
- Lunar Client v3.2.12.exe (PID: 7720)
Drops 7-zip archiver for unpacking
- Lunar Client v3.2.12.exe (PID: 7720)
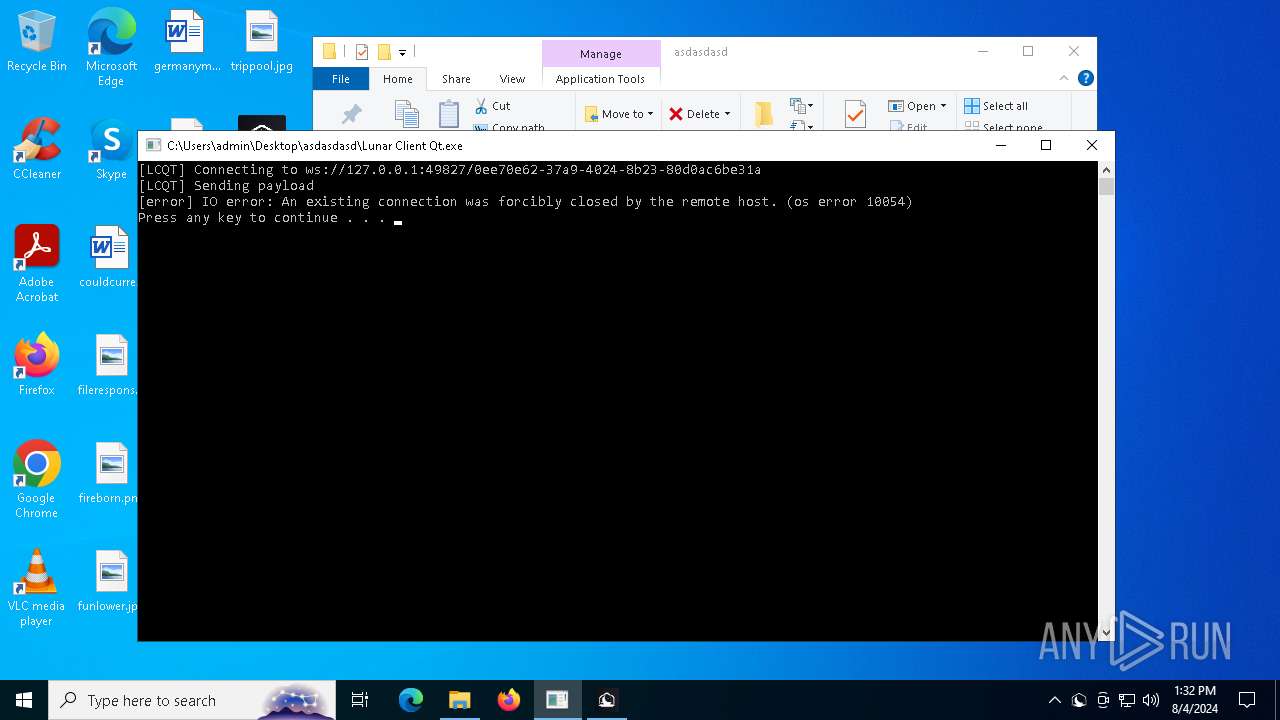
Starts CMD.EXE for commands execution
- Lunar Client Qt.exe (PID: 3700)
- Lunar Client.exe (PID: 3136)
- Lunar Client.exe (PID: 8052)
- Lunar Client Qt.exe (PID: 7464)
Starts application with an unusual extension
- cmd.exe (PID: 1236)
- cmd.exe (PID: 7692)
Application launched itself
- Lunar Client.exe (PID: 3136)
Uses REG/REGEDIT.EXE to modify registry
- Lunar Client.exe (PID: 3136)
INFO
Manual execution by a user
- Lunar Client Qt.exe (PID: 3700)
- Lunar Client.exe (PID: 3136)
- firefox.exe (PID: 5092)
- Lunar Client Qt.exe (PID: 7464)
- firefox.exe (PID: 7048)
- Taskmgr.exe (PID: 4088)
- Taskmgr.exe (PID: 7692)
Reads the computer name
- TextInputHost.exe (PID: 6728)
- Lunar Client v3.2.12.exe (PID: 7720)
- Lunar Client.exe (PID: 3136)
- Lunar Client.exe (PID: 7476)
- Lunar Client.exe (PID: 872)
- Lunar Client.exe (PID: 8052)
Checks supported languages
- Lunar Client Qt.exe (PID: 3700)
- TextInputHost.exe (PID: 6728)
- Lunar Client v3.2.12.exe (PID: 7720)
- Lunar Client.exe (PID: 3136)
- Lunar Client.exe (PID: 6592)
- Lunar Client.exe (PID: 872)
- Lunar Client.exe (PID: 7476)
- Lunar Client.exe (PID: 1680)
- Lunar Client Qt.exe (PID: 7464)
- Lunar Client.exe (PID: 8052)
- chcp.com (PID: 7292)
- chcp.com (PID: 8096)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 6452)
- firefox.exe (PID: 3140)
Application launched itself
- firefox.exe (PID: 5092)
- firefox.exe (PID: 3140)
- firefox.exe (PID: 7048)
- firefox.exe (PID: 8172)
Creates files or folders in the user directory
- Lunar Client v3.2.12.exe (PID: 7720)
- Lunar Client.exe (PID: 3136)
- Lunar Client.exe (PID: 872)
- Lunar Client.exe (PID: 6592)
Create files in a temporary directory
- Lunar Client v3.2.12.exe (PID: 7720)
- Lunar Client.exe (PID: 3136)
- Lunar Client.exe (PID: 8052)
The process uses the downloaded file
- firefox.exe (PID: 3140)
Reads the software policy settings
- Lunar Client v3.2.12.exe (PID: 7720)
Checks proxy server information
- Lunar Client v3.2.12.exe (PID: 7720)
- Lunar Client.exe (PID: 3136)
Reads the machine GUID from the registry
- Lunar Client v3.2.12.exe (PID: 7720)
- Lunar Client.exe (PID: 3136)
Reads Environment values
- Lunar Client.exe (PID: 3136)
- Lunar Client.exe (PID: 8052)
Reads product name
- Lunar Client.exe (PID: 3136)
- Lunar Client.exe (PID: 8052)
Drops the executable file immediately after the start
- firefox.exe (PID: 3140)
Process checks computer location settings
- Lunar Client.exe (PID: 3136)
- Lunar Client.exe (PID: 1680)
- Lunar Client.exe (PID: 8052)
Reads Microsoft Office registry keys
- firefox.exe (PID: 3140)
- firefox.exe (PID: 8172)
Reads security settings of Internet Explorer
- Taskmgr.exe (PID: 7692)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | 0x0800 |
| ZipCompression: | Deflated |
| ZipModifyDate: | 2023:08:13 02:41:44 |
| ZipCRC: | 0xe188f03b |
| ZipCompressedSize: | 4718653 |
| ZipUncompressedSize: | 5106958 |
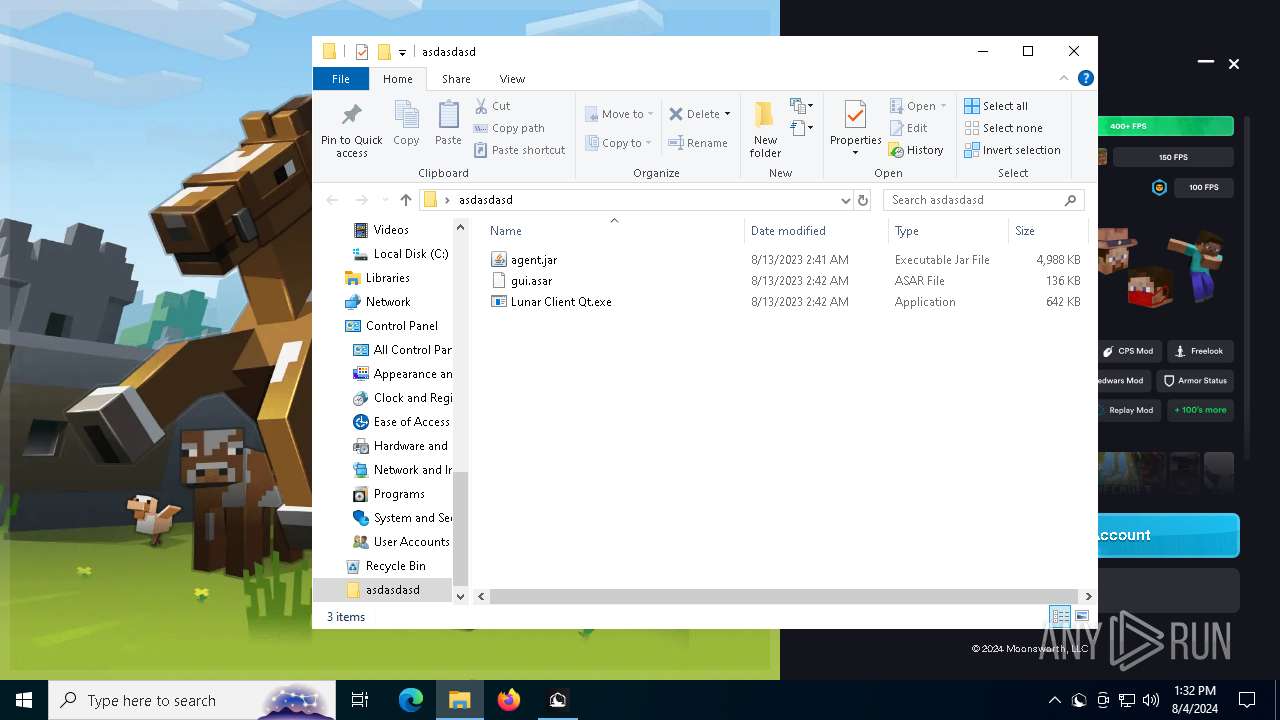
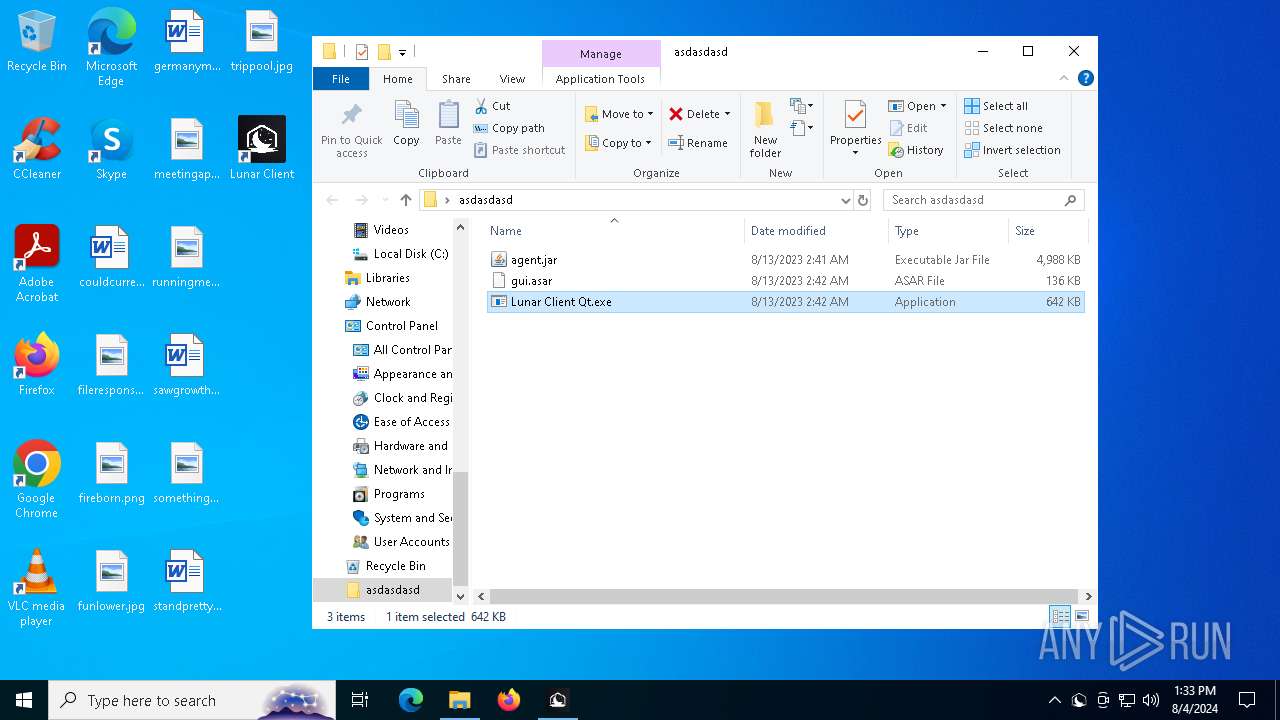
| ZipFileName: | agent.jar |
Total processes
191
Monitored processes
52
Malicious processes
5
Suspicious processes
2
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 872 | "C:\Users\admin\AppData\Local\Programs\lunarclient\Lunar Client.exe" --type=utility --utility-sub-type=network.mojom.NetworkService --lang=en-US --service-sandbox-type=none --user-data-dir="C:\Users\admin\AppData\Roaming\lunarclient" --secure-schemes=sentry-ipc --bypasscsp-schemes=sentry-ipc --cors-schemes=sentry-ipc --fetch-schemes=sentry-ipc --mojo-platform-channel-handle=2100 --field-trial-handle=1868,i,16325667773092885086,10261933034411734201,262144 --enable-features=kWebSQLAccess --disable-features=SpareRendererForSitePerProcess,WinDelaySpellcheckServiceInit,WinRetrieveSuggestionsOnlyOnDemand --variations-seed-version /prefetch:8 | C:\Users\admin\AppData\Local\Programs\lunarclient\Lunar Client.exe | Lunar Client.exe | ||||||||||||
User: admin Company: Moonsworth LLC Integrity Level: MEDIUM Description: Lunar Client Version: 3.2.12 Modules
| |||||||||||||||
| 1236 | C:\WINDOWS\system32\cmd.exe /d /s /c "chcp" | C:\Windows\System32\cmd.exe | — | Lunar Client.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1656 | "cmd.exe" /c pause | C:\Windows\System32\cmd.exe | — | Lunar Client Qt.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1680 | "C:\Users\admin\AppData\Local\Programs\lunarclient\Lunar Client.exe" --type=renderer --user-data-dir="C:\Users\admin\AppData\Roaming\lunarclient" --secure-schemes=sentry-ipc --bypasscsp-schemes=sentry-ipc --cors-schemes=sentry-ipc --fetch-schemes=sentry-ipc --app-user-model-id=com.moonsworth.client --app-path="C:\Users\admin\AppData\Local\Programs\lunarclient\resources\app.asar" --no-sandbox --no-zygote --first-renderer-process --lang=en-US --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=4 --mojo-platform-channel-handle=2532 --field-trial-handle=1868,i,16325667773092885086,10261933034411734201,262144 --enable-features=kWebSQLAccess --disable-features=SpareRendererForSitePerProcess,WinDelaySpellcheckServiceInit,WinRetrieveSuggestionsOnlyOnDemand --variations-seed-version /prefetch:1 | C:\Users\admin\AppData\Local\Programs\lunarclient\Lunar Client.exe | — | Lunar Client.exe | |||||||||||
User: admin Company: Moonsworth LLC Integrity Level: MEDIUM Description: Lunar Client Version: 3.2.12 Modules
| |||||||||||||||
| 1920 | "C:\Program Files\Mozilla Firefox\firefox.exe" -contentproc --channel=5752 -childID 3 -isForBrowser -prefsHandle 5744 -prefMapHandle 5748 -prefsLen 31702 -prefMapSize 244387 -jsInitHandle 1440 -jsInitLen 235124 -parentBuildID 20240213221259 -win32kLockedDown -appDir "C:\Program Files\Mozilla Firefox\browser" - {5191c858-658e-40aa-b264-45a7d2bb272b} 8172 "\\.\pipe\gecko-crash-server-pipe.8172" 212ad9224d0 tab | C:\Program Files\Mozilla Firefox\firefox.exe | — | firefox.exe | |||||||||||
User: admin Company: Mozilla Corporation Integrity Level: LOW Description: Firefox Exit code: 0 Version: 123.0 Modules
| |||||||||||||||
| 1928 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2324 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | Lunar Client Qt.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2400 | "cmd.exe" /c pause | C:\Windows\System32\cmd.exe | — | Lunar Client Qt.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 3221225786 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2508 | "C:\Program Files\Mozilla Firefox\firefox.exe" -contentproc --channel=5196 -parentBuildID 20240213221259 -sandboxingKind 0 -prefsHandle 5132 -prefMapHandle 5032 -prefsLen 35334 -prefMapSize 244387 -win32kLockedDown -appDir "C:\Program Files\Mozilla Firefox\browser" - {c817dba0-475f-4a5f-9be4-d7ba308c775a} 8172 "\\.\pipe\gecko-crash-server-pipe.8172" 212a867c510 utility | C:\Program Files\Mozilla Firefox\firefox.exe | — | firefox.exe | |||||||||||
User: admin Company: Mozilla Corporation Integrity Level: LOW Description: Firefox Exit code: 1 Version: 123.0 Modules
| |||||||||||||||
| 2632 | "C:\Program Files\Mozilla Firefox\firefox.exe" -contentproc --channel=4636 -childID 2 -isForBrowser -prefsHandle 4612 -prefMapHandle 4624 -prefsLen 35227 -prefMapSize 244387 -jsInitHandle 1440 -jsInitLen 235124 -parentBuildID 20240213221259 -win32kLockedDown -appDir "C:\Program Files\Mozilla Firefox\browser" - {d2b10425-2085-4d03-8274-278389284a70} 8172 "\\.\pipe\gecko-crash-server-pipe.8172" 212a9cf04d0 tab | C:\Program Files\Mozilla Firefox\firefox.exe | — | firefox.exe | |||||||||||
User: admin Company: Mozilla Corporation Integrity Level: LOW Description: Firefox Exit code: 0 Version: 123.0 Modules
| |||||||||||||||
Total events
48 231
Read events
48 080
Write events
130
Delete events
21
Modification events
| (PID) Process: | (6452) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (6452) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (6452) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\GoogleChromeEnterpriseBundle64.zip | |||
| (PID) Process: | (6452) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\windows-portable.zip | |||
| (PID) Process: | (6452) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (6452) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (6452) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (6452) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (6452) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface\MainWin |
| Operation: | write | Name: | Placement |
Value: 2C0000000000000001000000FFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFEB00000031000000AB0400001A020000 | |||
| (PID) Process: | (6452) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\General |
| Operation: | write | Name: | LastFolder |
Value: C:\Users\admin\AppData\Local\Temp | |||
Executable files
30
Suspicious files
458
Text files
81
Unknown types
19
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6452 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa6452.4951\gui.asar | asar | |
MD5:F9A97D77B21FBAE29581DE3A525F23BB | SHA256:C6F4CE5BEA8AC573BA120608EAF1488AEE32DC40359063833992DB9421BFCE28 | |||
| 3140 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\9kie7cg6.default-release\storage\permanent\chrome\idb\1657114595AmcateirvtiSty.sqlite-shm | binary | |
MD5:B7C14EC6110FA820CA6B65F5AEC85911 | SHA256:FD4C9FDA9CD3F9AE7C962B0DDF37232294D55580E1AA165AA06129B8549389EB | |||
| 6452 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa6452.4951\Lunar Client Qt.exe | executable | |
MD5:A0857553DFD17A66904235D9C247BDBA | SHA256:D02692720EC335FE39135D012BBE6318531DCB75B619F5B7F19D4D7C1D6D0D93 | |||
| 3140 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\9kie7cg6.default-release\storage\permanent\chrome\idb\3870112724rsegmnoittet-es.sqlite | — | |
MD5:— | SHA256:— | |||
| 3140 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\9kie7cg6.default-release\sessionCheckpoints.json | binary | |
MD5:EA8B62857DFDBD3D0BE7D7E4A954EC9A | SHA256:792955295AE9C382986222C6731C5870BD0E921E7F7E34CC4615F5CD67F225DA | |||
| 3140 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\9kie7cg6.default-release\storage\permanent\chrome\idb\3870112724rsegmnoittet-es.sqlite-shm | binary | |
MD5:B7C14EC6110FA820CA6B65F5AEC85911 | SHA256:FD4C9FDA9CD3F9AE7C962B0DDF37232294D55580E1AA165AA06129B8549389EB | |||
| 6452 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa6452.4951\agent.jar | compressed | |
MD5:3D232267E99F382AE9C4B7B3B6EA4BC7 | SHA256:927D1F9AB856F49044EA06F4C9FC3CE10BB81A10404D0583FA39EE1D9F23388E | |||
| 3140 | firefox.exe | C:\Users\admin\AppData\Local\Mozilla\Firefox\Profiles\9kie7cg6.default-release\startupCache\urlCache-current.bin | binary | |
MD5:297E88D7CEB26E549254EC875649F4EB | SHA256:8B75D4FB1845BAA06122888D11F6B65E6A36B140C54A72CC13DF390FD7C95702 | |||
| 3140 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\9kie7cg6.default-release\sessionCheckpoints.json.tmp | binary | |
MD5:EA8B62857DFDBD3D0BE7D7E4A954EC9A | SHA256:792955295AE9C382986222C6731C5870BD0E921E7F7E34CC4615F5CD67F225DA | |||
| 3140 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\9kie7cg6.default-release\prefs-1.js | text | |
MD5:913A810E4251DABCC713A58127A7E67F | SHA256:5567851FAED4B8F72F22C596CFE75F888CEC722812F80A96157340BDB4C36275 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
60
TCP/UDP connections
194
DNS requests
219
Threats
4
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
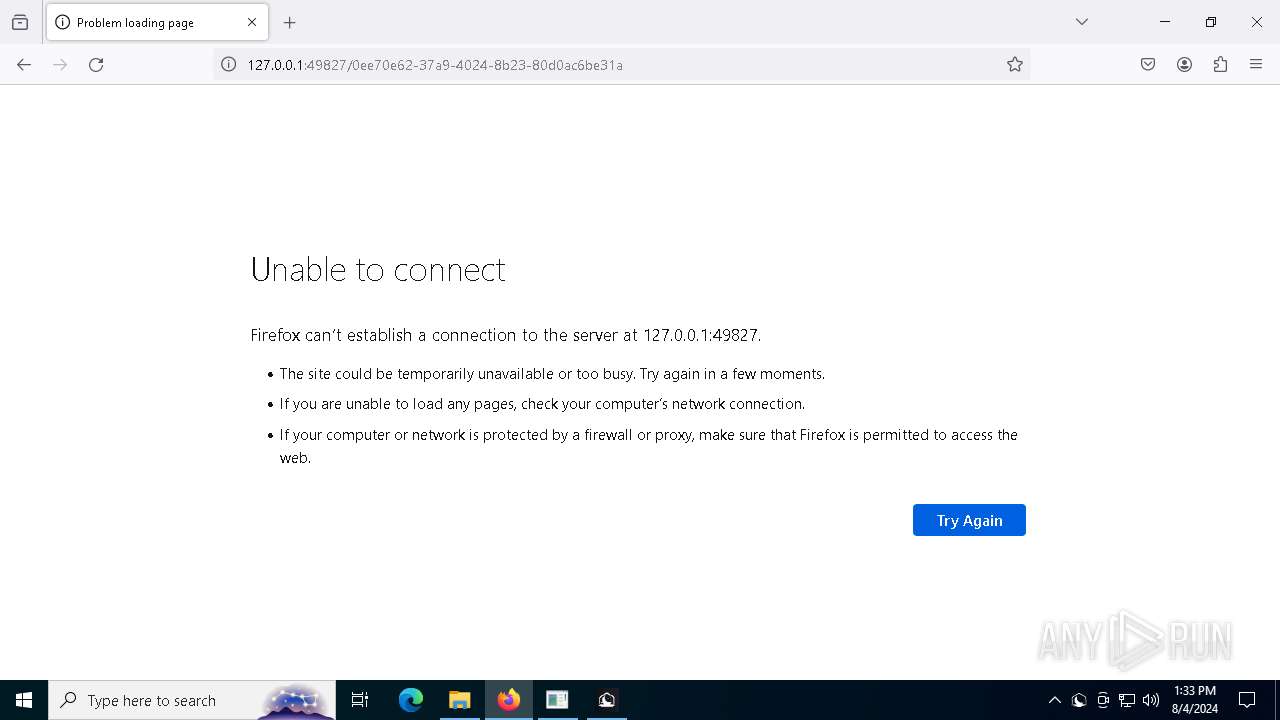
3140 | firefox.exe | GET | 200 | 34.107.221.82:80 | http://detectportal.firefox.com/success.txt?ipv4 | unknown | — | — | whitelisted |
3140 | firefox.exe | POST | 200 | 95.101.54.120:80 | http://r10.o.lencr.org/ | unknown | — | — | unknown |
3140 | firefox.exe | POST | 200 | 95.101.54.120:80 | http://r10.o.lencr.org/ | unknown | — | — | unknown |
6924 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
3140 | firefox.exe | POST | 200 | 95.101.54.120:80 | http://r10.o.lencr.org/ | unknown | — | — | unknown |
3140 | firefox.exe | POST | 200 | 142.250.185.227:80 | http://o.pki.goog/wr2 | unknown | — | — | unknown |
3140 | firefox.exe | POST | 200 | 95.101.54.120:80 | http://r10.o.lencr.org/ | unknown | — | — | unknown |
4436 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
5336 | SearchApp.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
4436 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2532 | svchost.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
4664 | RUXIMICS.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
2120 | MoUsoCoreWorker.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
3888 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
2532 | svchost.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
5336 | SearchApp.exe | 104.126.37.130:443 | www.bing.com | Akamai International B.V. | DE | unknown |
5336 | SearchApp.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
4436 | svchost.exe | 20.190.159.0:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
www.bing.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
login.live.com |
| whitelisted |
th.bing.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
fd.api.iris.microsoft.com |
| whitelisted |
arc.msn.com |
| whitelisted |
detectportal.firefox.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2256 | svchost.exe | Not Suspicious Traffic | INFO [ANY.RUN] An application monitoring request to sentry .io |
2256 | svchost.exe | Not Suspicious Traffic | INFO [ANY.RUN] An application monitoring request to sentry .io |
2256 | svchost.exe | Not Suspicious Traffic | INFO [ANY.RUN] An application monitoring request to sentry .io |
2256 | svchost.exe | Not Suspicious Traffic | INFO [ANY.RUN] An application monitoring request to sentry .io |