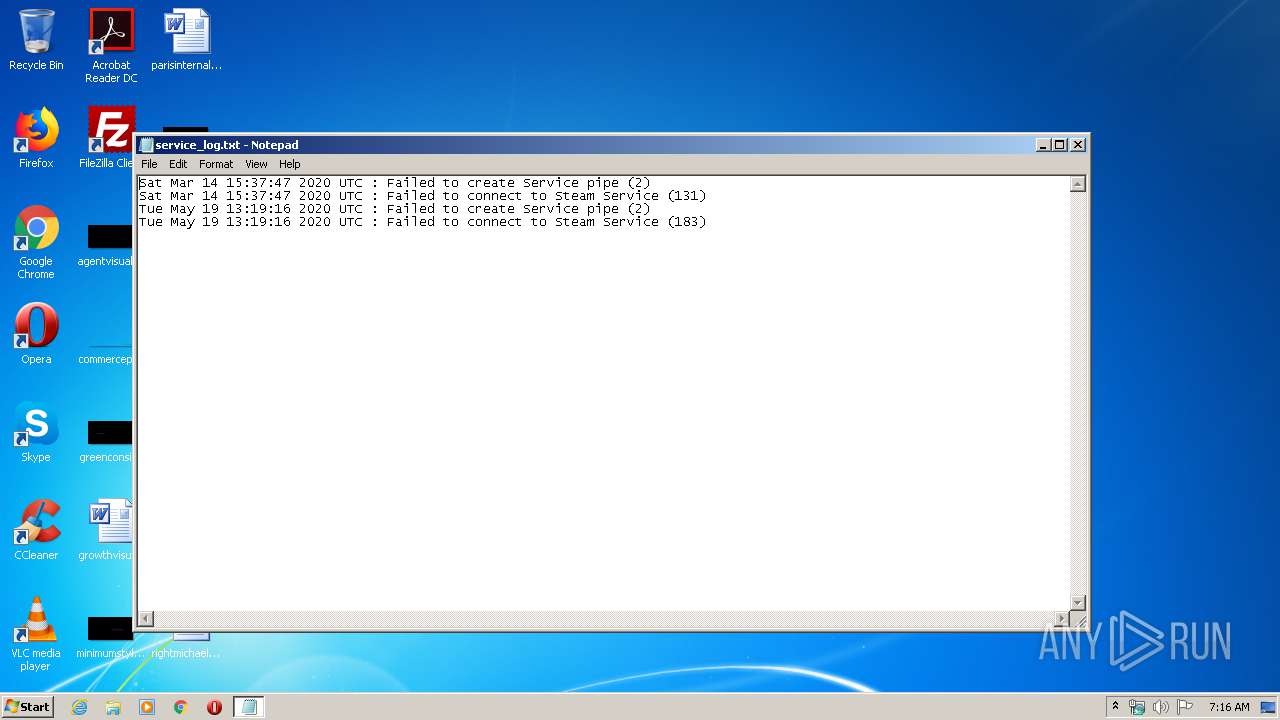
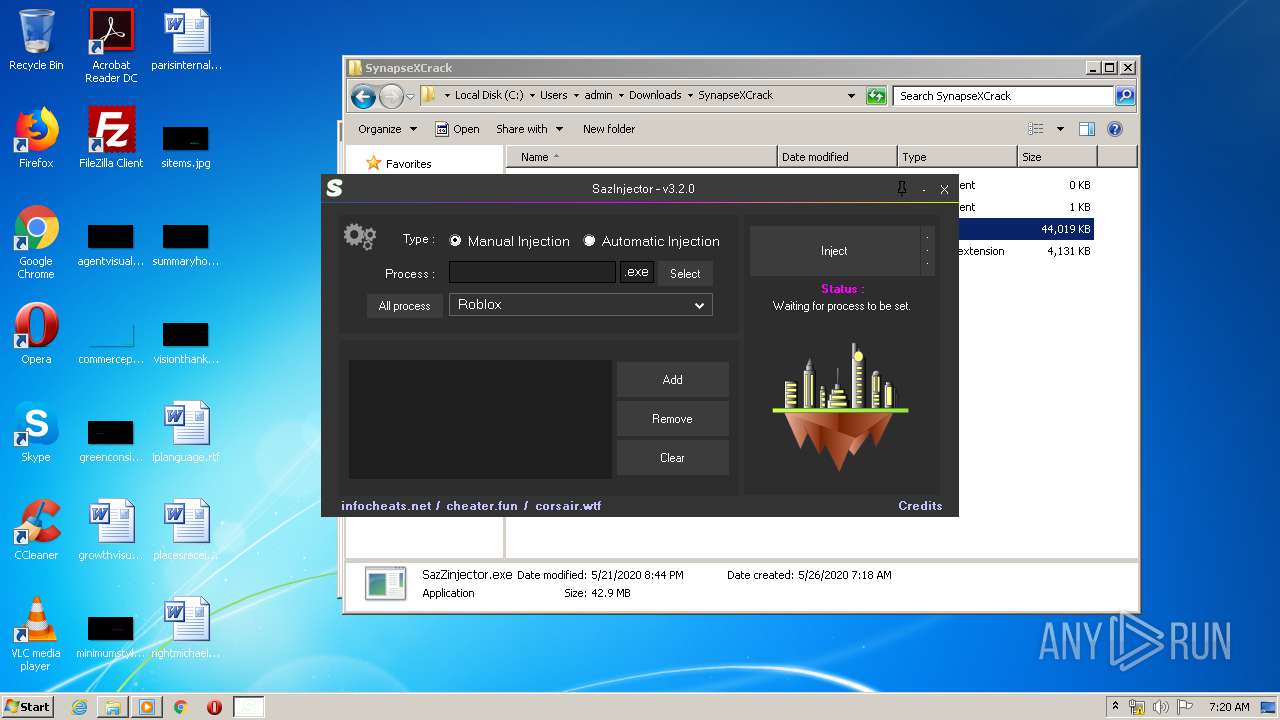
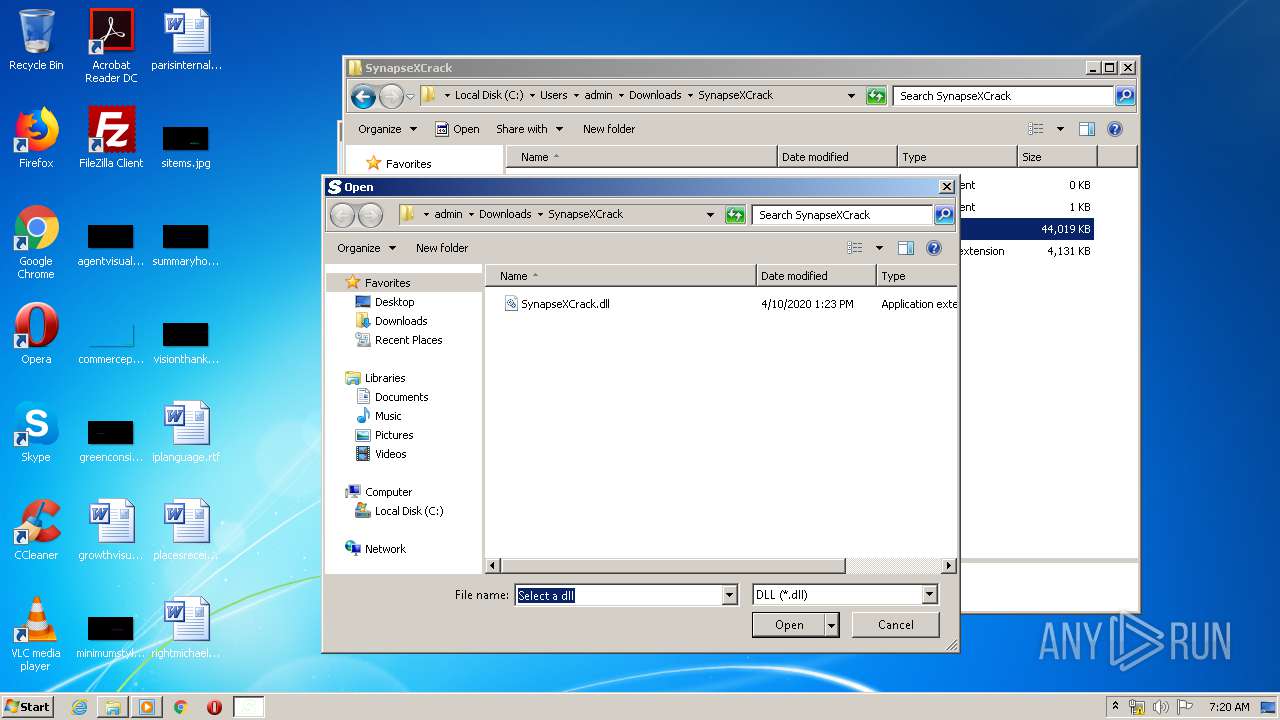
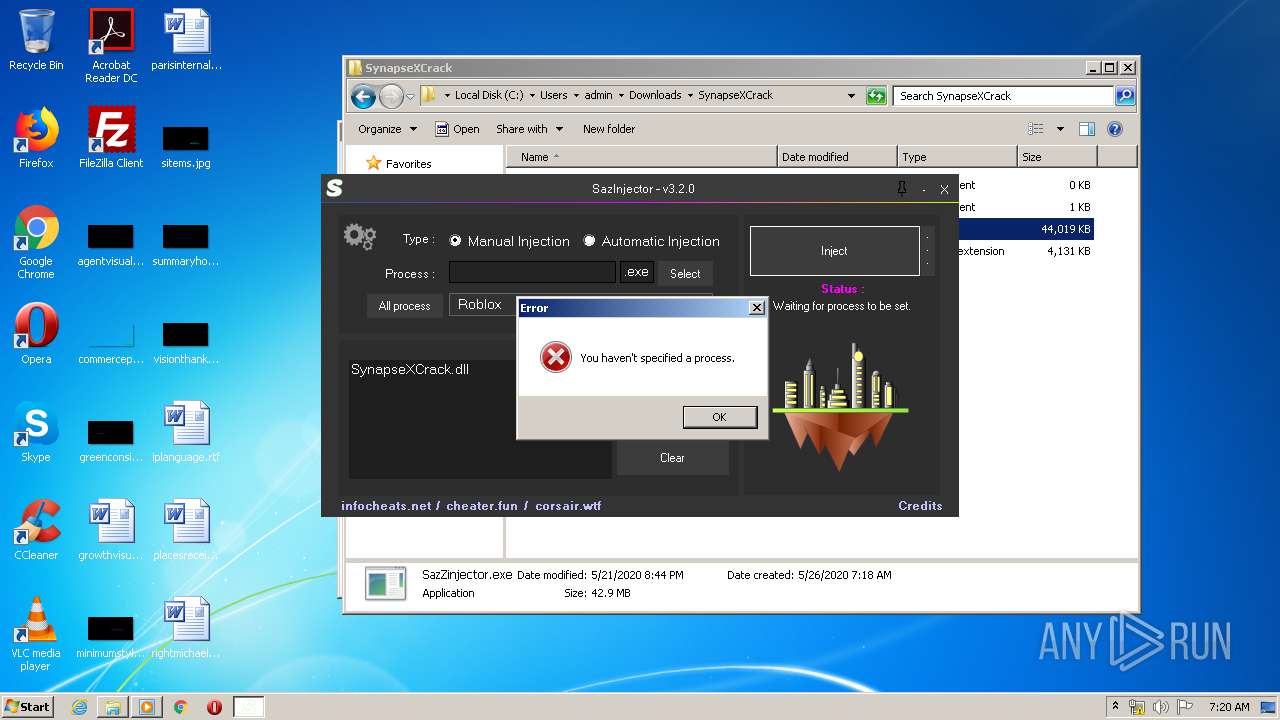
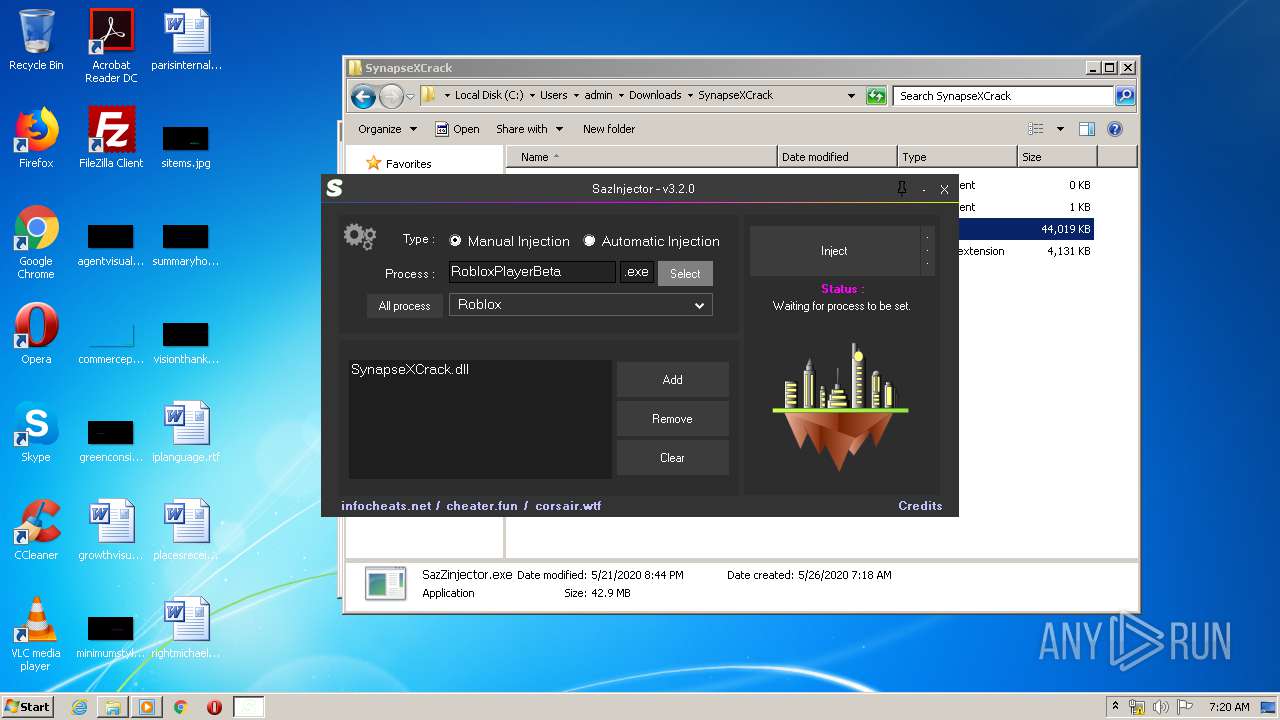
| File name: | service_log.txt |
| Full analysis: | https://app.any.run/tasks/a1c8911c-1b97-4a02-9628-92087e5d92f5 |
| Verdict: | Malicious activity |
| Analysis date: | May 26, 2020, 06:15:47 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | text/plain |
| File info: | ASCII text, with CRLF line terminators |
| MD5: | 702918BDD9DD13EE8FDEE31B94663FC7 |
| SHA1: | F126DE81B19C8883E6828A5A748D710D7267DA82 |
| SHA256: | 83792030482EB2B2D142133D23DE2FE9A3E867BE3F2EE9396636AE3840714E16 |
| SSDEEP: | 6:Mh/5MEQhyLVpMkUxsFn8cv/5MgaFn8cvyLVpMkUsn:MTQUXMkCk8ko8DXMkZ |
MALICIOUS
Loads dropped or rewritten executable
- SearchProtocolHost.exe (PID: 3056)
- tor.exe (PID: 780)
Application was dropped or rewritten from another process
- pUusgiOEN.exe (PID: 3224)
- svchost.exe (PID: 2528)
- Token.exe (PID: 1948)
- CL_Debug_Log.txt (PID: 2292)
- Helper.exe (PID: 3564)
- Helper.exe (PID: 2620)
- Helper.exe (PID: 2524)
- Helper.exe (PID: 2436)
- Helper.exe (PID: 3848)
- Helper.exe (PID: 2472)
- Helper.exe (PID: 4016)
- tor.exe (PID: 780)
Changes the autorun value in the registry
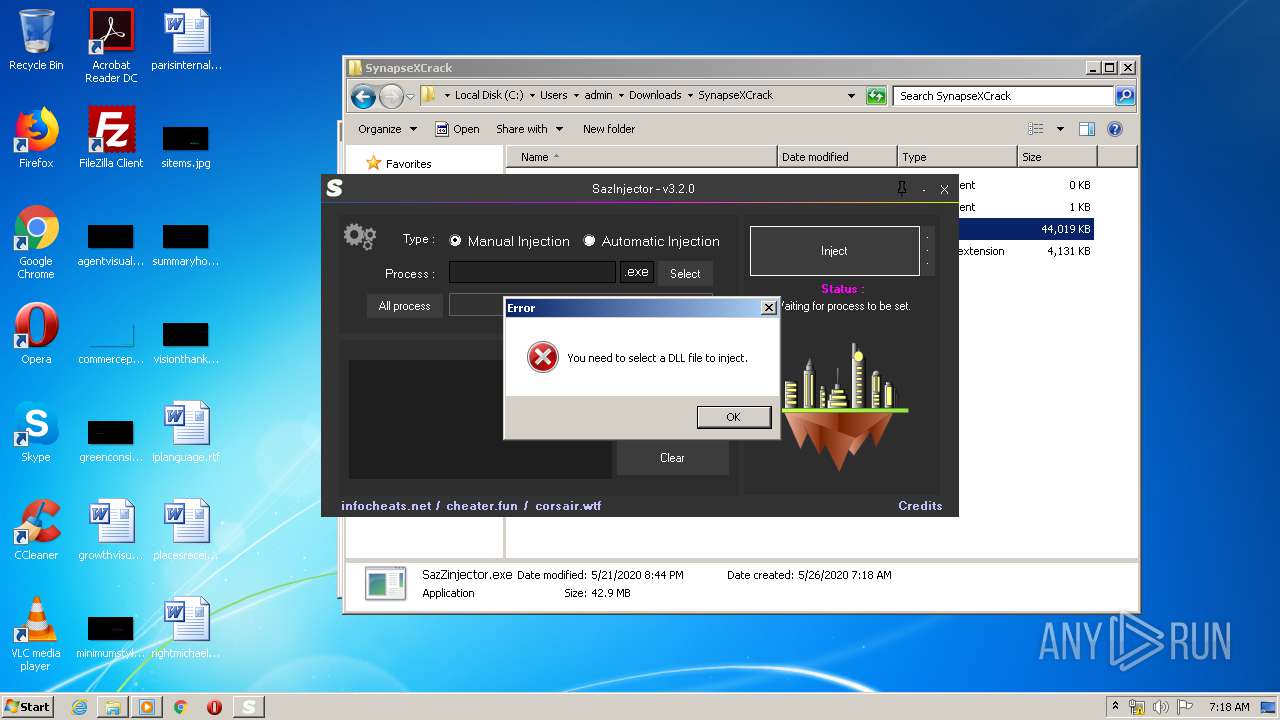
- SazZinjector.exe (PID: 644)
Uses Task Scheduler to run other applications
- cmd.exe (PID: 2156)
Loads the Task Scheduler COM API
- schtasks.exe (PID: 2052)
SUSPICIOUS
Modifies files in Chrome extension folder
- chrome.exe (PID: 2600)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 3836)
- SazZinjector.exe (PID: 644)
- svchost.exe (PID: 2528)
- CL_Debug_Log.txt (PID: 2292)
- Helper.exe (PID: 2524)
- Helper.exe (PID: 2620)
Creates executable files which already exist in Windows
- SazZinjector.exe (PID: 644)
Creates files in the user directory
- SazZinjector.exe (PID: 644)
- svchost.exe (PID: 2528)
- Helper.exe (PID: 2524)
- Helper.exe (PID: 2620)
- tor.exe (PID: 780)
Starts application with an unusual extension
- svchost.exe (PID: 2528)
Starts CMD.EXE for commands execution
- svchost.exe (PID: 2528)
Executed via Task Scheduler
- Helper.exe (PID: 2524)
- Helper.exe (PID: 3564)
- Helper.exe (PID: 2472)
- Helper.exe (PID: 4016)
- Helper.exe (PID: 2436)
- Helper.exe (PID: 3848)
Application launched itself
- Helper.exe (PID: 2524)
INFO
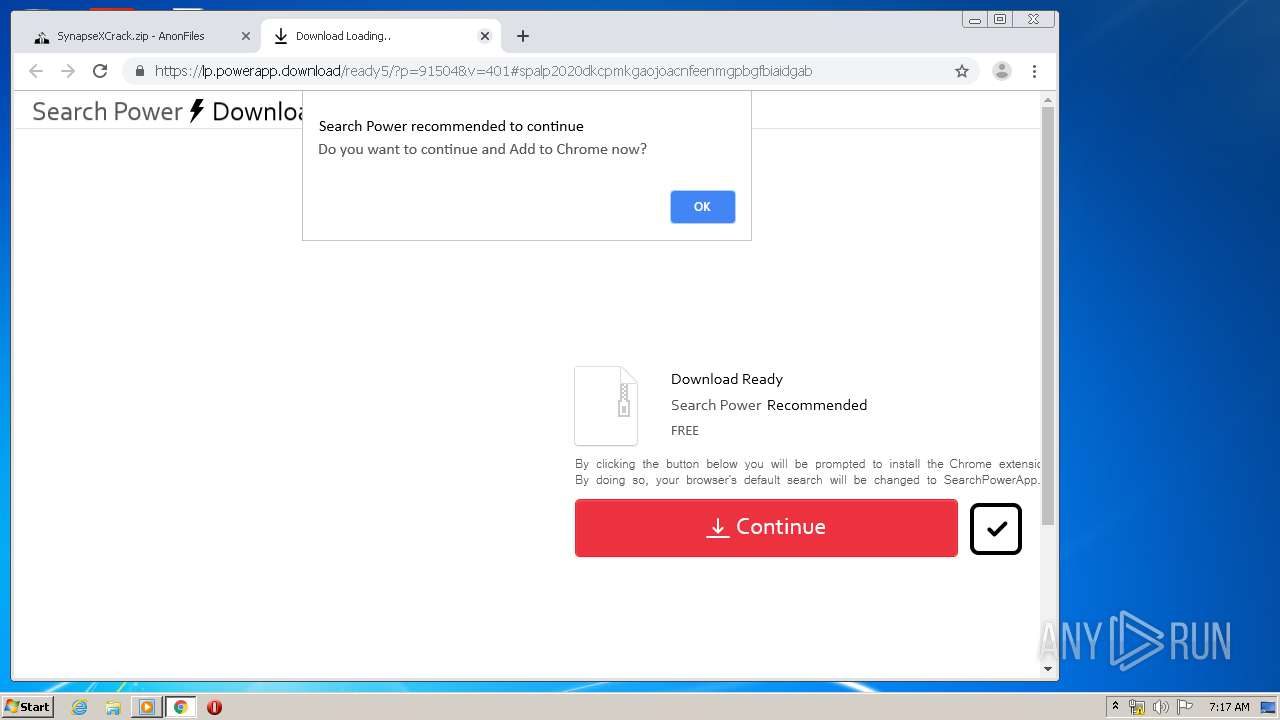
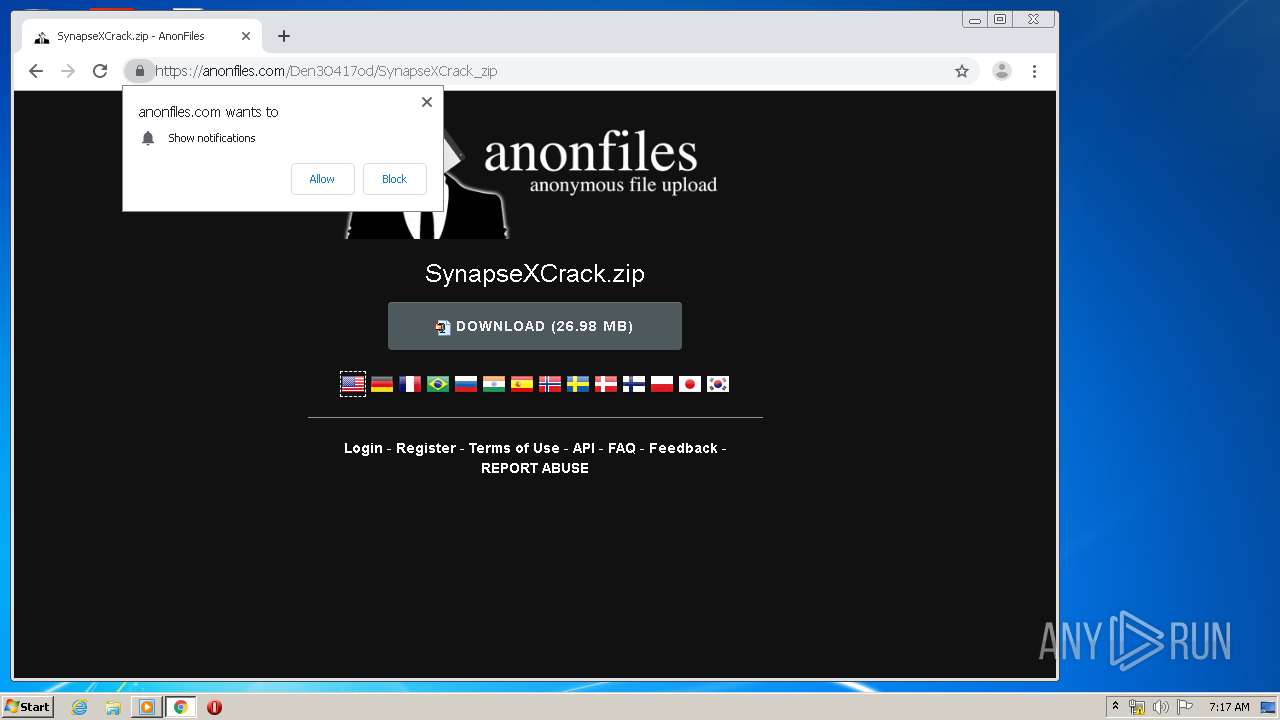
Manual execution by user
- chrome.exe (PID: 2600)
- wmplayer.exe (PID: 488)
- WinRAR.exe (PID: 3836)
- SazZinjector.exe (PID: 644)
Reads the hosts file
- chrome.exe (PID: 2600)
- chrome.exe (PID: 2268)
Dropped object may contain Bitcoin addresses
- chrome.exe (PID: 2600)
Creates files in the user directory
- chrome.exe (PID: 2600)
Reads Internet Cache Settings
- chrome.exe (PID: 2600)
Application launched itself
- chrome.exe (PID: 2600)
Reads settings of System Certificates
- chrome.exe (PID: 2268)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
106
Monitored processes
64
Malicious processes
7
Suspicious processes
5
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 120 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=gpu-process --field-trial-handle=996,10601155844165423474,3186418713255123437,131072 --enable-features=PasswordImport --disable-gpu-sandbox --use-gl=disabled --gpu-preferences=KAAAAAAAAADgAAAgAQAAAAAAAAAAAGAAAAAAAAAAAAAIAAAAAAAAACgAAAAEAAAAIAAAAAAAAAAoAAAAAAAAADAAAAAAAAAAOAAAAAAAAAAQAAAAAAAAAAAAAAAFAAAAEAAAAAAAAAAAAAAABgAAABAAAAAAAAAAAQAAAAUAAAAQAAAAAAAAAAEAAAAGAAAA --service-request-channel-token=12650112194692850476 --mojo-platform-channel-handle=4144 /prefetch:2 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 296 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --field-trial-handle=996,10601155844165423474,3186418713255123437,131072 --enable-features=PasswordImport --lang=en-US --no-sandbox --service-request-channel-token=9240969453007278519 --mojo-platform-channel-handle=2644 /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 488 | "C:\Program Files\Windows Media Player\wmplayer.exe" /prefetch:1 | C:\Program Files\Windows Media Player\wmplayer.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Media Player Exit code: 0 Version: 12.0.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 564 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --field-trial-handle=996,10601155844165423474,3186418713255123437,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=utility --service-request-channel-token=7717418529168021517 --mojo-platform-channel-handle=1656 --ignored=" --type=renderer " /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 620 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=996,10601155844165423474,3186418713255123437,131072 --enable-features=PasswordImport --disable-gpu-compositing --lang=en-US --enable-offline-auto-reload --enable-offline-auto-reload-visible-only --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --service-request-channel-token=4229549831285787341 --renderer-client-id=35 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=2076 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 644 | "C:\Users\admin\Downloads\SynapseXCrack\SazZinjector.exe" | C:\Users\admin\Downloads\SynapseXCrack\SazZinjector.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Description: Exit code: 0 Version: 0.0.0.0 Modules
| |||||||||||||||
| 680 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=gpu-process --field-trial-handle=996,10601155844165423474,3186418713255123437,131072 --enable-features=PasswordImport --gpu-preferences=KAAAAAAAAADgAAAgAQAAAAAAAAAAAGAAAAAAAAAAAAAIAAAAAAAAACgAAAAEAAAAIAAAAAAAAAAoAAAAAAAAADAAAAAAAAAAOAAAAAAAAAAQAAAAAAAAAAAAAAAFAAAAEAAAAAAAAAAAAAAABgAAABAAAAAAAAAAAQAAAAUAAAAQAAAAAAAAAAEAAAAGAAAA --service-request-channel-token=16316815819211560932 --mojo-platform-channel-handle=1036 --ignored=" --type=renderer " /prefetch:2 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 780 | "C:\Users\admin\AppData\Roaming\Microsoft\Windows\Tor\tor.exe" -f TorConfig | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Tor\tor.exe | Helper.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 840 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=996,10601155844165423474,3186418713255123437,131072 --enable-features=PasswordImport --disable-gpu-compositing --lang=en-US --enable-offline-auto-reload --enable-offline-auto-reload-visible-only --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --service-request-channel-token=1140687300006288270 --renderer-client-id=33 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=3812 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 888 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=996,10601155844165423474,3186418713255123437,131072 --enable-features=PasswordImport --lang=en-US --instant-process --enable-offline-auto-reload --enable-offline-auto-reload-visible-only --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --service-request-channel-token=4144351937999277233 --renderer-client-id=6 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=1948 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
Total events
3 069
Read events
2 863
Write events
200
Delete events
6
Modification events
| (PID) Process: | (2236) NOTEPAD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Notepad |
| Operation: | write | Name: | iWindowPosX |
Value: 132 | |||
| (PID) Process: | (2236) NOTEPAD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Notepad |
| Operation: | write | Name: | iWindowPosY |
Value: 132 | |||
| (PID) Process: | (2236) NOTEPAD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Notepad |
| Operation: | write | Name: | iWindowPosDX |
Value: 960 | |||
| (PID) Process: | (2236) NOTEPAD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Notepad |
| Operation: | write | Name: | iWindowPosDY |
Value: 501 | |||
| (PID) Process: | (488) wmplayer.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 0 | |||
| (PID) Process: | (488) wmplayer.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 1 | |||
| (PID) Process: | (2624) setup_wm.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\MediaPlayer\Setup\UserOptions |
| Operation: | write | Name: | DesktopShortcut |
Value: no | |||
| (PID) Process: | (2600) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BLBeacon |
| Operation: | write | Name: | failed_count |
Value: 0 | |||
| (PID) Process: | (2600) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BLBeacon |
| Operation: | write | Name: | state |
Value: 2 | |||
| (PID) Process: | (2600) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\ThirdParty |
| Operation: | write | Name: | StatusCodes |
Value: | |||
Executable files
20
Suspicious files
86
Text files
311
Unknown types
14
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2600 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\BrowserMetrics\BrowserMetrics-5ECCB42C-A28.pma | — | |
MD5:— | SHA256:— | |||
| 2600 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\b65dc487-8c81-4b19-abc2-c4f0467f5589.tmp | — | |
MD5:— | SHA256:— | |||
| 2600 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\data_reduction_proxy_leveldb\000028.dbtmp | — | |
MD5:— | SHA256:— | |||
| 2600 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\data_reduction_proxy_leveldb\CURRENT | — | |
MD5:— | SHA256:— | |||
| 2600 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Sync Data\LevelDB\LOG.old | text | |
MD5:— | SHA256:— | |||
| 2600 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\data_reduction_proxy_leveldb\LOG.old | text | |
MD5:— | SHA256:— | |||
| 2600 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Sync Data\LevelDB\LOG.old~RF15ba51.TMP | text | |
MD5:— | SHA256:— | |||
| 2600 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\data_reduction_proxy_leveldb\LOG.old~RF15ba51.TMP | text | |
MD5:— | SHA256:— | |||
| 2600 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\shared_proto_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 2600 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\shared_proto_db\LOG.old~RF15bc74.TMP | — | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
12
TCP/UDP connections
58
DNS requests
40
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
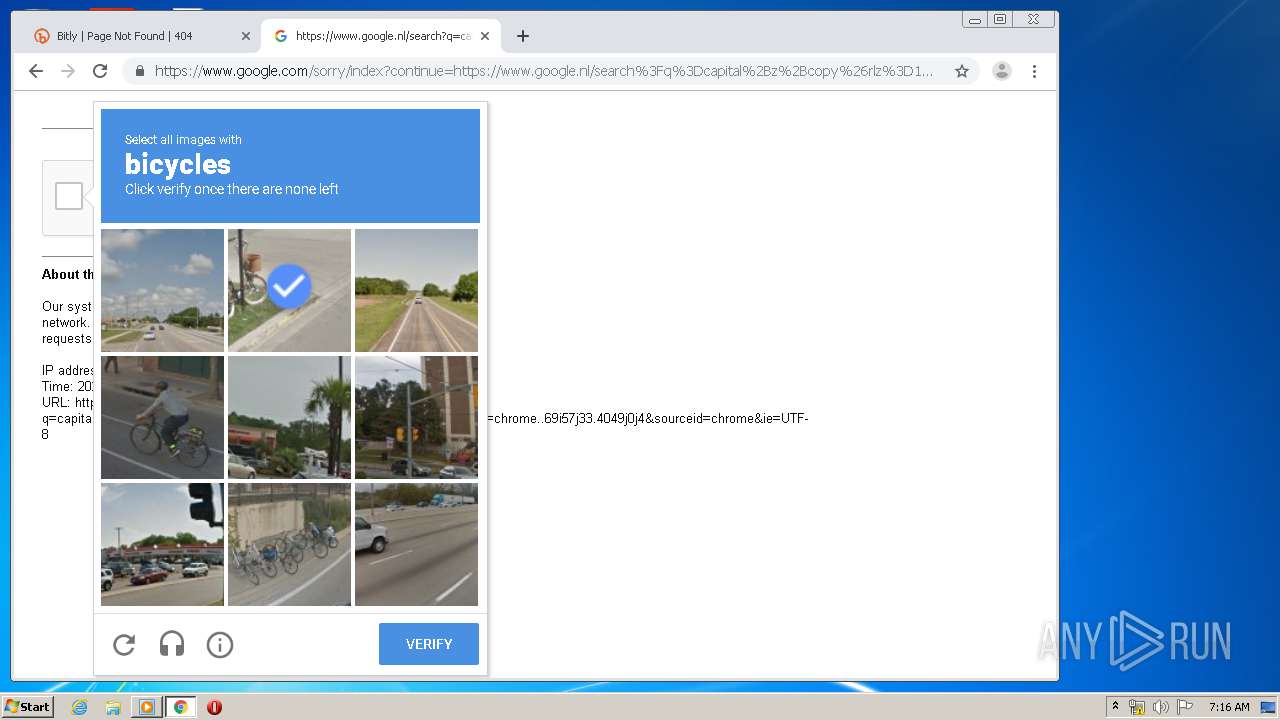
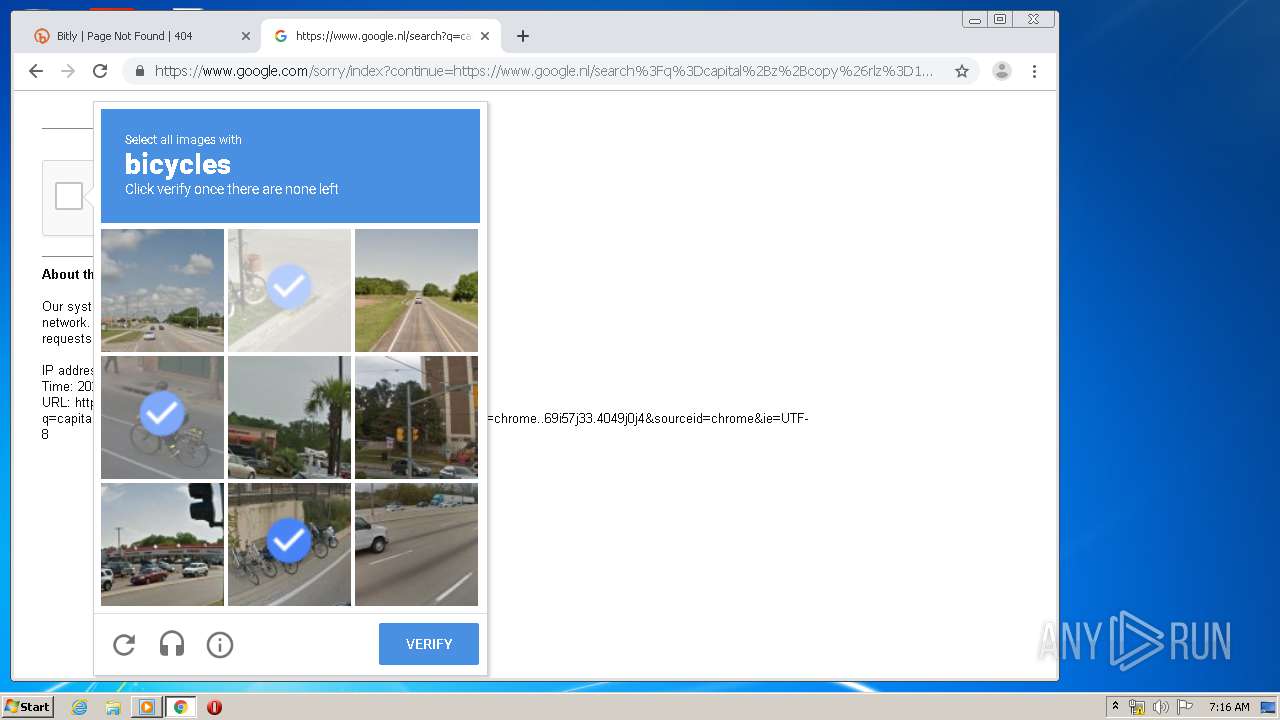
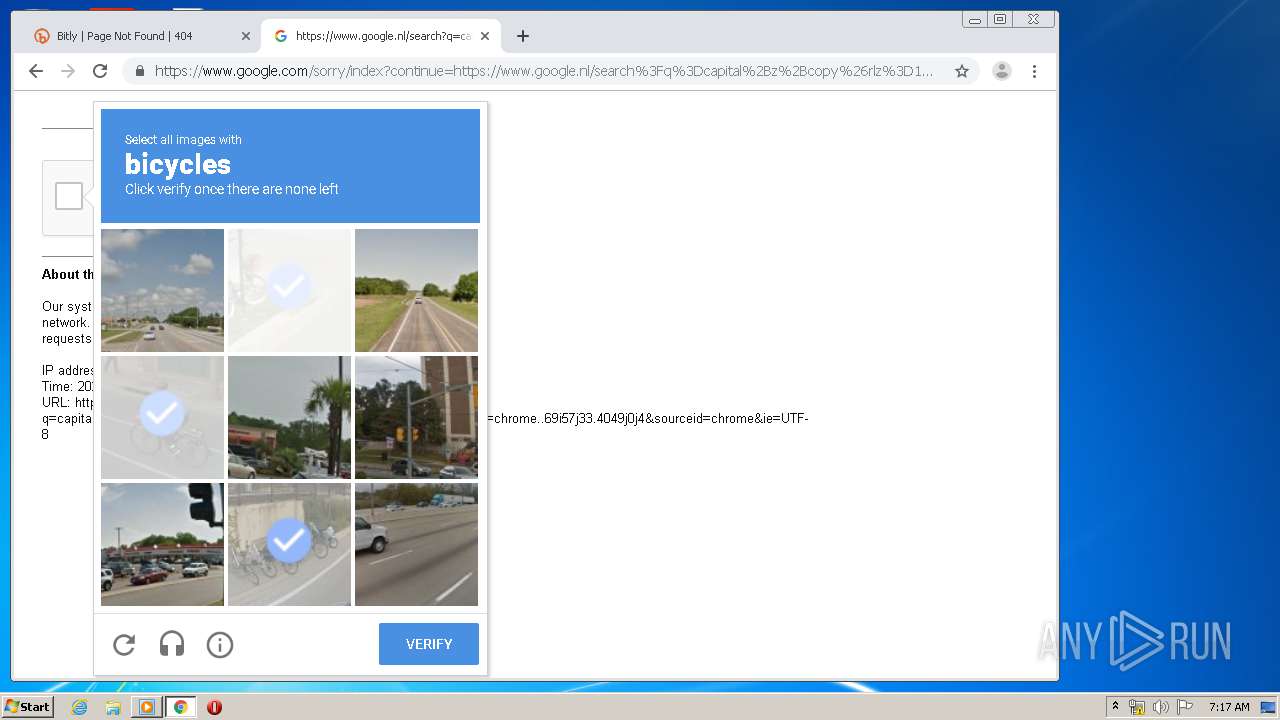
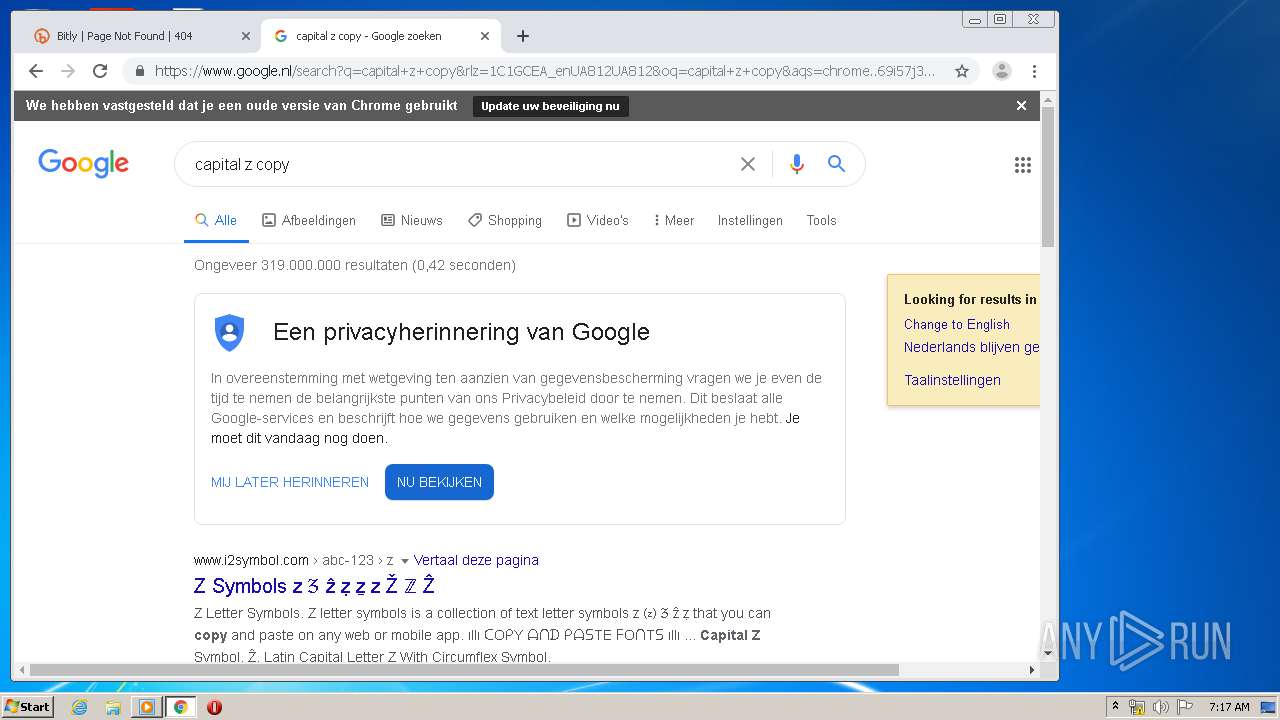
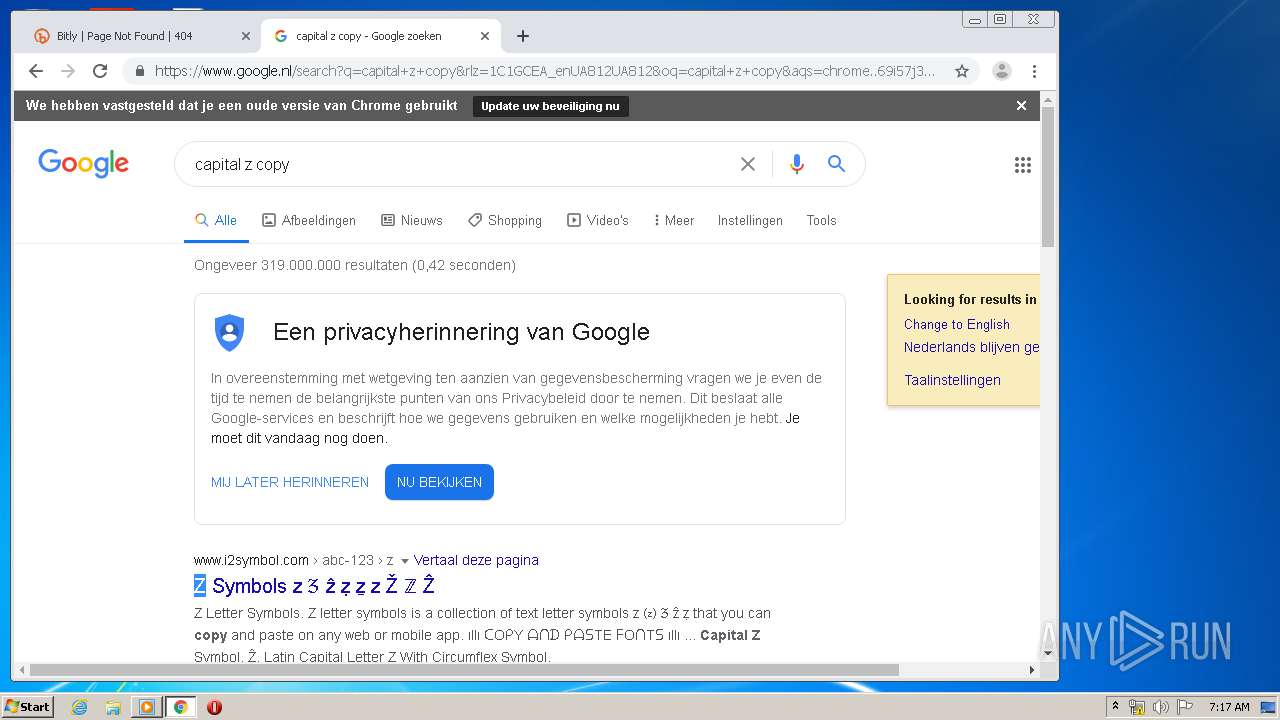
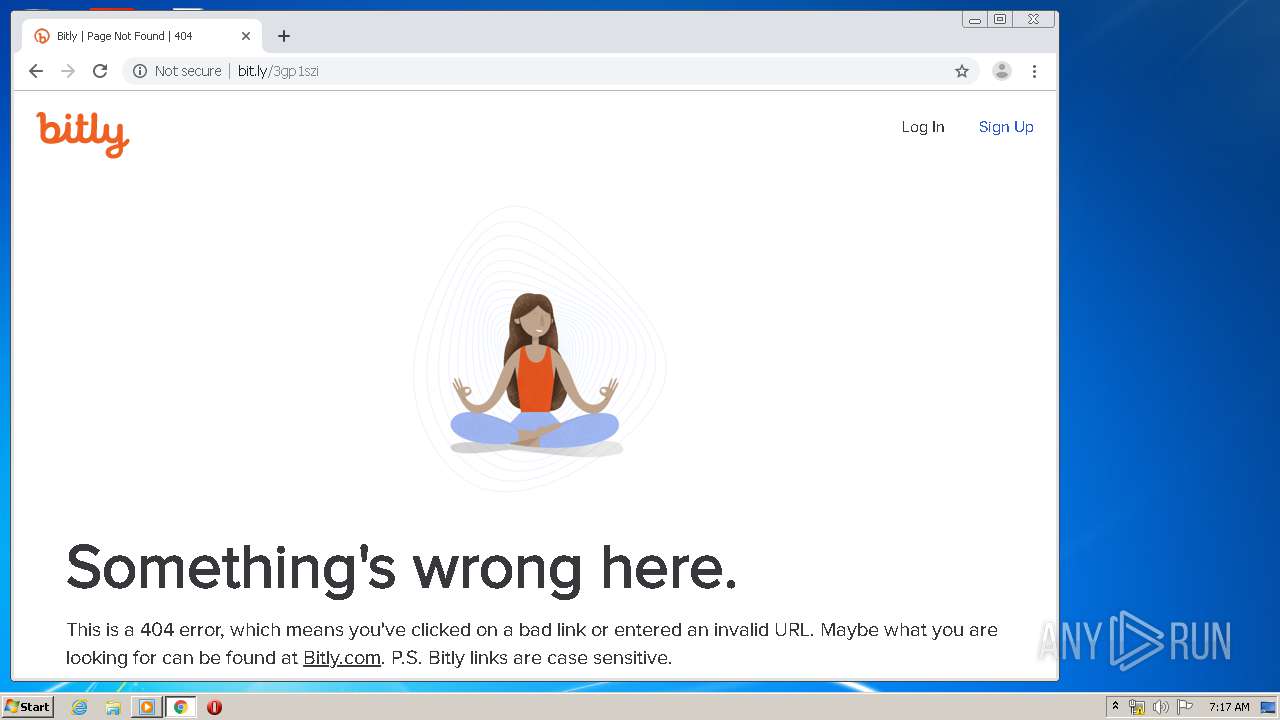
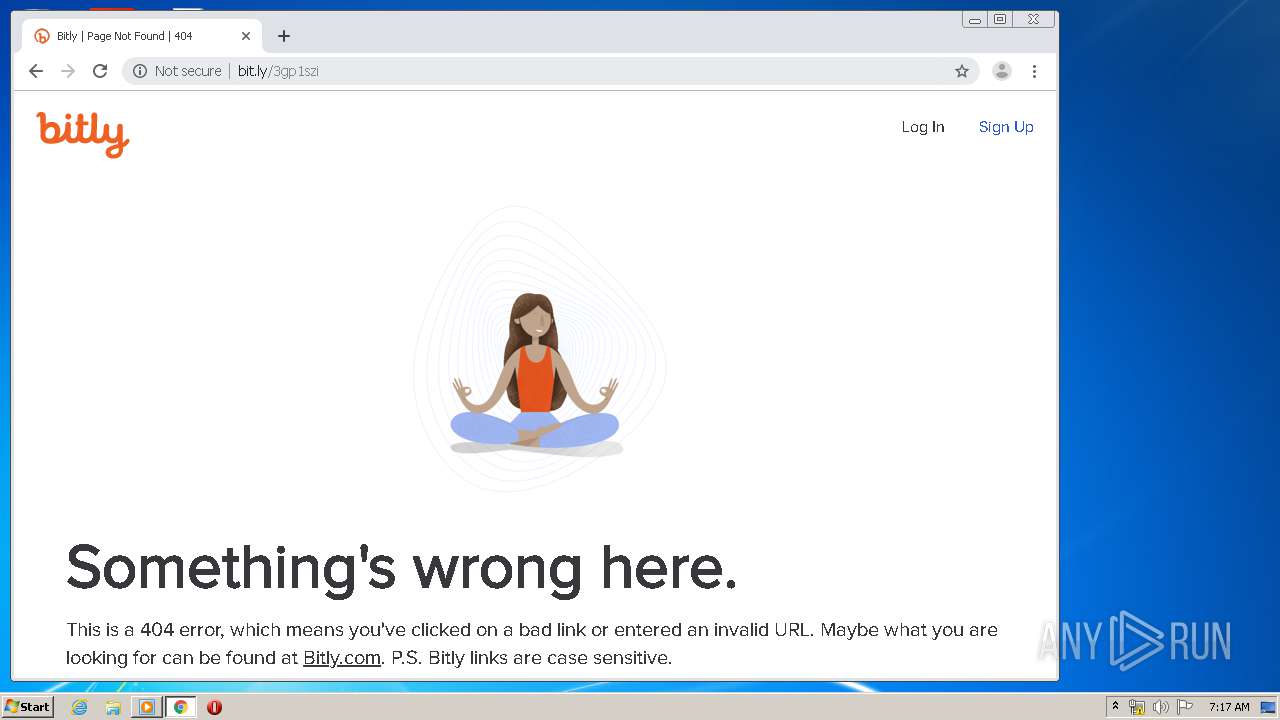
2268 | chrome.exe | GET | 404 | 67.199.248.10:80 | http://bit.ly/3gp1szi | US | html | 5.29 Kb | shared |
2268 | chrome.exe | GET | 302 | 172.217.23.142:80 | http://redirector.gvt1.com/edgedl/chromewebstore/L2Nocm9tZV9leHRlbnNpb24vYmxvYnMvOTRmQUFXVHlhaGJaUTdMLWtCSkNJUl9ZQQ/1.0.0.5_nmmhkkegccagdldgiimedpiccmgmieda.crx | US | html | 517 b | whitelisted |
2268 | chrome.exe | GET | 200 | 172.217.132.74:80 | http://r5---sn-5hne6nsr.gvt1.com/edgedl/chromewebstore/L2Nocm9tZV9leHRlbnNpb24vYmxvYnMvYjY5QUFXTEQwc2RPVXhRY3picjhxblh1dw/7619.603.0.2_pkedcjkdefgpdelpbcmbmeomcjbeemfm.crx?cms_redirect=yes&mh=Qx&mip=85.203.44.7&mm=28&mn=sn-5hne6nsr&ms=nvh&mt=1590473710&mv=m&mvi=4&pl=26&shardbypass=yes | US | crx | 816 Kb | whitelisted |
2268 | chrome.exe | GET | 302 | 172.217.23.142:80 | http://redirector.gvt1.com/edgedl/chromewebstore/L2Nocm9tZV9leHRlbnNpb24vYmxvYnMvYjY5QUFXTEQwc2RPVXhRY3picjhxblh1dw/7619.603.0.2_pkedcjkdefgpdelpbcmbmeomcjbeemfm.crx | US | html | 522 b | whitelisted |
2268 | chrome.exe | GET | 200 | 74.125.8.9:80 | http://r3---sn-5hne6n7e.gvt1.com/edgedl/chromewebstore/L2Nocm9tZV9leHRlbnNpb24vYmxvYnMvOTRmQUFXVHlhaGJaUTdMLWtCSkNJUl9ZQQ/1.0.0.5_nmmhkkegccagdldgiimedpiccmgmieda.crx?cms_redirect=yes&mh=QJ&mip=85.203.44.7&mm=28&mn=sn-5hne6n7e&ms=nvh&mt=1590473710&mv=m&mvi=2&pl=26&shardbypass=yes | US | crx | 293 Kb | whitelisted |
2268 | chrome.exe | GET | 200 | 67.199.248.10:80 | http://bit.ly/static/graphics/bitly_logo_red.svg | US | image | 3.47 Kb | shared |
2268 | chrome.exe | GET | 200 | 67.199.248.10:80 | http://bit.ly/static/graphics/meditation.png | US | image | 24.4 Kb | shared |
2268 | chrome.exe | GET | 200 | 67.199.248.10:80 | http://bit.ly/static/graphics/ProximaNova-Regular.woff2 | US | woff2 | 26.1 Kb | shared |
2268 | chrome.exe | GET | 200 | 172.217.23.110:80 | http://www.google-analytics.com/r/collect?v=1&_v=j82&a=427984408&t=pageview&_s=1&dl=http%3A%2F%2Fbit.ly%2F3gp1szi&ul=en-us&de=UTF-8&dt=Bitly%20%7C%20Page%20Not%20Found%20%7C%20404&sd=24-bit&sr=1280x720&vp=1042x587&je=0&_u=IEBAAEAB~&jid=1851727063&gjid=817667726&cid=200318040.1590473792&tid=UA-25224921-11&_gid=510857507.1590473792&_r=1&z=168031610 | US | image | 35 b | whitelisted |
2268 | chrome.exe | GET | 200 | 67.199.248.10:80 | http://bit.ly/favicon.ico | US | image | 5.30 Kb | shared |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2268 | chrome.exe | 172.217.21.234:443 | fonts.googleapis.com | Google Inc. | US | whitelisted |
2268 | chrome.exe | 172.217.16.131:443 | fonts.gstatic.com | Google Inc. | US | whitelisted |
2268 | chrome.exe | 216.58.212.163:443 | www.gstatic.com | Google Inc. | US | whitelisted |
2268 | chrome.exe | 216.58.210.14:443 | apis.google.com | Google Inc. | US | whitelisted |
2268 | chrome.exe | 172.217.23.174:443 | ogs.google.com.ua | Google Inc. | US | whitelisted |
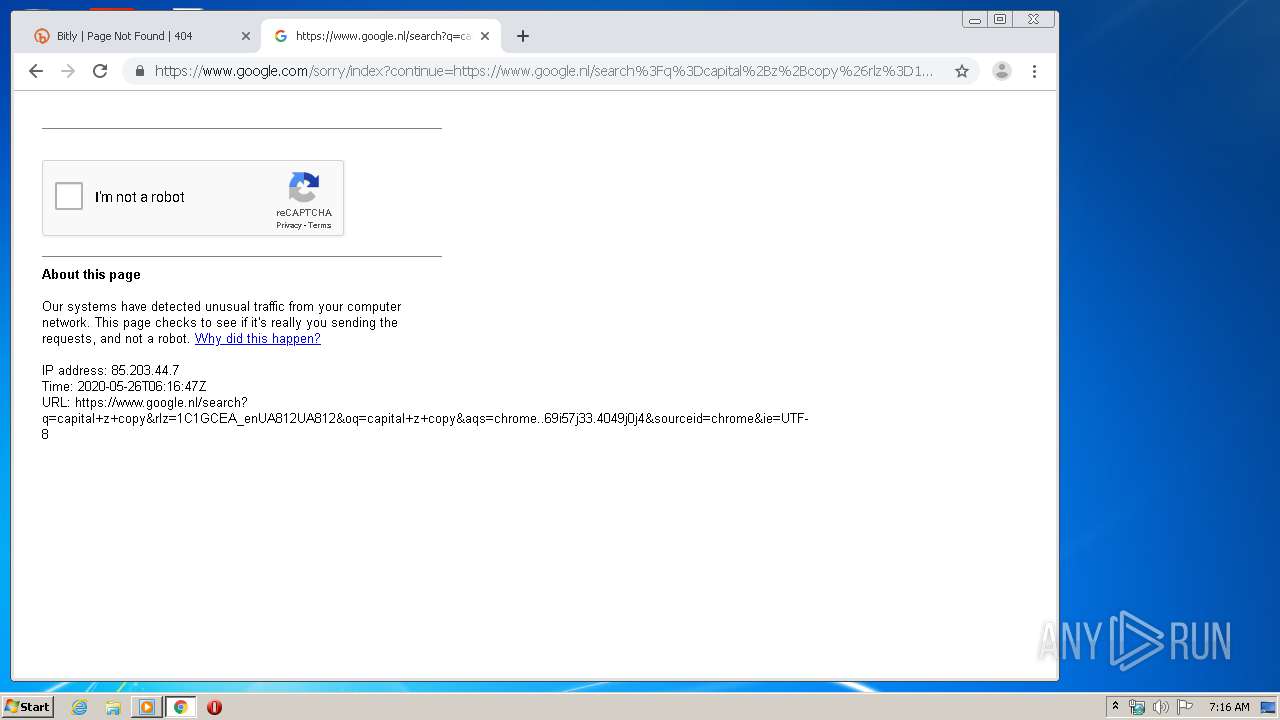
2268 | chrome.exe | 172.217.18.164:443 | www.google.com | Google Inc. | US | whitelisted |
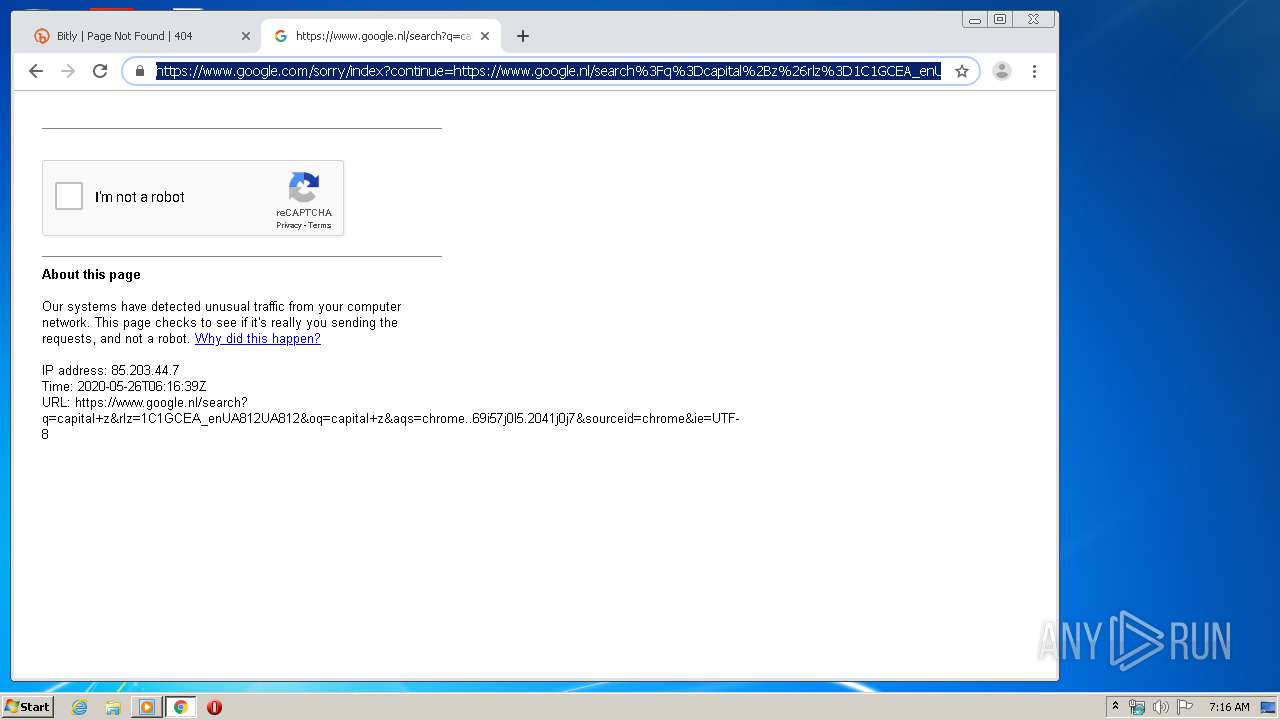
2268 | chrome.exe | 216.58.212.131:443 | www.google.nl | Google Inc. | US | whitelisted |
— | — | 216.58.212.131:443 | www.google.nl | Google Inc. | US | whitelisted |
2268 | chrome.exe | 172.217.21.195:443 | clientservices.googleapis.com | Google Inc. | US | whitelisted |
2268 | chrome.exe | 172.217.132.74:80 | r5---sn-5hne6nsr.gvt1.com | Google Inc. | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
clientservices.googleapis.com |
| whitelisted |
accounts.google.com |
| shared |
www.google.com.ua |
| whitelisted |
fonts.googleapis.com |
| whitelisted |
www.gstatic.com |
| whitelisted |
fonts.gstatic.com |
| whitelisted |
apis.google.com |
| whitelisted |
ogs.google.com.ua |
| whitelisted |
www.google.com |
| malicious |
www.google.nl |
| whitelisted |