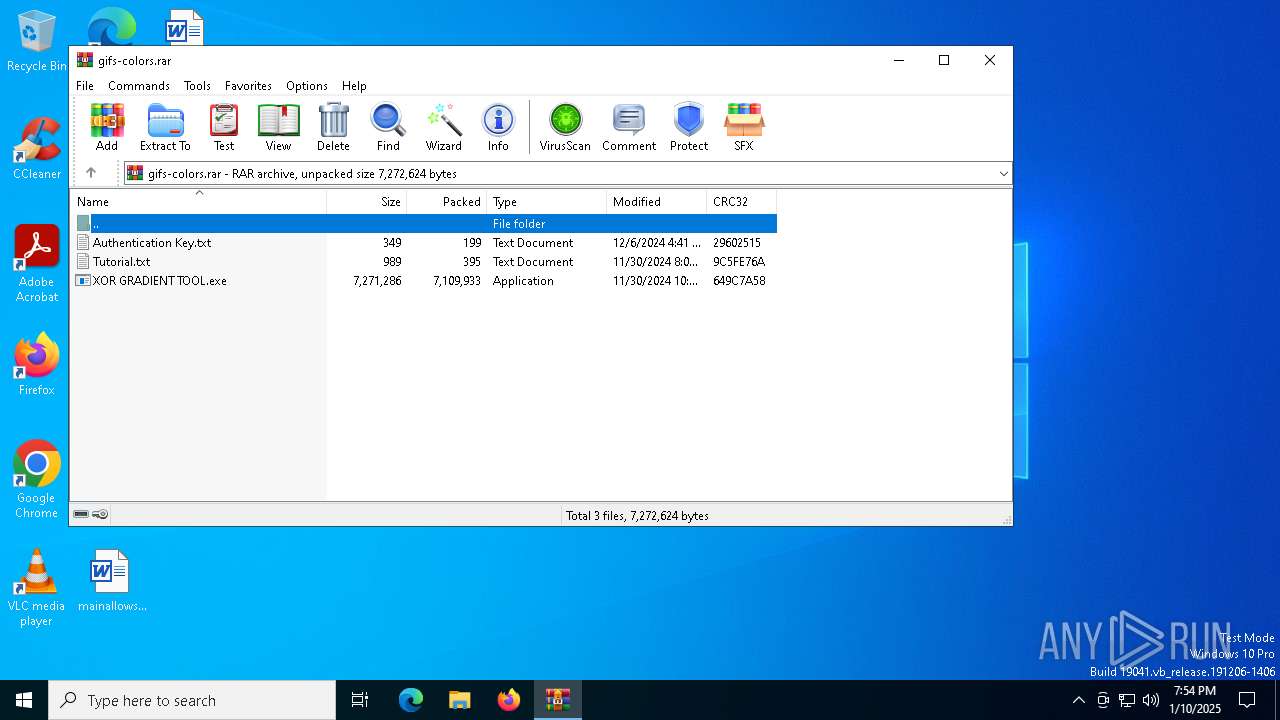
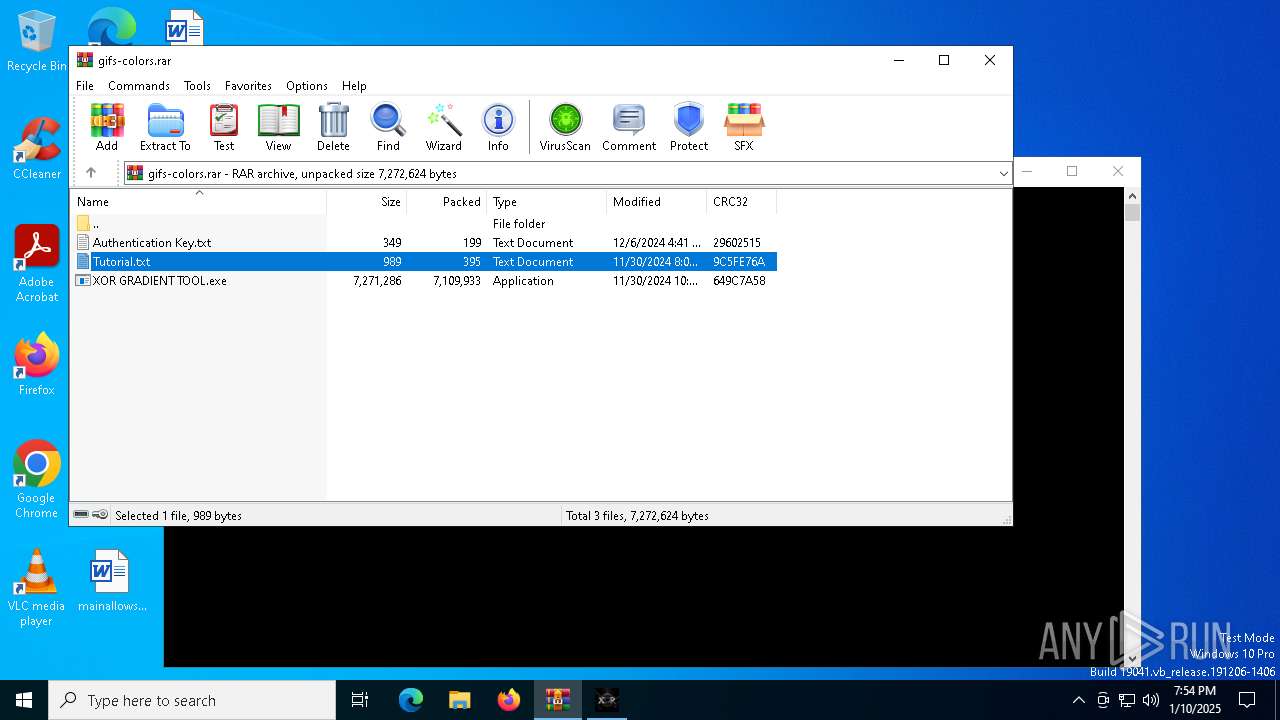
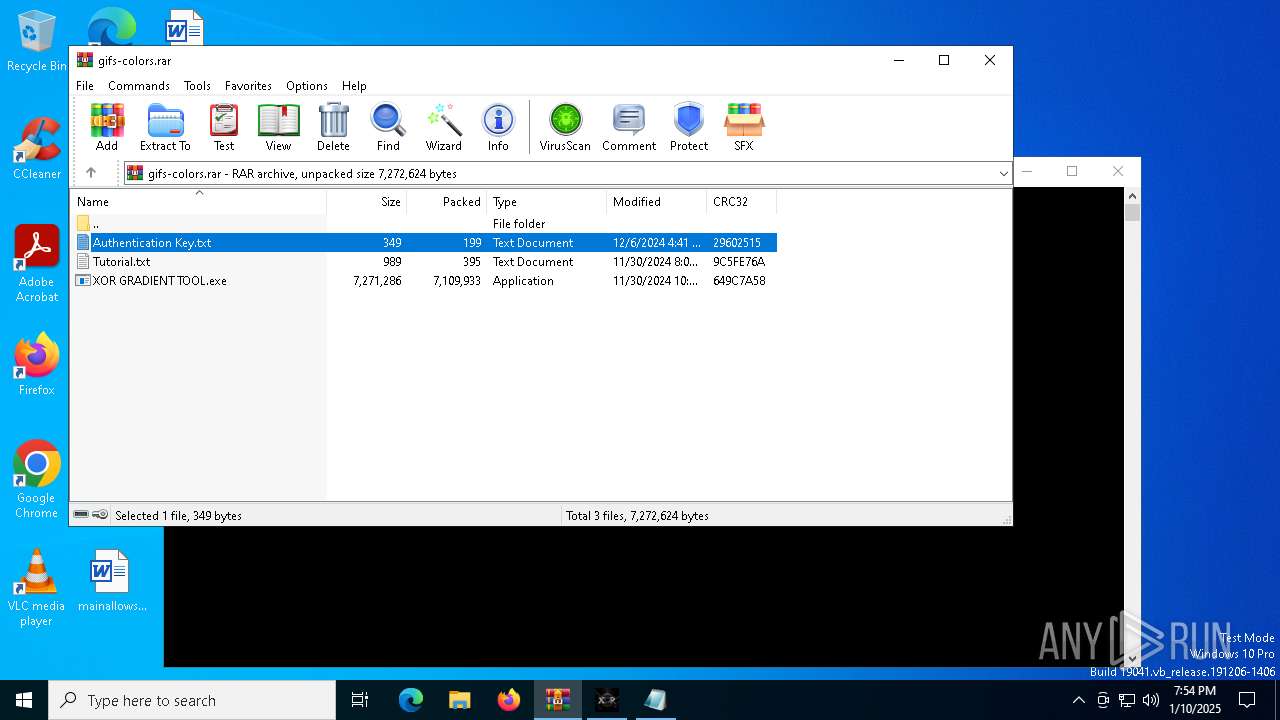
| File name: | gifs-colors.rar |
| Full analysis: | https://app.any.run/tasks/98717897-a761-46dd-9524-d235e03a89e7 |
| Verdict: | Malicious activity |
| Analysis date: | January 10, 2025, 19:54:20 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-rar |
| File info: | RAR archive data, v5 |
| MD5: | BA6C03DD0D60E51F2875A19361320E5C |
| SHA1: | 8B9A518D358C731E2B44FCCB664A01D6B73BE9F9 |
| SHA256: | 836831DA409E8E3AC692E74D10C2B5C713C4810AAEBB4291DE5C4E7AB81E617E |
| SSDEEP: | 98304:PiW3l6c7nKvq1+P1RNjMbxUmurfLMHJ+HyLAKleWYMEmPeiENjle+4sW8UBzi3O8:sOlh4Il+kcBhVCI |
MALICIOUS
Generic archive extractor
- WinRAR.exe (PID: 2100)
SUSPICIOUS
Executable content was dropped or overwritten
- XOR GRADIENT TOOL.exe (PID: 6444)
The process drops C-runtime libraries
- XOR GRADIENT TOOL.exe (PID: 6444)
Process drops legitimate windows executable
- XOR GRADIENT TOOL.exe (PID: 6444)
Process drops python dynamic module
- XOR GRADIENT TOOL.exe (PID: 6444)
Application launched itself
- XOR GRADIENT TOOL.exe (PID: 6444)
Reads security settings of Internet Explorer
- WinRAR.exe (PID: 2100)
Loads Python modules
- XOR GRADIENT TOOL.exe (PID: 6516)
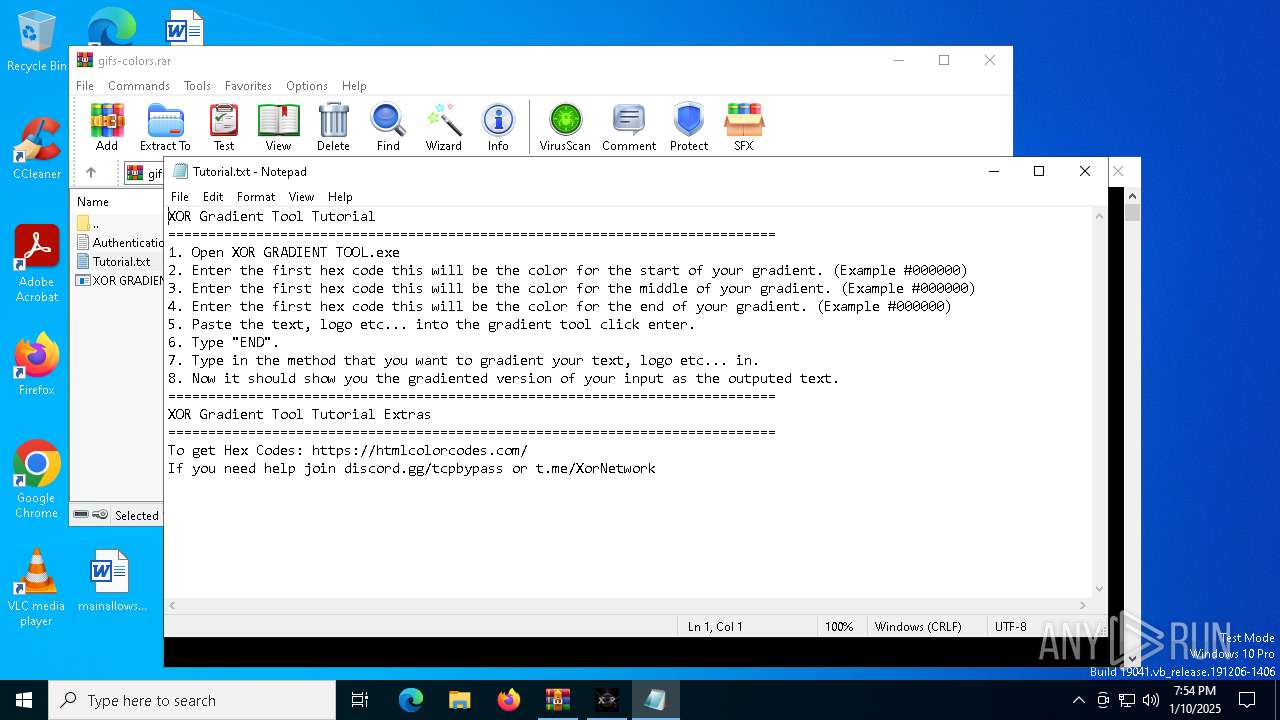
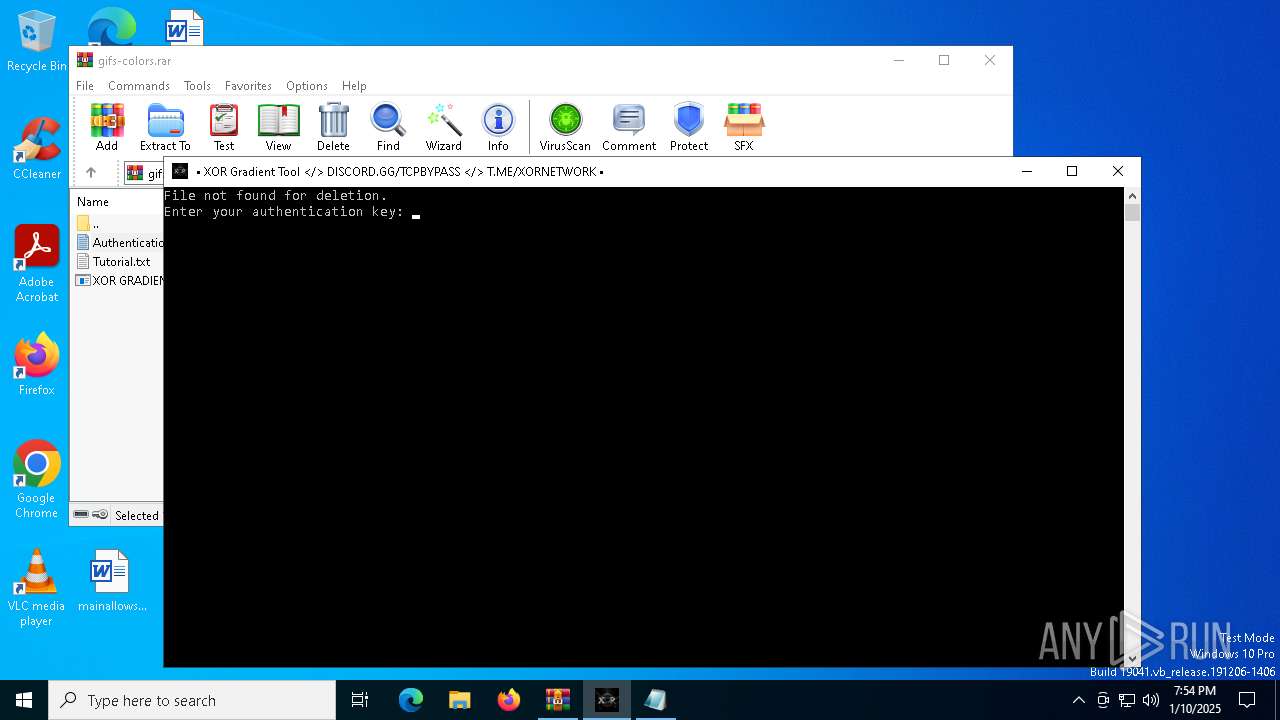
Start notepad (likely ransomware note)
- WinRAR.exe (PID: 2100)
Starts CMD.EXE for commands execution
- XOR GRADIENT TOOL.exe (PID: 6516)
INFO
Executable content was dropped or overwritten
- WinRAR.exe (PID: 2100)
The sample compiled with english language support
- XOR GRADIENT TOOL.exe (PID: 6444)
Create files in a temporary directory
- XOR GRADIENT TOOL.exe (PID: 6444)
Checks supported languages
- XOR GRADIENT TOOL.exe (PID: 6444)
- XOR GRADIENT TOOL.exe (PID: 6516)
Reads the computer name
- XOR GRADIENT TOOL.exe (PID: 6444)
The process uses the downloaded file
- WinRAR.exe (PID: 2100)
Reads Microsoft Office registry keys
- WinRAR.exe (PID: 2100)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .rar | | | RAR compressed archive (v5.0) (61.5) |
|---|---|---|
| .rar | | | RAR compressed archive (gen) (38.4) |
EXIF
ZIP
| FileVersion: | RAR v5 |
|---|---|
| CompressedSize: | 199 |
| UncompressedSize: | 349 |
| OperatingSystem: | Win32 |
| ArchivedFileName: | Authentication Key.txt |
Total processes
133
Monitored processes
7
Malicious processes
0
Suspicious processes
2
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 2100 | "C:\Program Files\WinRAR\WinRAR.exe" C:\Users\admin\AppData\Local\Temp\gifs-colors.rar | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Version: 5.91.0 Modules
| |||||||||||||||
| 6444 | "C:\Users\admin\AppData\Local\Temp\Rar$EXa2100.18138\XOR GRADIENT TOOL.exe" | C:\Users\admin\AppData\Local\Temp\Rar$EXa2100.18138\XOR GRADIENT TOOL.exe | WinRAR.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Modules
| |||||||||||||||
| 6452 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | XOR GRADIENT TOOL.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6516 | "C:\Users\admin\AppData\Local\Temp\Rar$EXa2100.18138\XOR GRADIENT TOOL.exe" | C:\Users\admin\AppData\Local\Temp\Rar$EXa2100.18138\XOR GRADIENT TOOL.exe | — | XOR GRADIENT TOOL.exe | |||||||||||
User: admin Integrity Level: MEDIUM Modules
| |||||||||||||||
| 6812 | "C:\WINDOWS\system32\NOTEPAD.EXE" C:\Users\admin\AppData\Local\Temp\Rar$DIa2100.19058\Tutorial.txt | C:\Windows\System32\notepad.exe | — | WinRAR.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Notepad Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
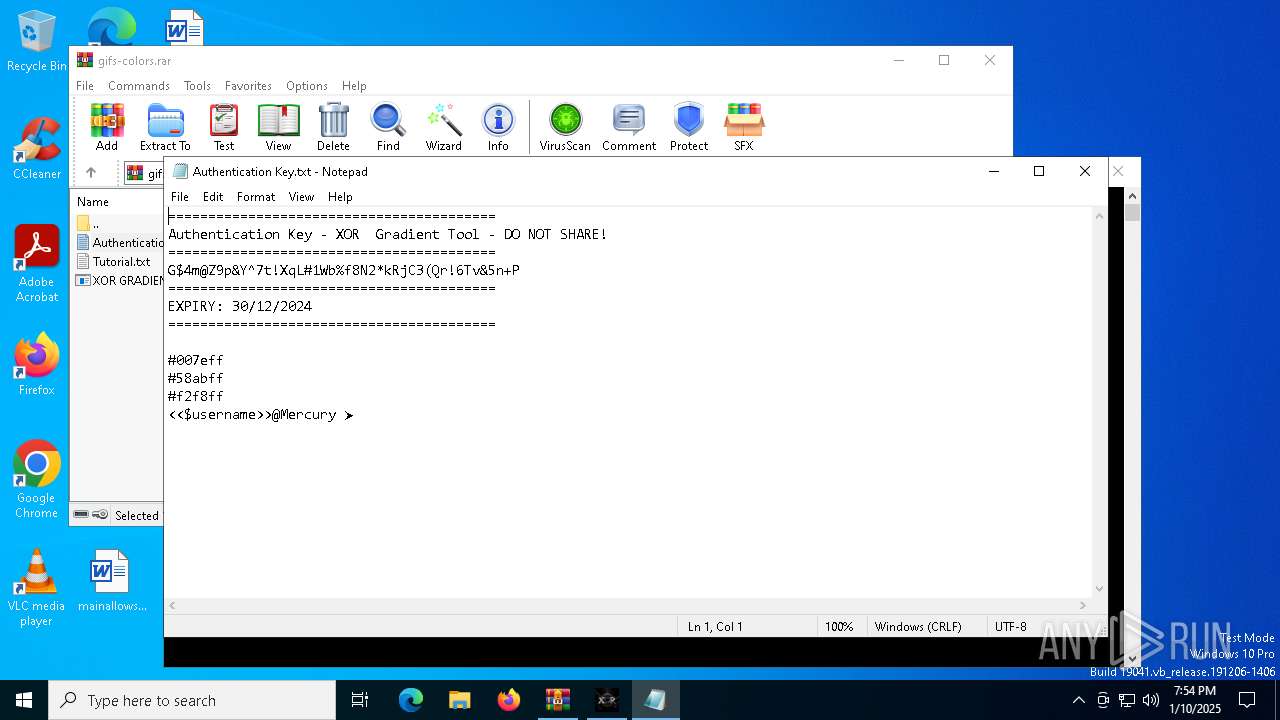
| 6940 | "C:\WINDOWS\system32\NOTEPAD.EXE" C:\Users\admin\AppData\Local\Temp\Rar$DIa2100.19624\Authentication Key.txt | C:\Windows\System32\notepad.exe | — | WinRAR.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Notepad Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 7164 | C:\WINDOWS\system32\cmd.exe /c cls | C:\Windows\System32\cmd.exe | — | XOR GRADIENT TOOL.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
2 959
Read events
2 949
Write events
10
Delete events
0
Modification events
| (PID) Process: | (2100) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\preferences.zip | |||
| (PID) Process: | (2100) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\chromium_ext.zip | |||
| (PID) Process: | (2100) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
| (PID) Process: | (2100) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\gifs-colors.rar | |||
| (PID) Process: | (2100) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (2100) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (2100) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (2100) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (2100) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\FileExts\.txt\OpenWithProgids |
| Operation: | write | Name: | txtfile |
Value: | |||
Executable files
13
Suspicious files
1
Text files
4
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2100 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa2100.18138\Authentication Key.txt | text | |
MD5:D371A08E65E413E11E1CEB7D52343D5B | SHA256:01AFA5CABCB74B9E5DD5B9D3606FAD1987FDFA630F1A9B407346F8612117A949 | |||
| 2100 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa2100.18138\XOR GRADIENT TOOL.exe | executable | |
MD5:4C60C172EAD861E7F94D79FE79853655 | SHA256:9401920FF063E2744DCA3E8BBC5D627AC6DB476540F3098271D48A8D27D82150 | |||
| 2100 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa2100.18138\Tutorial.txt | text | |
MD5:9963347A672E26D0D6A883D172350A83 | SHA256:9F4F1970A582A707F2532AEDD8AB94F1A83D52241F7B3CA48348039201521F35 | |||
| 6444 | XOR GRADIENT TOOL.exe | C:\Users\admin\AppData\Local\Temp\_MEI64442\select.pyd | executable | |
MD5:20831703486869B470006941B4D996F2 | SHA256:78E5994C29D8851F28B5B12D59D742D876683AEA58ECEEA1FB895B2036CDCDEB | |||
| 6444 | XOR GRADIENT TOOL.exe | C:\Users\admin\AppData\Local\Temp\_MEI64442\libcrypto-3.dll | executable | |
MD5:123AD0908C76CCBA4789C084F7A6B8D0 | SHA256:4E5D5D20D6D31E72AB341C81E97B89E514326C4C861B48638243BDF0918CFA43 | |||
| 6444 | XOR GRADIENT TOOL.exe | C:\Users\admin\AppData\Local\Temp\_MEI64442\base_library.zip | compressed | |
MD5:A9CBD0455B46C7D14194D1F18CA8719E | SHA256:DF6C19637D239BFEDC8CD13D20E0938C65E8FDF340622FF334DB533F2D30FA19 | |||
| 6444 | XOR GRADIENT TOOL.exe | C:\Users\admin\AppData\Local\Temp\_MEI64442\libffi-8.dll | executable | |
MD5:0F8E4992CA92BAAF54CC0B43AACCCE21 | SHA256:EFF52743773EB550FCC6CE3EFC37C85724502233B6B002A35496D828BD7B280A | |||
| 2100 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DIa2100.19058\Tutorial.txt | text | |
MD5:9963347A672E26D0D6A883D172350A83 | SHA256:9F4F1970A582A707F2532AEDD8AB94F1A83D52241F7B3CA48348039201521F35 | |||
| 2100 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DIa2100.19624\Authentication Key.txt | text | |
MD5:D371A08E65E413E11E1CEB7D52343D5B | SHA256:01AFA5CABCB74B9E5DD5B9D3606FAD1987FDFA630F1A9B407346F8612117A949 | |||
| 6444 | XOR GRADIENT TOOL.exe | C:\Users\admin\AppData\Local\Temp\_MEI64442\_ctypes.pyd | executable | |
MD5:A55E57D7594303C89B5F7A1D1D6F2B67 | SHA256:F63C6C7E71C342084D8F1A108786CA6975A52CEFEF8BE32CC2589E6E2FE060C8 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
6
TCP/UDP connections
32
DNS requests
20
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | GET | 200 | 2.23.246.101:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 2.16.241.19:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
6180 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAUZZSZEml49Gjh0j13P68w%3D | unknown | — | — | whitelisted |
7044 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
7044 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
1176 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4712 | MoUsoCoreWorker.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
3220 | svchost.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 2.16.241.19:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
— | — | 2.23.246.101:80 | www.microsoft.com | Ooredoo Q.S.C. | QA | whitelisted |
5064 | SearchApp.exe | 2.23.227.215:443 | www.bing.com | Ooredoo Q.S.C. | QA | whitelisted |
1176 | svchost.exe | 40.126.32.140:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
1076 | svchost.exe | 2.23.242.9:443 | go.microsoft.com | Ooredoo Q.S.C. | QA | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
www.bing.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
login.live.com |
| whitelisted |
go.microsoft.com |
| whitelisted |
arc.msn.com |
| whitelisted |
fd.api.iris.microsoft.com |
| whitelisted |