| File name: | InstallBC201401.exe |
| Full analysis: | https://app.any.run/tasks/b78e5397-394b-4293-b90a-410c9a9e4bbe |
| Verdict: | Malicious activity |
| Analysis date: | May 15, 2025, 13:51:30 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows, 7 sections |
| MD5: | CAFF801A280D42DBD1AD6B1266D3C43A |
| SHA1: | 08B9F5874AD1DC3EE1093C9CD08737645F33F13F |
| SHA256: | 834D1DBFAB8330EA5F1844F6E905ED0AC19D1033EE9A9F1122AD2051C56783DC |
| SSDEEP: | 196608:1UDU1mprZJy2p/HvE/uUhM32f0J0s6mW6W1rsWrzSWas5+VBI/93eiJGDXWku74:10UMpr3dvsM3+nmHW1DS/s5WQRVG3J |
MALICIOUS
No malicious indicators.SUSPICIOUS
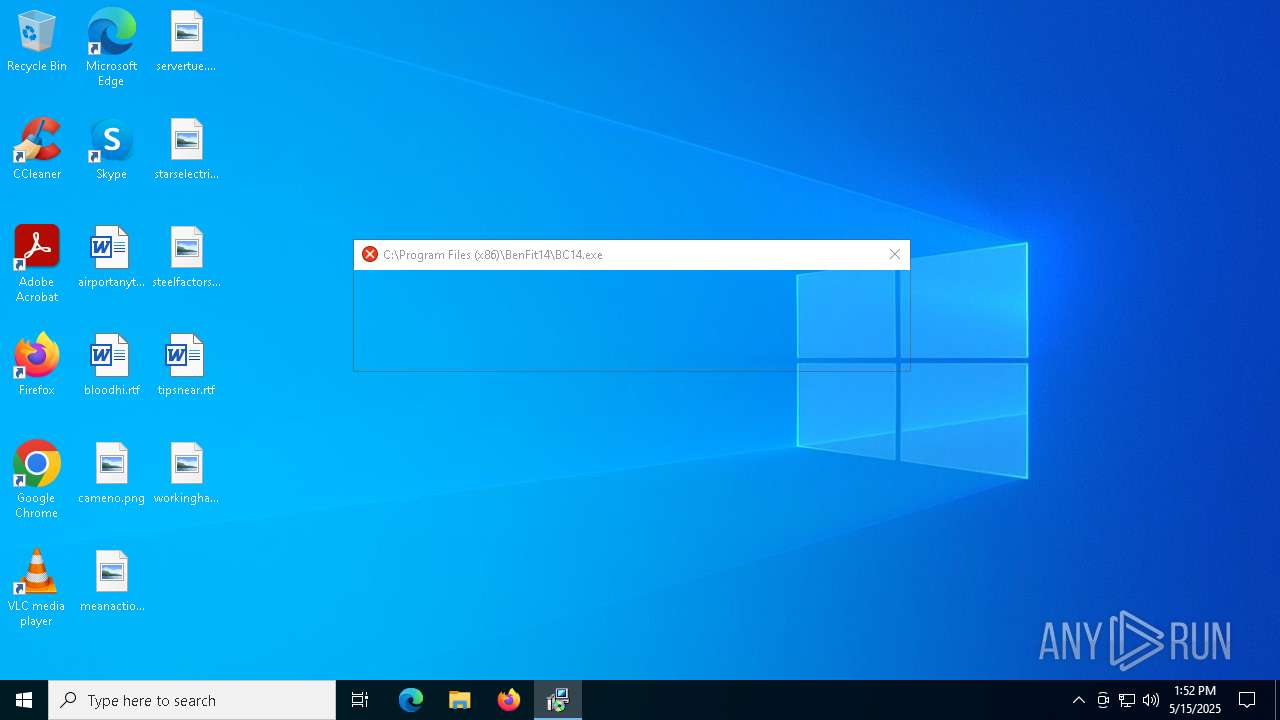
Executable content was dropped or overwritten
- InstallBC201401.exe (PID: 920)
Process drops legitimate windows executable
- InstallBC201401.exe (PID: 920)
The process creates files with name similar to system file names
- InstallBC201401.exe (PID: 920)
Creates a software uninstall entry
- InstallBC201401.exe (PID: 920)
INFO
Reads Environment values
- InstallBC201401.exe (PID: 920)
Checks supported languages
- InstallBC201401.exe (PID: 920)
Reads the computer name
- InstallBC201401.exe (PID: 920)
Create files in a temporary directory
- InstallBC201401.exe (PID: 920)
Creates files in the program directory
- InstallBC201401.exe (PID: 920)
TSULoader has been detected
- InstallBC201401.exe (PID: 920)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win32 Executable MS Visual C++ (generic) (42.2) |
|---|---|---|
| .exe | | | Win64 Executable (generic) (37.3) |
| .dll | | | Win32 Dynamic Link Library (generic) (8.8) |
| .exe | | | Win32 Executable (generic) (6) |
| .exe | | | Generic Win/DOS Executable (2.7) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2013:12:25 02:09:40+00:00 |
| ImageFileCharacteristics: | Executable, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 8 |
| CodeSize: | 7680 |
| InitializedDataSize: | 13362176 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x1495 |
| OSVersion: | 4 |
| ImageVersion: | 6 |
| SubsystemVersion: | 4 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 2014.1.4.1230 |
| ProductVersionNumber: | 0.0.0.0 |
| FileFlagsMask: | 0x003f |
| FileFlags: | Special build |
| FileOS: | Windows NT 32-bit |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | Neutral |
| CharacterSet: | Unicode |
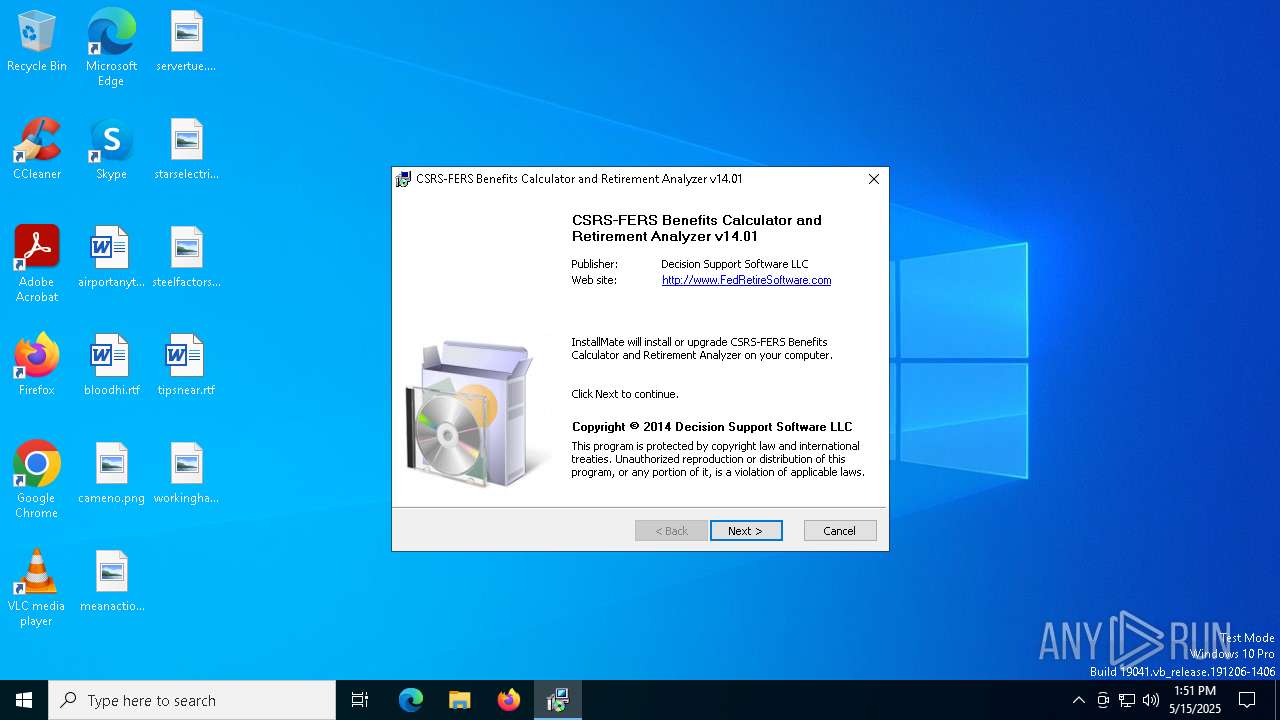
| ProductName: | CSRS-FERS Benefits Calculator and Retirement Analyzer |
| ProductVersion: | v14.01 |
| CompanyName: | Decision Support Software LLC |
| LegalCopyright: | Copyright © 2014 Decision Support Software LLC |
| Email: | ActivationDepartment@FedRetireSoftware.com |
| WebSite: | http://www.FedRetireSoftware.com |
| FileDescription: | Installer for CSRS-FERS Benefits Calculator and Retirement Analy |
| FileVersion: | 2014.1.4.1230 |
| InternalName: | TSULoader |
| OriginalFileName: | TSULoader.exe |
| Comments: | WinNT (x86) Unicode Lib Rel |
| ProductCode: | {1E453EA8-BB42-419D-8067-D2477A36B761} |
| PackageCode: | {D449BC32-6D28-4AF0-BB00-AB3391EF0F9A} |
| Arguments: | - |
| SpecialBuild: | - |
Total processes
126
Monitored processes
3
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 920 | "C:\Users\admin\AppData\Local\Temp\InstallBC201401.exe" | C:\Users\admin\AppData\Local\Temp\InstallBC201401.exe | explorer.exe | ||||||||||||
User: admin Company: Decision Support Software LLC Integrity Level: HIGH Description: Installer for CSRS-FERS Benefits Calculator and Retirement Analy Exit code: 0 Version: 2014.1.4.1230 Modules
| |||||||||||||||
| 5056 | "C:\Users\admin\AppData\Local\Temp\InstallBC201401.exe" | C:\Users\admin\AppData\Local\Temp\InstallBC201401.exe | — | explorer.exe | |||||||||||
User: admin Company: Decision Support Software LLC Integrity Level: MEDIUM Description: Installer for CSRS-FERS Benefits Calculator and Retirement Analy Exit code: 3221226540 Version: 2014.1.4.1230 Modules
| |||||||||||||||
| 5720 | C:\WINDOWS\System32\slui.exe -Embedding | C:\Windows\System32\slui.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Activation Client Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
445
Read events
418
Write events
22
Delete events
5
Modification events
| (PID) Process: | (920) InstallBC201401.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\{1E453EA8-BB42-419D-8067-D2477A36B761} |
| Operation: | write | Name: | UninstallString |
Value: C:\PROGRA~3\INSTAL~1\{1E453~1\Setup.exe /remove /q0 | |||
| (PID) Process: | (920) InstallBC201401.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\{1E453EA8-BB42-419D-8067-D2477A36B761} |
| Operation: | write | Name: | QuietUninstallString |
Value: C:\PROGRA~3\INSTAL~1\{1E453~1\Setup.exe /remove /q | |||
| (PID) Process: | (920) InstallBC201401.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\{1E453EA8-BB42-419D-8067-D2477A36B761} |
| Operation: | write | Name: | ModifyPath |
Value: C:\PROGRA~3\INSTAL~1\{1E453~1\Setup.exe /q0 | |||
| (PID) Process: | (920) InstallBC201401.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\{1E453EA8-BB42-419D-8067-D2477A36B761} |
| Operation: | write | Name: | Version |
Value: 0 | |||
| (PID) Process: | (920) InstallBC201401.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\{1E453EA8-BB42-419D-8067-D2477A36B761} |
| Operation: | write | Name: | VersionMajor |
Value: 0 | |||
| (PID) Process: | (920) InstallBC201401.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\{1E453EA8-BB42-419D-8067-D2477A36B761} |
| Operation: | write | Name: | VersionMinor |
Value: 0 | |||
| (PID) Process: | (920) InstallBC201401.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\{1E453EA8-BB42-419D-8067-D2477A36B761} |
| Operation: | write | Name: | EstimatedSize |
Value: 0 | |||
| (PID) Process: | (920) InstallBC201401.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\{1E453EA8-BB42-419D-8067-D2477A36B761} |
| Operation: | write | Name: | Language |
Value: 1033 | |||
| (PID) Process: | (920) InstallBC201401.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\{1E453EA8-BB42-419D-8067-D2477A36B761} |
| Operation: | write | Name: | TSAware |
Value: 1 | |||
| (PID) Process: | (920) InstallBC201401.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\{1E453EA8-BB42-419D-8067-D2477A36B761} |
| Operation: | write | Name: | TinFolder |
Value: C:\ProgramData\InstallMate\{1E453EA8-BB42-419D-8067-D2477A36B761} | |||
Executable files
8
Suspicious files
2
Text files
6
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 920 | InstallBC201401.exe | C:\Users\admin\AppData\Local\Temp\C84549B9.dat | binary | |
MD5:B0A7109B74113B1A5A532D4BAD90A8B5 | SHA256:77098FBEB11A37C5AAF858B4255BE416FE0847CEBD99331641FAF01038D838C9 | |||
| 920 | InstallBC201401.exe | C:\Users\admin\AppData\Local\Temp\C84549B9\Setup.ico | image | |
MD5:C3926CEF276C0940DADBC8142153CEC9 | SHA256:0EC48E3C1886BC0169A4BC262F012E9B7914E3B440BB0ECC4D8123924ABC9B93 | |||
| 920 | InstallBC201401.exe | C:\ProgramData\InstallMate\{1E453EA8-BB42-419D-8067-D2477A36B761}\_Setup.dll | executable | |
MD5:76DDA4C8CE17DF4591C5B9A7363854CE | SHA256:735A433ADE90EAF829FD9C11C4BF6A33DCF712F5451BBAB0B6B9435EDE7B6259 | |||
| 920 | InstallBC201401.exe | C:\ProgramData\InstallMate\{1E453EA8-BB42-419D-8067-D2477A36B761}\Readme.txt | text | |
MD5:741E8AAD1477503D201A622321D3A49A | SHA256:7936796E1A2A732AF971E7F137960EEF4891981379D2ED103B377002E8C6C59D | |||
| 920 | InstallBC201401.exe | C:\ProgramData\InstallMate\{1E453EA8-BB42-419D-8067-D2477A36B761}\Tsu.dll | executable | |
MD5:BE4559AB30CA2957A49209F0E786CCC7 | SHA256:F4B52618DB95A41819D623D44995BB7A3F9ACBCB406447CA8ECDDEE8859B94C1 | |||
| 920 | InstallBC201401.exe | C:\ProgramData\InstallMate\{1E453EA8-BB42-419D-8067-D2477A36B761}\Setup.ico | image | |
MD5:C3926CEF276C0940DADBC8142153CEC9 | SHA256:0EC48E3C1886BC0169A4BC262F012E9B7914E3B440BB0ECC4D8123924ABC9B93 | |||
| 920 | InstallBC201401.exe | C:\ProgramData\InstallMate\{1E453EA8-BB42-419D-8067-D2477A36B761}\Setup.exe | executable | |
MD5:39C78ACD07821DF6F706F695B5E566AB | SHA256:6C70D20E43651F4F40A39F0F5B9346157C17A9BBB0E2C738C713F545550FE58F | |||
| 920 | InstallBC201401.exe | C:\Users\admin\AppData\Local\Temp\Tsu80BA1495.dll | executable | |
MD5:BE4559AB30CA2957A49209F0E786CCC7 | SHA256:F4B52618DB95A41819D623D44995BB7A3F9ACBCB406447CA8ECDDEE8859B94C1 | |||
| 920 | InstallBC201401.exe | C:\Users\admin\AppData\Local\Temp\C84549B9\Setup.exe | executable | |
MD5:39C78ACD07821DF6F706F695B5E566AB | SHA256:6C70D20E43651F4F40A39F0F5B9346157C17A9BBB0E2C738C713F545550FE58F | |||
| 920 | InstallBC201401.exe | C:\Users\admin\AppData\Local\Temp\C84549B9\_Setup.dll | executable | |
MD5:76DDA4C8CE17DF4591C5B9A7363854CE | SHA256:735A433ADE90EAF829FD9C11C4BF6A33DCF712F5451BBAB0B6B9435EDE7B6259 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
4
TCP/UDP connections
17
DNS requests
12
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | GET | 200 | 2.20.245.139:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
5064 | SIHClient.exe | GET | 200 | 23.219.150.101:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
5064 | SIHClient.exe | GET | 200 | 23.219.150.101:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 2.20.245.139:80 | crl.microsoft.com | Akamai International B.V. | SE | whitelisted |
— | — | 95.101.149.131:80 | www.microsoft.com | Akamai International B.V. | NL | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
2104 | svchost.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
3216 | svchost.exe | 172.211.123.248:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | FR | whitelisted |
5064 | SIHClient.exe | 172.202.163.200:443 | slscr.update.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | GB | whitelisted |
5064 | SIHClient.exe | 23.219.150.101:80 | www.microsoft.com | AKAMAI-AS | CL | whitelisted |
5064 | SIHClient.exe | 13.95.31.18:443 | fe3cr.delivery.mp.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |
activation-v2.sls.microsoft.com |
| whitelisted |