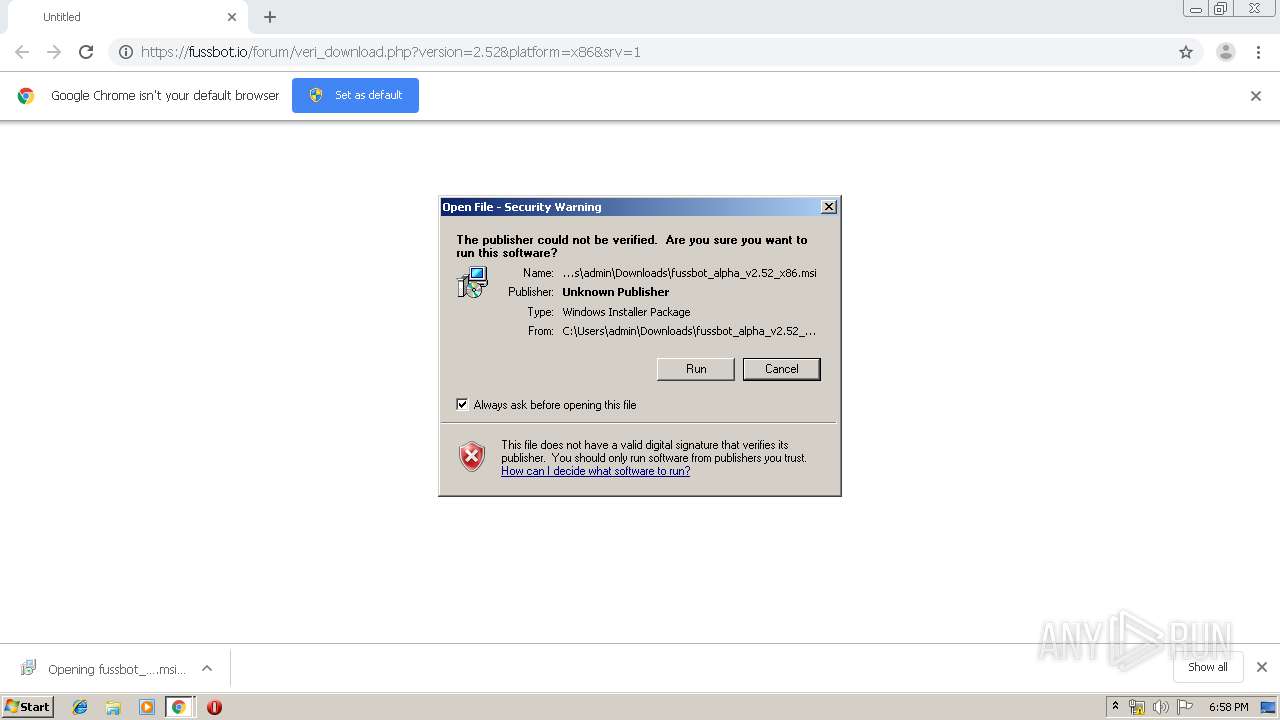
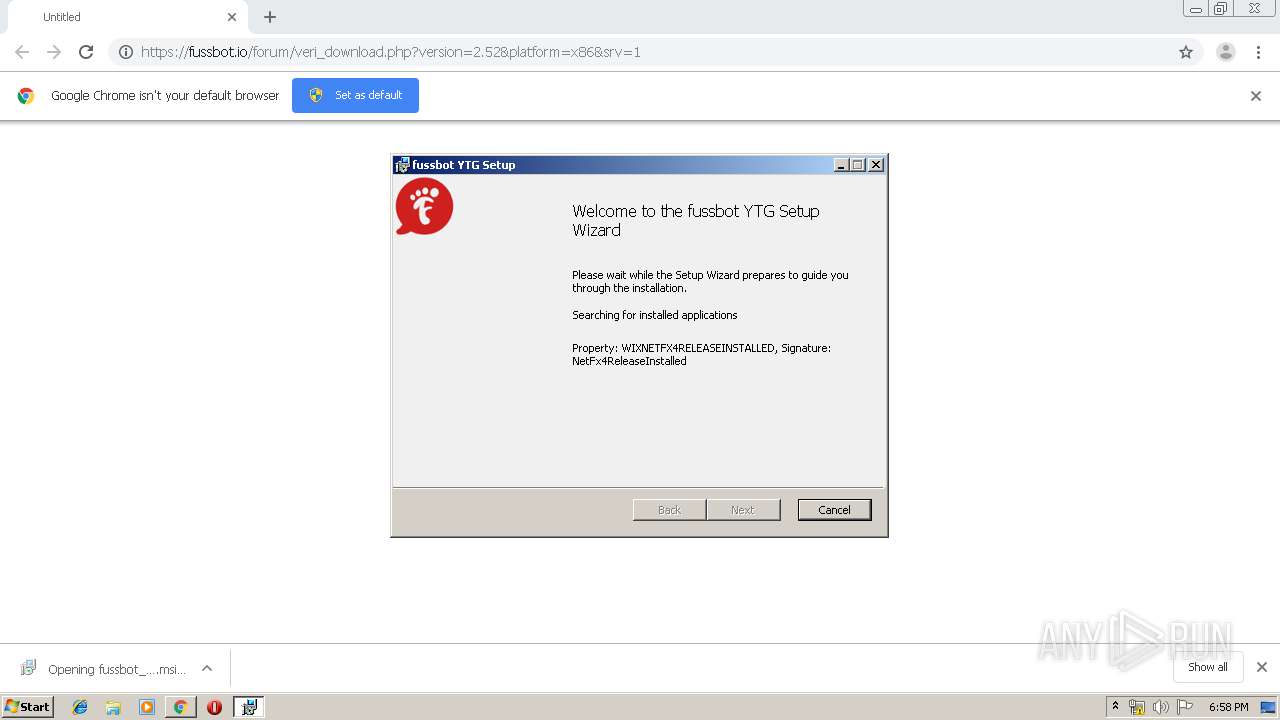
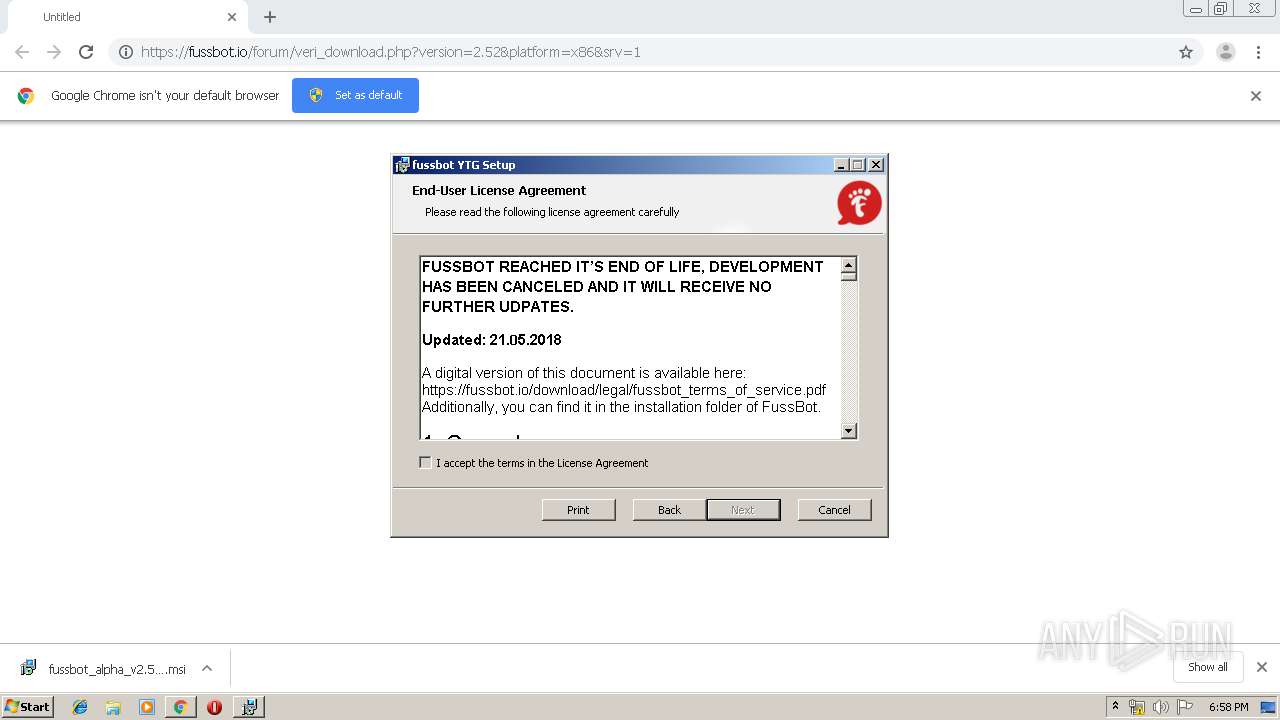
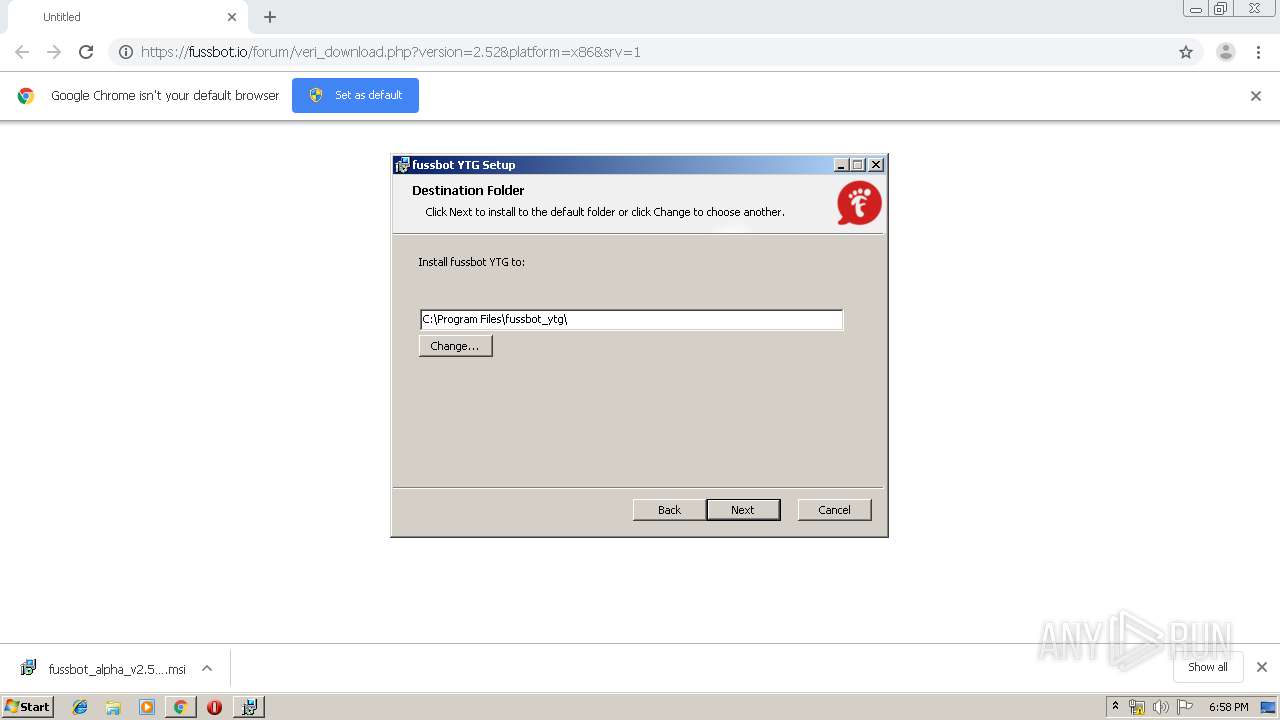
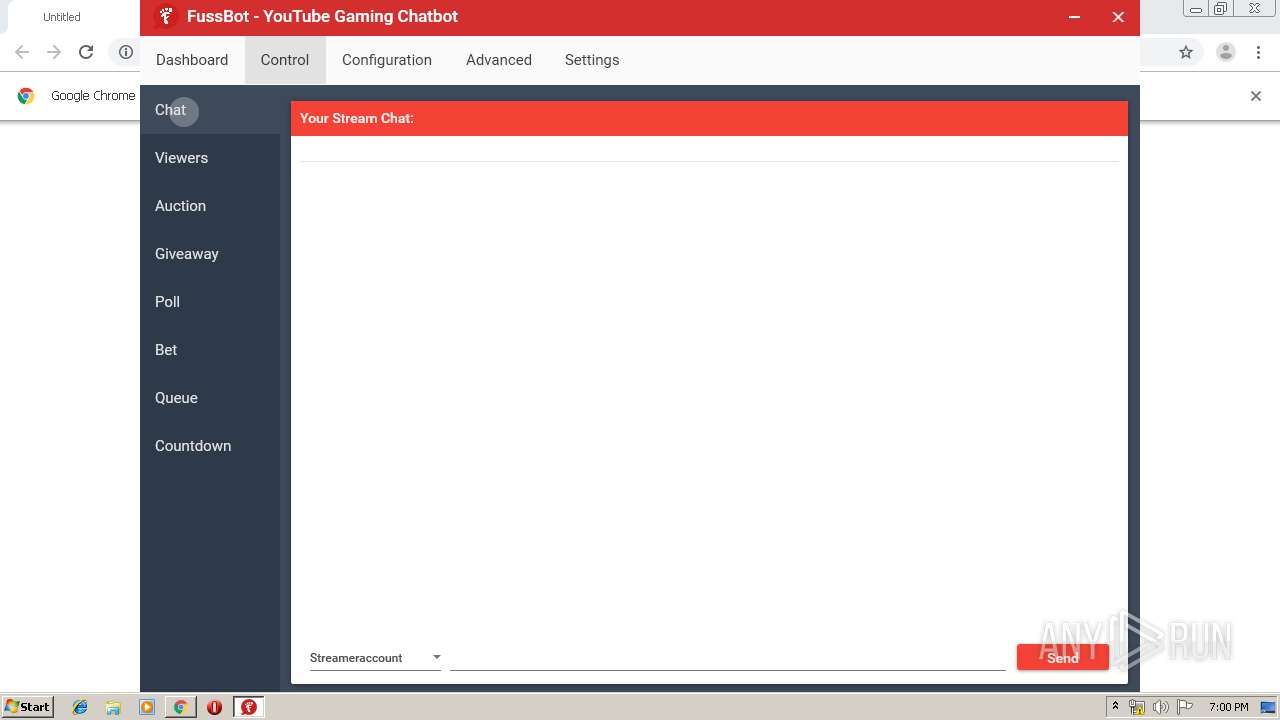
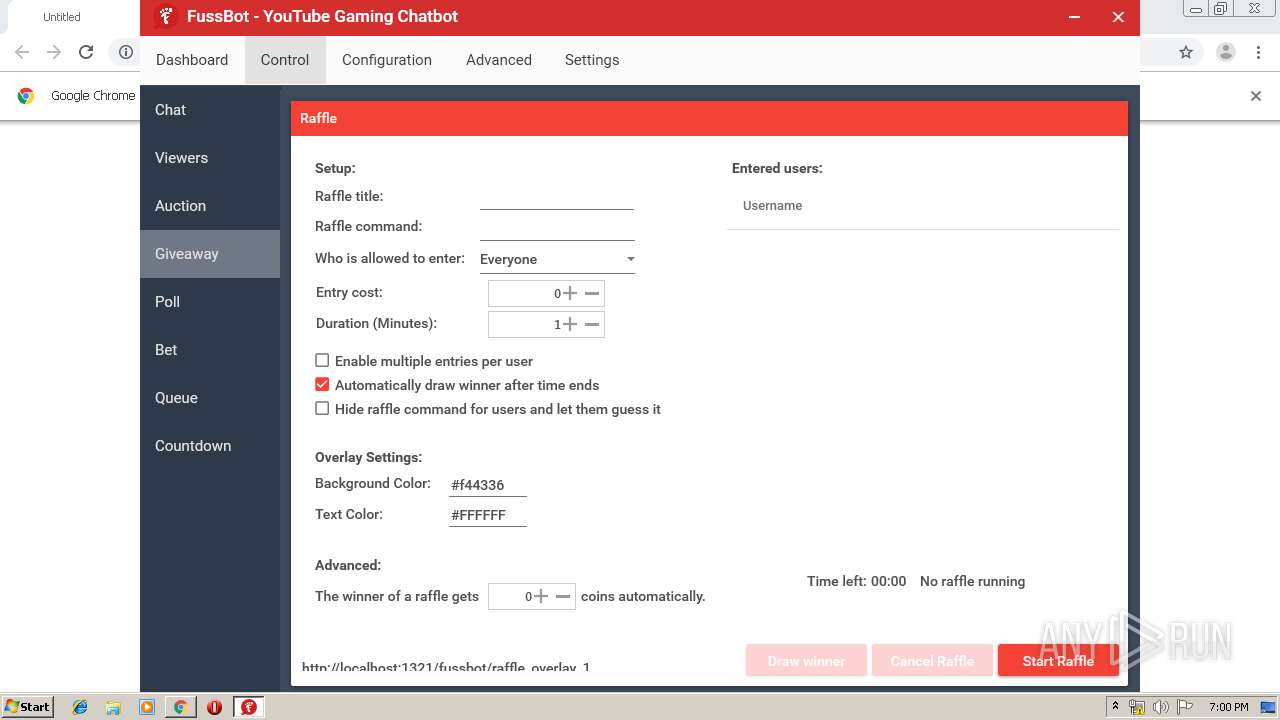
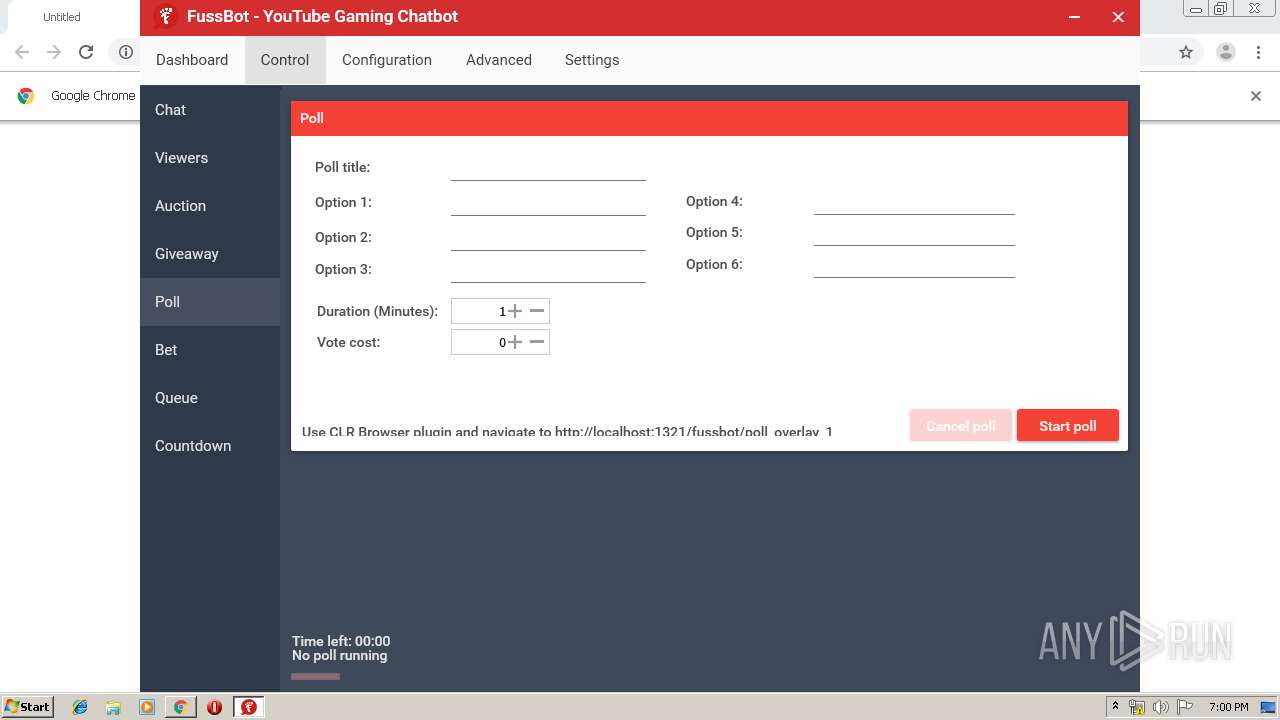
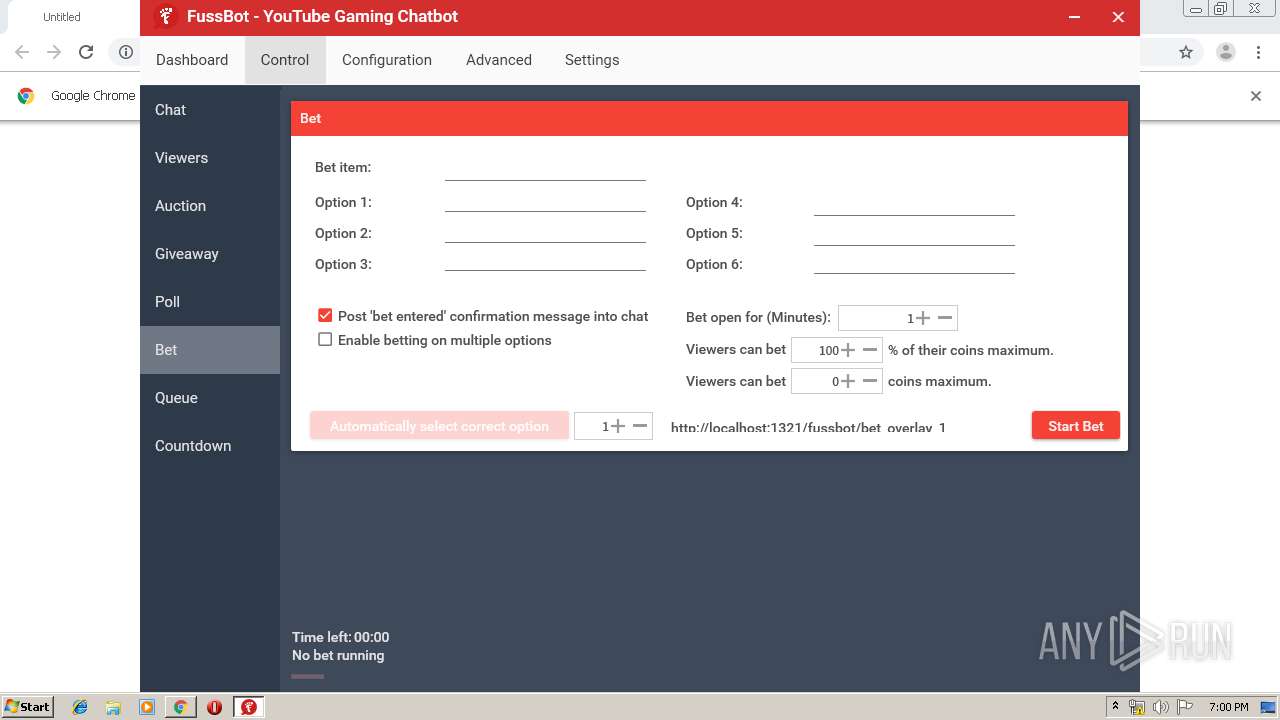
| URL: | https://fussbot.io/forum/veri_download.php?version=2.52&platform=x86&srv=1 |
| Full analysis: | https://app.any.run/tasks/c45d485a-9599-44e9-b5ff-9da9f35f4908 |
| Verdict: | Malicious activity |
| Analysis date: | September 08, 2019, 17:57:06 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MD5: | 0200F1A99733B0DA684599F8531CC9E2 |
| SHA1: | 3E15FFFE0E837F40E37B6CAD406EEEF2CE614713 |
| SHA256: | 834559515309FED386221E83AA33562C44527D5679AB49B5C2C711A9C661798F |
| SSDEEP: | 3:N820KDu9T3xXLQZ1fu9:22ze3RLQZ1M |
MALICIOUS
Application was dropped or rewritten from another process
- fussbot.exe (PID: 2688)
- CefSharp.BrowserSubprocess.exe (PID: 4020)
Loads dropped or rewritten executable
- rundll32.exe (PID: 3684)
- fussbot.exe (PID: 2688)
- CefSharp.BrowserSubprocess.exe (PID: 4020)
SUSPICIOUS
Starts Microsoft Installer
- chrome.exe (PID: 3400)
Executed via COM
- DrvInst.exe (PID: 2884)
Executed as Windows Service
- vssvc.exe (PID: 3480)
Executable content was dropped or overwritten
- msiexec.exe (PID: 4060)
- rundll32.exe (PID: 3684)
Uses RUNDLL32.EXE to load library
- MsiExec.exe (PID: 2060)
Uses NETSH.EXE for network configuration
- cmd.exe (PID: 3708)
- cmd.exe (PID: 1132)
Creates files in the user directory
- fussbot.exe (PID: 2688)
Reads Environment values
- fussbot.exe (PID: 2688)
Modifies files in Chrome extension folder
- chrome.exe (PID: 3400)
Creates COM task schedule object
- msiexec.exe (PID: 4060)
Creates files in the program directory
- fussbot.exe (PID: 2688)
Reads Internet Cache Settings
- fussbot.exe (PID: 2688)
Reads internet explorer settings
- fussbot.exe (PID: 2688)
Starts CMD.EXE for commands execution
- rundll32.exe (PID: 3684)
INFO
Application launched itself
- chrome.exe (PID: 3400)
- msiexec.exe (PID: 4060)
Reads Internet Cache Settings
- chrome.exe (PID: 3400)
Reads the hosts file
- chrome.exe (PID: 2852)
- chrome.exe (PID: 3400)
- fussbot.exe (PID: 2688)
Low-level read access rights to disk partition
- vssvc.exe (PID: 3480)
Searches for installed software
- msiexec.exe (PID: 4060)
Dropped object may contain Bitcoin addresses
- msiexec.exe (PID: 4060)
Reads settings of System Certificates
- chrome.exe (PID: 2852)
- fussbot.exe (PID: 2688)
Creates files in the user directory
- chrome.exe (PID: 3400)
Creates files in the program directory
- msiexec.exe (PID: 4060)
Creates a software uninstall entry
- msiexec.exe (PID: 4060)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
75
Monitored processes
34
Malicious processes
5
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 364 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --field-trial-handle=1008,5120036345417503058,4639523304978371558,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=utility --service-request-channel-token=5920303672691236665 --mojo-platform-channel-handle=752 --ignored=" --type=renderer " /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 976 | netsh http show urlacl url=http://localhost:1321/fussbot/ | C:\Windows\system32\netsh.exe | — | cmd.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Network Command Shell Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1132 | "cmd.exe" /c netsh http add urlacl url=http://localhost:1321/fussbot/ user=Everyone | C:\Windows\system32\cmd.exe | — | rundll32.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 1700 | netsh http add urlacl url=http://localhost:1321/fussbot/ user=Everyone | C:\Windows\System32\netsh.exe | — | cmd.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Network Command Shell Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2056 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --field-trial-handle=1008,5120036345417503058,4639523304978371558,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=utility --service-request-channel-token=13628749004765268145 --mojo-platform-channel-handle=580 --ignored=" --type=renderer " /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 2060 | C:\Windows\system32\MsiExec.exe -Embedding 15DBA8A0C427B6B2C2F46AC02991F5DC M Global\MSI0000 | C:\Windows\system32\MsiExec.exe | — | msiexec.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows® installer Exit code: 0 Version: 5.0.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2072 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --field-trial-handle=1008,5120036345417503058,4639523304978371558,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=utility --service-request-channel-token=5678711156316731013 --mojo-platform-channel-handle=3844 --ignored=" --type=renderer " /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 2196 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --field-trial-handle=1008,5120036345417503058,4639523304978371558,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=utility --service-request-channel-token=14309893825394381551 --mojo-platform-channel-handle=3544 --ignored=" --type=renderer " /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 2392 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --field-trial-handle=1008,5120036345417503058,4639523304978371558,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=utility --service-request-channel-token=16322075860979404154 --mojo-platform-channel-handle=3480 --ignored=" --type=renderer " /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 2440 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --field-trial-handle=1008,5120036345417503058,4639523304978371558,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=utility --service-request-channel-token=8380715306364752220 --mojo-platform-channel-handle=3536 --ignored=" --type=renderer " /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
Total events
3 523
Read events
1 623
Write events
1 883
Delete events
17
Modification events
| (PID) Process: | (3400) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BLBeacon |
| Operation: | write | Name: | failed_count |
Value: 0 | |||
| (PID) Process: | (3400) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BLBeacon |
| Operation: | write | Name: | state |
Value: 2 | |||
| (PID) Process: | (3400) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\ThirdParty |
| Operation: | write | Name: | StatusCodes |
Value: | |||
| (PID) Process: | (3400) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\ThirdParty |
| Operation: | write | Name: | StatusCodes |
Value: 01000000 | |||
| (PID) Process: | (3400) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BLBeacon |
| Operation: | write | Name: | state |
Value: 1 | |||
| (PID) Process: | (3424) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BrowserExitCodes |
| Operation: | write | Name: | 3400-13212439040553625 |
Value: 259 | |||
| (PID) Process: | (3400) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Update\ClientState\{8A69D345-D564-463c-AFF1-A69D9E530F96} |
| Operation: | write | Name: | dr |
Value: 1 | |||
| (PID) Process: | (3400) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome |
| Operation: | write | Name: | UsageStatsInSample |
Value: 0 | |||
| (PID) Process: | (3400) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BrowserExitCodes |
| Operation: | delete value | Name: | 1512-13197841398593750 |
Value: 0 | |||
| (PID) Process: | (3400) chrome.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Google\Update\ClientStateMedium\{8A69D345-D564-463C-AFF1-A69D9E530F96} |
| Operation: | write | Name: | usagestats |
Value: 0 | |||
Executable files
85
Suspicious files
34
Text files
322
Unknown types
67
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3400 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\d912d296-34bb-421c-b529-b95298761782.tmp | — | |
MD5:— | SHA256:— | |||
| 3400 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\data_reduction_proxy_leveldb\000020.dbtmp | — | |
MD5:— | SHA256:— | |||
| 3400 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\BudgetDatabase\LOG.old~RF169d7d.TMP | text | |
MD5:— | SHA256:— | |||
| 3400 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Site Characteristics Database\LOG.old | text | |
MD5:— | SHA256:— | |||
| 3400 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\shared_proto_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 3400 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Feature Engagement Tracker\EventDB\LOG.old~RF169d8d.TMP | text | |
MD5:— | SHA256:— | |||
| 3400 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Session Storage\LOG.old | text | |
MD5:— | SHA256:— | |||
| 3400 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\ShaderCache\GPUCache\data_1 | — | |
MD5:— | SHA256:— | |||
| 3400 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\data_reduction_proxy_leveldb\LOG.old | text | |
MD5:— | SHA256:— | |||
| 3400 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Site Characteristics Database\LOG.old~RF169d1f.TMP | text | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
5
TCP/UDP connections
29
DNS requests
19
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2852 | chrome.exe | GET | 302 | 172.217.18.14:80 | http://redirector.gvt1.com/edgedl/chromewebstore/L2Nocm9tZV9leHRlbnNpb24vYmxvYnMvOWVmQUFXS041NV9ZVXlJVWwxbGc5TUM4dw/7519.422.0.3_pkedcjkdefgpdelpbcmbmeomcjbeemfm.crx | US | html | 514 b | whitelisted |
2688 | fussbot.exe | GET | 302 | 188.68.47.24:80 | http://fussbot.io/download/updater/current_version.txt | DE | html | 299 b | whitelisted |
2688 | fussbot.exe | GET | 302 | 188.68.47.24:80 | http://fussbot.io/download/updater/current_changelog.txt | DE | html | 301 b | whitelisted |
2688 | fussbot.exe | POST | 200 | 172.217.16.206:80 | http://www.google-analytics.com/collect | US | image | 35 b | whitelisted |
2852 | chrome.exe | GET | 200 | 173.194.150.135:80 | http://r1---sn-f5f7ln7s.gvt1.com/edgedl/chromewebstore/L2Nocm9tZV9leHRlbnNpb24vYmxvYnMvOWVmQUFXS041NV9ZVXlJVWwxbGc5TUM4dw/7519.422.0.3_pkedcjkdefgpdelpbcmbmeomcjbeemfm.crx?cms_redirect=yes&mip=212.7.222.142&mm=28&mn=sn-f5f7ln7s&ms=nvh&mt=1567965037&mv=u&mvi=0&pl=23&shardbypass=yes | US | crx | 862 Kb | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2852 | chrome.exe | 172.217.18.4:443 | www.google.com | Google Inc. | US | whitelisted |
2852 | chrome.exe | 172.217.22.3:443 | ssl.gstatic.com | Google Inc. | US | whitelisted |
2852 | chrome.exe | 172.217.22.46:443 | clients4.google.com | Google Inc. | US | whitelisted |
2852 | chrome.exe | 172.217.18.174:443 | sb-ssl.google.com | Google Inc. | US | whitelisted |
2852 | chrome.exe | 216.58.208.35:443 | www.gstatic.com | Google Inc. | US | whitelisted |
2688 | fussbot.exe | 172.217.18.170:443 | www.googleapis.com | Google Inc. | US | whitelisted |
2688 | fussbot.exe | 172.217.16.206:80 | www.google-analytics.com | Google Inc. | US | whitelisted |
2688 | fussbot.exe | 188.68.47.24:80 | fussbot.io | netcup GmbH | DE | unknown |
2688 | fussbot.exe | 188.68.47.24:443 | fussbot.io | netcup GmbH | DE | unknown |
2688 | fussbot.exe | 172.64.103.13:443 | cookieinfoscript.com | Cloudflare Inc | US | shared |
DNS requests
Domain | IP | Reputation |
|---|---|---|
clientservices.googleapis.com |
| whitelisted |
fussbot.io |
| whitelisted |
accounts.google.com |
| shared |
srv1.fussdl.de |
| unknown |
www.google.com |
| malicious |
ssl.gstatic.com |
| whitelisted |
clients4.google.com |
| whitelisted |
www.gstatic.com |
| whitelisted |
sb-ssl.google.com |
| whitelisted |
clients1.google.com |
| whitelisted |
Threats
Process | Message |
|---|---|
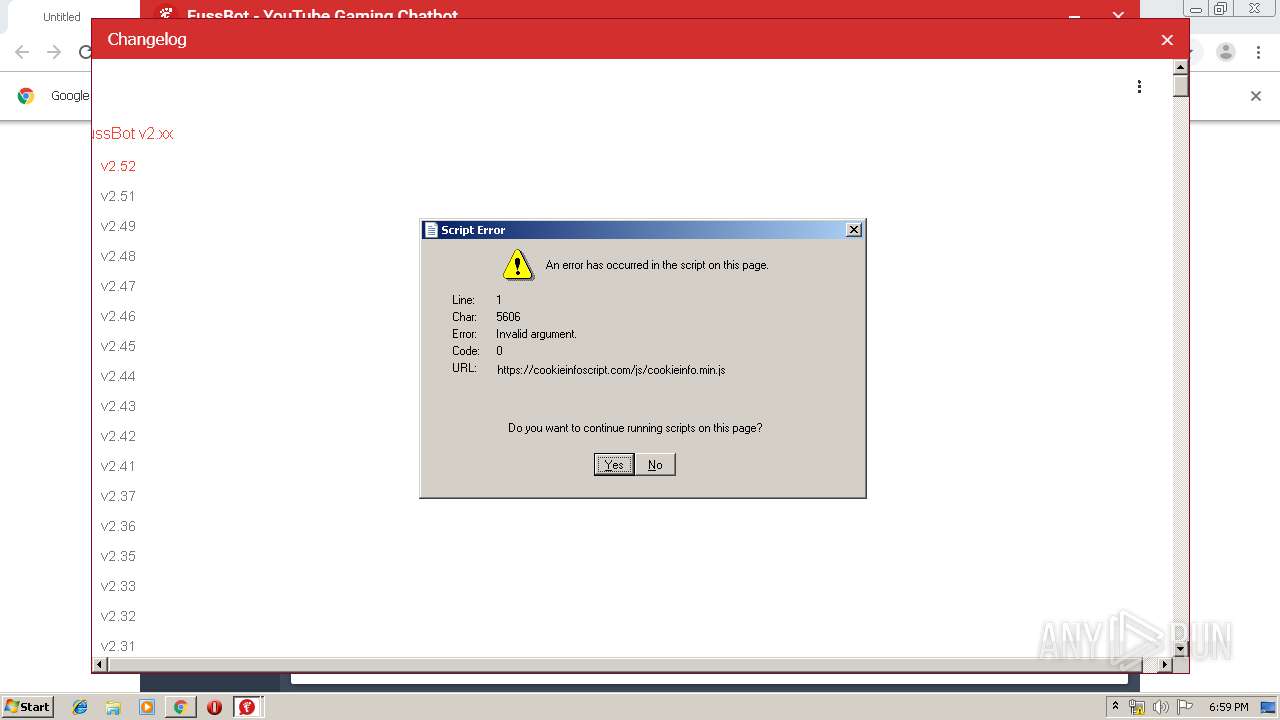
fussbot.exe | Native library pre-loader is trying to load native SQLite library "C:\Program Files\fussbot_ytg\x86\SQLite.Interop.dll"...
|
fussbot.exe | SQLite error (1): no such table: viewers_changes
|