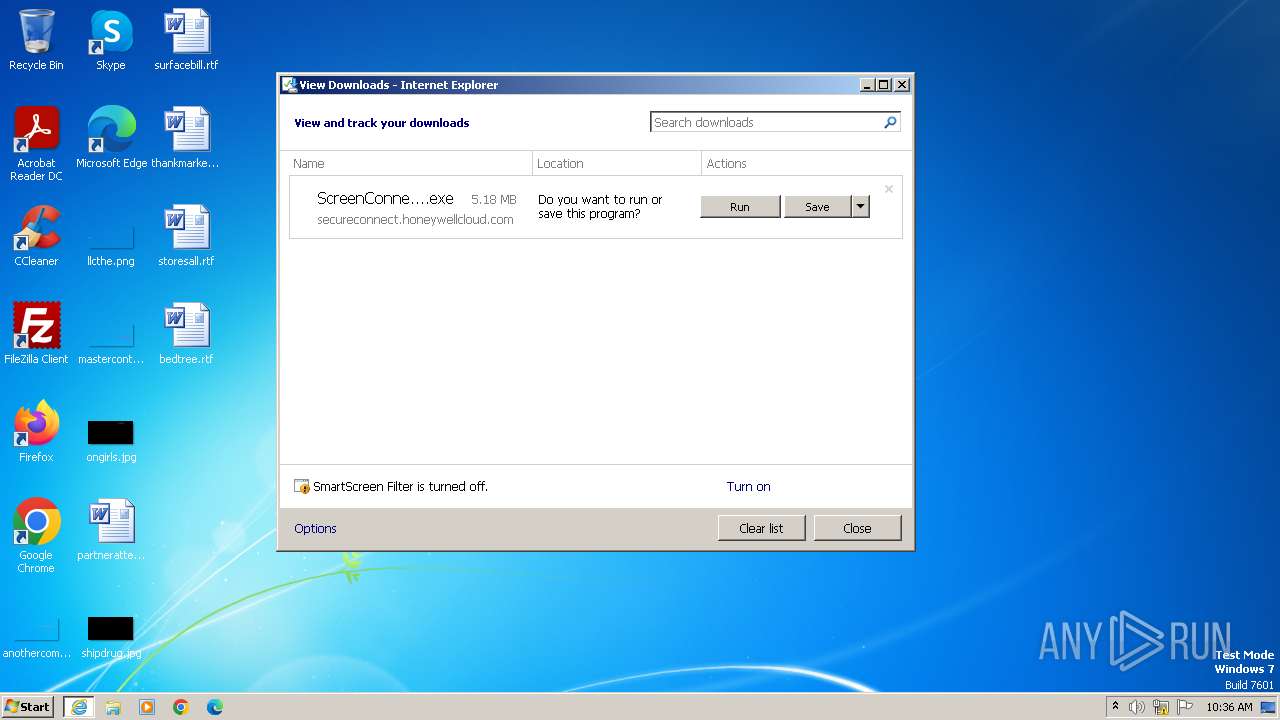
| URL: | https://secureconnect.honeywellcloud.com/Bin/ScreenConnect.ClientSetup.exe?e=Access&y=Guest&c=AUB%20Bank&c=Bahrain&c=Sayed%20Hussain&c=E482322&c=Sayed.Hussain%40Honeywell.com&c=KSA-EBI-META&c=&c= |
| Full analysis: | https://app.any.run/tasks/4b1eca19-7b99-4b1f-b4ab-dafbc445604e |
| Verdict: | Malicious activity |
| Analysis date: | November 26, 2023, 10:36:04 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| SHA1: | 08777B3FBFC9EB3E904936ACDA1A96346408D074 |
| SHA256: | 83445B9BB07DABC76745608D064C20C1D25337C0DCE47759865E34E99C97BD6E |
| SSDEEP: | 6:2Z2L1cuZcFKCF/G5AWYP21kTo7QGYgkZMIMLltY:2Z2L1mFg5AL2aRjZUhq |
MALICIOUS
Drops the executable file immediately after the start
- msiexec.exe (PID: 2316)
Creates a writable file in the system directory
- ScreenConnect.ClientService.exe (PID: 3172)
SCREENCONNECT has been detected (SURICATA)
- ScreenConnect.ClientService.exe (PID: 3172)
Connects to the CnC server
- ScreenConnect.ClientService.exe (PID: 3172)
SUSPICIOUS
Reads the Internet Settings
- ScreenConnect.ClientSetup.exe (PID: 3924)
- ScreenConnect.WindowsClient.exe (PID: 1872)
Executes as Windows Service
- VSSVC.exe (PID: 2072)
- ScreenConnect.ClientService.exe (PID: 3172)
The process creates files with name similar to system file names
- msiexec.exe (PID: 2316)
Creates or modifies Windows services
- ScreenConnect.ClientService.exe (PID: 3172)
Uses RUNDLL32.EXE to load library
- msiexec.exe (PID: 3208)
INFO
Reads the computer name
- wmpnscfg.exe (PID: 2820)
- ScreenConnect.ClientSetup.exe (PID: 3924)
- msiexec.exe (PID: 2316)
- msiexec.exe (PID: 3208)
- msiexec.exe (PID: 3600)
- msiexec.exe (PID: 3944)
- ScreenConnect.ClientService.exe (PID: 3172)
- ScreenConnect.WindowsClient.exe (PID: 1872)
- ScreenConnect.WindowsClient.exe (PID: 2904)
Manual execution by a user
- wmpnscfg.exe (PID: 2820)
Application launched itself
- iexplore.exe (PID: 2856)
- msiexec.exe (PID: 2316)
Drops the executable file immediately after the start
- iexplore.exe (PID: 3024)
- iexplore.exe (PID: 2856)
- msiexec.exe (PID: 1360)
- rundll32.exe (PID: 3396)
Checks supported languages
- wmpnscfg.exe (PID: 2820)
- ScreenConnect.ClientSetup.exe (PID: 3924)
- msiexec.exe (PID: 2316)
- msiexec.exe (PID: 3208)
- msiexec.exe (PID: 3600)
- ScreenConnect.ClientService.exe (PID: 3172)
- msiexec.exe (PID: 3944)
- ScreenConnect.WindowsClient.exe (PID: 1872)
- ScreenConnect.WindowsClient.exe (PID: 2904)
Reads the machine GUID from the registry
- wmpnscfg.exe (PID: 2820)
- ScreenConnect.ClientSetup.exe (PID: 3924)
- msiexec.exe (PID: 2316)
- msiexec.exe (PID: 3600)
- msiexec.exe (PID: 3944)
- ScreenConnect.ClientService.exe (PID: 3172)
- msiexec.exe (PID: 3208)
- ScreenConnect.WindowsClient.exe (PID: 1872)
- ScreenConnect.WindowsClient.exe (PID: 2904)
The process uses the downloaded file
- iexplore.exe (PID: 2856)
Create files in a temporary directory
- ScreenConnect.ClientSetup.exe (PID: 3924)
- rundll32.exe (PID: 3396)
- msiexec.exe (PID: 2316)
Reads CPU info
- ScreenConnect.WindowsClient.exe (PID: 2904)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
56
Monitored processes
15
Malicious processes
2
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
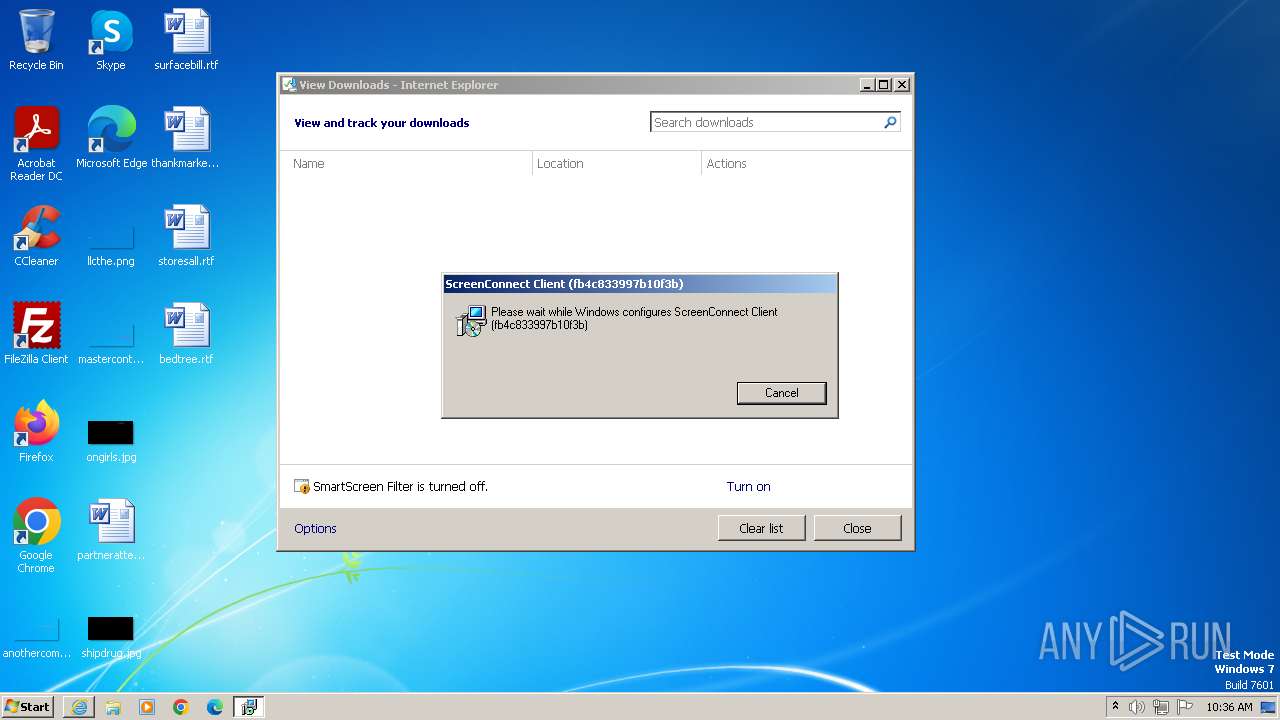
| 1360 | "C:\Windows\System32\msiexec.exe" /i "C:\Users\admin\AppData\Local\Temp\ScreenConnect\fb4c833997b10f3b\setup.msi" | C:\Windows\System32\msiexec.exe | — | ScreenConnect.ClientSetup.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows® installer Exit code: 0 Version: 5.0.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1872 | "C:\Program Files\ScreenConnect Client (fb4c833997b10f3b)\ScreenConnect.WindowsClient.exe" "RunRole" "d15408fe-a728-4923-aeaa-efc23cb5b5cf" "User" | C:\Program Files\ScreenConnect Client (fb4c833997b10f3b)\ScreenConnect.WindowsClient.exe | — | ScreenConnect.ClientService.exe | |||||||||||
User: admin Company: ScreenConnect Software Integrity Level: MEDIUM Description: ScreenConnect Client Exit code: 0 Version: 23.8.1.8686 Modules
| |||||||||||||||
| 2072 | C:\Windows\system32\vssvc.exe | C:\Windows\System32\VSSVC.exe | — | services.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Microsoft® Volume Shadow Copy Service Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2316 | C:\Windows\system32\msiexec.exe /V | C:\Windows\System32\msiexec.exe | — | services.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows® installer Exit code: 0 Version: 5.0.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2432 | "C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\78RFYB7Z\ScreenConnect.ClientSetup.exe" | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\78RFYB7Z\ScreenConnect.ClientSetup.exe | — | iexplore.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 3221226540 Modules
| |||||||||||||||
| 2820 | "C:\Program Files\Windows Media Player\wmpnscfg.exe" | C:\Program Files\Windows Media Player\wmpnscfg.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Media Player Network Sharing Service Configuration Application Exit code: 0 Version: 12.0.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2856 | "C:\Program Files\Internet Explorer\iexplore.exe" "https://secureconnect.honeywellcloud.com/Bin/ScreenConnect.ClientSetup.exe?e=Access&y=Guest&c=AUB%20Bank&c=Bahrain&c=Sayed%20Hussain&c=E482322&c=Sayed.Hussain%40Honeywell.com&c=KSA-EBI-META&c=&c=" | C:\Program Files\Internet Explorer\iexplore.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 2904 | "C:\Program Files\ScreenConnect Client (fb4c833997b10f3b)\ScreenConnect.WindowsClient.exe" "RunRole" "4bf7d33f-c276-4737-832a-891d4de02f28" "System" | C:\Program Files\ScreenConnect Client (fb4c833997b10f3b)\ScreenConnect.WindowsClient.exe | — | ScreenConnect.ClientService.exe | |||||||||||
User: SYSTEM Company: ScreenConnect Software Integrity Level: SYSTEM Description: ScreenConnect Client Exit code: 0 Version: 23.8.1.8686 Modules
| |||||||||||||||
| 3024 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:2856 CREDAT:267521 /prefetch:2 | C:\Program Files\Internet Explorer\iexplore.exe | iexplore.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 3172 | "C:\Program Files\ScreenConnect Client (fb4c833997b10f3b)\ScreenConnect.ClientService.exe" "?e=Access&y=Guest&h=screlay.honeywellcloud.com&p=443&s=161e92d8-52b2-45ab-88e9-cd6134a2407c&k=BgIAAACkAABSU0ExAAgAAAEAAQAj2ASeRAOdsLfwObXg3jgoM9%2f5OvKC9Uvi7ypgNXQwdTQG6i8th7X0rLWGtj6KXUN7EMfpk7J375sz92p8C6vGv0FvmCeBbtHqy6DKeQfXz2%2fyp3tfJIM4sKSTK0f1sEa8QiYCbh5QE7hHUzyqjWgrFjzYkrceb4cgwzFcRQk%2bhGmYWps579bbP1vH5I321b90RlV92iyX%2fL48avtY81Y9TIwGhsUqJPwt2lGPJ9%2f%2fXURGfZniGu6CQNZ5sMnll7ZH%2fE5IXobUNg2itlulbaQPyCxzFe5BfBAVszgTkqh9UWOZVlrW9ZPQJAXXbi9Ta3cEGFPdUSquTk1UDMNZuzea&c=AUB%20Bank&c=Bahrain&c=Sayed%20Hussain&c=E482322&c=Sayed.Hussain%40Honeywell.com&c=KSA-EBI-META&c=&c=" | C:\Program Files\ScreenConnect Client (fb4c833997b10f3b)\ScreenConnect.ClientService.exe | services.exe | ||||||||||||
User: SYSTEM Integrity Level: SYSTEM Exit code: 0 Version: 23.8.1.8686 Modules
| |||||||||||||||
Total events
16 165
Read events
16 057
Write events
95
Delete events
13
Modification events
| (PID) Process: | (2856) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPDaysSinceLastAutoMigration |
Value: 0 | |||
| (PID) Process: | (2856) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPLastLaunchHighDateTime |
Value: 30847387 | |||
| (PID) Process: | (2856) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateHighDateTime |
Value: 30847437 | |||
| (PID) Process: | (2856) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (2856) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (2856) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Main |
| Operation: | write | Name: | CompatibilityFlags |
Value: 0 | |||
| (PID) Process: | (2856) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (2856) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (2856) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
| (PID) Process: | (2856) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 0 | |||
Executable files
17
Suspicious files
22
Text files
11
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3924 | ScreenConnect.ClientSetup.exe | C:\Users\admin\AppData\Local\Temp\ScreenConnect\fb4c833997b10f3b\setup.msi | — | |
MD5:— | SHA256:— | |||
| 2316 | msiexec.exe | C:\System Volume Information\SPP\metadata-2 | — | |
MD5:— | SHA256:— | |||
| 2316 | msiexec.exe | C:\Windows\Installer\1c13fd.msi | — | |
MD5:— | SHA256:— | |||
| 2856 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Internet Explorer\Recovery\Active\{9CFAFC4B-8C47-11EE-A826-12A9866C77DE}.dat | binary | |
MD5:4C3649431F1B745F2DC6047CE24D12AF | SHA256:8643038A88FFB676B39D8D13AF18DD1056AD5EB1F4E7631EB99A3D4C551B818F | |||
| 3024 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\57C8EDB95DF3F0AD4EE2DC2B8CFD4157 | compressed | |
MD5:1BFE591A4FE3D91B03CDF26EAACD8F89 | SHA256:9CF94355051BF0F4A45724CA20D1CC02F76371B963AB7D1E38BD8997737B13D8 | |||
| 3024 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\MFAQUS6V\ScreenConnect.ClientSetup[1].exe | executable | |
MD5:BAFF53102BAB133BC81DA53F5C4EE3D7 | SHA256:8B6950E8F3D2A5B6705A10E20CFE9D1CB1FAEF27AA92E8745FA93070B153D537 | |||
| 3024 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\78RFYB7Z\ScreenConnect.ClientSetup.exe.5hfutc5.partial | executable | |
MD5:628F2596799B5EED516DE20A4067470C | SHA256:C8606F2B1432D18B4D11D83FD0275F5983245A5962E60DDB8D51C674FD8934C7 | |||
| 3024 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\EDC238BFF48A31D55A97E1E93892934B_C20E0DA2D0F89FE526E1490F4A2EE5AB | binary | |
MD5:ED5BE6D3A0AA575DCAB5F93B725E221B | SHA256:0E7614D2012E46875F5C920AD0D59D5BFBCE2B581F4509382C6BB0BB7C1396D5 | |||
| 3024 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\57C8EDB95DF3F0AD4EE2DC2B8CFD4157 | binary | |
MD5:B9D4554DE466A9C0392B4E7A2C1A1D62 | SHA256:E97B6DE38D23A65E56BA6CCAD5BD5E9CBCA66A87D8E35A6713E9F821D2C90ED9 | |||
| 3024 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\EDC238BFF48A31D55A97E1E93892934B_C20E0DA2D0F89FE526E1490F4A2EE5AB | binary | |
MD5:4C1C379E0F101BBBDE83F982E3F8CD9E | SHA256:2A5A2ABD86DABAAA6FE5A3F8E7671D200A9E963566130F0847BEDB76F3CAFAEA | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
6
TCP/UDP connections
16
DNS requests
6
Threats
2
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3024 | iexplore.exe | GET | 200 | 67.27.157.126:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?0e152650b56312b4 | unknown | compressed | 4.66 Kb | unknown |
1080 | svchost.exe | GET | 304 | 67.27.157.126:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?5c94acfb5b892539 | unknown | — | — | unknown |
3024 | iexplore.exe | GET | 200 | 67.27.157.126:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?be0537bbbaca182f | unknown | compressed | 4.66 Kb | unknown |
1080 | svchost.exe | GET | 200 | 67.27.157.126:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/authrootstl.cab?68f52e492152febd | unknown | compressed | 61.6 Kb | unknown |
2856 | iexplore.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | binary | 471 b | unknown |
3024 | iexplore.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTfqhLjKLEJQZPin0KCzkdAQpVYowQUsT7DaQP4v0cB1JgmGggC72NkK8MCEATh56TcXPLzbcArQrhdFZ8%3D | unknown | binary | 471 b | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
3024 | iexplore.exe | 20.72.175.38:443 | secureconnect.honeywellcloud.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | unknown |
1080 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
3024 | iexplore.exe | 67.27.157.126:80 | ctldl.windowsupdate.com | LEVEL3 | US | unknown |
2588 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
3024 | iexplore.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
1080 | svchost.exe | 67.27.157.126:80 | ctldl.windowsupdate.com | LEVEL3 | US | unknown |
3172 | ScreenConnect.ClientService.exe | 52.190.37.34:443 | screlay.honeywellcloud.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | unknown |
2856 | iexplore.exe | 152.199.19.161:443 | iecvlist.microsoft.com | EDGECAST | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
secureconnect.honeywellcloud.com |
| unknown |
ctldl.windowsupdate.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
screlay.honeywellcloud.com |
| unknown |
iecvlist.microsoft.com |
| whitelisted |
r20swj13mr.microsoft.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
3172 | ScreenConnect.ClientService.exe | Misc activity | ET INFO ScreenConnect/ConnectWise Initial Checkin Packet M2 |
3172 | ScreenConnect.ClientService.exe | Potential Corporate Privacy Violation | REMOTE [ANY.RUN] ScreenConnect Server Response |