| File name: | 8342c29aacd500b5d424822648331736379f18bdb6bc27a7e7a579544570fa8a.exe |
| Full analysis: | https://app.any.run/tasks/a7d8abe6-f1f4-4952-91da-c15c5f86b4e4 |
| Verdict: | Malicious activity |
| Analysis date: | May 26, 2024, 08:03:17 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows |
| MD5: | 236B78F3CD3A0B771D318F044DDA8F45 |
| SHA1: | F890CA2FFB6218FA01DF6844FE2A51B184E912B8 |
| SHA256: | 8342C29AACD500B5D424822648331736379F18BDB6BC27A7E7A579544570FA8A |
| SSDEEP: | 393216:s66QNHED1sPOw2+2PKZ5URAtXMdswoCOeaIaQ4ptHkiMbq:stQpED18b2PKZptX3hIFgtHpMO |
MALICIOUS
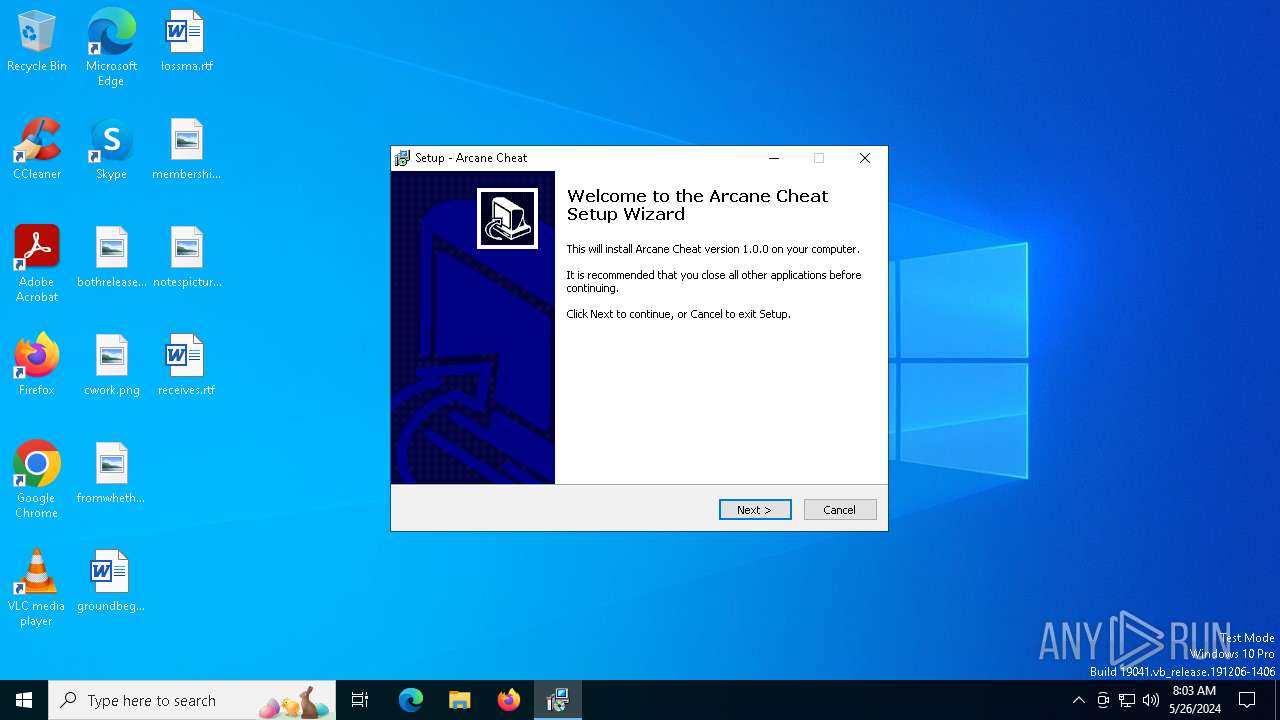
Drops the executable file immediately after the start
- 8342c29aacd500b5d424822648331736379f18bdb6bc27a7e7a579544570fa8a.exe (PID: 6408)
- Arcane CheatSetup.exe (PID: 6452)
- Arcane Cheat.exe (PID: 6508)
- Arcane CheatSetup.exe (PID: 6676)
- Arcane CheatSetup.tmp (PID: 6728)
Uses sleep, probably for evasion detection (SCRIPT)
- wscript.exe (PID: 6592)
SUSPICIOUS
Reads security settings of Internet Explorer
- 8342c29aacd500b5d424822648331736379f18bdb6bc27a7e7a579544570fa8a.exe (PID: 6408)
- Arcane CheatSetup.tmp (PID: 6524)
- Arcane Cheat.exe (PID: 6508)
Reads the date of Windows installation
- 8342c29aacd500b5d424822648331736379f18bdb6bc27a7e7a579544570fa8a.exe (PID: 6408)
- Arcane CheatSetup.tmp (PID: 6524)
- Arcane Cheat.exe (PID: 6508)
Executable content was dropped or overwritten
- 8342c29aacd500b5d424822648331736379f18bdb6bc27a7e7a579544570fa8a.exe (PID: 6408)
- Arcane CheatSetup.exe (PID: 6452)
- Arcane Cheat.exe (PID: 6508)
- Arcane CheatSetup.exe (PID: 6676)
- Arcane CheatSetup.tmp (PID: 6728)
Starts CMD.EXE for commands execution
- wscript.exe (PID: 6592)
Runs shell command (SCRIPT)
- wscript.exe (PID: 6592)
Executing commands from a ".bat" file
- wscript.exe (PID: 6592)
Process drops legitimate windows executable
- Arcane CheatSetup.tmp (PID: 6728)
Device Retrieving External IP Address Detected
- browserwinsvc.exe (PID: 6864)
Checks for external IP
- browserwinsvc.exe (PID: 6864)
Reads the Windows owner or organization settings
- Arcane CheatSetup.tmp (PID: 6728)
The process drops C-runtime libraries
- Arcane CheatSetup.tmp (PID: 6728)
INFO
Checks supported languages
- 8342c29aacd500b5d424822648331736379f18bdb6bc27a7e7a579544570fa8a.exe (PID: 6408)
- Arcane CheatSetup.exe (PID: 6452)
- Arcane Cheat.exe (PID: 6508)
- Arcane CheatSetup.tmp (PID: 6524)
- Arcane CheatSetup.exe (PID: 6676)
- Arcane CheatSetup.tmp (PID: 6728)
- browserwinsvc.exe (PID: 6864)
- Arcane Cheat.exe (PID: 6784)
- javaw.exe (PID: 6908)
Reads the computer name
- 8342c29aacd500b5d424822648331736379f18bdb6bc27a7e7a579544570fa8a.exe (PID: 6408)
- Arcane Cheat.exe (PID: 6508)
- Arcane CheatSetup.tmp (PID: 6524)
- Arcane CheatSetup.tmp (PID: 6728)
- browserwinsvc.exe (PID: 6864)
- javaw.exe (PID: 6908)
Create files in a temporary directory
- 8342c29aacd500b5d424822648331736379f18bdb6bc27a7e7a579544570fa8a.exe (PID: 6408)
- Arcane CheatSetup.exe (PID: 6452)
- Arcane CheatSetup.exe (PID: 6676)
- Arcane CheatSetup.tmp (PID: 6728)
- javaw.exe (PID: 6908)
Process checks computer location settings
- 8342c29aacd500b5d424822648331736379f18bdb6bc27a7e7a579544570fa8a.exe (PID: 6408)
- Arcane CheatSetup.tmp (PID: 6524)
- Arcane Cheat.exe (PID: 6508)
Reads the machine GUID from the registry
- browserwinsvc.exe (PID: 6864)
- javaw.exe (PID: 6908)
Reads Environment values
- browserwinsvc.exe (PID: 6864)
Disables trace logs
- browserwinsvc.exe (PID: 6864)
Checks proxy server information
- browserwinsvc.exe (PID: 6864)
Creates files in the program directory
- Arcane CheatSetup.tmp (PID: 6728)
Creates files or folders in the user directory
- javaw.exe (PID: 6908)
Creates a software uninstall entry
- Arcane CheatSetup.tmp (PID: 6728)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | InstallShield setup (83.4) |
|---|---|---|
| .exe | | | Win32 Executable (generic) (8.7) |
| .exe | | | Generic Win/DOS Executable (3.8) |
| .exe | | | DOS Executable Generic (3.8) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 1992:06:19 22:22:17+00:00 |
| ImageFileCharacteristics: | Executable, No line numbers, No symbols, Bytes reversed lo, 32-bit, Bytes reversed hi |
| PEType: | PE32 |
| LinkerVersion: | 2.25 |
| CodeSize: | 5120 |
| InitializedDataSize: | 48726016 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x20cc |
| OSVersion: | 4 |
| ImageVersion: | - |
| SubsystemVersion: | 4 |
| Subsystem: | Windows GUI |
Total processes
140
Monitored processes
12
Malicious processes
8
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 6408 | "C:\Users\admin\AppData\Local\Temp\8342c29aacd500b5d424822648331736379f18bdb6bc27a7e7a579544570fa8a.exe" | C:\Users\admin\AppData\Local\Temp\8342c29aacd500b5d424822648331736379f18bdb6bc27a7e7a579544570fa8a.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 6452 | "C:\Users\admin\AppData\Local\Temp\Arcane CheatSetup.exe" | C:\Users\admin\AppData\Local\Temp\Arcane CheatSetup.exe | 8342c29aacd500b5d424822648331736379f18bdb6bc27a7e7a579544570fa8a.exe | ||||||||||||
User: admin Company: Integrity Level: MEDIUM Description: Arcane Cheat Setup Exit code: 0 Version: Modules
| |||||||||||||||
| 6508 | "C:\Users\admin\AppData\Local\Temp\Arcane Cheat.exe" | C:\Users\admin\AppData\Local\Temp\Arcane Cheat.exe | 8342c29aacd500b5d424822648331736379f18bdb6bc27a7e7a579544570fa8a.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 6524 | "C:\Users\admin\AppData\Local\Temp\is-769CC.tmp\Arcane CheatSetup.tmp" /SL5="$A0168,46527891,119296,C:\Users\admin\AppData\Local\Temp\Arcane CheatSetup.exe" | C:\Users\admin\AppData\Local\Temp\is-769CC.tmp\Arcane CheatSetup.tmp | — | Arcane CheatSetup.exe | |||||||||||
User: admin Integrity Level: MEDIUM Description: Setup/Uninstall Exit code: 0 Version: 51.1052.0.0 Modules
| |||||||||||||||
| 6592 | "C:\WINDOWS\System32\WScript.exe" "C:\Surrogateprovidercomponentsessionmonitor\lEI1Ux7.vbe" | C:\Windows\SysWOW64\wscript.exe | — | Arcane Cheat.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft ® Windows Based Script Host Exit code: 0 Version: 5.812.10240.16384 Modules
| |||||||||||||||
| 6676 | "C:\Users\admin\AppData\Local\Temp\Arcane CheatSetup.exe" /SPAWNWND=$70060 /NOTIFYWND=$A0168 | C:\Users\admin\AppData\Local\Temp\Arcane CheatSetup.exe | Arcane CheatSetup.tmp | ||||||||||||
User: admin Company: Integrity Level: HIGH Description: Arcane Cheat Setup Exit code: 0 Version: Modules
| |||||||||||||||
| 6728 | "C:\Users\admin\AppData\Local\Temp\is-F6R4H.tmp\Arcane CheatSetup.tmp" /SL5="$501F6,46527891,119296,C:\Users\admin\AppData\Local\Temp\Arcane CheatSetup.exe" /SPAWNWND=$70060 /NOTIFYWND=$A0168 | C:\Users\admin\AppData\Local\Temp\is-F6R4H.tmp\Arcane CheatSetup.tmp | Arcane CheatSetup.exe | ||||||||||||
User: admin Integrity Level: HIGH Description: Setup/Uninstall Exit code: 0 Version: 51.1052.0.0 Modules
| |||||||||||||||
| 6756 | C:\WINDOWS\system32\cmd.exe /c ""C:\Surrogateprovidercomponentsessionmonitor\bjWdhUfYhC7CKzpdCHePv6eJ.bat" " | C:\Windows\SysWOW64\cmd.exe | — | wscript.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6784 | "C:\Program Files (x86)\Arcane Cheat\Arcane Cheat.exe" | C:\Program Files (x86)\Arcane Cheat\Arcane Cheat.exe | — | Arcane CheatSetup.tmp | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 6804 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
14 060
Read events
13 983
Write events
71
Delete events
6
Modification events
| (PID) Process: | (6408) 8342c29aacd500b5d424822648331736379f18bdb6bc27a7e7a579544570fa8a.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer |
| Operation: | write | Name: | SlowContextMenuEntries |
Value: 6024B221EA3A6910A2DC08002B30309D0A010000BD0E0C47735D584D9CEDE91E22E23282770100000114020000000000C0000000000000468D0000006078A409B011A54DAFA526D86198A780390100009AD298B2EDA6DE11BA8CA68E55D895936E000000 | |||
| (PID) Process: | (6408) 8342c29aacd500b5d424822648331736379f18bdb6bc27a7e7a579544570fa8a.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (6408) 8342c29aacd500b5d424822648331736379f18bdb6bc27a7e7a579544570fa8a.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (6408) 8342c29aacd500b5d424822648331736379f18bdb6bc27a7e7a579544570fa8a.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
| (PID) Process: | (6408) 8342c29aacd500b5d424822648331736379f18bdb6bc27a7e7a579544570fa8a.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 0 | |||
| (PID) Process: | (6508) Arcane Cheat.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\ApplicationAssociationToasts |
| Operation: | write | Name: | VBEFile_.vbe |
Value: 0 | |||
| (PID) Process: | (6508) Arcane Cheat.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\FileExts\.vbe\OpenWithProgids |
| Operation: | write | Name: | VBEFile |
Value: | |||
| (PID) Process: | (6508) Arcane Cheat.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (6508) Arcane Cheat.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (6508) Arcane Cheat.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
Executable files
238
Suspicious files
68
Text files
124
Unknown types
3
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6408 | 8342c29aacd500b5d424822648331736379f18bdb6bc27a7e7a579544570fa8a.exe | C:\Users\admin\AppData\Local\Temp\Arcane CheatSetup.exe | — | |
MD5:— | SHA256:— | |||
| 6728 | Arcane CheatSetup.tmp | C:\Users\admin\AppData\Local\Temp\is-964B3.tmp\_isetup\_setup64.tmp | executable | |
MD5:E4211D6D009757C078A9FAC7FF4F03D4 | SHA256:388A796580234EFC95F3B1C70AD4CB44BFDDC7BA0F9203BF4902B9929B136F95 | |||
| 6508 | Arcane Cheat.exe | C:\Surrogateprovidercomponentsessionmonitor\browserwinsvc.exe | executable | |
MD5:E780BB029D808CB41937F4F7CD022B45 | SHA256:772574576B825F97AA91CE0D24B0BA83FDB0DE3A0545296E1D6D28F1349F1456 | |||
| 6508 | Arcane Cheat.exe | C:\Surrogateprovidercomponentsessionmonitor\lEI1Ux7.vbe | binary | |
MD5:3944FF0B2B8A1617F5E571EBC259A0E6 | SHA256:693C79DBD630E1180DDB96B8D51895A9F27A01AE25C27AEBBC55BE5E4874335D | |||
| 6452 | Arcane CheatSetup.exe | C:\Users\admin\AppData\Local\Temp\is-769CC.tmp\Arcane CheatSetup.tmp | executable | |
MD5:129B8E200A6E90E813080C9CE0474063 | SHA256:CF0018AFFDD0B7921F922F1741AD229EC52C8A7D6C2B19889A149E0CC24AA839 | |||
| 6408 | 8342c29aacd500b5d424822648331736379f18bdb6bc27a7e7a579544570fa8a.exe | C:\Users\admin\AppData\Local\Temp\Arcane Cheat.exe | executable | |
MD5:593631A643AA6AB0AF08189773812E6D | SHA256:DA0500DB781CE974A0C4D9B6F245D2302F90DC932D23402D1441E3D5C77C6CD4 | |||
| 6728 | Arcane CheatSetup.tmp | C:\Users\admin\AppData\Local\Temp\is-964B3.tmp\_isetup\_shfoldr.dll | executable | |
MD5:92DC6EF532FBB4A5C3201469A5B5EB63 | SHA256:9884E9D1B4F8A873CCBD81F8AD0AE257776D2348D027D811A56475E028360D87 | |||
| 6728 | Arcane CheatSetup.tmp | C:\Program Files (x86)\Arcane Cheat\jre\README.txt | text | |
MD5:4BDA1F1B04053DCFE66E87A77B307BB1 | SHA256:FD475B1619675B9FB3F5CD11D448B97EDDEE8D1F6DDCCA13DED8BC6E0CAA9CF3 | |||
| 6728 | Arcane CheatSetup.tmp | C:\Program Files (x86)\Arcane Cheat\jre\release | text | |
MD5:A61B1E3FE507D37F0D2F3ADD5AC691E0 | SHA256:F9E84B54CF0D8CB0645E0D89BF47ED74C88AF98AC5BF9CCF3ACCB1A824F7DC3A | |||
| 6728 | Arcane CheatSetup.tmp | C:\Program Files (x86)\Arcane Cheat\jre\is-L0F56.tmp | text | |
MD5:67CB88F6234B6A1F2320A23B197FA3F6 | SHA256:263E21F4B43C118A8B4C07F1A8ACB11CAFC232886834433E34187F5663242360 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
10
TCP/UDP connections
55
DNS requests
22
Threats
2
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
6864 | browserwinsvc.exe | GET | 200 | 208.95.112.1:80 | http://ip-api.com/line/?fields=hosting | unknown | — | — | unknown |
2308 | svchost.exe | GET | 200 | 2.16.164.49:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | unknown |
2308 | svchost.exe | GET | 200 | 23.211.9.92:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | unknown |
5536 | firefox.exe | GET | 200 | 34.107.221.82:80 | http://detectportal.firefox.com/canonical.html | unknown | — | — | unknown |
5536 | firefox.exe | GET | 200 | 34.107.221.82:80 | http://detectportal.firefox.com/success.txt?ipv4 | unknown | — | — | unknown |
1412 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | unknown |
4680 | SearchApp.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAzlnDD9eoNTLi0BRrMy%2BWU%3D | unknown | — | — | unknown |
6264 | SIHClient.exe | GET | 200 | 23.211.9.92:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | unknown |
6264 | SIHClient.exe | GET | 200 | 23.211.9.92:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | unknown |
1512 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEApDqVCbATUviZV57HIIulA%3D | unknown | — | — | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | unknown |
4364 | svchost.exe | 239.255.255.250:1900 | — | — | — | unknown |
— | — | 51.124.78.146:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | NL | unknown |
2392 | RUXIMICS.exe | 51.124.78.146:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | NL | unknown |
5140 | MoUsoCoreWorker.exe | 51.124.78.146:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | NL | unknown |
4 | System | 192.168.100.255:138 | — | — | — | unknown |
6864 | browserwinsvc.exe | 208.95.112.1:80 | ip-api.com | TUT-AS | US | unknown |
2308 | svchost.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | unknown |
2308 | svchost.exe | 2.16.164.49:80 | crl.microsoft.com | Akamai International B.V. | NL | unknown |
2308 | svchost.exe | 23.211.9.92:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
ip-api.com |
| shared |
settings-win.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
detectportal.firefox.com |
| whitelisted |
prod.detectportal.prod.cloudops.mozgcp.net |
| whitelisted |
example.org |
| whitelisted |
ipv4only.arpa |
| whitelisted |
www.bing.com |
| whitelisted |
r.bing.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
6864 | browserwinsvc.exe | Device Retrieving External IP Address Detected | ET POLICY External IP Lookup ip-api.com |
6864 | browserwinsvc.exe | Device Retrieving External IP Address Detected | POLICY [ANY.RUN] External Hosting Lookup by ip-api |