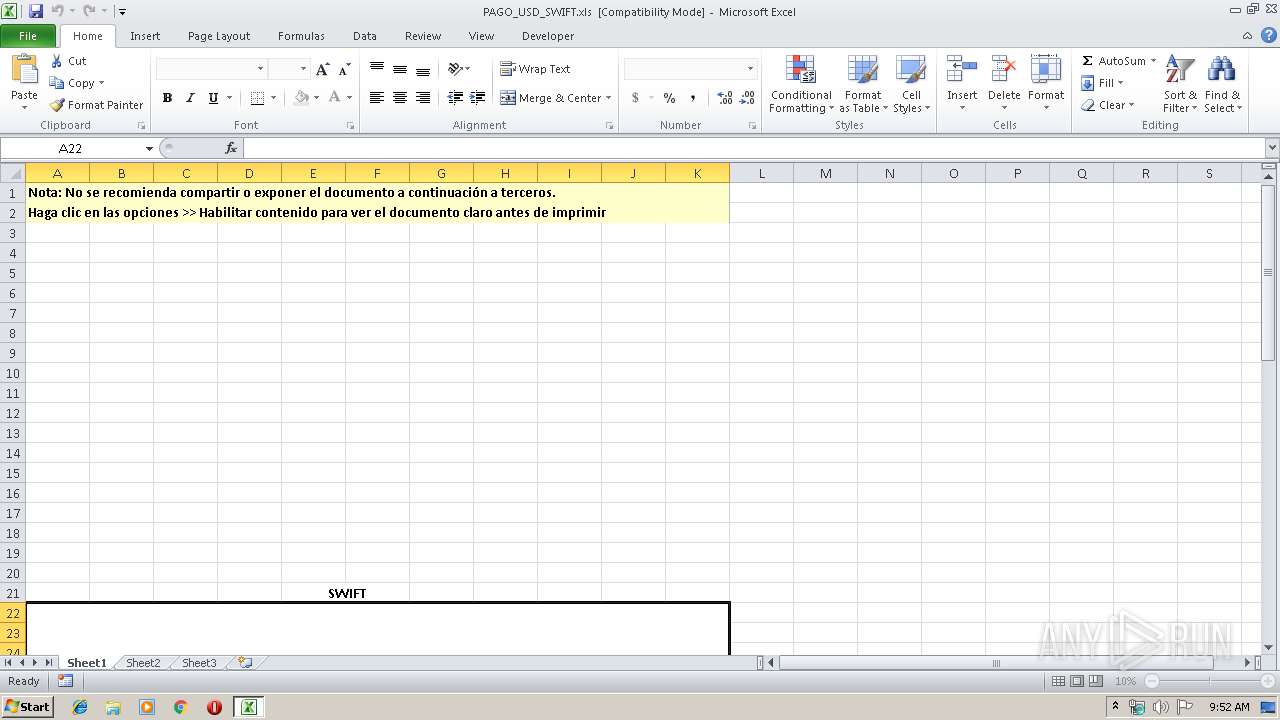
| File name: | PAGO_USD_SWIFT.xls |
| Full analysis: | https://app.any.run/tasks/75c5aed1-bbb7-4062-8340-6d3cb28483ab |
| Verdict: | Malicious activity |
| Analysis date: | September 11, 2019, 08:52:33 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| MIME: | application/vnd.ms-excel |
| File info: | Composite Document File V2 Document, Little Endian, Os: Windows, Version 6.1, Code page: 1252, Author: Windows User, Last Saved By: Windows User, Name of Creating Application: Microsoft Excel, Create Time/Date: Wed Sep 11 02:21:15 2019, Last Saved Time/Date: Wed Sep 11 02:27:30 2019, Security: 0 |
| MD5: | ADB79F7585A51EC4C818043BA58ADB15 |
| SHA1: | 1C6E542012379F22F90E85AC55BE4AE06DA7AD67 |
| SHA256: | 8341F827B489995B89F7337050F430DFBB9367E7DE7DBA10877B594361785D22 |
| SSDEEP: | 3072:w0xEtjPOtioVjDGUU1qfDlaGGx+cL2QnAw6iw7NDJd9EpL+fDPQXrOkq9Z7:HxEtjPOtioVjDGUU1qfDlavx+W2QnAw1 |
MALICIOUS
Requests a remote executable file from MS Office
- EXCEL.EXE (PID: 3556)
SUSPICIOUS
Unusual connect from Microsoft Office
- EXCEL.EXE (PID: 3556)
INFO
Reads Microsoft Office registry keys
- EXCEL.EXE (PID: 3556)
Creates files in the user directory
- EXCEL.EXE (PID: 3556)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .xls | | | Microsoft Excel sheet (48) |
|---|---|---|
| .xls | | | Microsoft Excel sheet (alternate) (39.2) |
EXIF
FlashPix
| Author: | Windows User |
|---|---|
| LastModifiedBy: | Windows User |
| Software: | Microsoft Excel |
| CreateDate: | 2019:09:11 01:21:15 |
| ModifyDate: | 2019:09:11 01:27:30 |
| Security: | None |
| CodePage: | Windows Latin 1 (Western European) |
| AppVersion: | 14 |
| ScaleCrop: | No |
| LinksUpToDate: | No |
| SharedDoc: | No |
| HyperlinksChanged: | No |
| TitleOfParts: |
|
| HeadingPairs: |
|
| CompObjUserTypeLen: | 31 |
| CompObjUserType: | Microsoft Excel 2003 Worksheet |
Total processes
33
Monitored processes
1
Malicious processes
0
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 3556 | "C:\Program Files\Microsoft Office\Office14\EXCEL.EXE" /dde | C:\Program Files\Microsoft Office\Office14\EXCEL.EXE | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Excel Exit code: 0 Version: 14.0.6024.1000 Modules
| |||||||||||||||
Total events
439
Read events
409
Write events
23
Delete events
7
Modification events
| (PID) Process: | (3556) EXCEL.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Excel\Resiliency\StartupItems |
| Operation: | write | Name: | ,#$ |
Value: 2C232400E40D0000010000000000000000000000 | |||
| (PID) Process: | (3556) EXCEL.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1033 |
Value: Off | |||
| (PID) Process: | (3556) EXCEL.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1033 |
Value: On | |||
| (PID) Process: | (3556) EXCEL.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Excel |
| Operation: | write | Name: | MTTT |
Value: E40D00006CE9D34A7E68D50100000000 | |||
| (PID) Process: | (3556) EXCEL.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Excel\Resiliency\StartupItems |
| Operation: | delete value | Name: | ,#$ |
Value: 2C232400E40D0000010000000000000000000000 | |||
| (PID) Process: | (3556) EXCEL.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Excel\Resiliency\StartupItems |
| Operation: | delete key | Name: | |
Value: | |||
| (PID) Process: | (3556) EXCEL.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Excel\Resiliency |
| Operation: | delete key | Name: | |
Value: | |||
| (PID) Process: | (3556) EXCEL.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 0 | |||
| (PID) Process: | (3556) EXCEL.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 1 | |||
| (PID) Process: | (3556) EXCEL.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Excel\Resiliency\DocumentRecovery\16A00E |
| Operation: | write | Name: | 16A00E |
Value: 04000000E40D00002900000043003A005C00550073006500720073005C00610064006D0069006E005C004400650073006B0074006F0070005C005000410047004F005F005500530044005F00530057004900460054002E0078006C007300000000001700000043003A005C00550073006500720073005C00610064006D0069006E005C004400650073006B0074006F0070005C000100000000000000A05DD54B7E68D5010EA016000EA0160000000000AC020000001000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
Executable files
0
Suspicious files
0
Text files
2
Unknown types
2
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3556 | EXCEL.EXE | C:\Users\admin\AppData\Local\Temp\CVR9B0C.tmp.cvr | — | |
MD5:— | SHA256:— | |||
| 3556 | EXCEL.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Office\Recent\PAGO_USD_SWIFT.xls.LNK | lnk | |
MD5:— | SHA256:— | |||
| 3556 | EXCEL.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Office\Recent\index.dat | text | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
1
TCP/UDP connections
1
DNS requests
1
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3556 | EXCEL.EXE | GET | — | 179.61.13.84:80 | http://rca-auditores.cl/Golkim/kuugkgyr.exe | CL | — | — | suspicious |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
3556 | EXCEL.EXE | 179.61.13.84:80 | rca-auditores.cl | HIVELOCITY VENTURES CORP | CL | suspicious |
DNS requests
Domain | IP | Reputation |
|---|---|---|
rca-auditores.cl |
| suspicious |