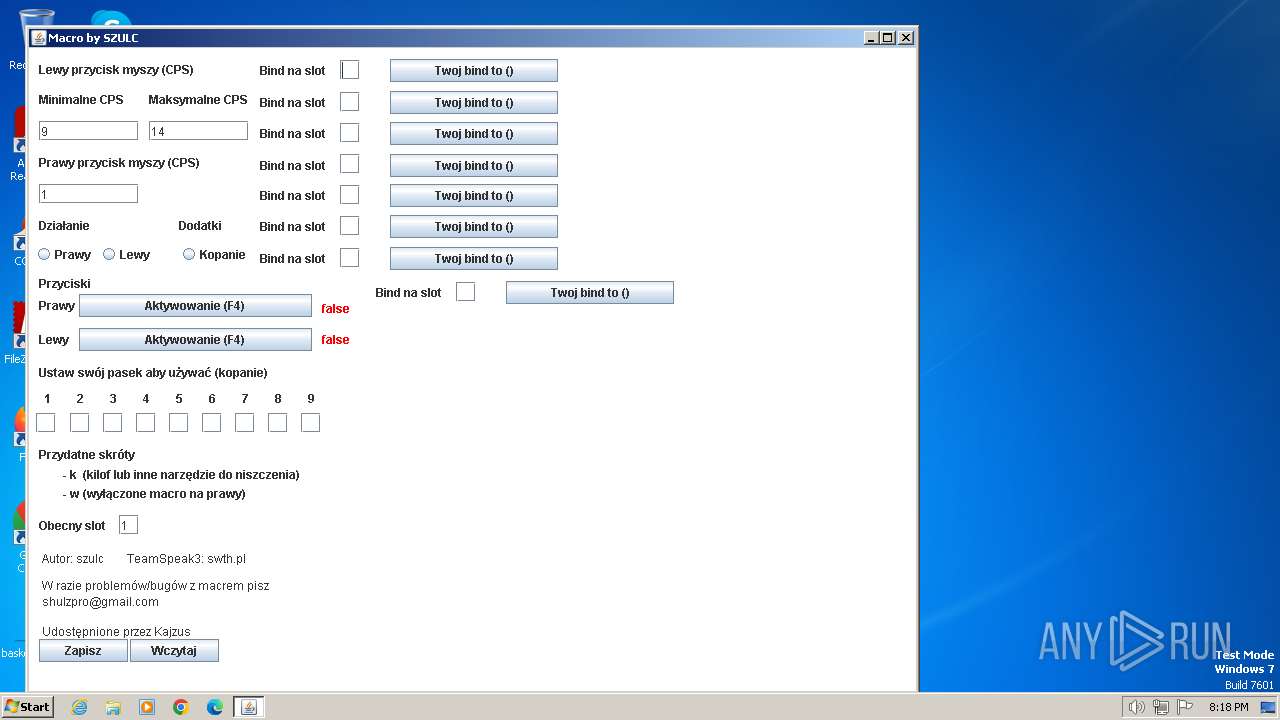
| File name: | Macro szulc 2.0 mini.jar |
| Full analysis: | https://app.any.run/tasks/72483dda-fda9-483c-8f37-55dc32716e01 |
| Verdict: | Malicious activity |
| Analysis date: | July 02, 2024, 19:18:04 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/java-archive |
| File info: | Java archive data (JAR) |
| MD5: | AE43808EF0C271DC495E101260EE8907 |
| SHA1: | 5DB3165AB7279EC5B71C6157AE161C40406C3ACC |
| SHA256: | 8307AC99940C924794D1310183A394E5C82331A705E97BBDC243F6EA288D8A60 |
| SSDEEP: | 49152:5pPCIeMtPD5mQKumQi2SNwsESlUNiK8UARC1FZZW:5pPCDIUQKPQtSdlmiKJUQLZW |
MALICIOUS
Drops the executable file immediately after the start
- javaw.exe (PID: 3256)
SUSPICIOUS
Executable content was dropped or overwritten
- javaw.exe (PID: 3256)
INFO
Checks supported languages
- javaw.exe (PID: 3256)
- wmpnscfg.exe (PID: 3344)
Reads the computer name
- wmpnscfg.exe (PID: 3344)
- javaw.exe (PID: 3256)
Manual execution by a user
- wmpnscfg.exe (PID: 3344)
Create files in a temporary directory
- javaw.exe (PID: 3256)
Creates files in the program directory
- javaw.exe (PID: 3256)
Reads the machine GUID from the registry
- javaw.exe (PID: 3256)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .jar | | | Java Archive (78.3) |
|---|---|---|
| .zip | | | ZIP compressed archive (21.6) |
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | 0x0808 |
| ZipCompression: | Deflated |
| ZipModifyDate: | 2018:06:28 09:31:44 |
| ZipCRC: | 0x422c0fce |
| ZipCompressedSize: | 1246 |
| ZipUncompressedSize: | 2262 |
| ZipFileName: | pl/macro/szulc/Listener/KeyListenSlot.class |
Total processes
41
Monitored processes
3
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 3256 | "C:\Program Files\Java\jre1.8.0_271\bin\javaw.exe" -jar "C:\Users\admin\Desktop\Macro szulc 2.0 mini.jar" | C:\Program Files\Java\jre1.8.0_271\bin\javaw.exe | explorer.exe | ||||||||||||
User: admin Company: Oracle Corporation Integrity Level: MEDIUM Description: Java(TM) Platform SE binary Version: 8.0.2710.9 Modules
| |||||||||||||||
| 3344 | "C:\Program Files\Windows Media Player\wmpnscfg.exe" | C:\Program Files\Windows Media Player\wmpnscfg.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Media Player Network Sharing Service Configuration Application Exit code: 0 Version: 12.0.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3520 | C:\Windows\system32\icacls.exe C:\ProgramData\Oracle\Java\.oracle_jre_usage /grant "everyone":(OI)(CI)M | C:\Windows\System32\icacls.exe | — | javaw.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
938
Read events
937
Write events
1
Delete events
0
Modification events
| (PID) Process: | (3256) javaw.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Direct3D\MostRecentApplication |
| Operation: | write | Name: | Name |
Value: javaw.exe | |||
Executable files
11
Suspicious files
0
Text files
1
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3256 | javaw.exe | C:\ProgramData\Oracle\Java\.oracle_jre_usage\17dfc292991c8061.timestamp | text | |
MD5:CD1C7682332E53B1433B86B85D4D426C | SHA256:DBFB846ACAB35B1412F12304F07930C744B4B9A7D19683E1DB31D4CF4A5C871E | |||
| 3256 | javaw.exe | C:\Users\admin\AppData\Local\Temp\jar_cache3525528843233224800.tmp | java | |
MD5:9C7B0FCB0472AE92B50CE17577E370D1 | SHA256:84C8667555EE8DD91FEF44B451419F6F16F71F727D5FC475A10C2663EBA83ABB | |||
| 3256 | javaw.exe | C:\Users\admin\AppData\Local\Temp\jna-92668751\jna8897561510353801845.dll | executable | |
MD5:9268651539D1ECBEC9E6ED81AECED380 | SHA256:67059E9D04131CF85B41B881D214FC745D8E165859DADB7634114E7E96EB6E42 | |||
| 3256 | javaw.exe | C:\Users\admin\AppData\Local\Temp\jar_cache7099764703522714966.tmp | java | |
MD5:2309AA0981207A1E853DD9C806C44082 | SHA256:FBC9DE96A0CC193A125B4008DBC348E9ED54E5E13FC67B8ED40E645D303CC51B | |||
| 3256 | javaw.exe | C:\Users\admin\AppData\Local\Temp\jar_cache2755168289086191366.tmp | java | |
MD5:2309AA0981207A1E853DD9C806C44082 | SHA256:FBC9DE96A0CC193A125B4008DBC348E9ED54E5E13FC67B8ED40E645D303CC51B | |||
| 3256 | javaw.exe | C:\Users\admin\AppData\Local\Temp\jar_cache7490604576256579472.tmp | java | |
MD5:2309AA0981207A1E853DD9C806C44082 | SHA256:FBC9DE96A0CC193A125B4008DBC348E9ED54E5E13FC67B8ED40E645D303CC51B | |||
| 3256 | javaw.exe | C:\Users\admin\AppData\Local\Temp\jar_cache7841151990157016449.tmp | java | |
MD5:DE6CF300C801226D4B19E4FDC258975E | SHA256:41565E543A043EE2073A0B3D93082B78614D2241AA2C6669E05385D94511851C | |||
| 3256 | javaw.exe | C:\Users\admin\AppData\Local\Temp\jar_cache5051152009101445259.tmp | java | |
MD5:9C7B0FCB0472AE92B50CE17577E370D1 | SHA256:84C8667555EE8DD91FEF44B451419F6F16F71F727D5FC475A10C2663EBA83ABB | |||
| 3256 | javaw.exe | C:\Users\admin\AppData\Local\Temp\jar_cache1550386819730847325.tmp | java | |
MD5:DE6CF300C801226D4B19E4FDC258975E | SHA256:41565E543A043EE2073A0B3D93082B78614D2241AA2C6669E05385D94511851C | |||
| 3256 | javaw.exe | C:\Users\admin\AppData\Local\Temp\JNativeHook-1460261087022425281.x86.dll | executable | |
MD5:1D82A7681960FCD739AC62E938C7E3A9 | SHA256:B2C4DBAA8E68295A7689EC8693A45123111FC0754F4C502CEDF022015341C541 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
4
TCP/UDP connections
12
DNS requests
6
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
1372 | svchost.exe | GET | 304 | 217.20.57.18:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?33775f6043c93e33 | unknown | — | — | unknown |
1372 | svchost.exe | GET | 200 | 2.21.20.137:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | unknown |
1372 | svchost.exe | GET | 200 | 23.52.120.96:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | unknown |
1060 | svchost.exe | GET | 304 | 217.20.57.18:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?fbe613066ac7852b | unknown | — | — | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
1060 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
2564 | svchost.exe | 239.255.255.250:3702 | — | — | — | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
1372 | svchost.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1372 | svchost.exe | 217.20.57.18:80 | ctldl.windowsupdate.com | — | US | unknown |
1372 | svchost.exe | 2.21.20.137:80 | crl.microsoft.com | Akamai International B.V. | DE | unknown |
1372 | svchost.exe | 23.52.120.96:80 | www.microsoft.com | AKAMAI-AS | DE | unknown |
1060 | svchost.exe | 217.20.57.18:80 | ctldl.windowsupdate.com | — | US | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
dns.msftncsi.com |
| shared |
settings-win.data.microsoft.com |
| whitelisted |
ctldl.windowsupdate.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |