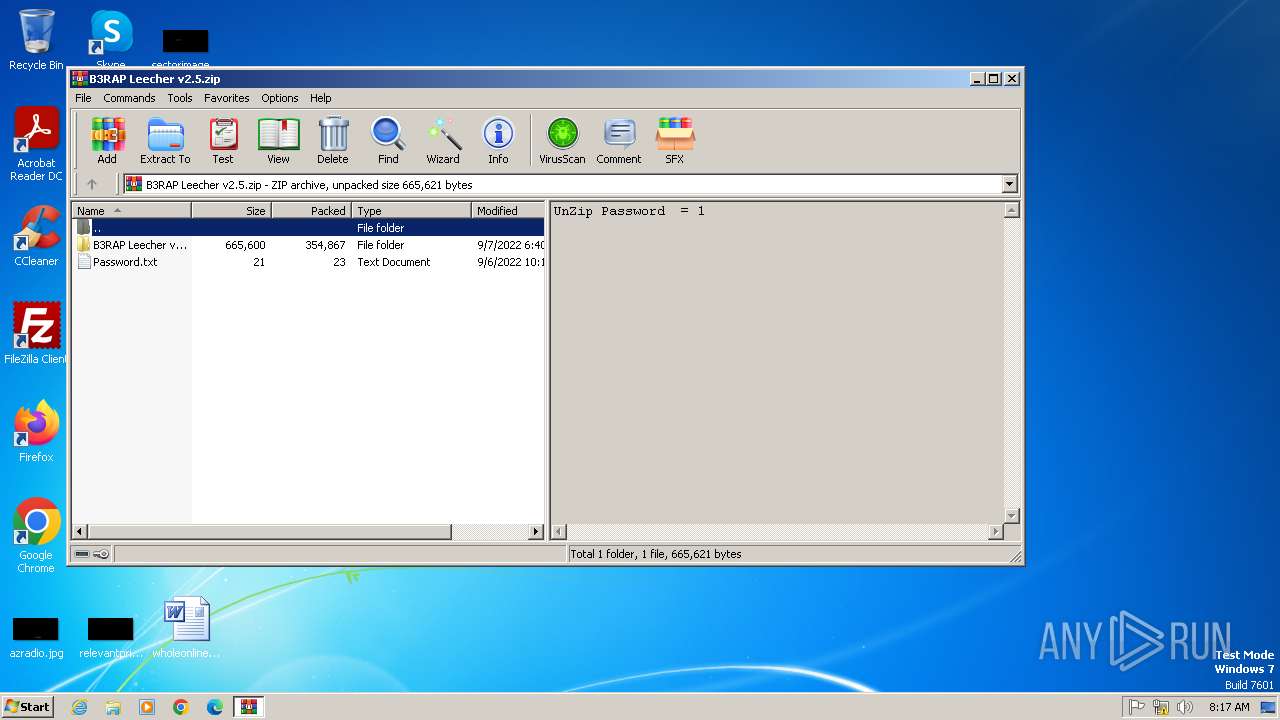
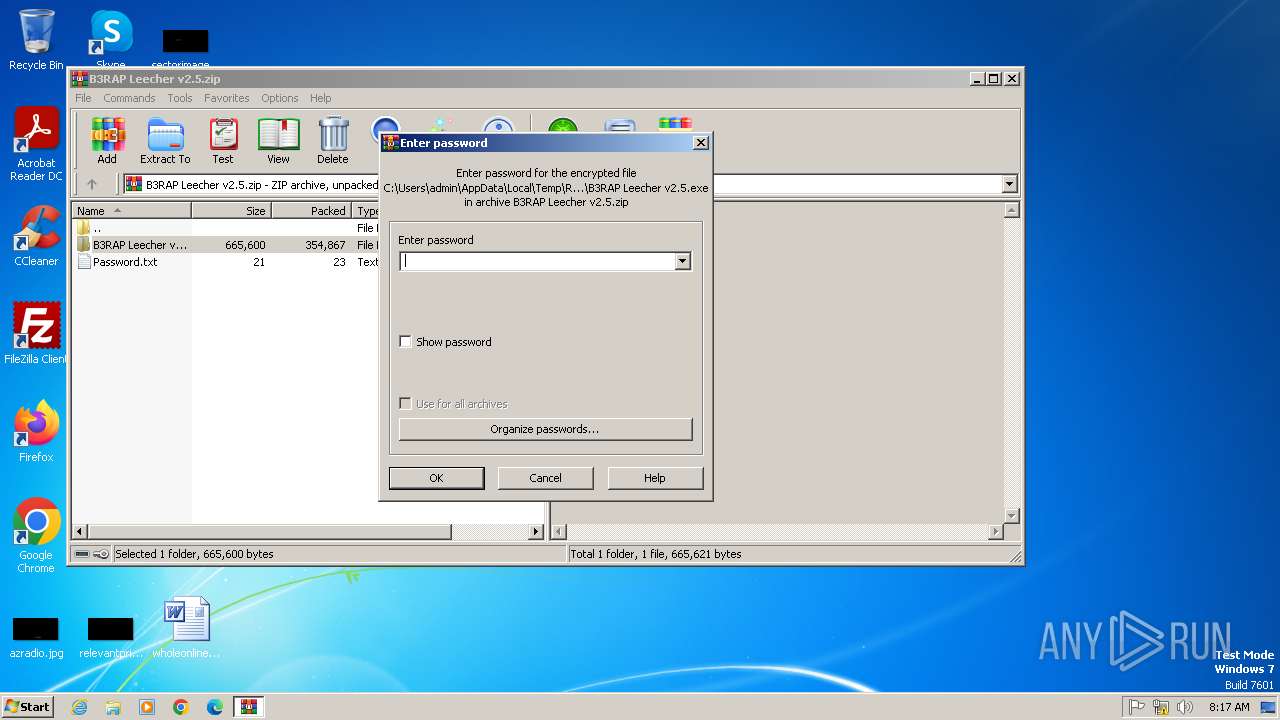
| File name: | B3RAP Leecher v2.5.zip |
| Full analysis: | https://app.any.run/tasks/fa631982-c09c-4b57-91fa-b031d39493e4 |
| Verdict: | Malicious activity |
| Analysis date: | May 17, 2025, 07:17:22 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v1.0 to extract, compression method=store |
| MD5: | E15CFC2A6EB8C6C6A414D0AEFAD8F586 |
| SHA1: | 6C043C1A7B31F85725BEF80B3FCA42C471C72D34 |
| SHA256: | 82F10601B471F55CCAE63FC3CA7CB5C2155AC4743D763B5049FE88637E4754EC |
| SSDEEP: | 12288:+A7MTtdQBHM9HNKSjBjwuKz9ngQZ2I9D1W0RF2PBz0:+eqtdQ9M9tKSjBjPKz9nXZ2I9DI0RF2C |
MALICIOUS
Changes the autorun value in the registry
- Setup.exe (PID: 268)
- explorer.exe (PID: 1980)
NJRAT has been detected (YARA)
- explorer.exe (PID: 1980)
SUSPICIOUS
Starts a Microsoft application from unusual location
- Setup.exe (PID: 1460)
- Setup.exe (PID: 268)
Reads the Internet Settings
- B3RAP Leecher v2.5.exe (PID: 1824)
- Setup.exe (PID: 268)
- svchost.exe (PID: 3876)
- explorer.exe (PID: 2356)
Generic archive extractor
- WinRAR.exe (PID: 2692)
Reads security settings of Internet Explorer
- B3RAP Leecher v2.5.exe (PID: 1824)
- Setup.exe (PID: 268)
- svchost.exe (PID: 3876)
- explorer.exe (PID: 2356)
Executable content was dropped or overwritten
- B3RAP Leecher v2.5.exe (PID: 1824)
- Setup.exe (PID: 268)
- svchost.exe (PID: 3876)
- explorer.exe (PID: 2356)
Process drops legitimate windows executable
- B3RAP Leecher v2.5.exe (PID: 1824)
- Setup.exe (PID: 268)
- svchost.exe (PID: 3876)
- explorer.exe (PID: 2356)
The process creates files with name similar to system file names
- Setup.exe (PID: 268)
- svchost.exe (PID: 3876)
- explorer.exe (PID: 2356)
Reads settings of System Certificates
- svchost.exe (PID: 3876)
Starts itself from another location
- explorer.exe (PID: 2356)
Uses NETSH.EXE to add a firewall rule or allowed programs
- explorer.exe (PID: 1980)
INFO
Checks supported languages
- B3RAP Leecher v2.5.exe (PID: 1824)
- B3RAP Leecher v2.5 .exe (PID: 1784)
- Setup.exe (PID: 1460)
- Setup.exe (PID: 268)
- svchost.exe (PID: 3876)
- explorer.exe (PID: 2356)
- explorer.exe (PID: 1980)
Reads the computer name
- B3RAP Leecher v2.5.exe (PID: 1824)
- B3RAP Leecher v2.5 .exe (PID: 1784)
- Setup.exe (PID: 1460)
- Setup.exe (PID: 268)
- svchost.exe (PID: 3876)
- explorer.exe (PID: 2356)
- explorer.exe (PID: 1980)
Create files in a temporary directory
- B3RAP Leecher v2.5.exe (PID: 1824)
- svchost.exe (PID: 3876)
Manual execution by a user
- B3RAP Leecher v2.5.exe (PID: 1824)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 2692)
Reads the machine GUID from the registry
- B3RAP Leecher v2.5.exe (PID: 1824)
- Setup.exe (PID: 1460)
- Setup.exe (PID: 268)
- B3RAP Leecher v2.5 .exe (PID: 1784)
- svchost.exe (PID: 3876)
- explorer.exe (PID: 2356)
- explorer.exe (PID: 1980)
Reads Environment values
- svchost.exe (PID: 3876)
- explorer.exe (PID: 1980)
- explorer.exe (PID: 2356)
Disables trace logs
- svchost.exe (PID: 3876)
Creates files or folders in the user directory
- Setup.exe (PID: 268)
- svchost.exe (PID: 3876)
- explorer.exe (PID: 2356)
The sample compiled with english language support
- svchost.exe (PID: 3876)
- explorer.exe (PID: 2356)
Reads product name
- explorer.exe (PID: 2356)
- explorer.exe (PID: 1980)
.NET Reactor protector has been detected
- svchost.exe (PID: 3876)
Reads the software policy settings
- svchost.exe (PID: 3876)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 10 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | None |
| ZipModifyDate: | 2022:09:08 00:40:34 |
| ZipCRC: | 0x00000000 |
| ZipCompressedSize: | - |
| ZipUncompressedSize: | - |
| ZipFileName: | B3RAP Leecher v2.5/ |
Total processes
43
Monitored processes
9
Malicious processes
5
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 268 | "C:\Users\admin\AppData\Local\Temp\Setup.exe" | C:\Users\admin\AppData\Local\Temp\Setup.exe | B3RAP Leecher v2.5.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Host Process for Windows Services Exit code: 0 Version: 1.0.0.0 Modules
| |||||||||||||||
| 1460 | "C:\Users\admin\AppData\Local\Temp\Setup.exe" | C:\Users\admin\AppData\Local\Temp\Setup.exe | — | B3RAP Leecher v2.5.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Host Process for Windows Services Exit code: 0 Version: 1.0.0.0 Modules
| |||||||||||||||
| 1784 | "C:\Users\admin\Desktop\B3RAP Leecher v2.5\B3RAP Leecher v2.5 .exe" | C:\Users\admin\Desktop\B3RAP Leecher v2.5\B3RAP Leecher v2.5 .exe | — | B3RAP Leecher v2.5.exe | |||||||||||
User: admin Company: B3RAP Softwares Integrity Level: MEDIUM Description: B3RAP Leecher v2.5.0.0 Version: 2.5.0.0 Modules
| |||||||||||||||
| 1824 | "C:\Users\admin\Desktop\B3RAP Leecher v2.5\B3RAP Leecher v2.5.exe" | C:\Users\admin\Desktop\B3RAP Leecher v2.5\B3RAP Leecher v2.5.exe | explorer.exe | ||||||||||||
User: admin Company: B3RAP Softwares Integrity Level: MEDIUM Description: B3RAP Leecher v2.5.0.0 Exit code: 3221225547 Version: 2.5.0.0 Modules
| |||||||||||||||
| 1980 | "C:\Users\admin\AppData\Roaming\Microsoft\Windows\explorer.exe" | C:\Users\admin\AppData\Roaming\Microsoft\Windows\explorer.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Explorer Version: 10.0.19041.4355 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2356 | "C:\Users\admin\AppData\Roaming\Microsoft\Windows\Templates\explorer.exe" | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Templates\explorer.exe | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Explorer Exit code: 0 Version: 10.0.19041.4355 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2692 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Temp\B3RAP Leecher v2.5.zip" | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
| 2716 | netsh firewall add allowedprogram "C:\Users\admin\AppData\Roaming\Microsoft\Windows\explorer.exe" "explorer.exe" ENABLE | C:\Windows\System32\netsh.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Network Command Shell Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3876 | "C:\Users\admin\AppData\Roaming\Microsoft\Windows\Templates\svchost.exe" | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Templates\svchost.exe | Setup.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Host Process for Windows Services Exit code: 0 Version: 8.1.1.7900 Modules
| |||||||||||||||
Total events
10 233
Read events
10 067
Write events
166
Delete events
0
Modification events
| (PID) Process: | (2692) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (2692) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (2692) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\182\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (2692) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\Win7-KB3191566-x86.zip | |||
| (PID) Process: | (2692) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\curl-8.5.0_1-win32-mingw.zip | |||
| (PID) Process: | (2692) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
| (PID) Process: | (2692) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\B3RAP Leecher v2.5.zip | |||
| (PID) Process: | (2692) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (2692) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (2692) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
Executable files
7
Suspicious files
2
Text files
1
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 1824 | B3RAP Leecher v2.5.exe | C:\Users\admin\AppData\Local\Temp\Setup.exe | executable | |
MD5:0E6C9432CBA1614FCCC232F201028C72 | SHA256:C9A2FAFFEE3DE29E278A89E54B07EDB1F520F5E665480A1002D401FD83CDE2E8 | |||
| 2692 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRb2692.6438\B3RAP Leecher v2.5\Leaf.xNet.dll | executable | |
MD5:C604DB05266803E0EC74479B7590B70D | SHA256:1ABA710A9270359C0791646BCA08A9E7F6997C6DA10BD0A5A26CCA0D53B05CF8 | |||
| 1824 | B3RAP Leecher v2.5.exe | C:\Users\admin\Desktop\B3RAP Leecher v2.5\B3RAP Leecher v2.5 .exe | executable | |
MD5:E863BE6B1A02A9BBBCAB06B679AB251B | SHA256:98B041D9D6F7B519F9D9D0AC0D59B68F47424055AD756577503909EA2473D6F3 | |||
| 268 | Setup.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Templates\svchost.zip | compressed | |
MD5:BBF128484E7EA29053C6DB91849067EA | SHA256:5E6F03B5AE15131C2AD374C563273389B3340168FF647433A6B5E7ACCE468B05 | |||
| 2692 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRb2692.6438\B3RAP Leecher v2.5\B3RAP Leecher v2.5.exe | executable | |
MD5:8A8ACB6DA5847D47B309E554B1D1E7FE | SHA256:DB53467DFB4433FFC0E419B870E5FB1C30578AD7CD8A909A0797BC7A13578542 | |||
| 3876 | svchost.exe | C:\Users\admin\AppData\Local\Temp\explorer.txt | text | |
MD5:2694465DFE4A5123F2A998366D7E488D | SHA256:9A7F4DEC22798E28AC786C06226197AEC1076962E4928B364AB0AF808D08E9F6 | |||
| 3876 | svchost.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Templates\explorer.zip | compressed | |
MD5:C91298A508EEA0C41740196875704B9A | SHA256:5CB3D04E1E3E21C3B4565744CB33D6AB17292E4CA3FE8E6097B332A3CBD38C70 | |||
| 268 | Setup.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Templates\svchost.exe | executable | |
MD5:301E8D9A2445DD999CE816C17D8DBBB3 | SHA256:2EA1FA52A6896CE0100084E3696712D76B4D1E995CA0012954BAE3107562A9EB | |||
| 2356 | explorer.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\explorer.exe | executable | |
MD5:1962B70A53AC796F7463B615EE1CBCA1 | SHA256:2A954265ED5269D1144295D72E0E97CCEEECA2B2BB4DAF83D38A87CC1789423C | |||
| 3876 | svchost.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Templates\explorer.exe | executable | |
MD5:1962B70A53AC796F7463B615EE1CBCA1 | SHA256:2A954265ED5269D1144295D72E0E97CCEEECA2B2BB4DAF83D38A87CC1789423C | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
3
TCP/UDP connections
7
DNS requests
4
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3876 | svchost.exe | HEAD | 200 | 107.180.41.239:80 | http://amazonhost.thedreamsop.com/2022/explorer.txt | unknown | — | — | unknown |
3876 | svchost.exe | GET | 200 | 107.180.41.239:80 | http://amazonhost.thedreamsop.com/2022/explorer.txt | unknown | — | — | unknown |
3876 | svchost.exe | GET | 200 | 107.180.41.239:80 | http://amazonhost.thedreamsop.com/2022/explorer.txt | unknown | — | — | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 224.0.0.252:5355 | — | — | — | whitelisted |
1080 | svchost.exe | 224.0.0.252:5355 | — | — | — | whitelisted |
3876 | svchost.exe | 107.180.41.239:80 | amazonhost.thedreamsop.com | AS-26496-GO-DADDY-COM-LLC | US | unknown |
3876 | svchost.exe | 142.250.185.193:443 | 24-06-2022-8080.blogspot.com | GOOGLE | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
google.com |
| whitelisted |
amazonhost.thedreamsop.com |
| unknown |
24-06-2022-8080.blogspot.com |
| whitelisted |
3058.cloudvonline.contact |
| unknown |