| File name: | HOIC v2.rar |
| Full analysis: | https://app.any.run/tasks/da841dd9-636c-4cc8-9bde-6a5638d6aecb |
| Verdict: | Malicious activity |
| Analysis date: | December 31, 2019, 06:48:40 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| MIME: | application/x-rar |
| File info: | RAR archive data, v5 |
| MD5: | FE6400B8F86D2F29BBF5ADAE4B1DEAB5 |
| SHA1: | 1742A98B0E94897A707C522B80E5B52CB253136E |
| SHA256: | 82EF9A6560C6BBA53BA742C6B3B3D13291F273DB0263576F94CF8EA8740683F9 |
| SSDEEP: | 49152:fb/Q8z2vs3EbOpj0NgNwTdcBZTWGg6oKce:fb/QG5OkKgbBFzce |
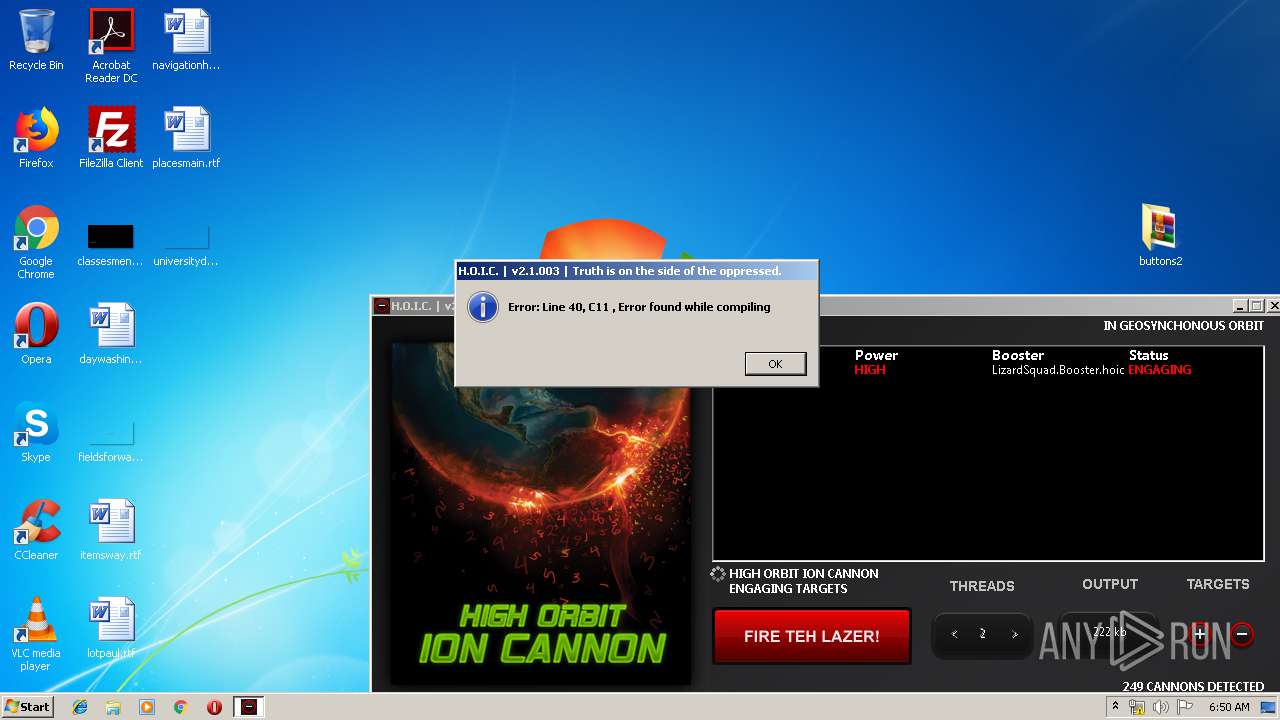
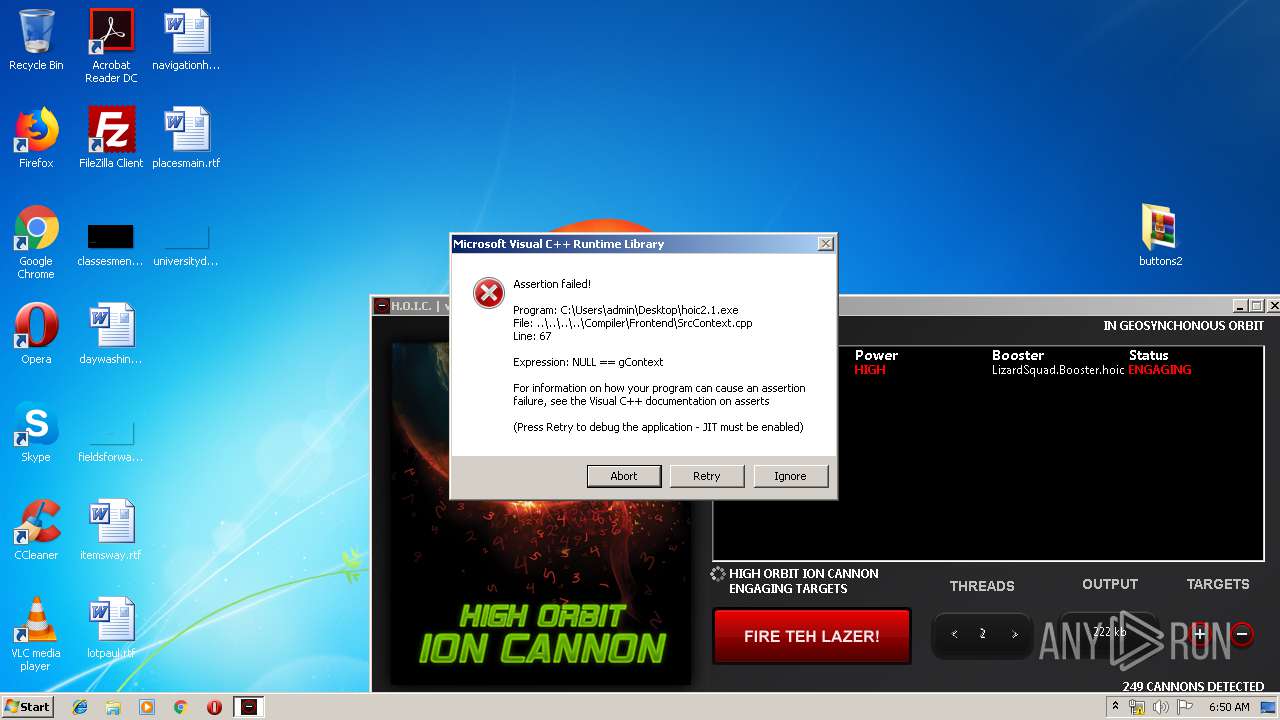
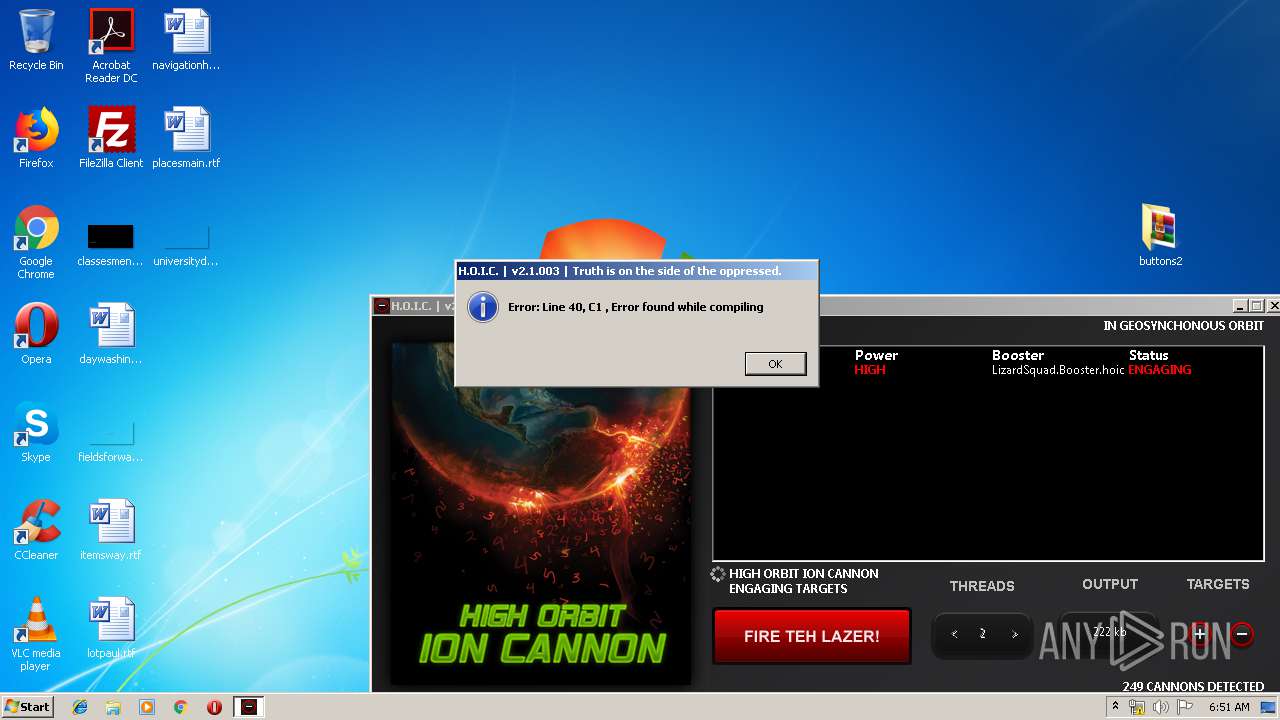
MALICIOUS
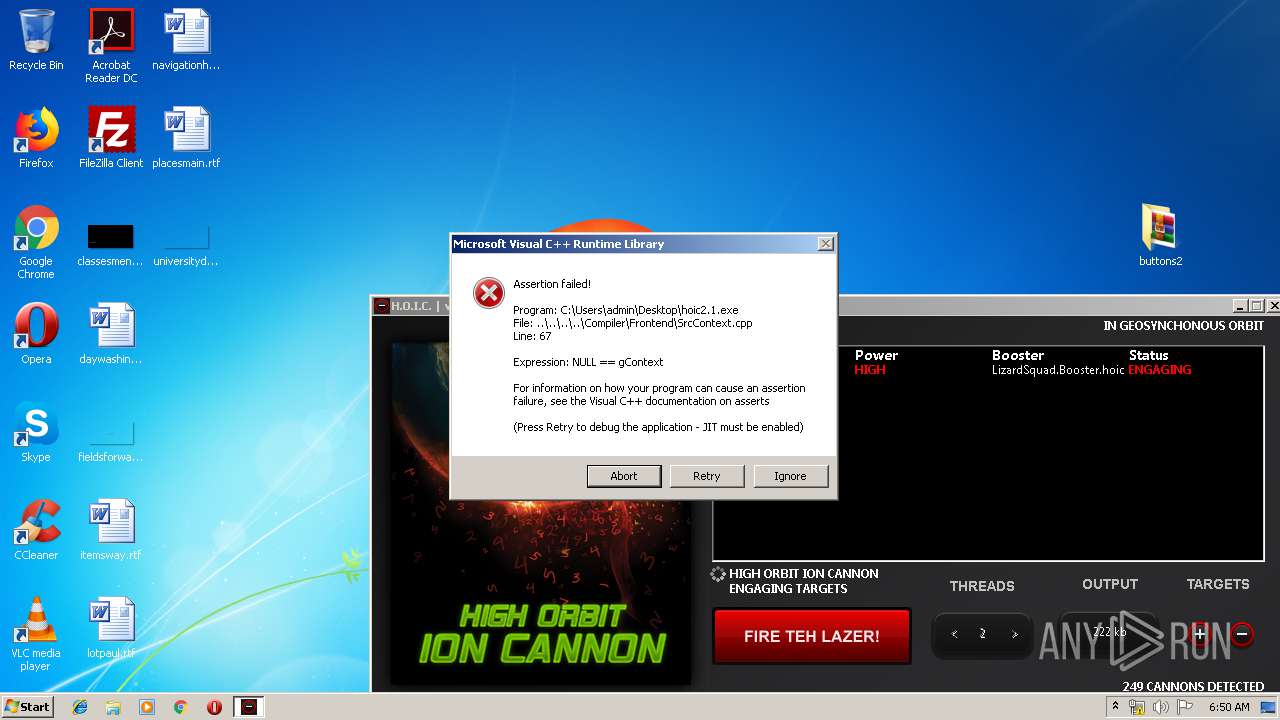
Application was dropped or rewritten from another process
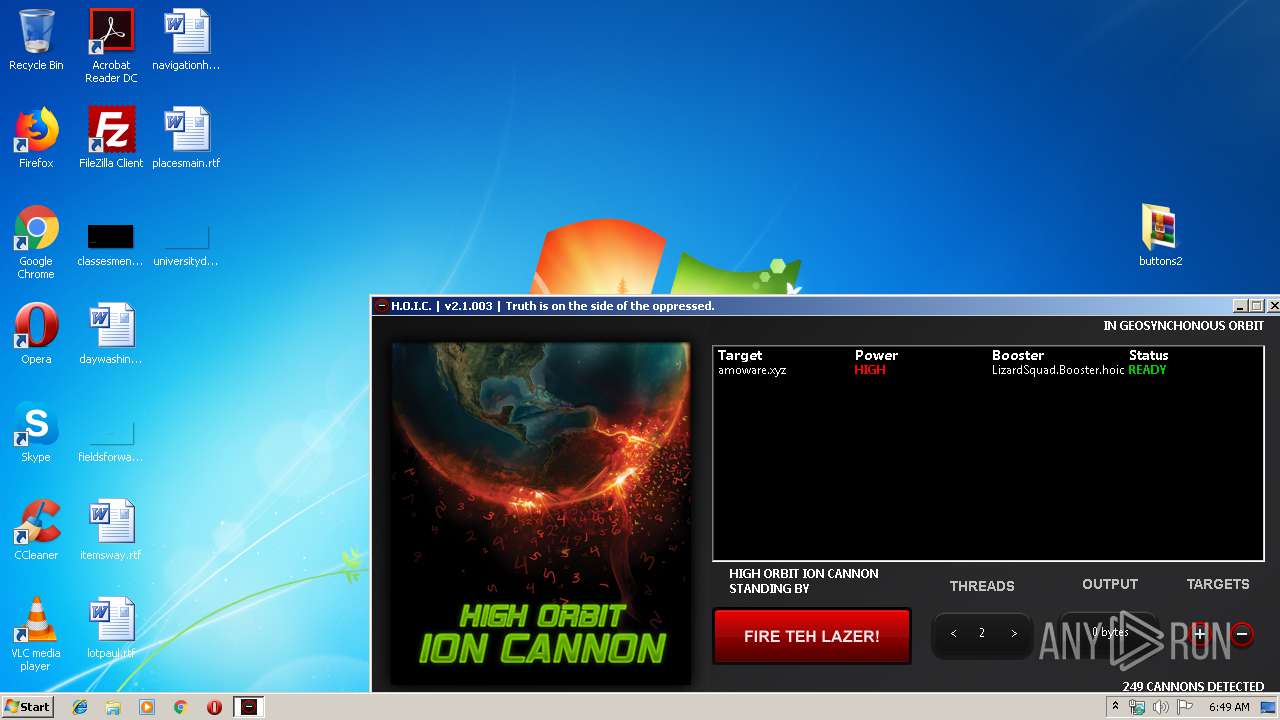
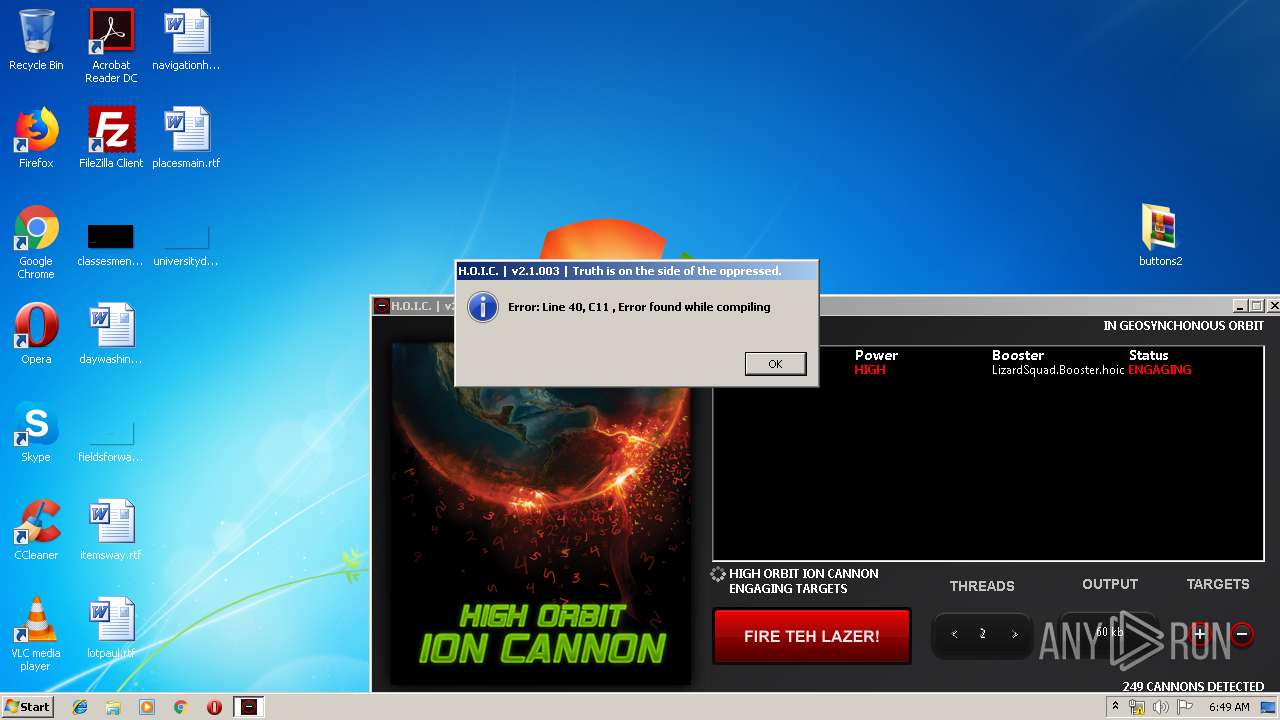
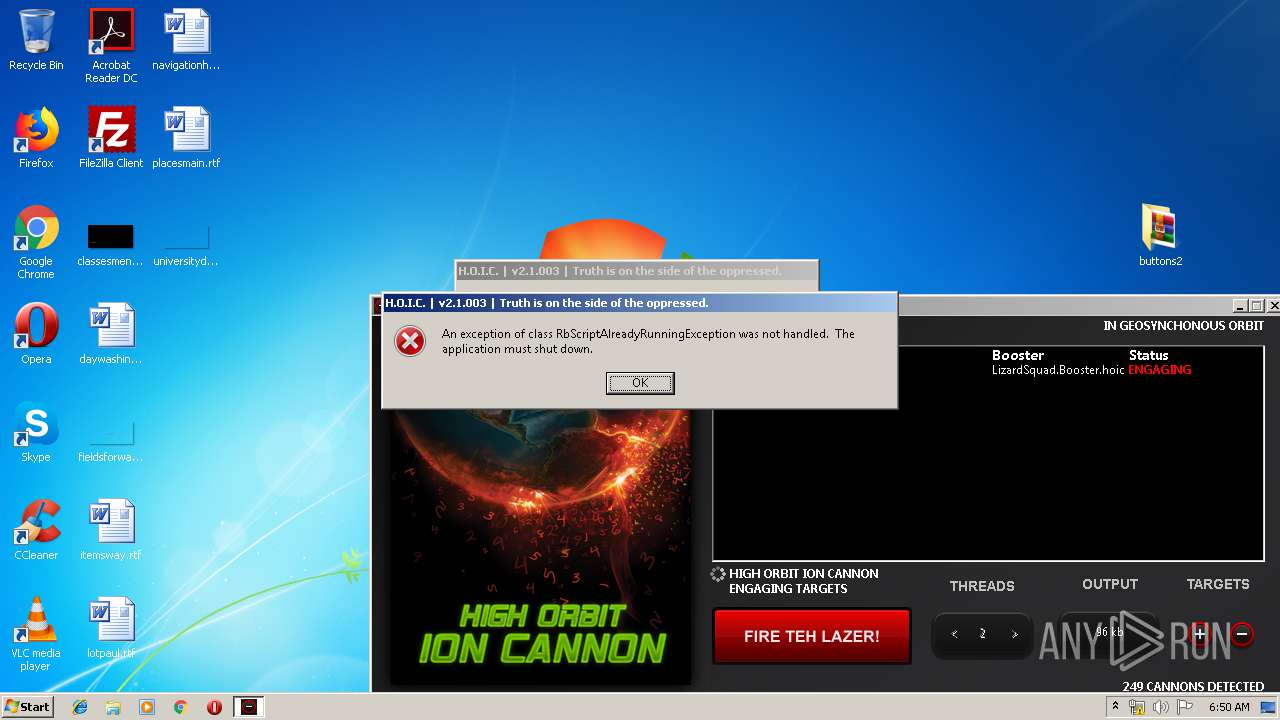
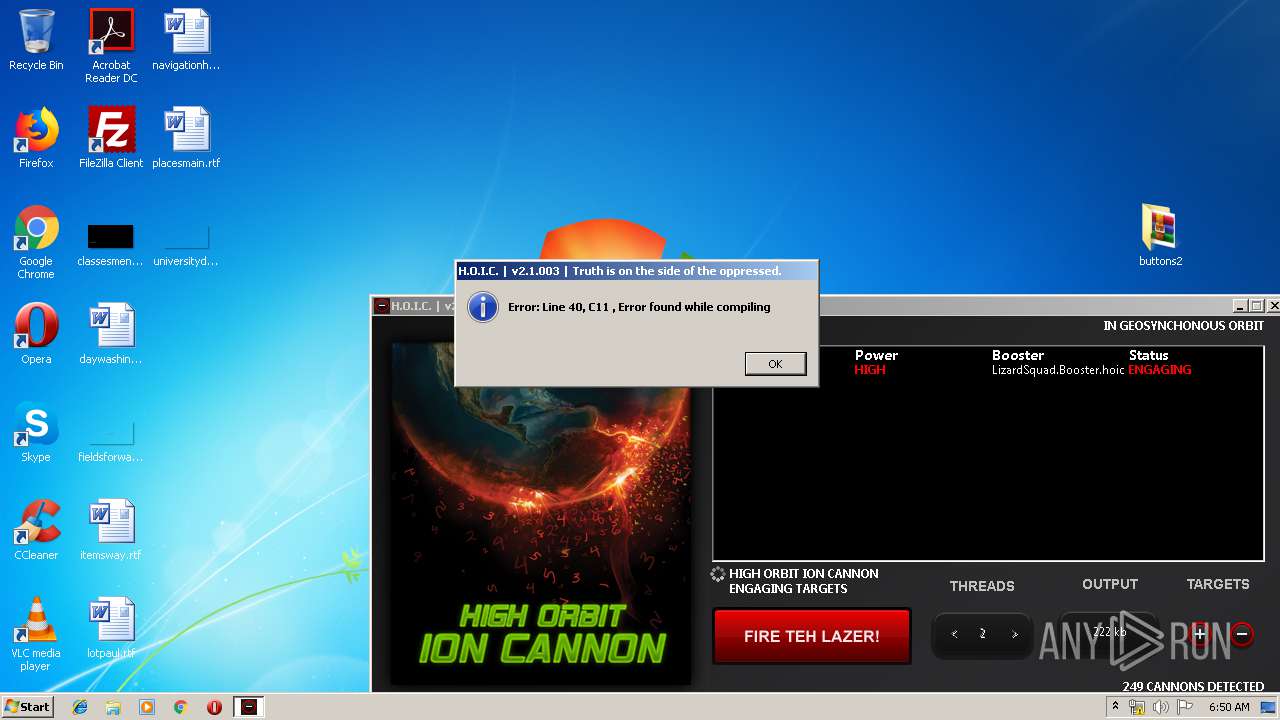
- hoic2.1.exe (PID: 1732)
SUSPICIOUS
No suspicious indicators.INFO
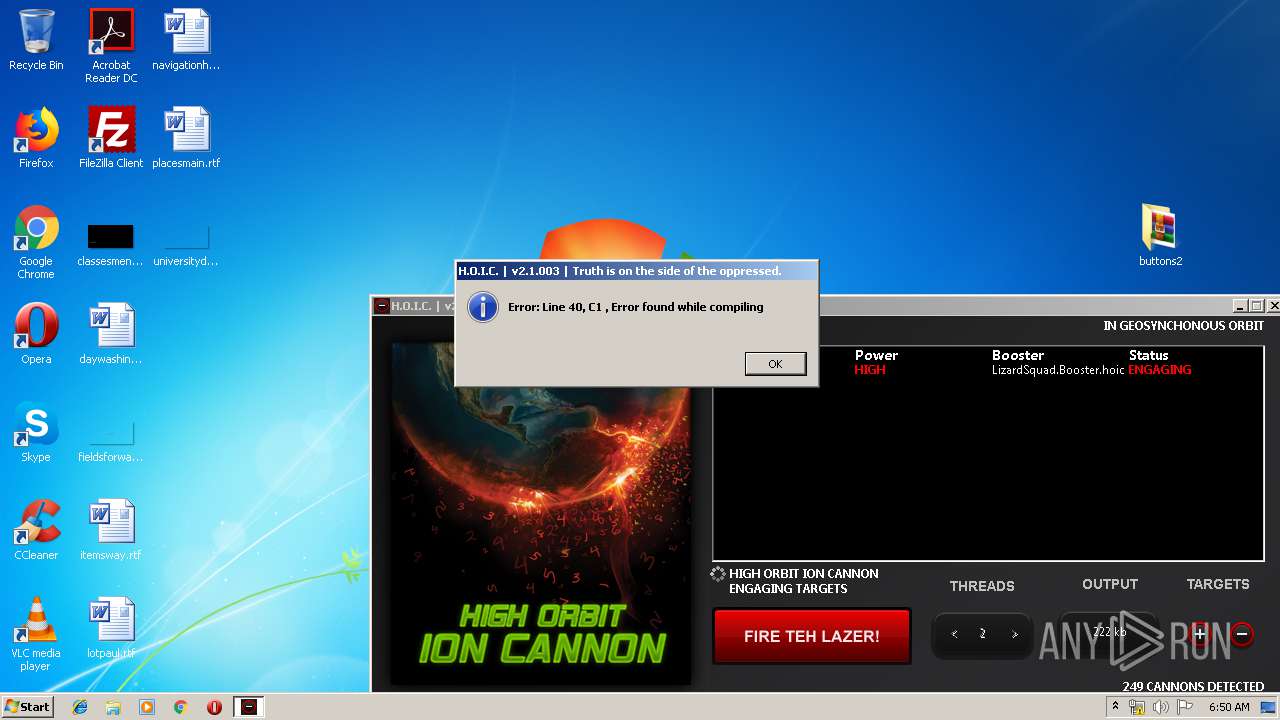
Manual execution by user
- hoic2.1.exe (PID: 1732)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .rar | | | RAR compressed archive (v5.0) (61.5) |
|---|---|---|
| .rar | | | RAR compressed archive (gen) (38.4) |
Total processes
36
Monitored processes
2
Malicious processes
0
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1732 | "C:\Users\admin\Desktop\hoic2.1.exe" | C:\Users\admin\Desktop\hoic2.1.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 2864 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Temp\HOIC v2.rar" | C:\Program Files\WinRAR\WinRAR.exe | — | explorer.exe | |||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.60.0 Modules
| |||||||||||||||
Total events
443
Read events
423
Write events
20
Delete events
0
Modification events
| (PID) Process: | (2864) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (2864) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (2864) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\12B\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (2864) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\HOIC v2.rar | |||
| (PID) Process: | (2864) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (2864) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (2864) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (2864) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (2864) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\MainWin |
| Operation: | write | Name: | Placement |
Value: 2C0000000000000001000000FFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFF42000000420000000204000037020000 | |||
| (PID) Process: | (2864) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\General |
| Operation: | write | Name: | LastFolder |
Value: C:\Users\admin\AppData\Local\Temp | |||
Executable files
0
Suspicious files
0
Text files
0
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2864 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa2864.44381\hoic2.1.exe | — | |
MD5:— | SHA256:— | |||
| 2864 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa2864.44381\LizardSquad.Booster.hoic | — | |
MD5:— | SHA256:— | |||
| 2864 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa2864.44381\Tutorial.txt | — | |
MD5:— | SHA256:— | |||
| 2864 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa2864.44381\buttons2\buttons\4add.png | — | |
MD5:— | SHA256:— | |||
| 2864 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa2864.44381\buttons2\buttons\6266.png | — | |
MD5:— | SHA256:— | |||
| 2864 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa2864.44381\buttons2\buttons\666.png | — | |
MD5:— | SHA256:— | |||
| 2864 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa2864.44381\buttons2\buttons\6666.png | — | |
MD5:— | SHA256:— | |||
| 2864 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa2864.44381\buttons2\buttons\add.png | — | |
MD5:— | SHA256:— | |||
| 2864 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa2864.44381\buttons2\buttons\add2.png | — | |
MD5:— | SHA256:— | |||
| 2864 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa2864.44381\buttons2\buttons\add3.png | — | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
74
TCP/UDP connections
74
DNS requests
1
Threats
74
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
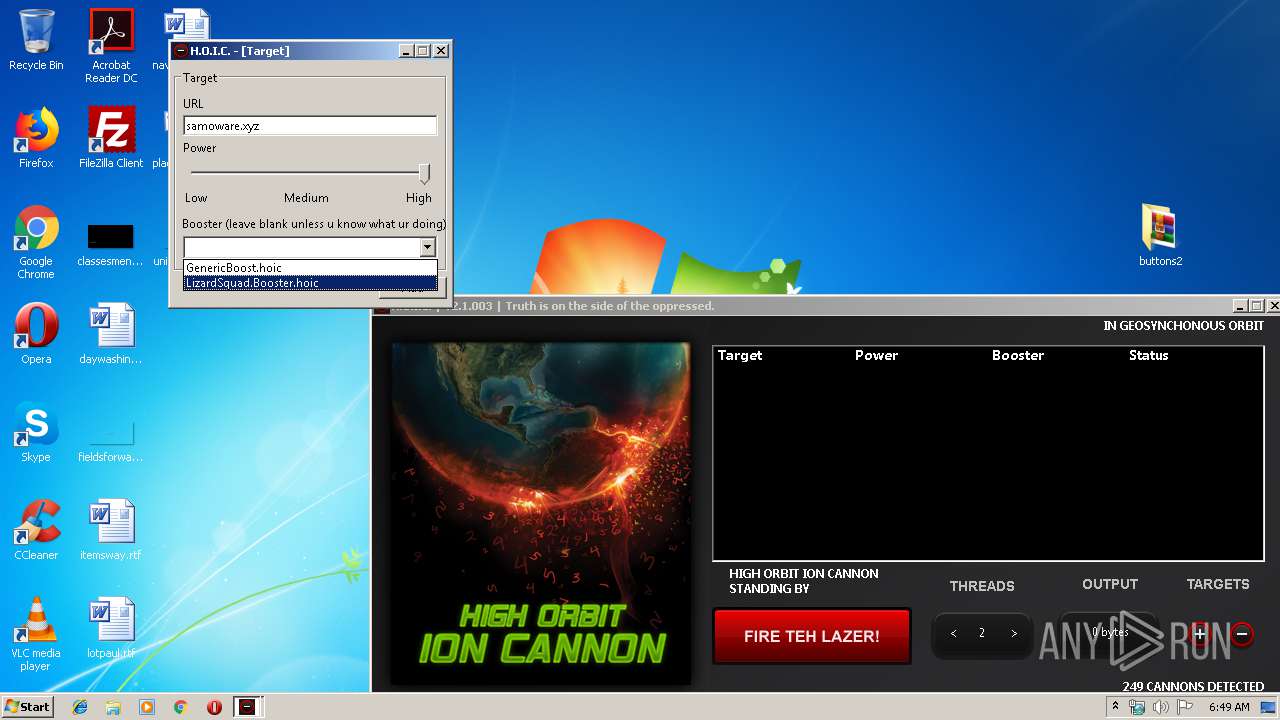
1732 | hoic2.1.exe | GET | 301 | 46.174.50.8:80 | http://samoware.xyz/ | RU | html | 169 b | malicious |
1732 | hoic2.1.exe | GET | 301 | 46.174.50.8:80 | http://samoware.xyz/ | RU | html | 169 b | malicious |
1732 | hoic2.1.exe | GET | 301 | 46.174.50.8:80 | http://samoware.xyz/ | RU | html | 169 b | malicious |
1732 | hoic2.1.exe | GET | 301 | 46.174.50.8:80 | http://samoware.xyz/ | RU | html | 169 b | malicious |
1732 | hoic2.1.exe | GET | 301 | 46.174.50.8:80 | http://samoware.xyz/ | RU | html | 169 b | malicious |
1732 | hoic2.1.exe | GET | 301 | 46.174.50.8:80 | http://samoware.xyz/ | RU | html | 169 b | malicious |
1732 | hoic2.1.exe | GET | 301 | 46.174.50.8:80 | http://samoware.xyz/ | RU | html | 169 b | malicious |
1732 | hoic2.1.exe | GET | 301 | 46.174.50.8:80 | http://samoware.xyz/ | RU | html | 169 b | malicious |
1732 | hoic2.1.exe | GET | 301 | 46.174.50.8:80 | http://samoware.xyz/ | RU | html | 169 b | malicious |
1732 | hoic2.1.exe | GET | 301 | 46.174.50.8:80 | http://samoware.xyz/ | RU | html | 169 b | malicious |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
1732 | hoic2.1.exe | 46.174.50.8:80 | samoware.xyz | RS-Media LLC | RU | malicious |
— | — | 46.174.50.8:80 | samoware.xyz | RS-Media LLC | RU | malicious |
DNS requests
Domain | IP | Reputation |
|---|---|---|
samoware.xyz |
| malicious |
Threats
PID | Process | Class | Message |
|---|---|---|---|
1732 | hoic2.1.exe | Potentially Bad Traffic | AV INFO HTTP Request to a *.xyz domain |
1732 | hoic2.1.exe | Potentially Bad Traffic | AV INFO HTTP Request to a *.xyz domain |
1732 | hoic2.1.exe | Potentially Bad Traffic | AV INFO HTTP Request to a *.xyz domain |
1732 | hoic2.1.exe | Potentially Bad Traffic | AV INFO HTTP Request to a *.xyz domain |
1732 | hoic2.1.exe | Potentially Bad Traffic | AV INFO HTTP Request to a *.xyz domain |
1732 | hoic2.1.exe | Potentially Bad Traffic | AV INFO HTTP Request to a *.xyz domain |
1732 | hoic2.1.exe | Potentially Bad Traffic | AV INFO HTTP Request to a *.xyz domain |
1732 | hoic2.1.exe | Potentially Bad Traffic | AV INFO HTTP Request to a *.xyz domain |
1732 | hoic2.1.exe | Potentially Bad Traffic | AV INFO HTTP Request to a *.xyz domain |
1732 | hoic2.1.exe | Potentially Bad Traffic | AV INFO HTTP Request to a *.xyz domain |