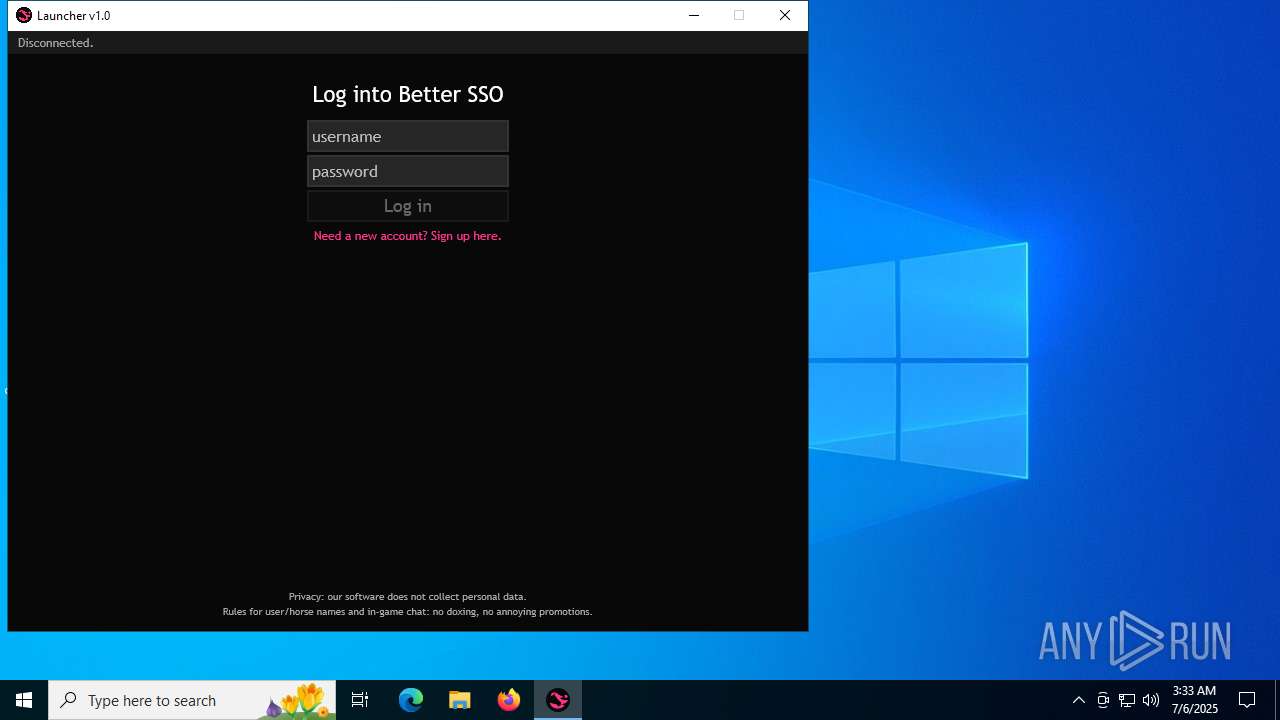
| File name: | bsso_launcher_v1.exe |
| Full analysis: | https://app.any.run/tasks/60ddd46f-caba-4c37-8765-a3a352059b99 |
| Verdict: | Malicious activity |
| Analysis date: | July 06, 2025, 03:33:41 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32+ executable (GUI) x86-64, for MS Windows, 4 sections |
| MD5: | 6A60F6FBD451BFB11D0C943706CEDA0A |
| SHA1: | 15AFE57C61DC29DB351B04F64FD494796EF07E37 |
| SHA256: | 82C2F0AF2F595FF2656F3C418246FFD7F8DAA22D0CC38605977DEF4E42FD32BD |
| SSDEEP: | 98304:jMKPc+QjvFRvN8UJjBxQFI8LbadAe4PqmMRL+O+y6TjWmtX9ZWWXLkvdG171UIrz:jMKLo |
MALICIOUS
No malicious indicators.SUSPICIOUS
Executable content was dropped or overwritten
- bsso_launcher_v1.exe (PID: 2080)
Connects to unusual port
- bsso_tor.exe (PID: 5884)
INFO
Create files in a temporary directory
- bsso_launcher_v1.exe (PID: 2080)
Reads the computer name
- bsso_launcher_v1.exe (PID: 2080)
- bsso_tor.exe (PID: 5884)
Checks supported languages
- bsso_launcher_v1.exe (PID: 2080)
- bsso_tor.exe (PID: 5884)
Creates files or folders in the user directory
- bsso_tor.exe (PID: 5884)
Reads the machine GUID from the registry
- bsso_tor.exe (PID: 5884)
Checks proxy server information
- slui.exe (PID: 1180)
Reads the software policy settings
- slui.exe (PID: 1180)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Generic Win/DOS Executable (50) |
|---|---|---|
| .exe | | | DOS Executable Generic (49.9) |
EXIF
EXE
| MachineType: | AMD AMD64 |
|---|---|
| TimeStamp: | 2024:07:25 22:57:13+00:00 |
| ImageFileCharacteristics: | Executable, Large address aware |
| PEType: | PE32+ |
| LinkerVersion: | 14.4 |
| CodeSize: | 66560 |
| InitializedDataSize: | 2619904 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x5800 |
| OSVersion: | 6 |
| ImageVersion: | - |
| SubsystemVersion: | 6 |
| Subsystem: | Windows GUI |
Total processes
135
Monitored processes
4
Malicious processes
0
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1180 | C:\WINDOWS\System32\slui.exe -Embedding | C:\Windows\System32\slui.exe | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Activation Client Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2080 | "C:\Users\admin\Desktop\bsso_launcher_v1.exe" | C:\Users\admin\Desktop\bsso_launcher_v1.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Modules
| |||||||||||||||
| 4500 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | bsso_tor.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5884 | "C:\Users\admin\AppData\Local\Temp\\bsso_tor.exe" | C:\Users\admin\AppData\Local\Temp\bsso_tor.exe | bsso_launcher_v1.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Modules
| |||||||||||||||
Total events
3 996
Read events
3 996
Write events
0
Delete events
0
Modification events
Executable files
1
Suspicious files
0
Text files
10
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2080 | bsso_launcher_v1.exe | C:\Users\admin\AppData\Local\Temp\bsso_tor.exe | executable | |
MD5:A46913AB31875CF8152C96BD25027B4D | SHA256:66FD723D0DD219807C6D7DCC331E25C8D05ADCCF4A66312928FBE1D0E45670ED | |||
| 5884 | bsso_tor.exe | C:\Users\admin\AppData\Roaming\tor\unverified-microdesc-consensus | text | |
MD5:A30D46477E4E4BFFF04979E863700C70 | SHA256:E5F0860F9FF88B37DACD7CC427F1BCA8ED3B91944EA7B8D0340B5DC19180A58F | |||
| 5884 | bsso_tor.exe | C:\Users\admin\AppData\Roaming\tor\cached-microdesc-consensus.tmp | text | |
MD5:A30D46477E4E4BFFF04979E863700C70 | SHA256:E5F0860F9FF88B37DACD7CC427F1BCA8ED3B91944EA7B8D0340B5DC19180A58F | |||
| 5884 | bsso_tor.exe | C:\Users\admin\AppData\Roaming\tor\cached-certs.tmp | text | |
MD5:1668F303D0DD87C9252FDB5235F6FDA5 | SHA256:7C391BEEC4057DE7784A54207E5EC627CB812667478893CFB854D2897A6EDADD | |||
| 5884 | bsso_tor.exe | C:\Users\admin\AppData\Roaming\tor\cached-microdesc-consensus | text | |
MD5:A30D46477E4E4BFFF04979E863700C70 | SHA256:E5F0860F9FF88B37DACD7CC427F1BCA8ED3B91944EA7B8D0340B5DC19180A58F | |||
| 5884 | bsso_tor.exe | C:\Users\admin\AppData\Roaming\tor\cached-certs | text | |
MD5:1668F303D0DD87C9252FDB5235F6FDA5 | SHA256:7C391BEEC4057DE7784A54207E5EC627CB812667478893CFB854D2897A6EDADD | |||
| 5884 | bsso_tor.exe | C:\Users\admin\AppData\Roaming\tor\state | text | |
MD5:07F3BBDFE334C0F4B16F93FD5FCE520B | SHA256:27EE96DFAC156B35F3338C09B0F778F51FBDC8E3B654015ABE3800D7685A66DA | |||
| 5884 | bsso_tor.exe | C:\Users\admin\AppData\Roaming\tor\unverified-microdesc-consensus.tmp | text | |
MD5:A30D46477E4E4BFFF04979E863700C70 | SHA256:E5F0860F9FF88B37DACD7CC427F1BCA8ED3B91944EA7B8D0340B5DC19180A58F | |||
| 5884 | bsso_tor.exe | C:\Users\admin\AppData\Roaming\tor\state.tmp | text | |
MD5:07F3BBDFE334C0F4B16F93FD5FCE520B | SHA256:27EE96DFAC156B35F3338C09B0F778F51FBDC8E3B654015ABE3800D7685A66DA | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
8
TCP/UDP connections
30
DNS requests
7
Threats
11
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
5944 | MoUsoCoreWorker.exe | GET | 200 | 2.20.245.137:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
1268 | svchost.exe | GET | 200 | 2.20.245.137:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
4372 | RUXIMICS.exe | GET | 200 | 2.20.245.137:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
1268 | svchost.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
5944 | MoUsoCoreWorker.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
4372 | RUXIMICS.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
— | — | POST | 500 | 20.83.72.98:443 | https://activation-v2.sls.microsoft.com/SLActivateProduct/SLActivateProduct.asmx?configextension=Retail | unknown | xml | 512 b | whitelisted |
— | — | POST | 500 | 20.83.72.98:443 | https://activation-v2.sls.microsoft.com/SLActivateProduct/SLActivateProduct.asmx?configextension=Retail | unknown | xml | 512 b | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
5944 | MoUsoCoreWorker.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
1268 | svchost.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4372 | RUXIMICS.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
5944 | MoUsoCoreWorker.exe | 2.20.245.137:80 | crl.microsoft.com | Akamai International B.V. | NL | whitelisted |
1268 | svchost.exe | 2.20.245.137:80 | crl.microsoft.com | Akamai International B.V. | NL | whitelisted |
4372 | RUXIMICS.exe | 2.20.245.137:80 | crl.microsoft.com | Akamai International B.V. | NL | whitelisted |
1268 | svchost.exe | 95.101.149.131:80 | www.microsoft.com | Akamai International B.V. | NL | whitelisted |
5944 | MoUsoCoreWorker.exe | 95.101.149.131:80 | www.microsoft.com | Akamai International B.V. | NL | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
activation-v2.sls.microsoft.com |
| whitelisted |
self.events.data.microsoft.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
5884 | bsso_tor.exe | Misc Attack | ET TOR Known Tor Exit Node Traffic group 10 |
5884 | bsso_tor.exe | Misc Attack | ET TOR Known Tor Relay/Router (Not Exit) Node Traffic group 10 |
5884 | bsso_tor.exe | Misc Attack | ET TOR Known Tor Relay/Router (Not Exit) Node Traffic group 446 |
5884 | bsso_tor.exe | Misc Attack | ET TOR Known Tor Relay/Router (Not Exit) Node Traffic group 228 |
5884 | bsso_tor.exe | Misc Attack | ET TOR Known Tor Relay/Router (Not Exit) Node Traffic group 633 |
5884 | bsso_tor.exe | Misc Attack | ET TOR Known Tor Relay/Router (Not Exit) Node Traffic group 163 |
5884 | bsso_tor.exe | Misc Attack | ET TOR Known Tor Exit Node Traffic group 10 |
5884 | bsso_tor.exe | Misc Attack | ET TOR Known Tor Relay/Router (Not Exit) Node Traffic group 633 |
5884 | bsso_tor.exe | Misc Attack | ET TOR Known Tor Relay/Router (Not Exit) Node Traffic group 163 |
5884 | bsso_tor.exe | Misc Attack | ET TOR Known Tor Relay/Router (Not Exit) Node Traffic group 10 |