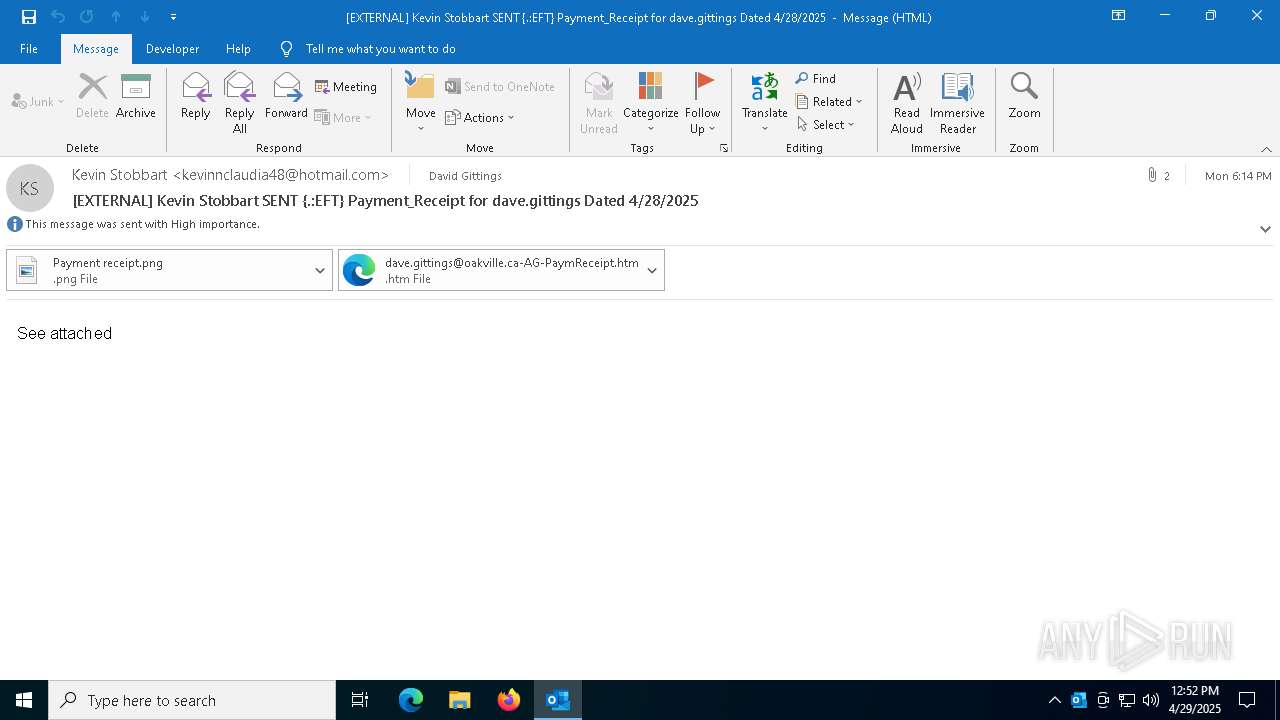
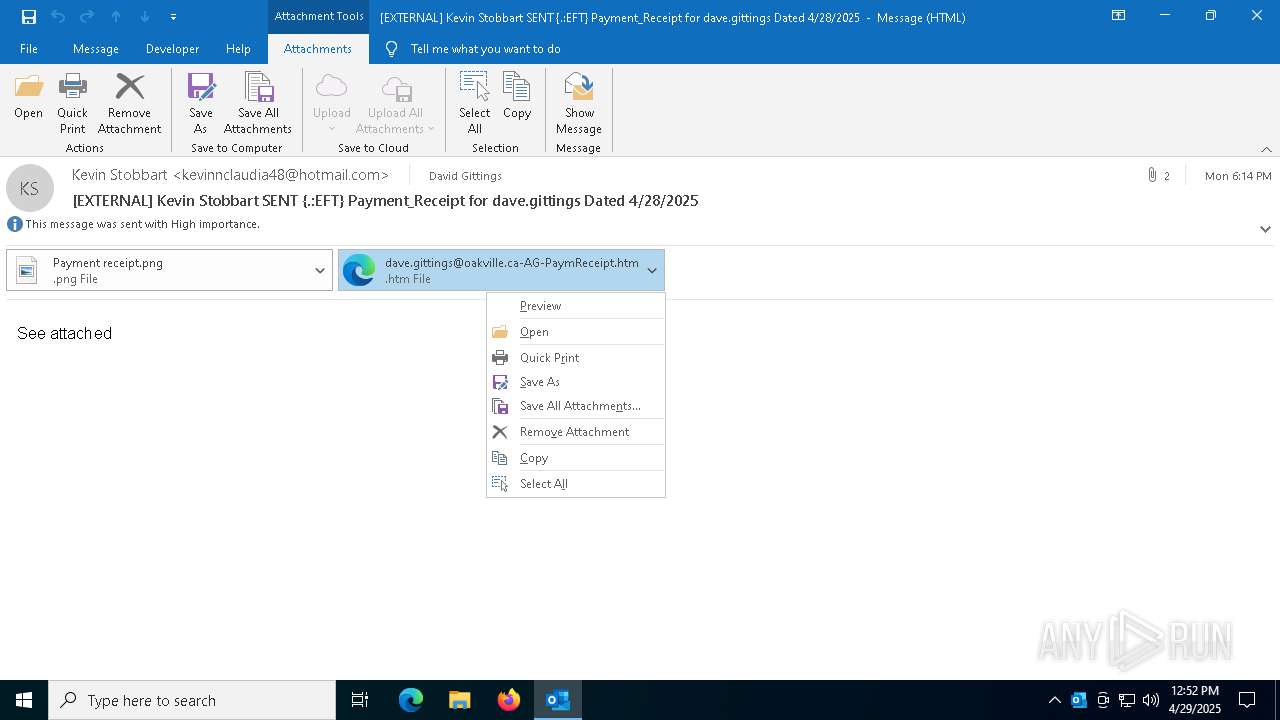
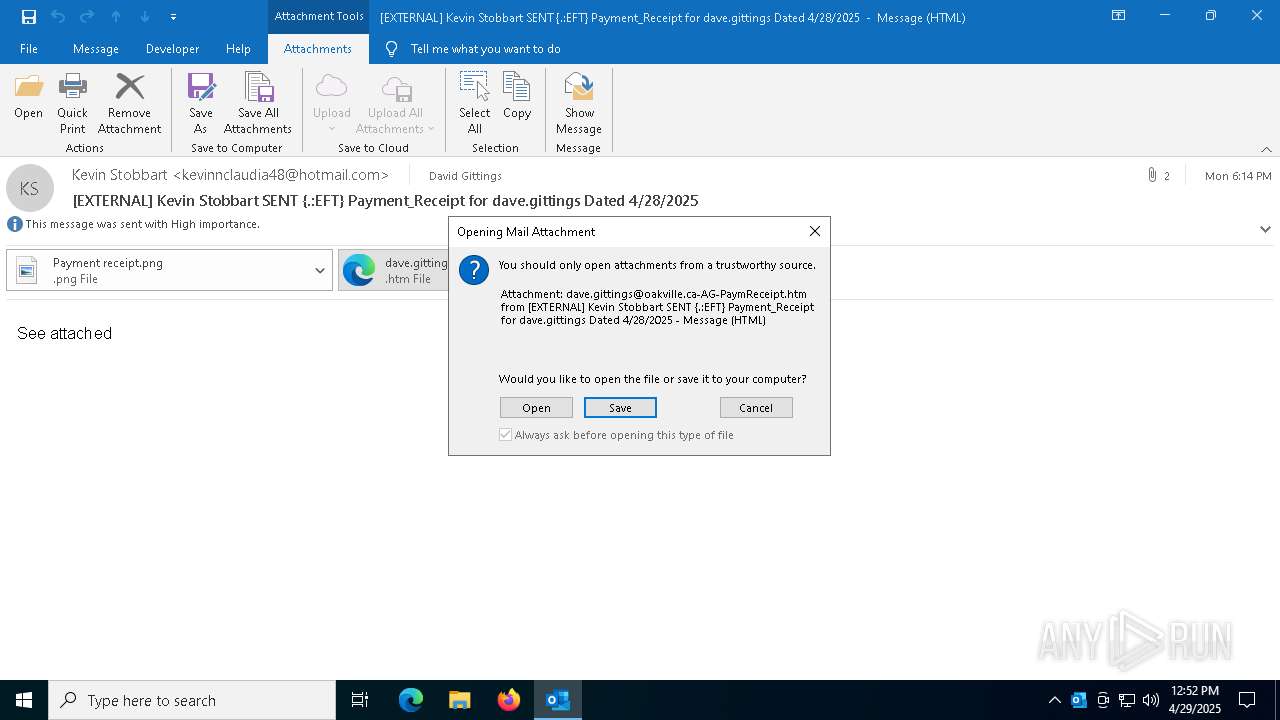
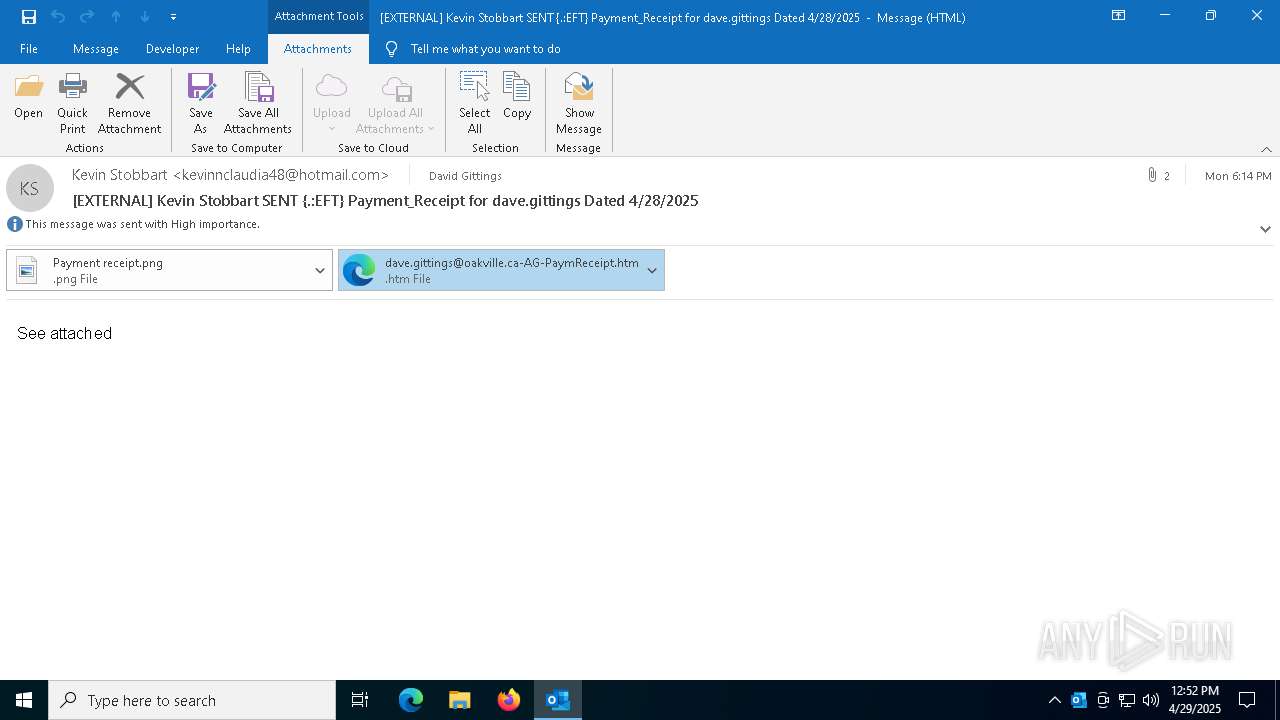
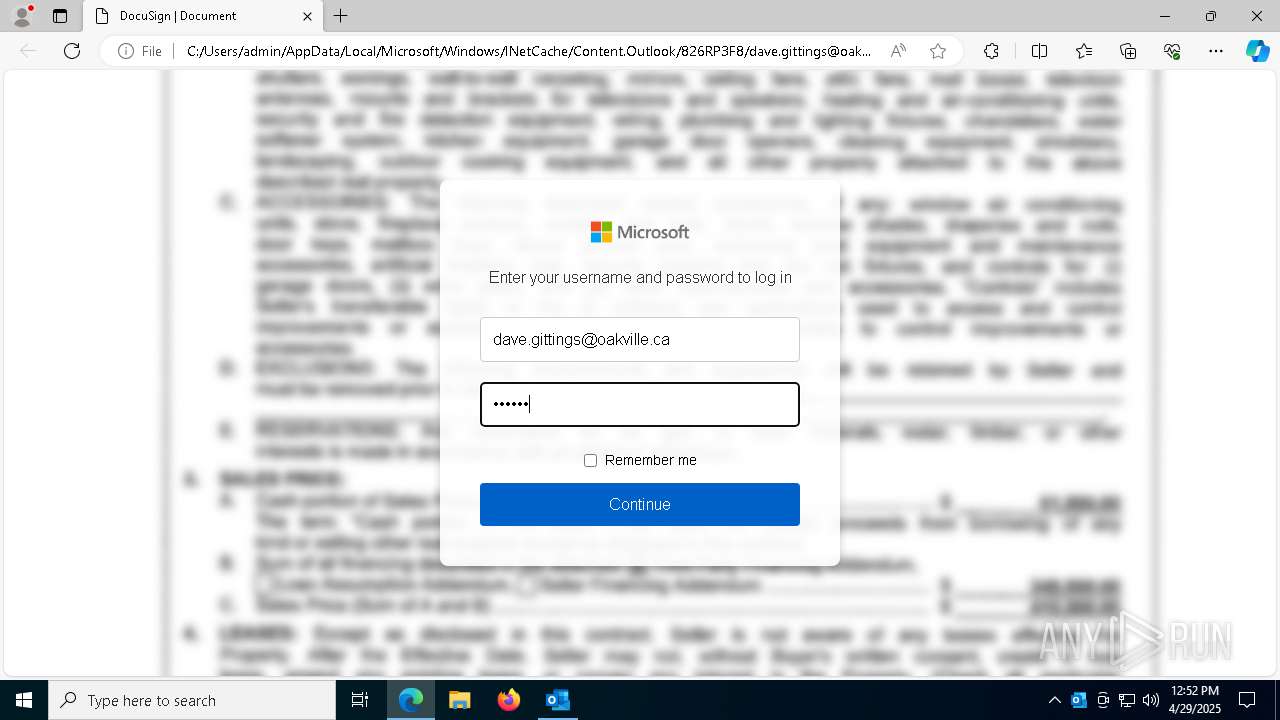
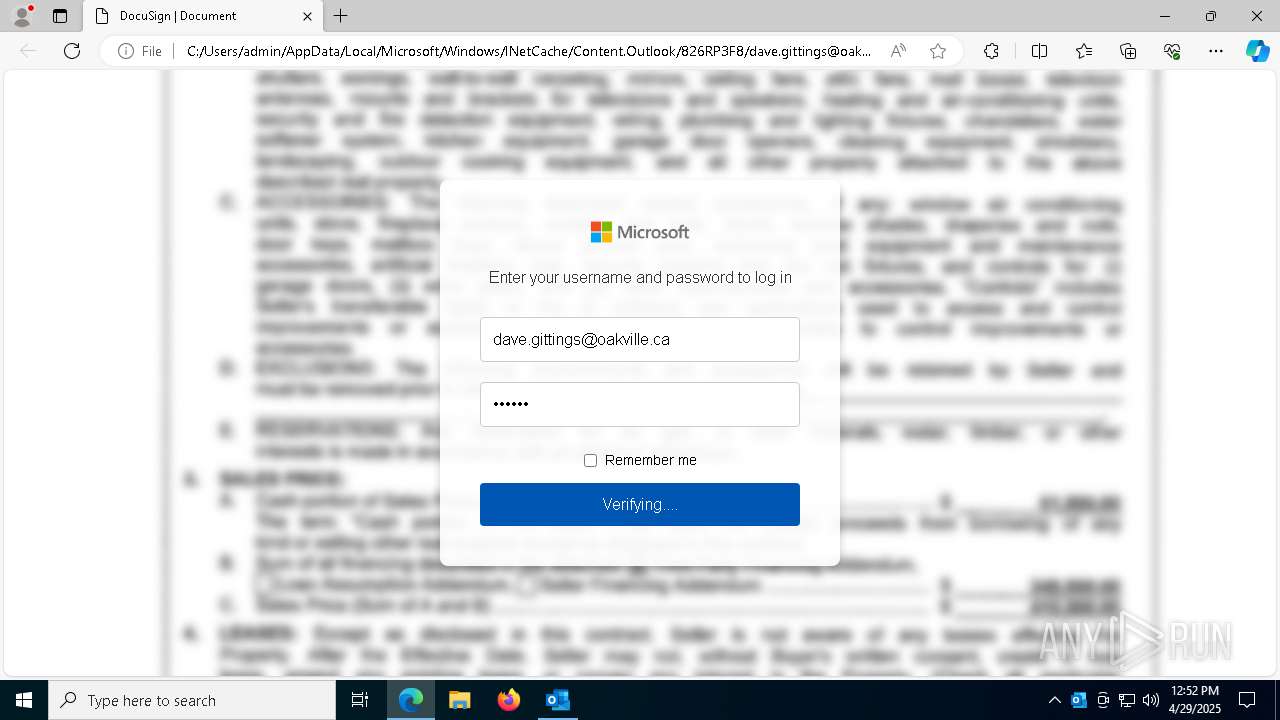
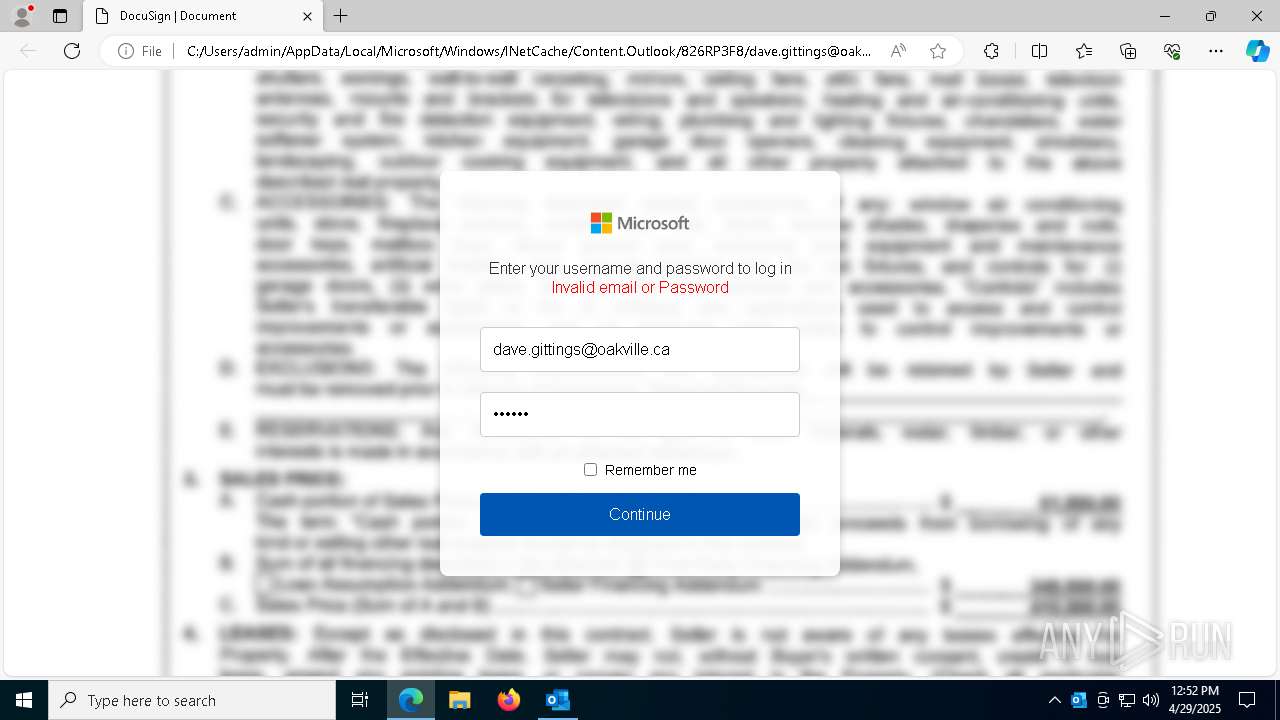
| File name: | EXTERNAL Kevin Stobbart SENT {.EFT} Payment_Receipt for dave.gittings Dated 4282025.msg |
| Full analysis: | https://app.any.run/tasks/0f8ff73f-4862-40f6-a129-8498e915bd1c |
| Verdict: | Malicious activity |
| Analysis date: | April 29, 2025, 12:51:51 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.ms-outlook |
| File info: | CDFV2 Microsoft Outlook Message |
| MD5: | 0597E500B231658196A44033CA684FE1 |
| SHA1: | C1012F4FA208B09F01D503B7747083BE268919FF |
| SHA256: | 82B7670E437FDABEAE881D6731E76E806F39700EDF38F8650DA519C64D39A472 |
| SSDEEP: | 6144:y7iKB4DyRBhVAt7G2VsBt+eobf/Q/QK51k8bTqFL4GxPhZ9hiAT/mSL3YF:y7iKB4DwkG2VsBt284m4F0Gxfte |
MALICIOUS
No malicious indicators.SUSPICIOUS
Possible usage of Discord/Telegram API has been detected (YARA)
- OUTLOOK.EXE (PID: 5256)
INFO
Reads Environment values
- identity_helper.exe (PID: 6512)
Application launched itself
- msedge.exe (PID: 7416)
Checks supported languages
- identity_helper.exe (PID: 6512)
Reads the computer name
- identity_helper.exe (PID: 6512)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
ims-api
(PID) Process(5256) OUTLOOK.EXE
Telegram-Tokens (1)7566743826:AAEFpW4ZACJwXEPQ6E0ceXcmctnV1sgdcRA
Telegram-Info-Links
7566743826:AAEFpW4ZACJwXEPQ6E0ceXcmctnV1sgdcRA
Get info about bothttps://api.telegram.org/bot7566743826:AAEFpW4ZACJwXEPQ6E0ceXcmctnV1sgdcRA/getMe
Get incoming updateshttps://api.telegram.org/bot7566743826:AAEFpW4ZACJwXEPQ6E0ceXcmctnV1sgdcRA/getUpdates
Get webhookhttps://api.telegram.org/bot7566743826:AAEFpW4ZACJwXEPQ6E0ceXcmctnV1sgdcRA/getWebhookInfo
Delete webhookhttps://api.telegram.org/bot7566743826:AAEFpW4ZACJwXEPQ6E0ceXcmctnV1sgdcRA/deleteWebhook
Drop incoming updateshttps://api.telegram.org/bot7566743826:AAEFpW4ZACJwXEPQ6E0ceXcmctnV1sgdcRA/deleteWebhook?drop_pending_updates=true
TRiD
| .msg | | | Outlook Message (58.9) |
|---|---|---|
| .oft | | | Outlook Form Template (34.4) |
Total processes
160
Monitored processes
28
Malicious processes
0
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 496 | "C:\WINDOWS\System32\SLUI.exe" RuleId=3482d82e-ca2c-4e1f-8864-da0267b484b2;Action=AutoActivate;AppId=55c92734-d682-4d71-983e-d6ec3f16059f;SkuId=4de7cb65-cdf1-4de9-8ae8-e3cce27b9f2c;NotificationInterval=1440;Trigger=TimerEvent | C:\Windows\System32\slui.exe | — | SppExtComObj.Exe | |||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows Activation Client Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2552 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --lang=en-US --service-sandbox-type=service --no-appcompat-clear --mojo-platform-channel-handle=6120 --field-trial-handle=2456,i,17634390509562864442,1639200834769825740,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 4844 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --lang=en-US --service-sandbox-type=service --no-appcompat-clear --mojo-platform-channel-handle=1452 --field-trial-handle=2456,i,17634390509562864442,1639200834769825740,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 5204 | C:\WINDOWS\system32\SppExtComObj.exe -Embedding | C:\Windows\System32\SppExtComObj.Exe | — | svchost.exe | |||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: KMS Connection Broker Version: 10.0.19041.3996 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5228 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --lang=en-US --service-sandbox-type=service --no-appcompat-clear --mojo-platform-channel-handle=6004 --field-trial-handle=2456,i,17634390509562864442,1639200834769825740,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 5244 | "C:\Program Files (x86)\Microsoft\Edge\Application\122.0.2365.59\identity_helper.exe" --type=utility --utility-sub-type=winrt_app_id.mojom.WinrtAppIdService --lang=en-US --service-sandbox-type=none --no-appcompat-clear --mojo-platform-channel-handle=5860 --field-trial-handle=2456,i,17634390509562864442,1639200834769825740,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\122.0.2365.59\identity_helper.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: PWA Identity Proxy Host Exit code: 3221226029 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 5256 | "C:\Program Files\Microsoft Office\Root\Office16\OUTLOOK.EXE" /f "C:\Users\admin\AppData\Local\Temp\EXTERNAL Kevin Stobbart SENT {.EFT} Payment_Receipt for dave.gittings Dated 4282025.msg" | C:\Program Files\Microsoft Office\root\Office16\OUTLOOK.EXE | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Outlook Version: 16.0.16026.20146 Modules
ims-api(PID) Process(5256) OUTLOOK.EXE Telegram-Tokens (1)7566743826:AAEFpW4ZACJwXEPQ6E0ceXcmctnV1sgdcRA Telegram-Info-Links 7566743826:AAEFpW4ZACJwXEPQ6E0ceXcmctnV1sgdcRA Get info about bothttps://api.telegram.org/bot7566743826:AAEFpW4ZACJwXEPQ6E0ceXcmctnV1sgdcRA/getMe Get incoming updateshttps://api.telegram.org/bot7566743826:AAEFpW4ZACJwXEPQ6E0ceXcmctnV1sgdcRA/getUpdates Get webhookhttps://api.telegram.org/bot7566743826:AAEFpW4ZACJwXEPQ6E0ceXcmctnV1sgdcRA/getWebhookInfo Delete webhookhttps://api.telegram.org/bot7566743826:AAEFpW4ZACJwXEPQ6E0ceXcmctnV1sgdcRA/deleteWebhook Drop incoming updateshttps://api.telegram.org/bot7566743826:AAEFpW4ZACJwXEPQ6E0ceXcmctnV1sgdcRA/deleteWebhook?drop_pending_updates=true | |||||||||||||||
| 5400 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=chrome.mojom.UtilWin --lang=en-US --service-sandbox-type=none --no-appcompat-clear --mojo-platform-channel-handle=6156 --field-trial-handle=2456,i,17634390509562864442,1639200834769825740,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 6080 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --lang=en-US --service-sandbox-type=service --no-appcompat-clear --mojo-platform-channel-handle=5840 --field-trial-handle=2456,i,17634390509562864442,1639200834769825740,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 6512 | "C:\Program Files (x86)\Microsoft\Edge\Application\122.0.2365.59\identity_helper.exe" --type=utility --utility-sub-type=winrt_app_id.mojom.WinrtAppIdService --lang=en-US --service-sandbox-type=none --no-appcompat-clear --mojo-platform-channel-handle=5860 --field-trial-handle=2456,i,17634390509562864442,1639200834769825740,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\122.0.2365.59\identity_helper.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: PWA Identity Proxy Host Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
Total events
13 794
Read events
12 669
Write events
1 005
Delete events
120
Modification events
| (PID) Process: | (5256) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\Common\ClientTelemetry\Sampling |
| Operation: | write | Name: | 6 |
Value: 01941A000000001000B24E9A3E06000000000000000600000000000000 | |||
| (PID) Process: | (5256) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\Common\CrashPersistence\OUTLOOK\5256 |
| Operation: | write | Name: | 0 |
Value: 0B0E10E4802DE143F22E448BE6B7027103E218230046DDE7AFFDD7A0EEED016A04102400449A7D64B29D01008500A907556E6B6E6F776EC906022222CA0DC2190000C91003783634C5118829D2120B6F00750074006C006F006F006B002E00650078006500C51620C517808004C91808323231322D44656300 | |||
| (PID) Process: | (5256) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Outlook\Diagnostics |
| Operation: | delete value | Name: | BootCommand |
Value: | |||
| (PID) Process: | (5256) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Outlook\Diagnostics |
| Operation: | delete value | Name: | BootFailureCount |
Value: | |||
| (PID) Process: | (5256) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Outlook\Diagnostics\BootDiagnosticsDataPreviousSession |
| Operation: | delete key | Name: | (default) |
Value: | |||
| (PID) Process: | (5256) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Outlook\Diagnostics\BootDiagnosticsDataPreviousSession |
| Operation: | write | Name: | CantBootResolution |
Value: BootSuccess | |||
| (PID) Process: | (5256) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Outlook\Diagnostics\BootDiagnosticsDataPreviousSession |
| Operation: | write | Name: | ProfileBeingOpened |
Value: Outlook | |||
| (PID) Process: | (5256) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Outlook\Diagnostics\BootDiagnosticsDataPreviousSession |
| Operation: | write | Name: | SessionId |
Value: C3D8E96E-C1AF-4750-8D52-F4E28119C131 | |||
| (PID) Process: | (5256) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Outlook\Diagnostics\BootDiagnosticsDataPreviousSession |
| Operation: | write | Name: | BootDiagnosticsLogFile |
Value: C:\Users\admin\AppData\Local\Temp\Outlook Logging\OUTLOOK_16_0_16026_20146-20240718T1116060318-1644.etl | |||
| (PID) Process: | (5256) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Outlook\Diagnostics |
| Operation: | delete value | Name: | ProfileBeingOpened |
Value: | |||
Executable files
1
Suspicious files
198
Text files
49
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 5256 | OUTLOOK.EXE | C:\Users\admin\Documents\Outlook Files\Outlook1.pst | — | |
MD5:— | SHA256:— | |||
| 5256 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\Office\16.0\AddInClassifierCache\OfficeSharedEntitiesUpdated.bin | text | |
MD5:E7BB97542570CD39D401D5764E5D864F | SHA256:39EC8024AC325DD5087173122E45CE4168CE3193605FCB4EA9C07BF6FCC1AFB1 | |||
| 5256 | OUTLOOK.EXE | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\E2C6CBAF0AF08CF203BA74BF0D0AB6D5_6372E0472AFF76BB926C97818BC773B9 | binary | |
MD5:F84931D22CE1015CBF202865B97AEC7D | SHA256:106736002167C15BC327D3545E8F8679A1178D3D161DBE93463C1BD111AC661B | |||
| 5256 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\INetCache\Content.Outlook\826RP3F8\Payment receipt.png | binary | |
MD5:E7FE1126CC2BA9974830897A0EB5FBE7 | SHA256:BBB0F40A3CE0970758CFF5E45846F6DB1E9FC2687972AA7198CA3BF282BA533B | |||
| 5256 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\Outlook\RoamCache\Stream_TableViewPreviewPrefs_2_4D8A0807FD34EB45AA8D866D1A2F41B2.dat | xml | |
MD5:0E092DB99AEE99FDFF9B5B222C732CFD | SHA256:D1614AD99ADED9F6F5C1BE7FE7FFA5124BD04A526580DA3818EA8A954E852AA6 | |||
| 7416 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Variations | binary | |
MD5:6971E42ED64D2BE125547F021EB852B1 | SHA256:B46CFDC4106DF566F71AA34D6F10B53767C561DFD17DD07A5930A18E67BB344B | |||
| 5256 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\TokenBroker\Cache\56a61aeb75d8f5be186c26607f4bb213abe7c5ec.tbres | binary | |
MD5:6648F2819D1ACF64B0655D2B8AE620B8 | SHA256:22761A9B794F8A2882B48F606FEB8EE984D5EDBBCB4E904D06693D121A9473C0 | |||
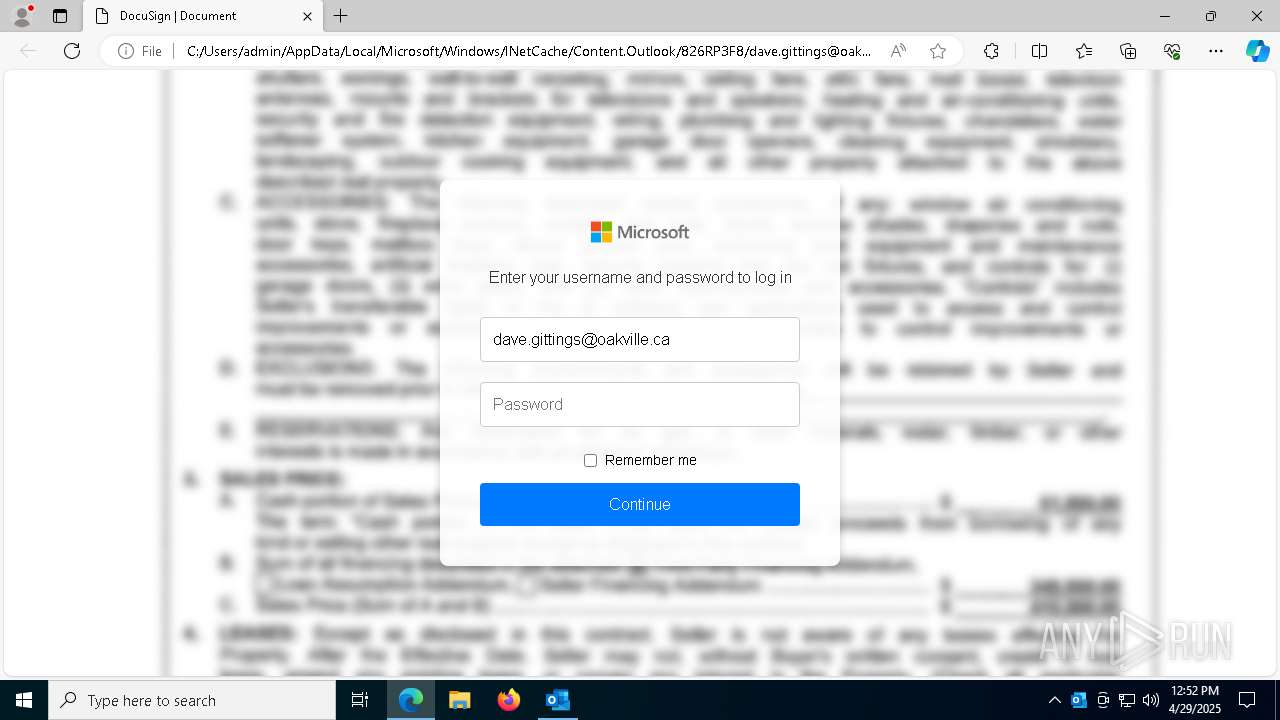
| 5256 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\INetCache\Content.Outlook\826RP3F8\dave.gittings@oakville.ca-AG-PaymReceipt.htm:Zone.Identifier | text | |
MD5:FBCCF14D504B7B2DBCB5A5BDA75BD93B | SHA256:EACD09517CE90D34BA562171D15AC40D302F0E691B439F91BE1B6406E25F5913 | |||
| 7416 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\commerce_subscription_db\LOG.old~RF10ed40.TMP | — | |
MD5:— | SHA256:— | |||
| 7416 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\commerce_subscription_db\LOG.old | — | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
6
TCP/UDP connections
43
DNS requests
51
Threats
3
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | GET | 200 | 23.216.77.21:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 2.23.181.156:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
5256 | OUTLOOK.EXE | GET | 200 | 184.30.131.245:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEA77flR%2B3w%2FxBpruV2lte6A%3D | unknown | — | — | whitelisted |
4208 | SIHClient.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
4208 | SIHClient.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
6544 | svchost.exe | GET | 200 | 184.30.131.245:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 23.216.77.21:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 2.23.181.156:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
— | — | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
2104 | svchost.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
5256 | OUTLOOK.EXE | 52.123.128.14:443 | ecs.office.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
6544 | svchost.exe | 20.190.159.73:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
6544 | svchost.exe | 184.30.131.245:80 | ocsp.digicert.com | AKAMAI-AS | US | whitelisted |
5256 | OUTLOOK.EXE | 52.109.68.129:443 | roaming.officeapps.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | FR | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
ecs.office.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
roaming.officeapps.live.com |
| whitelisted |
omex.cdn.office.net |
| whitelisted |
messaging.lifecycle.office.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
7656 | msedge.exe | Misc activity | ET HUNTING Telegram API Domain in DNS Lookup |
7656 | msedge.exe | Misc activity | ET HUNTING Telegram API Domain in DNS Lookup |
7656 | msedge.exe | Misc activity | ET HUNTING Observed Telegram API Domain (api .telegram .org in TLS SNI) |