| URL: | crl.verisign.com |
| Full analysis: | https://app.any.run/tasks/41cd7b06-6ace-40ec-aae8-ff0c0f67cd76 |
| Verdict: | Malicious activity |
| Analysis date: | March 05, 2024, 03:52:08 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MD5: | 740B1719F2CC389D72416720D88F453F |
| SHA1: | A6378FDB0E9CC384D2FB318722976706D8D28996 |
| SHA256: | 82AD8EFB2D8AD6D868DA6FFE541103A35B136C4F286E05551171E12EFC3B0F59 |
| SSDEEP: | 3:qTyMqdI:qWMoI |
MALICIOUS
Starts Visual C# compiler
- sdiagnhost.exe (PID: 952)
Drops the executable file immediately after the start
- csc.exe (PID: 784)
- csc.exe (PID: 2748)
- csc.exe (PID: 3336)
SUSPICIOUS
Process drops legitimate windows executable
- msdt.exe (PID: 2588)
Probably uses Microsoft diagnostics tool to execute malicious payload
- pcwrun.exe (PID: 764)
Reads settings of System Certificates
- msdt.exe (PID: 2588)
Reads the Internet Settings
- sdiagnhost.exe (PID: 952)
Uses .NET C# to load dll
- sdiagnhost.exe (PID: 952)
Executable content was dropped or overwritten
- csc.exe (PID: 2748)
- csc.exe (PID: 784)
- csc.exe (PID: 3336)
INFO
The process uses the downloaded file
- iexplore.exe (PID: 3864)
Modifies the phishing filter of IE
- iexplore.exe (PID: 3864)
Application launched itself
- iexplore.exe (PID: 3864)
Manual execution by a user
- csrstub.exe (PID: 3224)
- pcwrun.exe (PID: 764)
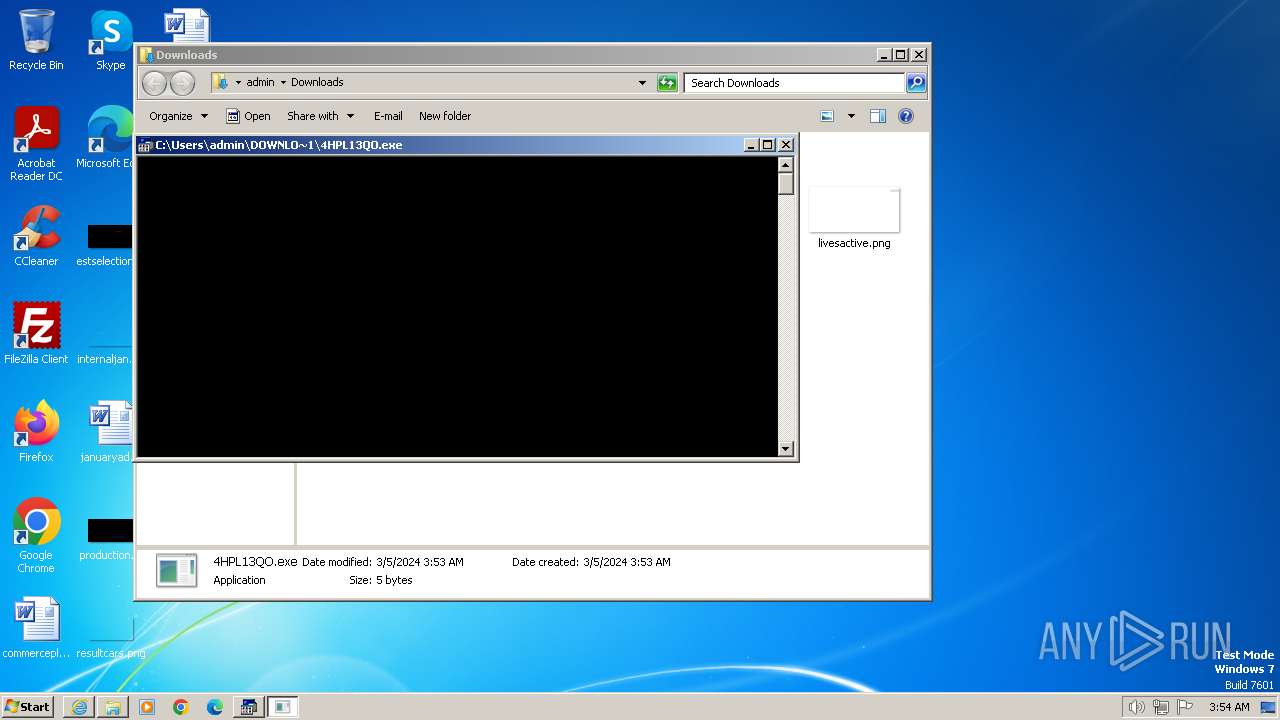
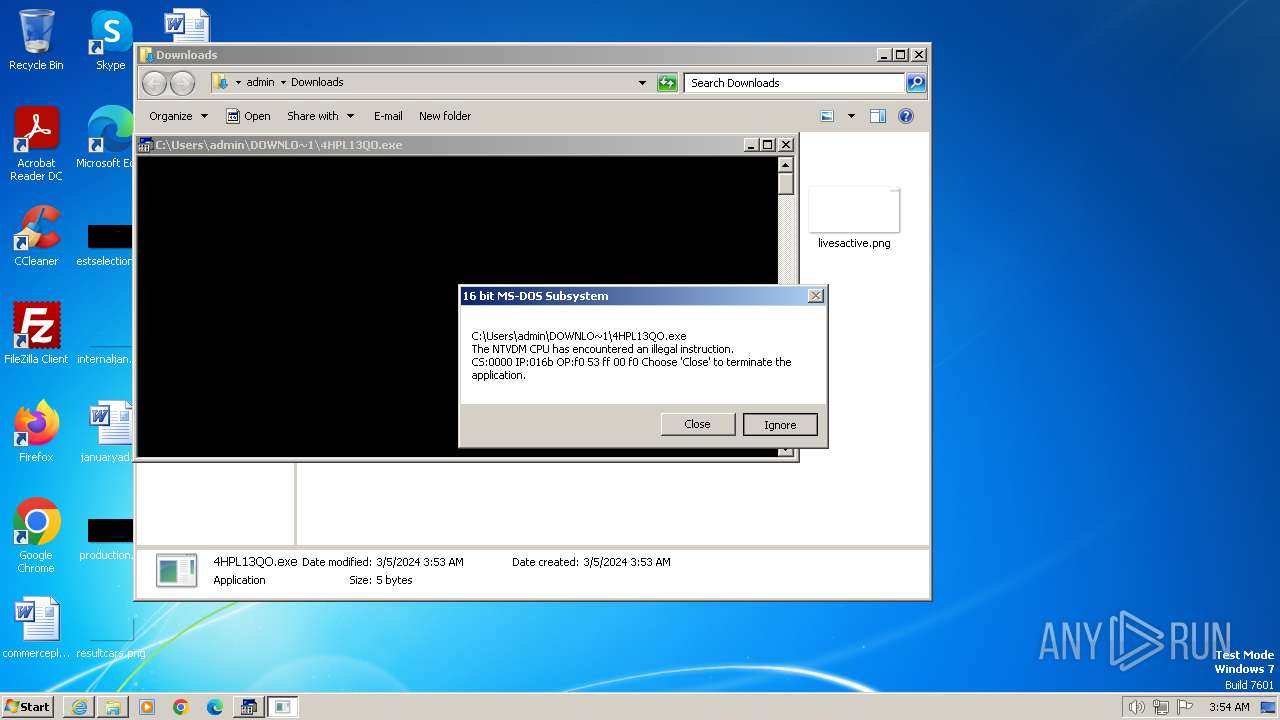
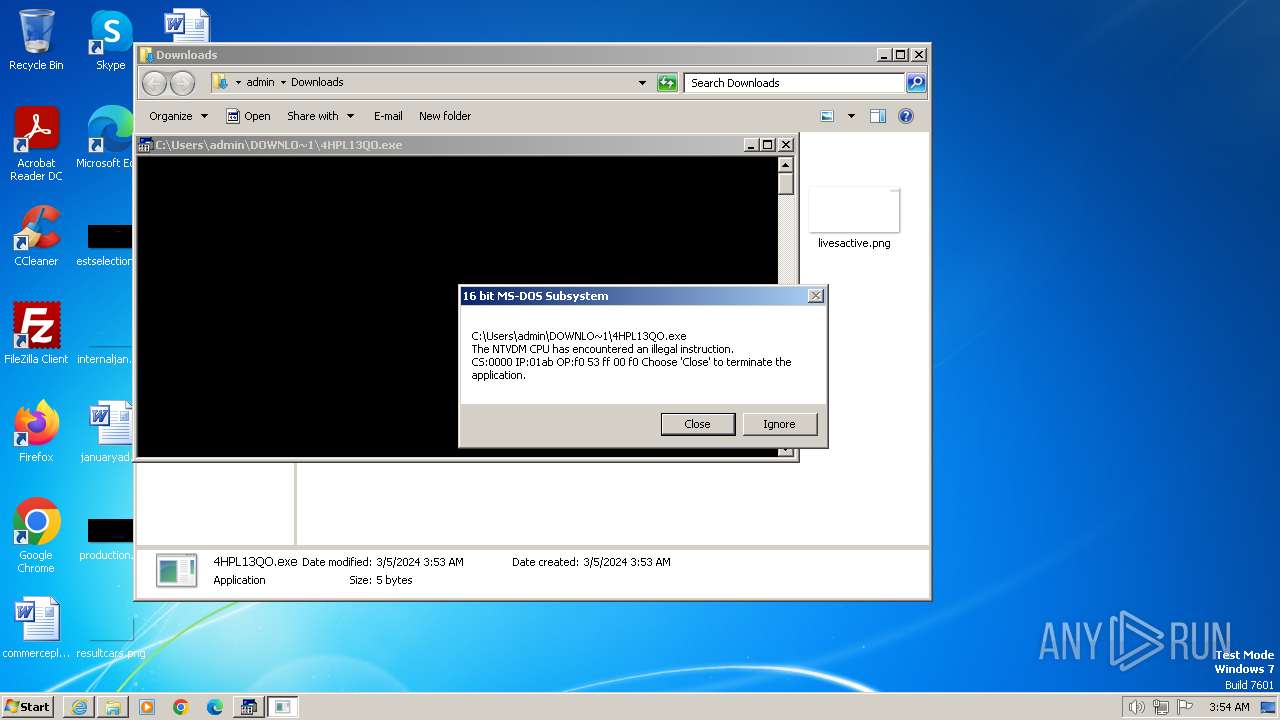
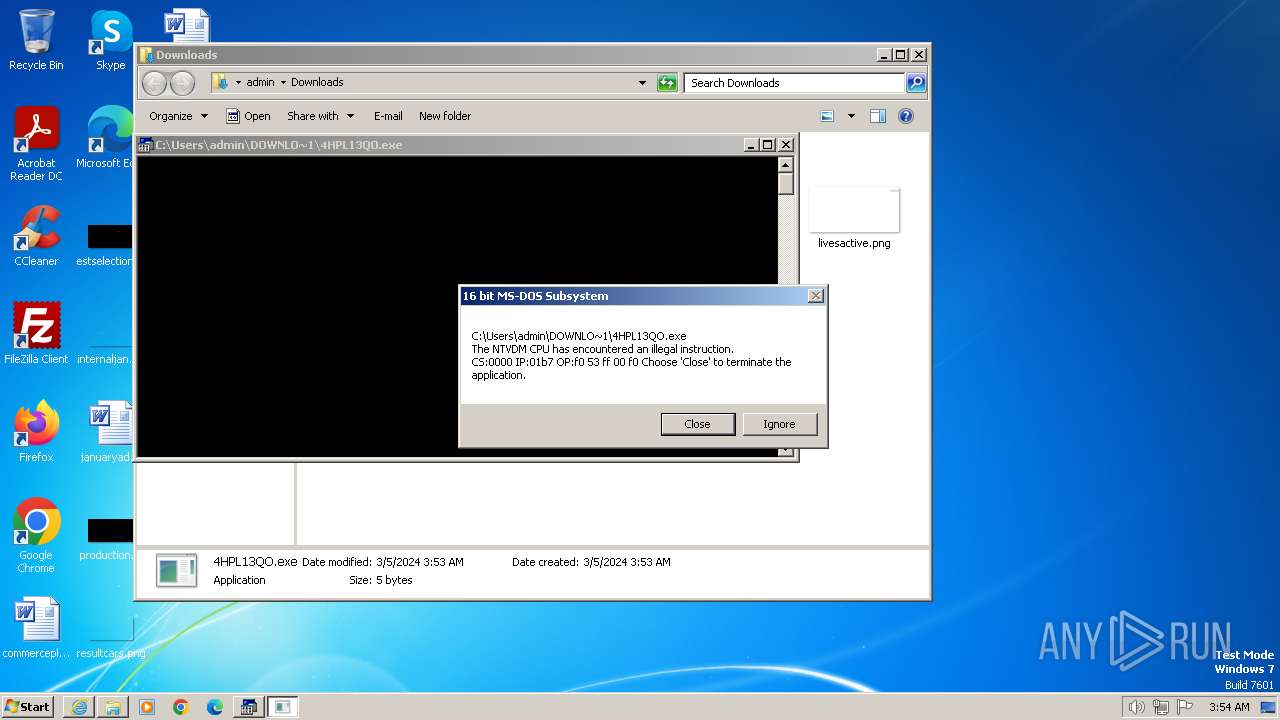
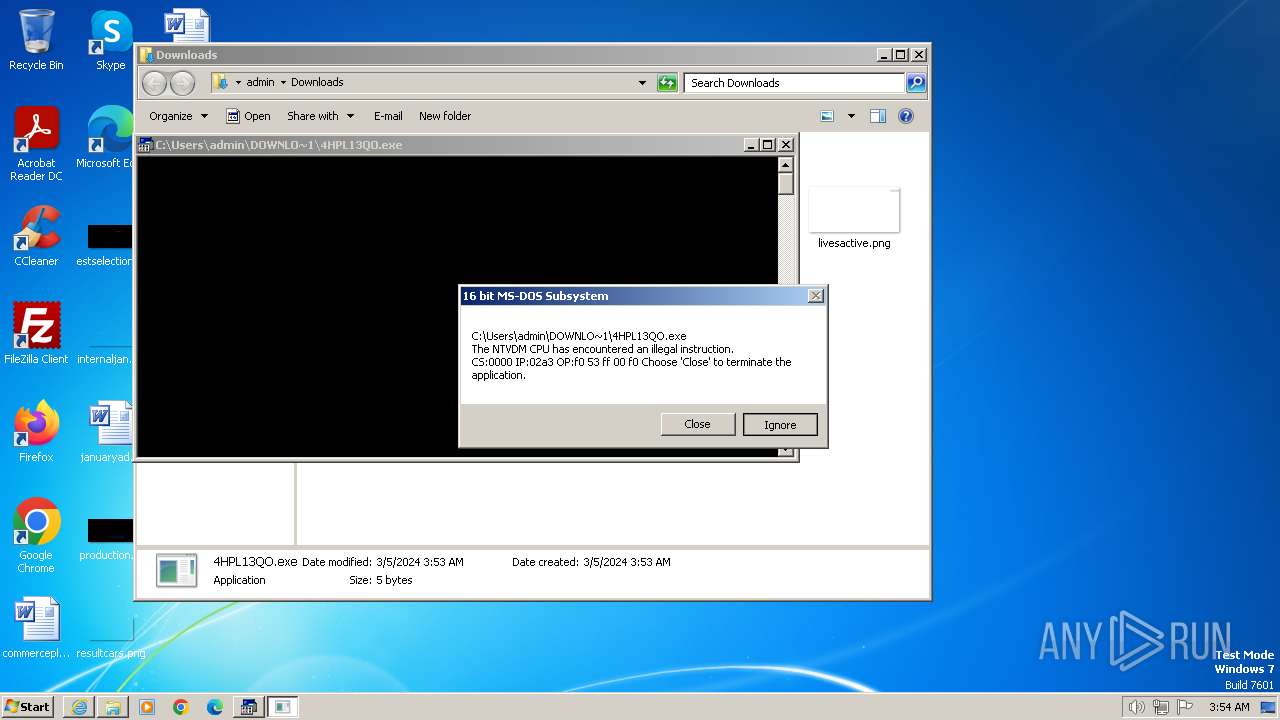
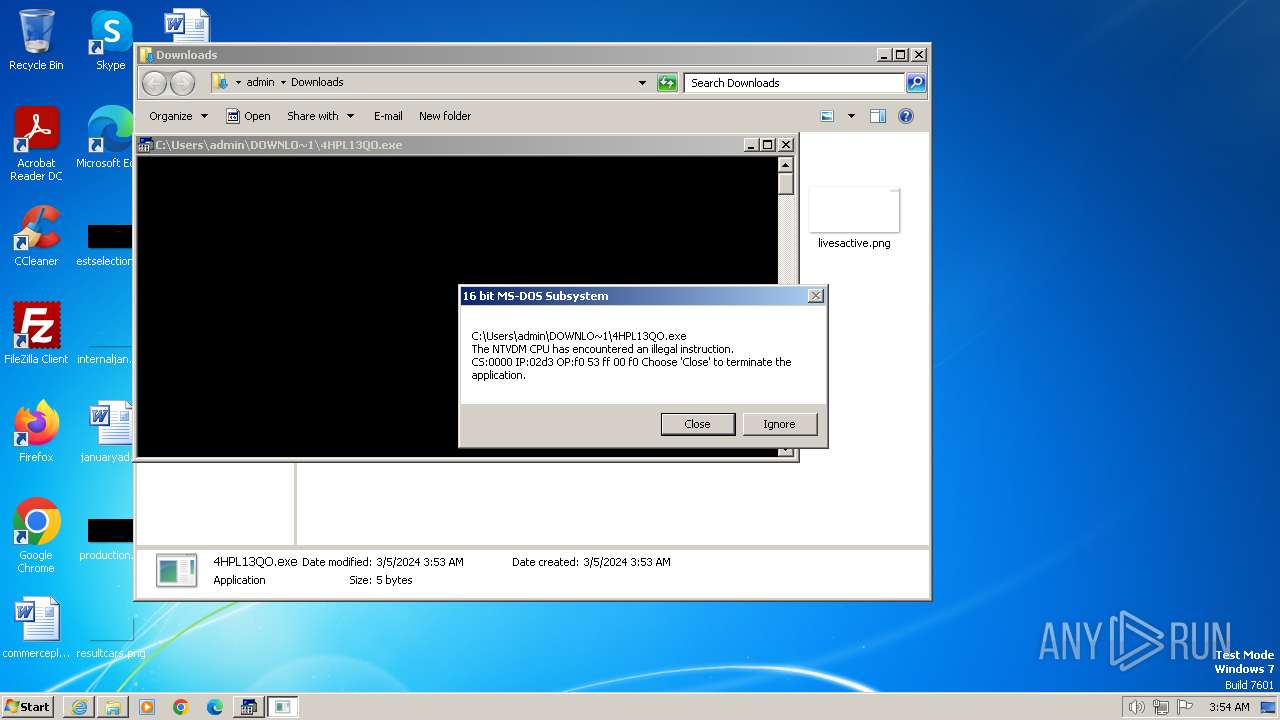
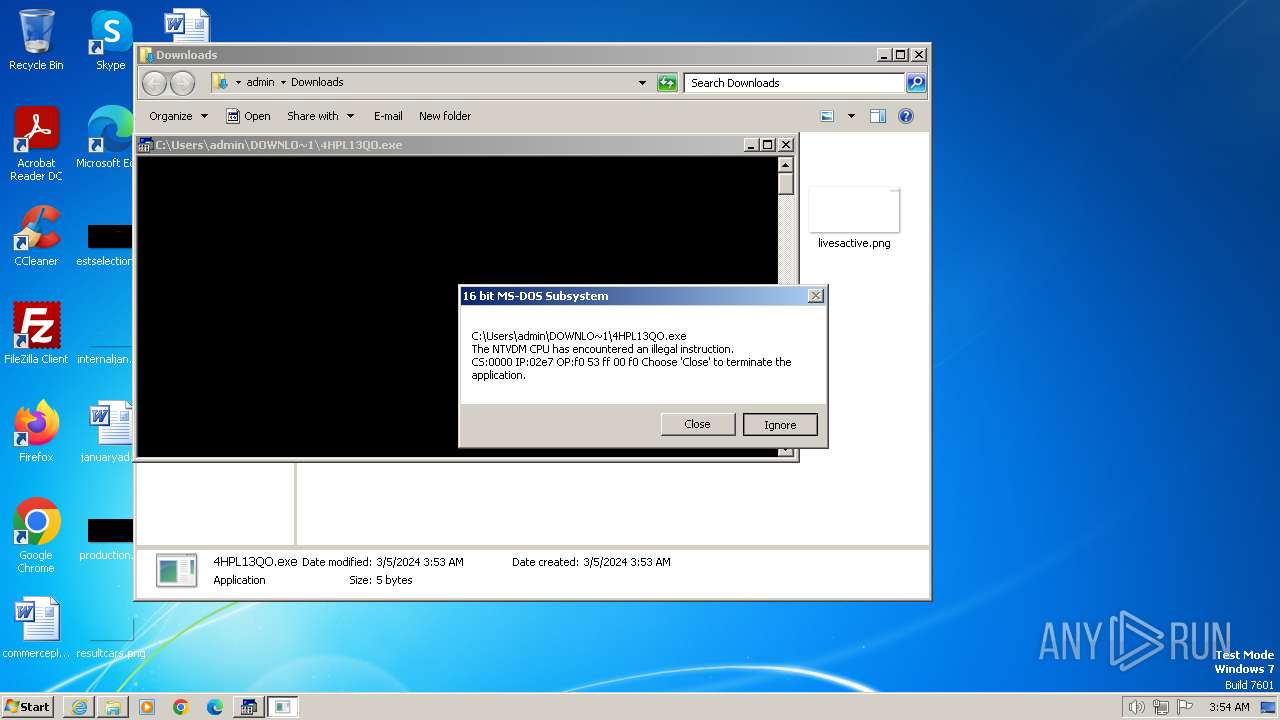
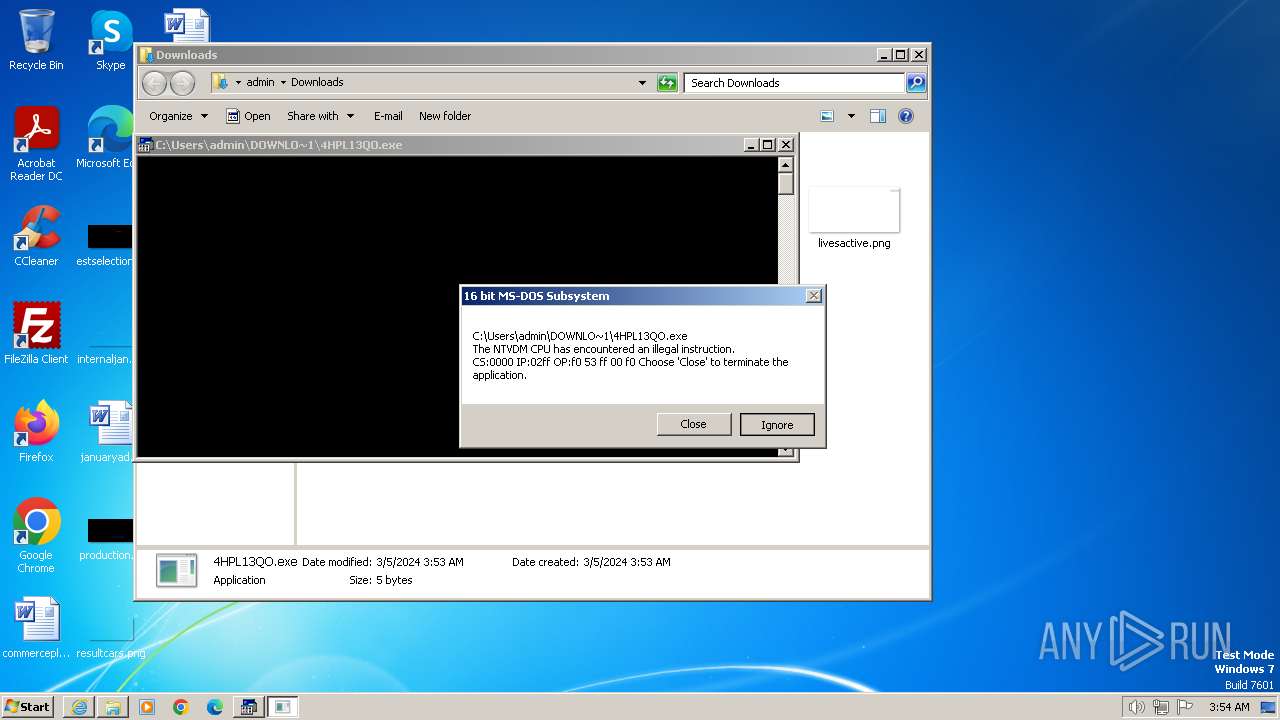
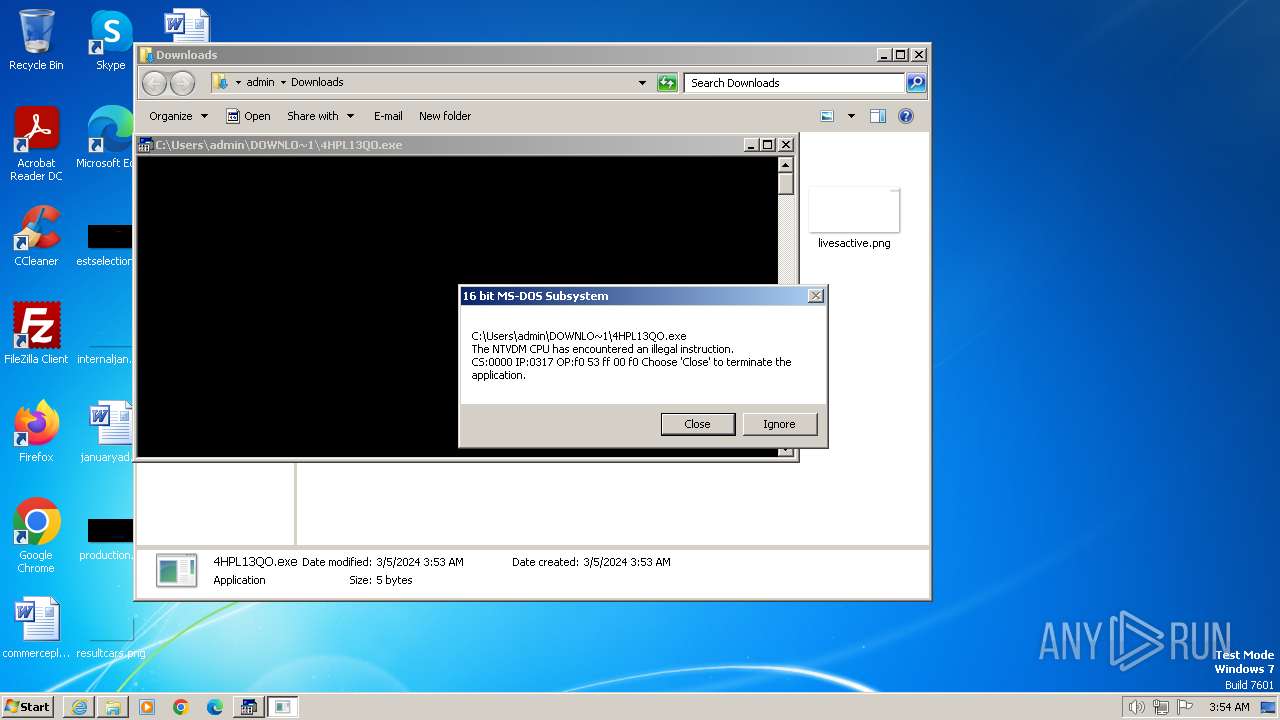
- ntvdm.exe (PID: 3400)
- notepad++.exe (PID: 4072)
Drops the executable file immediately after the start
- msdt.exe (PID: 2588)
Create files in a temporary directory
- pcwrun.exe (PID: 764)
- msdt.exe (PID: 2588)
- sdiagnhost.exe (PID: 952)
- csc.exe (PID: 784)
- cvtres.exe (PID: 2344)
- csc.exe (PID: 2748)
- cvtres.exe (PID: 2936)
- csc.exe (PID: 3336)
- cvtres.exe (PID: 2984)
Reads the software policy settings
- msdt.exe (PID: 2588)
Reads security settings of Internet Explorer
- msdt.exe (PID: 2588)
- sdiagnhost.exe (PID: 952)
Checks supported languages
- csc.exe (PID: 784)
- cvtres.exe (PID: 2344)
- csc.exe (PID: 2748)
- csc.exe (PID: 3336)
- cvtres.exe (PID: 2936)
- cvtres.exe (PID: 2984)
Reads the machine GUID from the registry
- csc.exe (PID: 784)
- cvtres.exe (PID: 2344)
- csc.exe (PID: 2748)
- cvtres.exe (PID: 2936)
- csc.exe (PID: 3336)
- cvtres.exe (PID: 2984)
Creates files or folders in the user directory
- msdt.exe (PID: 2588)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
61
Monitored processes
15
Malicious processes
2
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
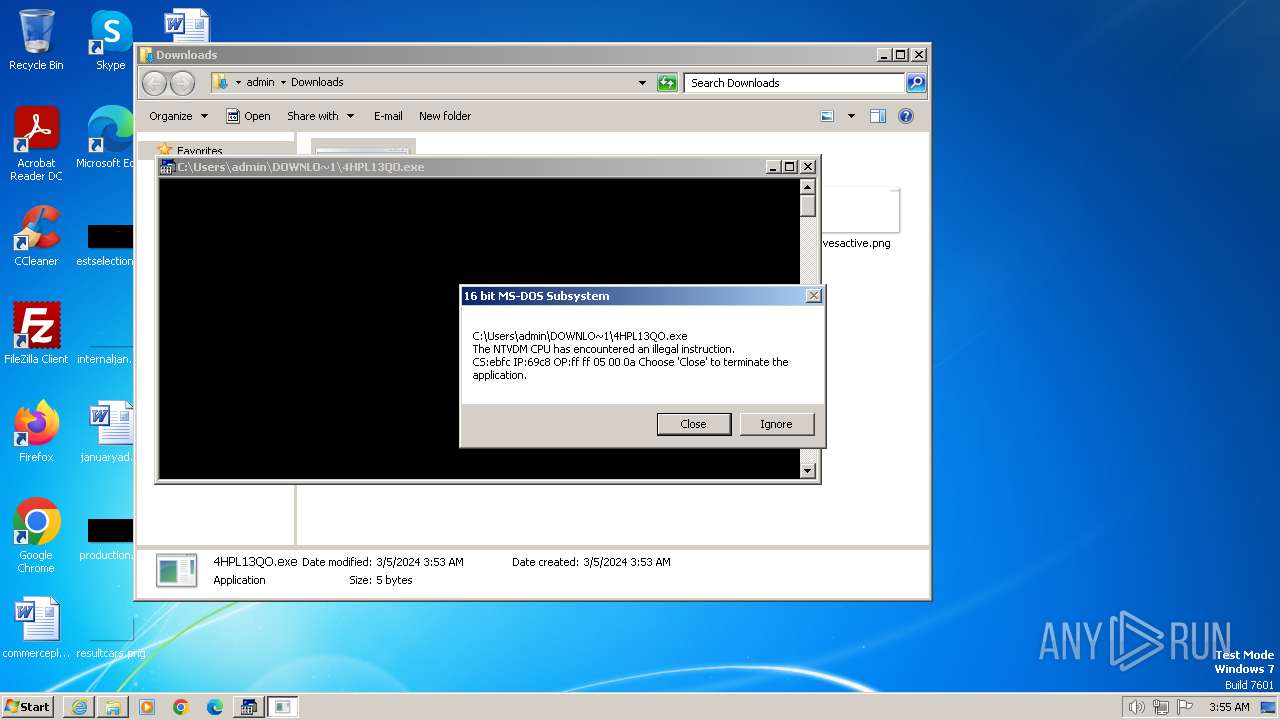
| 764 | C:\Windows\system32\pcwrun.exe "C:\Users\admin\Downloads\4HPL13QO.exe" | C:\Windows\System32\pcwrun.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Program Compatibility Troubleshooter Invoker Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 784 | "C:\Windows\Microsoft.NET\Framework\v2.0.50727\csc.exe" /noconfig /fullpaths @"C:\Users\admin\AppData\Local\Temp\aw9fkhoz.cmdline" | C:\Windows\Microsoft.NET\Framework\v2.0.50727\csc.exe | sdiagnhost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Visual C# Command Line Compiler Exit code: 0 Version: 8.0.50727.5483 (Win7SP1GDR.050727-5400) Modules
| |||||||||||||||
| 952 | C:\Windows\System32\sdiagnhost.exe -Embedding | C:\Windows\System32\sdiagnhost.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Scripted Diagnostics Native Host Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
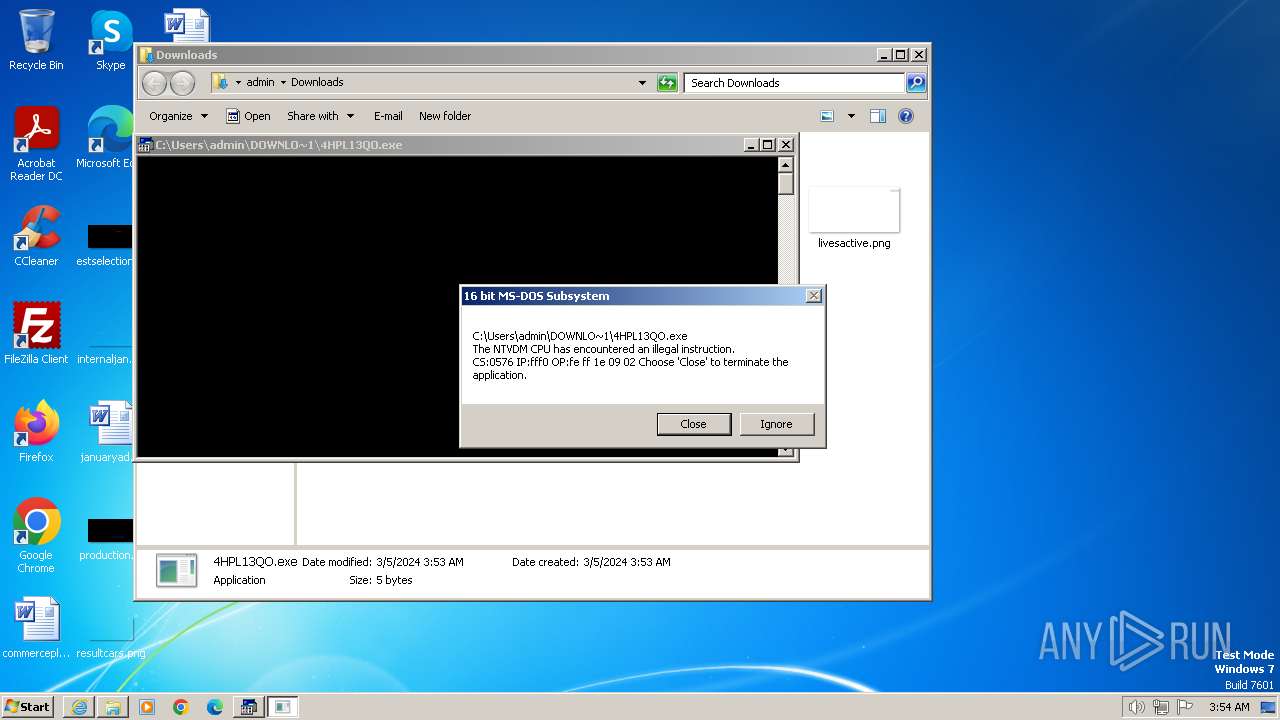
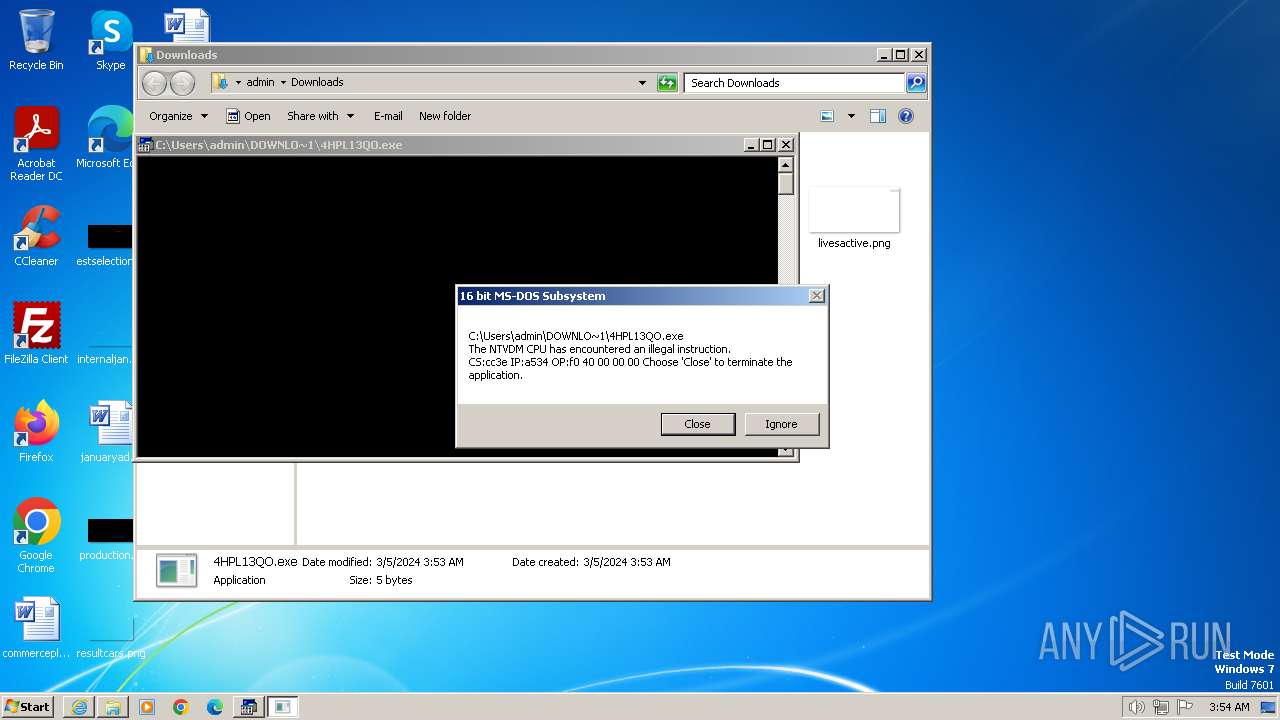
| 1792 | "C:\Windows\system32\ntvdm.exe" -i2 | C:\Windows\System32\ntvdm.exe | — | csrstub.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: NTVDM.EXE Exit code: 255 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2344 | C:\Windows\Microsoft.NET\Framework\v2.0.50727\cvtres.exe /NOLOGO /READONLY /MACHINE:IX86 "/OUT:C:\Users\admin\AppData\Local\Temp\RES8A6B.tmp" "c:\Users\admin\AppData\Local\Temp\CSC8A6A.tmp" | C:\Windows\Microsoft.NET\Framework\v2.0.50727\cvtres.exe | — | csc.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft® Resource File To COFF Object Conversion Utility Exit code: 0 Version: 8.00.50727.5003 (Win7SP1GDR.050727-5400) Modules
| |||||||||||||||
| 2588 | C:\Windows\System32\msdt.exe -path C:\Windows\diagnostics\index\PCWDiagnostic.xml -af C:\Users\admin\AppData\Local\Temp\PCW85D6.xml /skip TRUE | C:\Windows\System32\msdt.exe | — | pcwrun.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Diagnostics Troubleshooting Wizard Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2748 | "C:\Windows\Microsoft.NET\Framework\v2.0.50727\csc.exe" /noconfig /fullpaths @"C:\Users\admin\AppData\Local\Temp\szzfbj4j.cmdline" | C:\Windows\Microsoft.NET\Framework\v2.0.50727\csc.exe | sdiagnhost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Visual C# Command Line Compiler Exit code: 0 Version: 8.0.50727.5483 (Win7SP1GDR.050727-5400) Modules
| |||||||||||||||
| 2936 | C:\Windows\Microsoft.NET\Framework\v2.0.50727\cvtres.exe /NOLOGO /READONLY /MACHINE:IX86 "/OUT:C:\Users\admin\AppData\Local\Temp\RES8AC9.tmp" "c:\Users\admin\AppData\Local\Temp\CSC8AC8.tmp" | C:\Windows\Microsoft.NET\Framework\v2.0.50727\cvtres.exe | — | csc.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft® Resource File To COFF Object Conversion Utility Exit code: 0 Version: 8.00.50727.5003 (Win7SP1GDR.050727-5400) Modules
| |||||||||||||||
| 2984 | C:\Windows\Microsoft.NET\Framework\v2.0.50727\cvtres.exe /NOLOGO /READONLY /MACHINE:IX86 "/OUT:C:\Users\admin\AppData\Local\Temp\RES8B84.tmp" "c:\Users\admin\AppData\Local\Temp\CSC8B73.tmp" | C:\Windows\Microsoft.NET\Framework\v2.0.50727\cvtres.exe | — | csc.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft® Resource File To COFF Object Conversion Utility Exit code: 0 Version: 8.00.50727.5003 (Win7SP1GDR.050727-5400) Modules
| |||||||||||||||
| 3224 | C:\Windows\system32\csrstub.exe 67634196 -P "C:\Users\admin\Downloads\4HPL13QO.exe" | C:\Windows\System32\csrstub.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: allows lua to launch 16-bit applications Exit code: 255 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
22 074
Read events
21 921
Write events
124
Delete events
29
Modification events
| (PID) Process: | (3864) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPDaysSinceLastAutoMigration |
Value: 1 | |||
| (PID) Process: | (3864) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPLastLaunchLowDateTime |
Value: | |||
| (PID) Process: | (3864) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPLastLaunchHighDateTime |
Value: 31092400 | |||
| (PID) Process: | (3864) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateLowDateTime |
Value: | |||
| (PID) Process: | (3864) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateHighDateTime |
Value: 31092400 | |||
| (PID) Process: | (3864) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (3864) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (3864) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (3864) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Main |
| Operation: | write | Name: | CompatibilityFlags |
Value: 0 | |||
| (PID) Process: | (3864) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
Executable files
5
Suspicious files
22
Text files
42
Unknown types
10
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3972 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\MFAQUS6V\4HPL13QO | binary | |
MD5:4842E206E4CFFF2954901467AD54169E | SHA256:2ACAB1228E8935D5DFDD1756B8A19698B6C8B786C90F87993CE9799A67A96E4E | |||
| 3864 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Internet Explorer\VersionManager\ver6B09.tmp | xml | |
MD5:CBD0581678FA40F0EDCBC7C59E0CAD10 | SHA256:159BD4343F344A08F6AF3B716B6FA679859C1BD1D7030D26FF5EF0255B86E1D9 | |||
| 3864 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\7423F88C7F265F0DEFC08EA88C3BDE45_AA1E8580D4EBC816148CE81268683776 | der | |
MD5:9B587B23C0FF0D6F6F3FD9D901E72C21 | SHA256:B73D4C15AF0B2E45478CAED83C27D345E3F61625657F892976D6CECAE15D5B06 | |||
| 3864 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\7423F88C7F265F0DEFC08EA88C3BDE45_AA1E8580D4EBC816148CE81268683776 | binary | |
MD5:AFC9AC647A3739BD2D7EEB023A1859C4 | SHA256:E9EC9A54B3937ED2FDEF6078CE5D820ACC2CF68E0CFABE2306C40A5E492352FE | |||
| 3864 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Internet Explorer\VersionManager\versionlist.xml | xml | |
MD5:CBD0581678FA40F0EDCBC7C59E0CAD10 | SHA256:159BD4343F344A08F6AF3B716B6FA679859C1BD1D7030D26FF5EF0255B86E1D9 | |||
| 3864 | iexplore.exe | C:\Users\admin\Downloads\4HPL13QO.f888hpp.partial:Zone.Identifier | text | |
MD5:FBCCF14D504B7B2DBCB5A5BDA75BD93B | SHA256:EACD09517CE90D34BA562171D15AC40D302F0E691B439F91BE1B6406E25F5913 | |||
| 3864 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Internet Explorer\Recovery\Active\{C1F6E857-DAA3-11EE-AE0A-12A9866C77DE}.dat | binary | |
MD5:72778BF5D6806004FAECB6B86714A570 | SHA256:E102B2505D0B8B904E7BB4E91AE2AD4F00CDC81896C424CAACA7B517426E4B09 | |||
| 3864 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\~DF32015862E0DF4730.TMP | binary | |
MD5:339D656F28E2A3665DC9ACE550019854 | SHA256:D2D19AF165956B3F8E8FD47A0A9101E366D9FBBB186540DEEEF0363BE617E70E | |||
| 3864 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\B6QGX7LP\urlblockindex[1].bin | binary | |
MD5:FA518E3DFAE8CA3A0E495460FD60C791 | SHA256:775853600060162C4B4E5F883F9FD5A278E61C471B3EE1826396B6D129499AA7 | |||
| 3864 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\57C8EDB95DF3F0AD4EE2DC2B8CFD4157 | binary | |
MD5:CEB1A3CC79469944C8C7AD3FEE072285 | SHA256:EDC88F101D8769B3A235901EE5A85056B21EA2018723880D5F26FB1FC17DB04C | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
10
TCP/UDP connections
20
DNS requests
12
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3972 | iexplore.exe | GET | 200 | 192.229.221.95:80 | http://crl.verisign.com/ | unknown | binary | 5 b | unknown |
3864 | iexplore.exe | GET | 304 | 87.248.204.0:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?70d85e3b0e586cab | unknown | — | — | unknown |
3864 | iexplore.exe | GET | 304 | 87.248.204.0:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?bdc5ae628aaf0bd4 | unknown | — | — | unknown |
3864 | iexplore.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAxq6XzO1ZmDhpCgCp6lMhQ%3D | unknown | binary | 471 b | unknown |
3864 | iexplore.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | binary | 471 b | unknown |
3864 | iexplore.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEA177el9ggmWelJjG4vdGL0%3D | unknown | binary | 471 b | unknown |
3864 | iexplore.exe | GET | 304 | 87.248.204.0:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?96c8eb5dfc595a04 | unknown | — | — | unknown |
3864 | iexplore.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | binary | 471 b | unknown |
1080 | svchost.exe | GET | 200 | 87.248.205.0:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/authrootstl.cab?3e412f7b4eff0943 | unknown | compressed | 67.5 Kb | unknown |
1080 | svchost.exe | GET | 304 | 87.248.205.0:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?0754c686571bd23f | unknown | compressed | 67.5 Kb | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
1080 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
3972 | iexplore.exe | 192.229.221.95:80 | crl.verisign.com | EDGECAST | US | whitelisted |
3864 | iexplore.exe | 152.199.19.161:443 | iecvlist.microsoft.com | EDGECAST | US | whitelisted |
3864 | iexplore.exe | 87.248.204.0:80 | ctldl.windowsupdate.com | LLNW | US | unknown |
3864 | iexplore.exe | 192.229.221.95:80 | crl.verisign.com | EDGECAST | US | whitelisted |
1080 | svchost.exe | 87.248.205.0:80 | ctldl.windowsupdate.com | LLNW | US | unknown |
3864 | iexplore.exe | 204.79.197.200:443 | ieonline.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
3864 | iexplore.exe | 23.32.186.57:443 | go.microsoft.com | AKAMAI-AS | BR | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
crl.verisign.com |
| whitelisted |
iecvlist.microsoft.com |
| whitelisted |
r20swj13mr.microsoft.com |
| whitelisted |
ctldl.windowsupdate.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
ieonline.microsoft.com |
| whitelisted |
go.microsoft.com |
| whitelisted |
www.msn.com |
| whitelisted |
dns.msftncsi.com |
| shared |
Threats
Process | Message |
|---|---|
csc.exe |
*** HR originated: -2147024774
*** Source File: d:\iso_whid\x86fre\base\isolation\com\copyout.cpp, line 1302
|
csc.exe |
*** HR propagated: -2147024774
*** Source File: d:\iso_whid\x86fre\base\isolation\com\enumidentityattribute.cpp, line 144
|
csc.exe |
*** HR originated: -2147024774
*** Source File: d:\iso_whid\x86fre\base\isolation\com\copyout.cpp, line 1302
|
csc.exe |
*** HR propagated: -2147024774
*** Source File: d:\iso_whid\x86fre\base\isolation\com\enumidentityattribute.cpp, line 144
|
csc.exe |
*** HR originated: -2147024774
*** Source File: d:\iso_whid\x86fre\base\isolation\com\copyout.cpp, line 1302
|
csc.exe |
*** HR propagated: -2147024774
*** Source File: d:\iso_whid\x86fre\base\isolation\com\enumidentityattribute.cpp, line 144
|
csc.exe |
*** HR originated: -2147024774
*** Source File: d:\iso_whid\x86fre\base\isolation\com\copyout.cpp, line 1302
|
csc.exe |
*** HR propagated: -2147024774
*** Source File: d:\iso_whid\x86fre\base\isolation\com\enumidentityattribute.cpp, line 144
|
csc.exe |
*** HR originated: -2147024774
*** Source File: d:\iso_whid\x86fre\base\isolation\com\copyout.cpp, line 1302
|
csc.exe |
*** HR propagated: -2147024774
*** Source File: d:\iso_whid\x86fre\base\isolation\com\enumidentityattribute.cpp, line 144
|