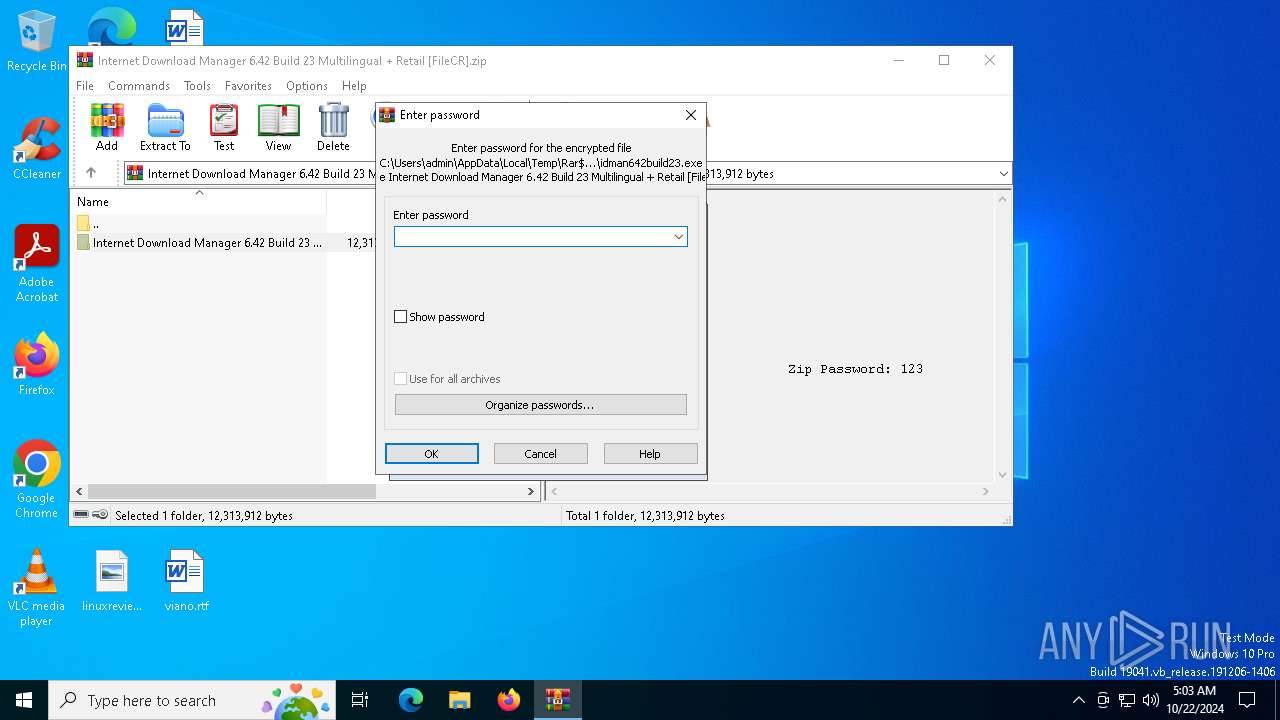
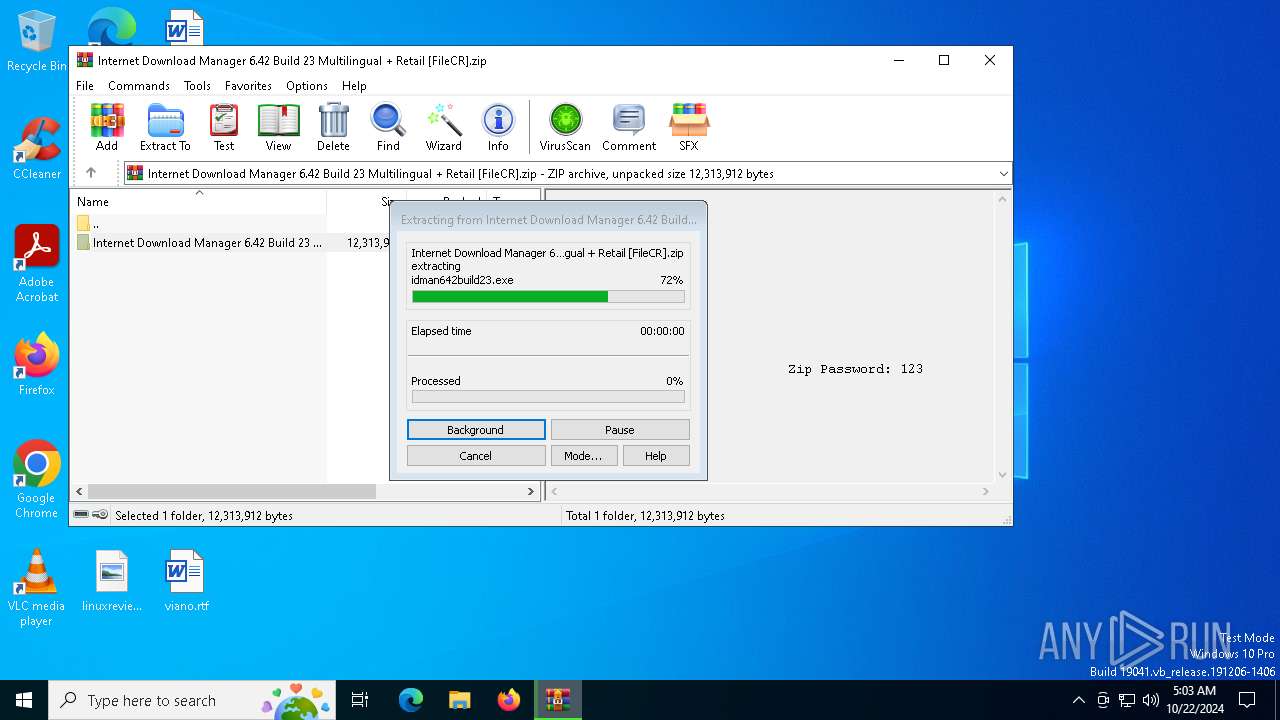
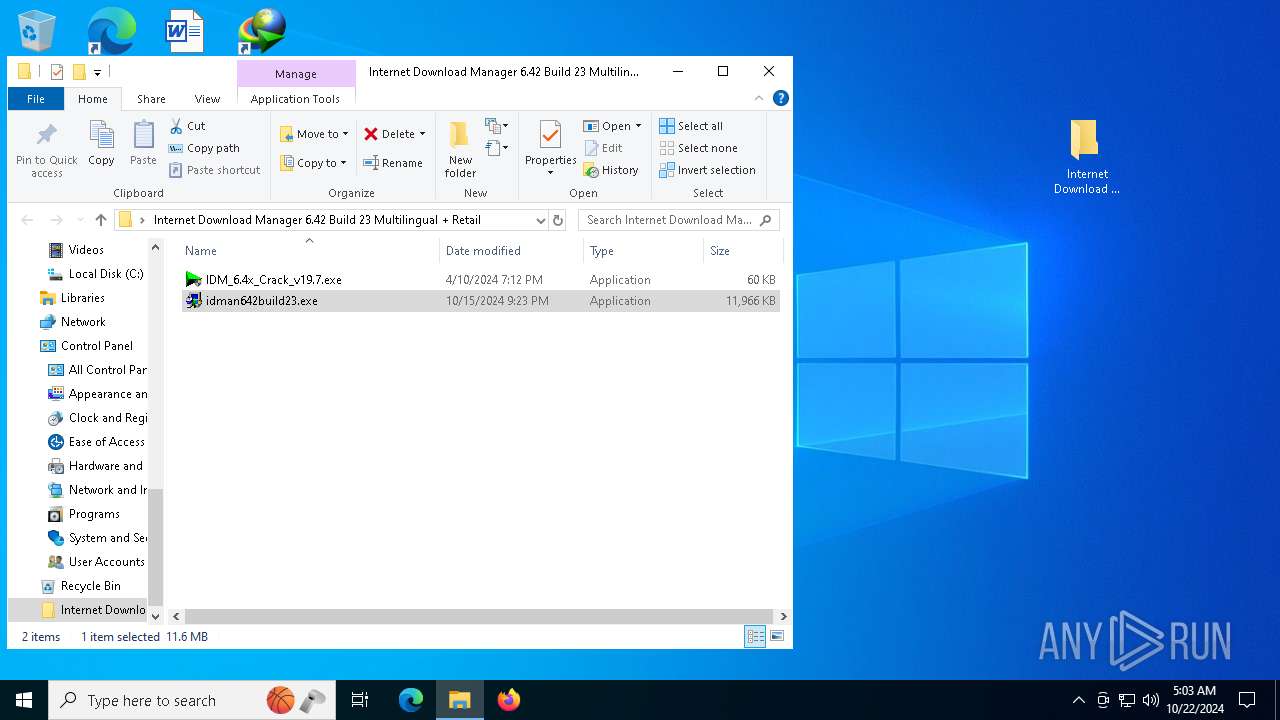
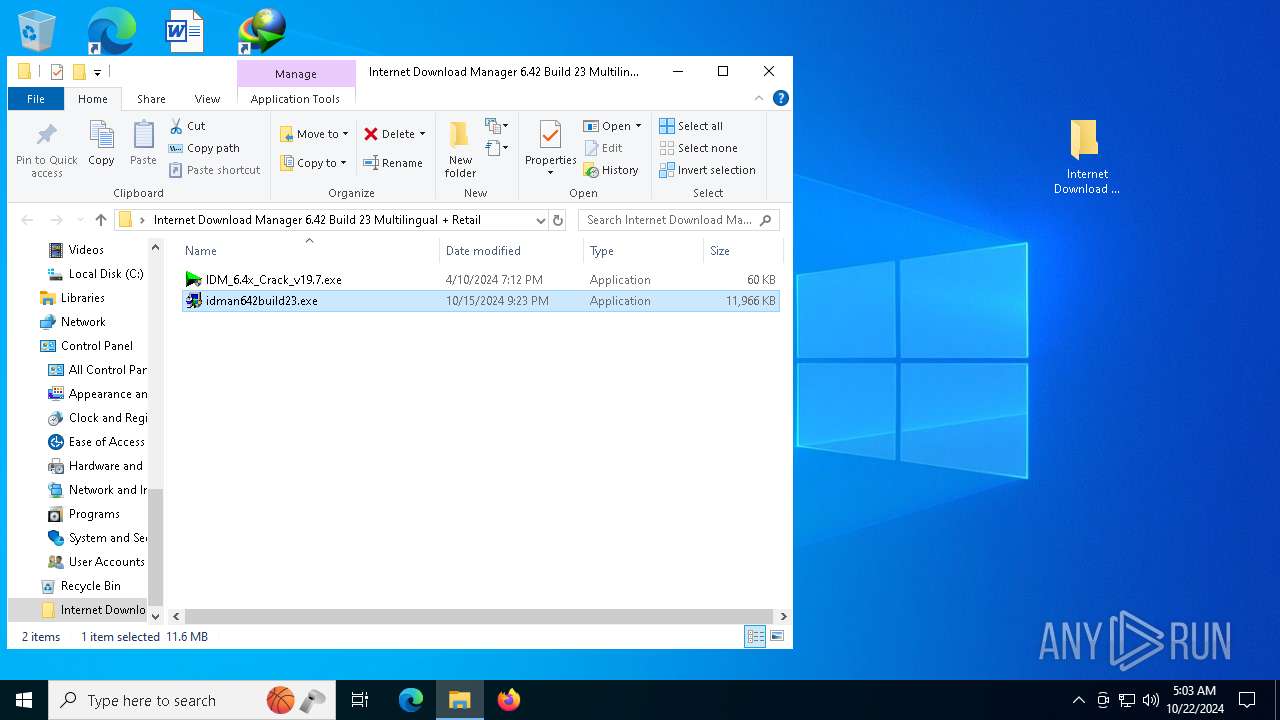
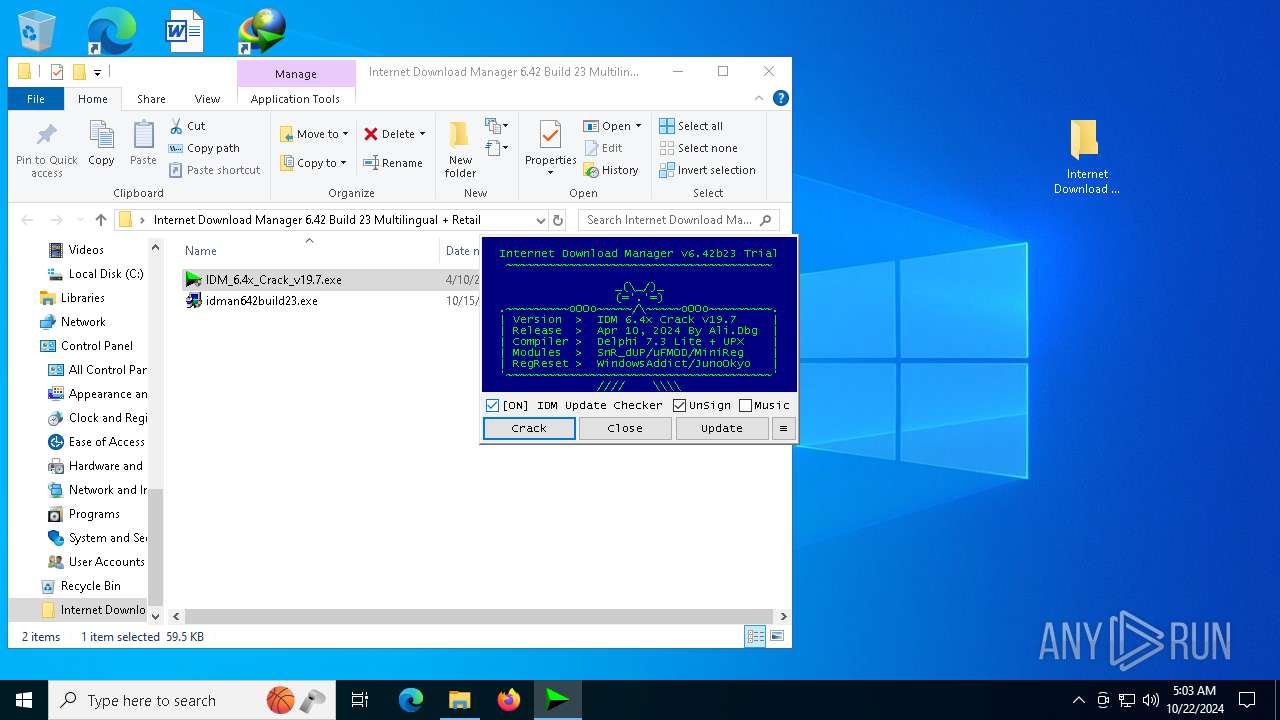
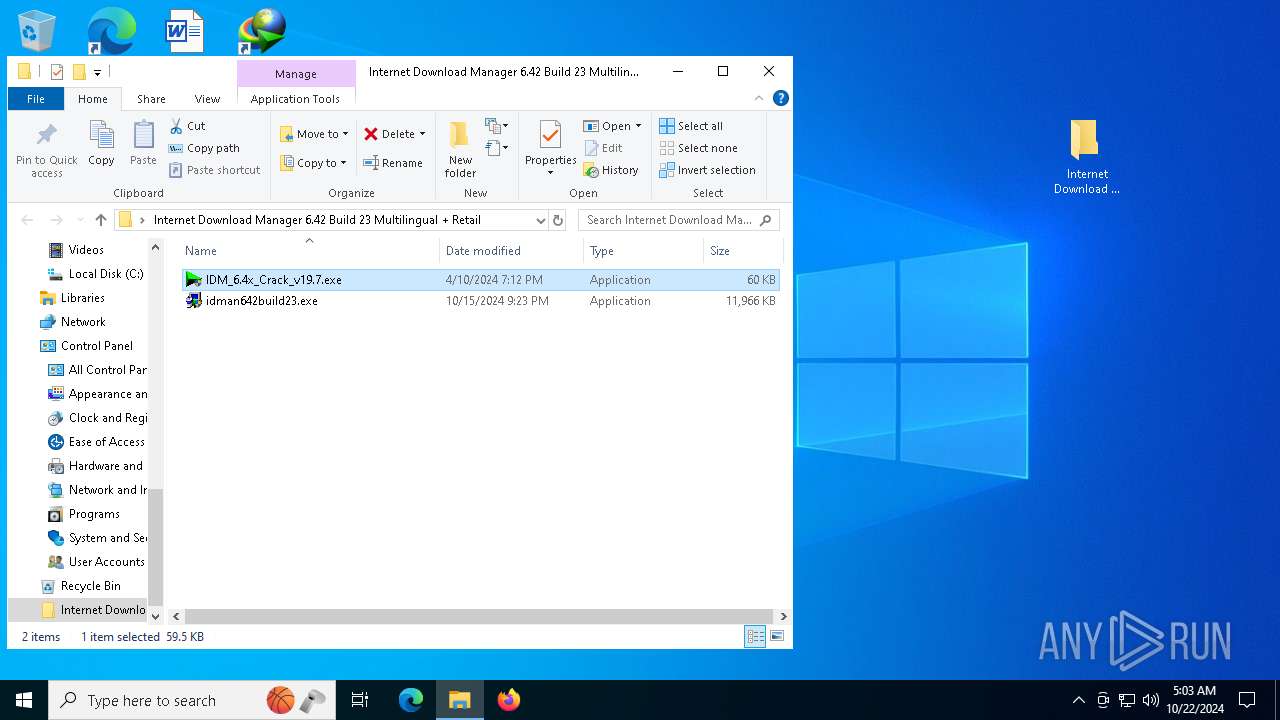
| File name: | Internet Download Manager 6.42 Build 23 Multilingual + Retail [FileCR].zip |
| Full analysis: | https://app.any.run/tasks/c982ac0f-74d2-4d16-a4af-d3c9039aa959 |
| Verdict: | Malicious activity |
| Analysis date: | October 22, 2024, 05:03:09 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v1.0 to extract, compression method=store |
| MD5: | C907A835DCDBA8CA1689E1200C1DA4E9 |
| SHA1: | E30A66822990672AC6C8417E295749C792911BFC |
| SHA256: | 828596A77F89CD72232D95C82ED3FBA344CD7D7148C8856863FDA9F29401B231 |
| SSDEEP: | 98304:cKahOGx1ogjImmDiafl4QuQQnU0pYzmm/HMeBnoPyi2R7Qx/O8aupZkGJgFyRgOY:bPAez/uQQfN0nIngR1zLqygV++KzDj |
MALICIOUS
Generic archive extractor
- WinRAR.exe (PID: 5284)
Registers / Runs the DLL via REGSVR32.EXE
- IDMan.exe (PID: 6888)
- IDM1.tmp (PID: 6772)
- Uninstall.exe (PID: 5264)
- IDMan.exe (PID: 8048)
Starts NET.EXE for service management
- Uninstall.exe (PID: 5264)
- net.exe (PID: 7832)
SUSPICIOUS
Starts application with an unusual extension
- idman642build23.exe (PID: 300)
- cmd.exe (PID: 7868)
Executable content was dropped or overwritten
- IDMan.exe (PID: 6888)
- rundll32.exe (PID: 1204)
- drvinst.exe (PID: 7172)
- IDM_6.4x_Crack_v19.7.exe (PID: 7768)
Drops a system driver (possible attempt to evade defenses)
- rundll32.exe (PID: 1204)
- drvinst.exe (PID: 7172)
Uses RUNDLL32.EXE to load library
- Uninstall.exe (PID: 5264)
Executing commands from a ".bat" file
- IDM_6.4x_Crack_v19.7.exe (PID: 7768)
- cmd.exe (PID: 7868)
Starts CMD.EXE for commands execution
- IDM_6.4x_Crack_v19.7.exe (PID: 7768)
- cmd.exe (PID: 7868)
- cmd.exe (PID: 1712)
Application launched itself
- cmd.exe (PID: 7868)
- cmd.exe (PID: 1712)
Uses REG/REGEDIT.EXE to modify registry
- IDM_6.4x_Crack_v19.7.exe (PID: 7768)
- cmd.exe (PID: 7868)
- cmd.exe (PID: 7784)
Probably obfuscated PowerShell command line is found
- cmd.exe (PID: 7868)
Starts POWERSHELL.EXE for commands execution
- cmd.exe (PID: 7868)
- cmd.exe (PID: 8008)
- cmd.exe (PID: 2784)
Possibly malicious use of IEX has been detected
- cmd.exe (PID: 7868)
Hides command output
- cmd.exe (PID: 8008)
- cmd.exe (PID: 7784)
INFO
Manual execution by a user
- idman642build23.exe (PID: 300)
- firefox.exe (PID: 6544)
- IDM_6.4x_Crack_v19.7.exe (PID: 7768)
- IDM_6.4x_Crack_v19.7.exe (PID: 7544)
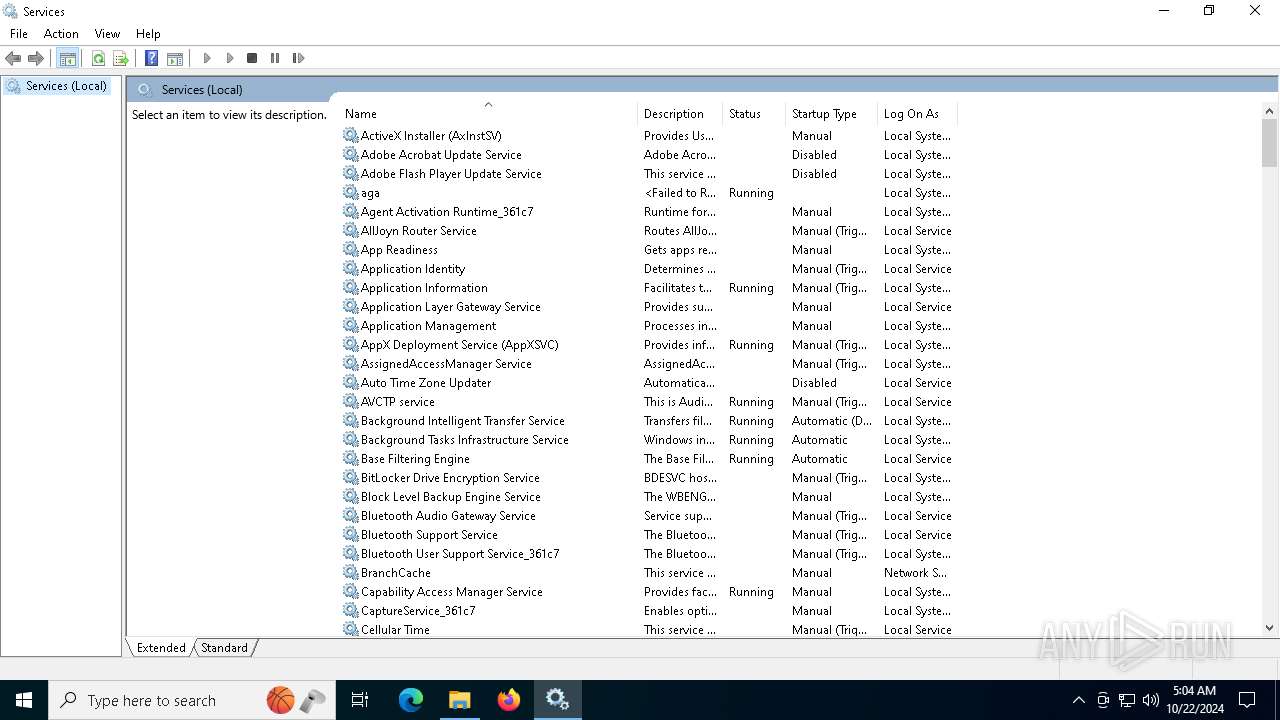
- mmc.exe (PID: 7780)
- mmc.exe (PID: 7880)
- idman642build23.exe (PID: 2928)
Application launched itself
- firefox.exe (PID: 6544)
- firefox.exe (PID: 5276)
Checks operating system version
- cmd.exe (PID: 7868)
Changes the display of characters in the console
- cmd.exe (PID: 7868)
The process uses the downloaded file
- WinRAR.exe (PID: 5284)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 5284)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 10 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | None |
| ZipModifyDate: | 2024:10:16 09:25:56 |
| ZipCRC: | 0x00000000 |
| ZipCompressedSize: | - |
| ZipUncompressedSize: | - |
| ZipFileName: | Internet Download Manager 6.42 Build 23 Multilingual + Retail/ |
Total processes
240
Monitored processes
103
Malicious processes
6
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 300 | "C:\Users\admin\Desktop\Internet Download Manager 6.42 Build 23 Multilingual + Retail\idman642build23.exe" | C:\Users\admin\Desktop\Internet Download Manager 6.42 Build 23 Multilingual + Retail\idman642build23.exe | explorer.exe | ||||||||||||
User: admin Company: Tonec Inc. Integrity Level: HIGH Description: Internet Download Manager installer Exit code: 0 Version: 6, 42, 23, 1 Modules
| |||||||||||||||
| 1204 | "C:\WINDOWS\Sysnative\RUNDLL32.EXE" SETUPAPI.DLL,InstallHinfSection DefaultInstall 128 C:\Program Files (x86)\Internet Download Manager\idmwfp.inf | C:\Windows\System32\rundll32.exe | Uninstall.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows host process (Rundll32) Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1204 | C:\WINDOWS\system32\cmd.exe /c ver | C:\Windows\SysWOW64\cmd.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.3636 (WinBuild.160101.0800) | |||||||||||||||
| 1712 | "C:\Windows\System32\regsvr32.exe" /s "C:\Program Files (x86)\Internet Download Manager\IDMGetAll64.dll" | C:\Windows\SysWOW64\regsvr32.exe | — | IDM1.tmp | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft(C) Register Server Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1712 | C:\WINDOWS\system32\cmd.exe /c echo prompt $E | cmd | C:\Windows\SysWOW64\cmd.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.3636 (WinBuild.160101.0800) | |||||||||||||||
| 1712 | reg query "HKCU\Software\DownloadManager" "/v" "LstCheck" | C:\Windows\System32\reg.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Registry Console Tool Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) | |||||||||||||||
| 1804 | C:\WINDOWS\system32\SppExtComObj.exe -Embedding | C:\Windows\System32\SppExtComObj.Exe | — | svchost.exe | |||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: KMS Connection Broker Version: 10.0.19041.3996 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1952 | /s "C:\Program Files (x86)\Internet Download Manager\IDMIECC64.dll" | C:\Windows\System32\regsvr32.exe | — | regsvr32.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft(C) Register Server Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2076 | "C:\WINDOWS\System32\SLUI.exe" RuleId=3482d82e-ca2c-4e1f-8864-da0267b484b2;Action=AutoActivate;AppId=55c92734-d682-4d71-983e-d6ec3f16059f;SkuId=4de7cb65-cdf1-4de9-8ae8-e3cce27b9f2c;NotificationInterval=1440;Trigger=TimerEvent | C:\Windows\System32\slui.exe | — | SppExtComObj.Exe | |||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows Activation Client Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2312 | "C:\Program Files (x86)\Internet Download Manager\idmBroker.exe" -RegServer | C:\Program Files (x86)\Internet Download Manager\idmBroker.exe | — | IDM1.tmp | |||||||||||
User: admin Company: Internet Download Manager, Tonec Inc. Integrity Level: HIGH Description: Broker for reading of IDM settings Exit code: 0 Version: 6, 35, 9, 1 Modules
| |||||||||||||||
Total events
26 858
Read events
26 012
Write events
680
Delete events
166
Modification events
| (PID) Process: | (5284) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\GoogleChromeEnterpriseBundle64.zip | |||
| (PID) Process: | (5284) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\Internet Download Manager 6.42 Build 23 Multilingual + Retail [FileCR].zip | |||
| (PID) Process: | (5284) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (5284) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (5284) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (5284) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (5284) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface |
| Operation: | write | Name: | ShowPassword |
Value: 0 | |||
| (PID) Process: | (5284) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface\MainWin |
| Operation: | write | Name: | Placement |
Value: 2C0000000000000001000000FFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFF3D0000002D000000FD03000016020000 | |||
| (PID) Process: | (5284) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\ArcColumnWidths |
| Operation: | write | Name: | name |
Value: 256 | |||
| (PID) Process: | (5284) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\ArcColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
Executable files
18
Suspicious files
94
Text files
29
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 5284 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRb5284.21054\Internet Download Manager 6.42 Build 23 Multilingual + Retail\IDM_6.4x_Crack_v19.7.exe | executable | |
MD5:27016937B5781C4F84B6B3432170F4D0 | SHA256:FC1A02B509B8F351AC45BD45EFD4E7296B365545A48FFD6A14E8E07BC7189155 | |||
| 5284 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRb5284.21054\Internet Download Manager 6.42 Build 23 Multilingual + Retail\idman642build23.exe | executable | |
MD5:EBADBF7B41AD0E9D0775914553B3A89E | SHA256:599577082052C683DA78FE30D24C413A614F8A8172A4560015FD85044403456B | |||
| 6772 | IDM1.tmp | C:\Users\admin\AppData\Local\Temp\IDM_Setup_Temp\IDMSetup2.log | binary | |
MD5:5A032ACD38AB177AE8FBD17D52335C22 | SHA256:10F2E057D9A43BC3E7C1D26CA19BC84E43BEB32D79A02EE6744468A2A0FDD808 | |||
| 6772 | IDM1.tmp | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Internet Download Manager\Internet Download Manager.lnk | lnk | |
MD5:8D746B474950900A8E256ECF2B67E05C | SHA256:F783C936DCBB291DB622BC13D373F12B2668DE9D685291A7B9F0763739178A22 | |||
| 6772 | IDM1.tmp | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Internet Download Manager\Uninstall IDM.lnk | binary | |
MD5:55BAF0B1501CAC6DA6C297A8E3FD6429 | SHA256:E8F7C9A89F211770735A6400FB6ACA5909CB2C08DDA78482AF6CC8230D21E887 | |||
| 6772 | IDM1.tmp | C:\ProgramData\Microsoft\Windows\Start Menu\Programs\Internet Download Manager\IDM Help.lnk | binary | |
MD5:7F5223121ACFF06BD0CD33469F823C2E | SHA256:2E1BD8CC2E6CA88E667F58D75F8C0ED9C6D8F1109EEE26F9777A5669FDF6EF1D | |||
| 6772 | IDM1.tmp | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Internet Download Manager\license.lnk | binary | |
MD5:526A48A694B5E394A11311B525252104 | SHA256:277990293F467BA689DF3968CF2337A8FAE66FD6772D9BCECE2DC7CECB8CF722 | |||
| 6772 | IDM1.tmp | C:\ProgramData\Microsoft\Windows\Start Menu\Programs\Internet Download Manager\Uninstall IDM.lnk | binary | |
MD5:EA87F4FBC43EFDB15184CCCD482D13BC | SHA256:8D4793D37B746F19971AB44501028F8361BE61A459760009541E1A1F697C73EE | |||
| 6772 | IDM1.tmp | C:\ProgramData\Microsoft\Windows\Start Menu\Programs\Internet Download Manager\license.lnk | binary | |
MD5:40C6E064C3A029DBF12098C557CF3BB4 | SHA256:86E9E2FAEB5B75159296169152048D7B85DEE58B0BE7614ED37D15107351F2B2 | |||
| 6772 | IDM1.tmp | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Internet Download Manager\IDM Help.lnk | binary | |
MD5:ADDE64AC18A08AEF73C178776F2AADBA | SHA256:5BEF0225F574EE352E0222070715809B7BADED5F3AE82DC4579228B5FBA00E1D | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
20
TCP/UDP connections
79
DNS requests
64
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
6376 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
1156 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
5276 | firefox.exe | GET | 200 | 34.107.221.82:80 | http://detectportal.firefox.com/canonical.html | unknown | — | — | whitelisted |
5276 | firefox.exe | POST | 200 | 95.101.54.114:80 | http://r10.o.lencr.org/ | unknown | — | — | whitelisted |
5276 | firefox.exe | GET | 200 | 34.107.221.82:80 | http://detectportal.firefox.com/success.txt?ipv4 | unknown | — | — | whitelisted |
5276 | firefox.exe | POST | 200 | 142.250.186.163:80 | http://o.pki.goog/s/wr3/XjA | unknown | — | — | whitelisted |
5276 | firefox.exe | POST | 200 | 95.101.54.114:80 | http://r10.o.lencr.org/ | unknown | — | — | whitelisted |
5276 | firefox.exe | POST | 200 | 95.101.54.114:80 | http://r10.o.lencr.org/ | unknown | — | — | whitelisted |
— | — | GET | 200 | 2.16.164.51:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
4360 | SearchApp.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
6944 | svchost.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
5488 | MoUsoCoreWorker.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 2.16.164.51:80 | crl.microsoft.com | Akamai International B.V. | NL | whitelisted |
— | — | 95.101.149.131:80 | www.microsoft.com | Akamai International B.V. | NL | whitelisted |
4360 | SearchApp.exe | 2.23.209.189:443 | www.bing.com | Akamai International B.V. | GB | whitelisted |
4360 | SearchApp.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
6376 | svchost.exe | 40.126.32.138:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
www.bing.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
google.com |
| whitelisted |
login.live.com |
| whitelisted |
th.bing.com |
| whitelisted |
go.microsoft.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |