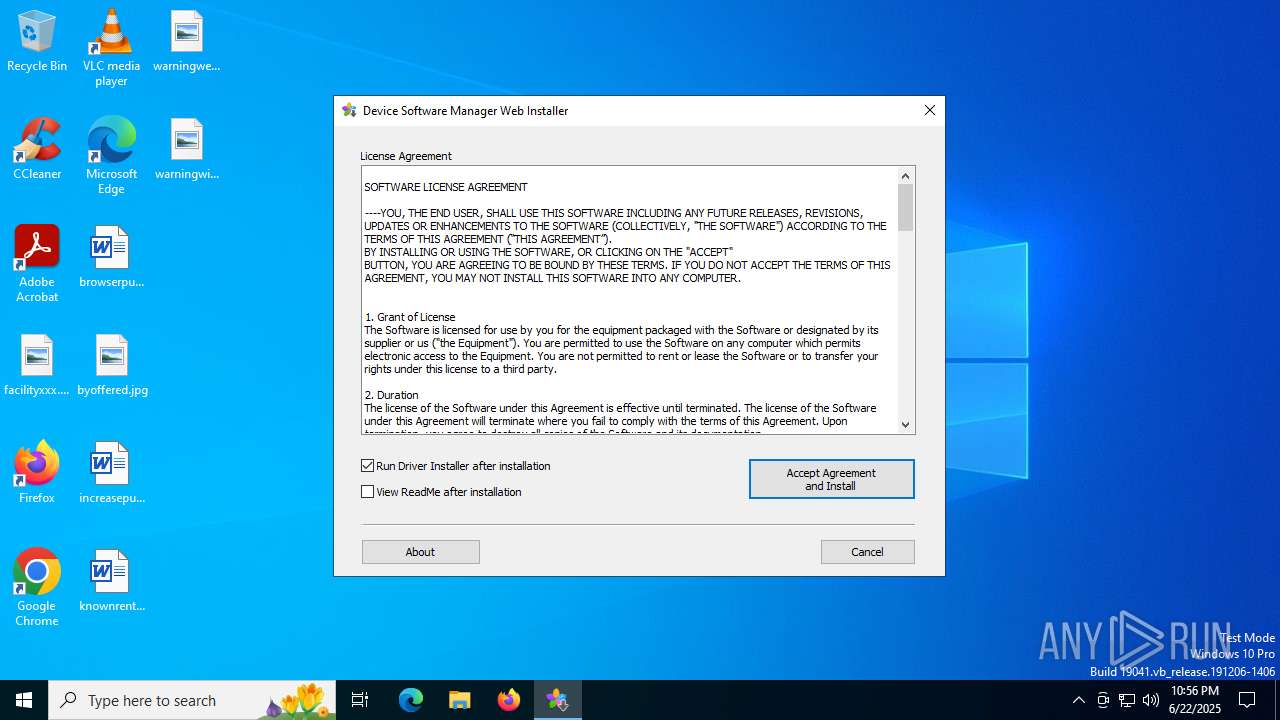
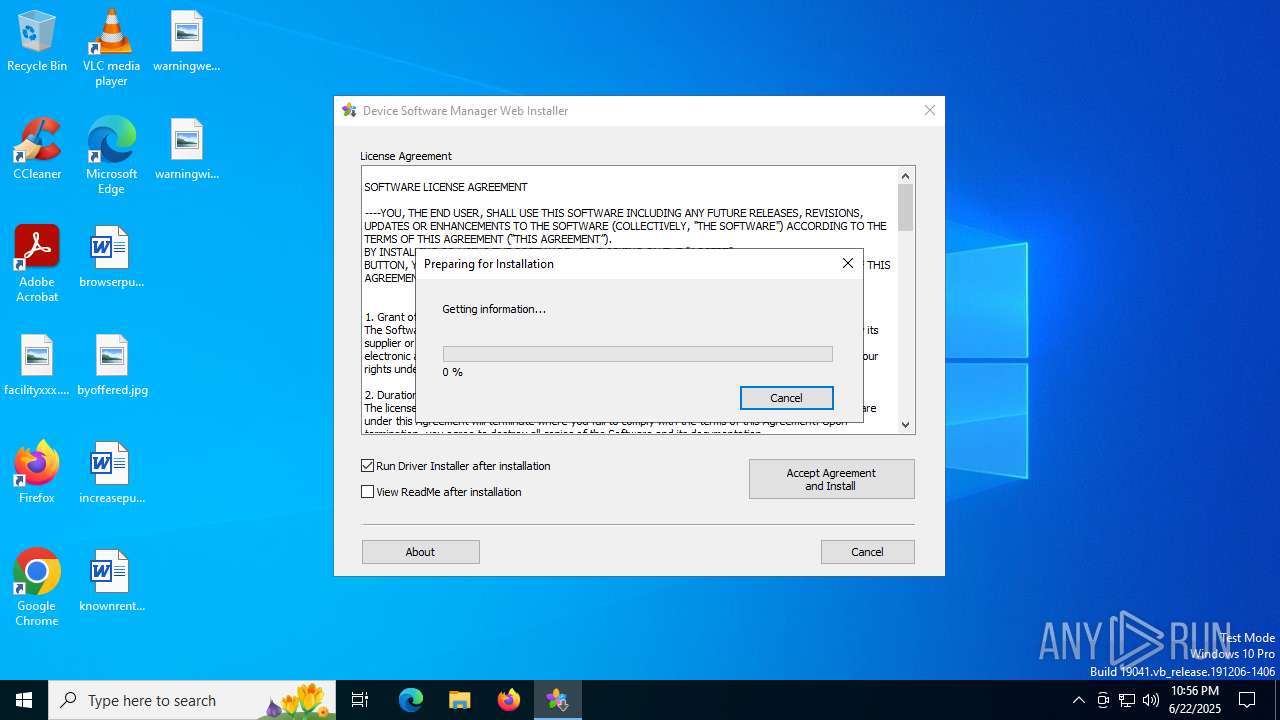
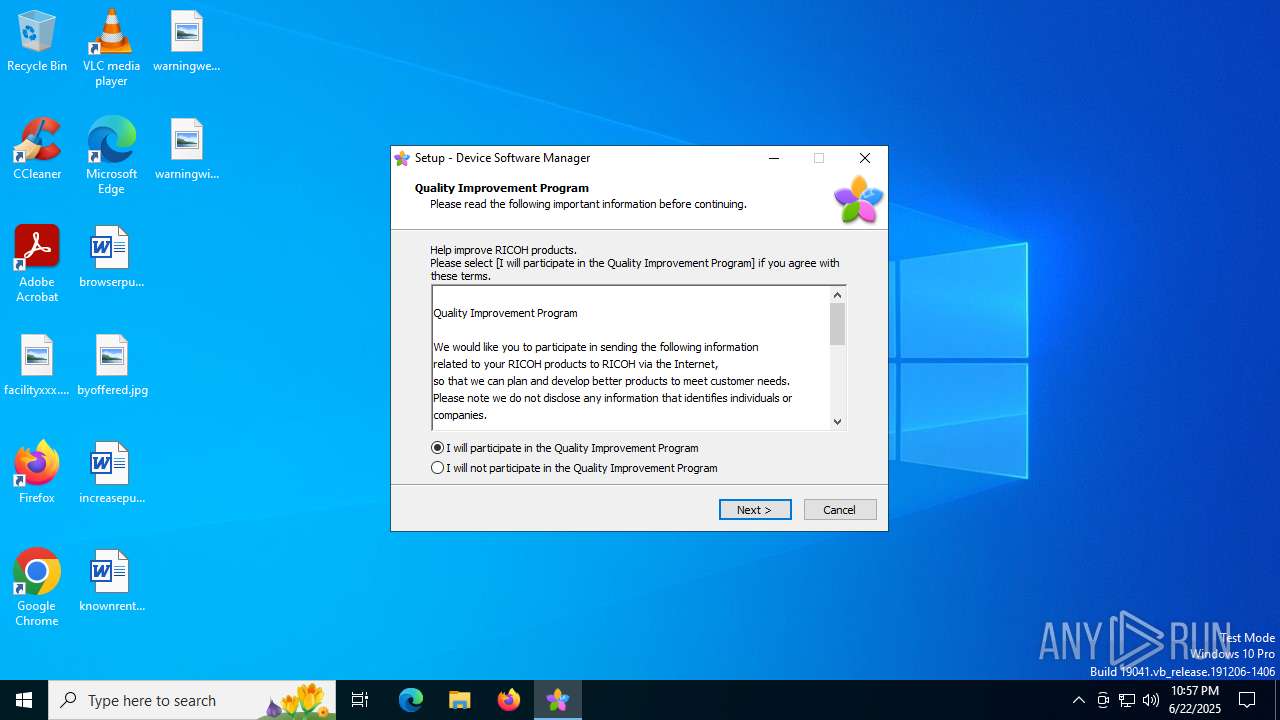
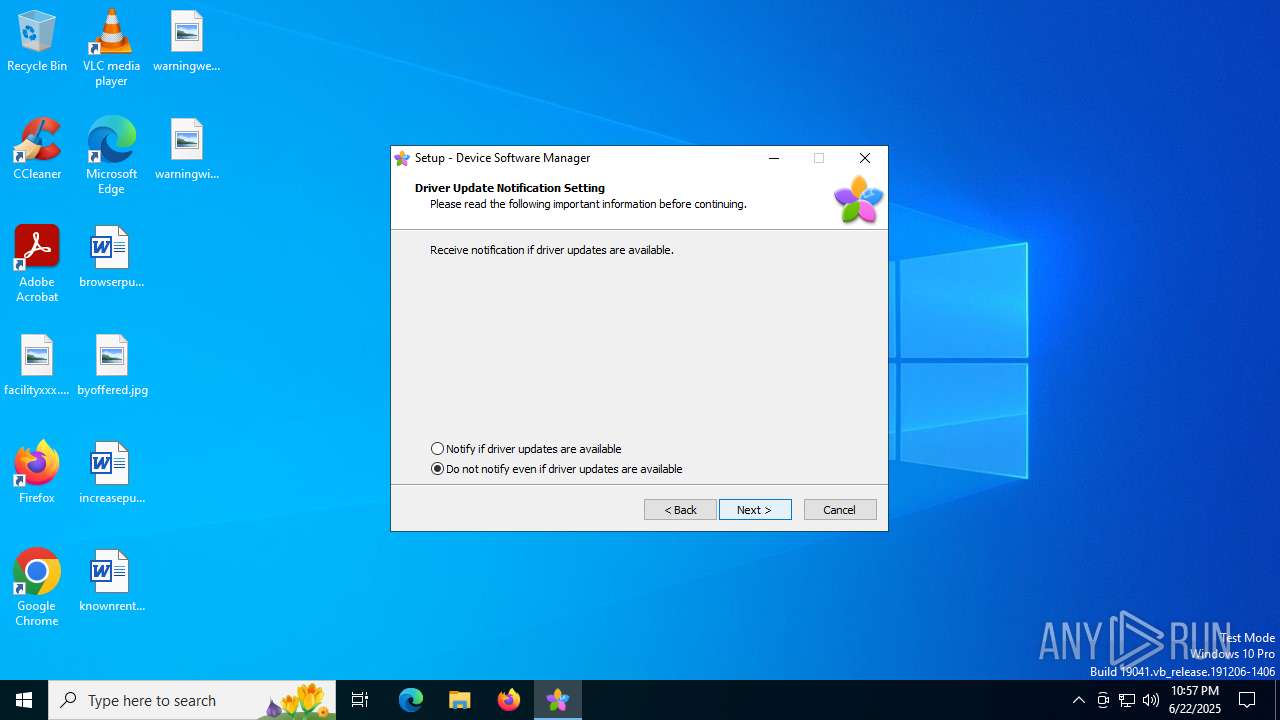
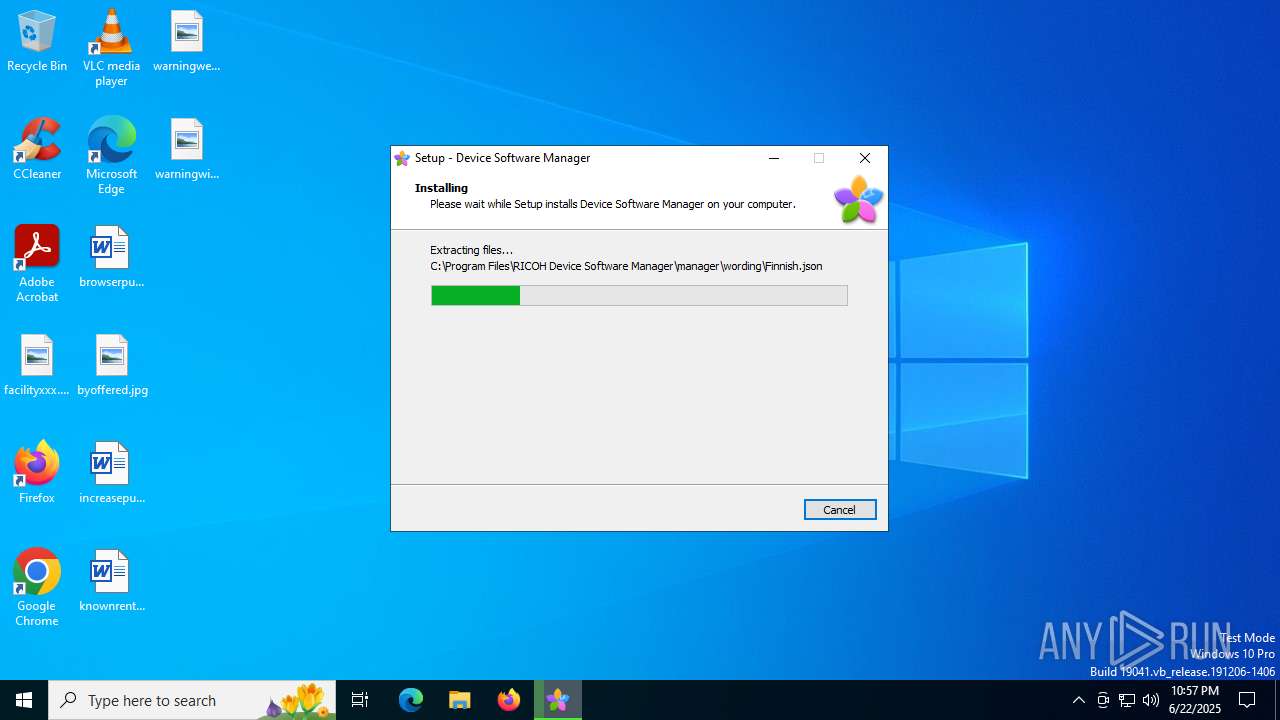
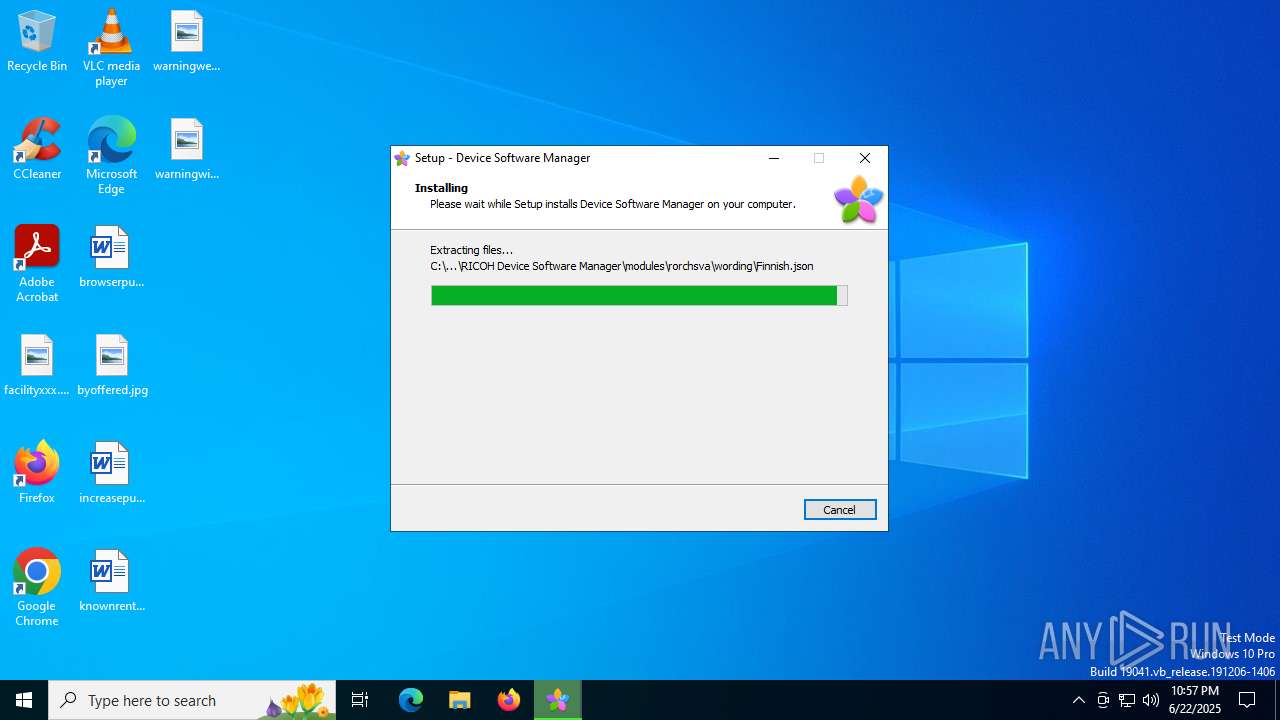
| File name: | driver_web_installer.exe |
| Full analysis: | https://app.any.run/tasks/b989314f-2f1c-4058-b903-ddecdda48444 |
| Verdict: | Malicious activity |
| Analysis date: | June 22, 2025, 22:56:42 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows, 6 sections |
| MD5: | F025C4DEF915CB2E5449CB5DFB2ACEF5 |
| SHA1: | CFC65DB69DB3B32254C2C7F545C8AE5FD9A627ED |
| SHA256: | 8282DF7DC7ECD6AE7689B89E6BA091F0F266622B1907D95F61D6B5B3DEA0F050 |
| SSDEEP: | 98304:zyjdEa2NQMIWK9evl0KYoyXvy9KPsvXcrojGDeHL427xhUVdYM9qem97kdsoBckf:w9ld0Kmm |
MALICIOUS
Executing a file with an untrusted certificate
- ISBEW64.exe (PID: 1100)
Starts NET.EXE for service management
- net.exe (PID: 7000)
- setup.tmp (PID: 4168)
- net.exe (PID: 2144)
SUSPICIOUS
Starts itself from another location
- driver_web_installer.exe (PID: 2044)
Executable content was dropped or overwritten
- driver_web_installer.exe (PID: 2044)
- _is5DA0.exe (PID: 1872)
- setup.tmp (PID: 4168)
- setup.exe (PID: 1560)
- driver_web_installer.exe (PID: 5168)
Reads security settings of Internet Explorer
- _is5DA0.exe (PID: 1872)
There is functionality for taking screenshot (YARA)
- _is5DA0.exe (PID: 1872)
Application launched itself
- _is5DA0.exe (PID: 1872)
Reads the Windows owner or organization settings
- setup.tmp (PID: 4168)
Process drops legitimate windows executable
- setup.tmp (PID: 4168)
Executes as Windows Service
- rorchcdk.exe (PID: 2632)
- rorchcdk.exe (PID: 6104)
INFO
Reads the computer name
- driver_web_installer.exe (PID: 2044)
- _is5DA0.exe (PID: 1872)
- driver_web_installer.exe (PID: 5168)
- setup.tmp (PID: 4168)
- ISBEW64.exe (PID: 1100)
- _is5DA0.exe (PID: 2804)
- rorchcdn.exe (PID: 4960)
- rorchcdk.exe (PID: 2632)
- rorchsvc.exe (PID: 2648)
- rorchpbo.exe (PID: 1352)
- rorchpdr.exe (PID: 6668)
- rorchsva.exe (PID: 3716)
- rorchppi.exe (PID: 6828)
- rorchsvc.exe (PID: 6512)
- rorchcdk.exe (PID: 6104)
- rorchppi.exe (PID: 6188)
- rorchcdn.exe (PID: 4576)
- rorchsvc.exe (PID: 3768)
- rorchsva.exe (PID: 2580)
Checks supported languages
- driver_web_installer.exe (PID: 2044)
- _is5DA0.exe (PID: 1872)
- driver_web_installer.exe (PID: 5168)
- _is5DA0.exe (PID: 2804)
- setup.exe (PID: 1560)
- setup.tmp (PID: 4168)
- ISBEW64.exe (PID: 1100)
- rorchcdn.exe (PID: 4960)
- rorchcdk.exe (PID: 2632)
- rorchsvc.exe (PID: 2648)
- rorchpdr.exe (PID: 6668)
- rorchpbo.exe (PID: 1352)
- rorchppi.exe (PID: 6188)
- rorchsva.exe (PID: 3716)
- rorchppi.exe (PID: 6828)
- rorchsvc.exe (PID: 6512)
- rorchcdk.exe (PID: 6104)
- rorchsva.exe (PID: 2580)
- rorchcdn.exe (PID: 4576)
- rorchsvc.exe (PID: 3768)
Create files in a temporary directory
- driver_web_installer.exe (PID: 2044)
- _is5DA0.exe (PID: 1872)
- setup.exe (PID: 1560)
- setup.tmp (PID: 4168)
The sample compiled with english language support
- driver_web_installer.exe (PID: 2044)
- _is5DA0.exe (PID: 1872)
- setup.tmp (PID: 4168)
Process checks computer location settings
- _is5DA0.exe (PID: 1872)
Creates files in the program directory
- driver_web_installer.exe (PID: 5168)
- rorchcdk.exe (PID: 2632)
- rorchcdn.exe (PID: 4960)
- rorchsvc.exe (PID: 2648)
- rorchpdr.exe (PID: 6668)
- setup.tmp (PID: 4168)
- rorchpbo.exe (PID: 1352)
- rorchppi.exe (PID: 6188)
- rorchsva.exe (PID: 3716)
- rorchsvc.exe (PID: 6512)
- rorchppi.exe (PID: 6828)
- rorchsva.exe (PID: 2580)
- rorchcdn.exe (PID: 4576)
- rorchsvc.exe (PID: 3768)
- rorchcdk.exe (PID: 6104)
Checks proxy server information
- driver_web_installer.exe (PID: 5168)
- rorchcdn.exe (PID: 4960)
- rorchcdn.exe (PID: 4576)
- rorchsva.exe (PID: 2580)
Detects InnoSetup installer (YARA)
- setup.exe (PID: 1560)
- setup.tmp (PID: 4168)
Compiled with Borland Delphi (YARA)
- setup.tmp (PID: 4168)
- setup.exe (PID: 1560)
Creates a software uninstall entry
- setup.tmp (PID: 4168)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win64 Executable (generic) (17.3) |
|---|---|---|
| .dll | | | Win32 Dynamic Link Library (generic) (4.1) |
| .exe | | | Win32 Executable (generic) (2.8) |
| .exe | | | Generic Win/DOS Executable (1.2) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2017:07:27 12:52:21+00:00 |
| ImageFileCharacteristics: | Executable, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 11 |
| CodeSize: | 868352 |
| InitializedDataSize: | 619008 |
| UninitializedDataSize: | - |
| EntryPoint: | 0xa098e |
| OSVersion: | 5.1 |
| ImageVersion: | - |
| SubsystemVersion: | 5.1 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 2.32.0.0 |
| ProductVersionNumber: | 2.32.0.0 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Dynamic link library |
| FileSubtype: | - |
| LanguageCode: | English (U.S.) |
| CharacterSet: | Unicode |
| CompanyName: | Flexera Software LLC |
| FileDescription: | Setup Suite Launcher Unicode |
| FileVersion: | 2.32.0.0 |
| InternalName: | SetupSuite |
| LegalCopyright: | Copyright (c) 2015 Flexera Software LLC. All Rights Reserved. |
| OriginalFileName: | InstallShield SetupSuite.exe |
| ProductName: | Device Software Manager Setup Tool 2.32.0.0 |
| ProductVersion: | 2.32.0.0 |
| InternalBuildNumber: | 176888 |
| ISInternalVersion: | 22.0.401 |
| ISInternalDescription: | Setup Suite Launcher Unicode |
Total processes
166
Monitored processes
29
Malicious processes
3
Suspicious processes
3
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1100 | C:\Users\admin\AppData\Local\Temp\{40FE81AE-C9D6-4872-9692-3743D74235B9}\ISBEW64.exe {EFB7539B-24F3-46B6-AF6E-3B021B51EFEF}:{00D53DFA-6EFE-4F46-AA82-02E04FFCF4EA} | C:\Users\admin\AppData\Local\Temp\{40FE81AE-C9D6-4872-9692-3743D74235B9}\ISBEW64.exe | — | _is5DA0.exe | |||||||||||
User: admin Company: Flexera Software LLC Integrity Level: HIGH Description: InstallShield (R) 64-bit Setup Engine Exit code: 0 Version: 22.0.401 Modules
| |||||||||||||||
| 1352 | "C:\Program Files\RICOH Device Software Manager\manager\..\modules\rorchpbo\rorchpbo.exe" -l install | C:\Program Files\RICOH Device Software Manager\modules\rorchpbo\rorchpbo.exe | — | rorchcdk.exe | |||||||||||
User: SYSTEM Company: Ricoh Company, Ltd. Integrity Level: SYSTEM Description: Device Software Manager Plugin Assistant Exit code: 0 Version: 2.32.0.0 Modules
| |||||||||||||||
| 1560 | C:\ProgramData\RICOH_OCH\_temp\rorchtri\temp\setup.exe /LicenseSkip /RunDriverInstaller /ReduceInstallStep | C:\ProgramData\RICOH_OCH\_temp\rorchtri\temp\setup.exe | driver_web_installer.exe | ||||||||||||
User: admin Company: Ricoh Company, Ltd. Integrity Level: HIGH Description: Device Software Manager Setup Exit code: 0 Version: 2.32.0.0 Modules
| |||||||||||||||
| 1636 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | net.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1872 | "C:\Users\admin\AppData\Local\Temp\{A06EDB30-9521-45AC-871D-D881123D605D}\_is5DA0.exe" -IS_temp ORIGINALSETUPEXEDIR="C:\Users\admin\AppData\Local\Temp" ORIGINALSETUPEXENAME="driver_web_installer.exe" | C:\Users\admin\AppData\Local\Temp\{A06EDB30-9521-45AC-871D-D881123D605D}\_is5DA0.exe | driver_web_installer.exe | ||||||||||||
User: admin Company: Flexera Software LLC Integrity Level: HIGH Description: Setup Suite Launcher Unicode Exit code: 1603 Version: 2.32.0.0 Modules
| |||||||||||||||
| 2044 | "C:\Users\admin\AppData\Local\Temp\driver_web_installer.exe" | C:\Users\admin\AppData\Local\Temp\driver_web_installer.exe | explorer.exe | ||||||||||||
User: admin Company: Flexera Software LLC Integrity Level: HIGH Description: Setup Suite Launcher Unicode Exit code: 1603 Version: 2.32.0.0 Modules
| |||||||||||||||
| 2144 | "net.exe" start "RicohDeviceSoftwareManager" | C:\Windows\System32\net.exe | — | setup.tmp | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Net Command Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2580 | "C:\Program Files\RICOH Device Software Manager\modules\rorchsva\rorchsva.exe" -f forcestart | C:\Program Files\RICOH Device Software Manager\modules\rorchsva\rorchsva.exe | — | setup.tmp | |||||||||||
User: admin Company: Ricoh Company, Ltd. Integrity Level: HIGH Description: Driver Installer Version: 2.32.0.0 Modules
| |||||||||||||||
| 2632 | "C:\Program Files\RICOH Device Software Manager\manager\..\service\rorchcdk.exe" | C:\Program Files\RICOH Device Software Manager\service\rorchcdk.exe | — | services.exe | |||||||||||
User: SYSTEM Company: Ricoh Company, Ltd. Integrity Level: SYSTEM Description: Device Software Manager Service Exit code: 0 Version: 2.32.0.0 Modules
| |||||||||||||||
| 2648 | "C:\Program Files\RICOH Device Software Manager\manager\..\modules\rorchsvc\rorchsvc.exe" -l install | C:\Program Files\RICOH Device Software Manager\modules\rorchsvc\rorchsvc.exe | — | rorchcdk.exe | |||||||||||
User: SYSTEM Company: Ricoh Company, Ltd. Integrity Level: SYSTEM Description: Device Software Downloader Exit code: 0 Version: 2.32.0.0 Modules
| |||||||||||||||
Total events
3 148
Read events
3 078
Write events
68
Delete events
2
Modification events
| (PID) Process: | (1872) _is5DA0.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\InstallShield\SuiteInstallers\{57CC066F-A168-42C6-B6E9-49210982F292} |
| Operation: | write | Name: | InfoPath |
Value: C:\Users\admin\AppData\Local\Temp\{40FE81AE-C9D6-4872-9692-3743D74235B9}\_is5DFE | |||
| (PID) Process: | (1872) _is5DA0.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\InstallShield\SuiteInstallers\{57CC066F-A168-42C6-B6E9-49210982F292} |
| Operation: | delete key | Name: | (default) |
Value: | |||
| (PID) Process: | (1872) _is5DA0.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\InstallShield\SuiteInstallers |
| Operation: | delete key | Name: | (default) |
Value: | |||
| (PID) Process: | (2632) rorchcdk.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\RicohDeviceSoftwareManager\Parameters\plugin\rorchcdn |
| Operation: | write | Name: | path |
Value: "C:\Program Files\RICOH Device Software Manager\manager\rorchcdn.exe" | |||
| (PID) Process: | (2632) rorchcdk.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\RicohDeviceSoftwareManager\Parameters\plugin\rorchcdn |
| Operation: | write | Name: | options |
Value: | |||
| (PID) Process: | (2632) rorchcdk.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\RicohDeviceSoftwareManager\Parameters\plugin\rorchcdn |
| Operation: | write | Name: | version |
Value: 2.32.0.0 | |||
| (PID) Process: | (4960) rorchcdn.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\RICOH\RicohDeviceSoftwareManagerModules\rorchcdn |
| Operation: | write | Name: | version |
Value: 2.32.0.0 | |||
| (PID) Process: | (4960) rorchcdn.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\RICOH\RicohDeviceSoftwareManagerModules\rorchcdn |
| Operation: | write | Name: | program_list |
Value: [{"attribute":"manager","module_list":[{"attribute":"manager","name":"rorchcdn","path":".\\"},{"name":"rorchsvc","path":"..\\modules\\rorchsvc\\"},{"name":"rorchpdr","path":"..\\modules\\rorchpdr\\"},{"name":"rorchpbo","path":"..\\modules\\rorchpbo\\"},{"name":"rorchppi","path":"..\\modules\\rorchppi\\"}],"name":"rorchcdn","version":"2.32.0.0"},{"module_list":[{"name":"rorchsva","path":"..\\modules\\rorchsva\\"}],"name":"rorchsva","version":"2.32.0.0"}] | |||
| (PID) Process: | (4960) rorchcdn.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\RICOH\RicohDeviceSoftwareManagerModules\rorchcdn\modules\rorchcdn |
| Operation: | write | Name: | update_date |
Value: {"wDay":22.000000,"wDayOfWeek":0.000000,"wHour":22.000000,"wMilliseconds":719.000000,"wMinute":57.000000,"wMonth":6.000000,"wSecond":20.000000,"wYear":2025.000000} | |||
| (PID) Process: | (2632) rorchcdk.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\RicohDeviceSoftwareManager\Parameters\plugin\rorchsvc |
| Operation: | write | Name: | path |
Value: "C:\Program Files\RICOH Device Software Manager\manager\..\modules\rorchsvc\rorchsvc.exe" | |||
Executable files
30
Suspicious files
251
Text files
49
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 1872 | _is5DA0.exe | C:\Users\admin\AppData\Local\Temp\{40FE81AE-C9D6-4872-9692-3743D74235B9}\Setup_UI.dll | executable | |
MD5:F6BE9DD6F4F8640A9EA4636B69BF94B6 | SHA256:19F61F7C23244FDB48EB2938419916755DC704CEFFCD611FD5EEB7E7F26E687A | |||
| 1872 | _is5DA0.exe | C:\Users\admin\AppData\Local\Temp\{40FE81AE-C9D6-4872-9692-3743D74235B9}\scale-150\Custom.png | image | |
MD5:41404BDC8ACC738078A96E03836A7017 | SHA256:2760DC6DA4DA352973B99D8209E54DC68C679D8C2800408F6D9481E03D9D3D9B | |||
| 1872 | _is5DA0.exe | C:\Users\admin\AppData\Local\Temp\{40FE81AE-C9D6-4872-9692-3743D74235B9}\scale-150\Application.png | image | |
MD5:46B2EB6C23572DA87ADA5A342F854641 | SHA256:016604E80FFC9921EE9CA036B6DDE317094C9D1CD8BF4928087317C708EB7C84 | |||
| 1872 | _is5DA0.exe | C:\Users\admin\AppData\Local\Temp\{40FE81AE-C9D6-4872-9692-3743D74235B9}\Typical.png | image | |
MD5:18E81590AD31A376D07F0356505E9C18 | SHA256:E5CBE9FC7F2CCDA733BEDBD355DC14EEEE83303D14E04CE09AD5DD08B3359C4E | |||
| 1872 | _is5DA0.exe | C:\Users\admin\AppData\Local\Temp\{40FE81AE-C9D6-4872-9692-3743D74235B9}\ISLogoSmall.png | image | |
MD5:0DE9D9BD4AE583015157D5D3BC77801F | SHA256:3039E1E23AFC42BD3C07A8F4B65FB5D0377CA70F9F4FFB6FD7E7F33D82D837D1 | |||
| 1872 | _is5DA0.exe | C:\Users\admin\AppData\Local\Temp\{40FE81AE-C9D6-4872-9692-3743D74235B9}\scale-150\Folder.png | image | |
MD5:F3F9575A23F7C4CD35C8324231F5BD9E | SHA256:2EE9AA1DDA88CD9964D342DDA3FE56164C9906D5441E8381297F4DCDAE6C3E9D | |||
| 1872 | _is5DA0.exe | C:\Users\admin\AppData\Local\Temp\{40FE81AE-C9D6-4872-9692-3743D74235B9}\Repair.png | image | |
MD5:260D3EDFC4ED042A8E152613CFC0D59C | SHA256:5B4CC813A251FBBE0C2EA6BAB31C512DA865BAA9B20FA61B46CA8A30D302BBFA | |||
| 1872 | _is5DA0.exe | C:\Users\admin\AppData\Local\Temp\{40FE81AE-C9D6-4872-9692-3743D74235B9}\scale-150\Typical.png | image | |
MD5:BE7A62B3CF3AA240CCBB2E8CDF60F29F | SHA256:1D21BEA5C93FCED9F777A86F2B7D9EE11B697BCB4D9306794A81BEBA60CA7AAC | |||
| 1872 | _is5DA0.exe | C:\Users\admin\AppData\Local\Temp\{40FE81AE-C9D6-4872-9692-3743D74235B9}\scale-200\Application.png | image | |
MD5:5CB34DD612581AB996FF4141E96140D2 | SHA256:A057F7981A7932ADB78268F111C3100186B0DED651B1985F4DF969E786B481C8 | |||
| 1872 | _is5DA0.exe | C:\Users\admin\AppData\Local\Temp\{40FE81AE-C9D6-4872-9692-3743D74235B9}\scale-150\Repair.png | image | |
MD5:C404CB5D0854361968716C3AB8630F92 | SHA256:ABDCECCB0963B6A2621BC1C1477C5D7FA0743E6656275FF1E3402464D7946C87 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
5
TCP/UDP connections
38
DNS requests
18
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
4944 | svchost.exe | GET | 200 | 2.23.77.188:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
1268 | svchost.exe | GET | 200 | 2.19.11.120:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
1268 | svchost.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
2976 | SIHClient.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
2976 | SIHClient.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
1268 | svchost.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
5944 | MoUsoCoreWorker.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
5900 | RUXIMICS.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
2336 | svchost.exe | 172.211.123.250:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | FR | whitelisted |
4944 | svchost.exe | 20.190.159.75:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4944 | svchost.exe | 2.23.77.188:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
5168 | driver_web_installer.exe | 23.196.247.66:443 | auto-ds1.support-download.com | AKAMAI-AS | DE | suspicious |
1268 | svchost.exe | 2.19.11.120:80 | crl.microsoft.com | Elisa Oyj | NL | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
auto-ds1.support-download.com |
| unknown |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
nexusrules.officeapps.live.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |