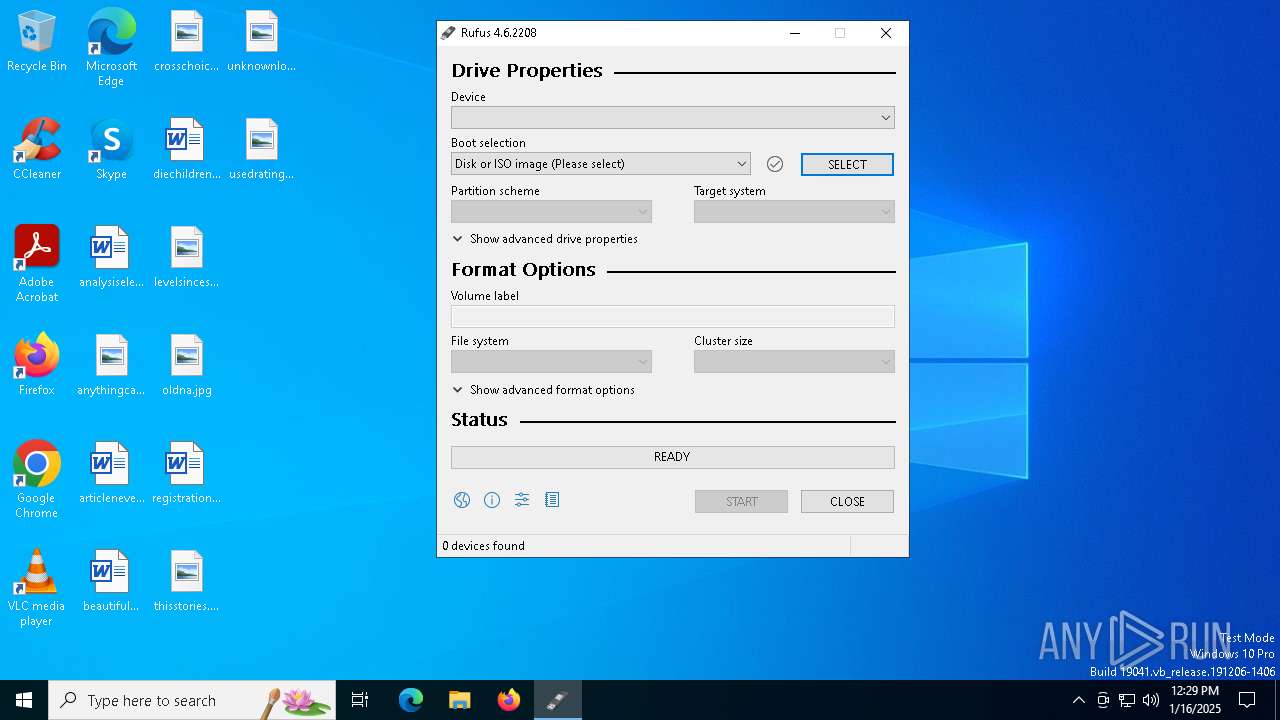
| File name: | rufus-4.6.exe |
| Full analysis: | https://app.any.run/tasks/faafea6f-8830-40a7-9784-2600327ae33e |
| Verdict: | Malicious activity |
| Analysis date: | January 16, 2025, 12:29:06 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32+ executable (GUI) x86-64 (stripped to external PDB), for MS Windows, 3 sections |
| MD5: | 8FE64DA09AF371B02A31828415ECE8F3 |
| SHA1: | 5B5C90DCD425C814B555A4567405601AA977EE0B |
| SHA256: | 8279696C1D78B14618500E9135886A3667B9DECC65946F3729002E4BFDBB20AB |
| SSDEEP: | 49152:d9kgFtkp4NxfvJwLv6S06WcSyYw+TkkU1xyocsO3j3054/Aqv3JedxLM1tYsNJfO:jkckp4NovdZSarkU1xws+z0SHJevLbMm |
MALICIOUS
GENERIC has been found (auto)
- rufus-4.6.exe (PID: 6256)
SUSPICIOUS
Reads security settings of Internet Explorer
- rufus-4.6.exe (PID: 6256)
Executes as Windows Service
- vds.exe (PID: 6340)
Checks Windows Trust Settings
- rufus-4.6.exe (PID: 6256)
INFO
Checks proxy server information
- rufus-4.6.exe (PID: 6256)
Reads the machine GUID from the registry
- rufus-4.6.exe (PID: 6256)
Reads the software policy settings
- rufus-4.6.exe (PID: 6256)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | UPX compressed Win32 Executable (87.1) |
|---|---|---|
| .exe | | | Generic Win/DOS Executable (6.4) |
| .exe | | | DOS Executable Generic (6.4) |
EXIF
EXE
| MachineType: | AMD AMD64 |
|---|---|
| TimeStamp: | 2024:10:21 14:50:37+00:00 |
| ImageFileCharacteristics: | Executable, No line numbers, No symbols, Large address aware, No debug |
| PEType: | PE32+ |
| LinkerVersion: | 2.43 |
| CodeSize: | 1568768 |
| InitializedDataSize: | 45056 |
| UninitializedDataSize: | 3026944 |
| EntryPoint: | 0x462170 |
| OSVersion: | 4 |
| ImageVersion: | - |
| SubsystemVersion: | 5.2 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 4.6.2208.0 |
| ProductVersionNumber: | 4.6.2208.0 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Windows NT 32-bit |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | Neutral |
| CharacterSet: | Unicode |
| Comments: | https://rufus.ie |
| CompanyName: | Akeo Consulting |
| FileDescription: | Rufus |
| FileVersion: | 4.6.2208 |
| InternalName: | Rufus |
| LegalCopyright: | © 2011-2024 Pete Batard (GPL v3) |
| LegalTrademarks: | https://www.gnu.org/licenses/gpl-3.0.html |
| OriginalFileName: | rufus-4.6.exe |
| ProductName: | Rufus |
| ProductVersion: | 4.6.2208 |
Total processes
133
Monitored processes
4
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 3832 | "C:\Users\admin\AppData\Local\Temp\rufus-4.6.exe" | C:\Users\admin\AppData\Local\Temp\rufus-4.6.exe | — | explorer.exe | |||||||||||
User: admin Company: Akeo Consulting Integrity Level: MEDIUM Description: Rufus Exit code: 3221226540 Version: 4.6.2208 Modules
| |||||||||||||||
| 6256 | "C:\Users\admin\AppData\Local\Temp\rufus-4.6.exe" | C:\Users\admin\AppData\Local\Temp\rufus-4.6.exe | explorer.exe | ||||||||||||
User: admin Company: Akeo Consulting Integrity Level: HIGH Description: Rufus Version: 4.6.2208 Modules
| |||||||||||||||
| 6304 | C:\WINDOWS\System32\vdsldr.exe -Embedding | C:\Windows\System32\vdsldr.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Virtual Disk Service Loader Exit code: 0 Version: 10.0.19041.3636 (WinBuild.160101.0800) | |||||||||||||||
| 6340 | C:\WINDOWS\System32\vds.exe | C:\Windows\System32\vds.exe | — | services.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Virtual Disk Service Exit code: 258 Version: 10.0.19041.1 (WinBuild.160101.0800) | |||||||||||||||
Total events
3 568
Read events
3 530
Write events
37
Delete events
1
Modification events
| (PID) Process: | (6256) rufus-4.6.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Akeo Consulting\Rufus |
| Operation: | write | Name: | UpdateCheckInterval |
Value: 86400 | |||
| (PID) Process: | (6256) rufus-4.6.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\BagMRU |
| Operation: | write | Name: | NodeSlots |
Value: 02020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202 | |||
| (PID) Process: | (6256) rufus-4.6.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\BagMRU |
| Operation: | write | Name: | MRUListEx |
Value: 040000000E0000000300000000000000100000000F0000000C0000000D0000000B000000050000000A000000090000000800000001000000070000000600000002000000FFFFFFFF | |||
| (PID) Process: | (6256) rufus-4.6.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\BagMRU\4 |
| Operation: | write | Name: | MRUListEx |
Value: 050000000000000004000000020000000100000003000000FFFFFFFF | |||
| (PID) Process: | (6256) rufus-4.6.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\Bags\120\Shell |
| Operation: | write | Name: | SniffedFolderType |
Value: Downloads | |||
| (PID) Process: | (6256) rufus-4.6.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\Bags\120\ComDlg\{885A186E-A440-4ADA-812B-DB871B942259} |
| Operation: | write | Name: | Mode |
Value: 4 | |||
| (PID) Process: | (6256) rufus-4.6.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\Bags\120\ComDlg\{885A186E-A440-4ADA-812B-DB871B942259} |
| Operation: | write | Name: | LogicalViewMode |
Value: 1 | |||
| (PID) Process: | (6256) rufus-4.6.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\Bags\120\ComDlg\{885A186E-A440-4ADA-812B-DB871B942259} |
| Operation: | write | Name: | FFlags |
Value: | |||
| (PID) Process: | (6256) rufus-4.6.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\Bags\120\ComDlg\{885A186E-A440-4ADA-812B-DB871B942259} |
| Operation: | write | Name: | IconSize |
Value: 16 | |||
| (PID) Process: | (6256) rufus-4.6.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\Bags\120\ComDlg\{885A186E-A440-4ADA-812B-DB871B942259} |
| Operation: | write | Name: | Sort |
Value: 000000000000000000000000000000000100000030F125B7EF471A10A5F102608C9EEBAC0A000000FFFFFFFF | |||
Executable files
0
Suspicious files
4
Text files
3
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6256 | rufus-4.6.exe | C:\Windows\System32\GroupPolicy\gpt.ini | text | |
MD5:3D89F23265C9E30A0CF055C3EB4D637C | SHA256:806582F6221C79BD4C7EACDC4B63E937CE247EEE2BA159F55C545CDFB2B1C25B | |||
| 6256 | rufus-4.6.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\103621DE9CD5414CC2538780B4B75751 | binary | |
MD5:E192462F281446B5D1500D474FBACC4B | SHA256:F1BA9F1B63C447682EBF9DE956D0DA2A027B1B779ABEF9522D347D3479139A60 | |||
| 6256 | rufus-4.6.exe | C:\Users\admin\AppData\Local\Temp\Ruf699A.tmp | text | |
MD5:903ACD7FECAB51ABB87835456159D49C | SHA256:BBB64F3615975E709A23577C867A6B563AD35CCFD8C7A4C7ABC5039B86B49E52 | |||
| 6256 | rufus-4.6.exe | C:\Windows\System32\GroupPolicy\Machine\Registry.pol | binary | |
MD5:0C014C71A70DC7758BFDC822E974F1F3 | SHA256:8EBD915268E16B55A3ABDE6F612363576FAB5DF656F955D672CCE8889C5FF9CA | |||
| 6256 | rufus-4.6.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\INetCache\IE\RR3E01RZ\Rufus_win.ver[1].sig | binary | |
MD5:C537D06B3CC3E92560950065FC01EF65 | SHA256:F9637B6C31EADB01ACEF2BE81EA6B3CCEDF3613CAF8B9948CE827CB9DF8D00E7 | |||
| 6256 | rufus-4.6.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\103621DE9CD5414CC2538780B4B75751 | binary | |
MD5:0046F72DA2E8C6A7DBA01010D4CEE5AF | SHA256:CDAED94E75C503A77B3E8D517A46F21A182FFCF3FCAF4B37B2AFFD7579B5DEDD | |||
| 6256 | rufus-4.6.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\INetCache\IE\RR3E01RZ\Rufus_win[1].ver | text | |
MD5:77A1926A292D4A84365E4805DDF09FC3 | SHA256:58C7AFB90032B99B1B8E0C9ECA1F39A9384B299A5C0DA6201BA725E232B87981 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
8
TCP/UDP connections
37
DNS requests
21
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 23.48.23.156:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
5064 | SearchApp.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
6256 | rufus-4.6.exe | GET | 200 | 23.209.209.135:80 | http://x1.c.lencr.org/ | unknown | — | — | whitelisted |
1176 | svchost.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
836 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
836 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
6956 | backgroundTaskHost.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAUZZSZEml49Gjh0j13P68w%3D | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
1572 | svchost.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4712 | MoUsoCoreWorker.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 2.23.227.208:443 | — | Ooredoo Q.S.C. | QA | unknown |
— | — | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
— | — | 23.48.23.156:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
— | — | 184.30.21.171:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
2192 | svchost.exe | 224.0.0.251:5353 | — | — | — | unknown |
2192 | svchost.exe | 224.0.0.252:5355 | — | — | — | whitelisted |
1572 | svchost.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
login.live.com |
| whitelisted |
go.microsoft.com |
| whitelisted |
rufus.ie |
| unknown |
x1.c.lencr.org |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
Threats
Process | Message |
|---|---|
rufus-4.6.exe | Could not open Internet session: [0x00002F83] The computer is disconnected from the network
|
rufus-4.6.exe | Could not open Internet session: [0x00002F83] The computer is disconnected from the network
|
rufus-4.6.exe | Rufus x64 v4.6.2208
|
rufus-4.6.exe | Windows version: Windows 10 Pro x64 (Build 19045.4046)
|
rufus-4.6.exe | Syslinux versions: 4.07/2013-07-25, 6.04/pre1
|
rufus-4.6.exe | System locale ID: 0x0409 (en-US)
|
rufus-4.6.exe | Grub versions: 0.4.6a, 2.12
|
rufus-4.6.exe | Found 517 revoked UEFI bootloaders from embedded list
|
rufus-4.6.exe | Will use default UI locale 0x0409
SetLGP: Successfully set NoDriveTypeAutorun policy to 0x0000009E
Localization set to 'en-US'
|
rufus-4.6.exe | Found 2351 additional revoked UEFI bootloaders from this system's SKUSiPolicy.p7b
|