| File name: | Block Adobe Acrobat.exe |
| Full analysis: | https://app.any.run/tasks/67401b1a-3bcc-4158-b852-e336ebc7e4e4 |
| Verdict: | Malicious activity |
| Analysis date: | March 15, 2024, 18:50:59 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows |
| MD5: | 37E03EDC3D9486DA77B1E98E54942046 |
| SHA1: | D8B4EABC45777B0DFBF2495101715863D3581097 |
| SHA256: | 8278F5BEA6E38FB25361233C7490DFE4945F38DFF1B9363A65225CF6229D5D6A |
| SSDEEP: | 98304:KZJ3XNrYQ9Om9OLkYEOTCvrQEUCwwmftUk61KkxiCsR3YqPyOM6Bu5MVf85FOVcC:gvSBco |
MALICIOUS
Drops the executable file immediately after the start
- Block Adobe Acrobat.exe (PID: 3936)
- QYWXTW.exe (PID: 2648)
SUSPICIOUS
Reads security settings of Internet Explorer
- Block Adobe Acrobat.exe (PID: 3936)
Reads the Internet Settings
- Block Adobe Acrobat.exe (PID: 3936)
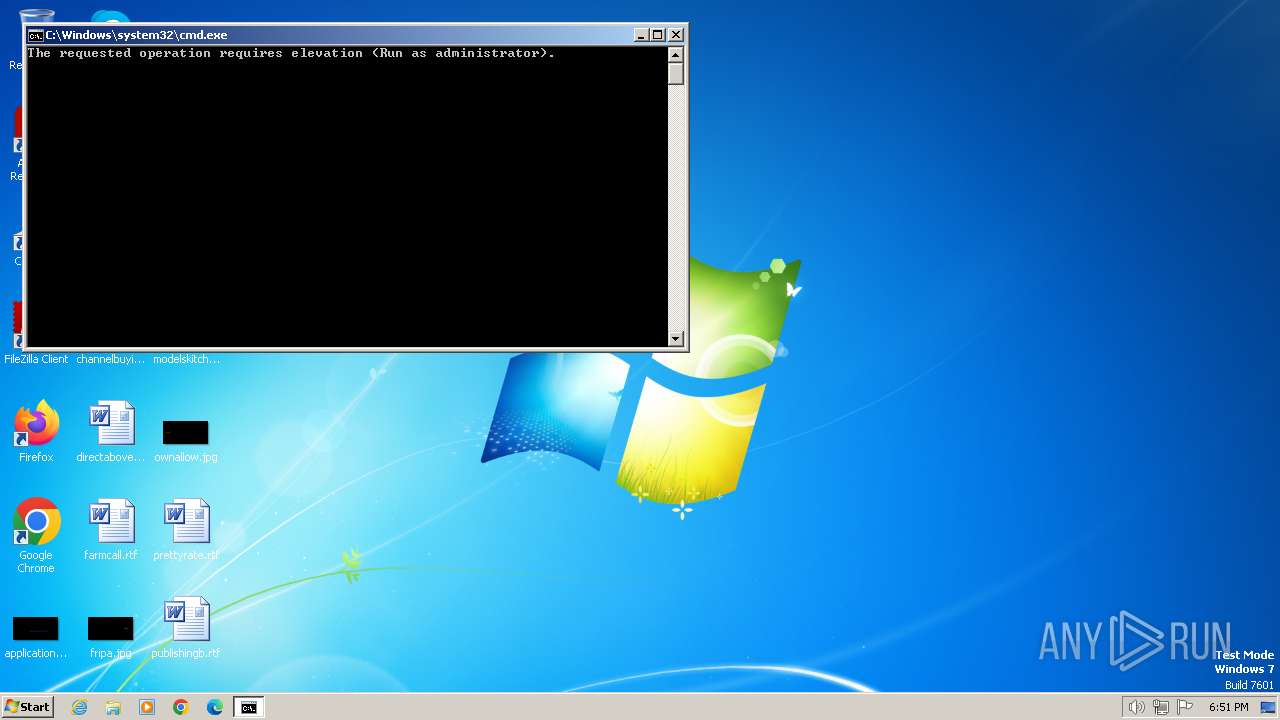
Executing commands from a ".bat" file
- Block Adobe Acrobat.exe (PID: 3936)
Starts CMD.EXE for commands execution
- Block Adobe Acrobat.exe (PID: 3936)
Executable content was dropped or overwritten
- QYWXTW.exe (PID: 2648)
- Block Adobe Acrobat.exe (PID: 3936)
Starts itself from another location
- QYWXTW.exe (PID: 2648)
Uses NETSH.EXE to add a firewall rule or allowed programs
- cmd.exe (PID: 2856)
INFO
Reads the computer name
- Block Adobe Acrobat.exe (PID: 3936)
- QYWXTW.exe (PID: 2648)
- icsys.icn.exe (PID: 956)
Create files in a temporary directory
- Block Adobe Acrobat.exe (PID: 3936)
- QYWXTW.exe (PID: 2648)
- icsys.icn.exe (PID: 956)
Checks supported languages
- Block Adobe Acrobat.exe (PID: 3936)
- QYWXTW.exe (PID: 2648)
- icsys.icn.exe (PID: 956)
Reads mouse settings
- Block Adobe Acrobat.exe (PID: 3936)
Reads the machine GUID from the registry
- QYWXTW.exe (PID: 2648)
- Block Adobe Acrobat.exe (PID: 3936)
- icsys.icn.exe (PID: 956)
Creates files or folders in the user directory
- QYWXTW.exe (PID: 2648)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win32 Executable MS Visual C++ (generic) (42.2) |
|---|---|---|
| .exe | | | Win64 Executable (generic) (37.3) |
| .dll | | | Win32 Dynamic Link Library (generic) (8.8) |
| .exe | | | Win32 Executable (generic) (6) |
| .exe | | | Generic Win/DOS Executable (2.7) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2012:01:29 21:32:28+00:00 |
| ImageFileCharacteristics: | No relocs, Executable, Large address aware, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 10 |
| CodeSize: | 526336 |
| InitializedDataSize: | 121856 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x165c1 |
| OSVersion: | 5 |
| ImageVersion: | - |
| SubsystemVersion: | 5 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 3.3.8.1 |
| ProductVersionNumber: | 3.3.8.1 |
| FileFlagsMask: | 0x0017 |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Unknown |
| FileSubtype: | - |
| LanguageCode: | English (British) |
| CharacterSet: | Unicode |
| FileDescription: | - |
| FileVersion: | 3, 3, 8, 1 |
| CompiledScript: | AutoIt v3 Script: 3, 3, 8, 1 |
Total processes
45
Monitored processes
8
Malicious processes
2
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 956 | C:\Users\admin\AppData\Local\icsys.icn.exe | C:\Users\admin\AppData\Local\icsys.icn.exe | — | QYWXTW.exe | |||||||||||
User: admin Company: Microsoft Integrity Level: MEDIUM Exit code: 0 Version: 1.00 Modules
| |||||||||||||||
| 2152 | netsh advfirewall firewall add rule name="Block Adobe Acrobat CEF Inbound" dir=in action=block program="C:\Program Files\Adobe\Acrobat DC\Acrobat\acrocef_1\AcroCEF.exe" | C:\Windows\System32\netsh.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Network Command Shell Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2648 | "C:\Users\admin\AppData\Local\Temp\QYWXTW.exe" | C:\Users\admin\AppData\Local\Temp\QYWXTW.exe | Block Adobe Acrobat.exe | ||||||||||||
User: admin Company: Microsoft Integrity Level: MEDIUM Exit code: 0 Version: 1.00 Modules
| |||||||||||||||
| 2856 | C:\Windows\system32\cmd.exe /c ""C:\Users\admin\AppData\Local\Temp\PRUHOM.bat" " | C:\Windows\System32\cmd.exe | — | Block Adobe Acrobat.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 1 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 3164 | netsh advfirewall firewall add rule name="Block Adobe Acrobat Outbound" dir=out action=block program="C:\Program Files\Adobe\Acrobat DC\Acrobat\Acrobat.exe" | C:\Windows\System32\netsh.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Network Command Shell Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3508 | netsh advfirewall firewall add rule name="Block Adobe Acrobat CEF Outbound" dir=out action=block program="C:\Program Files\Adobe\Acrobat DC\Acrobat\acrocef_1\AcroCEF.exe" | C:\Windows\System32\netsh.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Network Command Shell Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3936 | "C:\Users\admin\AppData\Local\Temp\Block Adobe Acrobat.exe" | C:\Users\admin\AppData\Local\Temp\Block Adobe Acrobat.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Version: 3, 3, 8, 1 Modules
| |||||||||||||||
| 4004 | netsh advfirewall firewall add rule name="Block Adobe Acrobat Inbound" dir=in action=block program="C:\Program Files\Adobe\Acrobat DC\Acrobat\Acrobat.exe" | C:\Windows\System32\netsh.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Network Command Shell Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
6 536
Read events
6 317
Write events
219
Delete events
0
Modification events
| (PID) Process: | (3936) Block Adobe Acrobat.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (3936) Block Adobe Acrobat.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (3936) Block Adobe Acrobat.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
| (PID) Process: | (3936) Block Adobe Acrobat.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 0 | |||
| (PID) Process: | (2648) QYWXTW.exe | Key: | HKEY_CURRENT_USER\Software\VB and VBA Program Settings\Explorer\Process |
| Operation: | write | Name: | LO |
Value: 1 | |||
| (PID) Process: | (4004) netsh.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\182\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (4004) netsh.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\182\52C64B7E |
| Operation: | write | Name: | @%SystemRoot%\system32\dhcpqec.dll,-100 |
Value: DHCP Quarantine Enforcement Client | |||
| (PID) Process: | (4004) netsh.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\182\52C64B7E |
| Operation: | write | Name: | @%SystemRoot%\system32\dhcpqec.dll,-101 |
Value: Provides DHCP based enforcement for NAP | |||
| (PID) Process: | (4004) netsh.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\182\52C64B7E |
| Operation: | write | Name: | @%SystemRoot%\system32\dhcpqec.dll,-103 |
Value: 1.0 | |||
| (PID) Process: | (4004) netsh.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\182\52C64B7E |
| Operation: | write | Name: | @%SystemRoot%\system32\dhcpqec.dll,-102 |
Value: Microsoft Corporation | |||
Executable files
4
Suspicious files
0
Text files
2
Unknown types
5
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3936 | Block Adobe Acrobat.exe | C:\Users\admin\AppData\Local\Temp\aut2D27.tmp | binary | |
MD5:8616EAFCD65E8ECED1679D5F10BF668B | SHA256:C281C3BB6A587D57E2054D2C0DD934CAC2BC72B3FEE431788B3E487196C0405C | |||
| 3936 | Block Adobe Acrobat.exe | C:\Users\admin\AppData\Local\Temp\PRUHOM.bat | text | |
MD5:6BCABF6CE3CC7CD3B9A5B08C4339CBB8 | SHA256:6E36E8A0649026ADB416C01389CF8D999EEADB80046D24008252E7E331EADF5C | |||
| 3936 | Block Adobe Acrobat.exe | C:\Users\admin\AppData\Local\Temp\aut2A09.tmp | binary | |
MD5:2A30EE0F0814E29B6A65482BEBE71F1A | SHA256:7B9B0C4F36A14BB4F874BDCAF267A18F92FE9FC504C9301387DE35F345AC524C | |||
| 2648 | QYWXTW.exe | C:\Users\admin\AppData\Local\icsys.icn.exe | executable | |
MD5:C5F78D788265A8C2B80017A0DC351266 | SHA256:0A48908B44578715B511D6C067B2B0C1351783C049C68183F6067AFFF1FF72D0 | |||
| 956 | icsys.icn.exe | C:\Users\admin\AppData\Local\Temp\~DFEBC2749FEA133EEA.TMP | binary | |
MD5:ABA546A28EAA8240F9FF9AED0DED864E | SHA256:BED93FD97FE3A2448DE4CE16456F6262D70C804964FFF2D11C56417F259078BB | |||
| 2648 | QYWXTW.exe | C:\Users\admin\AppData\Local\Temp\~DF61276A315DDEC49F.TMP | binary | |
MD5:3F616AFEE2E9B0983CF60A4F7884A6CA | SHA256:08F093A56963E4780887BFA2DCA2AE9E598FE5782F2EEE8B5419774B5E4E818B | |||
| 3936 | Block Adobe Acrobat.exe | C:\Users\admin\AppData\Local\Temp\QYWXTW.exe | executable | |
MD5:021079DC0918B9C7359E93E770678000 | SHA256:EE63E26E84D8092FDA9E527F7DB34777B6261D8DFC96ED42167383F88CF1C487 | |||
| 2648 | QYWXTW.exe | C:\users\admin\appdata\local\temp\qywxtw.exe | executable | |
MD5:2C2055233260E5BB20CE675AFD39ED0D | SHA256:306827F0EF0A4CBECD5458776244BF7EE99F2E49569DAF0034176B39F5D1C17D | |||
| 3936 | Block Adobe Acrobat.exe | C:\Users\admin\AppData\Local\Temp\aut2A58.tmp | binary | |
MD5:E2AA47F9CEB2F39F8A8E5EB859C5A6E9 | SHA256:7BC434C78607CC7671CEACBE2045A3CDF54C9CF890D3A17125797598E5205558 | |||
| 3936 | Block Adobe Acrobat.exe | C:\Users\admin\AppData\Local\Temp\dconybr | text | |
MD5:5159B9EDDBF7013343862C7F1BBFFD93 | SHA256:E63AD9435283F818B55C50254FAC9AB1BEC9D208CB3C2A0A0D289905C493B543 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
4
DNS requests
0
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
— | — | 224.0.0.252:5355 | — | — | — | unknown |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
1080 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |