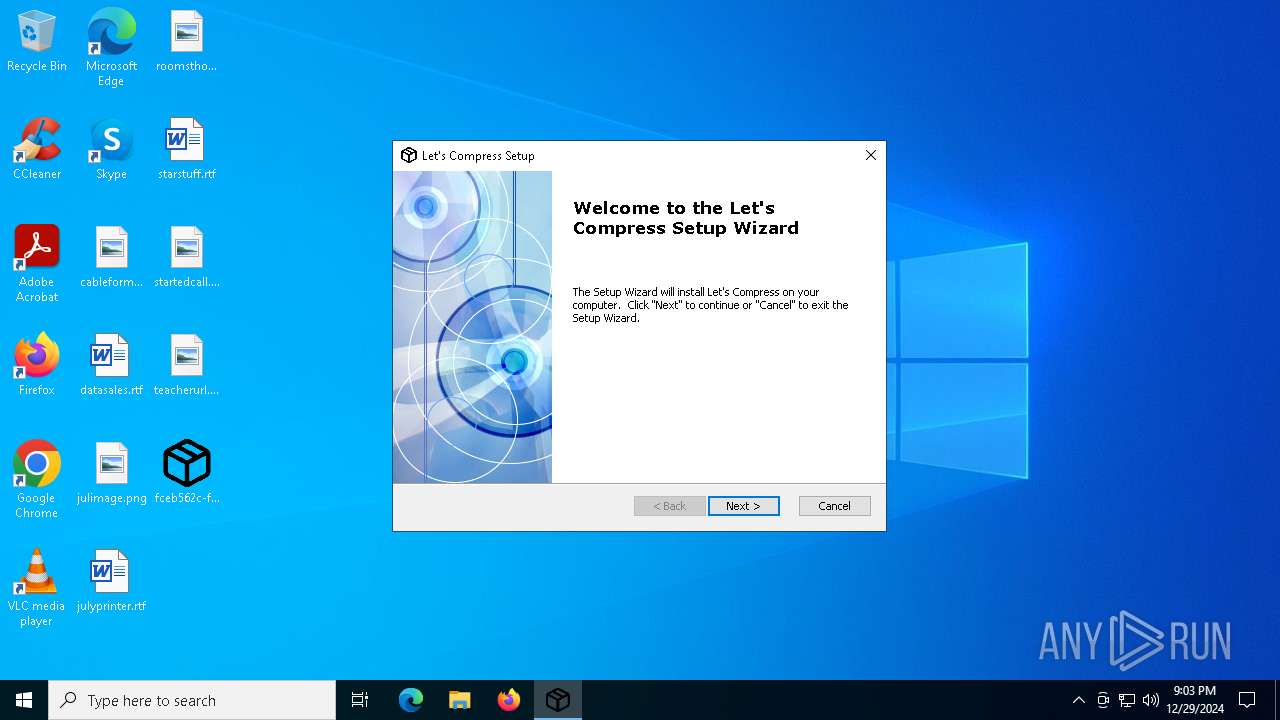
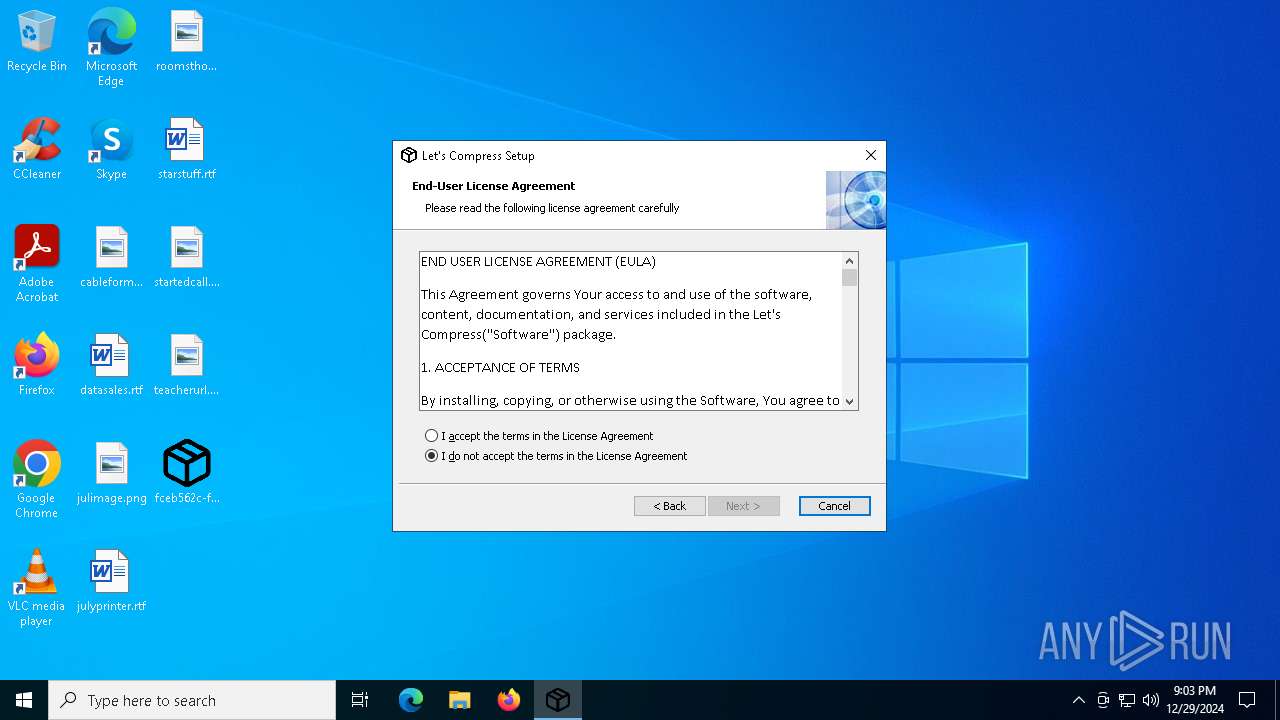
| File name: | Let's%20Compress.exe |
| Full analysis: | https://app.any.run/tasks/fceb562c-fb15-4cd9-97f2-f6ed2ef10ebd |
| Verdict: | Malicious activity |
| Analysis date: | December 29, 2024, 21:03:13 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows, 5 sections |
| MD5: | 2D433FBD6EA054E6F3FD76A4BDBBAC9F |
| SHA1: | 10019E9350410CB8C0F44CE56E2E989FE75CAF4D |
| SHA256: | 8274999029D17B1E9AD93CFDA903DA9EE7BF9992F5DA010EA70BB73FE09E42D7 |
| SSDEEP: | 98304:bL0druM/vIX0pafjCHE6B5fMxNRlOqAhcNAjcXILaOvjyv2C9EckMN4sjrway8eD:A7cY5 |
MALICIOUS
Changes powershell execution policy (Bypass)
- msiexec.exe (PID: 6400)
Bypass execution policy to execute commands
- powershell.exe (PID: 5320)
SUSPICIOUS
Reads security settings of Internet Explorer
- fceb562c-fb15-4cd9-97f2-f6ed2ef10ebd.exe (PID: 1296)
- fceb562c-fb15-4cd9-97f2-f6ed2ef10ebd.exe (PID: 3884)
- msiexec.exe (PID: 5240)
Reads the Windows owner or organization settings
- fceb562c-fb15-4cd9-97f2-f6ed2ef10ebd.exe (PID: 1296)
- fceb562c-fb15-4cd9-97f2-f6ed2ef10ebd.exe (PID: 3884)
- msiexec.exe (PID: 6248)
ADVANCEDINSTALLER mutex has been found
- fceb562c-fb15-4cd9-97f2-f6ed2ef10ebd.exe (PID: 1296)
Process drops legitimate windows executable
- fceb562c-fb15-4cd9-97f2-f6ed2ef10ebd.exe (PID: 1296)
- fceb562c-fb15-4cd9-97f2-f6ed2ef10ebd.exe (PID: 3884)
- msiexec.exe (PID: 5240)
Checks Windows Trust Settings
- fceb562c-fb15-4cd9-97f2-f6ed2ef10ebd.exe (PID: 1296)
- fceb562c-fb15-4cd9-97f2-f6ed2ef10ebd.exe (PID: 3884)
- msiexec.exe (PID: 6248)
- msiexec.exe (PID: 5240)
Executable content was dropped or overwritten
- fceb562c-fb15-4cd9-97f2-f6ed2ef10ebd.exe (PID: 1296)
- rundll32.exe (PID: 6544)
- rundll32.exe (PID: 6956)
- rundll32.exe (PID: 7004)
- rundll32.exe (PID: 7064)
- rundll32.exe (PID: 6224)
- fceb562c-fb15-4cd9-97f2-f6ed2ef10ebd.exe (PID: 3884)
- rundll32.exe (PID: 6852)
- rundll32.exe (PID: 5268)
Application launched itself
- fceb562c-fb15-4cd9-97f2-f6ed2ef10ebd.exe (PID: 1296)
Drops 7-zip archiver for unpacking
- msiexec.exe (PID: 5240)
Reads Internet Explorer settings
- fceb562c-fb15-4cd9-97f2-f6ed2ef10ebd.exe (PID: 1296)
The process hide an interactive prompt from the user
- msiexec.exe (PID: 6400)
The process bypasses the loading of PowerShell profile settings
- msiexec.exe (PID: 6400)
Starts POWERSHELL.EXE for commands execution
- msiexec.exe (PID: 6400)
The process drops C-runtime libraries
- msiexec.exe (PID: 5240)
The process executes Powershell scripts
- msiexec.exe (PID: 6400)
INFO
The sample compiled with english language support
- fceb562c-fb15-4cd9-97f2-f6ed2ef10ebd.exe (PID: 1296)
- fceb562c-fb15-4cd9-97f2-f6ed2ef10ebd.exe (PID: 3884)
- msiexec.exe (PID: 6248)
- msiexec.exe (PID: 5240)
Checks supported languages
- fceb562c-fb15-4cd9-97f2-f6ed2ef10ebd.exe (PID: 1296)
- msiexec.exe (PID: 6248)
- msiexec.exe (PID: 6400)
- fceb562c-fb15-4cd9-97f2-f6ed2ef10ebd.exe (PID: 3884)
- msiexec.exe (PID: 5240)
Reads the computer name
- fceb562c-fb15-4cd9-97f2-f6ed2ef10ebd.exe (PID: 1296)
- msiexec.exe (PID: 6400)
- msiexec.exe (PID: 6248)
- fceb562c-fb15-4cd9-97f2-f6ed2ef10ebd.exe (PID: 3884)
- msiexec.exe (PID: 5240)
Creates files or folders in the user directory
- fceb562c-fb15-4cd9-97f2-f6ed2ef10ebd.exe (PID: 1296)
- msiexec.exe (PID: 6248)
- msiexec.exe (PID: 5240)
Reads the software policy settings
- fceb562c-fb15-4cd9-97f2-f6ed2ef10ebd.exe (PID: 1296)
- fceb562c-fb15-4cd9-97f2-f6ed2ef10ebd.exe (PID: 3884)
- rundll32.exe (PID: 6956)
- rundll32.exe (PID: 7064)
- rundll32.exe (PID: 7004)
- rundll32.exe (PID: 6224)
- msiexec.exe (PID: 6248)
- msiexec.exe (PID: 5240)
- rundll32.exe (PID: 6852)
- rundll32.exe (PID: 6544)
- rundll32.exe (PID: 5268)
- powershell.exe (PID: 5320)
Reads Environment values
- fceb562c-fb15-4cd9-97f2-f6ed2ef10ebd.exe (PID: 1296)
- msiexec.exe (PID: 6400)
- fceb562c-fb15-4cd9-97f2-f6ed2ef10ebd.exe (PID: 3884)
- msiexec.exe (PID: 5240)
Checks proxy server information
- fceb562c-fb15-4cd9-97f2-f6ed2ef10ebd.exe (PID: 1296)
- rundll32.exe (PID: 6544)
- rundll32.exe (PID: 6956)
- rundll32.exe (PID: 7004)
- rundll32.exe (PID: 7064)
- rundll32.exe (PID: 6224)
- msiexec.exe (PID: 5240)
- rundll32.exe (PID: 6852)
- rundll32.exe (PID: 5268)
Create files in a temporary directory
- fceb562c-fb15-4cd9-97f2-f6ed2ef10ebd.exe (PID: 1296)
- rundll32.exe (PID: 6956)
- rundll32.exe (PID: 6544)
- rundll32.exe (PID: 7004)
- rundll32.exe (PID: 7064)
- rundll32.exe (PID: 6224)
- fceb562c-fb15-4cd9-97f2-f6ed2ef10ebd.exe (PID: 3884)
- rundll32.exe (PID: 6852)
- rundll32.exe (PID: 5268)
- msiexec.exe (PID: 6400)
- powershell.exe (PID: 5320)
Disables trace logs
- rundll32.exe (PID: 6956)
- rundll32.exe (PID: 7004)
- rundll32.exe (PID: 6224)
- rundll32.exe (PID: 6544)
- rundll32.exe (PID: 7064)
- rundll32.exe (PID: 6852)
- rundll32.exe (PID: 5268)
Reads the machine GUID from the registry
- fceb562c-fb15-4cd9-97f2-f6ed2ef10ebd.exe (PID: 1296)
- fceb562c-fb15-4cd9-97f2-f6ed2ef10ebd.exe (PID: 3884)
- msiexec.exe (PID: 6248)
- msiexec.exe (PID: 5240)
Executable content was dropped or overwritten
- msiexec.exe (PID: 6248)
- msiexec.exe (PID: 5240)
Creates a software uninstall entry
- msiexec.exe (PID: 6248)
Uses string replace method (POWERSHELL)
- powershell.exe (PID: 5320)
Reads security settings of Internet Explorer
- powershell.exe (PID: 5320)
The process uses the downloaded file
- powershell.exe (PID: 5320)
Checks if a key exists in the options dictionary (POWERSHELL)
- powershell.exe (PID: 5320)
Script raised an exception (POWERSHELL)
- powershell.exe (PID: 5320)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win64 Executable (generic) (64.6) |
|---|---|---|
| .dll | | | Win32 Dynamic Link Library (generic) (15.4) |
| .exe | | | Win32 Executable (generic) (10.5) |
| .exe | | | Generic Win/DOS Executable (4.6) |
| .exe | | | DOS Executable Generic (4.6) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2023:08:08 12:49:22+00:00 |
| ImageFileCharacteristics: | Executable, Large address aware, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 14.36 |
| CodeSize: | 2534912 |
| InitializedDataSize: | 988160 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x1e0862 |
| OSVersion: | 6 |
| ImageVersion: | - |
| SubsystemVersion: | 6 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 2.3.26.0 |
| ProductVersionNumber: | 2.3.26.0 |
| FileFlagsMask: | 0x003f |
| FileFlags: | Debug |
| FileOS: | Win32 |
| ObjectFileType: | Dynamic link library |
| FileSubtype: | - |
| LanguageCode: | English (U.S.) |
| CharacterSet: | Unicode |
| CompanyName: | Let's Compress |
| FileDescription: | Let's Compress Installer |
| FileVersion: | 2.3.26.0 |
| InternalName: | lets_compress_without_update |
| LegalCopyright: | Copyright (C) 2024 Let's Compress |
| OriginalFileName: | lets_compress_without_update.exe |
| ProductName: | Let's Compress |
| ProductVersion: | 2.3.26.0 |
Total processes
144
Monitored processes
14
Malicious processes
4
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 524 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1296 | "C:\Users\admin\Desktop\fceb562c-fb15-4cd9-97f2-f6ed2ef10ebd.exe" | C:\Users\admin\Desktop\fceb562c-fb15-4cd9-97f2-f6ed2ef10ebd.exe | explorer.exe | ||||||||||||
User: admin Company: Let's Compress Integrity Level: MEDIUM Description: Let's Compress Installer Exit code: 0 Version: 2.3.26.0 Modules
| |||||||||||||||
| 3884 | C:\Users\admin\Desktop\fceb562c-fb15-4cd9-97f2-f6ed2ef10ebd.exe /i "C:\Users\admin\AppData\Roaming\Let's Compress\Let's Compress 2.3.26.0\install\DF0F6B8\lets_compress_without_update.msi" AI_EUIMSI=1 APPDIR="C:\Users\admin\AppData\Roaming\Let's Compress" SECONDSEQUENCE="1" CLIENTPROCESSID="1296" CHAINERUIPROCESSID="1296Chainer" ACTION="INSTALL" EXECUTEACTION="INSTALL" CLIENTUILEVEL="0" ADDLOCAL="MainFeature" ACTIVE_WINDOW_NAME="ready_installation" PRIMARYFOLDER="APPDIR" ROOTDRIVE="C:\" AI_SETUPEXEPATH="C:\Users\admin\Desktop\fceb562c-fb15-4cd9-97f2-f6ed2ef10ebd.exe" SETUPEXEDIR="C:\Users\admin\Desktop\" EXE_CMD_LINE="/exenoupdates /forcecleanup /wintime 1735504931 " AI_INSTALL="1" TARGETDIR="C:\" AI_SETUPEXEPATH_ORIGINAL="C:\Users\admin\Desktop\fceb562c-fb15-4cd9-97f2-f6ed2ef10ebd.exe" | C:\Users\admin\Desktop\fceb562c-fb15-4cd9-97f2-f6ed2ef10ebd.exe | fceb562c-fb15-4cd9-97f2-f6ed2ef10ebd.exe | ||||||||||||
User: admin Company: Let's Compress Integrity Level: MEDIUM Description: Let's Compress Installer Exit code: 0 Version: 2.3.26.0 Modules
| |||||||||||||||
| 5240 | C:\Windows\syswow64\MsiExec.exe -Embedding 44B3AD59D321FC33F1657EB1975D3C7C | C:\Windows\SysWOW64\msiexec.exe | msiexec.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows® installer Exit code: 0 Version: 5.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5268 | rundll32.exe "C:\Users\admin\AppData\Local\Temp\MSID0F1.tmp",zzzzInvokeManagedCustomActionOutOfProc SfxCA_1298671 1833 RequestSender!RequestSender.CustomActions.FinishInstall | C:\Windows\SysWOW64\rundll32.exe | msiexec.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Exit code: 0 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5320 | -NoProfile -Noninteractive -ExecutionPolicy Bypass -File "C:\Users\admin\AppData\Local\Temp\pssD142.ps1" -propFile "C:\Users\admin\AppData\Local\Temp\msiD13E.txt" -scriptFile "C:\Users\admin\AppData\Local\Temp\scrD13F.ps1" -scriptArgsFile "C:\Users\admin\AppData\Local\Temp\scrD140.txt" -propSep " :<->: " -lineSep " <<:>> " -testPrefix "_testValue." | C:\Windows\SysWOW64\WindowsPowerShell\v1.0\powershell.exe | — | msiexec.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6224 | rundll32.exe "C:\Users\admin\AppData\Local\Temp\MSI9D5D.tmp",zzzzInvokeManagedCustomActionOutOfProc SfxCA_1285484 1051 RequestSender!RequestSender.CustomActions.NextReadyInstallation | C:\Windows\SysWOW64\rundll32.exe | msiexec.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Exit code: 0 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6248 | C:\WINDOWS\system32\msiexec.exe /V | C:\Windows\System32\msiexec.exe | services.exe | ||||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows® installer Version: 5.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6400 | C:\Windows\syswow64\MsiExec.exe -Embedding BEEB715CCB032F261D20DB04021AD25D C | C:\Windows\SysWOW64\msiexec.exe | — | msiexec.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows® installer Exit code: 0 Version: 5.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6544 | rundll32.exe "C:\Users\admin\AppData\Local\Temp\MSI6182.tmp",zzzzInvokeManagedCustomActionOutOfProc SfxCA_1270156 352 RequestSender!RequestSender.CustomActions.Start | C:\Windows\SysWOW64\rundll32.exe | msiexec.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Exit code: 0 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
27 833
Read events
27 691
Write events
130
Delete events
12
Modification events
| (PID) Process: | (6956) rundll32.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Tracing\rundll32_RASMANCS |
| Operation: | write | Name: | EnableFileTracing |
Value: 0 | |||
| (PID) Process: | (6956) rundll32.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Tracing\rundll32_RASMANCS |
| Operation: | write | Name: | EnableAutoFileTracing |
Value: 0 | |||
| (PID) Process: | (6956) rundll32.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Tracing\rundll32_RASMANCS |
| Operation: | write | Name: | EnableConsoleTracing |
Value: 0 | |||
| (PID) Process: | (6956) rundll32.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Tracing\rundll32_RASMANCS |
| Operation: | write | Name: | FileTracingMask |
Value: | |||
| (PID) Process: | (6956) rundll32.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Tracing\rundll32_RASMANCS |
| Operation: | write | Name: | ConsoleTracingMask |
Value: | |||
| (PID) Process: | (6956) rundll32.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Tracing\rundll32_RASMANCS |
| Operation: | write | Name: | MaxFileSize |
Value: 1048576 | |||
| (PID) Process: | (6956) rundll32.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Tracing\rundll32_RASMANCS |
| Operation: | write | Name: | FileDirectory |
Value: %windir%\tracing | |||
| (PID) Process: | (6544) rundll32.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Tracing\rundll32_RASAPI32 |
| Operation: | write | Name: | EnableFileTracing |
Value: 0 | |||
| (PID) Process: | (6544) rundll32.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Tracing\rundll32_RASAPI32 |
| Operation: | write | Name: | EnableAutoFileTracing |
Value: 0 | |||
| (PID) Process: | (6544) rundll32.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Tracing\rundll32_RASAPI32 |
| Operation: | write | Name: | EnableConsoleTracing |
Value: 0 | |||
Executable files
76
Suspicious files
57
Text files
27
Unknown types
2
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 1296 | fceb562c-fb15-4cd9-97f2-f6ed2ef10ebd.exe | C:\Users\admin\AppData\Roaming\Let's Compress\Let's Compress 2.3.26.0\install\holder0.aiph | binary | |
MD5:DCCC7F915AABB69110CA196B37DDE265 | SHA256:B8A24F4F7EF71D59BF7A0B8812CE7FF23F39347FC481F9E2321D74B67BDA00E8 | |||
| 1296 | fceb562c-fb15-4cd9-97f2-f6ed2ef10ebd.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\9CB4373A4252DE8D2212929836304EC5_1AB74AA2E3A56E1B8AD8D3FEC287554E | binary | |
MD5:2C31EDC8CFE69462015894EF5A0330BE | SHA256:F0F9CE4C7151331E7E08BBC0AB933C96C791DF25AA2CB0432FA95FC5F118BD96 | |||
| 1296 | fceb562c-fb15-4cd9-97f2-f6ed2ef10ebd.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\357F04AD41BCF5FE18FCB69F60C6680F_D343022F8C5E519322B5D9E07C403E21 | der | |
MD5:78E526651C254538F6817F210302BEB1 | SHA256:6384ECB4C0816EFAB9AF265E633E455A5D3627D0A7D2C8C8EE1694169E839ADB | |||
| 1296 | fceb562c-fb15-4cd9-97f2-f6ed2ef10ebd.exe | C:\Users\admin\AppData\Local\Temp\shi5FC7.tmp | executable | |
MD5:84A34BF3486F7B9B7035DB78D78BDD1E | SHA256:F85911C910B660E528D2CF291BAA40A92D09961996D6D84E7A53A7095C7CD96E | |||
| 1296 | fceb562c-fb15-4cd9-97f2-f6ed2ef10ebd.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\9CB4373A4252DE8D2212929836304EC5_1AB74AA2E3A56E1B8AD8D3FEC287554E | der | |
MD5:38CFC4A9EC3A488B0F6A38C294FFB781 | SHA256:DD506D5723B5CA91D44C2C24634B3B35733BD9DD5CF081ACF45018E650E37AD0 | |||
| 6544 | rundll32.exe | C:\Users\admin\AppData\Local\Temp\MSI6182.tmp-\RequestSender.dll | executable | |
MD5:B580A63E82C50119ACA3D2864897700C | SHA256:3766A96231D79108A8DD6867927A0B081C1AD2B3265F9117839050BC7A3E2600 | |||
| 1296 | fceb562c-fb15-4cd9-97f2-f6ed2ef10ebd.exe | C:\Users\admin\AppData\Local\Temp\MSI6025.tmp | executable | |
MD5:B7A6A99CBE6E762C0A61A8621AD41706 | SHA256:39FD8D36F8E5D915AD571EA429DB3C3DE6E9C160DBEA7C3E137C9BA4B7FD301D | |||
| 1296 | fceb562c-fb15-4cd9-97f2-f6ed2ef10ebd.exe | C:\Users\admin\AppData\Local\Temp\MSI6151.tmp | executable | |
MD5:B7A6A99CBE6E762C0A61A8621AD41706 | SHA256:39FD8D36F8E5D915AD571EA429DB3C3DE6E9C160DBEA7C3E137C9BA4B7FD301D | |||
| 6544 | rundll32.exe | C:\Users\admin\AppData\Local\Temp\MSI6182.tmp-\CustomAction.config | xml | |
MD5:8C22D283225F3BDB8E36522C359796F9 | SHA256:5D6FD5049F33AC6B16EC0431787FA61C66630BA1916BB4C70F3F6B5844B74ECB | |||
| 6544 | rundll32.exe | C:\Users\admin\AppData\Local\Temp\MSI6182.tmp-\Microsoft.Deployment.WindowsInstaller.dll | executable | |
MD5:1A5CAEA6734FDD07CAA514C3F3FB75DA | SHA256:CF06D4ED4A8BAF88C82D6C9AE0EFC81C469DE6DA8788AB35F373B350A4B4CDCA | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
10
TCP/UDP connections
41
DNS requests
22
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | GET | 200 | 2.23.9.218:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 23.48.23.176:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
1296 | fceb562c-fb15-4cd9-97f2-f6ed2ef10ebd.exe | GET | 200 | 151.101.66.133:80 | http://ocsp.globalsign.com/codesigningrootr45/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQVFZP5vqhCrtRN5SWf40Rn6NM1IAQUHwC%2FRoAK%2FHg5t6W0Q9lWULvOljsCEHe9DgW3WQu2HUdhUx4%2Fde0%3D | unknown | — | — | whitelisted |
1296 | fceb562c-fb15-4cd9-97f2-f6ed2ef10ebd.exe | GET | 200 | 151.101.66.133:80 | http://ocsp.globalsign.com/gsgccr45evcodesignca2020/ME0wSzBJMEcwRTAJBgUrDgMCGgUABBQaCbVYh07WONuW4e63Ydlu4AlbDAQUJZ3Q%2FFkJhmPF7POxEztXHAOSNhECDEa8nmSLUN2zOQqKig%3D%3D | unknown | — | — | whitelisted |
1176 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
5064 | SearchApp.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
6884 | SIHClient.exe | GET | 200 | 88.221.169.152:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
2892 | svchost.exe | GET | 200 | 2.19.217.103:80 | http://x1.c.lencr.org/ | unknown | — | — | whitelisted |
5240 | msiexec.exe | GET | 200 | 2.16.202.121:80 | http://r11.o.lencr.org/MFMwUTBPME0wSzAJBgUrDgMCGgUABBQaUrm0WeTDM5ghfoZtS72KO9ZnzgQUCLkRO6XQhRi06g%2BgrZ%2BGHo78OCcCEgQ%2F5C%2FM4neRmA5u6wQrmKSbNg%3D%3D | unknown | — | — | whitelisted |
6884 | SIHClient.exe | GET | 200 | 88.221.169.152:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4712 | MoUsoCoreWorker.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
3508 | svchost.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 23.48.23.176:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
— | — | 2.23.9.218:80 | www.microsoft.com | AKAMAI-AS | CZ | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
5064 | SearchApp.exe | 23.212.110.154:443 | www.bing.com | Akamai International B.V. | CZ | whitelisted |
1296 | fceb562c-fb15-4cd9-97f2-f6ed2ef10ebd.exe | 151.101.66.133:80 | ocsp.globalsign.com | FASTLY | US | whitelisted |
1176 | svchost.exe | 20.190.159.73:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
www.bing.com |
| whitelisted |
ocsp.globalsign.com |
| whitelisted |
login.live.com |
| whitelisted |
go.microsoft.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
e.letscompress.online |
| unknown |