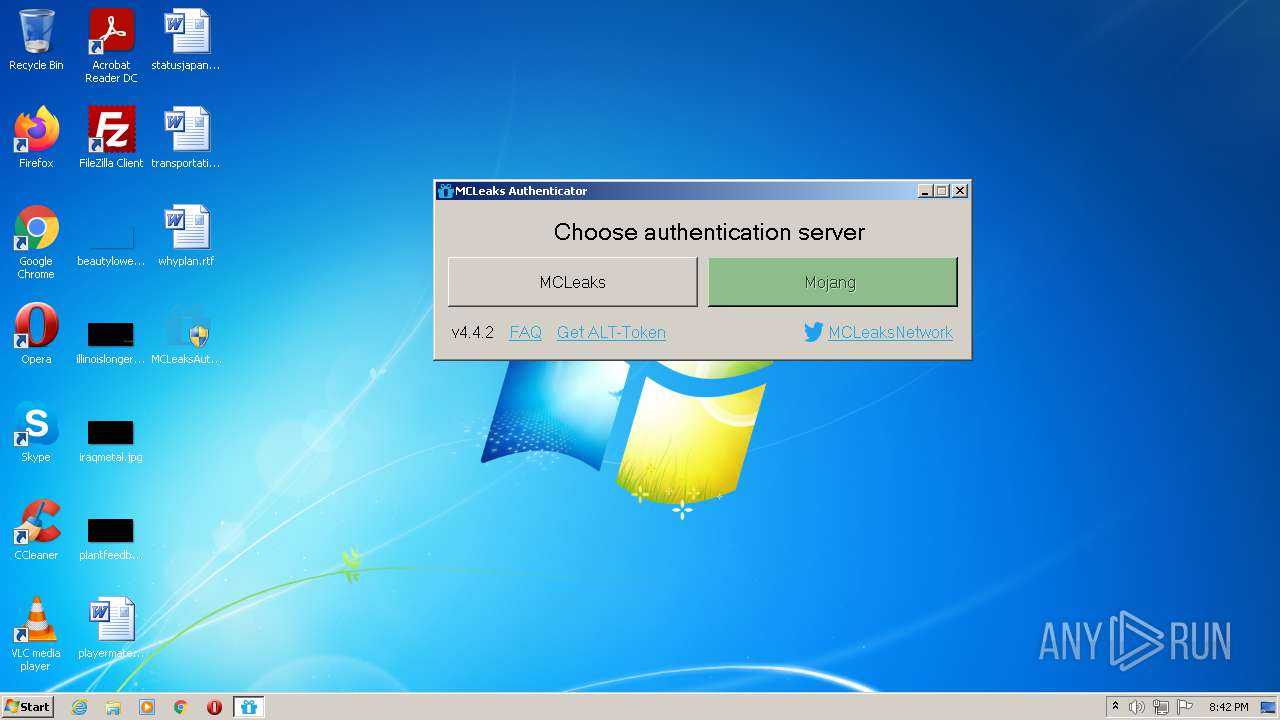
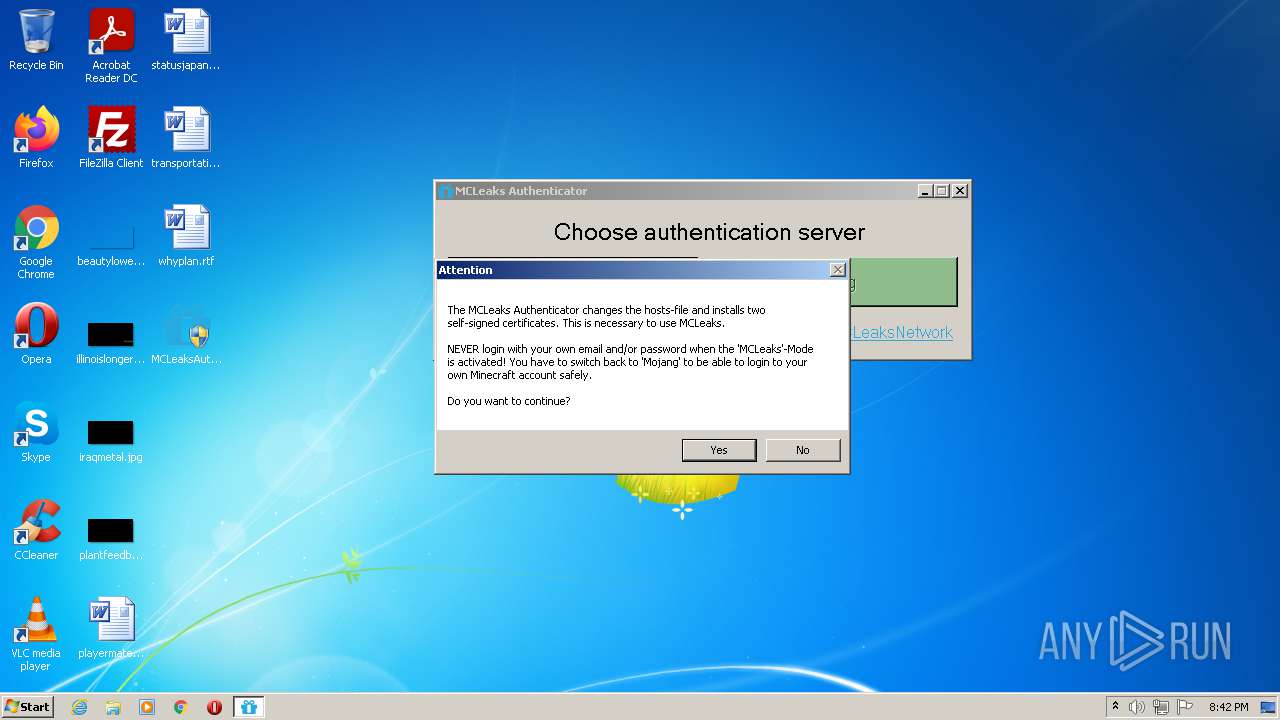
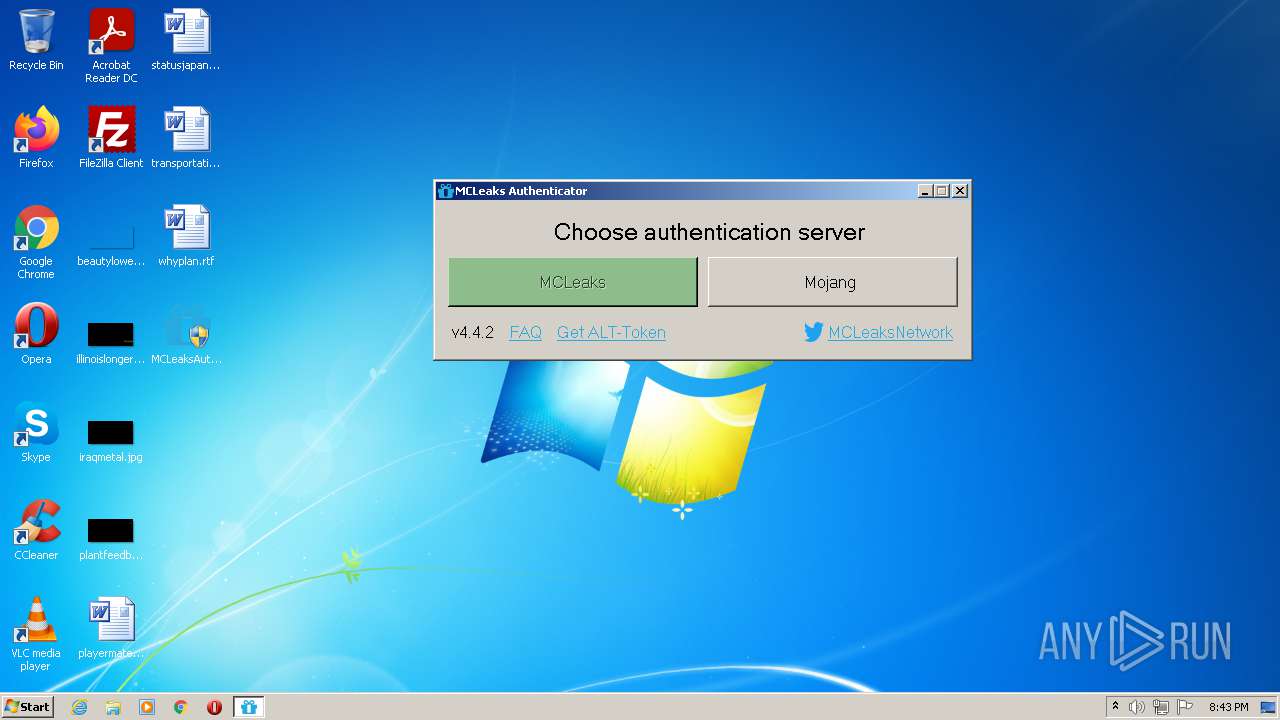
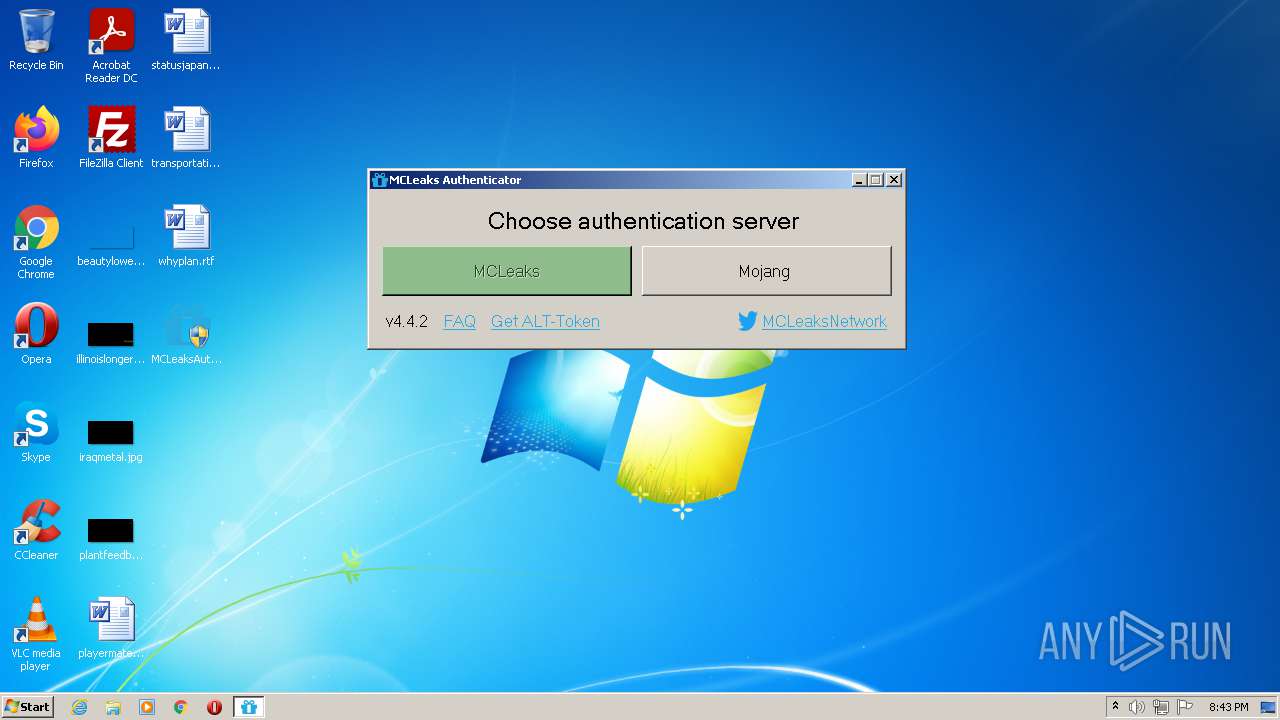
| download: | MCLeaksAuthenticator_4.4.2.exe |
| Full analysis: | https://app.any.run/tasks/ab2ed9e0-9a9c-4bec-a34b-be405f4d9f45 |
| Verdict: | Malicious activity |
| Analysis date: | June 25, 2021, 19:42:11 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386 Mono/.Net assembly, for MS Windows |
| MD5: | 3D178B9C1CB35E3838E18E2F041AF940 |
| SHA1: | 03B53B2469C7F535FA36517D417A927F85FF60CC |
| SHA256: | 8268A4E84EB89DE66F6884E784BC0238A5C274D68DA6A4654CE9996CA4BBE9C2 |
| SSDEEP: | 12288:UHSvxsZFpo+2pK5RT2U+Y3m/X/VURdB1vdLvOc:UHSvxsP8pKn2U+is8 |
MALICIOUS
Changes settings of System certificates
- certutil.exe (PID: 3600)
Writes to the hosts file
- MCLeaksAuthenticator_4.4.2.exe (PID: 3992)
SUSPICIOUS
Reads the computer name
- MCLeaksAuthenticator_4.4.2.exe (PID: 3992)
Creates files in the Windows directory
- certutil.exe (PID: 3600)
Checks supported languages
- MCLeaksAuthenticator_4.4.2.exe (PID: 3992)
Creates files in the user directory
- MCLeaksAuthenticator_4.4.2.exe (PID: 3992)
Removes files from Windows directory
- certutil.exe (PID: 3600)
Starts Internet Explorer
- MCLeaksAuthenticator_4.4.2.exe (PID: 3992)
Reads Microsoft Outlook installation path
- iexplore.exe (PID: 2440)
Reads Environment values
- MCLeaksAuthenticator_4.4.2.exe (PID: 3992)
INFO
Reads settings of System Certificates
- MCLeaksAuthenticator_4.4.2.exe (PID: 3992)
- certutil.exe (PID: 3600)
- iexplore.exe (PID: 2440)
- iexplore.exe (PID: 3840)
Checks supported languages
- certutil.exe (PID: 3600)
- iexplore.exe (PID: 3840)
- iexplore.exe (PID: 2440)
Reads the computer name
- certutil.exe (PID: 3600)
- iexplore.exe (PID: 2440)
- iexplore.exe (PID: 3840)
Application launched itself
- iexplore.exe (PID: 3840)
Reads the hosts file
- MCLeaksAuthenticator_4.4.2.exe (PID: 3992)
Changes internet zones settings
- iexplore.exe (PID: 3840)
Reads internet explorer settings
- iexplore.exe (PID: 2440)
Checks Windows Trust Settings
- iexplore.exe (PID: 2440)
- iexplore.exe (PID: 3840)
Creates files in the user directory
- iexplore.exe (PID: 2440)
Changes settings of System certificates
- iexplore.exe (PID: 2440)
Adds / modifies Windows certificates
- iexplore.exe (PID: 2440)
Reads the date of Windows installation
- iexplore.exe (PID: 3840)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Generic CIL Executable (.NET, Mono, etc.) (63.1) |
|---|---|---|
| .exe | | | Win64 Executable (generic) (23.8) |
| .dll | | | Win32 Dynamic Link Library (generic) (5.6) |
| .exe | | | Win32 Executable (generic) (3.8) |
| .exe | | | Generic Win/DOS Executable (1.7) |
EXIF
EXE
| AssemblyVersion: | 4.4.2.0 |
|---|---|
| ProductVersion: | 4.4.2.0 |
| ProductName: | MCLeaksAuthenticator |
| OriginalFileName: | MCLeaksAuthenticator.exe |
| LegalTrademarks: | - |
| LegalCopyright: | Copyright © 2021 MCLeaks |
| InternalName: | MCLeaksAuthenticator.exe |
| FileVersion: | 4.4.2.0 |
| FileDescription: | MCLeaksAuthenticator |
| CompanyName: | MCLeaks |
| Comments: | The MCLeaks Tool |
| CharacterSet: | Unicode |
| LanguageCode: | Neutral |
| FileSubtype: | - |
| ObjectFileType: | Executable application |
| FileOS: | Win32 |
| FileFlags: | (none) |
| FileFlagsMask: | 0x003f |
| ProductVersionNumber: | 4.4.2.0 |
| FileVersionNumber: | 4.4.2.0 |
| Subsystem: | Windows GUI |
| SubsystemVersion: | 6 |
| ImageVersion: | - |
| OSVersion: | 4 |
| EntryPoint: | 0x95dfa |
| UninitializedDataSize: | - |
| InitializedDataSize: | 19456 |
| CodeSize: | 605696 |
| LinkerVersion: | 48 |
| PEType: | PE32 |
| TimeStamp: | 2021:04:11 12:55:30+02:00 |
| MachineType: | Intel 386 or later, and compatibles |
Summary
| Architecture: | IMAGE_FILE_MACHINE_I386 |
|---|---|
| Subsystem: | IMAGE_SUBSYSTEM_WINDOWS_GUI |
| Compilation Date: | 11-Apr-2021 10:55:30 |
| Debug artifacts: |
|
| Comments: | The MCLeaks Tool |
| CompanyName: | MCLeaks |
| FileDescription: | MCLeaksAuthenticator |
| FileVersion: | 4.4.2.0 |
| InternalName: | MCLeaksAuthenticator.exe |
| LegalCopyright: | Copyright © 2021 MCLeaks |
| LegalTrademarks: | - |
| OriginalFilename: | MCLeaksAuthenticator.exe |
| ProductName: | MCLeaksAuthenticator |
| ProductVersion: | 4.4.2.0 |
| Assembly Version: | 4.4.2.0 |
DOS Header
| Magic number: | MZ |
|---|---|
| Bytes on last page of file: | 0x0090 |
| Pages in file: | 0x0003 |
| Relocations: | 0x0000 |
| Size of header: | 0x0004 |
| Min extra paragraphs: | 0x0000 |
| Max extra paragraphs: | 0xFFFF |
| Initial SS value: | 0x0000 |
| Initial SP value: | 0x00B8 |
| Checksum: | 0x0000 |
| Initial IP value: | 0x0000 |
| Initial CS value: | 0x0000 |
| Overlay number: | 0x0000 |
| OEM identifier: | 0x0000 |
| OEM information: | 0x0000 |
| Address of NE header: | 0x00000080 |
PE Headers
| Signature: | PE |
|---|---|
| Machine: | IMAGE_FILE_MACHINE_I386 |
| Number of sections: | 3 |
| Time date stamp: | 11-Apr-2021 10:55:30 |
| Pointer to Symbol Table: | 0x00000000 |
| Number of symbols: | 0 |
| Size of Optional Header: | 0x00E0 |
| Characteristics: |
|
Sections
Name | Virtual Address | Virtual Size | Raw Size | Charateristics | Entropy |
|---|---|---|---|---|---|
.text | 0x00002000 | 0x00093E00 | 0x00093E00 | IMAGE_SCN_CNT_CODE, IMAGE_SCN_MEM_EXECUTE, IMAGE_SCN_MEM_READ | 7.68748 |
.rsrc | 0x00096000 | 0x00004998 | 0x00004A00 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ | 3.40757 |
.reloc | 0x0009C000 | 0x0000000C | 0x00000200 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_DISCARDABLE, IMAGE_SCN_MEM_READ | 0.10191 |
Resources
Title | Entropy | Size | Codepage | Language | Type |
|---|---|---|---|---|---|
1 | 4.95516 | 622 | UNKNOWN | UNKNOWN | RT_MANIFEST |
32512 | 1.91924 | 20 | UNKNOWN | UNKNOWN | RT_GROUP_ICON |
Imports
mscoree.dll |
Total processes
44
Monitored processes
5
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 2440 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:3840 CREDAT:275457 /prefetch:2 | C:\Program Files\Internet Explorer\iexplore.exe | iexplore.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 3600 | "certutil" -addstore "Root" "C:\Users\admin\AppData\Roaming\mcleaks\authserver.mojang.com.crt" | C:\Windows\system32\certutil.exe | — | MCLeaksAuthenticator_4.4.2.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: CertUtil.exe Exit code: 0 Version: 6.1.7601.18151 (win7sp1_gdr.130512-1533) Modules
| |||||||||||||||
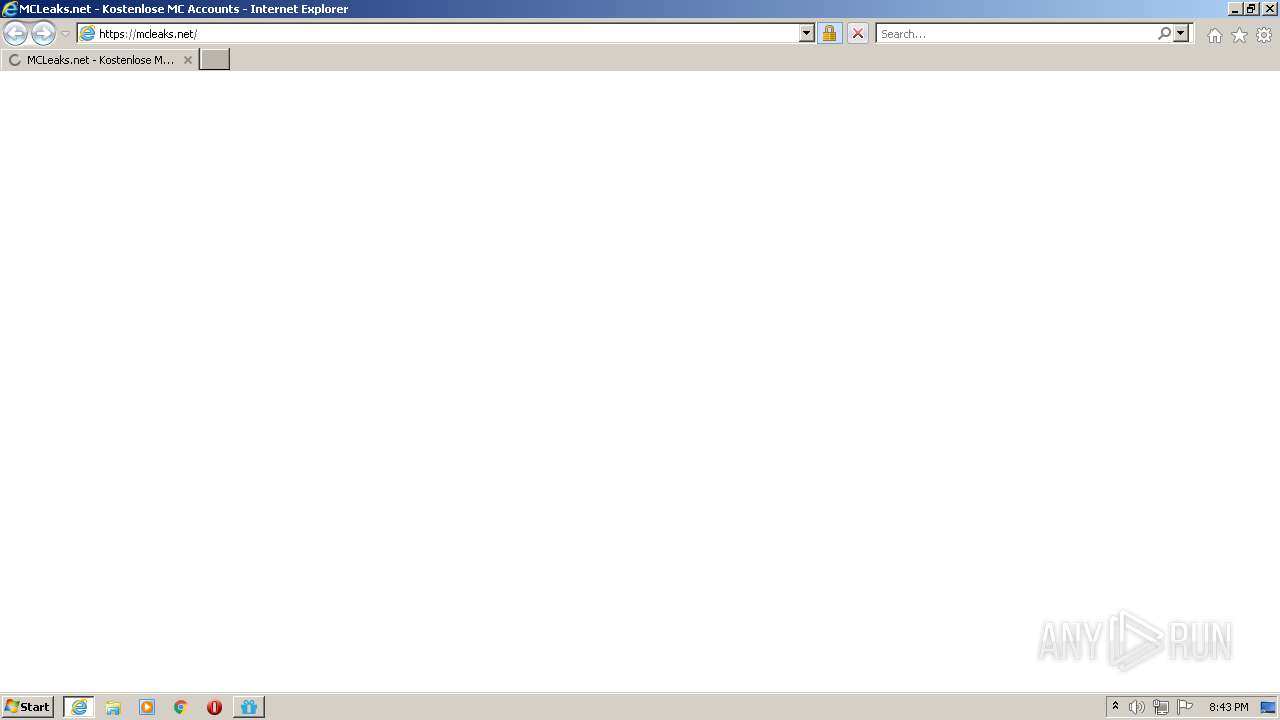
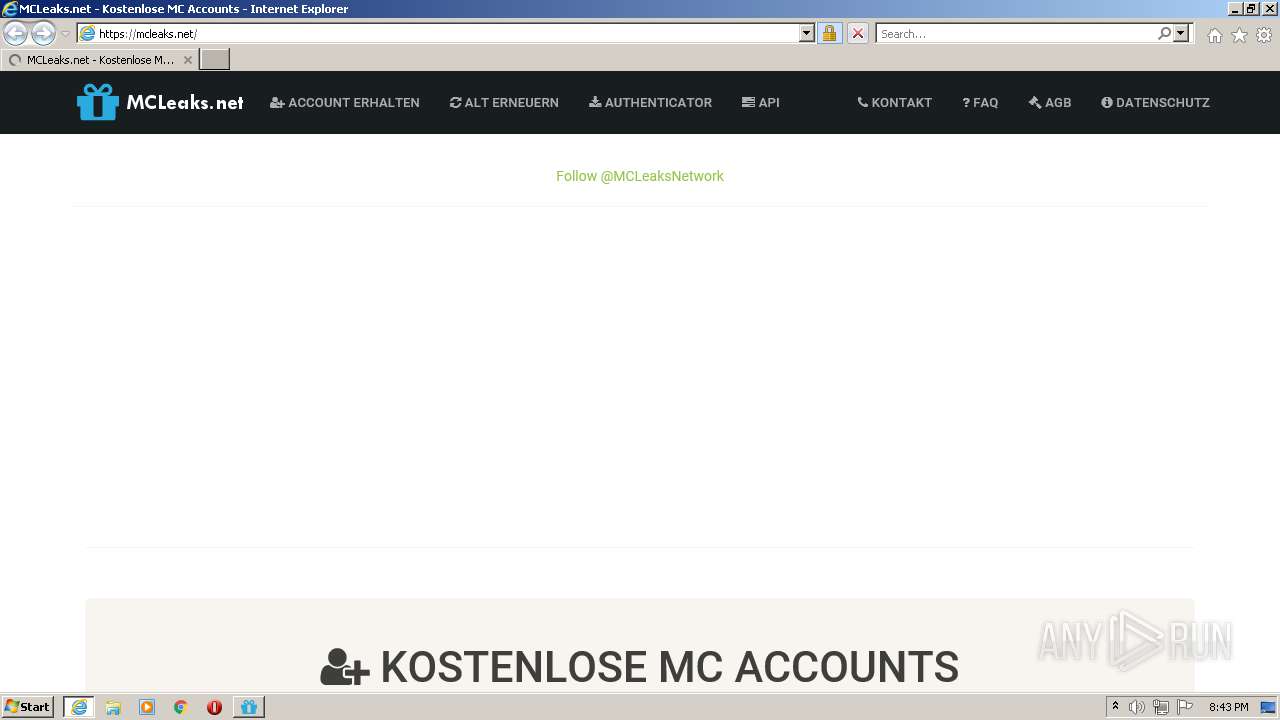
| 3840 | "C:\Program Files\Internet Explorer\iexplore.exe" https://mcleaks.net/ | C:\Program Files\Internet Explorer\iexplore.exe | MCLeaksAuthenticator_4.4.2.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 3992 | "C:\Users\admin\Desktop\MCLeaksAuthenticator_4.4.2.exe" | C:\Users\admin\Desktop\MCLeaksAuthenticator_4.4.2.exe | Explorer.EXE | ||||||||||||
User: admin Company: MCLeaks Integrity Level: HIGH Description: MCLeaksAuthenticator Exit code: 0 Version: 4.4.2.0 Modules
| |||||||||||||||
| 4068 | "C:\Users\admin\Desktop\MCLeaksAuthenticator_4.4.2.exe" | C:\Users\admin\Desktop\MCLeaksAuthenticator_4.4.2.exe | — | Explorer.EXE | |||||||||||
User: admin Company: MCLeaks Integrity Level: MEDIUM Description: MCLeaksAuthenticator Exit code: 3221226540 Version: 4.4.2.0 Modules
| |||||||||||||||
Total events
24 516
Read events
24 290
Write events
226
Delete events
0
Modification events
| (PID) Process: | (3992) MCLeaksAuthenticator_4.4.2.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\MCLeaksAuthenticator_4_RASAPI32 |
| Operation: | write | Name: | EnableFileTracing |
Value: 0 | |||
| (PID) Process: | (3992) MCLeaksAuthenticator_4.4.2.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\MCLeaksAuthenticator_4_RASAPI32 |
| Operation: | write | Name: | EnableConsoleTracing |
Value: 0 | |||
| (PID) Process: | (3992) MCLeaksAuthenticator_4.4.2.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\MCLeaksAuthenticator_4_RASAPI32 |
| Operation: | write | Name: | FileTracingMask |
Value: | |||
| (PID) Process: | (3992) MCLeaksAuthenticator_4.4.2.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\MCLeaksAuthenticator_4_RASAPI32 |
| Operation: | write | Name: | ConsoleTracingMask |
Value: | |||
| (PID) Process: | (3992) MCLeaksAuthenticator_4.4.2.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\MCLeaksAuthenticator_4_RASAPI32 |
| Operation: | write | Name: | MaxFileSize |
Value: 1048576 | |||
| (PID) Process: | (3992) MCLeaksAuthenticator_4.4.2.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\MCLeaksAuthenticator_4_RASAPI32 |
| Operation: | write | Name: | FileDirectory |
Value: %windir%\tracing | |||
| (PID) Process: | (3992) MCLeaksAuthenticator_4.4.2.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\MCLeaksAuthenticator_4_RASMANCS |
| Operation: | write | Name: | EnableFileTracing |
Value: 0 | |||
| (PID) Process: | (3992) MCLeaksAuthenticator_4.4.2.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\MCLeaksAuthenticator_4_RASMANCS |
| Operation: | write | Name: | EnableConsoleTracing |
Value: 0 | |||
| (PID) Process: | (3992) MCLeaksAuthenticator_4.4.2.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\MCLeaksAuthenticator_4_RASMANCS |
| Operation: | write | Name: | FileTracingMask |
Value: | |||
| (PID) Process: | (3992) MCLeaksAuthenticator_4.4.2.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\MCLeaksAuthenticator_4_RASMANCS |
| Operation: | write | Name: | ConsoleTracingMask |
Value: | |||
Executable files
0
Suspicious files
26
Text files
57
Unknown types
28
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3992 | MCLeaksAuthenticator_4.4.2.exe | C:\Users\admin\AppData\Roaming\mcleaks\cacerts | jks | |
MD5:— | SHA256:— | |||
| 3992 | MCLeaksAuthenticator_4.4.2.exe | C:\Users\admin\AppData\Roaming\mcleaks\sessionserver.mojang.com.crt | text | |
MD5:— | SHA256:— | |||
| 3992 | MCLeaksAuthenticator_4.4.2.exe | C:\Users\admin\AppData\Roaming\mcleaks\authserver.mojang.com.crt | text | |
MD5:— | SHA256:— | |||
| 2440 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\B6QGX7LP\DH4HHFZ5.htm | html | |
MD5:— | SHA256:— | |||
| 2440 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\6Z2BCOUL\bootstrap[1].css | text | |
MD5:— | SHA256:— | |||
| 2440 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\57C8EDB95DF3F0AD4EE2DC2B8CFD4157 | binary | |
MD5:— | SHA256:— | |||
| 2440 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\B6QGX7LP\AO8m5kQ6-4SOBwoOUjwUiWZKC7M[1].js | text | |
MD5:— | SHA256:— | |||
| 2440 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\6BADA8974A10C4BD62CC921D13E43B18_28DEA62A0AE77228DD387E155AD0BA27 | der | |
MD5:— | SHA256:— | |||
| 2440 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\6Z2BCOUL\custom[1].js | text | |
MD5:— | SHA256:— | |||
| 2440 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\CFE86DBBE02D859DC92F1E17E0574EE8_46766FC45507C0B9E264E4C18BC7288B | der | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
20
TCP/UDP connections
59
DNS requests
28
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2440 | iexplore.exe | GET | 200 | 151.139.128.14:80 | http://ocsp.comodoca.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBRTtU9uFqgVGHhJwXZyWCNXmVR5ngQUoBEKIz6W8Qfs4q8p74Klf9AwpLQCEDlyRDr5IrdR19NsEN0xNZU%3D | US | der | 471 b | whitelisted |
2440 | iexplore.exe | GET | 200 | 216.58.214.227:80 | http://ocsp.pki.goog/gts1o1core/MFIwUDBOMEwwSjAJBgUrDgMCGgUABBRCRjDCJxnb3nDwj%2Fxz5aZfZjgXvAQUmNH4bhDrz5vsYJ8YkBug630J%2FSsCEQCxnynH5ycfFgUAAAAAh%2BRd | US | der | 472 b | whitelisted |
2440 | iexplore.exe | GET | 200 | 216.58.214.227:80 | http://ocsp.pki.goog/gts1c3/MFIwUDBOMEwwSjAJBgUrDgMCGgUABBTHLnmK3f9hNLO67UdCuLvGwCQHYwQUinR%2Fr4XN7pXNPZzQ4kYU83E1HScCEQC02wBtvW1eJwoAAAAA3JF%2B | US | der | 472 b | whitelisted |
2440 | iexplore.exe | GET | 200 | 151.139.128.14:80 | http://ocsp.usertrust.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTNMNJMNDqCqx8FcBWK16EHdimS6QQUU3m%2FWqorSs9UgOHYm8Cd8rIDZssCEH1bUSa0droR23QWC7xTDac%3D | US | der | 727 b | whitelisted |
2440 | iexplore.exe | GET | 200 | 216.58.214.227:80 | http://ocsp.pki.goog/gts1c3/MFIwUDBOMEwwSjAJBgUrDgMCGgUABBTHLnmK3f9hNLO67UdCuLvGwCQHYwQUinR%2Fr4XN7pXNPZzQ4kYU83E1HScCEQDAj6AZuIBzdAoAAAAA3JuZ | US | der | 472 b | whitelisted |
2440 | iexplore.exe | GET | 200 | 216.58.214.227:80 | http://ocsp.pki.goog/gts1o1core/MFIwUDBOMEwwSjAJBgUrDgMCGgUABBRCRjDCJxnb3nDwj%2Fxz5aZfZjgXvAQUmNH4bhDrz5vsYJ8YkBug630J%2FSsCEQCxyUYW89XmnAUAAAAAh%2BPe | US | der | 472 b | whitelisted |
2440 | iexplore.exe | GET | 200 | 216.58.214.227:80 | http://ocsp.pki.goog/gts1c3/MFIwUDBOMEwwSjAJBgUrDgMCGgUABBTHLnmK3f9hNLO67UdCuLvGwCQHYwQUinR%2Fr4XN7pXNPZzQ4kYU83E1HScCEQCa%2BkMO6O7i%2FwoAAAAA3KDI | US | der | 472 b | whitelisted |
2440 | iexplore.exe | GET | 200 | 216.58.214.227:80 | http://ocsp.pki.goog/gts1c3/MFIwUDBOMEwwSjAJBgUrDgMCGgUABBTHLnmK3f9hNLO67UdCuLvGwCQHYwQUinR%2Fr4XN7pXNPZzQ4kYU83E1HScCEQCvGbInaJdxsAoAAAAA3JGP | US | der | 472 b | whitelisted |
2440 | iexplore.exe | GET | 200 | 216.58.214.227:80 | http://ocsp.pki.goog/gts1c3/MFIwUDBOMEwwSjAJBgUrDgMCGgUABBTHLnmK3f9hNLO67UdCuLvGwCQHYwQUinR%2Fr4XN7pXNPZzQ4kYU83E1HScCEQCh60gbhQdNXgoAAAAA3JGB | US | der | 472 b | whitelisted |
2440 | iexplore.exe | GET | 200 | 216.58.214.227:80 | http://ocsp.pki.goog/gsr2/ME4wTDBKMEgwRjAJBgUrDgMCGgUABBTgXIsxbvr2lBkPpoIEVRE6gHlCnAQUm%2BIHV2ccHsBqBt5ZtJot39wZhi4CDQHjtJqhjYqpgSVpULg%3D | US | der | 468 b | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
3992 | MCLeaksAuthenticator_4.4.2.exe | 172.67.190.251:443 | api.mcleaks.net | — | US | unknown |
2440 | iexplore.exe | 172.67.190.251:443 | api.mcleaks.net | — | US | unknown |
2440 | iexplore.exe | 2.21.242.189:80 | ctldl.windowsupdate.com | Akamai International B.V. | NL | whitelisted |
2440 | iexplore.exe | 2.21.242.196:80 | ctldl.windowsupdate.com | Akamai International B.V. | NL | whitelisted |
2440 | iexplore.exe | 93.184.220.29:80 | ocsp.digicert.com | MCI Communications Services, Inc. d/b/a Verizon Business | US | whitelisted |
2440 | iexplore.exe | 142.250.185.202:443 | fonts.googleapis.com | Google Inc. | US | whitelisted |
2440 | iexplore.exe | 104.16.18.94:443 | cdnjs.cloudflare.com | Cloudflare Inc | US | unknown |
2440 | iexplore.exe | 142.250.186.98:443 | pagead2.googlesyndication.com | Google Inc. | US | suspicious |
2440 | iexplore.exe | 69.16.175.42:443 | code.jquery.com | Highwinds Network Group, Inc. | US | malicious |
2440 | iexplore.exe | 142.250.74.196:443 | www.google.com | Google Inc. | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
api.mcleaks.net |
| malicious |
mcleaks.net |
| whitelisted |
ctldl.windowsupdate.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
fonts.googleapis.com |
| whitelisted |
cdnjs.cloudflare.com |
| whitelisted |
code.jquery.com |
| whitelisted |
pagead2.googlesyndication.com |
| whitelisted |
www.google.com |
| malicious |
www.google-analytics.com |
| whitelisted |