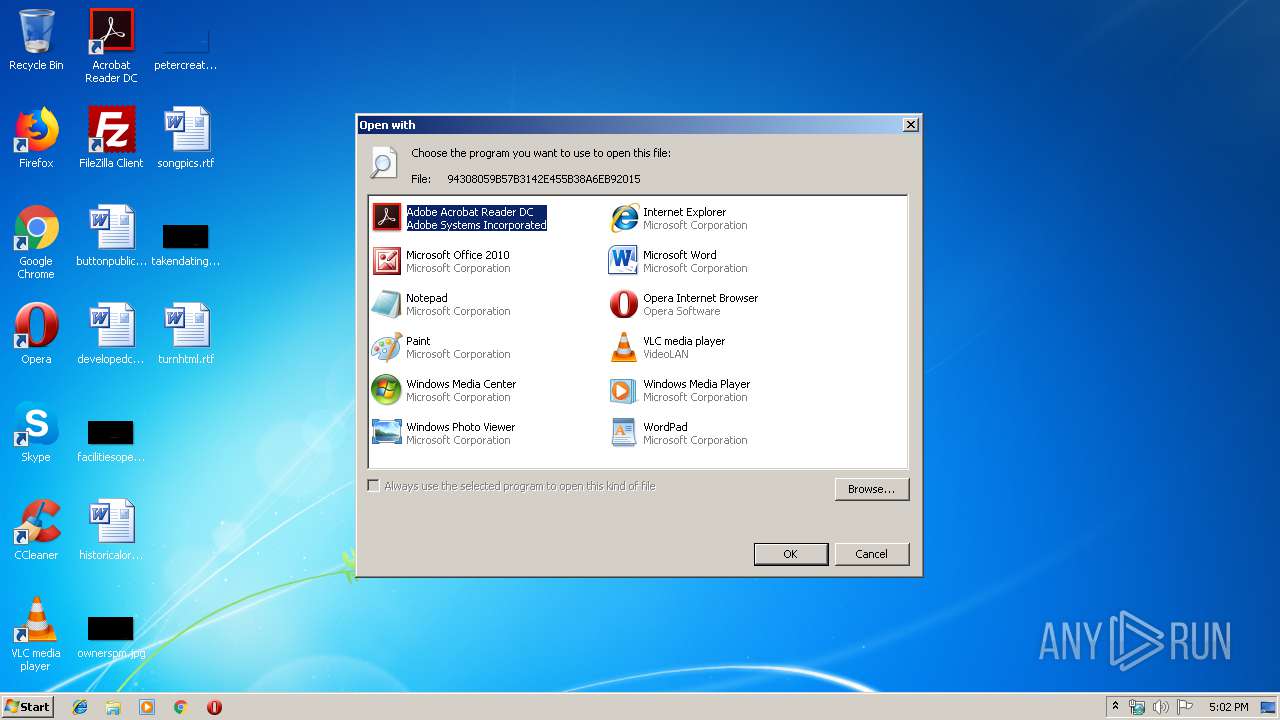
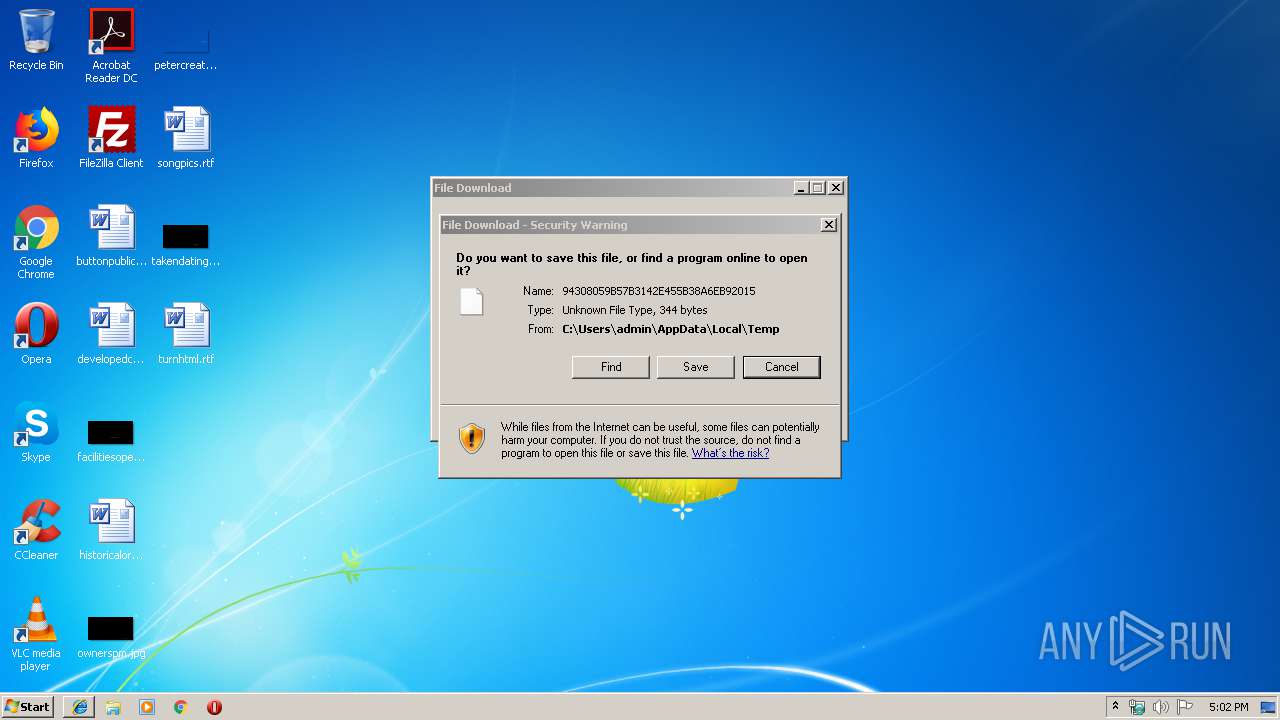
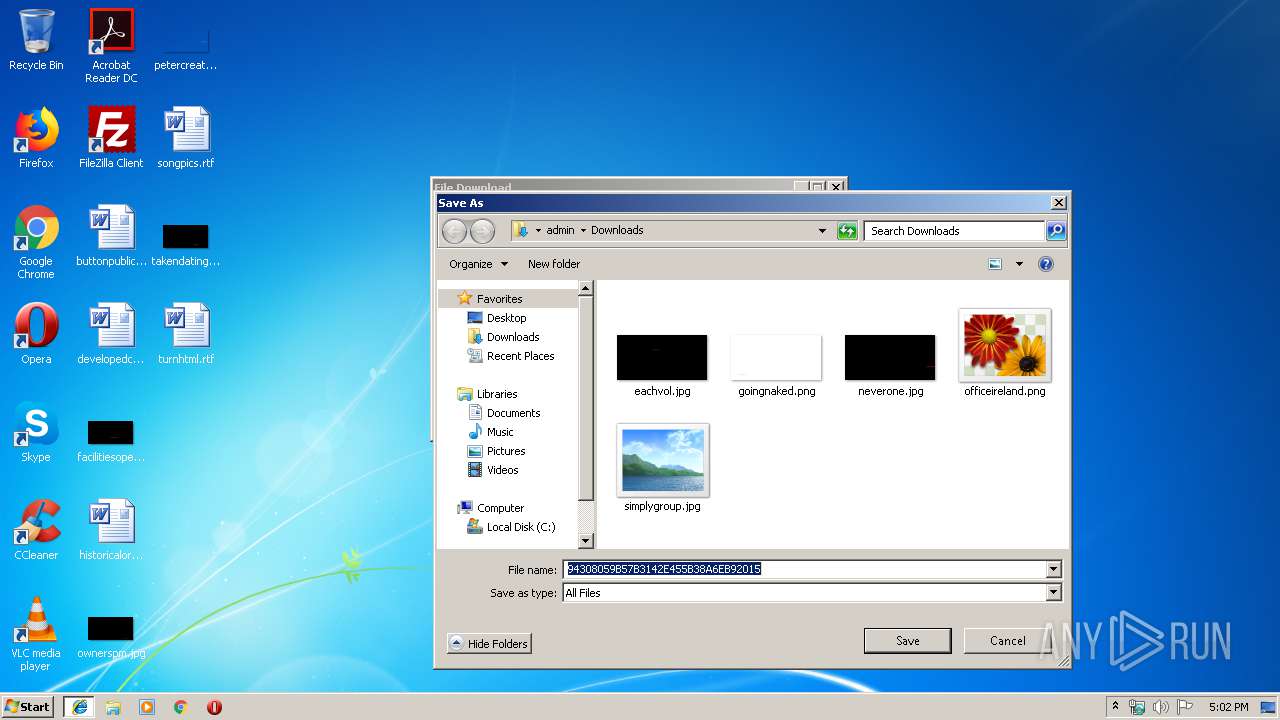
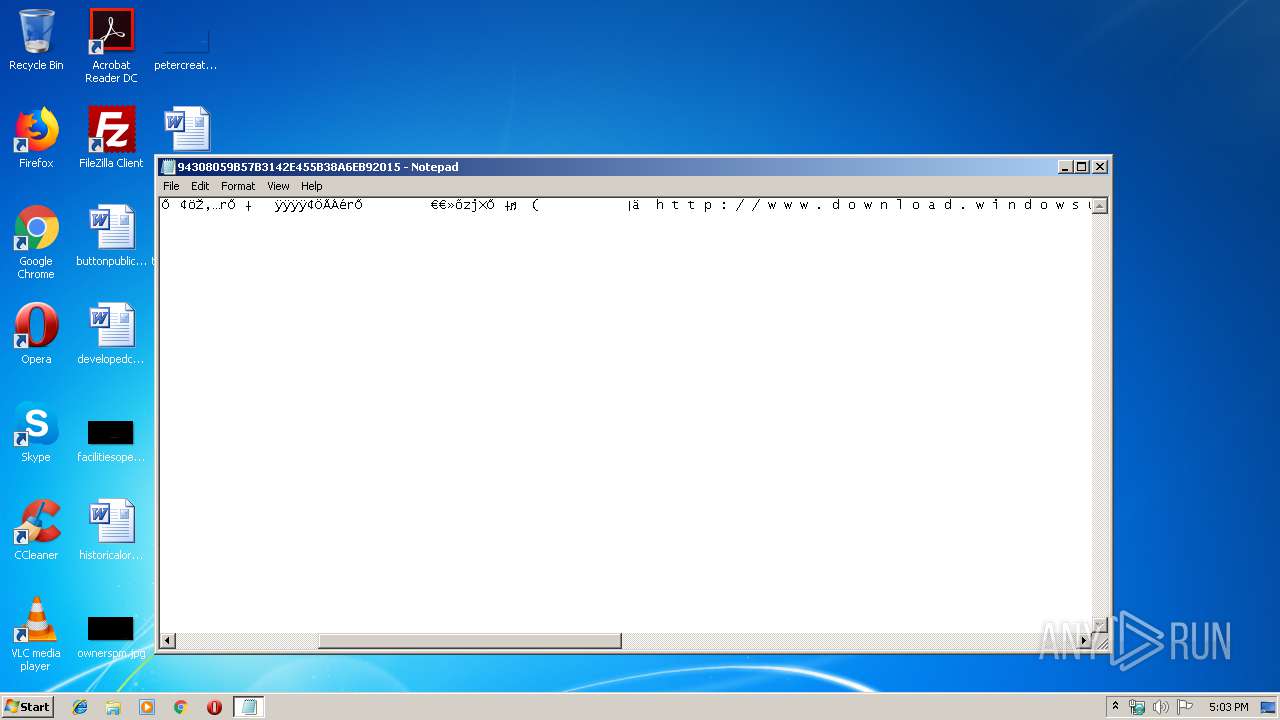
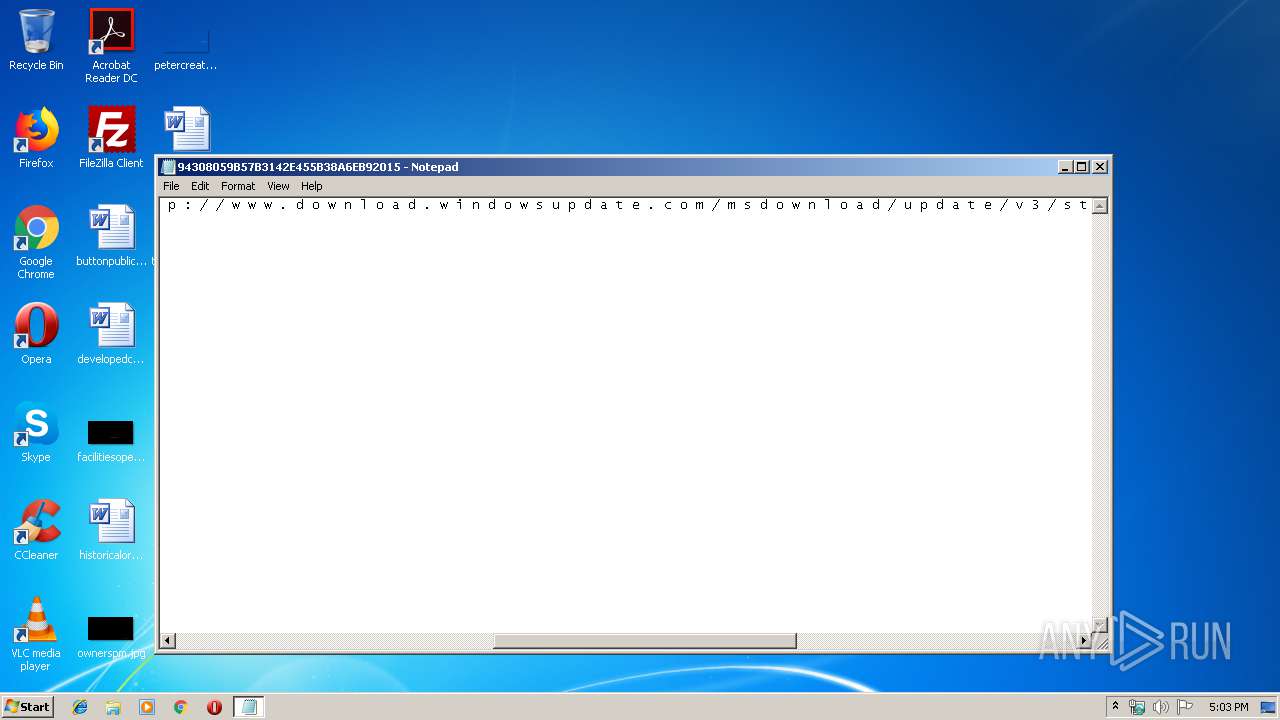
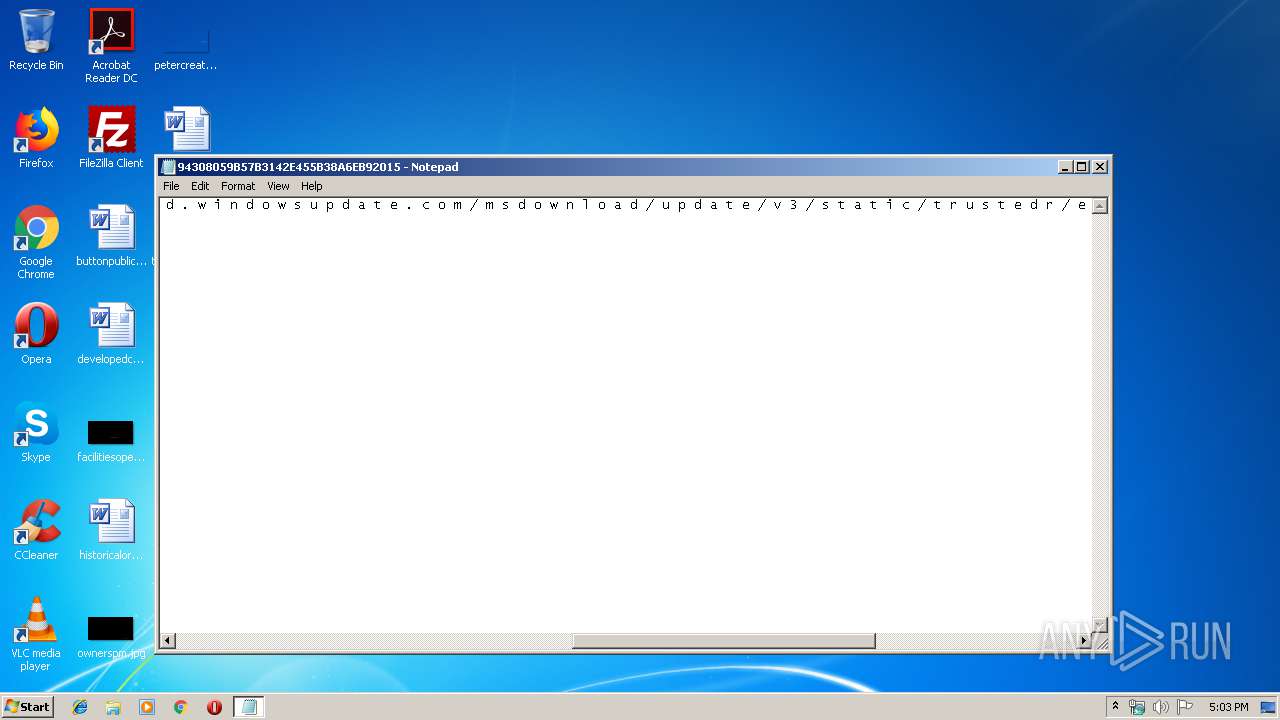
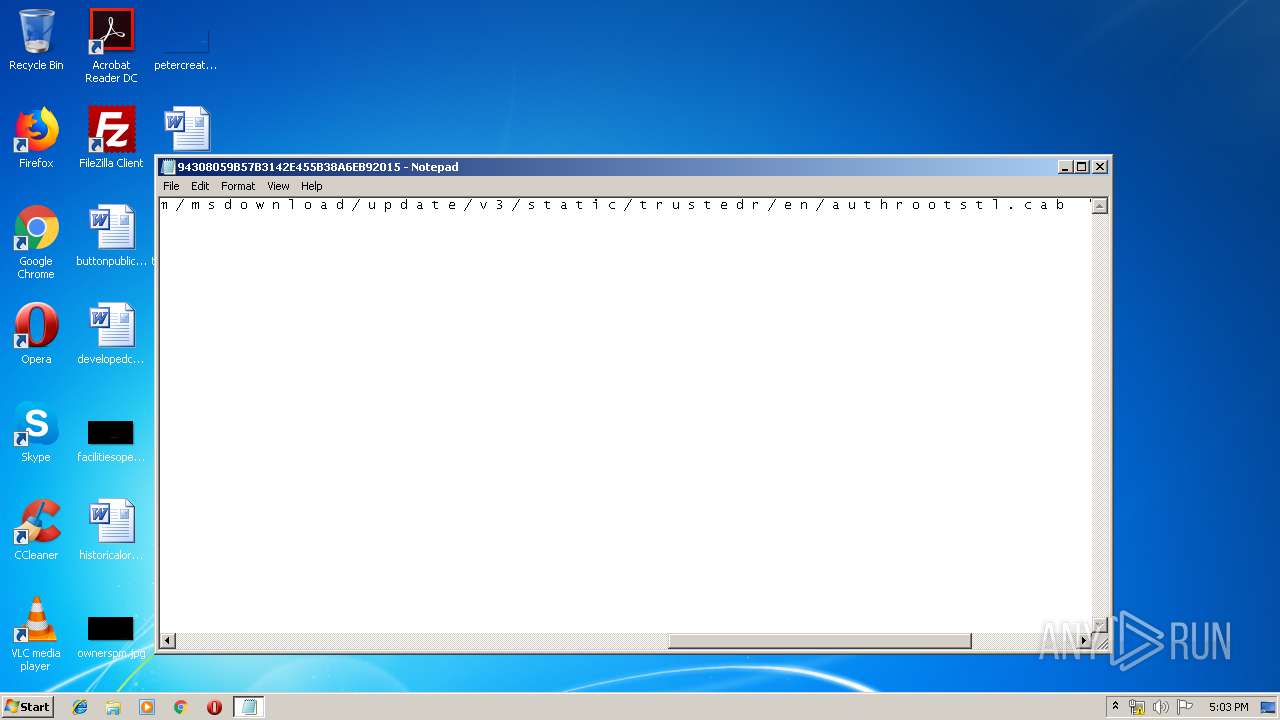
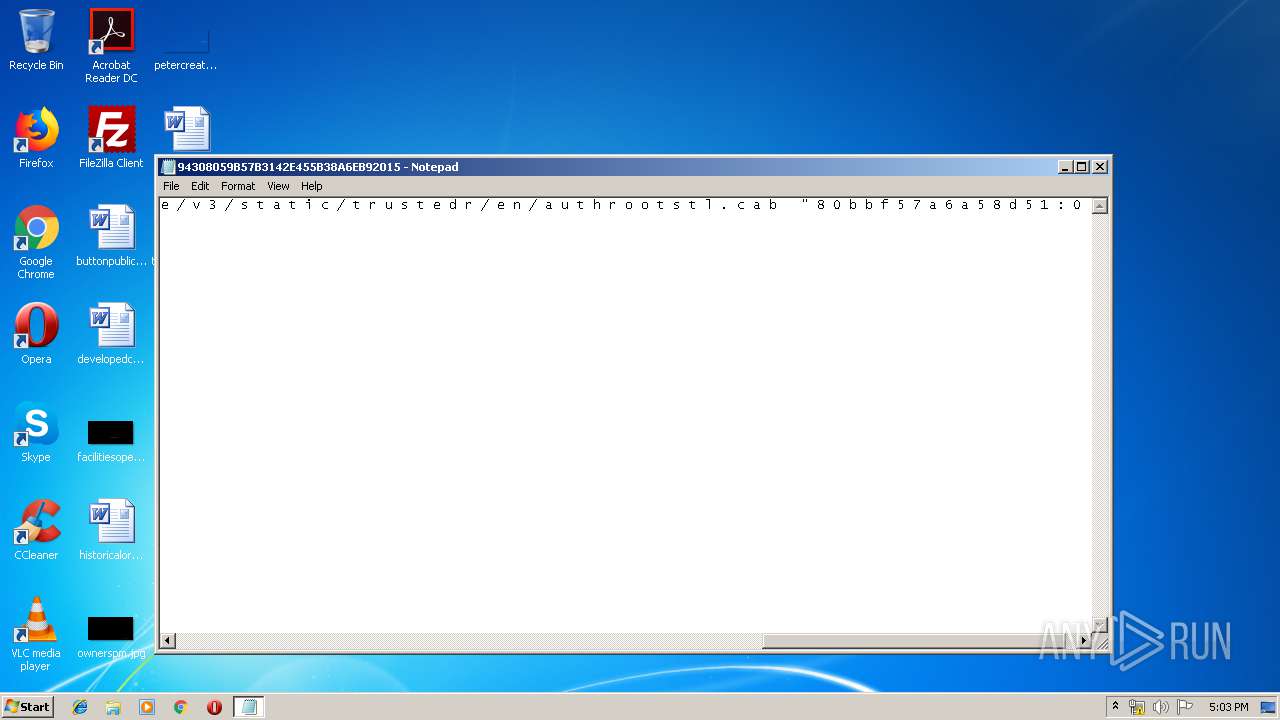
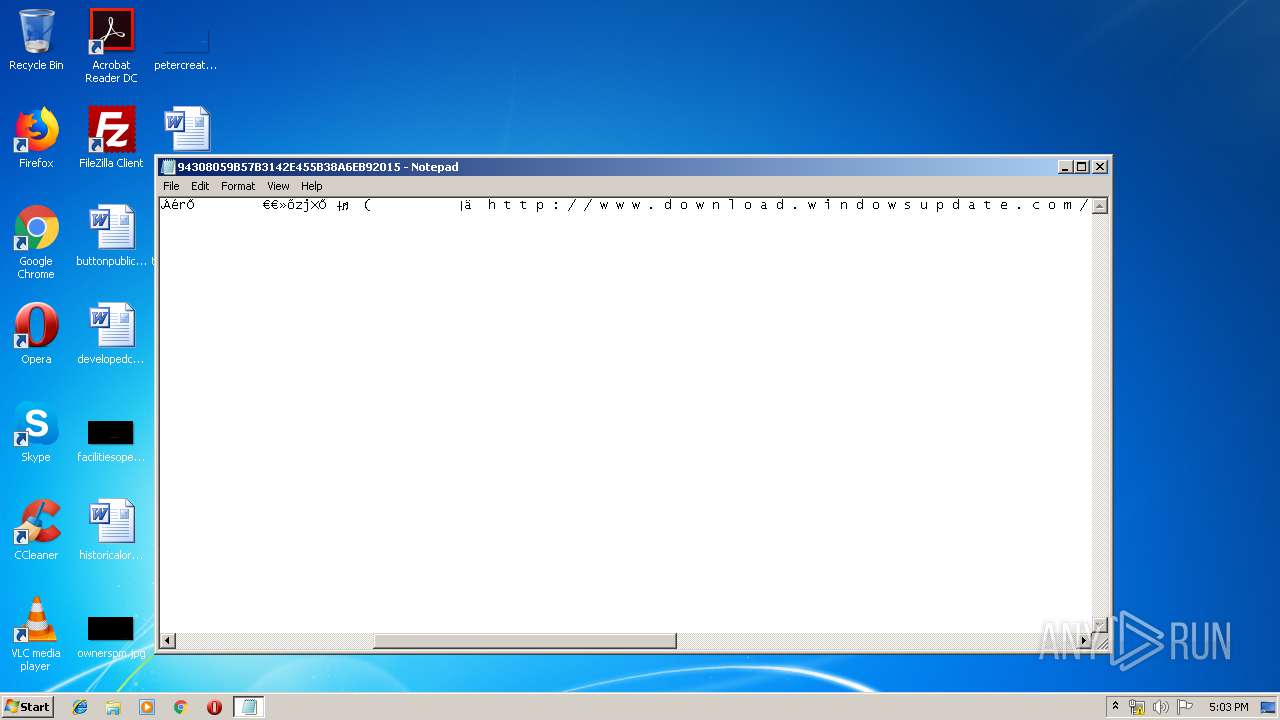
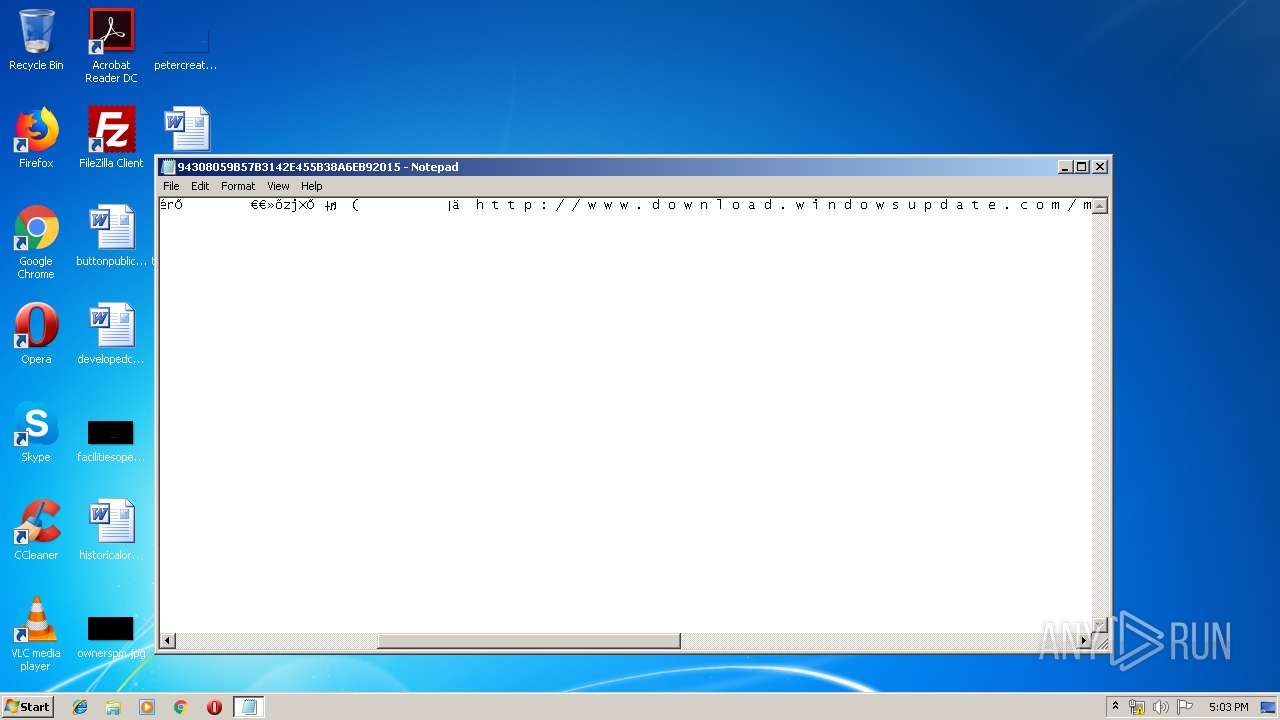
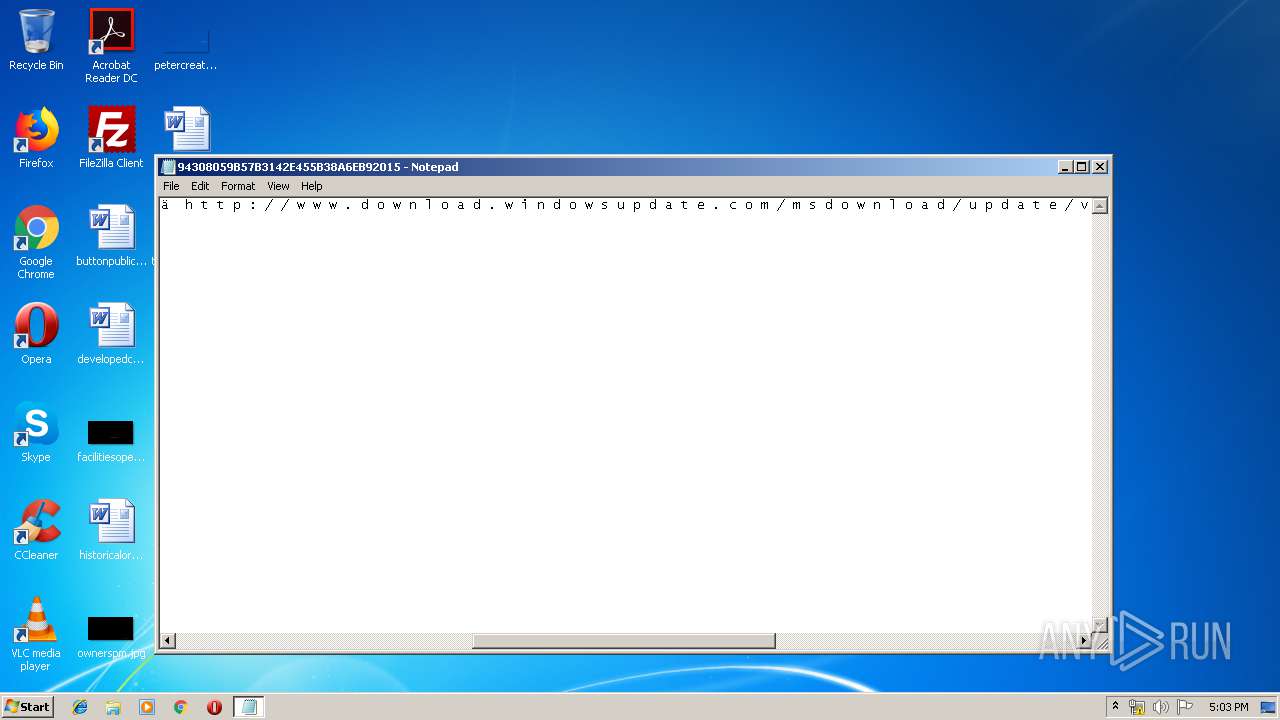
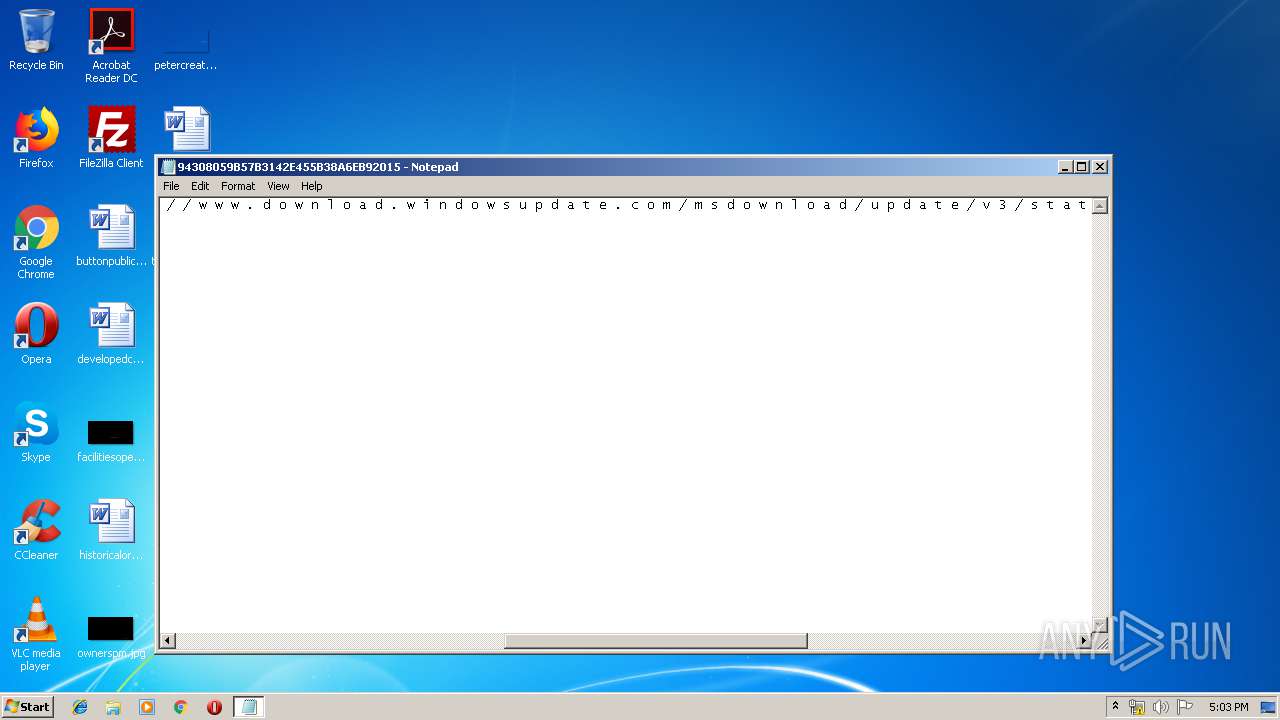
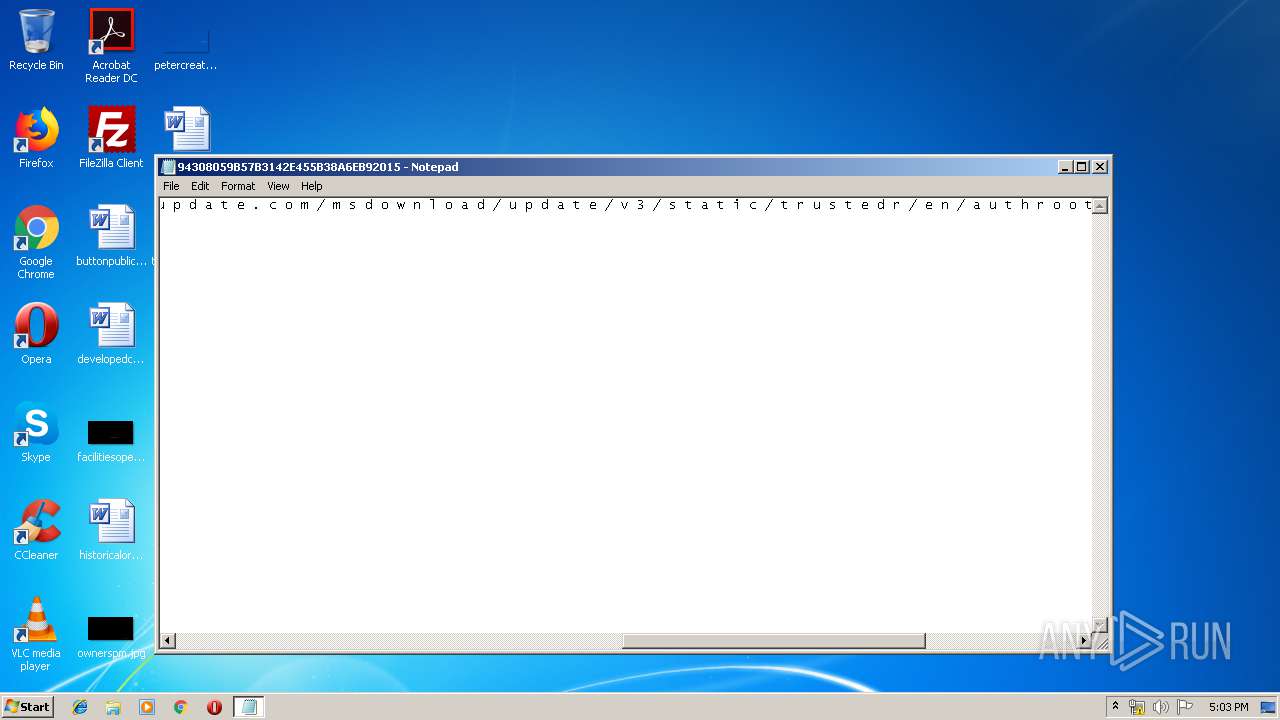
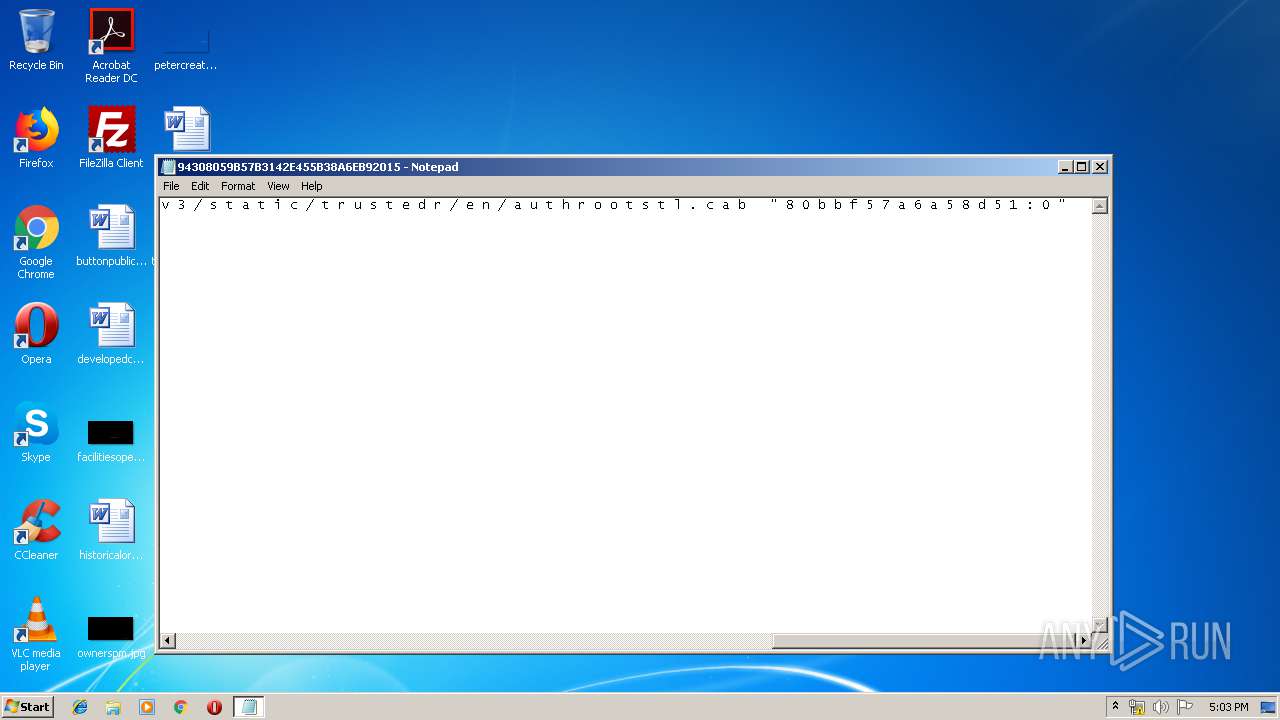
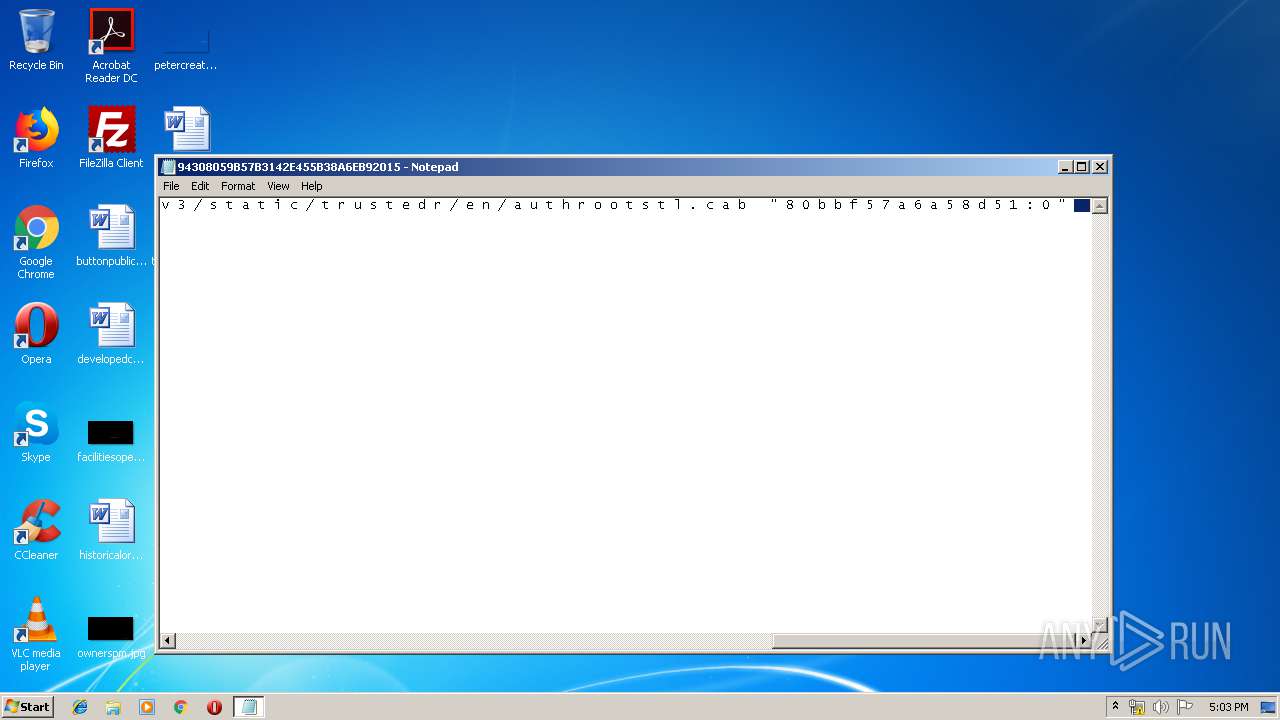
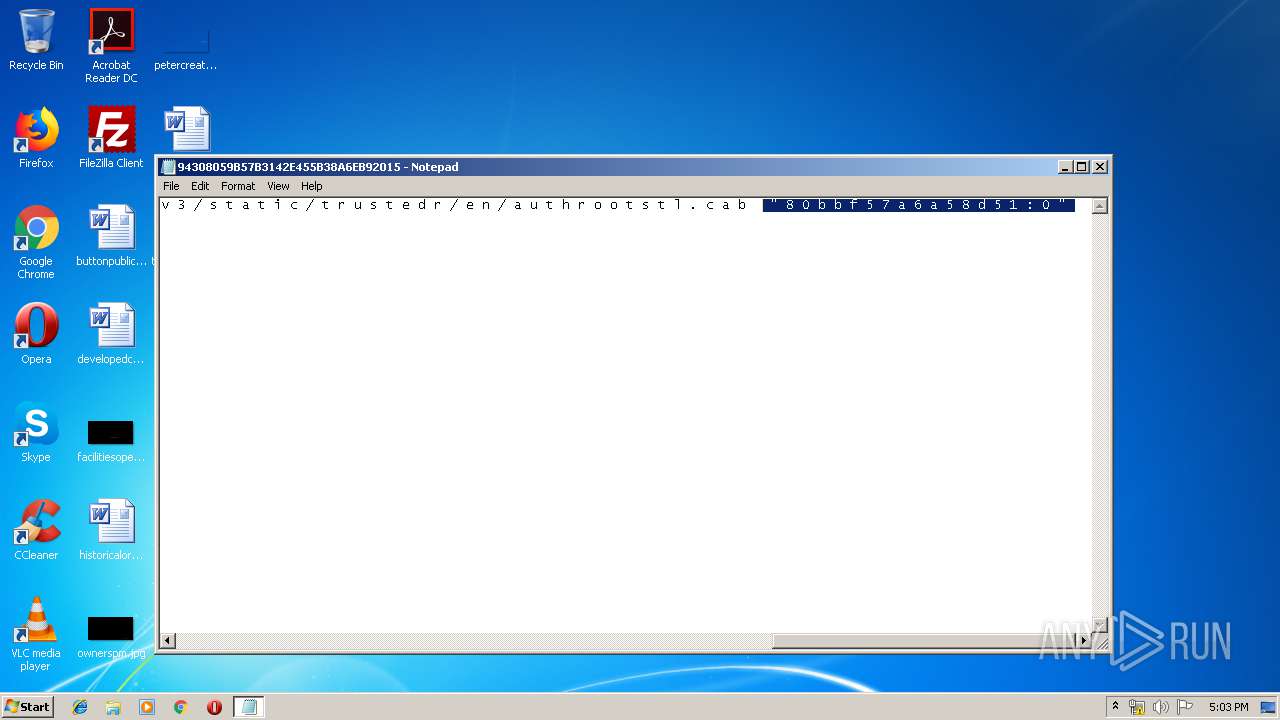
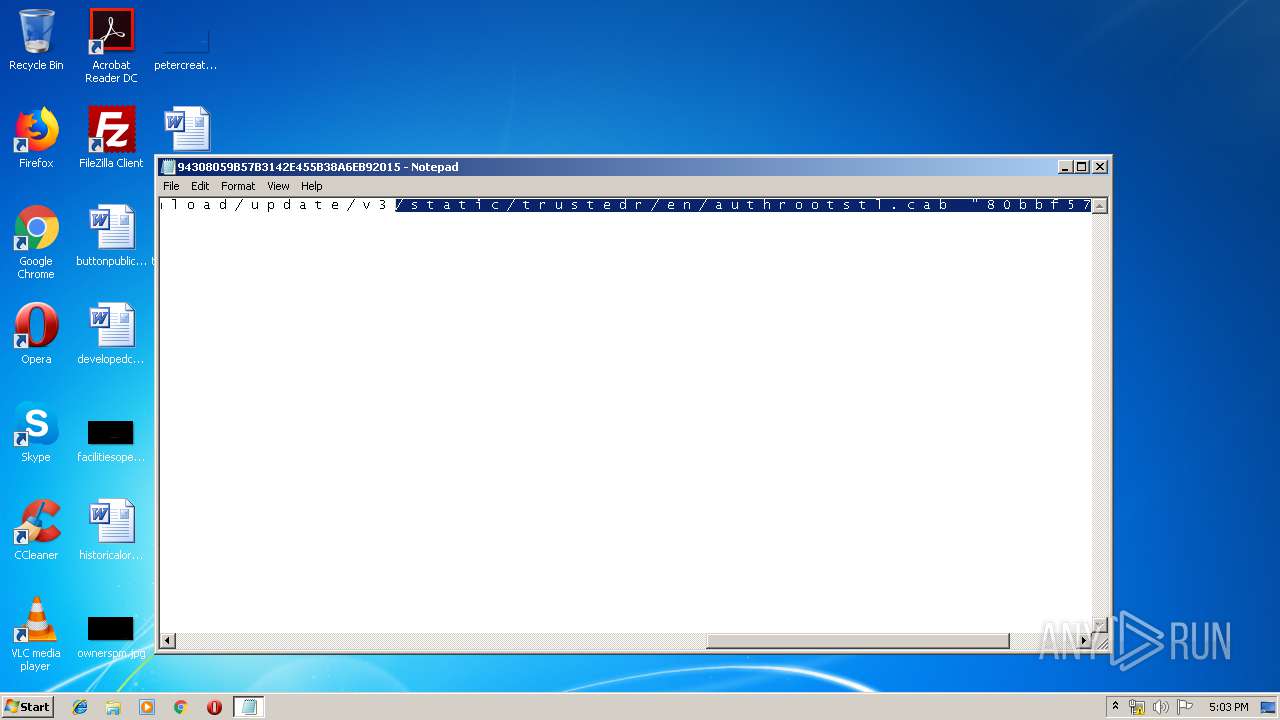
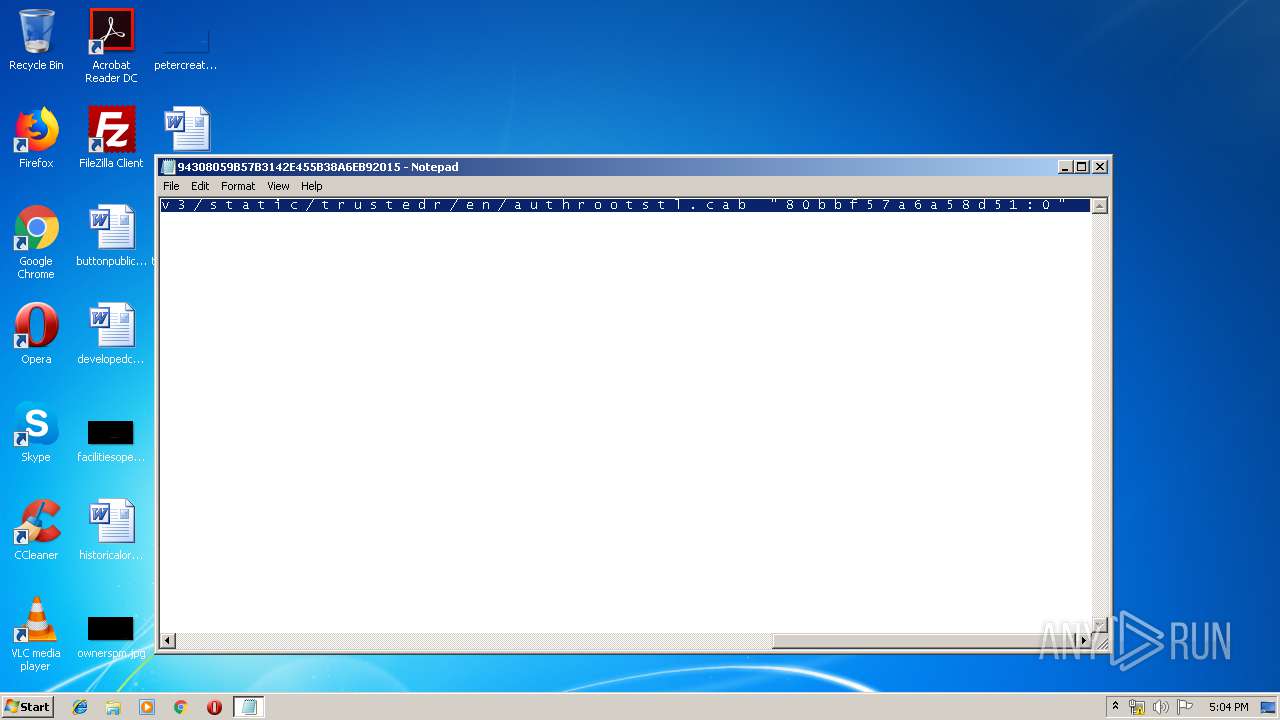
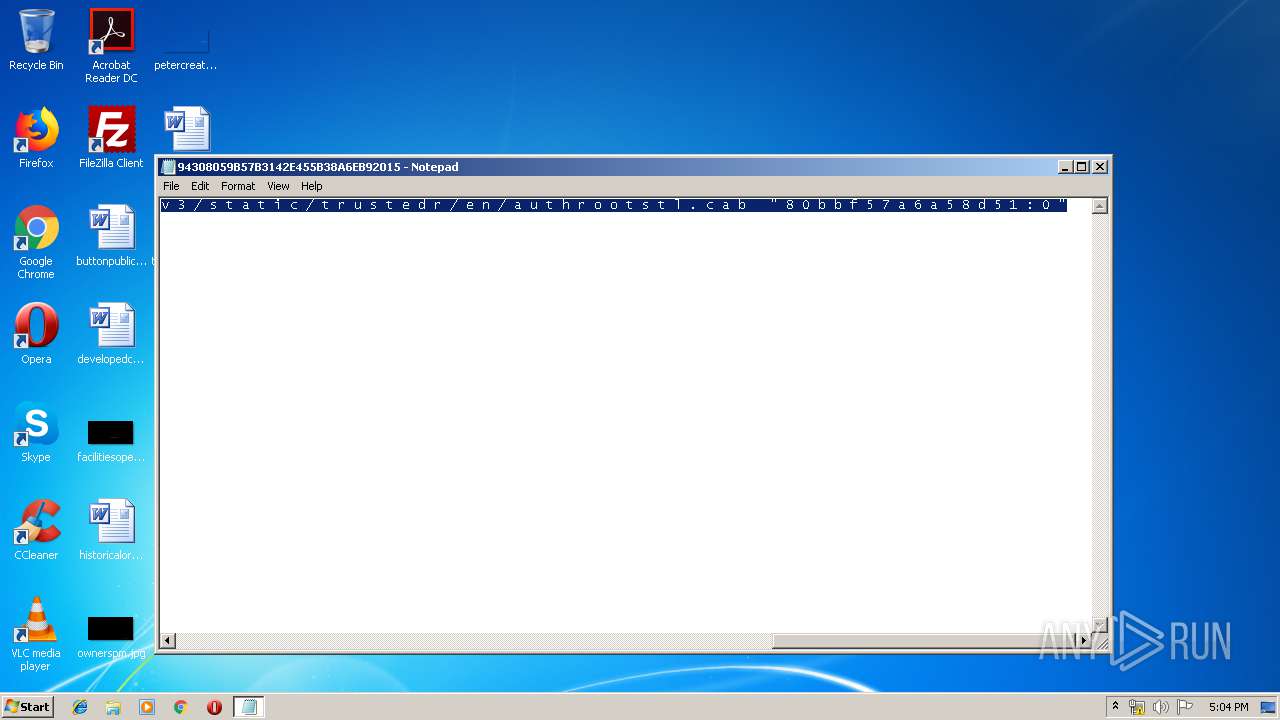
| File name: | C:\Windows\system32\config\systemprofile\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\94308059B57B3142E455B38A6EB92015 |
| Full analysis: | https://app.any.run/tasks/00a66d93-8093-40c8-9923-6ee49e1bdfdc |
| Verdict: | No threats detected |
| Analysis date: | September 17, 2019, 16:02:05 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/octet-stream |
| File info: | data |
| MD5: | DF6CC6413633512EA7546648D79D7390 |
| SHA1: | 32389EE0A3D5B6E83B0653C2B71EE5A18B02C8EC |
| SHA256: | 82497427CF7DED78D132D8B3E89B386EEF26510E8E21143FB5D42E5246CFE0F2 |
| SSDEEP: | 6:kKtMl6MBkqJSw8xq3sb8W4Y+SkQlPlEGYRMY9z+4KlDA3RUej6aUt:lZepSw8c3E8WokPlE99SNxAhUe7Ut |
MALICIOUS
No malicious indicators.SUSPICIOUS
Starts Internet Explorer
- rundll32.exe (PID: 3572)
Uses RUNDLL32.EXE to load library
- iexplore.exe (PID: 3244)
INFO
Reads Internet Cache Settings
- iexplore.exe (PID: 3244)
- iexplore.exe (PID: 2012)
Manual execution by user
- iexplore.exe (PID: 3172)
Application launched itself
- iexplore.exe (PID: 2368)
- iexplore.exe (PID: 3172)
Changes internet zones settings
- iexplore.exe (PID: 2368)
- iexplore.exe (PID: 3172)
Creates files in the user directory
- iexplore.exe (PID: 2012)
Reads internet explorer settings
- iexplore.exe (PID: 2012)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
42
Monitored processes
7
Malicious processes
0
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 2012 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:3172 CREDAT:71937 | C:\Program Files\Internet Explorer\iexplore.exe | iexplore.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Internet Explorer Exit code: 0 Version: 8.00.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2368 | "C:\Program Files\Internet Explorer\iexplore.exe" C:\Users\admin\AppData\Local\Temp\94308059B57B3142E455B38A6EB92015 | C:\Program Files\Internet Explorer\iexplore.exe | rundll32.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Internet Explorer Exit code: 1 Version: 8.00.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3172 | "C:\Program Files\Internet Explorer\iexplore.exe" | C:\Program Files\Internet Explorer\iexplore.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Internet Explorer Exit code: 0 Version: 8.00.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3244 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:2368 CREDAT:79873 | C:\Program Files\Internet Explorer\iexplore.exe | — | iexplore.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Internet Explorer Exit code: 0 Version: 8.00.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
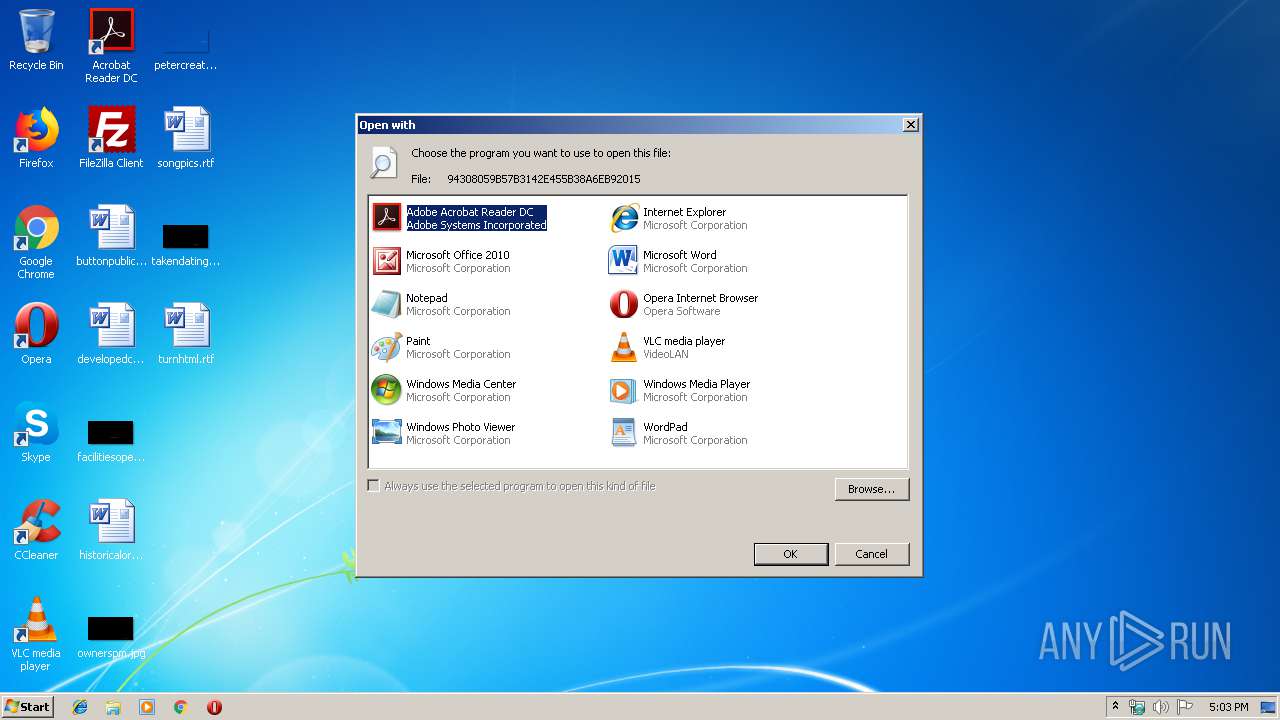
| 3572 | "C:\Windows\system32\rundll32.exe" C:\Windows\system32\shell32.dll,OpenAs_RunDLL C:\Users\admin\AppData\Local\Temp\94308059B57B3142E455B38A6EB92015 | C:\Windows\system32\rundll32.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3600 | "C:\Windows\system32\rundll32.exe" C:\Windows\system32\shell32.dll,OpenAs_RunDLL C:\Users\admin\Downloads\94308059B57B3142E455B38A6EB92015 | C:\Windows\system32\rundll32.exe | — | iexplore.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3924 | "C:\Windows\system32\NOTEPAD.EXE" C:\Users\admin\Downloads\94308059B57B3142E455B38A6EB92015 | C:\Windows\system32\NOTEPAD.EXE | — | rundll32.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Notepad Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
2 209
Read events
1 905
Write events
299
Delete events
5
Modification events
| (PID) Process: | (3572) rundll32.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\MuiCache |
| Operation: | write | Name: | C:\Windows\system32\NOTEPAD.EXE |
Value: Notepad | |||
| (PID) Process: | (3572) rundll32.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\MuiCache |
| Operation: | write | Name: | C:\PROGRA~1\MICROS~1\Office14\OIS.EXE |
Value: Microsoft Office 2010 | |||
| (PID) Process: | (3572) rundll32.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\MuiCache |
| Operation: | write | Name: | C:\Program Files\Microsoft Office\Office14\WINWORD.EXE |
Value: Microsoft Word | |||
| (PID) Process: | (3572) rundll32.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 0 | |||
| (PID) Process: | (3572) rundll32.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 1 | |||
| (PID) Process: | (3572) rundll32.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\72\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (2368) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Main |
| Operation: | write | Name: | CompatibilityFlags |
Value: 0 | |||
| (PID) Process: | (2368) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 0 | |||
| (PID) Process: | (2368) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 1 | |||
| (PID) Process: | (2368) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\Zones |
| Operation: | write | Name: | SecuritySafe |
Value: 1 | |||
Executable files
0
Suspicious files
2
Text files
24
Unknown types
7
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2368 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\~DF75728EECAEFAC43F.TMP | — | |
MD5:— | SHA256:— | |||
| 2368 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\LH043OAM\favicon[1].ico | — | |
MD5:— | SHA256:— | |||
| 2368 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\Internet Explorer\Services\search_{0633EE93-D776-472f-A0FF-E1416B8B2E3A}.ico | — | |
MD5:— | SHA256:— | |||
| 2368 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\~DF12F909E453AB2268.TMP | — | |
MD5:— | SHA256:— | |||
| 2368 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Internet Explorer\Recovery\Active\RecoveryStore.{93FA3A7F-D964-11E9-B86F-5254004A04AF}.dat | — | |
MD5:— | SHA256:— | |||
| 3172 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\Internet Explorer\Services\search_{0633EE93-D776-472f-A0FF-E1416B8B2E3A}.ico | — | |
MD5:— | SHA256:— | |||
| 2012 | iexplore.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Cookies\Low\admin@bing[2].txt | — | |
MD5:— | SHA256:— | |||
| 2012 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\3JA71AGY\search[1].txt | — | |
MD5:— | SHA256:— | |||
| 2368 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Internet Explorer\Recovery\Active\{93FA3A80-D964-11E9-B86F-5254004A04AF}.dat | binary | |
MD5:— | SHA256:— | |||
| 3244 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\History\History.IE5\MSHist012019091720190918\index.dat | dat | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
22
TCP/UDP connections
12
DNS requests
7
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
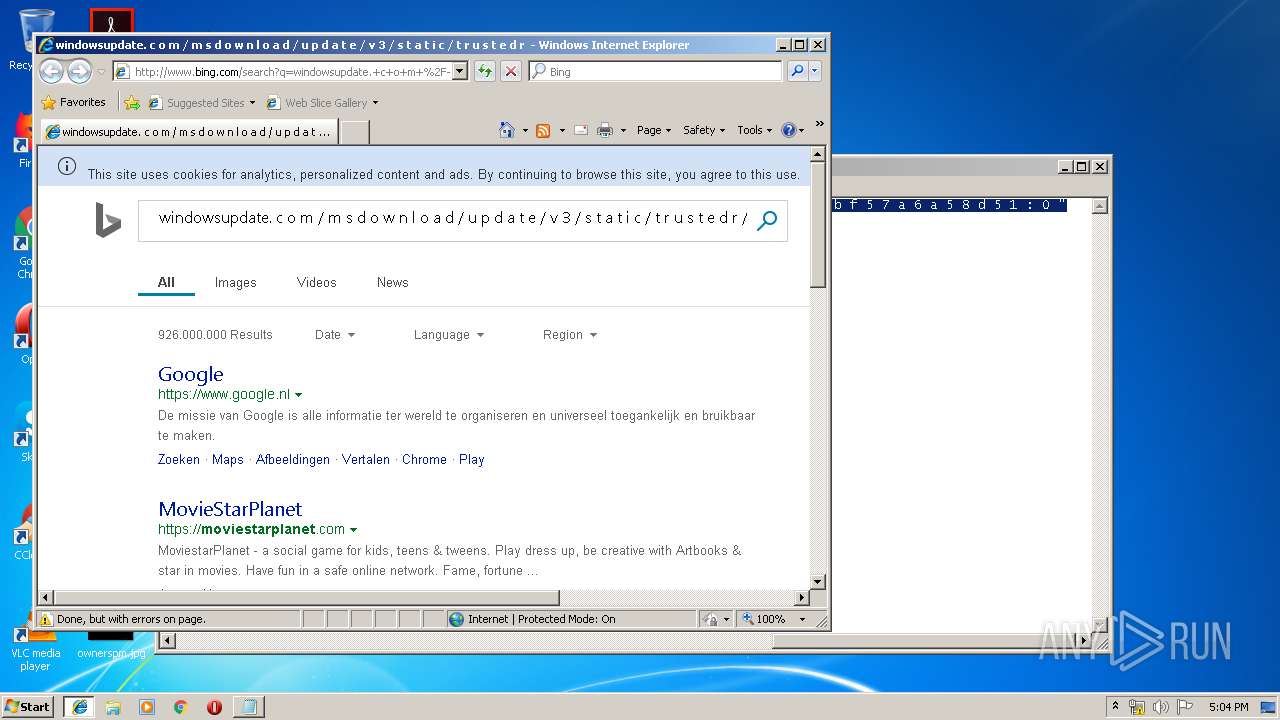
2012 | iexplore.exe | GET | 200 | 204.79.197.200:80 | http://www.bing.com/rs/30/27/cj,nj/4c7364c5/40e1b425.js | US | text | 816 b | whitelisted |
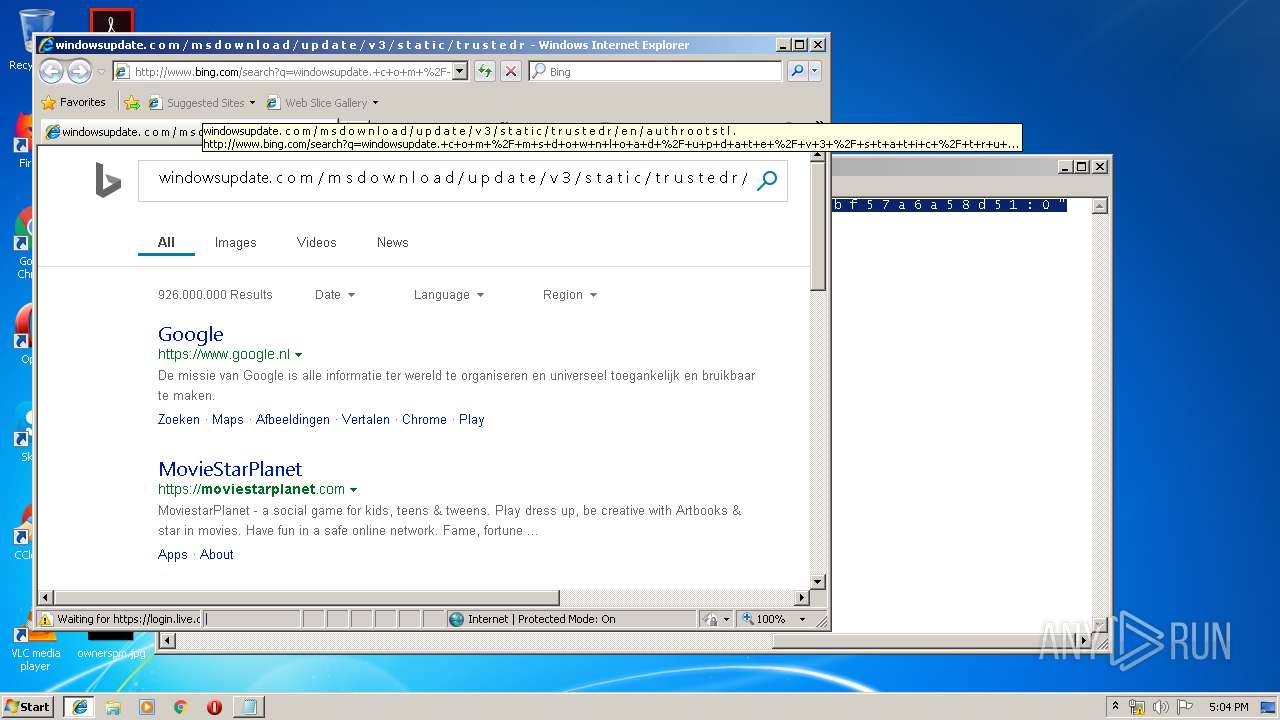
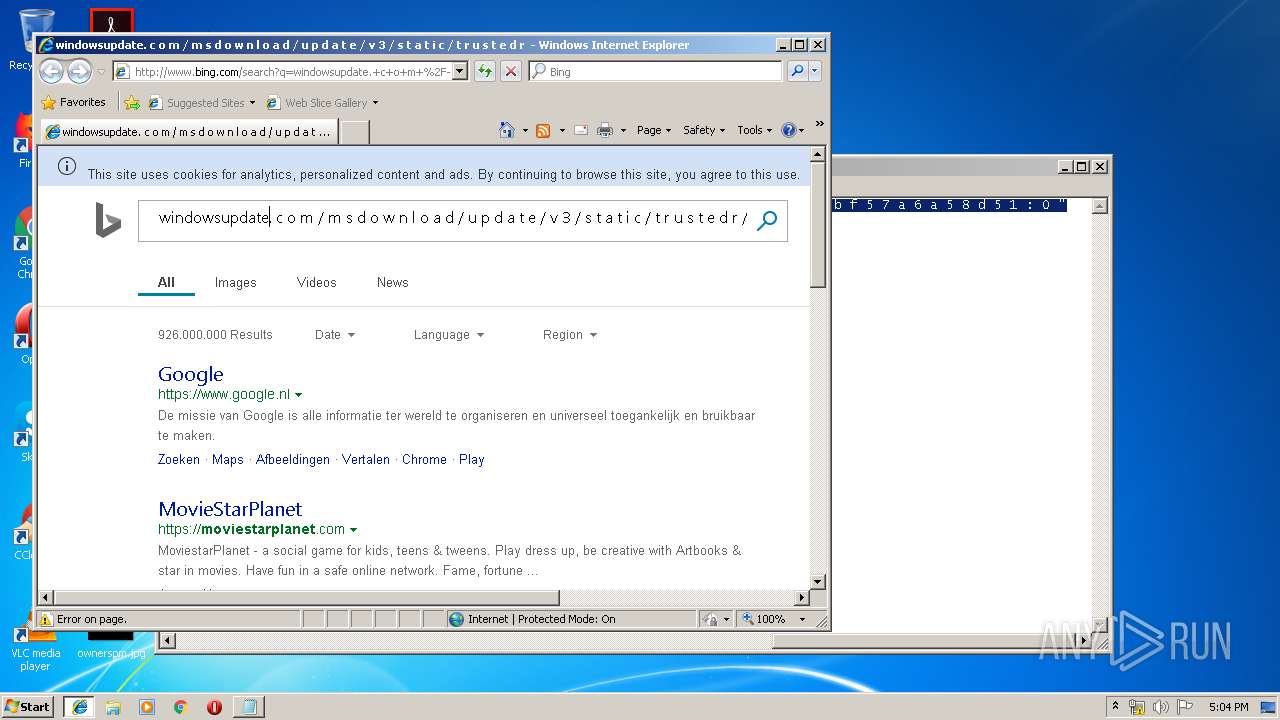
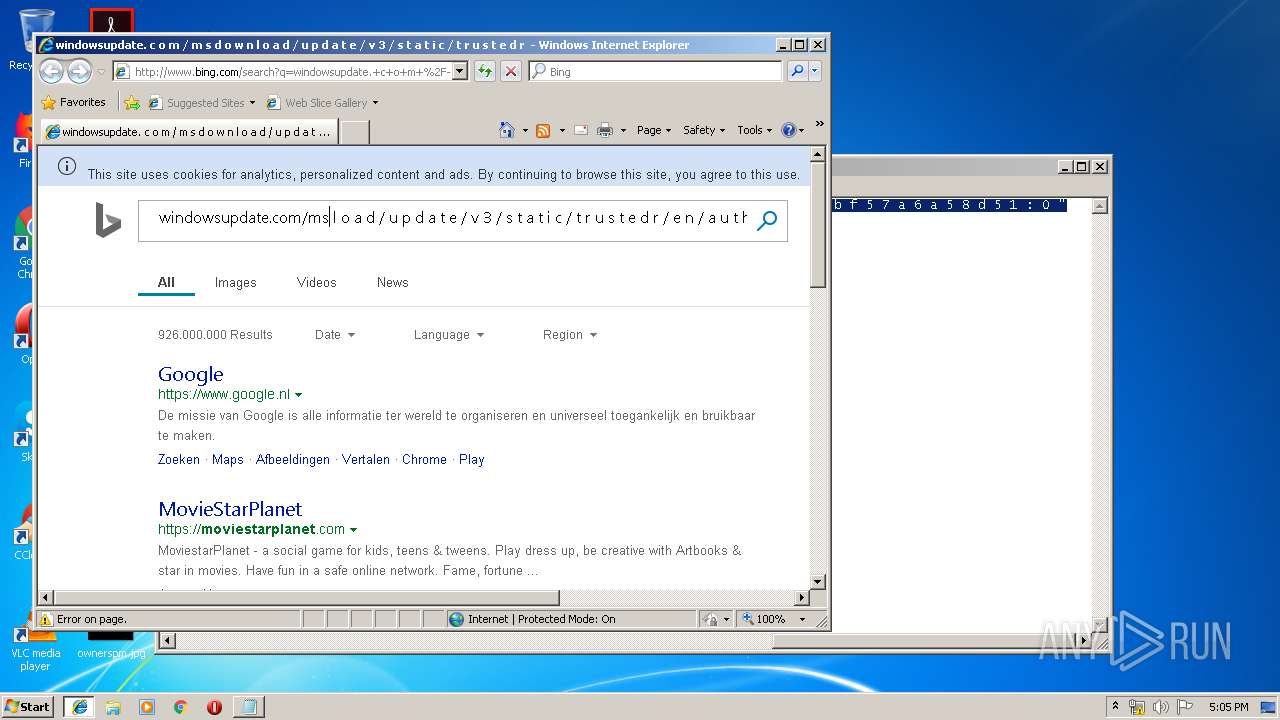
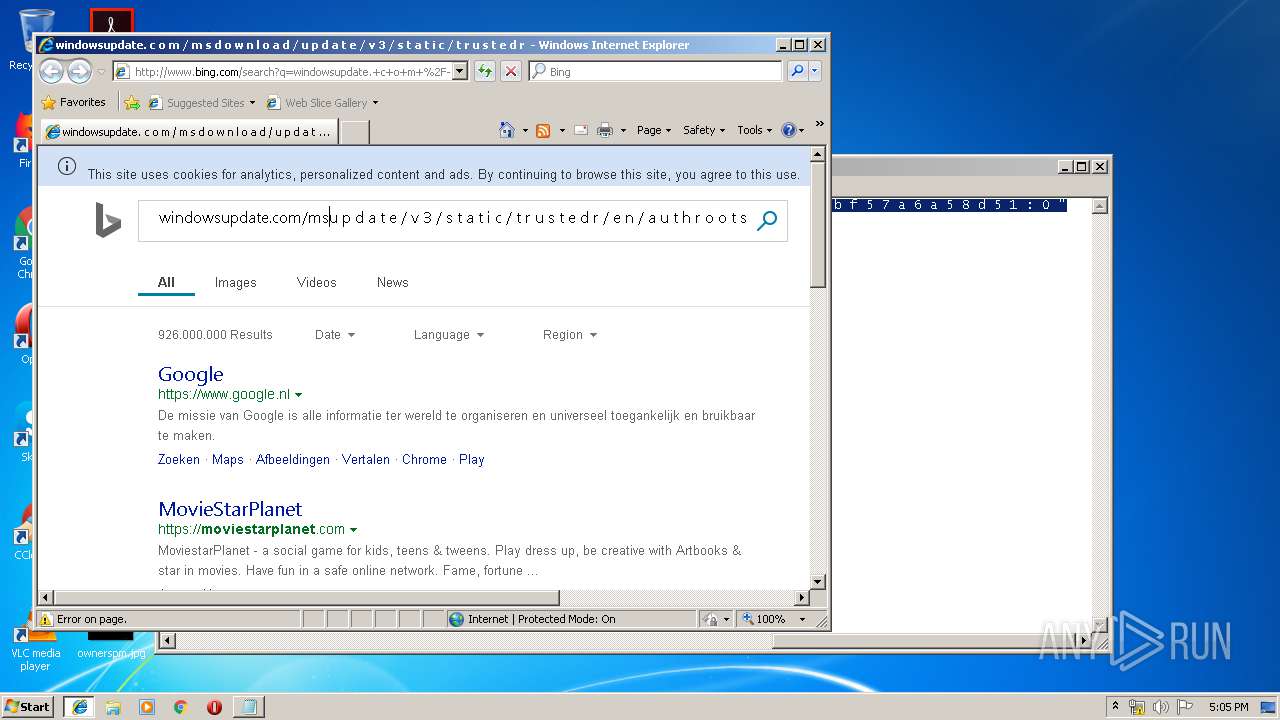
2012 | iexplore.exe | GET | 200 | 204.79.197.200:80 | http://www.bing.com/search?q=windowsupdate.+c+o+m+%2F+m+s+d+o+w+n+l+o+a+d+%2F+u+p+d+a+t+e+%2F+v+3+%2F+s+t+a+t+i+c+%2F+t+r+u+s+t+e+d+r+%2F+e+n+%2F+a+u+t+h+r+o+o+t+s+t+l+.+c+a+b+++%22+8+0+b+b+f+5+7+a+6+a+5+8+d+5+1+%3A+0+%22&src=IE-SearchBox&FORM=IE8SRC | US | html | 32.6 Kb | whitelisted |
2012 | iexplore.exe | GET | 200 | 204.79.197.200:80 | http://www.bing.com/rs/5d/2C/cj,nj/08abbb2f/e177b199.js | US | text | 2.86 Kb | whitelisted |
2012 | iexplore.exe | GET | 200 | 204.79.197.200:80 | http://www.bing.com/sa/simg/SharedSpriteDesktopRewards_022118.png | US | image | 5.73 Kb | whitelisted |
2012 | iexplore.exe | GET | 200 | 204.79.197.200:80 | http://www.bing.com/rs/6p/5f/cj,nj/dd882357/b8881a70.js | US | text | 1.77 Kb | whitelisted |
2012 | iexplore.exe | GET | 200 | 204.79.197.200:80 | http://www.bing.com/fd/ls/l?IG=B08CAE530870456C8436776729DB0FFC&CID=15DC2C0C43256073082A21D6421061E6&Type=Event.ClientInst&DATA=[{"T":"CI.GetError","FID":"CI","Name":"JSGetError","Text":"%27SVGElement%27%20is%20undefined","Meta":"http%3A//www.bing.com/search%3Fq%3Dwindowsupdate.+c+o+m+%252F+m+s+d+o+w+n+l+o+a+d+%252F+u+p+d+a+t+e+%252F+v+3+%252F+s+t+a+t+i+c+%252F+t+r+u+s+t+e+d+r+%252F+e+n+%252F+a+u+t+h+r+o+o+t+s+t+l+.+c+a+b+++%2522+8+0+b+b+f+5+7+a+6+a+5+8+d+5+1+%253A+0+%2522%26src%3DIE-SearchBox%26FORM%3DIE8SRC","Line":9132351,"Char":%20undefined}] | US | compressed | 816 b | whitelisted |
2012 | iexplore.exe | GET | 200 | 204.79.197.222:80 | http://ebc0b645c68af2af3aa1d7007f485b04.clo.footprintdns.com/apc/trans.gif | US | image | 43 b | suspicious |
2012 | iexplore.exe | GET | 200 | 13.107.18.254:80 | http://53946d9b9155d8719d358bc44f488ff7.clo.footprintdns.com/apc/trans.gif | US | image | 43 b | suspicious |
2012 | iexplore.exe | GET | 200 | 204.79.197.222:80 | http://a56218aeeb4b8de514bbd1c01c482df7.clo.footprintdns.com/apc/trans.gif | US | image | 43 b | suspicious |
2012 | iexplore.exe | GET | 200 | 204.79.197.222:80 | http://ebc0b645c68af2af3aa1d7007f485b04.clo.footprintdns.com/apc/trans.gif?ebc0b645c68af2af3aa1d7007f485b04 | US | image | 43 b | suspicious |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2368 | iexplore.exe | 204.79.197.200:80 | www.bing.com | Microsoft Corporation | US | whitelisted |
2012 | iexplore.exe | 204.79.197.200:80 | www.bing.com | Microsoft Corporation | US | whitelisted |
2012 | iexplore.exe | 40.90.23.208:443 | login.live.com | Microsoft Corporation | US | unknown |
2012 | iexplore.exe | 204.79.197.200:443 | www.bing.com | Microsoft Corporation | US | whitelisted |
2012 | iexplore.exe | 13.107.18.254:80 | 53946d9b9155d8719d358bc44f488ff7.clo.footprintdns.com | Microsoft Corporation | US | whitelisted |
2012 | iexplore.exe | 204.79.197.222:80 | ebc0b645c68af2af3aa1d7007f485b04.clo.footprintdns.com | Microsoft Corporation | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
www.bing.com |
| whitelisted |
login.live.com |
| whitelisted |
ebc0b645c68af2af3aa1d7007f485b04.clo.footprintdns.com |
| suspicious |
a56218aeeb4b8de514bbd1c01c482df7.clo.footprintdns.com |
| suspicious |
53946d9b9155d8719d358bc44f488ff7.clo.footprintdns.com |
| suspicious |
fp.msedge.net |
| whitelisted |