| URL: | http://www.harlemrenaissancecentennial.org/En_us/Details/122018/file-0860656557577421.doc |
| Full analysis: | https://app.any.run/tasks/d78c813f-715c-4919-b320-7280f4918d10 |
| Verdict: | Malicious activity |
| Analysis date: | December 14, 2018, 20:33:55 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MD5: | B19A5409A9520743C134AB48197CA0CE |
| SHA1: | 687FC3F62173077B2162B8A73E5EDE78F1E101EF |
| SHA256: | 823234A732A137A083DFD263E98C9BD1A36E577DE0ACD30DA6C0284271644970 |
| SSDEEP: | 3:N1KJS4x8XWELFAtt7siMnOXVEKQJAIVdKjHXyd:Cc4iL6DI/OXpQJAoITid |
MALICIOUS
No malicious indicators.SUSPICIOUS
No suspicious indicators.INFO
Application launched itself
- firefox.exe (PID: 3544)
Reads CPU info
- firefox.exe (PID: 3188)
- firefox.exe (PID: 3544)
- firefox.exe (PID: 3328)
- firefox.exe (PID: 4040)
Creates files in the user directory
- firefox.exe (PID: 3544)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
36
Monitored processes
5
Malicious processes
0
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 3188 | "C:\Program Files\Mozilla Firefox\firefox.exe" -contentproc --channel="3544.0.1741005666\853275442" -childID 1 -isForBrowser -prefsHandle 1404 -prefsLen 8310 -schedulerPrefs 0001,2 -greomni "C:\Program Files\Mozilla Firefox\omni.ja" -appomni "C:\Program Files\Mozilla Firefox\browser\omni.ja" -appdir "C:\Program Files\Mozilla Firefox\browser" - 3544 "\\.\pipe\gecko-crash-server-pipe.3544" 1492 tab | C:\Program Files\Mozilla Firefox\firefox.exe | firefox.exe | ||||||||||||
User: admin Company: Mozilla Corporation Integrity Level: LOW Description: Firefox Exit code: 0 Version: 61.0.2 Modules
| |||||||||||||||
| 3328 | "C:\Program Files\Mozilla Firefox\firefox.exe" -contentproc --channel="3544.12.1502055242\247943358" -childID 3 -isForBrowser -prefsHandle 2356 -prefsLen 12017 -schedulerPrefs 0001,2 -greomni "C:\Program Files\Mozilla Firefox\omni.ja" -appomni "C:\Program Files\Mozilla Firefox\browser\omni.ja" -appdir "C:\Program Files\Mozilla Firefox\browser" - 3544 "\\.\pipe\gecko-crash-server-pipe.3544" 2892 tab | C:\Program Files\Mozilla Firefox\firefox.exe | firefox.exe | ||||||||||||
User: admin Company: Mozilla Corporation Integrity Level: LOW Description: Firefox Exit code: 0 Version: 61.0.2 Modules
| |||||||||||||||
| 3544 | "C:\Program Files\Mozilla Firefox\firefox.exe" http://www.harlemrenaissancecentennial.org/En_us/Details/122018/file-0860656557577421.doc | C:\Program Files\Mozilla Firefox\firefox.exe | explorer.exe | ||||||||||||
User: admin Company: Mozilla Corporation Integrity Level: MEDIUM Description: Firefox Exit code: 0 Version: 61.0.2 Modules
| |||||||||||||||
| 4016 | "C:\Program Files\Mozilla Firefox\pingsender.exe" https://incoming.telemetry.mozilla.org/submit/telemetry/ae84e1ed-1bc5-472d-8b03-e39491b05772/main/Firefox/61.0.2/release/20180807170231?v=4 C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\qldyz51w.default\saved-telemetry-pings\ae84e1ed-1bc5-472d-8b03-e39491b05772 | C:\Program Files\Mozilla Firefox\pingsender.exe | firefox.exe | ||||||||||||
User: admin Company: Mozilla Foundation Integrity Level: MEDIUM Exit code: 0 Version: 61.0.2 Modules
| |||||||||||||||
| 4040 | "C:\Program Files\Mozilla Firefox\firefox.exe" -contentproc --channel="3544.6.1062583262\1374390218" -childID 2 -isForBrowser -prefsHandle 2540 -prefsLen 11442 -schedulerPrefs 0001,2 -greomni "C:\Program Files\Mozilla Firefox\omni.ja" -appomni "C:\Program Files\Mozilla Firefox\browser\omni.ja" -appdir "C:\Program Files\Mozilla Firefox\browser" - 3544 "\\.\pipe\gecko-crash-server-pipe.3544" 2504 tab | C:\Program Files\Mozilla Firefox\firefox.exe | firefox.exe | ||||||||||||
User: admin Company: Mozilla Corporation Integrity Level: LOW Description: Firefox Exit code: 0 Version: 61.0.2 Modules
| |||||||||||||||
Total events
434
Read events
430
Write events
4
Delete events
0
Modification events
| (PID) Process: | (3544) firefox.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings |
| Operation: | write | Name: | ProxyEnable |
Value: 0 | |||
| (PID) Process: | (3544) firefox.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\Connections |
| Operation: | write | Name: | SavedLegacySettings |
Value: 4600000069000000010000000000000000000000000000000000000000000000C0E333BBEAB1D301000000000000000000000000020000001700000000000000FE800000000000007D6CB050D9C573F70B000000000000006D00330032005C004D00530049004D004700330032002E0064006C000100000004AA400014AA4000040000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000002000000C0A8016400000000000000000000000000000000000000000800000000000000805D3F00983740000008000002000000000000600000002060040000B8A94000020000008802000060040000B8A9400004000000F8010000B284000088B64000B84B400043003A000000000000000000000000000000000000000000 | |||
| (PID) Process: | (4016) pingsender.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings |
| Operation: | write | Name: | ProxyEnable |
Value: 0 | |||
| (PID) Process: | (4016) pingsender.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\Connections |
| Operation: | write | Name: | SavedLegacySettings |
Value: 460000006A000000010000000000000000000000000000000000000000000000C0E333BBEAB1D301000000000000000000000000020000001700000000000000FE800000000000007D6CB050D9C573F70B000000000000006D00330032005C004D00530049004D004700330032002E0064006C000100000004AA400014AA4000040000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000002000000C0A8016400000000000000000000000000000000000000000800000000000000805D3F00983740000008000002000000000000600000002060040000B8A94000020000008802000060040000B8A9400004000000F8010000B284000088B64000B84B400043003A000000000000000000000000000000000000000000 | |||
Executable files
0
Suspicious files
68
Text files
22
Unknown types
29
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3544 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\qldyz51w.default\cookies.sqlite-shm | — | |
MD5:— | SHA256:— | |||
| 3544 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\qldyz51w.default\sessionCheckpoints.json.tmp | — | |
MD5:— | SHA256:— | |||
| 3544 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\qldyz51w.default\prefs-1.js | — | |
MD5:— | SHA256:— | |||
| 3544 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\qldyz51w.default\storage\permanent\chrome\idb\3561288849sdhlie.sqlite-shm | — | |
MD5:— | SHA256:— | |||
| 3544 | firefox.exe | C:\Users\admin\AppData\Local\Mozilla\Firefox\Profiles\qldyz51w.default\safebrowsing-updating\allow-flashallow-digest256.pset | — | |
MD5:— | SHA256:— | |||
| 3544 | firefox.exe | C:\Users\admin\AppData\Local\Mozilla\Firefox\Profiles\qldyz51w.default\safebrowsing-updating\allow-flashallow-digest256.sbstore | — | |
MD5:— | SHA256:— | |||
| 3544 | firefox.exe | C:\Users\admin\AppData\Local\Mozilla\Firefox\Profiles\qldyz51w.default\safebrowsing-updating\base-track-digest256.pset | — | |
MD5:— | SHA256:— | |||
| 3544 | firefox.exe | C:\Users\admin\AppData\Local\Mozilla\Firefox\Profiles\qldyz51w.default\safebrowsing-updating\base-track-digest256.sbstore | — | |
MD5:— | SHA256:— | |||
| 3544 | firefox.exe | C:\Users\admin\AppData\Local\Mozilla\Firefox\Profiles\qldyz51w.default\safebrowsing-updating\block-flash-digest256.pset | — | |
MD5:— | SHA256:— | |||
| 3544 | firefox.exe | C:\Users\admin\AppData\Local\Mozilla\Firefox\Profiles\qldyz51w.default\safebrowsing-updating\block-flash-digest256.sbstore | — | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
22
TCP/UDP connections
13
DNS requests
28
Threats
5
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
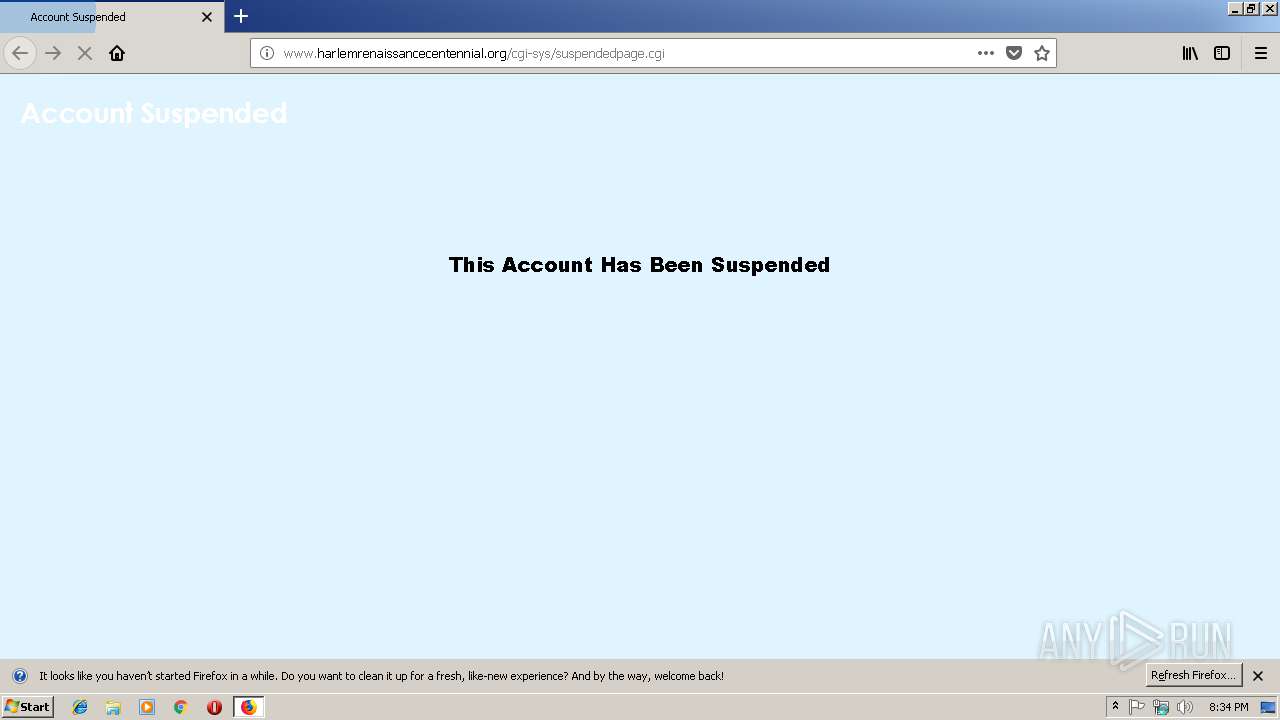
3544 | firefox.exe | GET | 302 | 149.47.131.249:80 | http://www.harlemrenaissancecentennial.org/En_us/Details/122018/file-0860656557577421.doc | US | html | 252 b | malicious |
3544 | firefox.exe | GET | 404 | 149.47.131.249:80 | http://www.harlemrenaissancecentennial.org/img-sys/headerbg.jpg | US | html | 258 b | malicious |
3544 | firefox.exe | GET | 302 | 149.47.131.249:80 | http://www.harlemrenaissancecentennial.org/favicon.ico | US | html | 252 b | malicious |
3544 | firefox.exe | GET | 302 | 149.47.131.249:80 | http://www.harlemrenaissancecentennial.org/favicon.ico | US | html | 252 b | malicious |
3544 | firefox.exe | GET | 404 | 149.47.131.249:80 | http://www.harlemrenaissancecentennial.org/img-sys/bg.jpg | US | html | 257 b | malicious |
3544 | firefox.exe | POST | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/ | US | der | 471 b | whitelisted |
3544 | firefox.exe | GET | 302 | 149.47.131.249:80 | http://www.harlemrenaissancecentennial.org/ | US | html | 252 b | malicious |
3544 | firefox.exe | GET | 404 | 149.47.131.249:80 | http://www.harlemrenaissancecentennial.org/img-sys/contentbox.jpg | US | html | 262 b | malicious |
3544 | firefox.exe | GET | 404 | 149.47.131.249:80 | http://www.harlemrenaissancecentennial.org/img-sys/bg.jpg | US | html | 257 b | malicious |
3544 | firefox.exe | GET | 404 | 149.47.131.249:80 | http://www.harlemrenaissancecentennial.org/img-sys/bg.jpg | US | html | 257 b | malicious |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
3544 | firefox.exe | 2.18.212.136:80 | detectportal.firefox.com | Akamai International B.V. | — | whitelisted |
3544 | firefox.exe | 149.47.131.249:80 | www.harlemrenaissancecentennial.org | NEXCESS.NET L.L.C. | US | suspicious |
3544 | firefox.exe | 54.187.46.234:443 | tiles.services.mozilla.com | Amazon.com, Inc. | US | unknown |
3544 | firefox.exe | 52.89.32.107:443 | search.services.mozilla.com | Amazon.com, Inc. | US | unknown |
3544 | firefox.exe | 93.184.220.29:80 | ocsp.digicert.com | MCI Communications Services, Inc. d/b/a Verizon Business | US | whitelisted |
3544 | firefox.exe | 172.217.168.10:443 | safebrowsing.googleapis.com | Google Inc. | US | whitelisted |
4016 | pingsender.exe | 34.217.184.213:443 | incoming.telemetry.mozilla.org | Amazon.com, Inc. | US | unknown |
3544 | firefox.exe | 13.32.223.232:443 | tracking-protection.cdn.mozilla.net | Amazon.com, Inc. | US | malicious |
3544 | firefox.exe | 172.217.168.14:80 | ocsp.pki.goog | Google Inc. | US | whitelisted |
3544 | firefox.exe | 52.34.90.23:443 | shavar.services.mozilla.com | Amazon.com, Inc. | US | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
detectportal.firefox.com |
| whitelisted |
www.harlemrenaissancecentennial.org |
| malicious |
a1089.dscd.akamai.net |
| whitelisted |
harlemrenaissancecentennial.org |
| malicious |
search.services.mozilla.com |
| whitelisted |
search.r53-2.services.mozilla.com |
| whitelisted |
tiles.services.mozilla.com |
| whitelisted |
tiles.r53-2.services.mozilla.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
cs9.wac.phicdn.net |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
3544 | firefox.exe | A Network Trojan was detected | SC TROJAN_DOWNLOADER Suspicious redirect to 'suspendedpage.cgi' |
3544 | firefox.exe | A Network Trojan was detected | SC TROJAN_DOWNLOADER Suspicious redirect to 'suspendedpage.cgi' |
3544 | firefox.exe | A Network Trojan was detected | SC TROJAN_DOWNLOADER Suspicious redirect to 'suspendedpage.cgi' |
3544 | firefox.exe | Generic Protocol Command Decode | SURICATA STREAM excessive retransmissions |
3544 | firefox.exe | A Network Trojan was detected | SC TROJAN_DOWNLOADER Suspicious redirect to 'suspendedpage.cgi' |