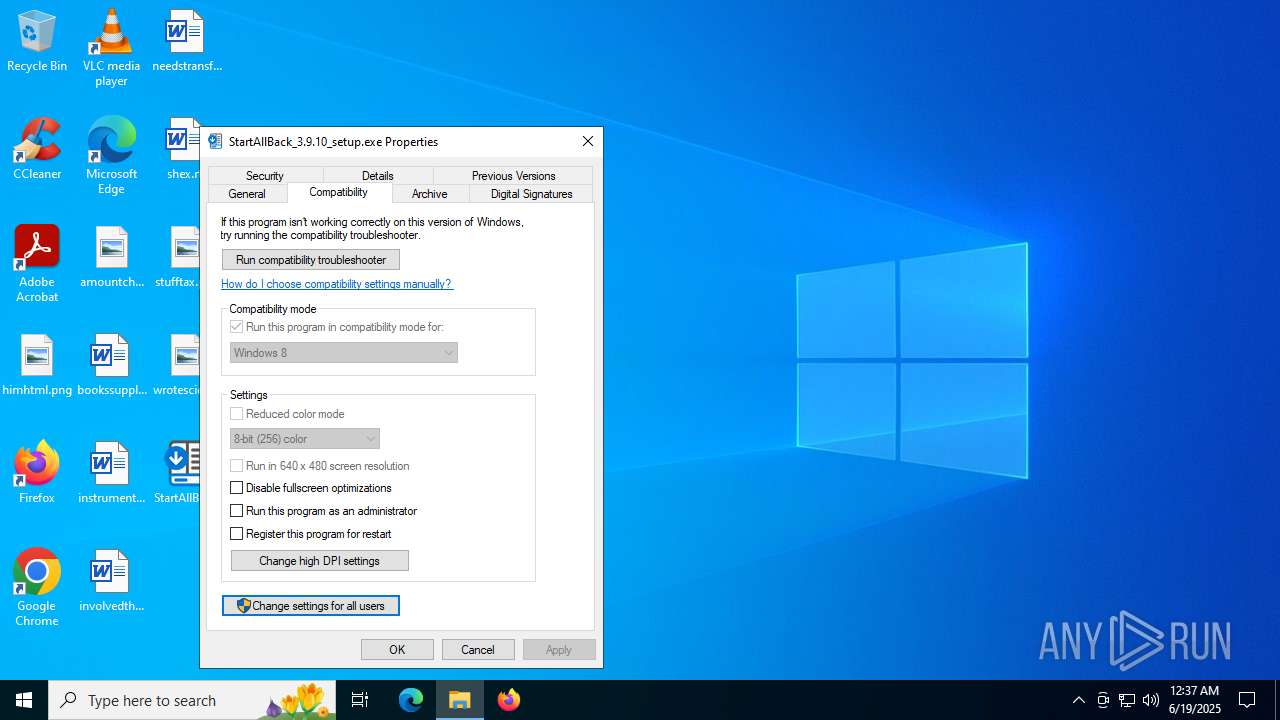
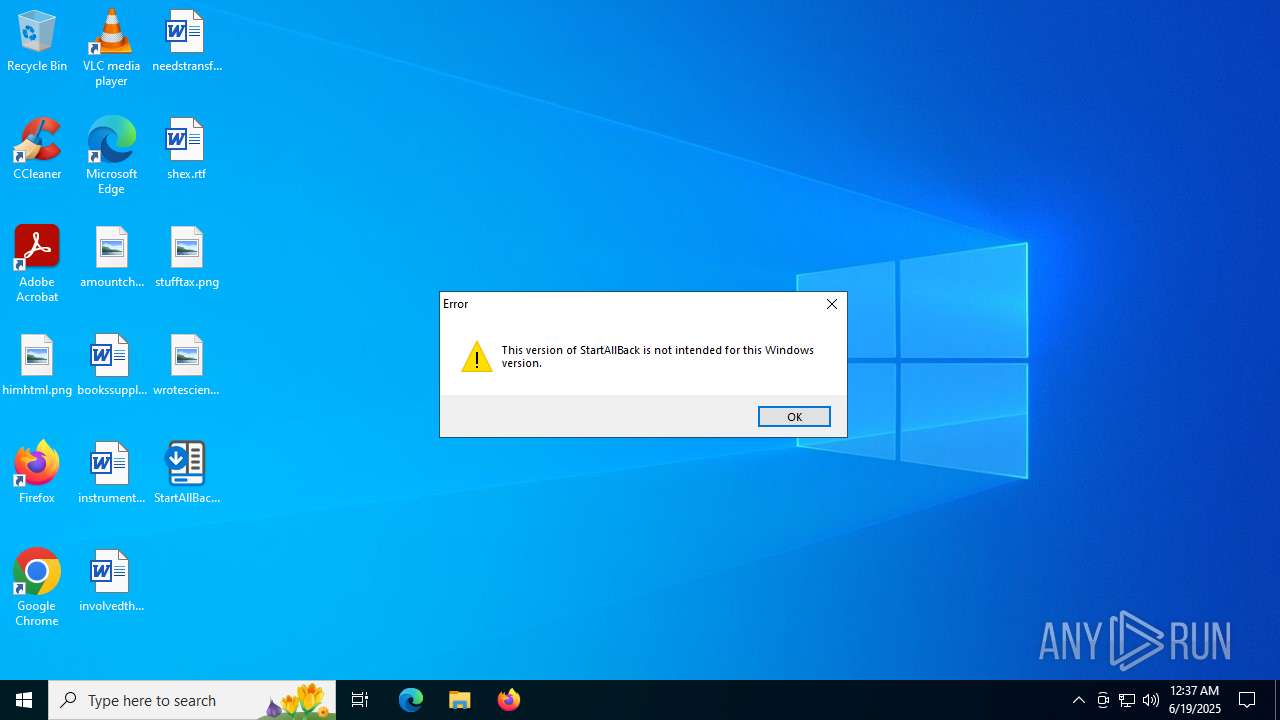
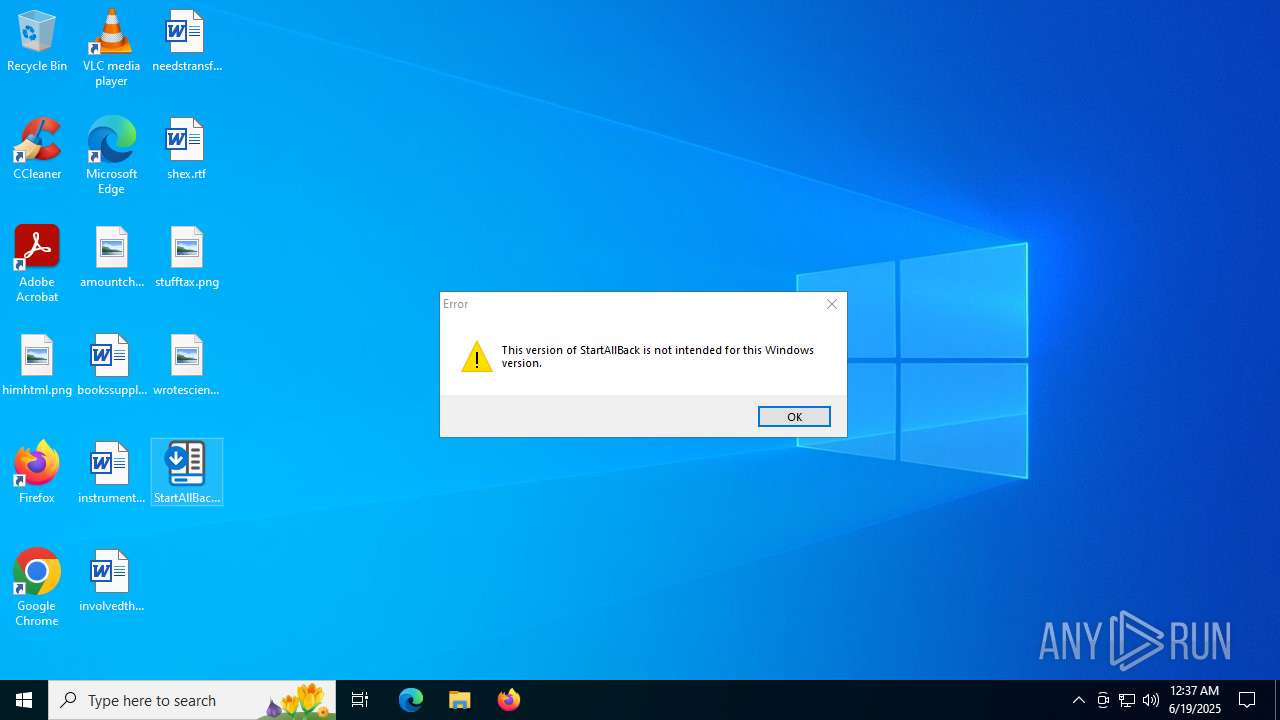
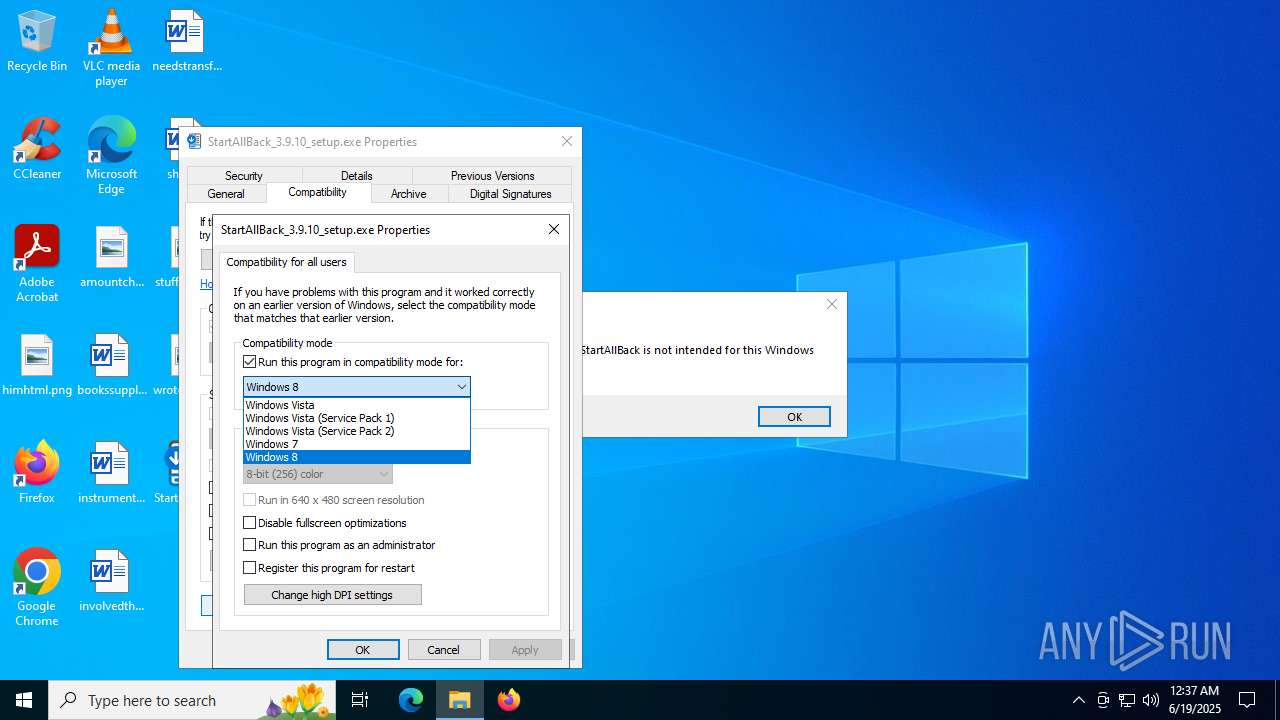
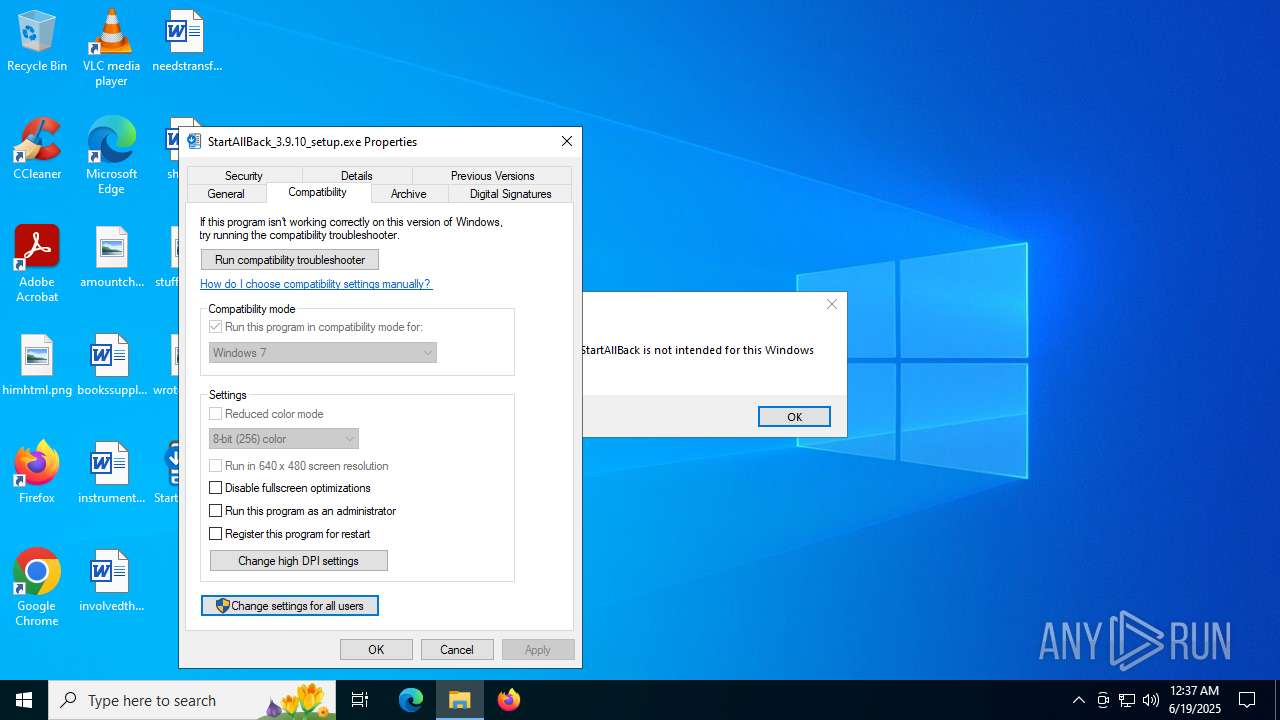
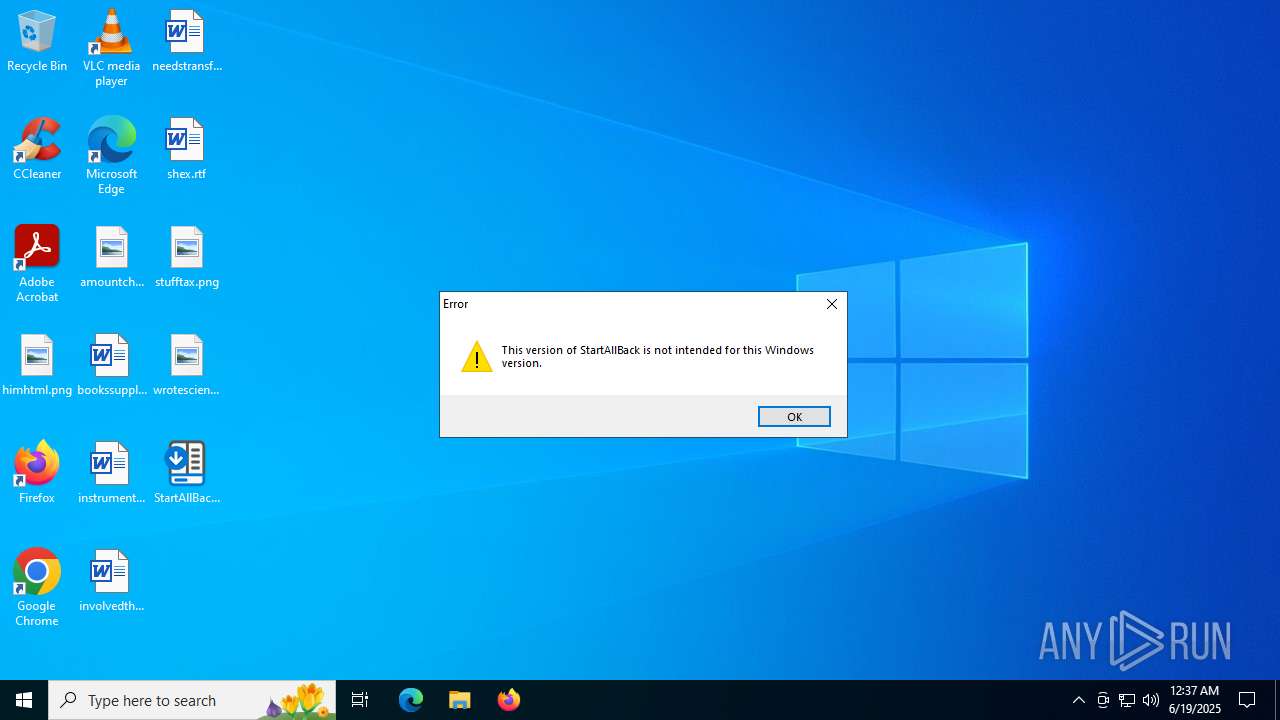
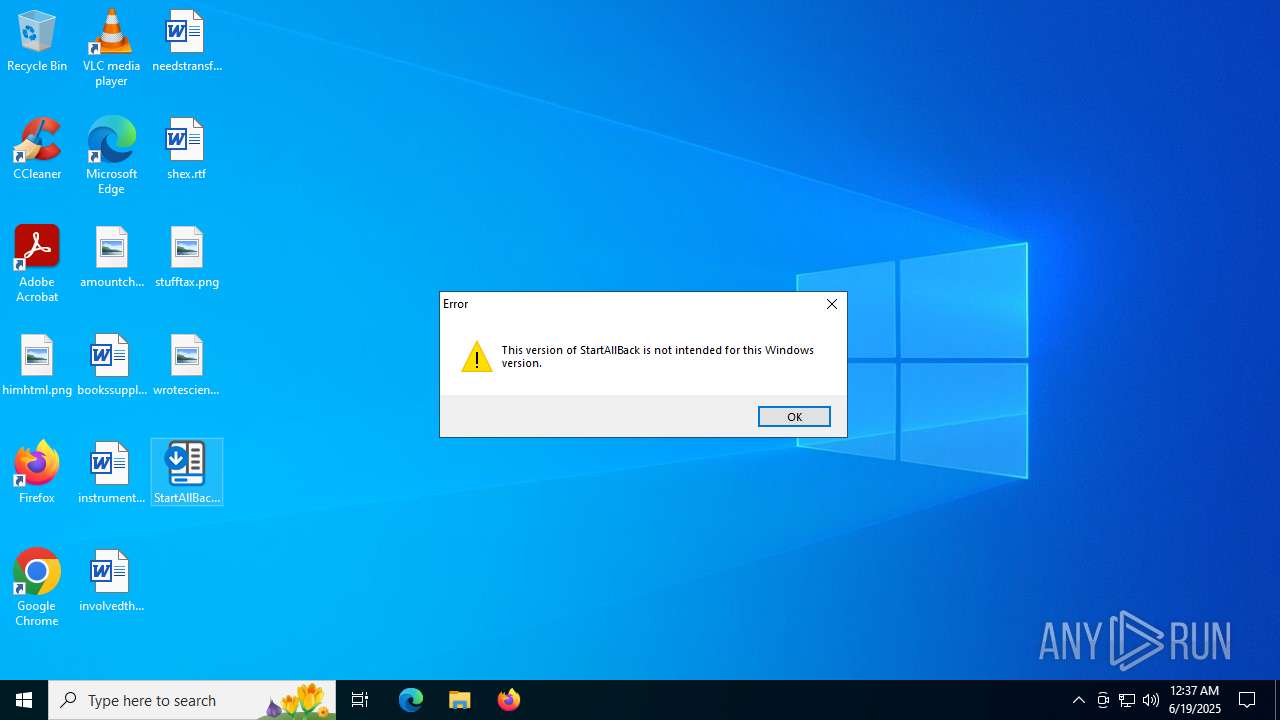
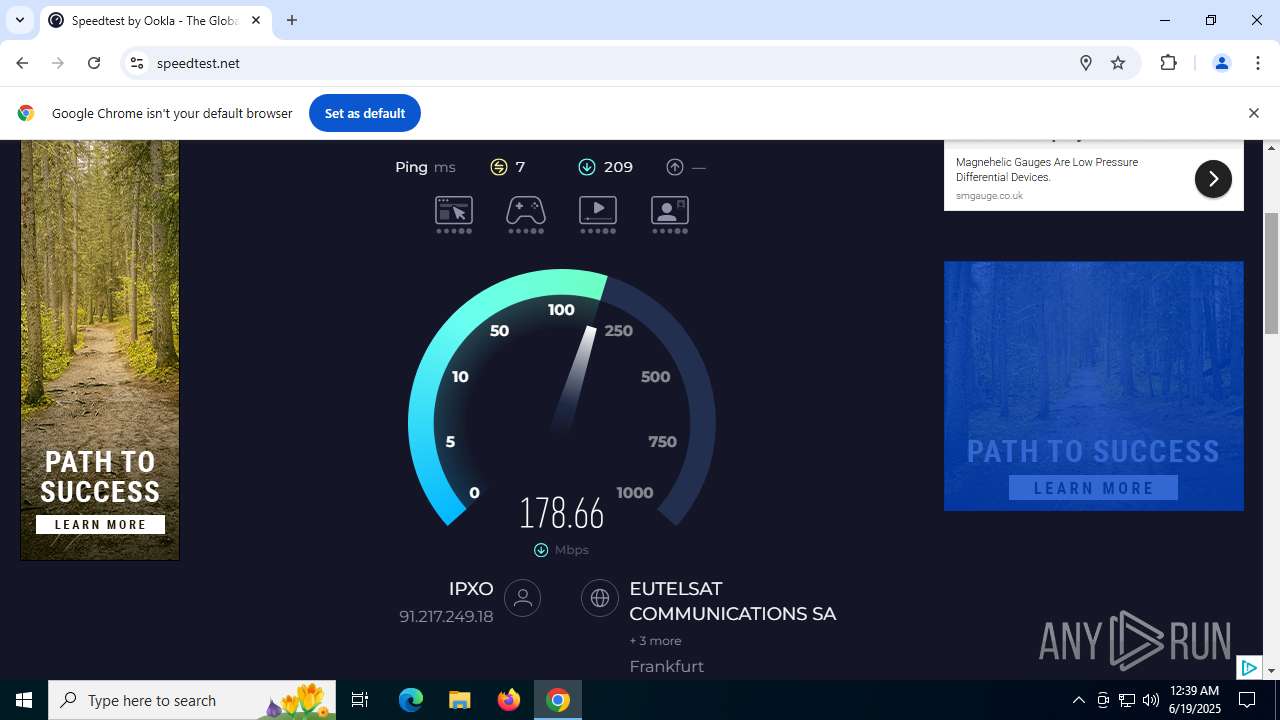
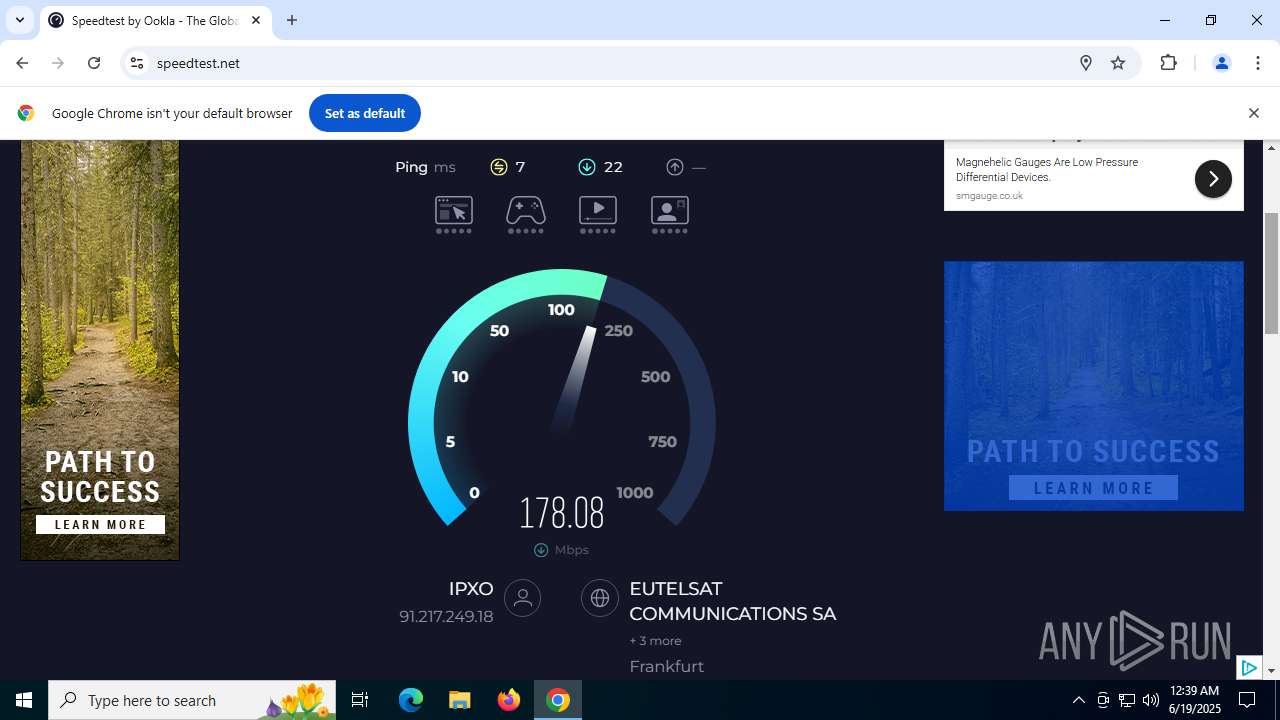
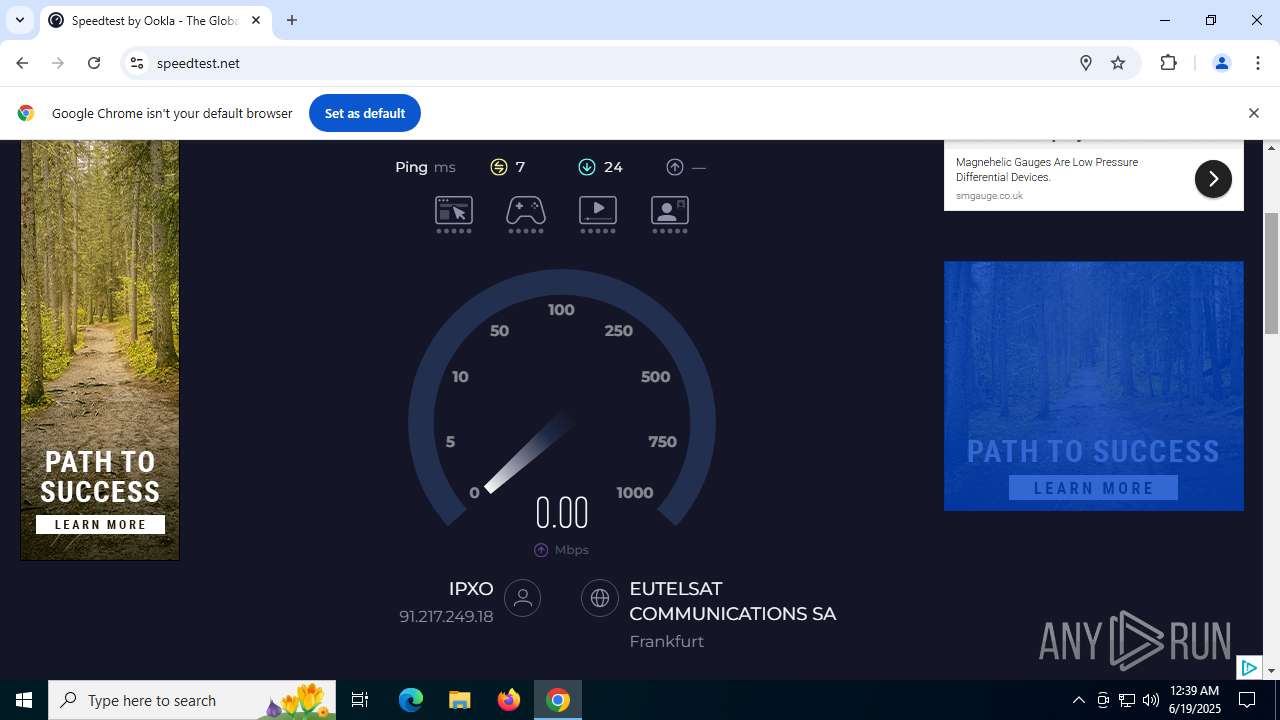
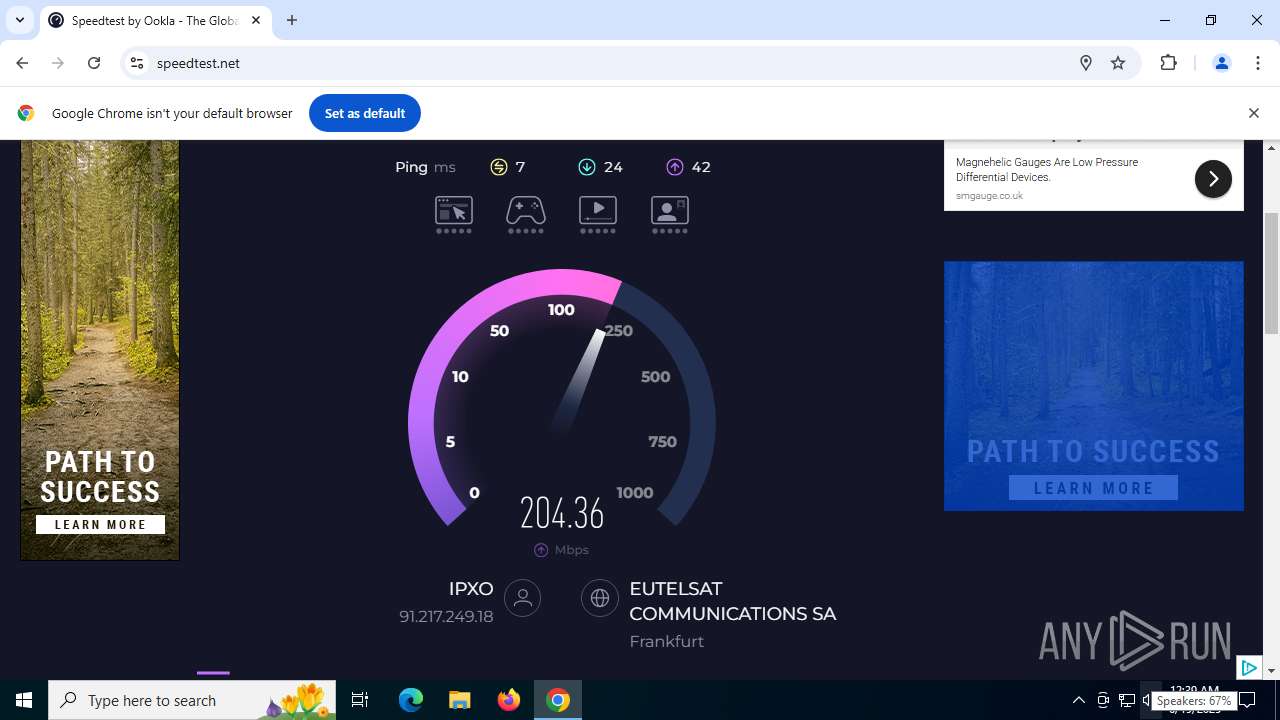
| File name: | StartAllBack_3.9.10_setup.exe |
| Full analysis: | https://app.any.run/tasks/6df071da-c3a2-4c53-8cc2-e2617dcb1775 |
| Verdict: | Malicious activity |
| Analysis date: | June 19, 2025, 00:35:30 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32+ executable (GUI) x86-64, for MS Windows, 6 sections |
| MD5: | 8E0A0735C9797E50FB58B6FE1F5D54C8 |
| SHA1: | EBAB7EAF700532203F92C82009643E7319F923AA |
| SHA256: | 8223B8FE745C7C579B0F0F82604C0F48BBD0A147130D2E9FDA97FAC0CD6742E0 |
| SSDEEP: | 98304:ZVHHjGbwrmoMlCvBxy7uUPNn0iec0pbcG4UyLuAUdGuTJpIxJ1iMA+XOrlczMzbc:+eY |
MALICIOUS
No malicious indicators.SUSPICIOUS
Reads the date of Windows installation
- StartAllBack_3.9.10_setup.exe (PID: 2760)
- StartAllBack_3.9.10_setup.exe (PID: 5020)
- StartAllBack_3.9.10_setup.exe (PID: 6828)
- StartAllBack_3.9.10_setup.exe (PID: 5828)
Reads security settings of Internet Explorer
- StartAllBack_3.9.10_setup.exe (PID: 2760)
- ShellExperienceHost.exe (PID: 6164)
- StartAllBack_3.9.10_setup.exe (PID: 6828)
- StartAllBack_3.9.10_setup.exe (PID: 5828)
- StartAllBack_3.9.10_setup.exe (PID: 5020)
Executable content was dropped or overwritten
- StartAllBack_3.9.10_setup.exe (PID: 2760)
- StartAllBack_3.9.10_setup.exe (PID: 5020)
- StartAllBack_3.9.10_setup.exe (PID: 6828)
- StartAllBack_3.9.10_setup.exe (PID: 5828)
There is functionality for taking screenshot (YARA)
- StartAllBackCfg.exe (PID: 4120)
INFO
The sample compiled with english language support
- StartAllBack_3.9.10_setup.exe (PID: 2760)
- StartAllBack_3.9.10_setup.exe (PID: 5020)
- StartAllBack_3.9.10_setup.exe (PID: 6828)
- StartAllBack_3.9.10_setup.exe (PID: 5828)
Create files in a temporary directory
- StartAllBack_3.9.10_setup.exe (PID: 2760)
- StartAllBack_3.9.10_setup.exe (PID: 5020)
- StartAllBack_3.9.10_setup.exe (PID: 6828)
- StartAllBack_3.9.10_setup.exe (PID: 5828)
Checks supported languages
- StartAllBackCfg.exe (PID: 6124)
- StartAllBack_3.9.10_setup.exe (PID: 2760)
- ShellExperienceHost.exe (PID: 6164)
- StartAllBack_3.9.10_setup.exe (PID: 5020)
- StartAllBackCfg.exe (PID: 2764)
- StartAllBack_3.9.10_setup.exe (PID: 6828)
- StartAllBackCfg.exe (PID: 4120)
- StartAllBack_3.9.10_setup.exe (PID: 5828)
- StartAllBackCfg.exe (PID: 6500)
Process checks computer location settings
- StartAllBack_3.9.10_setup.exe (PID: 2760)
- StartAllBack_3.9.10_setup.exe (PID: 5020)
- StartAllBack_3.9.10_setup.exe (PID: 6828)
- StartAllBack_3.9.10_setup.exe (PID: 5828)
Reads the computer name
- StartAllBack_3.9.10_setup.exe (PID: 2760)
- StartAllBackCfg.exe (PID: 6124)
- ShellExperienceHost.exe (PID: 6164)
- StartAllBack_3.9.10_setup.exe (PID: 5020)
- StartAllBack_3.9.10_setup.exe (PID: 6828)
- StartAllBackCfg.exe (PID: 2764)
- StartAllBackCfg.exe (PID: 4120)
- StartAllBack_3.9.10_setup.exe (PID: 5828)
- StartAllBackCfg.exe (PID: 6500)
Manual execution by a user
- StartAllBack_3.9.10_setup.exe (PID: 5020)
- StartAllBack_3.9.10_setup.exe (PID: 6828)
- StartAllBack_3.9.10_setup.exe (PID: 5828)
- chrome.exe (PID: 2296)
Reads the software policy settings
- slui.exe (PID: 1164)
Checks proxy server information
- slui.exe (PID: 1164)
Compiled with Borland Delphi (YARA)
- StartAllBackCfg.exe (PID: 4120)
Application launched itself
- chrome.exe (PID: 2296)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win64 Executable (generic) (87.3) |
|---|---|---|
| .exe | | | Generic Win/DOS Executable (6.3) |
| .exe | | | DOS Executable Generic (6.3) |
EXIF
EXE
| MachineType: | AMD AMD64 |
|---|---|
| TimeStamp: | 2024:04:20 16:00:09+00:00 |
| ImageFileCharacteristics: | Executable, Large address aware |
| PEType: | PE32+ |
| LinkerVersion: | 14.39 |
| CodeSize: | 34304 |
| InitializedDataSize: | 54784 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x1880 |
| OSVersion: | 6 |
| ImageVersion: | - |
| SubsystemVersion: | 6 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 1.0.0.1000 |
| ProductVersionNumber: | 1.0.0.1000 |
| FileFlagsMask: | 0x0000 |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | English (U.S.) |
| CharacterSet: | Unicode |
| CompanyName: | www.startallback.com |
| FileDescription: | StartAllBack setup SFX |
| FileVersion: | 1.0.0 |
| LegalCopyright: | Copyright (C) 2012-2022, Tihiy |
| OriginalFileName: | 7-zip SfxSetup.exe |
| ProductName: | StartAllBack |
| ProductVersion: | 1.0.0 |
Total processes
254
Monitored processes
91
Malicious processes
0
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 504 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --lang=en-US --service-sandbox-type=service --disable-quic --string-annotations --field-trial-handle=5508,i,3311635990189310883,8531654300088963499,262144 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction --variations-seed-version=20250221-144540.991000 --mojo-platform-channel-handle=5748 /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Version: 133.0.6943.127 Modules
| |||||||||||||||
| 724 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --string-annotations --enable-dinosaur-easter-egg-alt-images --disable-gpu-compositing --video-capture-use-gpu-memory-buffer --lang=en-US --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=8 --field-trial-handle=4724,i,3311635990189310883,8531654300088963499,262144 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction --variations-seed-version=20250221-144540.991000 --mojo-platform-channel-handle=4732 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 133.0.6943.127 Modules
| |||||||||||||||
| 768 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --string-annotations --enable-dinosaur-easter-egg-alt-images --disable-gpu-compositing --video-capture-use-gpu-memory-buffer --lang=en-US --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=28 --field-trial-handle=7392,i,3311635990189310883,8531654300088963499,262144 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction --variations-seed-version=20250221-144540.991000 --mojo-platform-channel-handle=6952 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Version: 133.0.6943.127 Modules
| |||||||||||||||
| 856 | C:\WINDOWS\system32\DllHost.exe /Processid:{513D916F-2A8E-4F51-AEAB-0CBC76FB1AF8} | C:\Windows\System32\dllhost.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: COM Surrogate Exit code: 0 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1100 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --string-annotations --enable-dinosaur-easter-egg-alt-images --disable-gpu-compositing --video-capture-use-gpu-memory-buffer --lang=en-US --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=21 --field-trial-handle=6248,i,3311635990189310883,8531654300088963499,262144 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction --variations-seed-version=20250221-144540.991000 --mojo-platform-channel-handle=6280 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 133.0.6943.127 Modules
| |||||||||||||||
| 1164 | C:\WINDOWS\System32\slui.exe -Embedding | C:\Windows\System32\slui.exe | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Activation Client Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1200 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --string-annotations --enable-dinosaur-easter-egg-alt-images --disable-gpu-compositing --video-capture-use-gpu-memory-buffer --lang=en-US --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=72 --field-trial-handle=11992,i,3311635990189310883,8531654300088963499,262144 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction --variations-seed-version=20250221-144540.991000 --mojo-platform-channel-handle=6316 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 133.0.6943.127 Modules
| |||||||||||||||
| 1440 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=unzip.mojom.Unzipper --lang=en-US --service-sandbox-type=service --disable-quic --string-annotations --field-trial-handle=864,i,3311635990189310883,8531654300088963499,262144 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction --variations-seed-version=20250221-144540.991000 --mojo-platform-channel-handle=4800 /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 133.0.6943.127 Modules
| |||||||||||||||
| 1480 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --string-annotations --enable-dinosaur-easter-egg-alt-images --disable-gpu-compositing --video-capture-use-gpu-memory-buffer --lang=en-US --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=30 --field-trial-handle=7684,i,3311635990189310883,8531654300088963499,262144 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction --variations-seed-version=20250221-144540.991000 --mojo-platform-channel-handle=7348 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Version: 133.0.6943.127 Modules
| |||||||||||||||
| 1496 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --string-annotations --enable-dinosaur-easter-egg-alt-images --disable-gpu-compositing --video-capture-use-gpu-memory-buffer --lang=en-US --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=12 --field-trial-handle=3348,i,3311635990189310883,8531654300088963499,262144 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction --variations-seed-version=20250221-144540.991000 --mojo-platform-channel-handle=3360 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 133.0.6943.127 Modules
| |||||||||||||||
Total events
12 140
Read events
12 102
Write events
26
Delete events
12
Modification events
| (PID) Process: | (6164) ShellExperienceHost.exe | Key: | \REGISTRY\A\{184d6f1c-419c-a3f5-a50f-2a2353827c03}\LocalState |
| Operation: | write | Name: | LastNetworkingFlyoutHeight |
Value: 000012436D60443FB2E0DB01 | |||
| (PID) Process: | (2228) dllhost.exe | Key: | \REGISTRY\A\{9985e4a5-4b1b-ae58-674a-b1bfe5cc34fd}\Root\InventoryApplicationFile |
| Operation: | write | Name: | WritePermissionsCheck |
Value: 1 | |||
| (PID) Process: | (2228) dllhost.exe | Key: | \REGISTRY\A\{9985e4a5-4b1b-ae58-674a-b1bfe5cc34fd}\Root\InventoryApplicationFile\PermissionsCheckTestKey |
| Operation: | delete key | Name: | (default) |
Value: | |||
| (PID) Process: | (856) dllhost.exe | Key: | \REGISTRY\A\{a9485a31-5e4f-90e1-1e74-b1cce5a43028}\Root\InventoryApplicationFile |
| Operation: | write | Name: | WritePermissionsCheck |
Value: 1 | |||
| (PID) Process: | (856) dllhost.exe | Key: | \REGISTRY\A\{a9485a31-5e4f-90e1-1e74-b1cce5a43028}\Root\InventoryApplicationFile\PermissionsCheckTestKey |
| Operation: | delete key | Name: | (default) |
Value: | |||
| (PID) Process: | (2296) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Google\Chrome\BLBeacon |
| Operation: | write | Name: | failed_count |
Value: 0 | |||
| (PID) Process: | (2296) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Google\Chrome\BLBeacon |
| Operation: | write | Name: | state |
Value: 2 | |||
| (PID) Process: | (2296) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Google\Chrome\BLBeacon |
| Operation: | write | Name: | state |
Value: 1 | |||
| (PID) Process: | (2296) chrome.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Google\Update\ClientStateMedium\{8A69D345-D564-463C-AFF1-A69D9E530F96} |
| Operation: | write | Name: | usagestats |
Value: 0 | |||
| (PID) Process: | (2296) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Google\Chrome\StabilityMetrics |
| Operation: | write | Name: | user_experience_metrics.stability.exited_cleanly |
Value: 0 | |||
Executable files
61
Suspicious files
311
Text files
246
Unknown types
12
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2760 | StartAllBack_3.9.10_setup.exe | C:\Users\admin\AppData\Local\Temp\SIBSFX.76627AC8\Ribbon\theme-light\windows.hideSelected.svg | image | |
MD5:969F2A95D9F8F53871EC2915B7F899E4 | SHA256:5CB0408302A93EFE9DC8CAB07F2F6D450945026F844A5CE7728D2E830D0EEAE1 | |||
| 2760 | StartAllBack_3.9.10_setup.exe | C:\Users\admin\AppData\Local\Temp\SIBSFX.76627AC8\Orbs\clover.svg | image | |
MD5:47B9BE5D069D6873CC9BFC3FC7C3B9B2 | SHA256:1E0E1EA6149FFFE9A6D09A77B404FE17DB7D455D1036FAEBDC168B1CE5869282 | |||
| 2760 | StartAllBack_3.9.10_setup.exe | C:\Users\admin\AppData\Local\Temp\SIBSFX.76627AC8\Ribbon\theme-dark\easyaccess.svg | image | |
MD5:B0DBCBB94384185AA810405152782157 | SHA256:6CEBC92632E26A4FEA23D3E95E3590912F0037F2500EBE576E6D0AF54ABD4C79 | |||
| 2760 | StartAllBack_3.9.10_setup.exe | C:\Users\admin\AppData\Local\Temp\SIBSFX.76627AC8\Ribbon\theme-dark\windows.folderoptions.svg | image | |
MD5:FB052EE6B0D4EB3A0AC028075E212E49 | SHA256:3615AD11593E0FA41C9FCEBE32B9E96865CF13A27640F87802AA3C33730A05EB | |||
| 2760 | StartAllBack_3.9.10_setup.exe | C:\Users\admin\AppData\Local\Temp\SIBSFX.76627AC8\Orbs\e1evenorb-pr.png | image | |
MD5:E5ECAD423623A327B850919BD8A41BD4 | SHA256:6E451FE2D887698C4290B830AEC1A4A196DE22EB3BCF6734B567521BF2D6EDF2 | |||
| 2760 | StartAllBack_3.9.10_setup.exe | C:\Users\admin\AppData\Local\Temp\SIBSFX.76627AC8\Orbs\w8logo.svg | image | |
MD5:F13738B41B7A2042C53DD228601639E0 | SHA256:C75684410793A98A051A1CF95395709C73E9589037D47BE3F6277B4AC355B7FB | |||
| 2760 | StartAllBack_3.9.10_setup.exe | C:\Users\admin\AppData\Local\Temp\SIBSFX.76627AC8\Ribbon\theme-dark\Windows.AddRemovePrograms.svg | image | |
MD5:E0F7EF3D2F36317931A42DDDD494C9C2 | SHA256:F51C5B5B68F6BC5104188A93F145CA2D6E57D94636FDA34E41599BAE0E5EC682 | |||
| 2760 | StartAllBack_3.9.10_setup.exe | C:\Users\admin\AppData\Local\Temp\SIBSFX.76627AC8\Ribbon\theme-dark\accessmedia.svg | image | |
MD5:87549BFACB19AC7EEA47DFDDDCA9EA80 | SHA256:A14B44B414971FAE445DF013A5DE357FF625E4A509BFEAD3B0C01A74844AA515 | |||
| 2760 | StartAllBack_3.9.10_setup.exe | C:\Users\admin\AppData\Local\Temp\SIBSFX.76627AC8\Orbs\Windows 7.orb | executable | |
MD5:85328E698E8A74852B4061A683915DC8 | SHA256:E5B74E9E7BD6758A0154B11462AE3328EDD143190865198104D8BD53B9AF7275 | |||
| 2760 | StartAllBack_3.9.10_setup.exe | C:\Users\admin\AppData\Local\Temp\SIBSFX.76627AC8\Ribbon\theme-dark\windows.hideSelected.svg | image | |
MD5:AEA15430DEF6CFDA52866C7ACCE670CB | SHA256:931320E31E415B420AA1985D2B7305D4F3B1D2F1D8FFDDB18C01690AA84F3D20 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
28
TCP/UDP connections
783
DNS requests
1 011
Threats
8
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
5040 | SystemSettings.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAUZZSZEml49Gjh0j13P68w%3D | unknown | — | — | whitelisted |
6508 | SIHClient.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
4944 | svchost.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
3756 | svchost.exe | GET | 206 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/acpeapixpwuzscfa5h5j5m7c4xaa_2025.6.16.0/niikhdgajlphfehepabhhblakbdgeefj_2025.06.16.00_all_acgsomx5qtwgffxcrxwhoksfom7q.crx3 | unknown | — | — | whitelisted |
3756 | svchost.exe | HEAD | 200 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/acdvcifl2ztime6bsz3eijtcfeaq_2025.5.15.1/kiabhabjdbkjdpjbpigfodbdjmbglcoo_2025.05.15.01_all_ehum5zzx5qnqq3vyyhyi6ytrfq.crx3 | unknown | — | — | whitelisted |
3756 | svchost.exe | GET | 206 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/acpeapixpwuzscfa5h5j5m7c4xaa_2025.6.16.0/niikhdgajlphfehepabhhblakbdgeefj_2025.06.16.00_all_acgsomx5qtwgffxcrxwhoksfom7q.crx3 | unknown | — | — | whitelisted |
3756 | svchost.exe | GET | 206 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/acpeapixpwuzscfa5h5j5m7c4xaa_2025.6.16.0/niikhdgajlphfehepabhhblakbdgeefj_2025.06.16.00_all_acgsomx5qtwgffxcrxwhoksfom7q.crx3 | unknown | — | — | whitelisted |
3756 | svchost.exe | GET | 200 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/acdvcifl2ztime6bsz3eijtcfeaq_2025.5.15.1/kiabhabjdbkjdpjbpigfodbdjmbglcoo_2025.05.15.01_all_ehum5zzx5qnqq3vyyhyi6ytrfq.crx3 | unknown | — | — | whitelisted |
3756 | svchost.exe | GET | 206 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/acpeapixpwuzscfa5h5j5m7c4xaa_2025.6.16.0/niikhdgajlphfehepabhhblakbdgeefj_2025.06.16.00_all_acgsomx5qtwgffxcrxwhoksfom7q.crx3 | unknown | — | — | whitelisted |
3756 | svchost.exe | HEAD | 200 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/aevtvjsxpcrwhjvp5w32fej6zq_9.56.0/gcmjkmgdlgnkkcocmoeiminaijmmjnii_9.56.0_all_acq3rupi4ymeq53so4pzqroatfea.crx3 | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
5944 | MoUsoCoreWorker.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
3732 | RUXIMICS.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
1268 | svchost.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
2336 | svchost.exe | 172.211.123.249:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | FR | whitelisted |
4944 | svchost.exe | 20.190.159.23:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4944 | svchost.exe | 2.17.190.73:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
1268 | svchost.exe | 23.48.23.143:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
1268 | svchost.exe | 184.30.21.171:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
google.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
nexusrules.officeapps.live.com |
| whitelisted |
cxcs.microsoft.net |
| whitelisted |
www.bing.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
5652 | chrome.exe | Not Suspicious Traffic | INFO [ANY.RUN] Google Tag Manager analytics (googletagmanager .com) |
5652 | chrome.exe | Not Suspicious Traffic | INFO [ANY.RUN] Google Tag Manager analytics (googletagmanager .com) |
5652 | chrome.exe | Not Suspicious Traffic | INFO [ANY.RUN] Google Tag Manager analytics (googletagmanager .com) |
5652 | chrome.exe | Not Suspicious Traffic | INFO [ANY.RUN] Google Tag Manager analytics (googletagmanager .com) |
5652 | chrome.exe | Not Suspicious Traffic | INFO [ANY.RUN] Requests to a free CDN for open source projects (jsdelivr .net) |
5652 | chrome.exe | Not Suspicious Traffic | INFO [ANY.RUN] Requests to a free CDN for open source projects (jsdelivr .net) |
5652 | chrome.exe | Not Suspicious Traffic | INFO [ANY.RUN] Cloudflare Network Error Logging (NEL) |
5652 | chrome.exe | Not Suspicious Traffic | INFO [ANY.RUN] Cloudflare Network Error Logging (NEL) |
Process | Message |
|---|---|
StartAllBack_3.9.10_setup.exe | FTH: (5020): *** Fault tolerant heap shim applied to current process. This is usually due to previous crashes. ***
|
StartAllBackCfg.exe | FTH: (2764): *** Fault tolerant heap shim applied to current process. This is usually due to previous crashes. ***
|
StartAllBack_3.9.10_setup.exe | FTH: (6828): *** Fault tolerant heap shim applied to current process. This is usually due to previous crashes. ***
|
StartAllBackCfg.exe | FTH: (4120): *** Fault tolerant heap shim applied to current process. This is usually due to previous crashes. ***
|
StartAllBack_3.9.10_setup.exe | FTH: (5828): *** Fault tolerant heap shim applied to current process. This is usually due to previous crashes. ***
|
StartAllBackCfg.exe | FTH: (6500): *** Fault tolerant heap shim applied to current process. This is usually due to previous crashes. ***
|