| File name: | malware sample.exe |
| Full analysis: | https://app.any.run/tasks/0ba44932-f892-439d-af18-9cddde5275f6 |
| Verdict: | Malicious activity |
| Analysis date: | May 10, 2024, 14:49:01 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows |
| MD5: | C6BF2BA00A017119CE0EDFBC8672CC91 |
| SHA1: | DE4717F8C2C21A645E1D6277F44D758987F7689D |
| SHA256: | 82214454A367AE2C003BA28F11F7FDCB433347661B99EA54ABE36B548CAA2AE8 |
| SSDEEP: | 98304:i+cD4dn88HgsM3mOBrA5rRhbpfbp3BV7KDCDt3ntTzYLy7xIDkpddsum5tfhALEd:FVRz6ivLCwZYTC2iOJ |
MALICIOUS
Drops the executable file immediately after the start
- malware sample.exe (PID: 3972)
- malware sample.exe (PID: 1200)
- malware sample.tmp (PID: 928)
SUSPICIOUS
Executable content was dropped or overwritten
- malware sample.exe (PID: 3972)
- malware sample.exe (PID: 1200)
- malware sample.tmp (PID: 928)
Reads the Windows owner or organization settings
- malware sample.tmp (PID: 928)
INFO
Checks supported languages
- malware sample.exe (PID: 3972)
- malware sample.tmp (PID: 3988)
- malware sample.exe (PID: 1200)
- malware sample.tmp (PID: 928)
Reads the computer name
- malware sample.tmp (PID: 3988)
- malware sample.tmp (PID: 928)
Create files in a temporary directory
- malware sample.exe (PID: 3972)
- malware sample.exe (PID: 1200)
Creates files in the program directory
- malware sample.tmp (PID: 928)
Creates a software uninstall entry
- malware sample.tmp (PID: 928)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Inno Setup installer (65.1) |
|---|---|---|
| .exe | | | Win32 EXE PECompact compressed (generic) (24.6) |
| .dll | | | Win32 Dynamic Link Library (generic) (3.9) |
| .exe | | | Win32 Executable (generic) (2.6) |
| .exe | | | Win16/32 Executable Delphi generic (1.2) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2023:02:15 14:54:16+00:00 |
| ImageFileCharacteristics: | No relocs, Executable, No line numbers, No symbols, Bytes reversed lo, 32-bit, Bytes reversed hi |
| PEType: | PE32 |
| LinkerVersion: | 2.25 |
| CodeSize: | 741888 |
| InitializedDataSize: | 38912 |
| UninitializedDataSize: | - |
| EntryPoint: | 0xb5eec |
| OSVersion: | 6.1 |
| ImageVersion: | 6 |
| SubsystemVersion: | 6.1 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 0.0.0.0 |
| ProductVersionNumber: | 0.0.0.0 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | Neutral |
| CharacterSet: | Unicode |
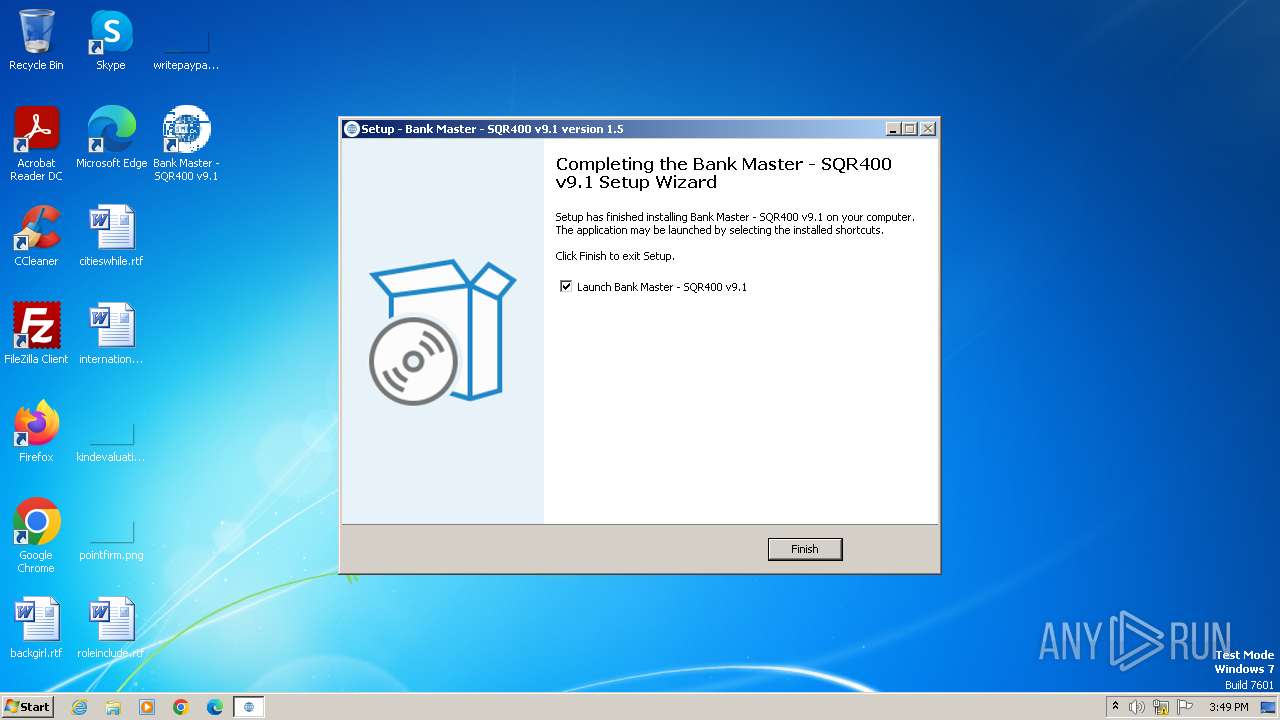
| Comments: | This installation was built with Inno Setup. |
| CompanyName: | My Company, Inc. |
| FileDescription: | Bank Master - SQR400 v9.1 Setup |
| FileVersion: | |
| LegalCopyright: | |
| OriginalFileName: | |
| ProductName: | Bank Master - SQR400 v9.1 |
| ProductVersion: | 1.5 |
Total processes
39
Monitored processes
4
Malicious processes
3
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
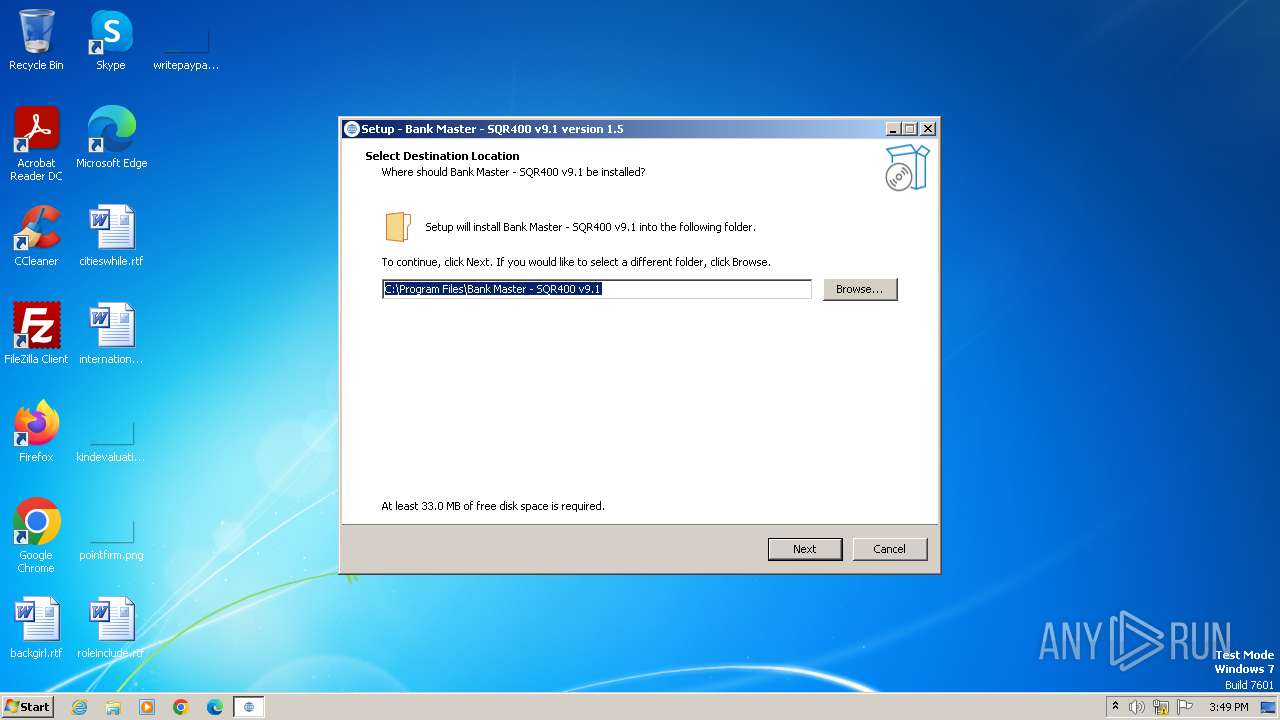
| 928 | "C:\Users\admin\AppData\Local\Temp\is-BMLM3.tmp\malware sample.tmp" /SL5="$2013A,10187784,781824,C:\Users\admin\AppData\Local\Temp\malware sample.exe" /SPAWNWND=$40130 /NOTIFYWND=$20138 | C:\Users\admin\AppData\Local\Temp\is-BMLM3.tmp\malware sample.tmp | malware sample.exe | ||||||||||||
User: admin Company: My Company, Inc. Integrity Level: HIGH Description: Setup/Uninstall Exit code: 0 Version: 51.1052.0.0 Modules
| |||||||||||||||
| 1200 | "C:\Users\admin\AppData\Local\Temp\malware sample.exe" /SPAWNWND=$40130 /NOTIFYWND=$20138 | C:\Users\admin\AppData\Local\Temp\malware sample.exe | malware sample.tmp | ||||||||||||
User: admin Company: My Company, Inc. Integrity Level: HIGH Description: Bank Master - SQR400 v9.1 Setup Exit code: 0 Version: Modules
| |||||||||||||||
| 3972 | "C:\Users\admin\AppData\Local\Temp\malware sample.exe" | C:\Users\admin\AppData\Local\Temp\malware sample.exe | explorer.exe | ||||||||||||
User: admin Company: My Company, Inc. Integrity Level: MEDIUM Description: Bank Master - SQR400 v9.1 Setup Exit code: 0 Version: Modules
| |||||||||||||||
| 3988 | "C:\Users\admin\AppData\Local\Temp\is-FLQDQ.tmp\malware sample.tmp" /SL5="$20138,10187784,781824,C:\Users\admin\AppData\Local\Temp\malware sample.exe" | C:\Users\admin\AppData\Local\Temp\is-FLQDQ.tmp\malware sample.tmp | — | malware sample.exe | |||||||||||
User: admin Company: My Company, Inc. Integrity Level: MEDIUM Description: Setup/Uninstall Exit code: 0 Version: 51.1052.0.0 Modules
| |||||||||||||||
Total events
3 466
Read events
3 428
Write events
32
Delete events
6
Modification events
| (PID) Process: | (928) malware sample.tmp | Key: | HKEY_CURRENT_USER\Software\Microsoft\RestartManager\Session0000 |
| Operation: | write | Name: | Owner |
Value: A003000078303438E9A2DA01 | |||
| (PID) Process: | (928) malware sample.tmp | Key: | HKEY_CURRENT_USER\Software\Microsoft\RestartManager\Session0000 |
| Operation: | write | Name: | SessionHash |
Value: 4216E2426DADFAB735E5AC110527B0E32B569D938A960420680800F2FCA447FA | |||
| (PID) Process: | (928) malware sample.tmp | Key: | HKEY_CURRENT_USER\Software\Microsoft\RestartManager\Session0000 |
| Operation: | write | Name: | Sequence |
Value: 1 | |||
| (PID) Process: | (928) malware sample.tmp | Key: | HKEY_CURRENT_USER\Software\Microsoft\RestartManager\Session0000 |
| Operation: | write | Name: | RegFiles0000 |
Value: C:\Program Files\Bank Master - SQR400 v9.1\bankflash.exe | |||
| (PID) Process: | (928) malware sample.tmp | Key: | HKEY_CURRENT_USER\Software\Microsoft\RestartManager\Session0000 |
| Operation: | write | Name: | RegFilesHash |
Value: 20277B9298A44E4044AB361A9557B28F39D2CC5BA9E1B00F7594CFF484ECA576 | |||
| (PID) Process: | (928) malware sample.tmp | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Classes\.myp\OpenWithProgids |
| Operation: | write | Name: | BankMaster-SQR400v9.1File.myp |
Value: | |||
| (PID) Process: | (928) malware sample.tmp | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Classes\Applications\bankflash.exe\SupportedTypes |
| Operation: | write | Name: | .myp |
Value: | |||
| (PID) Process: | (928) malware sample.tmp | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\{D1909E11-1008-4B85-BC67-D4D1D201E94E}_is1 |
| Operation: | write | Name: | Inno Setup: Setup Version |
Value: 6.2.2 | |||
| (PID) Process: | (928) malware sample.tmp | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\{D1909E11-1008-4B85-BC67-D4D1D201E94E}_is1 |
| Operation: | write | Name: | Inno Setup: App Path |
Value: C:\Program Files\Bank Master - SQR400 v9.1 | |||
| (PID) Process: | (928) malware sample.tmp | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\{D1909E11-1008-4B85-BC67-D4D1D201E94E}_is1 |
| Operation: | write | Name: | InstallLocation |
Value: C:\Program Files\Bank Master - SQR400 v9.1\ | |||
Executable files
11
Suspicious files
44
Text files
13
Unknown types
3
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 928 | malware sample.tmp | C:\Program Files\Bank Master - SQR400 v9.1\data\is-FALKO.tmp | — | |
MD5:— | SHA256:— | |||
| 928 | malware sample.tmp | C:\Program Files\Bank Master - SQR400 v9.1\data\app.so | — | |
MD5:— | SHA256:— | |||
| 928 | malware sample.tmp | C:\Program Files\Bank Master - SQR400 v9.1\is-EG8RN.tmp | executable | |
MD5:2D371A04AB07C6B4EA958A7EC53F2973 | SHA256:CBDA98B22DCBB6C3CA4D7EE67FBF8882876943658A8F9E246D963A34E9630014 | |||
| 928 | malware sample.tmp | C:\Program Files\Bank Master - SQR400 v9.1\unins000.exe | executable | |
MD5:2D371A04AB07C6B4EA958A7EC53F2973 | SHA256:CBDA98B22DCBB6C3CA4D7EE67FBF8882876943658A8F9E246D963A34E9630014 | |||
| 928 | malware sample.tmp | C:\Program Files\Bank Master - SQR400 v9.1\is-POMJN.tmp | executable | |
MD5:87C4A4A0B1CD30B71645C9B6026D2057 | SHA256:E1B2FE27174E8A311533F73436FBAE823FF21414D8B7CAB9852CBE7FE6083E8B | |||
| 3972 | malware sample.exe | C:\Users\admin\AppData\Local\Temp\is-FLQDQ.tmp\malware sample.tmp | executable | |
MD5:11E44C2A63D451042F20BE7925DAF156 | SHA256:C6B3EE75C6B85AA030F1435F7E93F479A835CD0C7FDD5609569CFCE59F092D58 | |||
| 928 | malware sample.tmp | C:\Program Files\Bank Master - SQR400 v9.1\data\is-GRFB7.tmp | binary | |
MD5:DA48E432FE61F451154F0715B2A7B174 | SHA256:65EA729083128DFCE1C00726BA932B91AAAF5E48736B5644DD37478E5F2875AC | |||
| 928 | malware sample.tmp | C:\Program Files\Bank Master - SQR400 v9.1\is-QDVF2.tmp | executable | |
MD5:3DD61ACA82B1D5F5E78D2AF286856A4D | SHA256:0829F06332A7437852C8A4AD6C4A0D069AE4CE3D4A6C9C554A1444AA6124A1E4 | |||
| 928 | malware sample.tmp | C:\Program Files\Bank Master - SQR400 v9.1\bankflash.exe | executable | |
MD5:3DD61ACA82B1D5F5E78D2AF286856A4D | SHA256:0829F06332A7437852C8A4AD6C4A0D069AE4CE3D4A6C9C554A1444AA6124A1E4 | |||
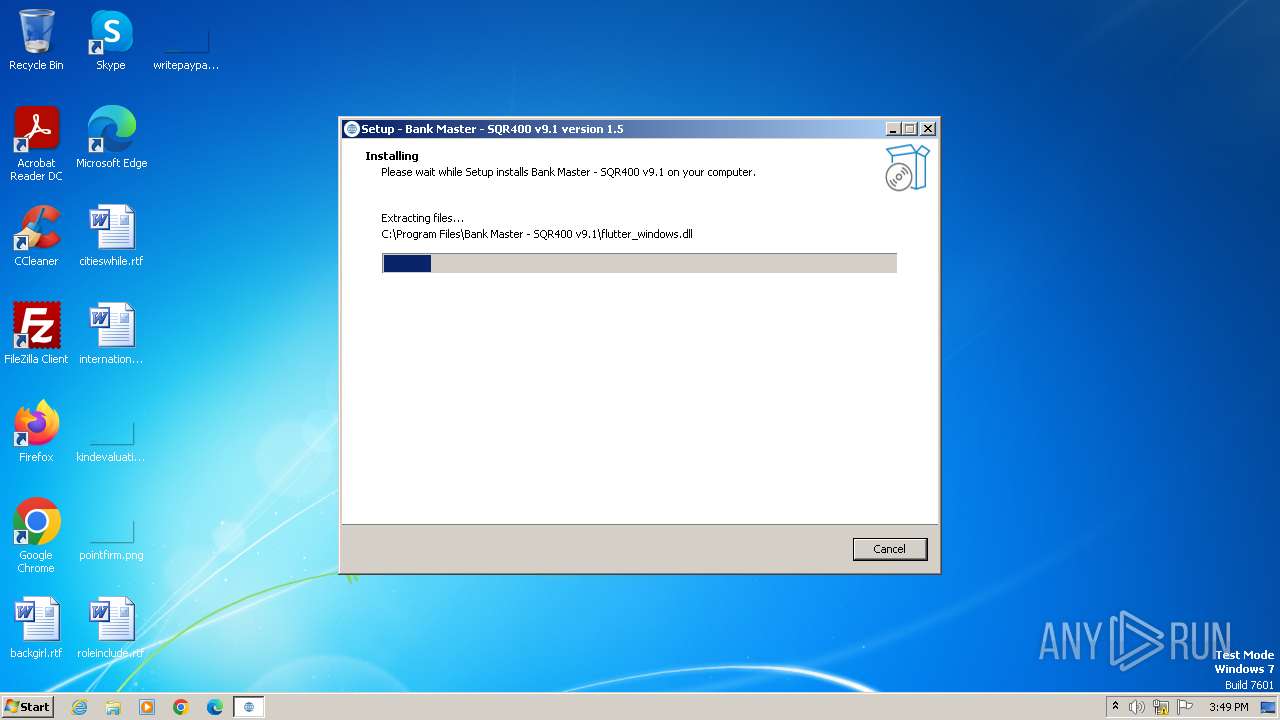
| 928 | malware sample.tmp | C:\Program Files\Bank Master - SQR400 v9.1\flutter_windows.dll | executable | |
MD5:42C5A6B7DB5911DD85DAF5B0FABDFF22 | SHA256:28EB582019E20ADB30AF9756CC1622940F0F872ACDEF3A08327CB980CA6115EB | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
3
DNS requests
0
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | unknown |
— | — | 224.0.0.252:5355 | — | — | — | unknown |