| File name: | Player.exe |
| Full analysis: | https://app.any.run/tasks/c6ed3232-9741-4513-89f0-e8267c6378ab |
| Verdict: | Malicious activity |
| Analysis date: | October 30, 2023, 16:39:21 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows |
| MD5: | 3C128D2D200508B075A4C468C984F9C4 |
| SHA1: | B2FAA4FEB487546254152D61C657A20917C44FCE |
| SHA256: | 8207AB2EE7875805985F809489F40BF9304570CC868C94A61ED39E2A8D7F9684 |
| SSDEEP: | 98304:gFbX4QVU0LVMamD6GXicz2iWde1gwiJvzNoetcwDbeLwfNwS4TbPiP9kFjb5S+aj:YBPfq4v |
MALICIOUS
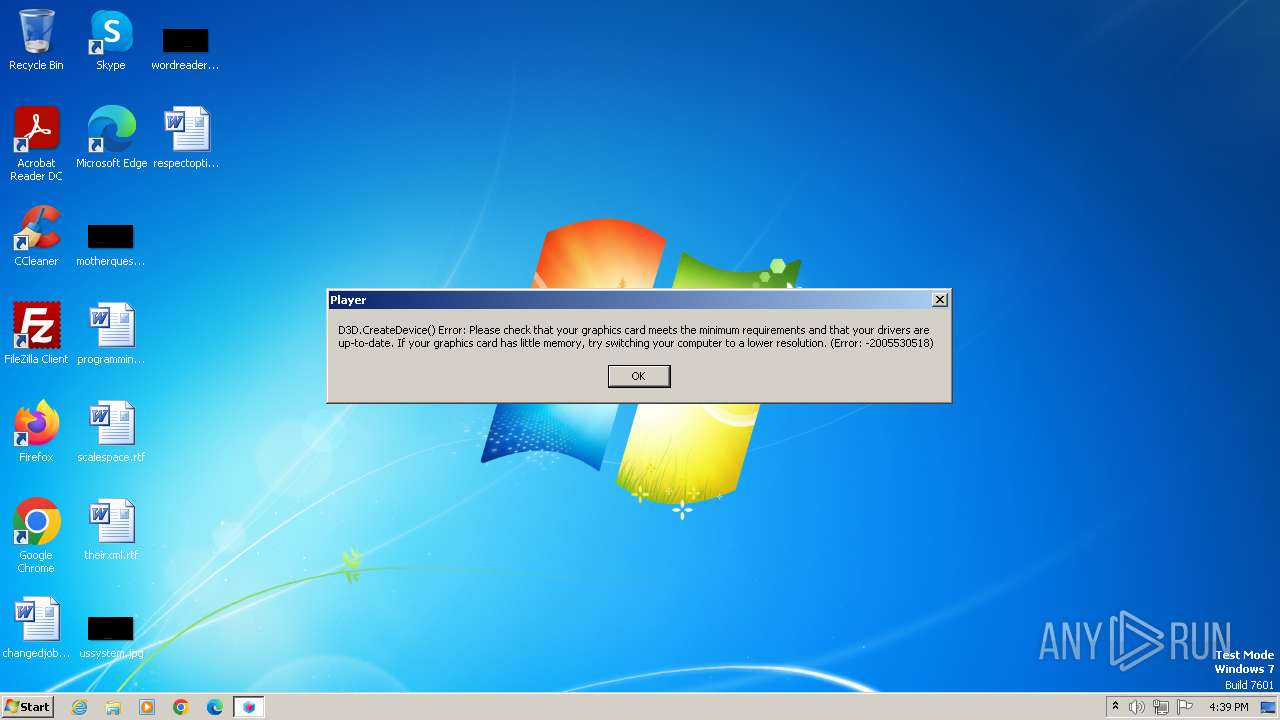
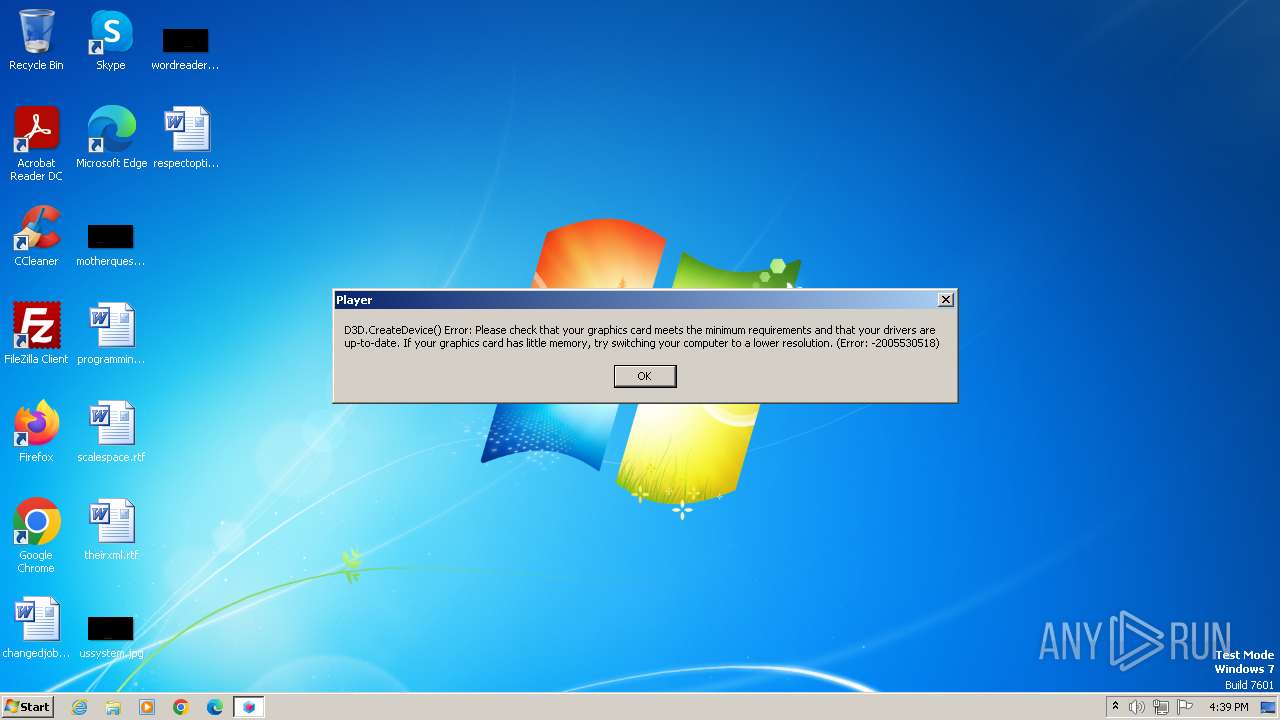
Drops the executable file immediately after the start
- Player.exe (PID: 3412)
Loads dropped or rewritten executable
- Player.exe (PID: 3412)
SUSPICIOUS
Reads the Internet Settings
- Player.exe (PID: 3412)
INFO
Checks supported languages
- Player.exe (PID: 3412)
Reads the computer name
- Player.exe (PID: 3412)
Checks proxy server information
- Player.exe (PID: 3412)
Create files in a temporary directory
- Player.exe (PID: 3412)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win32 EXE PECompact compressed (generic) (63.7) |
|---|---|---|
| .scr | | | Windows screen saver (20) |
| .exe | | | Win32 Executable (generic) (6.9) |
| .exe | | | Win16/32 Executable Delphi generic (3.1) |
| .exe | | | Generic Win/DOS Executable (3) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2012:01:18 17:33:17+01:00 |
| ImageFileCharacteristics: | No relocs, Executable, No line numbers, No symbols, Large address aware, Bytes reversed lo, 32-bit, Bytes reversed hi |
| PEType: | PE32 |
| LinkerVersion: | 2.25 |
| CodeSize: | 2596864 |
| InitializedDataSize: | 669696 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x27ae44 |
| OSVersion: | 5 |
| ImageVersion: | - |
| SubsystemVersion: | 5 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 1.0.0.0 |
| ProductVersionNumber: | 1.0.0.0 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | English (U.S.) |
| CharacterSet: | Windows, Latin1 |
| CompanyName: | - |
| FileDescription: | - |
| FileVersion: | 1.0.0.0 |
| InternalName: | - |
| LegalCopyright: | - |
| LegalTrademarks: | - |
| OriginalFileName: | - |
| ProductName: | - |
| ProductVersion: | 1.0.0.0 |
| Comments: | - |
Total processes
36
Monitored processes
1
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 3412 | "C:\Users\admin\AppData\Local\Temp\Player.exe" | C:\Users\admin\AppData\Local\Temp\Player.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Version: 1.0.0.0 Modules
| |||||||||||||||
Total events
280
Read events
280
Write events
0
Delete events
0
Modification events
Executable files
7
Suspicious files
0
Text files
21
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3412 | Player.exe | C:\Users\admin\AppData\Local\Temp\gm_ttt_51624\round_brick.d3d | text | |
MD5:A0F765180FB8D3CB3E9928E2B1950022 | SHA256:22EFA7399128A466EB5AE77E1C6B86DB309073F66B06FC09C9CE11788E0F8381 | |||
| 3412 | Player.exe | C:\Users\admin\AppData\Local\Temp\gm_ttt_51624\fence_middle.d3d | text | |
MD5:6AC5233AF7109F93A470010D4CB06180 | SHA256:DDA14BB01229EF16BBAB0CC04DA3050B99070CADD18527B706DA9F1CEEEC2BCF | |||
| 3412 | Player.exe | C:\Users\admin\AppData\Local\Temp\gm_ttt_51624\d3dmlf81141\d3dmlf.dll | executable | |
MD5:E5E1F22BD872AA3D93CE2037FD907209 | SHA256:AFE2F30C1B1EE726A917004E92AD1DCA45ACAEBEADA53214A737E5154FD4E734 | |||
| 3412 | Player.exe | C:\Users\admin\AppData\Local\Temp\gm_ttt_51624\fence_bottom.d3d | text | |
MD5:993778E84FFA78C353A040D64349D92E | SHA256:FD84D5ADA23E8DE072196A80E53C424E8F7C9FA2339A80078EDF3E047C1BF0DA | |||
| 3412 | Player.exe | C:\Users\admin\AppData\Local\Temp\gm_ttt_51624\corner_inv.d3d | text | |
MD5:5E656502C7034B6EE015D6681AA40E29 | SHA256:CBF6C59CECC51BD7418E9A0CEB93BA32CE2417B3F107CC71788813BF28C44847 | |||
| 3412 | Player.exe | C:\Users\admin\AppData\Local\Temp\gm_ttt_51624\dome.d3d | text | |
MD5:AC2FFFAD5B694D3C0BDD355C35D7684B | SHA256:F0578B8F3816D0919FF89972C47B8ACBAD0B922F41FC0256331DA388B8A3936B | |||
| 3412 | Player.exe | C:\Users\admin\AppData\Local\Temp\gm_ttt_51624\vent.d3d | text | |
MD5:124B7B888115F3CF892DC405D5C93E06 | SHA256:2E4D8BD1490C203DC01143E8D6B51AAEF822E8F91DD4A5E07F45B9DD92450918 | |||
| 3412 | Player.exe | C:\Users\admin\AppData\Local\Temp\gm_ttt_51624\gm82\gm82net.dll | executable | |
MD5:1BC86F3A814D1149C5030DE05F4E4E4D | SHA256:EB72731FC648631C3F031BBE1F889CE8602C7B394AAB7AA4CC14A89428A46D8F | |||
| 3412 | Player.exe | C:\Users\admin\AppData\Local\Temp\gm_ttt_51624\D3DX8.dll | executable | |
MD5:8C7C11DBF9CBA3BCB065201C560945E3 | SHA256:120C8E8FEF7EA02713D2966DBAD325D631323CB207B11CFA768AEEC48F5150CC | |||
| 3412 | Player.exe | C:\Users\admin\AppData\Local\Temp\gm_ttt_51624\arch.d3d | text | |
MD5:C33706BD9CF39340CF45ED3D896D945B | SHA256:BD4D310BA6C8F7161D86FB3E9E448F1AE83A4A3F52E15FFC5A10176D61B48512 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
4
DNS requests
0
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2656 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
1088 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |