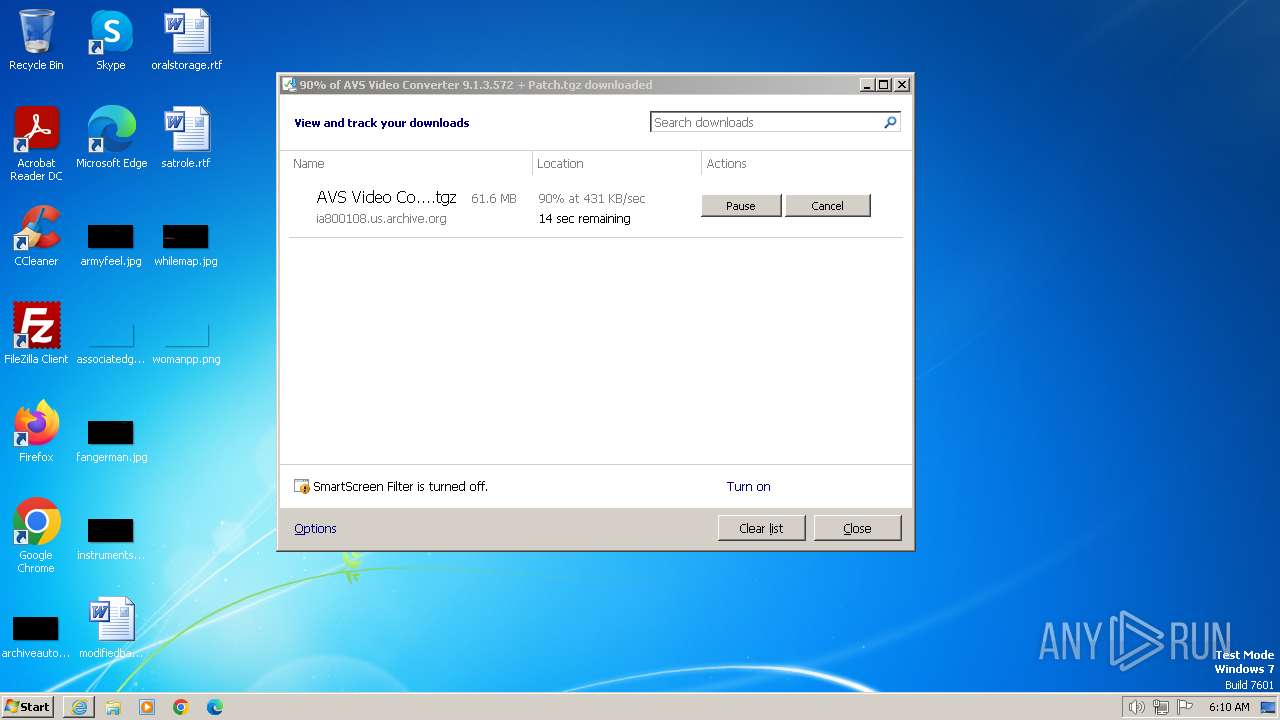
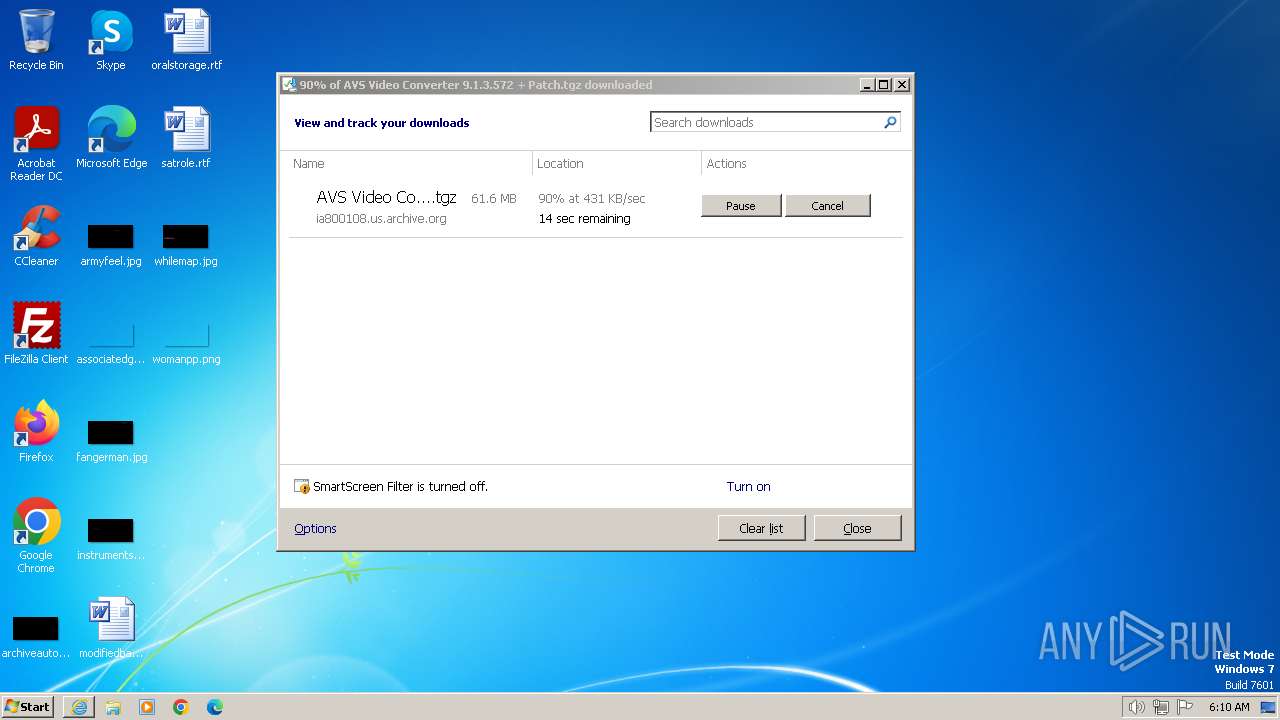
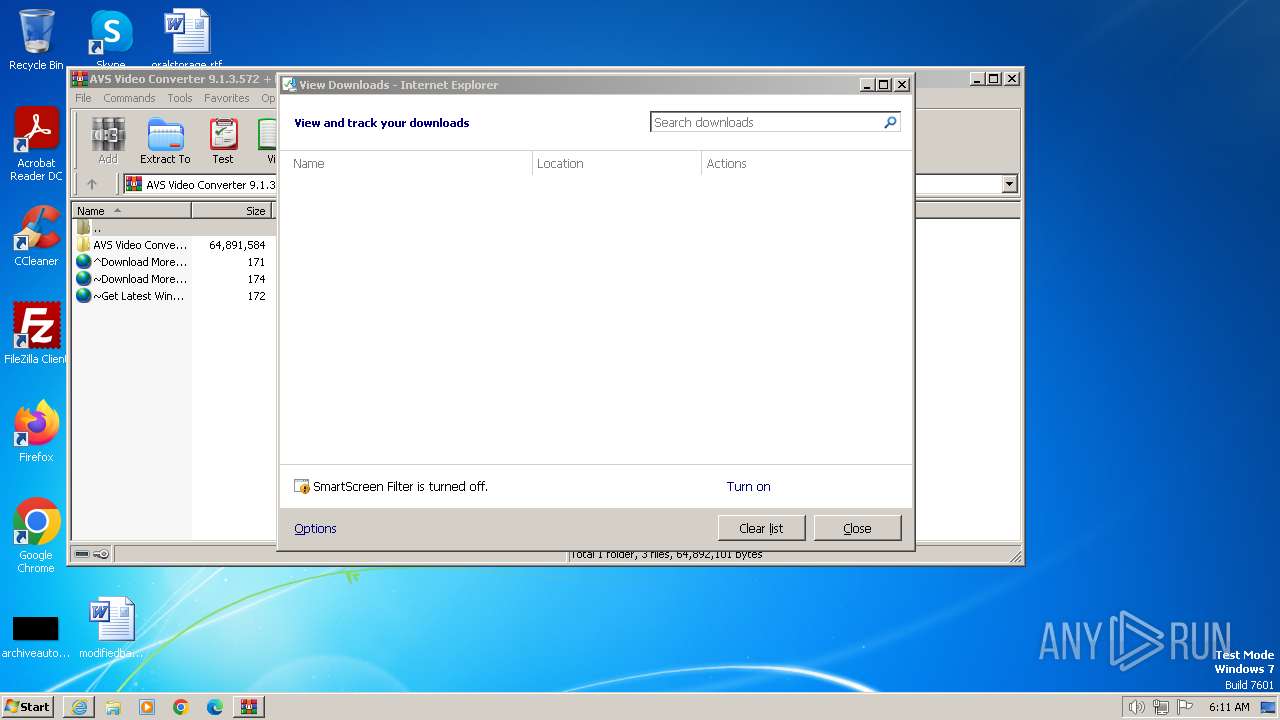
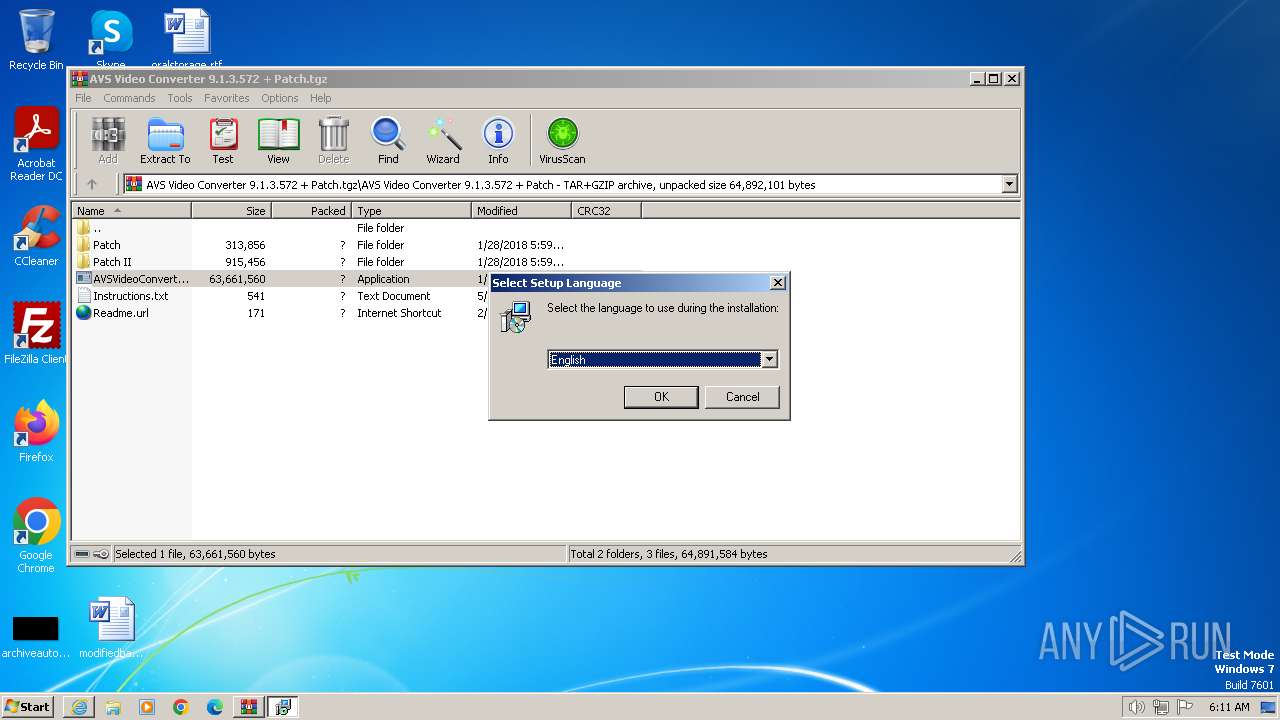
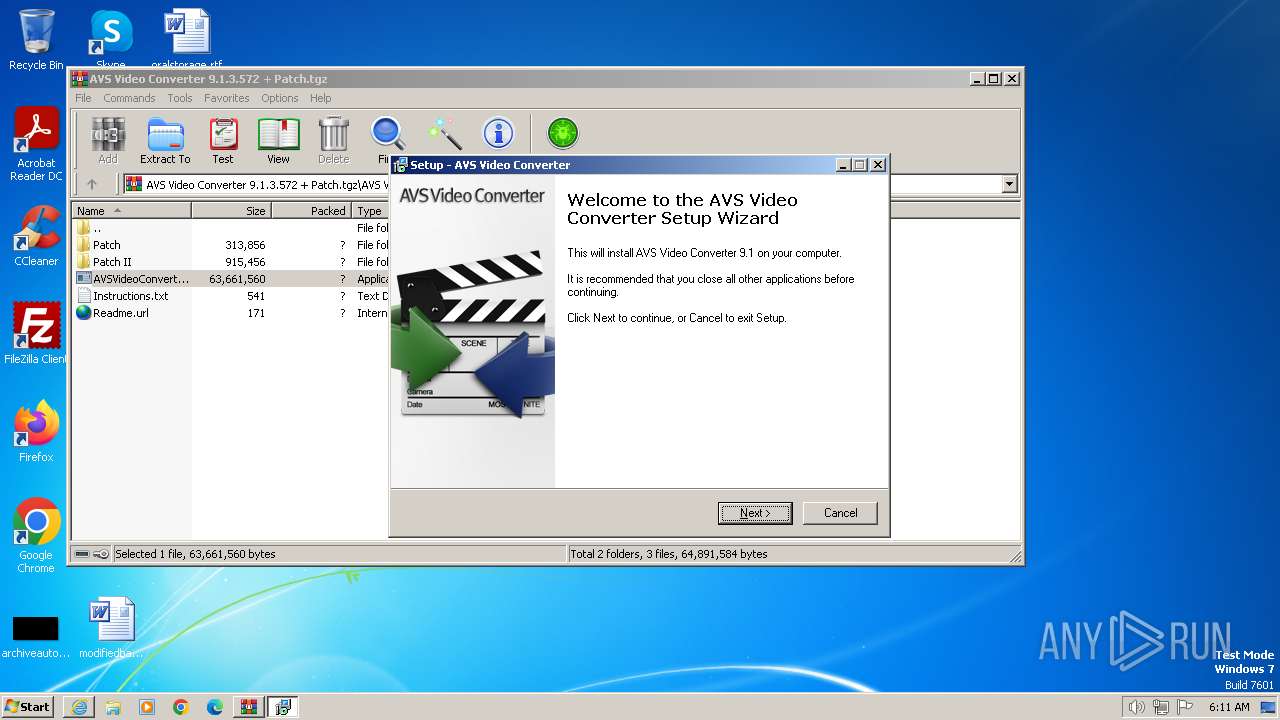
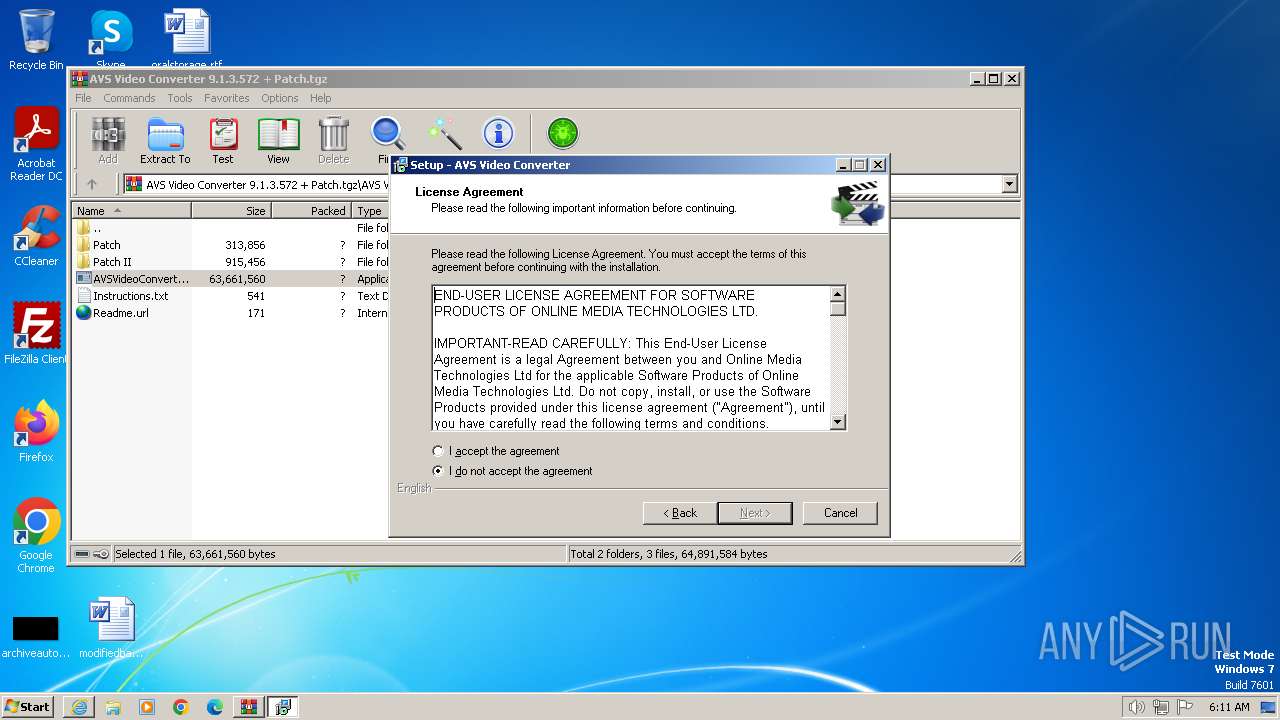
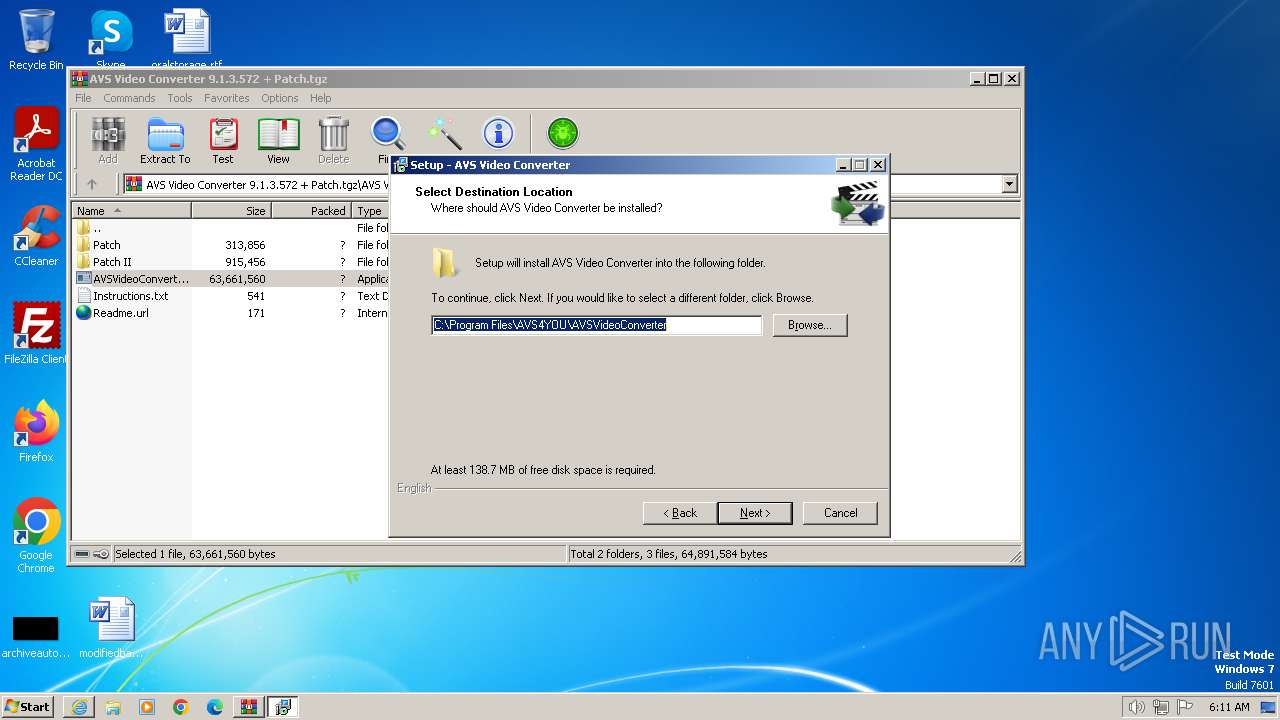
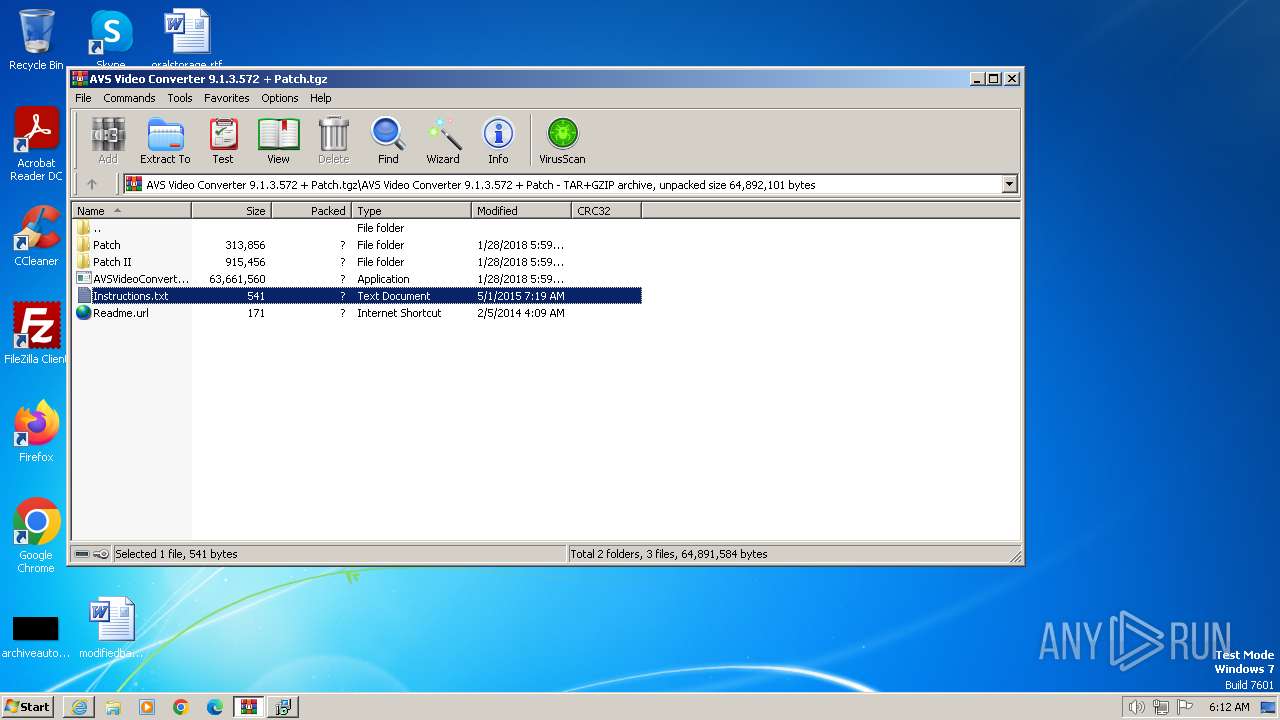
| URL: | https://archive.org/download/AVSVideoConverter9.1.3.572Patch100WorkingAxsoft_20180130/AVS%20Video%20Converter%209.1.3.572%20%2B%20Patch.tgz |
| Full analysis: | https://app.any.run/tasks/cad0b36b-ad91-4193-bd5a-3c4074988245 |
| Verdict: | Malicious activity |
| Analysis date: | January 15, 2024, 06:07:05 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MD5: | 3039E84FB5EF171B34278DF38B29C8F2 |
| SHA1: | 619EBE7729BC6641DFE7B44C89C957E5D47D50FD |
| SHA256: | 81F6D054912B2151AD271491407D0ACADC32A9ADD5F2A70AE3030CF4C6DCC465 |
| SSDEEP: | 3:N8MFXJ26U9QMBzU9GNU6MOMLdWY3d+eZMtxxb1TFynyf4b:2MFX+ZB4960gWpQxxdFynyfI |
MALICIOUS
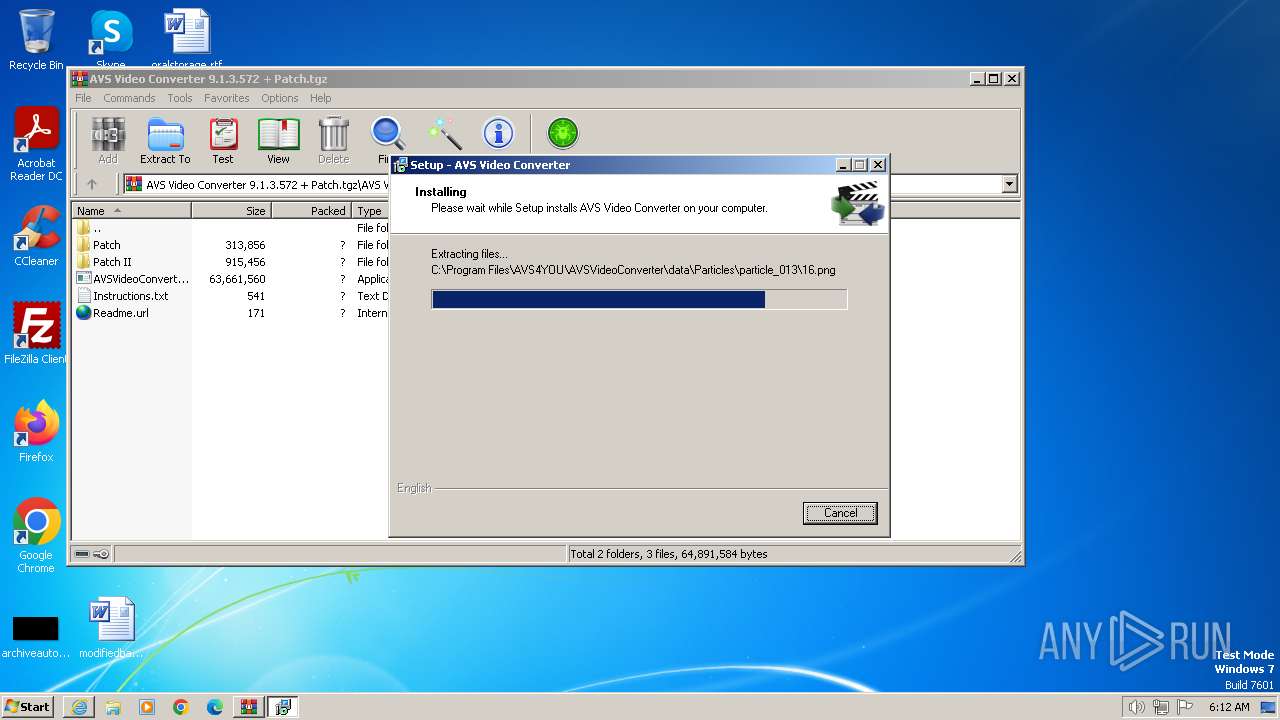
Drops the executable file immediately after the start
- AVSVideoConverter.exe (PID: 2788)
- setup.exe (PID: 2476)
- msiexec.exe (PID: 2860)
- setup.tmp (PID: 2524)
Creates a writable file in the system directory
- setup.tmp (PID: 2524)
SUSPICIOUS
Malware-specific behavior (creating "System.dll" in Temp)
- AVSVideoConverter.exe (PID: 2788)
Reads the Internet Settings
- AVSVideoConverter.exe (PID: 2788)
- setup.tmp (PID: 2524)
The process creates files with name similar to system file names
- AVSVideoConverter.exe (PID: 2788)
Executable content was dropped or overwritten
- setup.exe (PID: 2476)
- AVSVideoConverter.exe (PID: 2788)
- setup.tmp (PID: 2524)
- vcredist_x86.exe (PID: 2508)
Reads the Windows owner or organization settings
- setup.tmp (PID: 2524)
- msiexec.exe (PID: 2860)
Process drops legitimate windows executable
- setup.tmp (PID: 2524)
- msiexec.exe (PID: 2860)
Searches for installed software
- setup.tmp (PID: 2524)
Checks Windows Trust Settings
- msiexec.exe (PID: 2860)
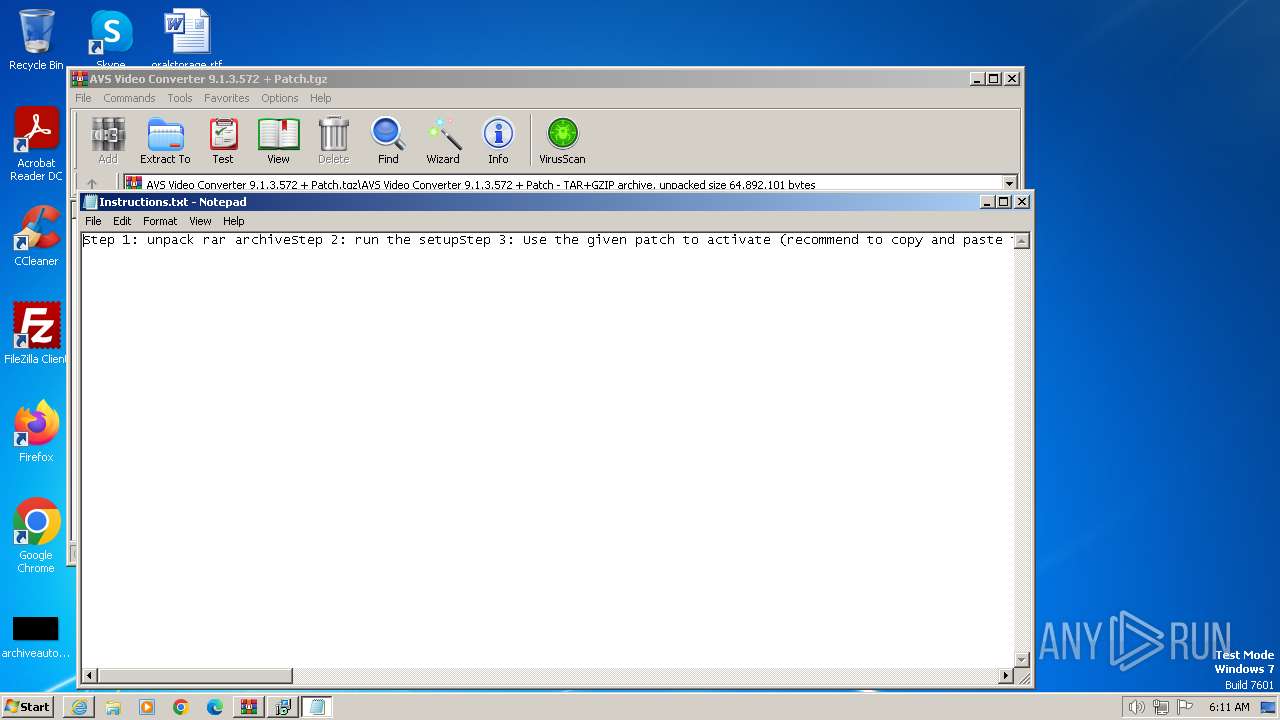
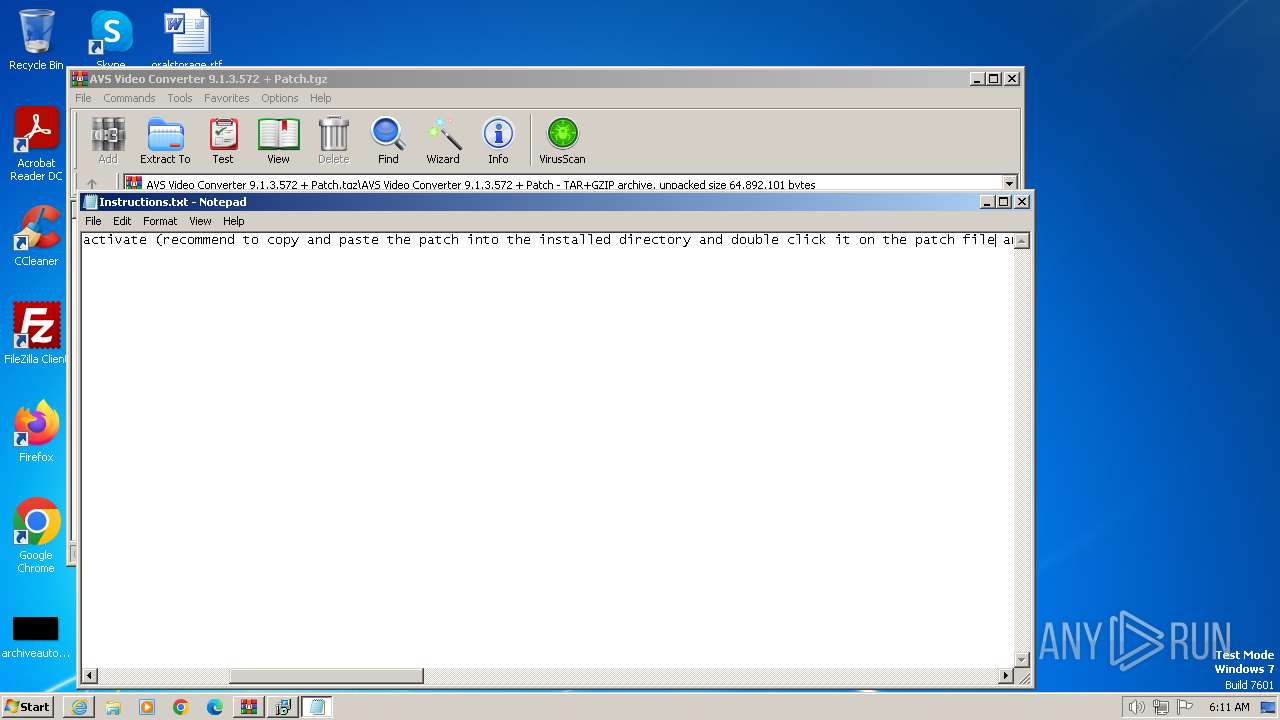
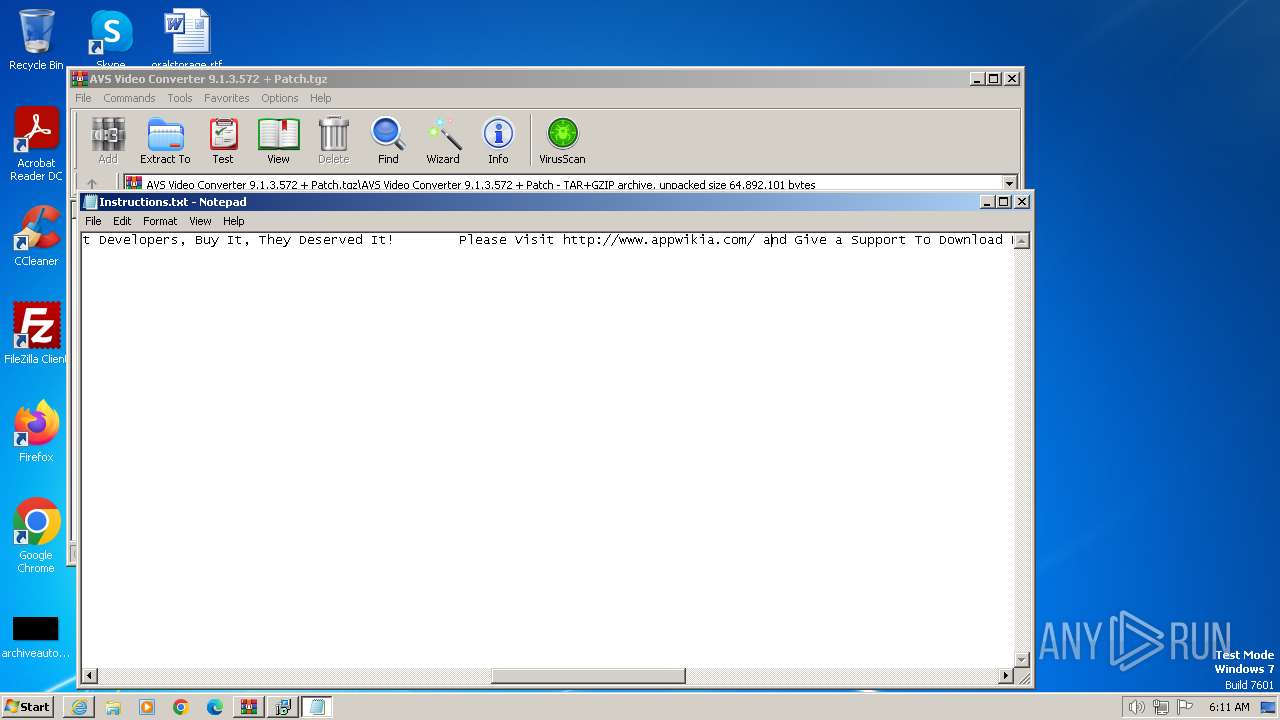
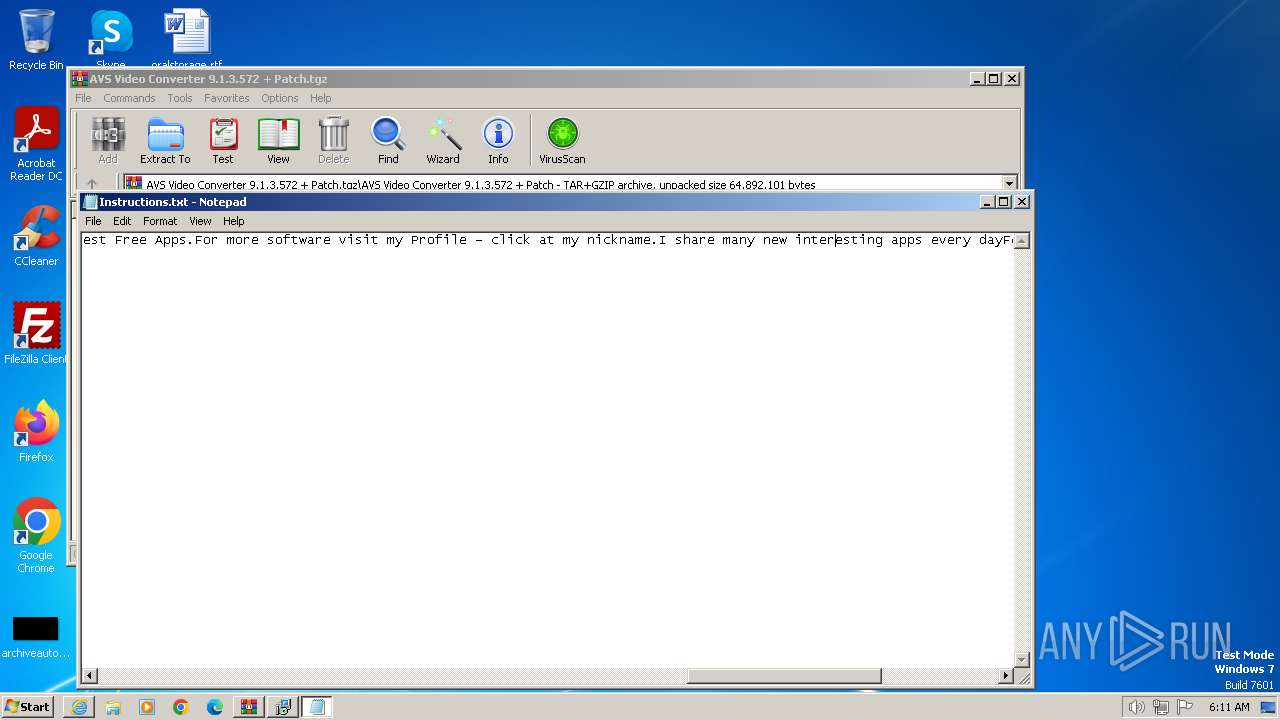
Start notepad (likely ransomware note)
- WinRAR.exe (PID: 552)
The process drops C-runtime libraries
- msiexec.exe (PID: 2860)
INFO
Manual execution by a user
- explorer.exe (PID: 2348)
Reads the computer name
- AVSVideoConverter.exe (PID: 2788)
- setup.tmp (PID: 2524)
- msiexec.exe (PID: 2860)
- msiexec.exe (PID: 1484)
Create files in a temporary directory
- AVSVideoConverter.exe (PID: 2788)
- setup.exe (PID: 2476)
- setup.tmp (PID: 2524)
- vcredist_x86.exe (PID: 2508)
- msiexec.exe (PID: 2860)
The process uses the downloaded file
- iexplore.exe (PID: 128)
- WinRAR.exe (PID: 552)
Checks supported languages
- AVSVideoConverter.exe (PID: 2788)
- setup.exe (PID: 2476)
- setup.tmp (PID: 2524)
- msiexec.exe (PID: 2860)
- AVSInstLauncher.exe (PID: 2516)
- vcredist_x86.exe (PID: 2508)
- msiexec.exe (PID: 1484)
Application launched itself
- iexplore.exe (PID: 128)
- msiexec.exe (PID: 2860)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 552)
- msiexec.exe (PID: 2860)
Drops the executable file immediately after the start
- WinRAR.exe (PID: 552)
Creates files in the program directory
- setup.tmp (PID: 2524)
Reads the machine GUID from the registry
- msiexec.exe (PID: 2860)
- msiexec.exe (PID: 1484)
- AVSVideoConverter.exe (PID: 2788)
Checks proxy server information
- AVSVideoConverter.exe (PID: 2788)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
56
Monitored processes
14
Malicious processes
6
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 128 | "C:\Program Files\Internet Explorer\iexplore.exe" "https://archive.org/download/AVSVideoConverter9.1.3.572Patch100WorkingAxsoft_20180130/AVS%20Video%20Converter%209.1.3.572%20%2B%20Patch.tgz" | C:\Program Files\Internet Explorer\iexplore.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 324 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:128 CREDAT:267521 /prefetch:2 | C:\Program Files\Internet Explorer\iexplore.exe | iexplore.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 552 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\PO2HN1X2\AVS Video Converter 9.1.3.572 + Patch.tgz" | C:\Program Files\WinRAR\WinRAR.exe | iexplore.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
| 980 | "C:\Users\admin\AppData\Local\Temp\Rar$EXa552.6082\AVS Video Converter 9.1.3.572 + Patch\AVSVideoConverter.exe" | C:\Users\admin\AppData\Local\Temp\Rar$EXa552.6082\AVS Video Converter 9.1.3.572 + Patch\AVSVideoConverter.exe | — | WinRAR.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 3221226540 Modules
| |||||||||||||||
| 1484 | C:\Windows\system32\MsiExec.exe -Embedding D9A88EB6B78949CF76856EC1D0A063DB | C:\Windows\System32\msiexec.exe | — | msiexec.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows® installer Exit code: 0 Version: 5.0.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2348 | "C:\Windows\explorer.exe" | C:\Windows\explorer.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Explorer Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2476 | C:\Users\admin\AppData\Local\Temp\nslC3EA.tmp\setup.exe | C:\Users\admin\AppData\Local\Temp\nslC3EA.tmp\setup.exe | AVSVideoConverter.exe | ||||||||||||
User: admin Company: Online Media Technologies Ltd. Integrity Level: HIGH Description: AVS Video Converter Setup Exit code: 0 Version: 9.1.3.572 Modules
| |||||||||||||||
| 2492 | msiexec /i vcredist.msi /qn | C:\Windows\System32\msiexec.exe | — | vcredist_x86.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows® installer Exit code: 0 Version: 5.0.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2508 | "C:\Program Files\AVS4YOU\AVSVideoConverter\vcredist_x86.exe" /q:a /c:"msiexec /i vcredist.msi /qn" | C:\Program Files\AVS4YOU\AVSVideoConverter\vcredist_x86.exe | AVSInstLauncher.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Win32 Cabinet Self-Extractor Exit code: 0 Version: 6.00.2900.2180 (xpsp_sp2_rtm.040803-2158) Modules
| |||||||||||||||
| 2516 | "C:\Program Files\AVS4YOU\AVSVideoConverter\AVSInstLauncher.exe" C:\Program Files\AVS4YOU\AVSVideoConverter\vcredist_x86.exe /q:a /c:"msiexec /i vcredist.msi /qn" | C:\Program Files\AVS4YOU\AVSVideoConverter\AVSInstLauncher.exe | — | setup.tmp | |||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
Total events
28 966
Read events
28 814
Write events
140
Delete events
12
Modification events
| (PID) Process: | (128) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPDaysSinceLastAutoMigration |
Value: 0 | |||
| (PID) Process: | (128) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPLastLaunchHighDateTime |
Value: 30847387 | |||
| (PID) Process: | (128) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateHighDateTime |
Value: 30847437 | |||
| (PID) Process: | (128) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (128) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (128) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Main |
| Operation: | write | Name: | CompatibilityFlags |
Value: 0 | |||
| (PID) Process: | (128) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (128) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (128) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
| (PID) Process: | (128) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 0 | |||
Executable files
318
Suspicious files
39
Text files
620
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 324 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\EB2C4AB8B68FFA4B7733A9139239A396_D76DB901EE986B889F30D8CC06229E2D | binary | |
MD5:128EBD1FD036D7CC72CE50F8DF6E0E90 | SHA256:46725815855BED4E3ADCE6DFC32BC39BA0CA6E42EFDC7B4845B8799EF3469A18 | |||
| 324 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\57C8EDB95DF3F0AD4EE2DC2B8CFD4157 | binary | |
MD5:F5952E639987E4269D72C5E3E484B947 | SHA256:C89A5DD36160618ECC289E75318FB88DC8F091925AA3A70B80B9DE5881BD848A | |||
| 324 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\223DE96EE265046957A660ED7C9DD9E7_EFF9B9BA98DEAA773F261FA85A0B1771 | binary | |
MD5:DBDDD6B4C7659C111399F9A9A4F26C44 | SHA256:70A10920A87DBBF4129C50EDCAE557190C910ED19E547807C4E848F760B8A03B | |||
| 128 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Internet Explorer\VersionManager\ver72F9.tmp | xml | |
MD5:CBD0581678FA40F0EDCBC7C59E0CAD10 | SHA256:159BD4343F344A08F6AF3B716B6FA679859C1BD1D7030D26FF5EF0255B86E1D9 | |||
| 128 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\7423F88C7F265F0DEFC08EA88C3BDE45_AA1E8580D4EBC816148CE81268683776 | binary | |
MD5:8CACCAEFF2F45108CD90AF50D30CFD18 | SHA256:DBA60BF3F9E91FE505E2F6AA9E4DC90C87E08AD67DCA3058B70431A33526831C | |||
| 128 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\7423F88C7F265F0DEFC08EA88C3BDE45_AA1E8580D4EBC816148CE81268683776 | der | |
MD5:EFBD8A07FC0323406B87FE9482489647 | SHA256:351BFA58FA50D54BDFBA5C6A37C4F8F9C6A88B979E1379EC0B0900B4EF0E4E19 | |||
| 128 | iexplore.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Cookies\45Q7O3I4.txt | text | |
MD5:BCEB3F865E798C7425C3B67FA4CFBEAC | SHA256:40B9BEA4BBDEC56A31AC7A0D99773F847DBA119C0F60BB6D691A513407738A03 | |||
| 128 | iexplore.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Cookies\GQRHRC67.txt | text | |
MD5:EE7C201D601E1886DC6178390D4D6D83 | SHA256:F50DDBFDC2ECC8984EE0A73C00EB3FC8460CD73A1D4480C4855C9DB6C4C3E373 | |||
| 324 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\MFAQUS6V\AVS%20Video%20Converter%209.1.3.572%20+%20Patch[1].tgz | compressed | |
MD5:E0AA625D23F0BC1761E5E98A3C2230C4 | SHA256:0C3536DE4DF740794D005B1E356552C6D185D94058BC4E17FEC2CBD579EADB62 | |||
| 128 | iexplore.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Cookies\O6O5618I.txt | text | |
MD5:FDA4A449C373942E69C247BCAB22D68F | SHA256:FF187355A19BD936908FB478B471D9F72465E74A4D2E698AB05157D390A5E616 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
12
TCP/UDP connections
25
DNS requests
17
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
324 | iexplore.exe | GET | 200 | 192.124.249.22:80 | http://ocsp.godaddy.com//MEQwQjBAMD4wPDAJBgUrDgMCGgUABBTkIInKBAzXkF0Qh0pel3lfHJ9GPAQU0sSw0pHUTBFxs2HLPaH%2B3ahq1OMCAxvnFQ%3D%3D | unknown | binary | 1.98 Kb | unknown |
324 | iexplore.exe | GET | 200 | 192.124.249.22:80 | http://ocsp.godaddy.com//MEIwQDA%2BMDwwOjAJBgUrDgMCGgUABBQdI2%2BOBkuXH93foRUj4a7lAr4rGwQUOpqFBxBnKLbv9r0FQW4gwZTaD94CAQc%3D | unknown | binary | 2.01 Kb | unknown |
128 | iexplore.exe | GET | 304 | 23.216.77.55:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?ca04fd3518ca5bb7 | unknown | — | — | unknown |
1080 | svchost.exe | GET | 304 | 23.216.77.81:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?0754c686571bd23f | unknown | — | — | unknown |
128 | iexplore.exe | GET | 304 | 23.216.77.55:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?08d91df001b427ad | unknown | — | — | unknown |
128 | iexplore.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEA177el9ggmWelJjG4vdGL0%3D | unknown | binary | 471 b | unknown |
128 | iexplore.exe | GET | 304 | 23.216.77.55:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?a85e8d0c2f0a71a5 | unknown | — | — | unknown |
128 | iexplore.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | binary | 471 b | unknown |
128 | iexplore.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | binary | 471 b | unknown |
324 | iexplore.exe | GET | 200 | 23.216.77.45:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?53bfb7cf8a6cf97e | unknown | compressed | 4.66 Kb | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
324 | iexplore.exe | 207.241.224.2:443 | archive.org | INTERNET-ARCHIVE | US | malicious |
324 | iexplore.exe | 23.216.77.45:80 | ctldl.windowsupdate.com | Akamai International B.V. | DE | unknown |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1080 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
324 | iexplore.exe | 192.124.249.22:80 | ocsp.godaddy.com | SUCURI-SEC | US | unknown |
324 | iexplore.exe | 207.241.232.18:443 | ia800108.us.archive.org | INTERNET-ARCHIVE | US | unknown |
128 | iexplore.exe | 152.199.19.161:443 | iecvlist.microsoft.com | EDGECAST | US | whitelisted |
128 | iexplore.exe | 23.216.77.55:80 | ctldl.windowsupdate.com | Akamai International B.V. | DE | unknown |
128 | iexplore.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
archive.org |
| whitelisted |
ctldl.windowsupdate.com |
| whitelisted |
ocsp.godaddy.com |
| whitelisted |
ia800108.us.archive.org |
| unknown |
iecvlist.microsoft.com |
| whitelisted |
r20swj13mr.microsoft.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
ieonline.microsoft.com |
| whitelisted |
go.microsoft.com |
| whitelisted |
www.msn.com |
| whitelisted |