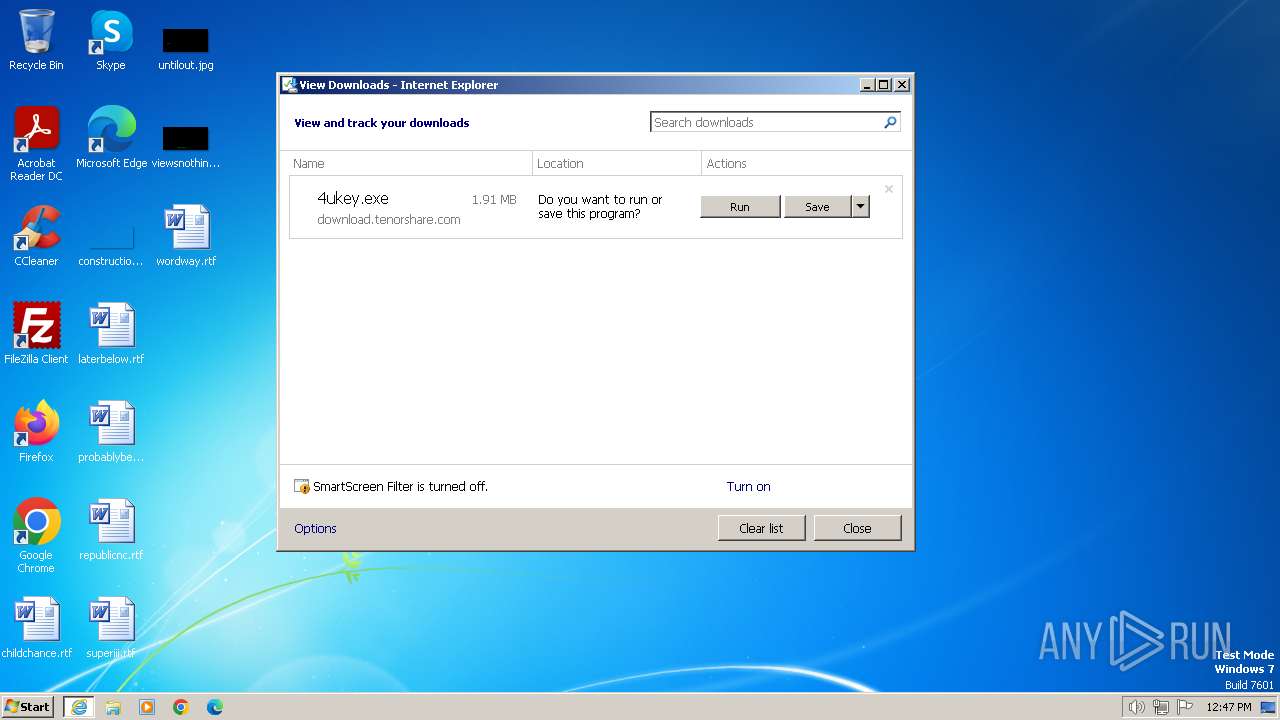
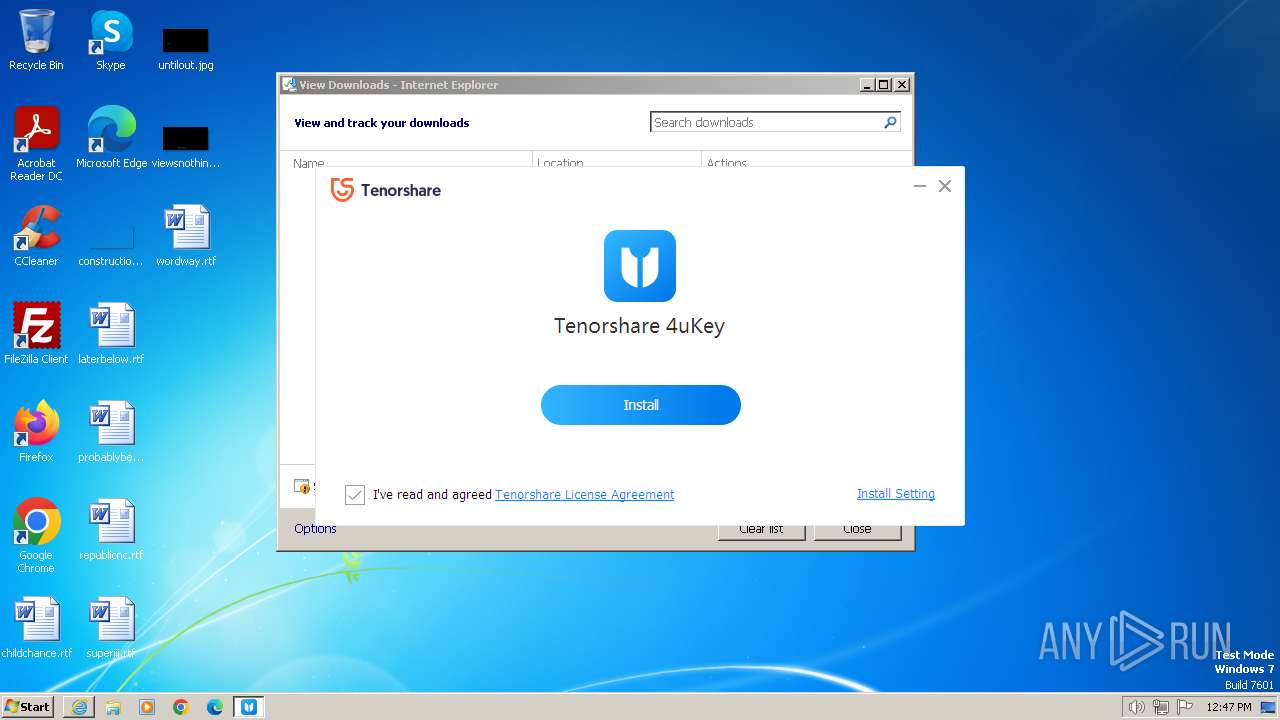
| URL: | https://download.tenorshare.com/downloads/4ukey_1002.exe |
| Full analysis: | https://app.any.run/tasks/6680c324-485b-419e-9619-a8d70d8fd813 |
| Verdict: | Malicious activity |
| Analysis date: | April 11, 2024, 11:46:53 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MD5: | BC5EB5A81152F97942B4E838EE06C13E |
| SHA1: | A13170A40DCE2FAFE4397B907225D680C6A00616 |
| SHA256: | 81F02C8160C9F98C4639250C1CCE9E80DFB01EC07C068F8BCEC1B80BAB29A761 |
| SSDEEP: | 3:N8SElzILGKxKXKRVdSA:2SKELGNa5SA |
MALICIOUS
Connects to the CnC server
- 4ukey.exe (PID: 2904)
Drops the executable file immediately after the start
- 4ukeyforios_ts_3.5.5.exe (PID: 4084)
- 4ukeyforios_ts_3.5.5.tmp (PID: 268)
- drvinst.exe (PID: 3928)
- drvinst.exe (PID: 2436)
Creates a writable file in the system directory
- drvinst.exe (PID: 3928)
- drvinst.exe (PID: 2436)
SUSPICIOUS
Reads the Internet Settings
- 4ukey.exe (PID: 2904)
- 4ukeyforios_ts_3.5.5.tmp (PID: 268)
- Start.exe (PID: 3592)
- Tenorshare 4uKey.exe (PID: 3644)
- WMIC.exe (PID: 3080)
- WMIC.exe (PID: 3780)
- WMIC.exe (PID: 2416)
- WMIC.exe (PID: 1504)
- WMIC.exe (PID: 1880)
- WMIC.exe (PID: 3436)
- WMIC.exe (PID: 2932)
Reads security settings of Internet Explorer
- 4ukey.exe (PID: 2904)
- 4ukeyforios_ts_3.5.5.tmp (PID: 268)
- Start.exe (PID: 3592)
- Tenorshare 4uKey.exe (PID: 3644)
Reads settings of System Certificates
- 4ukey.exe (PID: 2904)
- Tenorshare 4uKey.exe (PID: 3644)
Checks for external IP
- 4ukey.exe (PID: 2904)
Executable content was dropped or overwritten
- 4ukeyforios_ts_3.5.5.exe (PID: 4084)
- 4ukeyforios_ts_3.5.5.tmp (PID: 268)
- PnPutil.exe (PID: 2960)
- drvinst.exe (PID: 3928)
- drvinst.exe (PID: 2436)
- PnPutil.exe (PID: 2652)
Reads the Windows owner or organization settings
- 4ukeyforios_ts_3.5.5.tmp (PID: 268)
Uses TASKKILL.EXE to kill process
- cmd.exe (PID: 752)
Starts CMD.EXE for commands execution
- 4ukeyforios_ts_3.5.5.tmp (PID: 268)
- Tenorshare 4uKey.exe (PID: 3644)
Process drops legitimate windows executable
- 4ukeyforios_ts_3.5.5.tmp (PID: 268)
- PnPutil.exe (PID: 2652)
- drvinst.exe (PID: 2436)
The process drops C-runtime libraries
- 4ukeyforios_ts_3.5.5.tmp (PID: 268)
Non-standard symbols in registry
- 4ukeyforios_ts_3.5.5.tmp (PID: 268)
Drops a system driver (possible attempt to evade defenses)
- 4ukeyforios_ts_3.5.5.tmp (PID: 268)
- PnPutil.exe (PID: 2960)
- drvinst.exe (PID: 3928)
- PnPutil.exe (PID: 2652)
- drvinst.exe (PID: 2436)
Creates a software uninstall entry
- 4ukey.exe (PID: 2904)
- Tenorshare 4uKey.exe (PID: 3644)
Drops 7-zip archiver for unpacking
- 4ukeyforios_ts_3.5.5.tmp (PID: 268)
Searches for installed software
- Tenorshare 4uKey.exe (PID: 3644)
Changes Internet Explorer settings (feature browser emulation)
- Tenorshare 4uKey.exe (PID: 3644)
Starts SC.EXE for service management
- cmd.exe (PID: 3504)
- cmd.exe (PID: 3228)
- cmd.exe (PID: 3492)
- cmd.exe (PID: 3944)
- cmd.exe (PID: 2240)
- cmd.exe (PID: 3196)
- cmd.exe (PID: 2792)
Uses WMIC.EXE to obtain data on the base board management (motherboard or system board)
- Tenorshare 4uKey.exe (PID: 3644)
Checks Windows Trust Settings
- Tenorshare 4uKey.exe (PID: 3644)
- 4ukey.exe (PID: 2904)
- drvinst.exe (PID: 3928)
- drvinst.exe (PID: 2436)
Creates files in the driver directory
- drvinst.exe (PID: 3928)
- drvinst.exe (PID: 2436)
INFO
Executable content was dropped or overwritten
- iexplore.exe (PID: 3092)
- iexplore.exe (PID: 2120)
Modifies the phishing filter of IE
- iexplore.exe (PID: 2120)
Drops the executable file immediately after the start
- iexplore.exe (PID: 3092)
- iexplore.exe (PID: 2120)
- PnPutil.exe (PID: 2960)
- PnPutil.exe (PID: 2652)
The process uses the downloaded file
- iexplore.exe (PID: 2120)
Application launched itself
- iexplore.exe (PID: 2120)
- msedge.exe (PID: 3896)
- msedge.exe (PID: 2292)
Reads the computer name
- 4ukey.exe (PID: 2904)
- 4ukeyforios_ts_3.5.5.tmp (PID: 268)
- Start.exe (PID: 3592)
- Tenorshare 4uKey.exe (PID: 3644)
- AppleMobileDeviceProcess.exe (PID: 2584)
- Monitor.exe (PID: 3948)
- mDNSResponder.exe (PID: 924)
- CheckErrorx86.exe (PID: 3100)
- infInstallx86.exe (PID: 3852)
- infInstallx86.exe (PID: 1848)
- drvinst.exe (PID: 3928)
- drvinst.exe (PID: 2436)
Checks supported languages
- 4ukey.exe (PID: 2904)
- 4ukeyforios_ts_3.5.5.tmp (PID: 268)
- 4ukeyforios_ts_3.5.5.exe (PID: 4084)
- Start.exe (PID: 3592)
- Tenorshare 4uKey.exe (PID: 3644)
- Monitor.exe (PID: 3948)
- mDNSResponder.exe (PID: 924)
- AppleMobileDeviceProcess.exe (PID: 2584)
- CheckErrorx86.exe (PID: 3100)
- infInstallx86.exe (PID: 3852)
- infInstallx86.exe (PID: 1848)
- infInstallx86.exe (PID: 3364)
- drvinst.exe (PID: 3928)
- infInstallx86.exe (PID: 2304)
- drvinst.exe (PID: 2436)
Reads Environment values
- 4ukey.exe (PID: 2904)
- Tenorshare 4uKey.exe (PID: 3644)
Checks proxy server information
- 4ukey.exe (PID: 2904)
- Tenorshare 4uKey.exe (PID: 3644)
Create files in a temporary directory
- 4ukey.exe (PID: 2904)
- 4ukeyforios_ts_3.5.5.exe (PID: 4084)
- 4ukeyforios_ts_3.5.5.tmp (PID: 268)
- Tenorshare 4uKey.exe (PID: 3644)
- PnPutil.exe (PID: 2960)
- PnPutil.exe (PID: 2652)
Creates files or folders in the user directory
- 4ukey.exe (PID: 2904)
- Tenorshare 4uKey.exe (PID: 3644)
Reads the machine GUID from the registry
- 4ukey.exe (PID: 2904)
- Tenorshare 4uKey.exe (PID: 3644)
- drvinst.exe (PID: 3928)
- drvinst.exe (PID: 2436)
Reads the software policy settings
- 4ukey.exe (PID: 2904)
- Tenorshare 4uKey.exe (PID: 3644)
- drvinst.exe (PID: 3928)
- drvinst.exe (PID: 2436)
Creates files in the program directory
- 4ukey.exe (PID: 2904)
- 4ukeyforios_ts_3.5.5.tmp (PID: 268)
- Tenorshare 4uKey.exe (PID: 3644)
- Start.exe (PID: 3592)
- AppleMobileDeviceProcess.exe (PID: 2584)
Dropped object may contain TOR URL's
- 4ukeyforios_ts_3.5.5.tmp (PID: 268)
Creates a software uninstall entry
- 4ukeyforios_ts_3.5.5.tmp (PID: 268)
Manual execution by a user
- msedge.exe (PID: 2292)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
121
Monitored processes
55
Malicious processes
9
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 268 | "C:\Users\admin\AppData\Local\Temp\is-CI17P.tmp\4ukeyforios_ts_3.5.5.tmp" /SL5="$140180,105369235,284672,C:\Users\admin\AppData\Local\Temp\4ukeyforios_ts\4ukeyforios_ts_3.5.5.exe" /VERYSILENT /SP- /NORESTART /DIR="C:\Program Files\Tenorshare\Tenorshare 4uKey\" /LANG=en /LOG="C:\Users\admin\AppData\Local\Temp\Tenorshare 4uKey_Setup_20240411124817.log" /sptrack null | C:\Users\admin\AppData\Local\Temp\is-CI17P.tmp\4ukeyforios_ts_3.5.5.tmp | 4ukeyforios_ts_3.5.5.exe | ||||||||||||
User: admin Integrity Level: HIGH Description: Setup/Uninstall Exit code: 0 Version: 51.1052.0.0 Modules
| |||||||||||||||
| 752 | "C:\Windows\system32\cmd.exe" /c taskkill /f /t /im "Tenorshare 4uKey.exe" | C:\Windows\System32\cmd.exe | — | 4ukeyforios_ts_3.5.5.tmp | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 128 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 908 | sc start winmgmt | C:\Windows\System32\sc.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: A tool to aid in developing services for WindowsNT Exit code: 1056 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 924 | "C:\Program Files\Tenorshare\Tenorshare 4uKey\mdns\mDNSResponder.exe" -server | C:\Program Files\Tenorshare\Tenorshare 4uKey\mdns\mDNSResponder.exe | Tenorshare 4uKey.exe | ||||||||||||
User: admin Company: Apple Inc. Integrity Level: HIGH Description: Bonjour Service Version: 3,1,0,1 Modules
| |||||||||||||||
| 980 | "C:\Program Files\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=network.mojom.NetworkService --lang=en-US --service-sandbox-type=none --mojo-platform-channel-handle=1560 --field-trial-handle=1340,i,525743247729784516,639622648425630400,131072 /prefetch:3 | C:\Program Files\Microsoft\Edge\Application\msedge.exe | msedge.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Edge Version: 109.0.1518.115 Modules
| |||||||||||||||
| 1504 | wmic BaseBoard get SerialNumber | C:\Windows\System32\wbem\WMIC.exe | — | Tenorshare 4uKey.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: WMI Commandline Utility Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1548 | sc start winmgmt | C:\Windows\System32\sc.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: A tool to aid in developing services for WindowsNT Exit code: 1056 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1848 | "C:\Program Files\Tenorshare\Tenorshare 4uKey\iTunesRepairResources\x86\infInstallx86.exe" -d "C:\Program Files\Tenorshare\Tenorshare 4uKey\iTunesRepairResources\x86\NetDrivers86\netaapl.inf" | C:\Program Files\Tenorshare\Tenorshare 4uKey\iTunesRepairResources\x86\infInstallx86.exe | — | Tenorshare 4uKey.exe | |||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 1880 | wmic BaseBoard get SerialNumber | C:\Windows\System32\wbem\WMIC.exe | — | Tenorshare 4uKey.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: WMI Commandline Utility Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1972 | "C:\Program Files\Microsoft\Edge\Application\msedge.exe" --type=crashpad-handler "--user-data-dir=C:\Users\admin\AppData\Local\Microsoft\Edge\User Data" /prefetch:7 --monitor-self-annotation=ptype=crashpad-handler "--database=C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Crashpad" "--metrics-dir=C:\Users\admin\AppData\Local\Microsoft\Edge\User Data" --annotation=IsOfficialBuild=1 --annotation=channel= --annotation=chromium-version=109.0.5414.149 "--annotation=exe=C:\Program Files\Microsoft\Edge\Application\msedge.exe" --annotation=plat=Win32 "--annotation=prod=Microsoft Edge" --annotation=ver=109.0.1518.115 --initial-client-data=0xc8,0xcc,0xd0,0x9c,0xdc,0x6043f598,0x6043f5a8,0x6043f5b4 | C:\Program Files\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Edge Version: 109.0.1518.115 Modules
| |||||||||||||||
Total events
48 731
Read events
48 361
Write events
323
Delete events
47
Modification events
| (PID) Process: | (2120) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPDaysSinceLastAutoMigration |
Value: 1 | |||
| (PID) Process: | (2120) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPLastLaunchLowDateTime |
Value: | |||
| (PID) Process: | (2120) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPLastLaunchHighDateTime |
Value: 31099909 | |||
| (PID) Process: | (2120) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateLowDateTime |
Value: 157050390 | |||
| (PID) Process: | (2120) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateHighDateTime |
Value: 31099910 | |||
| (PID) Process: | (2120) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (2120) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (2120) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (2120) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Main |
| Operation: | write | Name: | CompatibilityFlags |
Value: 0 | |||
| (PID) Process: | (2120) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
Executable files
534
Suspicious files
98
Text files
161
Unknown types
49
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3092 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\57C8EDB95DF3F0AD4EE2DC2B8CFD4157 | binary | |
MD5:— | SHA256:— | |||
| 3092 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\24BD96D5497F70B3F510A6B53CD43F3E_3A89246FB90C5EE6620004F1AE0EB0EA | der | |
MD5:— | SHA256:— | |||
| 3092 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\24BD96D5497F70B3F510A6B53CD43F3E_3A89246FB90C5EE6620004F1AE0EB0EA | binary | |
MD5:— | SHA256:— | |||
| 3092 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\CAF4703619713E3F18D8A9D5D88D6288_F2DAF19C1F776537105D08FC8D978464 | der | |
MD5:— | SHA256:— | |||
| 3092 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\CAF4703619713E3F18D8A9D5D88D6288_F2DAF19C1F776537105D08FC8D978464 | binary | |
MD5:— | SHA256:— | |||
| 3092 | iexplore.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Cookies\Low\1QNN6R31.txt | text | |
MD5:— | SHA256:— | |||
| 3092 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\MFAQUS6V\4ukey[1].exe | executable | |
MD5:— | SHA256:— | |||
| 3092 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\B6QGX7LP\4ukey.exe.ygwddy5.partial | executable | |
MD5:— | SHA256:— | |||
| 2120 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\~DF0F99434424E21700.TMP | binary | |
MD5:— | SHA256:— | |||
| 2120 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Internet Explorer\Recovery\Active\{351B6331-F7F9-11EE-AE0A-12A9866C77DE}.dat | binary | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
61
TCP/UDP connections
171
DNS requests
68
Threats
9
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3092 | iexplore.exe | GET | 304 | 199.232.214.172:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?bd117e088266f0f9 | unknown | — | — | unknown |
2904 | 4ukey.exe | POST | 200 | 142.250.185.174:80 | http://www.google-analytics.com/collect | unknown | — | — | unknown |
2904 | 4ukey.exe | POST | 200 | 142.250.185.174:80 | http://www.google-analytics.com/collect | unknown | — | — | unknown |
2904 | 4ukey.exe | POST | 200 | 142.250.185.174:80 | http://www.google-analytics.com/collect | unknown | — | — | unknown |
2904 | 4ukey.exe | POST | 200 | 142.250.185.174:80 | http://www.google-analytics.com/collect | unknown | — | — | unknown |
2904 | 4ukey.exe | POST | 200 | 142.250.185.174:80 | http://www.google-analytics.com/collect | unknown | — | — | unknown |
3092 | iexplore.exe | GET | 304 | 199.232.210.172:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?545e1839169dd0e6 | unknown | — | — | unknown |
2904 | 4ukey.exe | GET | 304 | 199.232.210.172:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?c0741a00714f912a | unknown | — | — | unknown |
2904 | 4ukey.exe | GET | 301 | 104.17.192.141:80 | http://www.tenorshare.com/downloads/service/softwarelog.txt | unknown | — | — | unknown |
2904 | 4ukey.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAhflMAthXvozBT%2FU%2B2iPio%3D | unknown | — | — | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
3092 | iexplore.exe | 104.18.24.249:443 | download.tenorshare.com | CLOUDFLARENET | — | unknown |
— | — | 224.0.0.252:5355 | — | — | — | unknown |
3092 | iexplore.exe | 199.232.214.172:80 | ctldl.windowsupdate.com | FASTLY | US | unknown |
3092 | iexplore.exe | 199.232.210.172:80 | ctldl.windowsupdate.com | FASTLY | US | unknown |
3092 | iexplore.exe | 142.250.181.227:80 | ocsp.pki.goog | GOOGLE | US | whitelisted |
1080 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
2904 | 4ukey.exe | 104.17.192.141:80 | www.tenorshare.com | CLOUDFLARENET | — | unknown |
2904 | 4ukey.exe | 104.17.192.141:443 | www.tenorshare.com | CLOUDFLARENET | — | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
download.tenorshare.com |
| unknown |
ctldl.windowsupdate.com |
| whitelisted |
ocsp.pki.goog |
| whitelisted |
www.tenorshare.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
update.tenorshare.com |
| unknown |
ip-api.com |
| shared |
www.google-analytics.com |
| whitelisted |
iecvlist.microsoft.com |
| whitelisted |
r20swj13mr.microsoft.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2904 | 4ukey.exe | Potential Corporate Privacy Violation | ET POLICY Unsupported/Fake Windows NT Version 5.0 |
— | — | Potential Corporate Privacy Violation | ET POLICY Unsupported/Fake Windows NT Version 5.0 |
— | — | Potential Corporate Privacy Violation | AV POLICY Internal Host Retrieving External IP Address (ip-api. com) |
— | — | Device Retrieving External IP Address Detected | ET POLICY External IP Lookup ip-api.com |
2904 | 4ukey.exe | Possibly Unwanted Program Detected | ET ADWARE_PUP Tensorshare Google Analytics Checkin |
3644 | Tenorshare 4uKey.exe | Potential Corporate Privacy Violation | ET POLICY Unsupported/Fake Windows NT Version 5.0 |
3 ETPRO signatures available at the full report
Process | Message |
|---|---|
Tenorshare 4uKey.exe | 2024-04-11 12:49:26:489 Tenorshare 4uKey<3836>:: TSClientContext::Init ios_manager version = 5.0.0.752
|
Tenorshare 4uKey.exe | 2024-04-11 12:49:26:793 Tenorshare 4uKey<3836>:: TSDeviceInfo::UpdateJsonDevInfo JSON File in parent directory open Failed
|
Tenorshare 4uKey.exe | 2024-04-11 12:49:26:793 Tenorshare 4uKey<3836>:: TSDeviceInfo::UpdateJsonDevInfo JSON File in current directory open Failed
|
Tenorshare 4uKey.exe | 2024-04-11 12:49:26:797 Tenorshare 4uKey<664>:: TSDeviceStateManagerImpl::DetectUsbInsertion Enter
|
Tenorshare 4uKey.exe | 2024-04-11 12:49:26:797 Tenorshare 4uKey<664>:: TSDeviceStateManagerImpl::DetectUsbInsertion RegisterDeviceNotification
|
AppleMobileDeviceProcess.exe | ASL checking for logging parameters in environment variable "asl.log"
|
AppleMobileDeviceProcess.exe | ASL checking for logging parameters in environment variable "AppleMobileDeviceProcess.exe.log"
|
Tenorshare 4uKey.exe | Couldn't load our private device map. Device identification will be limited. |
Tenorshare 4uKey.exe | DeviceMap argument is empty. Skipping appending of deprecated devices. |
Tenorshare 4uKey.exe | |