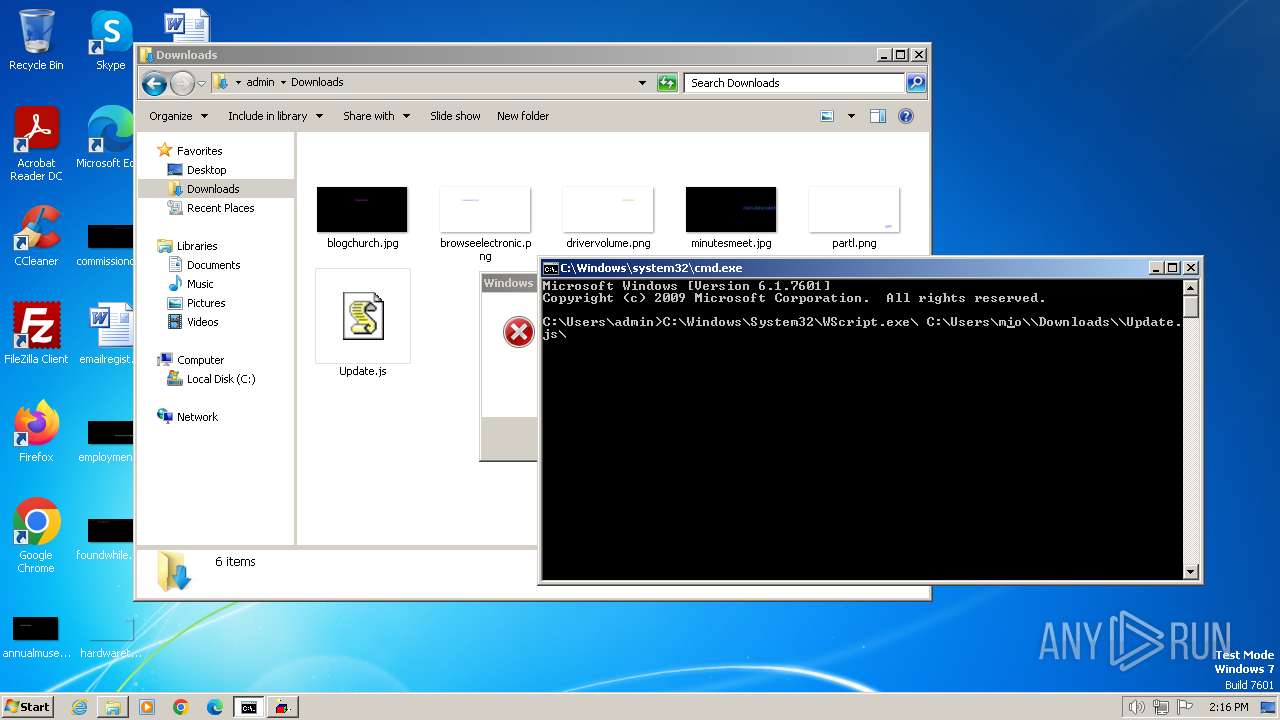
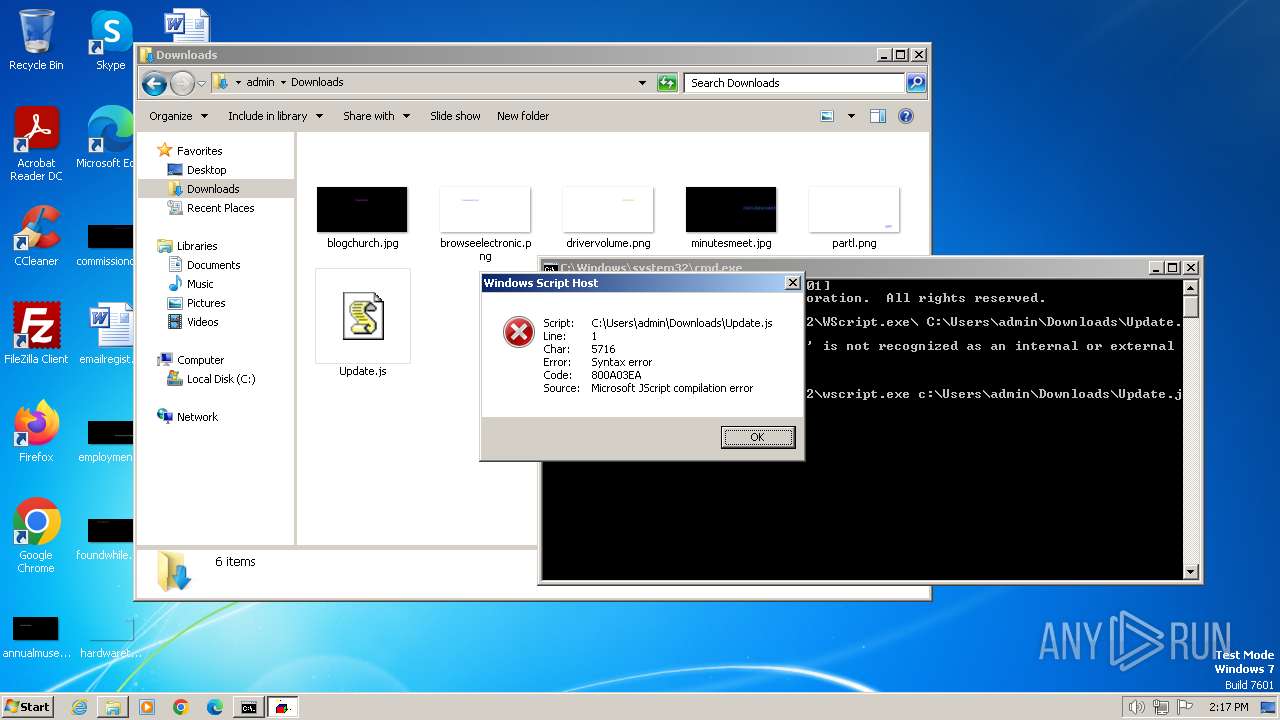
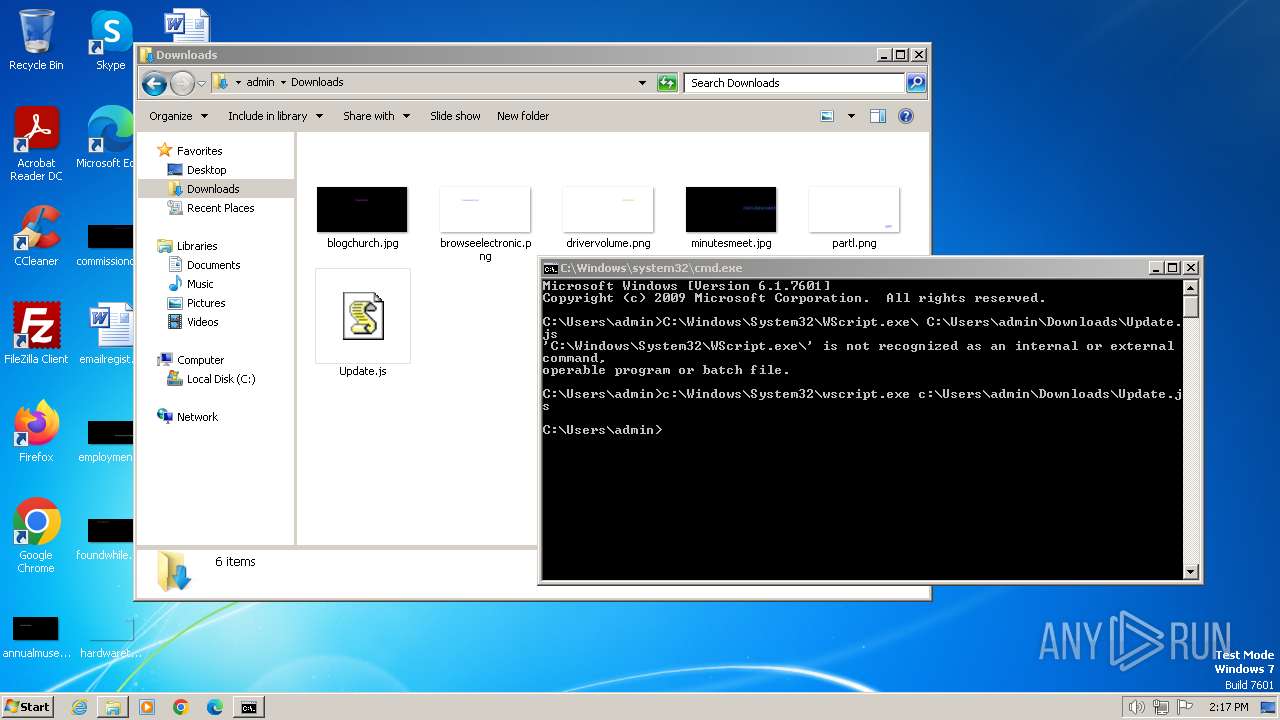
| File name: | Update.js |
| Full analysis: | https://app.any.run/tasks/c174c644-157f-4a79-aef9-d475ec65e10e |
| Verdict: | Malicious activity |
| Analysis date: | February 20, 2024, 14:15:56 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | text/plain |
| File info: | ASCII text, with very long lines (5944), with no line terminators |
| MD5: | D89BF6EC0A60FC09AB97D654E0012AE1 |
| SHA1: | 4021B5D908ED28DE3B42A4244FA145733C33846E |
| SHA256: | 81E3243A83D162AF6FB36F731A6BACDCCAEC2F0EF1FB6E1BBF9AF55AF72DED5D |
| SSDEEP: | 96:2GdFnT2r+ezMBmAepeS6hLx7XqwxvXqOXqIXqrcE5AxkXqUXqIXqrccXXqZFlSrq:BiFM7eperhLDk5ENG8nqxaUEitaNJgFV |
MALICIOUS
Creates internet connection object (SCRIPT)
- wscript.exe (PID: 3672)
- wscript.exe (PID: 3724)
Opens an HTTP connection (SCRIPT)
- wscript.exe (PID: 3672)
- wscript.exe (PID: 3724)
Connects to the CnC server
- wscript.exe (PID: 3672)
- wscript.exe (PID: 3724)
Unusual connection from system programs
- wscript.exe (PID: 3672)
- wscript.exe (PID: 3724)
Sends HTTP request (SCRIPT)
- wscript.exe (PID: 3672)
- wscript.exe (PID: 3724)
SUSPICIOUS
Reads the Internet Settings
- wscript.exe (PID: 3672)
- wscript.exe (PID: 3724)
Adds/modifies Windows certificates
- wscript.exe (PID: 3672)
- wscript.exe (PID: 3724)
Adds, changes, or deletes HTTP request header (SCRIPT)
- wscript.exe (PID: 3672)
- wscript.exe (PID: 3724)
The process executes JS scripts
- cmd.exe (PID: 4044)
INFO
Checks proxy server information
- wscript.exe (PID: 3672)
- wscript.exe (PID: 3724)
Manual execution by a user
- explorer.exe (PID: 1876)
- cmd.exe (PID: 4044)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
43
Monitored processes
4
Malicious processes
3
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1876 | "C:\Windows\explorer.exe" | C:\Windows\explorer.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Explorer Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3672 | "C:\Windows\System32\WScript.exe" "C:\Users\admin\Downloads\Update.js" | C:\Windows\System32\wscript.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft ® Windows Based Script Host Exit code: 0 Version: 5.8.7600.16385 Modules
| |||||||||||||||
| 3724 | c:\Windows\System32\wscript.exe c:\Users\admin\Downloads\Update.js | C:\Windows\System32\wscript.exe | cmd.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft ® Windows Based Script Host Exit code: 0 Version: 5.8.7600.16385 Modules
| |||||||||||||||
| 4044 | "C:\Windows\system32\cmd.exe" | C:\Windows\System32\cmd.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
Total events
8 447
Read events
8 275
Write events
103
Delete events
69
Modification events
| (PID) Process: | (3672) wscript.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (3672) wscript.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (3672) wscript.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
| (PID) Process: | (3672) wscript.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 0 | |||
| (PID) Process: | (3672) wscript.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings |
| Operation: | write | Name: | ProxyEnable |
Value: 0 | |||
| (PID) Process: | (3672) wscript.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings |
| Operation: | delete value | Name: | ProxyServer |
Value: | |||
| (PID) Process: | (3672) wscript.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings |
| Operation: | delete value | Name: | ProxyOverride |
Value: | |||
| (PID) Process: | (3672) wscript.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings |
| Operation: | delete value | Name: | AutoConfigURL |
Value: | |||
| (PID) Process: | (3672) wscript.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings |
| Operation: | delete value | Name: | AutoDetect |
Value: | |||
| (PID) Process: | (3672) wscript.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\Connections |
| Operation: | write | Name: | SavedLegacySettings |
Value: 460000005C010000090000000000000000000000000000000400000000000000C0E333BBEAB1D3010000000000000000000000000100000002000000C0A8016B000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
Executable files
0
Suspicious files
4
Text files
0
Unknown types
3
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3672 | wscript.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\518DFDD116D9AD0210609502E2F95908 | binary | |
MD5:437DFB87E3D7DDCD94C7DD33F4425B5E | SHA256:80D338D5FD6CF7665FD9AD344DF4A689BDB467BAE6884B9A4762BE1CC88C0CBD | |||
| 3672 | wscript.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\57C8EDB95DF3F0AD4EE2DC2B8CFD4157 | binary | |
MD5:FA022B1B0CFEA0C2DA6F18A120B9E102 | SHA256:34B7F62F232237B38C47878A42EC89C5A048511344EDF1E9BF7B52F1D29FB283 | |||
| 3672 | wscript.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\518DFDD116D9AD0210609502E2F95908 | der | |
MD5:DD982383A2370B4FFBEE127C259C9BF6 | SHA256:E09C36D4677C9986B0766345054BD522B0B7352B5B1BF60762EF925B925D0668 | |||
| 3672 | wscript.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\D0E1C4B6144E7ECAB3F020E4A19EFC29_03D1B482EE3032A122274428715A4E19 | der | |
MD5:50CB447F2A8F99CB126CB51392696C7F | SHA256:0D00728A79F840F071F85740EFFF9A27EC0C7D1F489511B5B7C4C861767AA059 | |||
| 3672 | wscript.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\B2FAF7692FD9FFBD64EDE317E42334BA_89854CA6A0F0936A4D2ECA78845CEA25 | binary | |
MD5:6D3EEA3DDD973CD16ACBB604875046CC | SHA256:9D8E2969AEA7DBA730DF4EAB635EE2AE072726A125F479FF9ADFC3640C93747A | |||
| 3672 | wscript.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\B2FAF7692FD9FFBD64EDE317E42334BA_89854CA6A0F0936A4D2ECA78845CEA25 | der | |
MD5:A99377A27910F2447A1D4C78A1D55540 | SHA256:CD3094C0DF506297237C88653680D7A4E83E613696E78C30B99E428FDE3C4B48 | |||
| 3672 | wscript.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\D0E1C4B6144E7ECAB3F020E4A19EFC29_03D1B482EE3032A122274428715A4E19 | binary | |
MD5:8A3AA440A2711CCF5CCEE6B80692E75C | SHA256:8F6BE5B097D0B9EEA24C2C3B5A222CE338C6EA89C8DBBD901BFD201921109027 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
6
TCP/UDP connections
11
DNS requests
5
Threats
5
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3672 | wscript.exe | GET | 304 | 93.184.221.240:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?9fefac189b26be47 | unknown | — | — | unknown |
3672 | wscript.exe | GET | 200 | 172.64.149.23:80 | http://ocsp.comodoca.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBRTtU9uFqgVGHhJwXZyWCNXmVR5ngQUoBEKIz6W8Qfs4q8p74Klf9AwpLQCEFZnHQTqT5lMbxCBR1nSdZQ%3D | unknown | binary | 1.42 Kb | unknown |
3672 | wscript.exe | GET | 200 | 172.64.149.23:80 | http://ocsp.usertrust.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSr83eyJy3njhjVpn5bEpfc6MXawQQUOuEJhtTPGcKWdnRJdtzgNcZjY5oCECO3bePBuysaUZYeCOq3ZOg%3D | unknown | binary | 977 b | unknown |
3672 | wscript.exe | GET | 200 | 172.64.149.23:80 | http://zerossl.ocsp.sectigo.com/MFIwUDBOMEwwSjAJBgUrDgMCGgUABBQzH%2F4%2F%2FQuEFihPlI1WwH4Dktj2TQQUD2vmS845R672fpAeefAwkZLIX6MCEQDTtGnFkWrZ88rhk1957mc%2B | unknown | binary | 317 b | unknown |
1080 | svchost.exe | GET | 304 | 93.184.221.240:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?1b8fee253118cbef | unknown | compressed | 65.2 Kb | unknown |
1080 | svchost.exe | GET | 200 | 93.184.221.240:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/authrootstl.cab?c503292d7802e201 | unknown | compressed | 65.2 Kb | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
1080 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
3672 | wscript.exe | 45.59.170.106:443 | hgxb.members.openarmscv.com | SPRINTLINK | RE | unknown |
3672 | wscript.exe | 93.184.221.240:80 | ctldl.windowsupdate.com | EDGECAST | GB | whitelisted |
3672 | wscript.exe | 172.64.149.23:80 | ocsp.comodoca.com | CLOUDFLARENET | US | unknown |
1080 | svchost.exe | 93.184.221.240:80 | ctldl.windowsupdate.com | EDGECAST | GB | whitelisted |
3724 | wscript.exe | 45.59.170.106:443 | hgxb.members.openarmscv.com | SPRINTLINK | RE | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
hgxb.members.openarmscv.com |
| unknown |
ctldl.windowsupdate.com |
| whitelisted |
ocsp.comodoca.com |
| whitelisted |
ocsp.usertrust.com |
| whitelisted |
zerossl.ocsp.sectigo.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
1080 | svchost.exe | Domain Observed Used for C2 Detected | ET MALWARE SocGholish CnC Domain in DNS Lookup (* .members .openarmscv .com) |
3672 | wscript.exe | Domain Observed Used for C2 Detected | ET MALWARE SocGholish CnC Domain in TLS SNI (* .members .openarmscv .com) |
3672 | wscript.exe | Misc activity | ET INFO Observed ZeroSSL SSL/TLS Certificate |
3724 | wscript.exe | Domain Observed Used for C2 Detected | ET MALWARE SocGholish CnC Domain in TLS SNI (* .members .openarmscv .com) |
3724 | wscript.exe | Misc activity | ET INFO Observed ZeroSSL SSL/TLS Certificate |