| File name: | 1.zip |
| Full analysis: | https://app.any.run/tasks/097c9174-dcb4-4634-bb8d-53addecac9e1 |
| Verdict: | Malicious activity |
| Analysis date: | December 25, 2024, 15:16:24 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract, compression method=deflate |
| MD5: | 95E010FEB14CFB00C835FA50FE0E57CF |
| SHA1: | F822971E417D4C5EB7D0CDA8831BBAC91BAE798D |
| SHA256: | 81C77C5E75627424061C5A005BAD6F873B92B692DA469D2A38B211B3BEF9357B |
| SSDEEP: | 196608:Brw0F4f/ivqcht/elltZRIEArfc994aoBFJ3:5w//MqchQlfIEAr0r7ofp |
MALICIOUS
Generic archive extractor
- WinRAR.exe (PID: 2324)
Antivirus name has been found in the command line (generic signature)
- MpCmdRun.exe (PID: 2008)
SUSPICIOUS
Reads security settings of Internet Explorer
- ת הקשורות להפרת זכויות יוצרים.exe (PID: 5244)
- WinRAR.exe (PID: 2324)
Executing commands from a ".bat" file
- WinRAR.exe (PID: 2324)
Starts CMD.EXE for commands execution
- WinRAR.exe (PID: 2324)
Checks for external IP
- ת הקשורות להפרת זכויות יוצרים.exe (PID: 5244)
INFO
Reads the computer name
- ת הקשורות להפרת זכויות יוצרים.exe (PID: 5244)
- MpCmdRun.exe (PID: 2008)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 2324)
Checks supported languages
- ת הקשורות להפרת זכויות יוצרים.exe (PID: 5244)
- MpCmdRun.exe (PID: 2008)
The sample compiled with english language support
- WinRAR.exe (PID: 2324)
Checks proxy server information
- ת הקשורות להפרת זכויות יוצרים.exe (PID: 5244)
Manual execution by a user
- ת הקשורות להפרת זכויות יוצרים.exe (PID: 5244)
The process uses the downloaded file
- WinRAR.exe (PID: 2324)
Create files in a temporary directory
- MpCmdRun.exe (PID: 2008)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | 0x0002 |
| ZipCompression: | Deflated |
| ZipModifyDate: | 2024:12:25 00:25:04 |
| ZipCRC: | 0x2211c678 |
| ZipCompressedSize: | 18516173 |
| ZipUncompressedSize: | 31272960 |
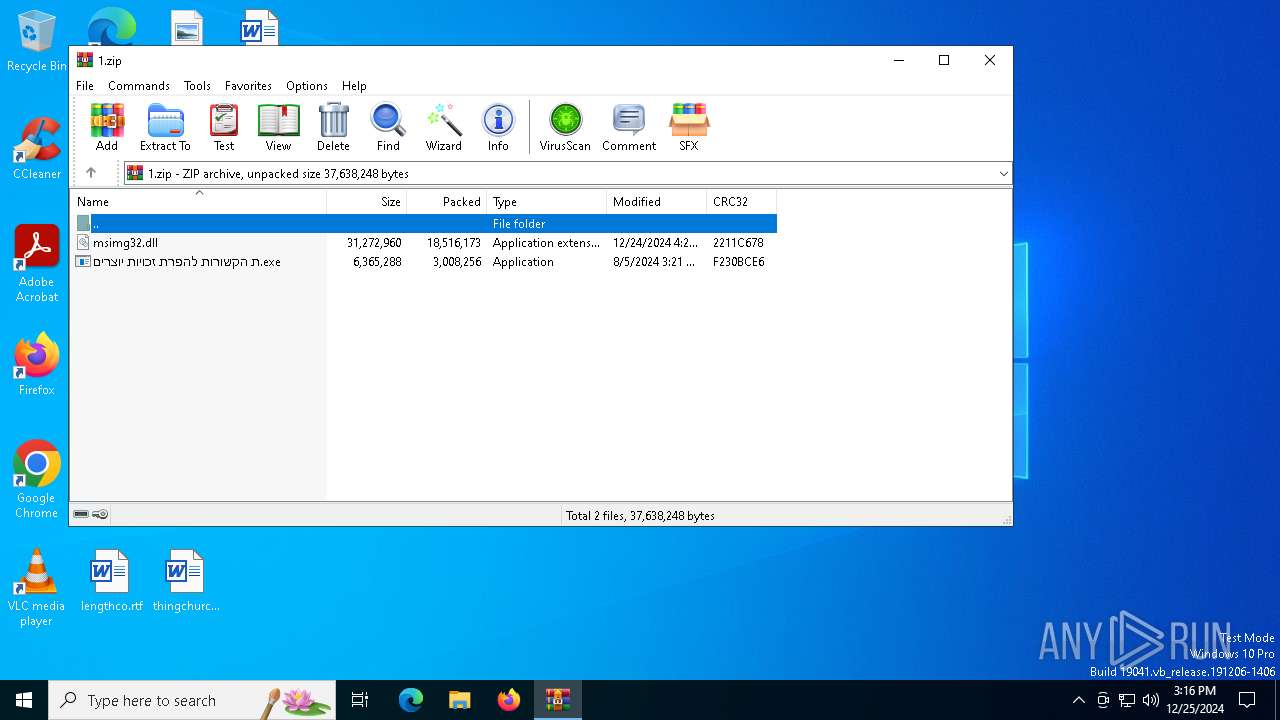
| ZipFileName: | msimg32.dll |
Total processes
121
Monitored processes
5
Malicious processes
1
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1016 | C:\WINDOWS\system32\cmd.exe /c ""C:\Users\admin\AppData\Local\Temp\Rar$VR2324.13593\Rar$Scan22487.bat" " | C:\Windows\System32\cmd.exe | — | WinRAR.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
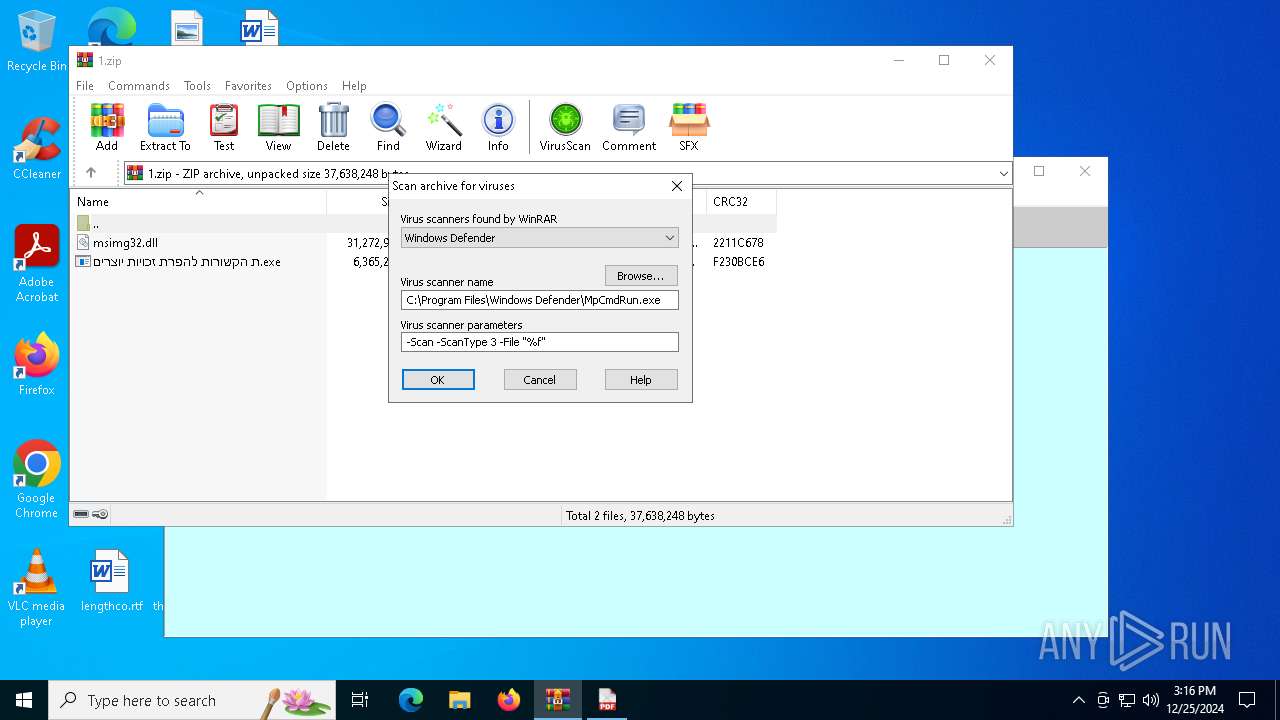
| 2008 | "C:\Program Files\Windows Defender\MpCmdRun.exe" -Scan -ScanType 3 -File "C:\Users\admin\AppData\Local\Temp\Rar$VR2324.13593" | C:\Program Files\Windows Defender\MpCmdRun.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Malware Protection Command Line Utility Exit code: 2 Version: 4.18.1909.6 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2324 | "C:\Program Files\WinRAR\WinRAR.exe" C:\Users\admin\Desktop\1.zip | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Version: 5.91.0 Modules
| |||||||||||||||
| 2796 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5244 | "C:\Users\admin\Desktop\ת הקשורות להפרת זכויות יוצרים.exe" | C:\Users\admin\Desktop\ת הקשורות להפרת זכויות יוצרים.exe | explorer.exe | ||||||||||||
User: admin Company: Haihaisoft Limited Integrity Level: MEDIUM Description: Haihaisoft PDF Reader Version: 1.5.7.0 Modules
| |||||||||||||||
Total events
2 054
Read events
2 044
Write events
10
Delete events
0
Modification events
| (PID) Process: | (2324) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\preferences.zip | |||
| (PID) Process: | (2324) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\chromium_ext.zip | |||
| (PID) Process: | (2324) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
| (PID) Process: | (2324) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\1.zip | |||
| (PID) Process: | (2324) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (2324) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (2324) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (2324) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (5244) ת הקשורות להפרת זכויות יוצרים.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Haihaisoft PDF Reader |
| Operation: | write | Name: | UpdateDate |
Value: 133796134086640000 | |||
| (PID) Process: | (2324) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\VirusScan |
| Operation: | write | Name: | DefScanner |
Value: Windows Defender | |||
Executable files
2
Suspicious files
0
Text files
2
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2324 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$VR2324.13593\1.zip\msimg32.dll | executable | |
MD5:A4B49EFA4D0BA48A1888422E174FDEB2 | SHA256:B2FA5AC6E8619A365F5FFC1D98E8C2927FEDF8BEA71418A01BB0184B684A601C | |||
| 2324 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$VR2324.13593\Rar$Scan22487.bat | text | |
MD5:7870417323E0FCAA19BF5A8935F96682 | SHA256:7199DBAEEF46A82C692005D2E30FDF1161A76FFC609F2A3FEF61C19547A56C9F | |||
| 2008 | MpCmdRun.exe | C:\Users\admin\AppData\Local\Temp\MpCmdRun.log | text | |
MD5:DB44169F16BDAF5509C80DB3C4D6D0EC | SHA256:5373E1632A045D836E8FC0EC4AF80D857DF02075E24F18C6D66C53E40178A17F | |||
| 2324 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$VR2324.13593\1.zip\ת הקשורות להפרת זכויות יוצרים.exe | executable | |
MD5:4864A55CFF27F686023456A22371E790 | SHA256:08C7FB6067ACC8AC207D28AB616C9EA5BC0D394956455D6A3EECB73F8010F7A2 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
5
TCP/UDP connections
22
DNS requests
10
Threats
1
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
640 | svchost.exe | GET | 200 | 23.53.40.178:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
4712 | MoUsoCoreWorker.exe | GET | 200 | 23.53.40.178:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
4712 | MoUsoCoreWorker.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
5244 | ת הקשורות להפרת זכויות יוצרים.exe | GET | 200 | 163.171.128.241:80 | http://www.drm-x.com/pdfversion.htm | unknown | — | — | unknown |
640 | svchost.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4712 | MoUsoCoreWorker.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
640 | svchost.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | unknown |
— | — | 192.168.100.255:138 | — | — | — | whitelisted |
— | — | 2.23.209.135:443 | www.bing.com | Akamai International B.V. | GB | whitelisted |
640 | svchost.exe | 23.53.40.178:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
4712 | MoUsoCoreWorker.exe | 23.53.40.178:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
640 | svchost.exe | 184.30.21.171:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
5244 | ת הקשורות להפרת זכויות יוצרים.exe | 163.171.128.241:80 | www.drm-x.com | QUANTILNETWORKS | DE | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
www.bing.com |
| whitelisted |
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
www.drm-x.com |
| unknown |
self.events.data.microsoft.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
5244 | ת הקשורות להפרת זכויות יוצרים.exe | Device Retrieving External IP Address Detected | SUSPICIOUS [ANY.RUN] An IP address was received from the server as a result of an HTTP request |