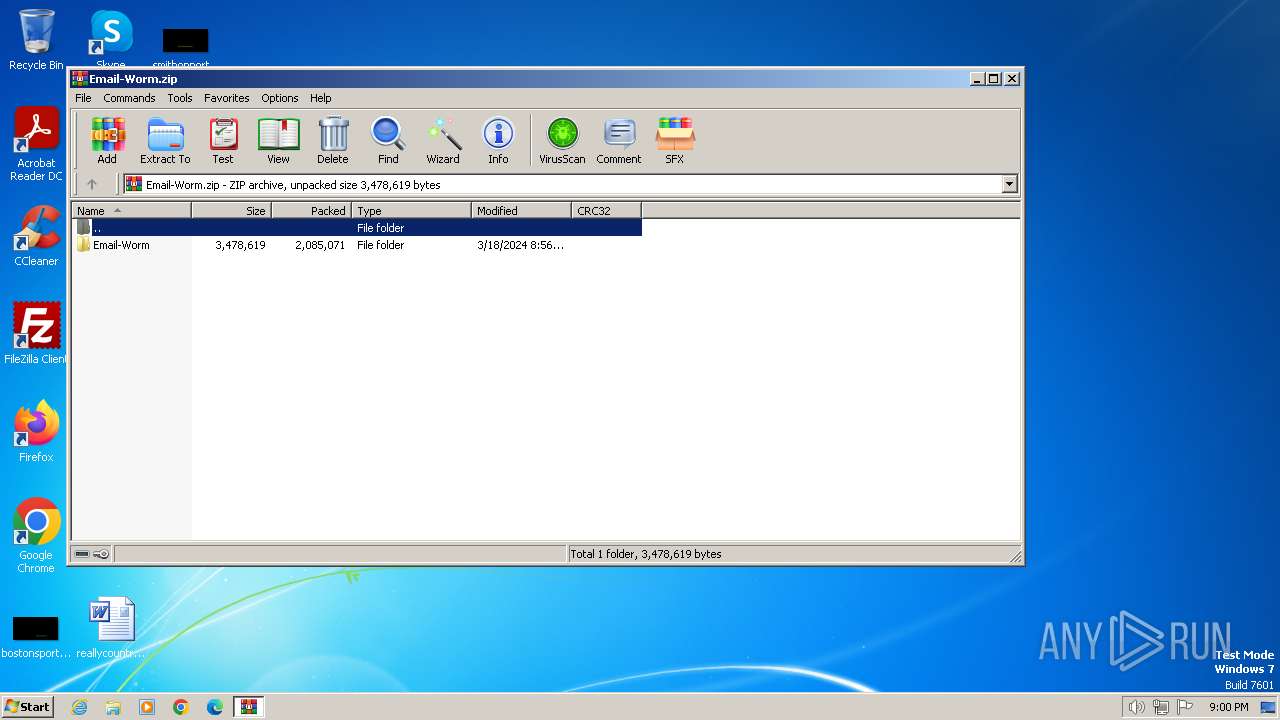
| File name: | Email-Worm.zip |
| Full analysis: | https://app.any.run/tasks/40938d7c-9ec6-4e89-801b-36eafc3a77a1 |
| Verdict: | Malicious activity |
| Analysis date: | March 18, 2024, 21:00:28 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v4.5 to extract, compression method=deflate |
| MD5: | 2AB2209B7761B6633D994FCD97C365FC |
| SHA1: | 1D471219DC1A814E96F810F1ACDED6D7E325FE41 |
| SHA256: | 81B70B63C5D8C8C7A1855A293525695C76FEA6A7B130FED829243E73DECCFA09 |
| SSDEEP: | 98304:PsMVNsNeXpO+QYxkBrAlRmTUPNgHM30fE9CRvz1vaXoSoSpRMQd+Z+n1qVTGfaIt:UM7VQxGjCvi |
MALICIOUS
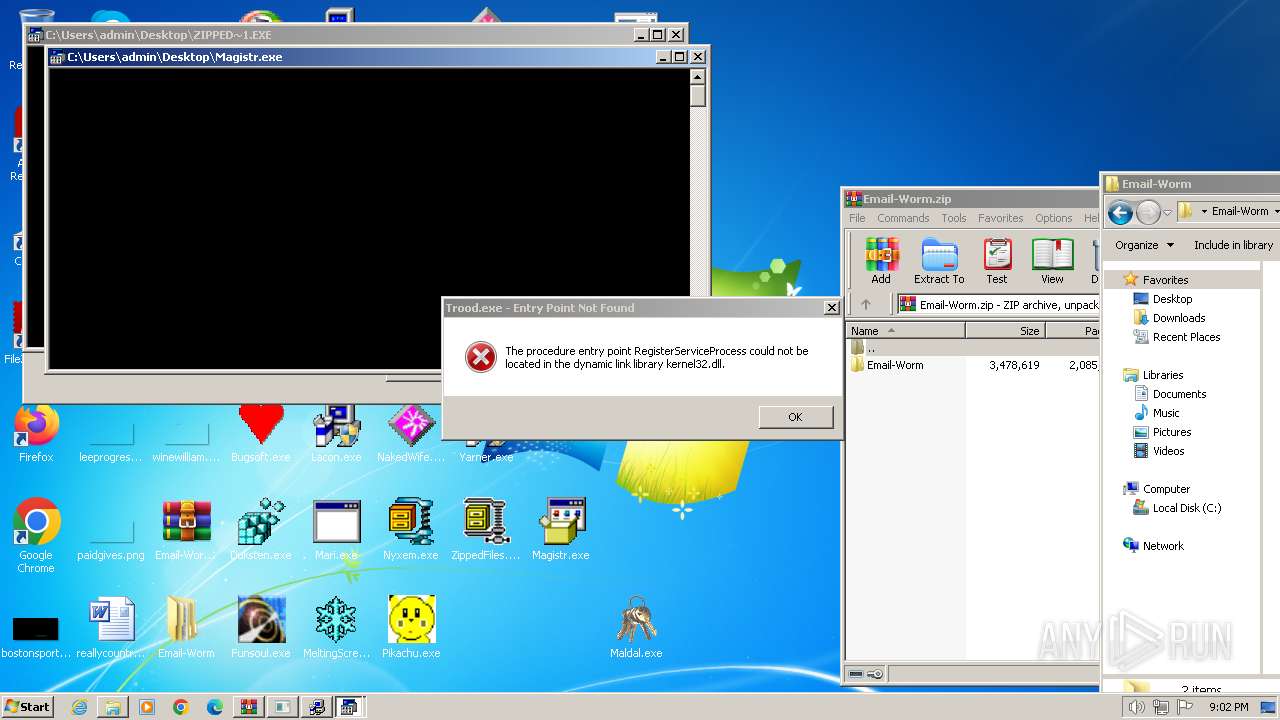
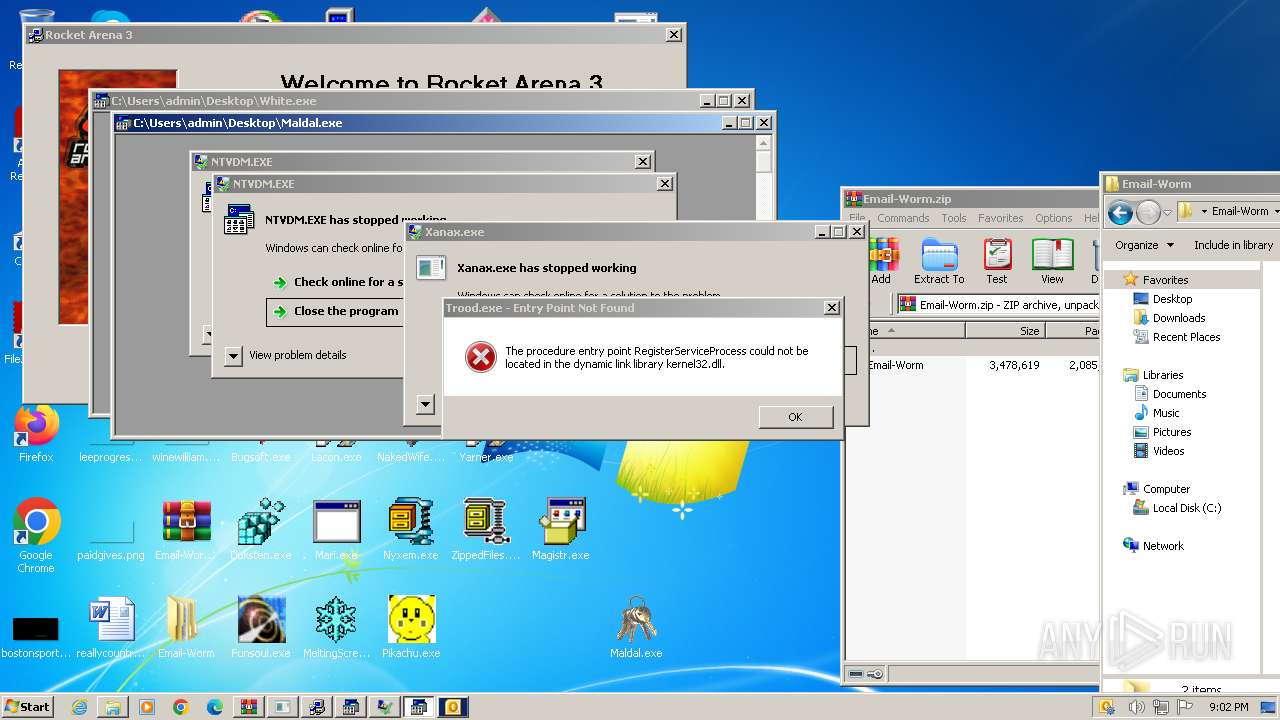
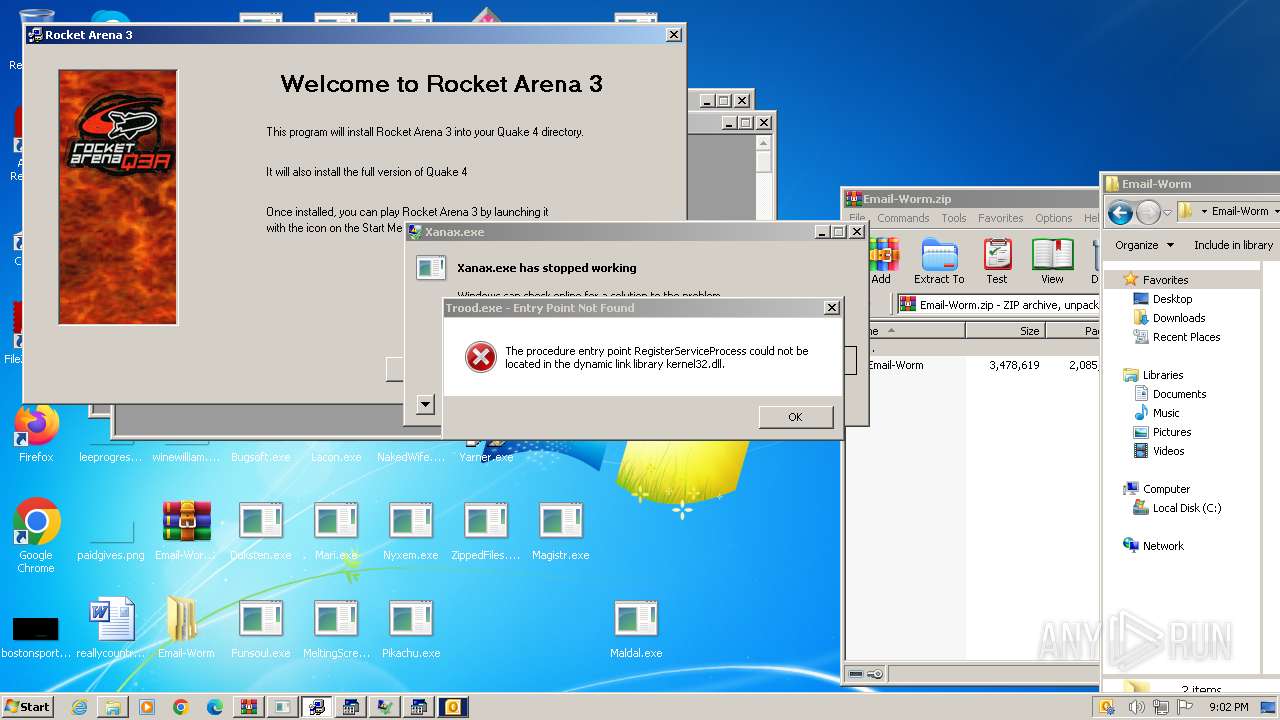
Drops the executable file immediately after the start
- WinRAR.exe (PID: 3500)
- Prolin.exe (PID: 2244)
- Xanax.exe (PID: 2384)
- Yarner.exe (PID: 2632)
Changes the autorun value in the registry
- Quamo.exe (PID: 492)
- Yarner.exe (PID: 2632)
Creates a writable file in the system directory
- OUTLOOK.EXE (PID: 844)
Actions looks like stealing of personal data
- Yarner.exe (PID: 2632)
SUSPICIOUS
Executable content was dropped or overwritten
- Prolin.exe (PID: 2244)
- Xanax.exe (PID: 2384)
- Yarner.exe (PID: 2632)
Creates file in the systems drive root
- Prolin.exe (PID: 2244)
- ntvdm.exe (PID: 2620)
Starts a Microsoft application from unusual location
- Trood.exe (PID: 1864)
Process drops legitimate windows executable
- Xanax.exe (PID: 2384)
- Yarner.exe (PID: 2632)
Non-standard symbols in registry
- OUTLOOK.EXE (PID: 844)
INFO
Executable content was dropped or overwritten
- WinRAR.exe (PID: 3500)
Checks supported languages
- Prolin.exe (PID: 2244)
- Quamo.exe (PID: 492)
- Xanax.exe (PID: 2384)
- Yarner.exe (PID: 2632)
Reads the computer name
- Prolin.exe (PID: 2244)
- Yarner.exe (PID: 2632)
Reads the machine GUID from the registry
- Prolin.exe (PID: 2244)
- Quamo.exe (PID: 492)
- Yarner.exe (PID: 2632)
Manual execution by a user
- Prolin.exe (PID: 2244)
- Quamo.exe (PID: 492)
- Trood.exe (PID: 1864)
- Xanax.exe (PID: 2384)
- Yarner.exe (PID: 2632)
- csrstub.exe (PID: 1232)
- csrstub.exe (PID: 992)
- csrstub.exe (PID: 952)
- csrstub.exe (PID: 948)
- csrstub.exe (PID: 4064)
- ntvdm.exe (PID: 4036)
- ntvdm.exe (PID: 3408)
- ntvdm.exe (PID: 2948)
- ntvdm.exe (PID: 2328)
Create files in a temporary directory
- Prolin.exe (PID: 2244)
- Quamo.exe (PID: 492)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 45 |
|---|---|
| ZipBitFlag: | 0x0800 |
| ZipCompression: | Deflated |
| ZipModifyDate: | 2024:03:18 20:56:18 |
| ZipCRC: | 0x00000000 |
| ZipCompressedSize: | 2 |
| ZipUncompressedSize: | - |
| ZipFileName: | Email-Worm/ |
Total processes
95
Monitored processes
21
Malicious processes
3
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 492 | "C:\Users\admin\Desktop\Quamo.exe" | C:\Users\admin\Desktop\Quamo.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Version: 1.00 Modules
| |||||||||||||||
| 844 | "C:\Program Files\Microsoft Office\Office14\OUTLOOK.EXE" -Embedding | C:\Program Files\Microsoft Office\Office14\OUTLOOK.EXE | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft Outlook Exit code: 0 Version: 14.0.6025.1000 Modules
| |||||||||||||||
| 948 | C:\Windows\system32\csrstub.exe 67634196 -P "C:\Users\admin\Desktop\White.exe" | C:\Windows\System32\csrstub.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: allows lua to launch 16-bit applications Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 952 | C:\Windows\system32\csrstub.exe 67634196 -P "C:\Users\admin\Desktop\Winevar.exe" | C:\Windows\System32\csrstub.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: allows lua to launch 16-bit applications Exit code: 3221225477 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 992 | C:\Windows\system32\csrstub.exe 67634196 -P "C:\Users\admin\Desktop\Magistr.exe" | C:\Windows\System32\csrstub.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: allows lua to launch 16-bit applications Exit code: 3221225477 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1232 | C:\Windows\system32\csrstub.exe 67634196 -P "C:\Users\admin\Desktop\ZippedFiles.exe" | C:\Windows\System32\csrstub.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: allows lua to launch 16-bit applications Exit code: 3221225477 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1796 | "C:\Windows\system32\ntvdm.exe" -i2 | C:\Windows\System32\ntvdm.exe | — | csrstub.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: NTVDM.EXE Exit code: 3221225477 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1864 | "C:\Users\admin\Desktop\Trood.exe" | C:\Users\admin\Desktop\Trood.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: TCP/IP Update for Microsoft Windows 95/98 Exit code: 3221225785 Version: 6.6.6 Modules
| |||||||||||||||
| 2244 | "C:\Users\admin\Desktop\Prolin.exe" | C:\Users\admin\Desktop\Prolin.exe | explorer.exe | ||||||||||||
User: admin Company: Macromedia, Inc., Integrity Level: HIGH Description: Flash Exit code: 0 Version: 4.00 Modules
| |||||||||||||||
| 2328 | "C:\Windows\system32\ntvdm.exe" -i9 | C:\Windows\System32\ntvdm.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: NTVDM.EXE Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
8 520
Read events
8 389
Write events
108
Delete events
23
Modification events
| (PID) Process: | (3500) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (3500) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (3500) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\182\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (3500) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\phacker.zip | |||
| (PID) Process: | (3500) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\Win7-KB3191566-x86.zip | |||
| (PID) Process: | (3500) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\curl-8.5.0_1-win32-mingw.zip | |||
| (PID) Process: | (3500) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\Email-Worm.zip | |||
| (PID) Process: | (3500) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (3500) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (3500) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
Executable files
44
Suspicious files
0
Text files
22
Unknown types
4
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3500 | WinRAR.exe | C:\Users\admin\Desktop\Email-Worm\Email-Worm\Funsoul.exe | executable | |
MD5:A13A4DB860D743A088EF7AB9BACB4DDA | SHA256:69EE59CEE5A1D39739D935701CFA917F75787B29E0B9BDA9ADA9E2642ADE434C | |||
| 3500 | WinRAR.exe | C:\Users\admin\Desktop\Email-Worm\Email-Worm\MyPics.exe | executable | |
MD5:94EC47428DABB492AF96756E7C95C644 | SHA256:0AE040287546A70F8A2D5FC2DA45A83E253DA044BF10246AE77830AF971B3359 | |||
| 3500 | WinRAR.exe | C:\Users\admin\Desktop\Email-Worm\Email-Worm\Duksten.exe | executable | |
MD5:900EBFF3E658825F828AB95B30FAD2E7 | SHA256:CAEC6E664B3CFF5717DD2EFEA8DCD8715ABDCFE7F611456BE7009771F22A8F50 | |||
| 3500 | WinRAR.exe | C:\Users\admin\Desktop\Email-Worm\Email-Worm\Xanax.exe | executable | |
MD5:DF24E1CCCEB3C75DADA950A1C1ABCA4D | SHA256:910C03D210381F0443BFCEFE682717F28378DCFE5415071DD127A9837A97B0A6 | |||
| 3500 | WinRAR.exe | C:\Users\admin\Desktop\Email-Worm\Email-Worm\Maldal.exe | executable | |
MD5:CBCD34A252A7CF61250B0F7F1CBA3382 | SHA256:ABAC285F290F0CFCD308071C9DFA9B7B4B48D10B4A3B4D75048804E59A447787 | |||
| 3500 | WinRAR.exe | C:\Users\admin\Desktop\Email-Worm\Email-Worm\Axam.exe | executable | |
MD5:0FBF8022619BA56C545B20D172BF3B87 | SHA256:4AE7D63EC497143C2ACDE1BA79F1D9EED80086A420B6F0A07B1E2917DA0A6C74 | |||
| 3500 | WinRAR.exe | C:\Users\admin\Desktop\Email-Worm\Email-Worm\Quamo.exe | executable | |
MD5:A1F722324492FDA51077449EC2DB2827 | SHA256:FC2CED1D89845DCFAE55B6E854CD0E622FDF98BAEEB4A67A60852ECD1212F93B | |||
| 3500 | WinRAR.exe | C:\Users\admin\Desktop\Email-Worm\Email-Worm\MeltingScreen.exe | executable | |
MD5:4784E42C3B15D1A141A5E0C8ABC1205C | SHA256:9D355E4F9A51536B05269F696B304859155985957BA95EB575F3F38C599D913C | |||
| 3500 | WinRAR.exe | C:\Users\admin\Desktop\Email-Worm\Email-Worm\Trood.exe | executable | |
MD5:47D1F48A127736E63AAD709DDC9D81D0 | SHA256:24DD269B4D5EDEB591AD992DB33553D90F1848F58C06C9DD9FB3CDB4EAF812F5 | |||
| 3500 | WinRAR.exe | C:\Users\admin\Desktop\Email-Worm\Email-Worm\Anap.exe | executable | |
MD5:0231C3A7D92EAD1BAD77819D5BDA939D | SHA256:DA1798C0A49B991FBDA674F02007B0A3BE4703E2B07EE540539DB7E5BF983278 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
1
TCP/UDP connections
5
DNS requests
3
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
844 | OUTLOOK.EXE | GET | — | 64.4.26.155:80 | http://config.messenger.msn.com/config/msgrconfig.asmx?op=GetOlcConfig | unknown | — | — | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1080 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
844 | OUTLOOK.EXE | 64.4.26.155:80 | config.messenger.msn.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
config.messenger.msn.com |
| whitelisted |
toad.com |
| unknown |