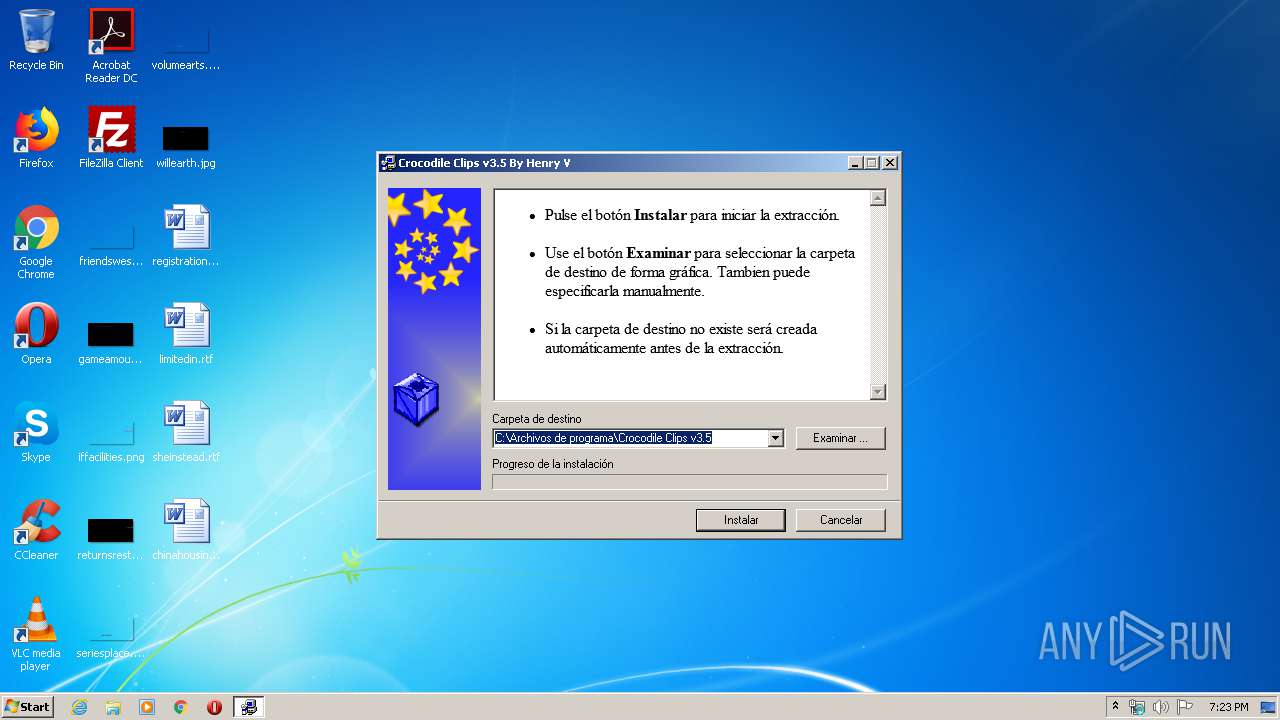
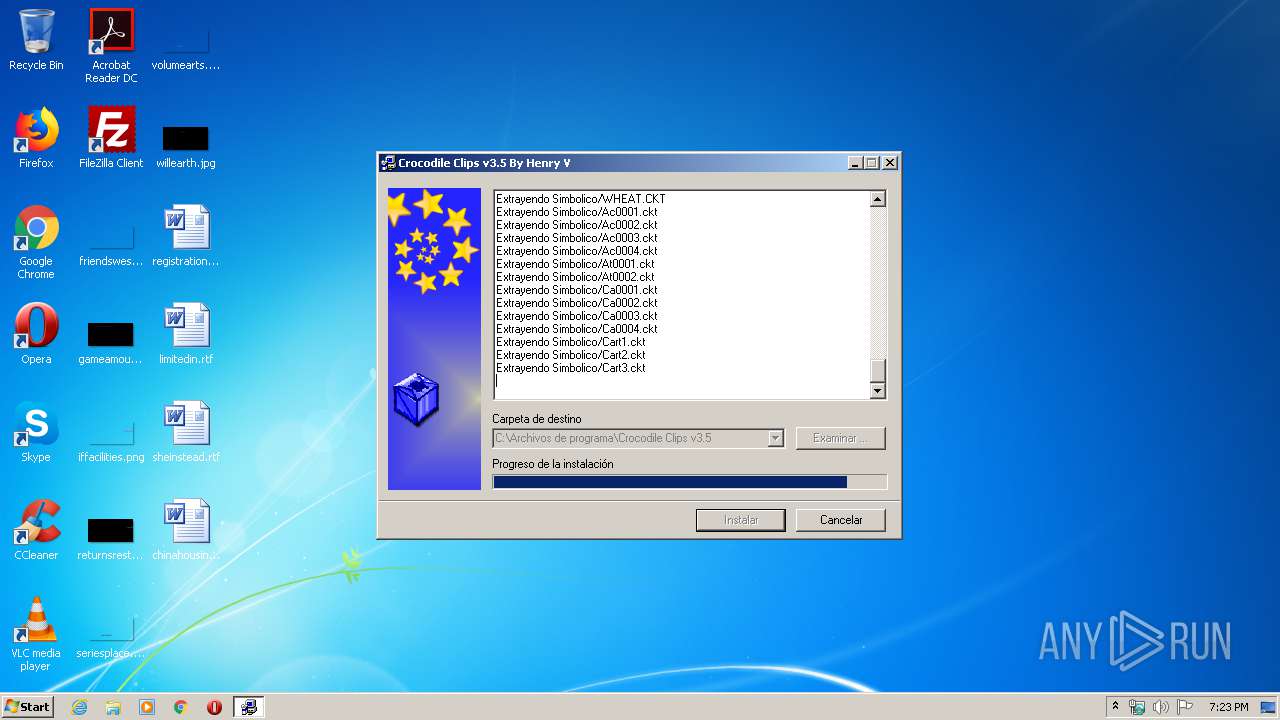
| File name: | Crocodile_Clips_v3.5.exe |
| Full analysis: | https://app.any.run/tasks/323dfc8e-d9a8-4d56-b97d-1232a25d9aa1 |
| Verdict: | Malicious activity |
| Analysis date: | May 11, 2020, 18:22:51 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows |
| MD5: | 1738BB884694D2C595D0BD1264796AA6 |
| SHA1: | 0AE356644B83FC927DC0A822DA166996C9CDA704 |
| SHA256: | 81A67B024347C05C9C35D357501B59D849B32AE40D1EE412C53363B2B98B26DA |
| SSDEEP: | 24576:/AB74/AQpHosQSBUG4uV3szIHNAljLwW+vT37vkfXCz5zxkB:/AajzBUg3tAljqT3rk6tuB |
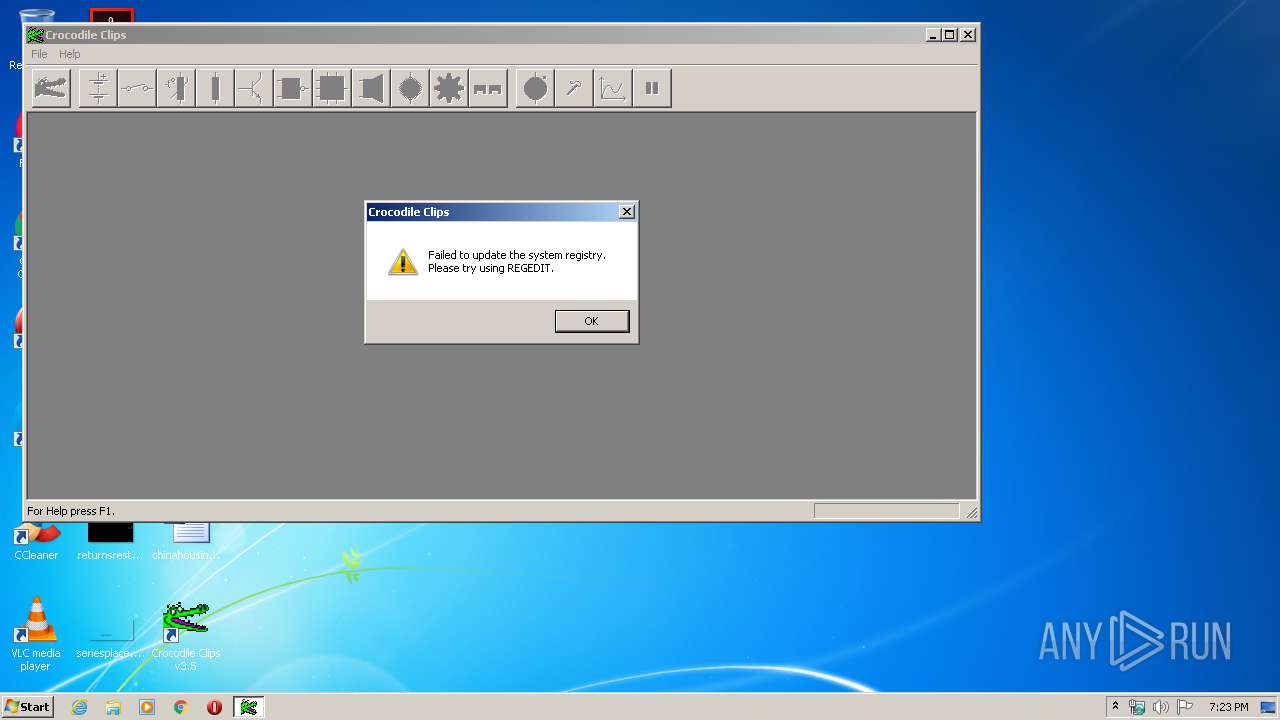
MALICIOUS
Application was dropped or rewritten from another process
- CROCCLIP.EXE (PID: 2852)
SUSPICIOUS
Executable content was dropped or overwritten
- Crocodile_Clips_v3.5.exe (PID: 3320)
Reads internet explorer settings
- Crocodile_Clips_v3.5.exe (PID: 3320)
Reads Internet Cache Settings
- Crocodile_Clips_v3.5.exe (PID: 3320)
Creates files in the program directory
- Crocodile_Clips_v3.5.exe (PID: 3320)
INFO
Manual execution by user
- CROCCLIP.EXE (PID: 2852)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | WinRAR Self Extracting archive (94.8) |
|---|---|---|
| .scr | | | Windows screen saver (2.3) |
| .dll | | | Win32 Dynamic Link Library (generic) (1.2) |
| .exe | | | Win32 Executable (generic) (0.8) |
| .exe | | | Generic Win/DOS Executable (0.3) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2006:08:04 20:28:10+02:00 |
| PEType: | PE32 |
| LinkerVersion: | 5 |
| CodeSize: | 45056 |
| InitializedDataSize: | 128512 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x1000 |
| OSVersion: | 4 |
| ImageVersion: | - |
| SubsystemVersion: | 4 |
| Subsystem: | Windows GUI |
Summary
| Architecture: | IMAGE_FILE_MACHINE_I386 |
|---|---|
| Subsystem: | IMAGE_SUBSYSTEM_WINDOWS_GUI |
| Compilation Date: | 04-Aug-2006 18:28:10 |
| Detected languages: |
|
DOS Header
| Magic number: | MZ |
|---|---|
| Bytes on last page of file: | 0x0050 |
| Pages in file: | 0x0002 |
| Relocations: | 0x0000 |
| Size of header: | 0x0004 |
| Min extra paragraphs: | 0x000F |
| Max extra paragraphs: | 0xFFFF |
| Initial SS value: | 0x0000 |
| Initial SP value: | 0x00B8 |
| Checksum: | 0x0000 |
| Initial IP value: | 0x0000 |
| Initial CS value: | 0x0000 |
| Overlay number: | 0x001A |
| OEM identifier: | 0x0000 |
| OEM information: | 0x0000 |
| Address of NE header: | 0x00000200 |
PE Headers
| Signature: | PE |
|---|---|
| Machine: | IMAGE_FILE_MACHINE_I386 |
| Number of sections: | 4 |
| Time date stamp: | 04-Aug-2006 18:28:10 |
| Pointer to Symbol Table: | 0x00000000 |
| Number of symbols: | 0 |
| Size of Optional Header: | 0x00E0 |
| Characteristics: |
|
Sections
Name | Virtual Address | Virtual Size | Raw Size | Charateristics | Entropy |
|---|---|---|---|---|---|
.text | 0x00001000 | 0x0000B000 | 0x0000A400 | IMAGE_SCN_CNT_CODE, IMAGE_SCN_MEM_EXECUTE, IMAGE_SCN_MEM_READ | 6.39363 |
.data | 0x0000C000 | 0x00010000 | 0x00000E00 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ, IMAGE_SCN_MEM_WRITE | 5.83782 |
.idata | 0x0001C000 | 0x00001000 | 0x00001000 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ | 4.85932 |
.rsrc | 0x0001D000 | 0x0001D750 | 0x0001D800 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ | 6.6418 |
Resources
Title | Entropy | Size | Codepage | Language | Type |
|---|---|---|---|---|---|
1 | 5.10885 | 531 | Latin 1 / Western European | Russian - Russia | RT_MANIFEST |
2 | 3.18265 | 296 | Latin 1 / Western European | Process Default Language | RT_ICON |
7 | 3.24143 | 556 | Latin 1 / Western European | Russian - Russia | RT_STRING |
8 | 3.28574 | 946 | Latin 1 / Western European | Russian - Russia | RT_STRING |
9 | 3.04375 | 530 | Latin 1 / Western European | Russian - Russia | RT_STRING |
10 | 3.15563 | 638 | Latin 1 / Western European | Russian - Russia | RT_STRING |
100 | 1.97134 | 34 | Latin 1 / Western European | Process Default Language | RT_GROUP_ICON |
101 | 6.62164 | 112384 | Latin 1 / Western European | Process Default Language | RT_BITMAP |
ASKNEXTVOL | 3.42532 | 642 | Latin 1 / Western European | Russian - Russia | RT_DIALOG |
GETPASSWORD1 | 3.29928 | 314 | Latin 1 / Western European | Russian - Russia | RT_DIALOG |
Imports
ADVAPI32.DLL |
COMCTL32.DLL |
GDI32.DLL |
KERNEL32.DLL |
OLE32.DLL |
SHELL32.DLL |
USER32.DLL |
Total processes
46
Monitored processes
3
Malicious processes
1
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1328 | "C:\Users\admin\AppData\Local\Temp\Crocodile_Clips_v3.5.exe" | C:\Users\admin\AppData\Local\Temp\Crocodile_Clips_v3.5.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 3221226540 Modules
| |||||||||||||||
| 2852 | "C:\Archivos de programa\Crocodile Clips v3.5\CROCCLIP.EXE" | C:\Archivos de programa\Crocodile Clips v3.5\CROCCLIP.EXE | — | explorer.exe | |||||||||||
User: admin Company: Crocodile Clips Ltd. Integrity Level: MEDIUM Description: Crocclip Exit code: 0 Version: 3, 5, 0, 0 Modules
| |||||||||||||||
| 3320 | "C:\Users\admin\AppData\Local\Temp\Crocodile_Clips_v3.5.exe" | C:\Users\admin\AppData\Local\Temp\Crocodile_Clips_v3.5.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
Total events
240
Read events
228
Write events
12
Delete events
0
Modification events
| (PID) Process: | (3320) Crocodile_Clips_v3.5.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings |
| Operation: | write | Name: | ProxyEnable |
Value: 0 | |||
| (PID) Process: | (3320) Crocodile_Clips_v3.5.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\Connections |
| Operation: | write | Name: | SavedLegacySettings |
Value: 46000000A1000000010000000000000000000000000000000000000000000000C0E333BBEAB1D301000000000000000000000000020000001700000000000000FE800000000000007D6CB050D9C573F70B000000000000006D00330032005C004D00530049004D004700330032002E0064006C000100000004AA400014AA4000040000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000002000000C0A8016400000000000000000000000000000000000000000800000000000000805D3F00983740000008000002000000000000600000002060040000B8A94000020000008802000060040000B8A9400004000000F8010000B284000088B64000B84B400043003A000000000000000000000000000000000000000000 | |||
| (PID) Process: | (3320) Crocodile_Clips_v3.5.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 0 | |||
| (PID) Process: | (3320) Crocodile_Clips_v3.5.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 1 | |||
| (PID) Process: | (3320) Crocodile_Clips_v3.5.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (3320) Crocodile_Clips_v3.5.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (3320) Crocodile_Clips_v3.5.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (3320) Crocodile_Clips_v3.5.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR SFX |
| Operation: | write | Name: | C%%Archivos de programa%Crocodile Clips v3.5 |
Value: C:\Archivos de programa\Crocodile Clips v3.5 | |||
| (PID) Process: | (3320) Crocodile_Clips_v3.5.exe | Key: | HKEY_USERS\S-1-5-21-1302019708-1500728564-335382590-500\Software\WinRAR SFX |
| Operation: | write | Name: | C%%Program Files%WinRAR |
Value: C:\Program Files\WinRAR | |||
| (PID) Process: | (3320) Crocodile_Clips_v3.5.exe | Key: | HKEY_USERS\S-1-5-21-1302019708-1500728564-335382590-500\Software\WinRAR SFX |
| Operation: | write | Name: | C%%Archivos de programa%Crocodile Clips v3.5 |
Value: C:\Archivos de programa\Crocodile Clips v3.5 | |||
Executable files
2
Suspicious files
1
Text files
1
Unknown types
178
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3320 | Crocodile_Clips_v3.5.exe | C:\Archivos de programa\Crocodile Clips v3.5\Elemental\PR0002.CKT | mp3 | |
MD5:399F122F1928568478B33B8118F5D19A | SHA256:86579420994E24C93C19837607AD659FBFB2CAFCD1BF3E8895486ED30103DBB7 | |||
| 3320 | Crocodile_Clips_v3.5.exe | C:\Archivos de programa\Crocodile Clips v3.5\Elemental\PR0007.CKT | mp3 | |
MD5:CF5CBD56C46F67C852B0B8B14A44D413 | SHA256:9E899229253F2404D0D02F7FEDE3119B80A5DD24533AA841D7CA545D3164C1AB | |||
| 3320 | Crocodile_Clips_v3.5.exe | C:\Archivos de programa\Crocodile Clips v3.5\Elemental\PR0001.CKT | mp3 | |
MD5:6AECE5ACE6586E6938D099F20EC3F24D | SHA256:0F7A020DDE5619068216DB65A02243C0E530F7157701FAB7BA1A2F7A89487772 | |||
| 3320 | Crocodile_Clips_v3.5.exe | C:\Archivos de programa\Crocodile Clips v3.5\Elemental\PR0005.CKT | mp3 | |
MD5:BED7E3A50CF9610A0929F244F4F66F71 | SHA256:3801426970A5095A99D82FAFC57068A4AD161D32ACE4FBA5DAFDE93C99103A76 | |||
| 3320 | Crocodile_Clips_v3.5.exe | C:\Archivos de programa\Crocodile Clips v3.5\Elemental\PR0003.CKT | mp3 | |
MD5:821D296C32CE4D1DBF5B192B165D35DF | SHA256:52EFBF52A0EB5CA077F949C90DCDFC3E3F33AAB2C6A4C8F2F9F25A49F2CA1B18 | |||
| 3320 | Crocodile_Clips_v3.5.exe | C:\Archivos de programa\Crocodile Clips v3.5\Elemental\PR0008.CKT | mp3 | |
MD5:7EB1AEAF651E0FED5FA71D69FFF22C4C | SHA256:3F98CDDC716E641E9052E21800077B670BED6F11240BC7346F573084A0C72BE1 | |||
| 3320 | Crocodile_Clips_v3.5.exe | C:\Archivos de programa\Crocodile Clips v3.5\Elemental\PR0004.CKT | mp3 | |
MD5:4B726B52CE0AED53E8EC41509DFB8A3B | SHA256:179A8750D4A8811791AA9EE5B7D327FFBA5AC2F6BD884B91D16C6F157998EF1C | |||
| 3320 | Crocodile_Clips_v3.5.exe | C:\Archivos de programa\Crocodile Clips v3.5\Leeme.doc | document | |
MD5:B8C6897F81FF2B7E91411EE5F11EA477 | SHA256:5E52C9C5AF84D0774ECF80360E84774FA31464E7FBD2D9A83384B075E9EB8E20 | |||
| 3320 | Crocodile_Clips_v3.5.exe | C:\Archivos de programa\Crocodile Clips v3.5\CROCCLIP.CNT | text | |
MD5:1BAD49E9E9779081C6DBB926D5C24FFD | SHA256:50A67920BA0B8D1D65E2D7F480C6A12178FE2AD145863FB2F6087310039B5E10 | |||
| 3320 | Crocodile_Clips_v3.5.exe | C:\Archivos de programa\Crocodile Clips v3.5\DEISL1.ISU | isu | |
MD5:14BC43A16E96A5265EE546DB930B746D | SHA256:4FFA8F5B36C85CCA8EEAF37E82986A43B5481178ACFA551DE4B6DF689CFD36A2 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
0
DNS requests
0
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report