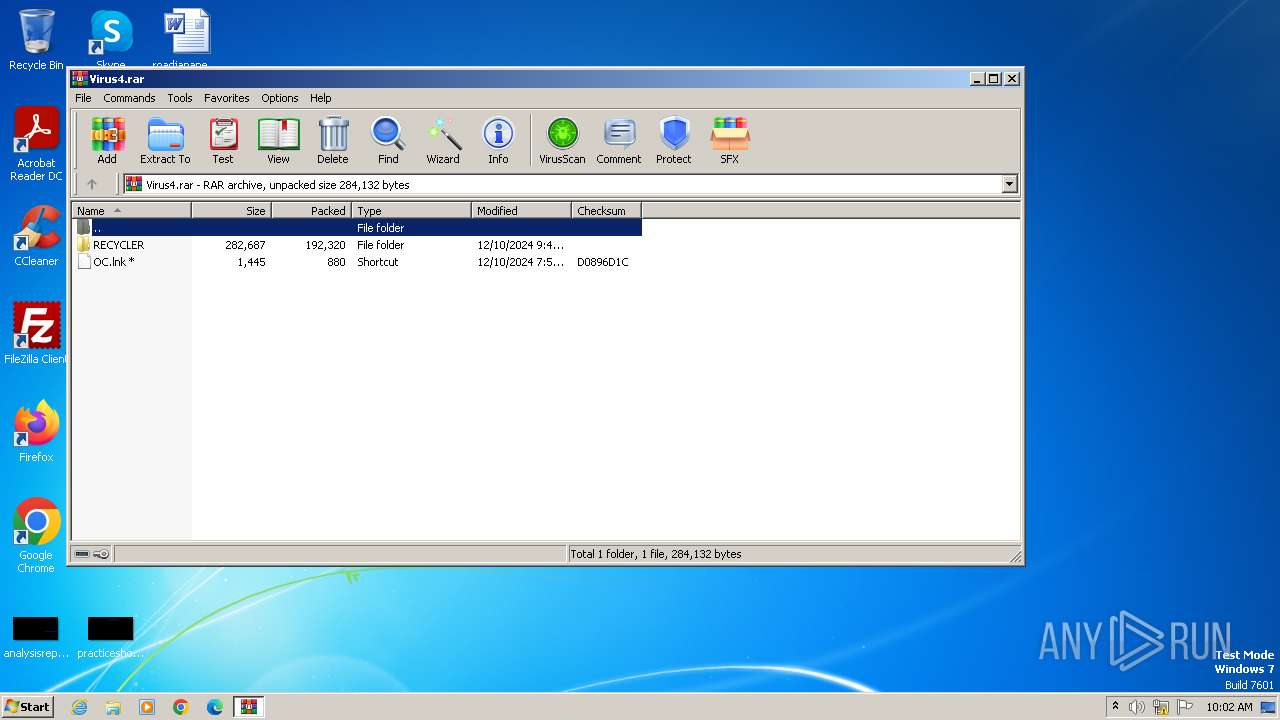
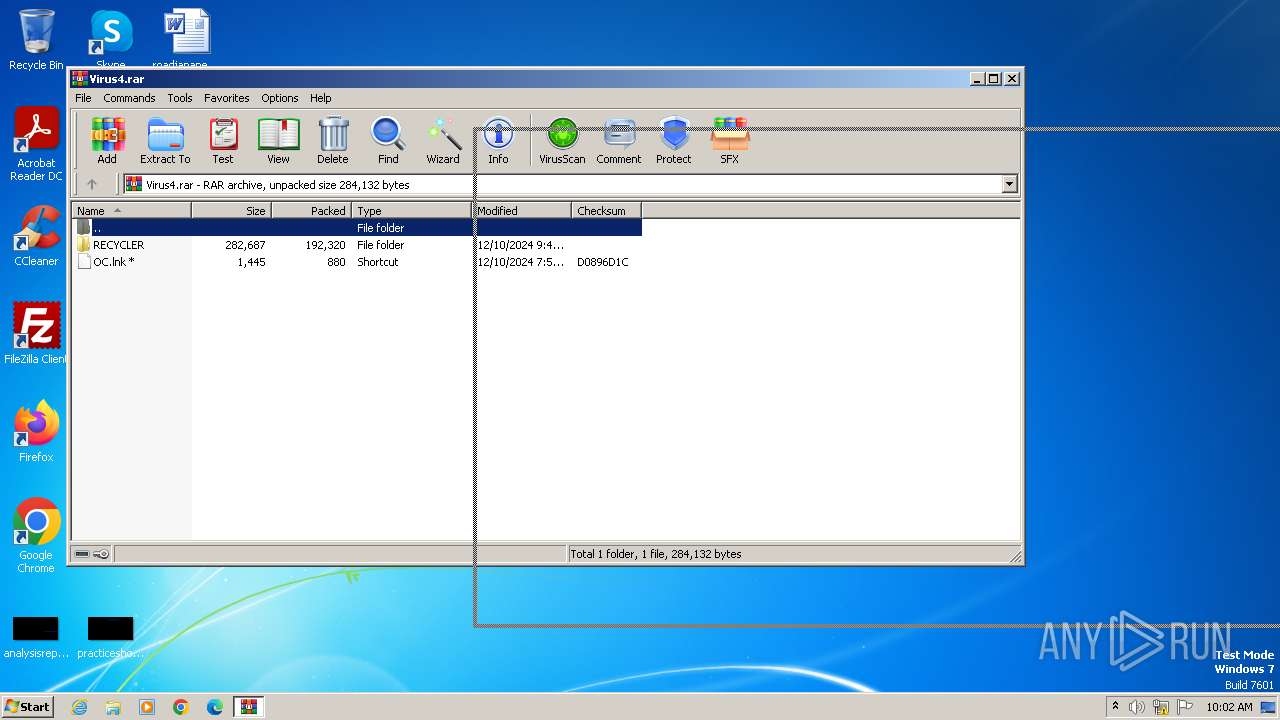
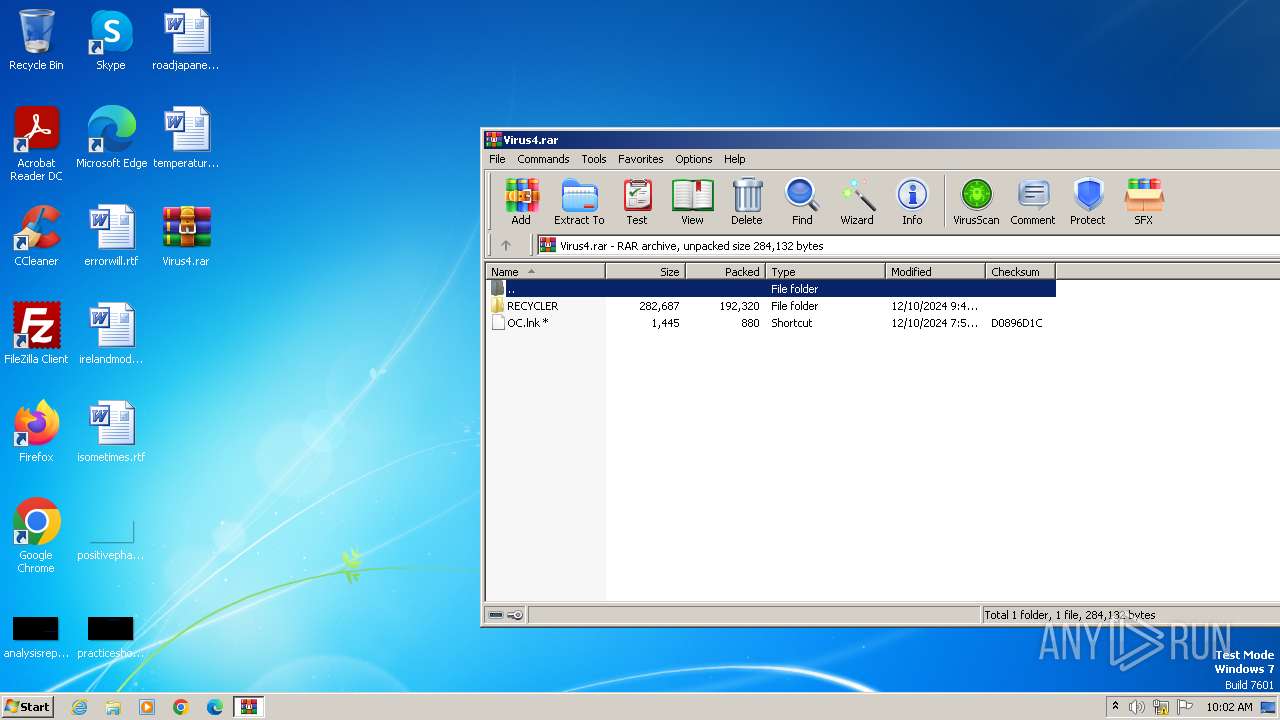
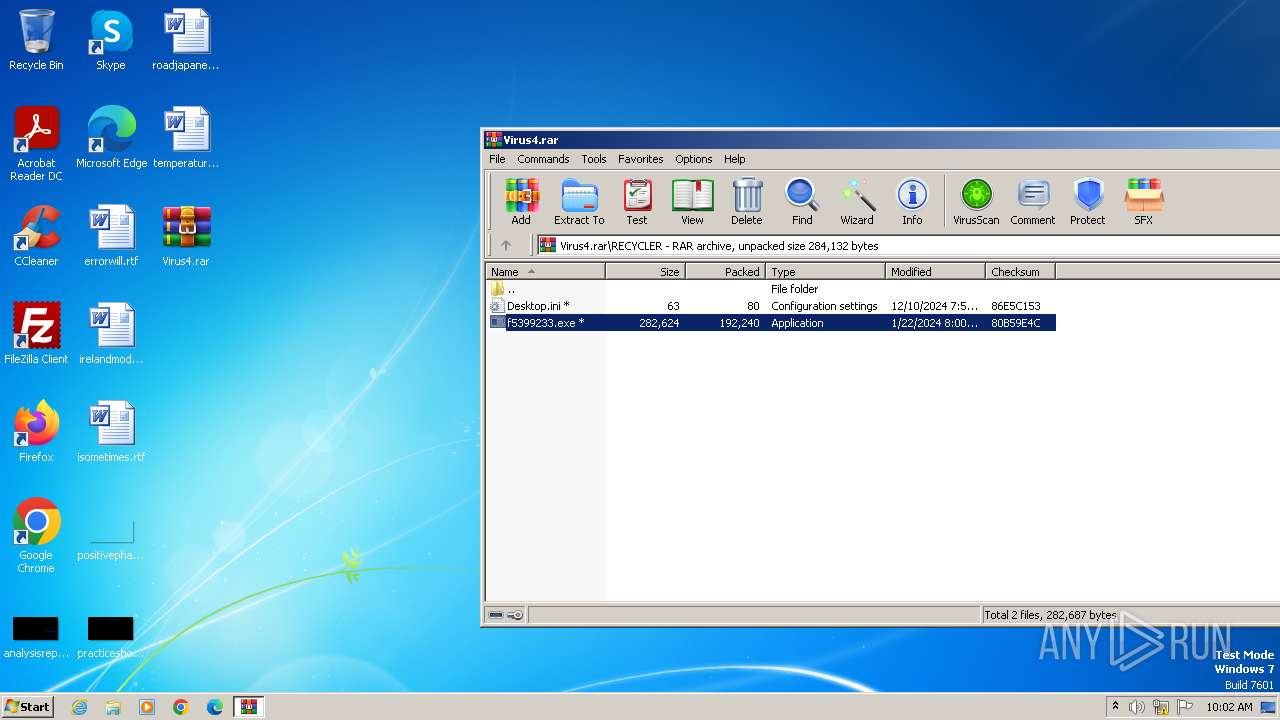
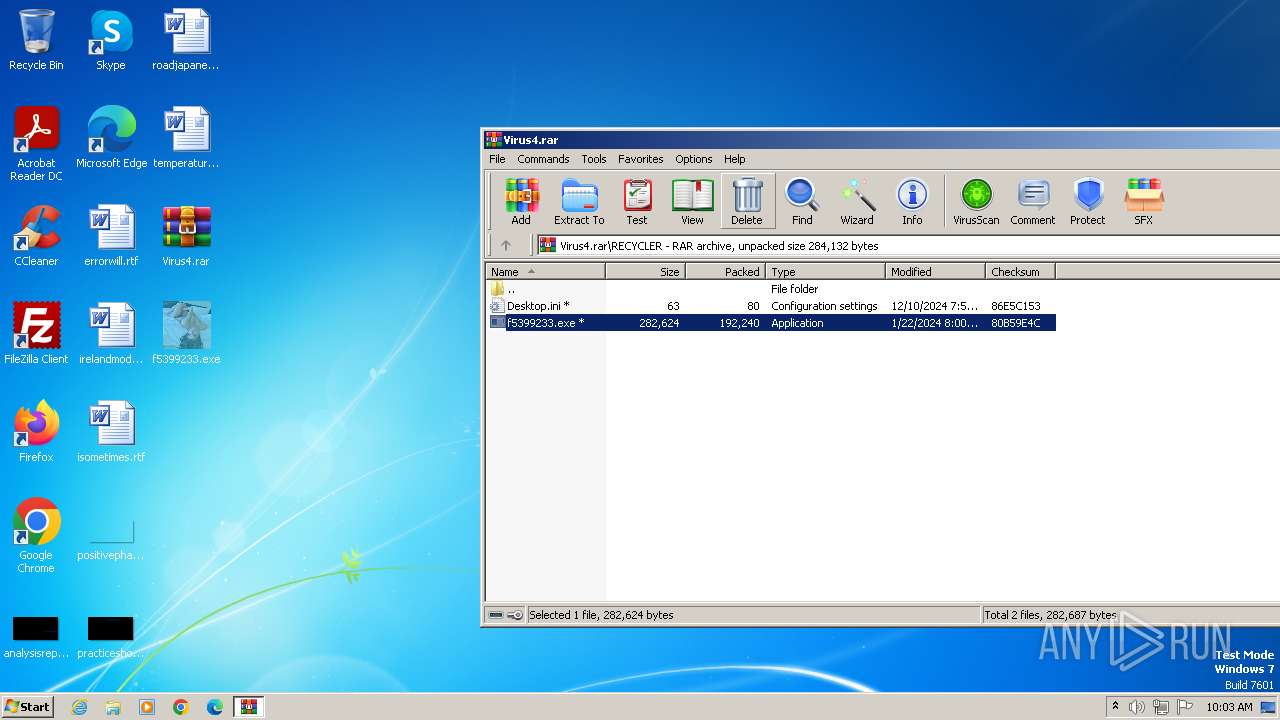
| File name: | Virus4.rar |
| Full analysis: | https://app.any.run/tasks/5fbcd1e4-7863-4a85-b685-4135717c66de |
| Verdict: | Malicious activity |
| Analysis date: | December 10, 2024, 10:02:28 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-rar |
| File info: | RAR archive data, v5 |
| MD5: | D2690DD4394A3E17871384E477946FE2 |
| SHA1: | 21022B550CCDB69AED4834D5C3D80CF951ED1964 |
| SHA256: | 819A9F9F63F94AC2217B3F05B6A4BC74737A3D47F7A8ACA1985640BDEF1DCC7C |
| SSDEEP: | 6144:SiDfF3n/gJoOmr23w1aw/Fj/7Ct4sPIfw+a/ky8oZRNOk:SiDtXUop23w1aQFjGt4sPI5okloZRsk |
MALICIOUS
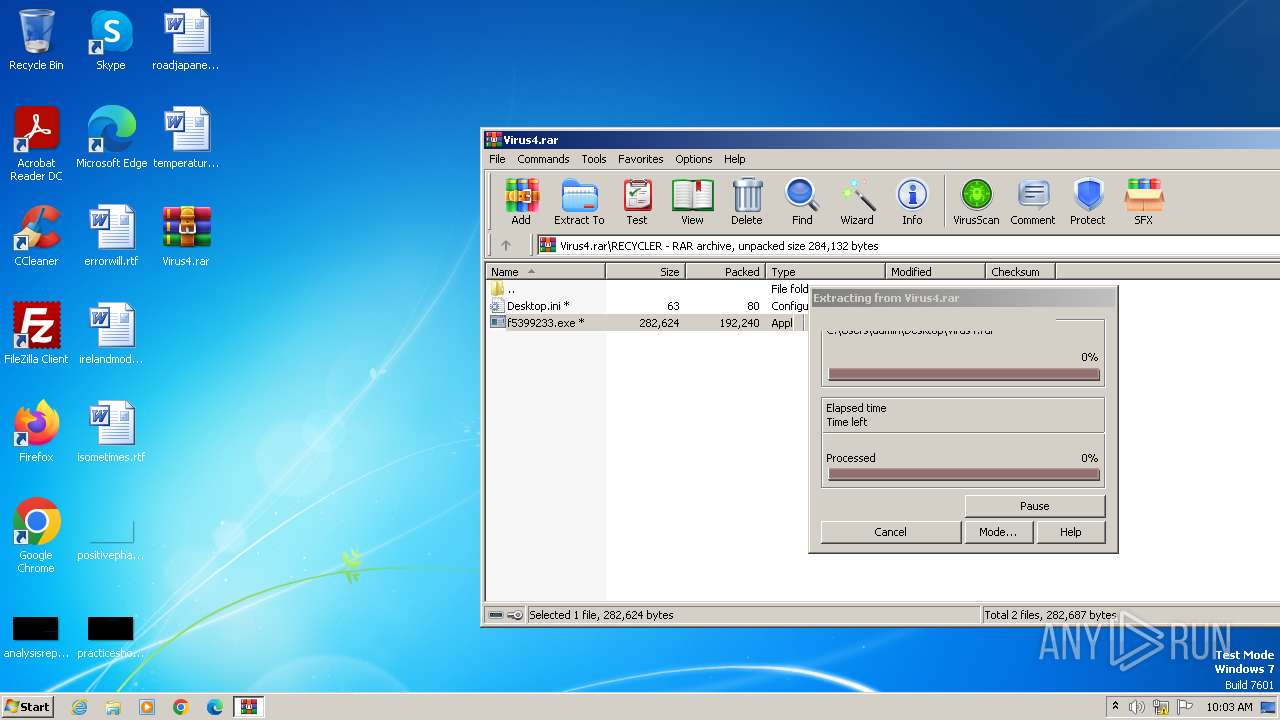
Generic archive extractor
- WinRAR.exe (PID: 1824)
Application was injected by another process
- taskeng.exe (PID: 124)
- dwm.exe (PID: 388)
- ctfmon.exe (PID: 1372)
- explorer.exe (PID: 932)
Runs injected code in another process
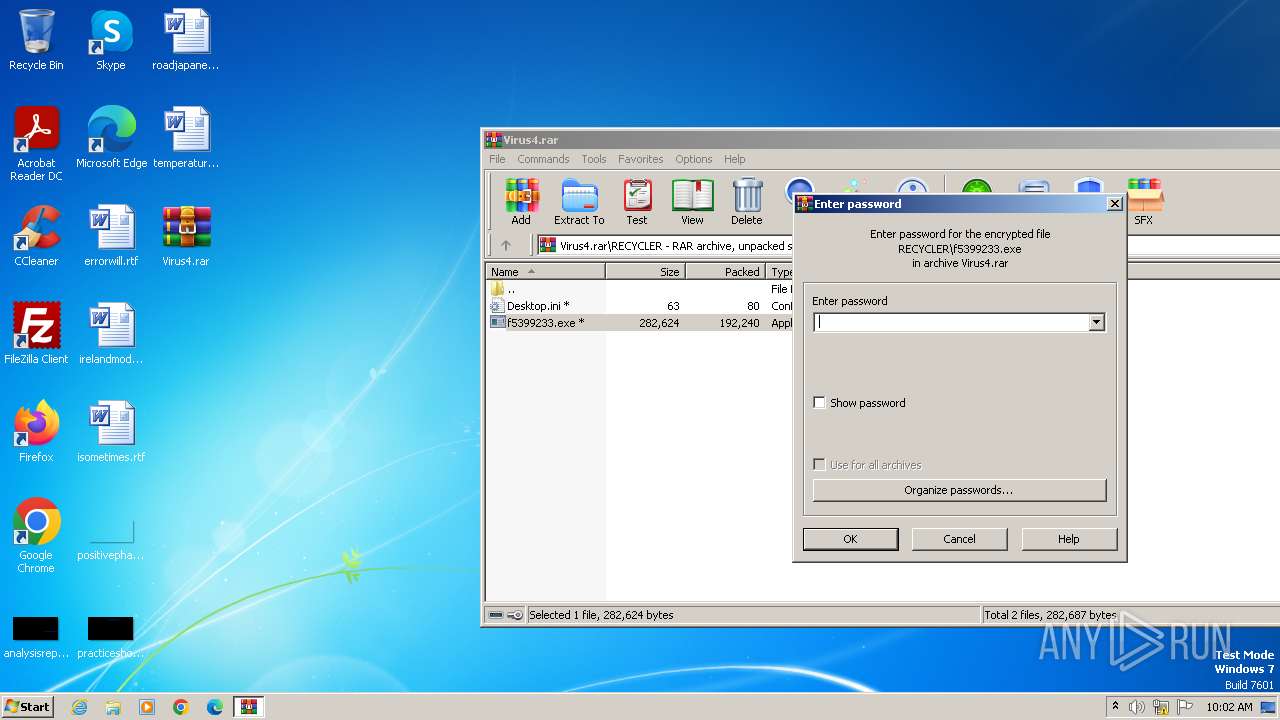
- f5399233.exe (PID: 3016)
Request for a sinkholed resource
- svchost.exe (PID: 1108)
Changes the autorun value in the registry
- explorer.exe (PID: 932)
SUSPICIOUS
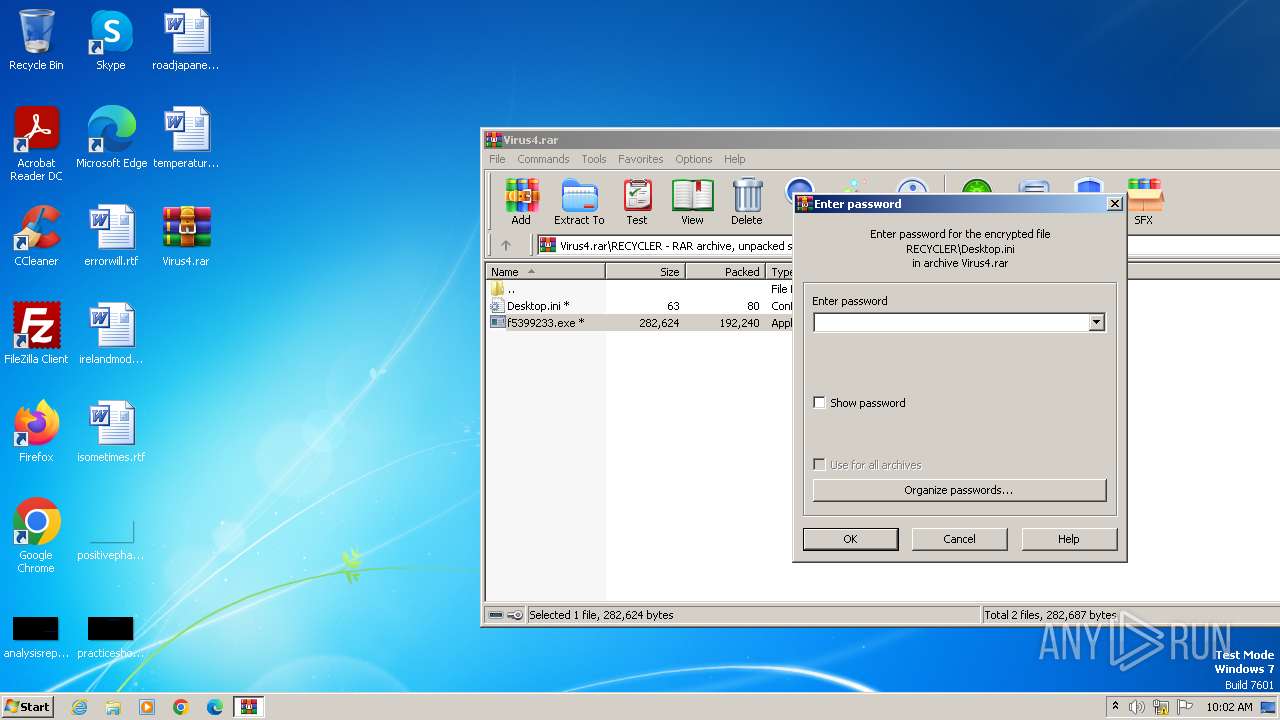
Write to the desktop.ini file (may be used to cloak folders)
- WinRAR.exe (PID: 1824)
Reads security settings of Internet Explorer
- WinRAR.exe (PID: 1824)
Application launched itself
- f5399233.exe (PID: 2260)
- cmd.exe (PID: 660)
- cmd.exe (PID: 1388)
- cmd.exe (PID: 1972)
- f5399233.exe (PID: 3396)
Starts application from unusual location
- f5399233.exe (PID: 2260)
- WinRAR.exe (PID: 1824)
- f5399233.exe (PID: 3016)
- explorer.exe (PID: 932)
Starts CMD.EXE for commands execution
- cmd.exe (PID: 660)
- explorer.exe (PID: 932)
- cmd.exe (PID: 1972)
- cmd.exe (PID: 1388)
INFO
Reads the Internet Settings
- explorer.exe (PID: 932)
Checks supported languages
- f5399233.exe (PID: 3016)
- f5399233.exe (PID: 2260)
- wmpnscfg.exe (PID: 3116)
- f5399233.exe (PID: 3396)
- f5399233.exe (PID: 532)
The process uses the downloaded file
- WinRAR.exe (PID: 1824)
- explorer.exe (PID: 932)
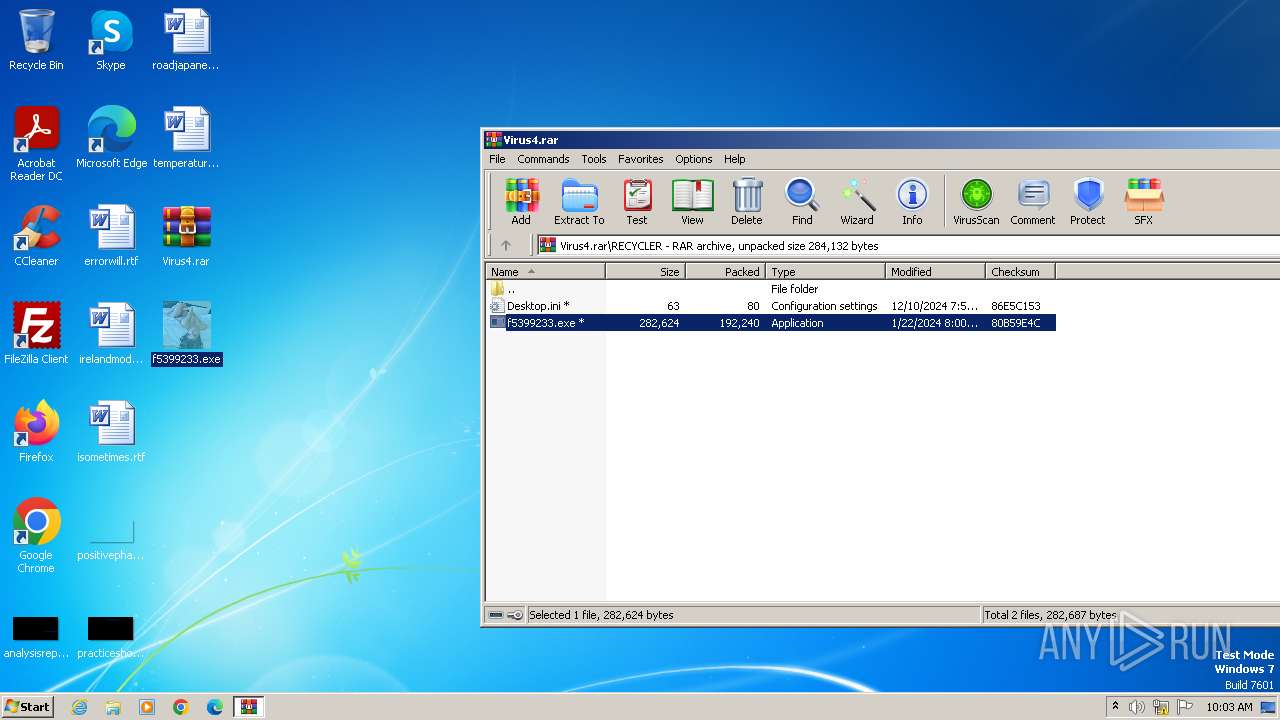
Executable content was dropped or overwritten
- WinRAR.exe (PID: 1824)
Reads the computer name
- f5399233.exe (PID: 3016)
- wmpnscfg.exe (PID: 3116)
- f5399233.exe (PID: 3396)
- f5399233.exe (PID: 532)
Creates files or folders in the user directory
- explorer.exe (PID: 932)
Checks proxy server information
- explorer.exe (PID: 932)
Reads security settings of Internet Explorer
- explorer.exe (PID: 932)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .rar | | | RAR compressed archive (v5.0) (61.5) |
|---|---|---|
| .rar | | | RAR compressed archive (gen) (38.4) |
EXIF
ZIP
| FileVersion: | RAR v5 |
|---|---|
| CompressedSize: | 80 |
| UncompressedSize: | 63 |
| OperatingSystem: | Win32 |
| ArchivedFileName: | RECYCLER/Desktop.ini |
Total processes
51
Monitored processes
17
Malicious processes
5
Suspicious processes
3
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 124 | taskeng.exe {AE534151-C06B-4791-966B-F00B6E167CB5} | C:\Windows\System32\taskeng.exe | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Task Scheduler Engine Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 388 | "C:\Windows\system32\Dwm.exe" | C:\Windows\System32\dwm.exe | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Desktop Window Manager Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 532 | C:\Users\admin\Desktop\f5399233.exe | C:\Users\admin\Desktop\f5399233.exe | — | f5399233.exe | |||||||||||
User: admin Company: Integrity Level: MEDIUM Description: Exit code: 0 Version: 2, 0, 8, 1 Modules
| |||||||||||||||
| 660 | "C:\Windows\system32\cmd.exe" | C:\Windows\System32\cmd.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 932 | C:\Windows\Explorer.EXE | C:\Windows\explorer.exe | — | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Explorer Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1108 | C:\Windows\system32\svchost.exe -k NetworkService | C:\Windows\System32\svchost.exe | services.exe | ||||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Host Process for Windows Services Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1372 | C:\Windows\System32\ctfmon.exe | C:\Windows\System32\ctfmon.exe | taskeng.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: CTF Loader Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1388 | C:\Windows\system32\cmd.exe /c "start "C:\Users\admin\Desktop\f5399233.exe" | C:\Windows\System32\cmd.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 1824 | "C:\Program Files\WinRAR\WinRAR.exe" C:\Users\admin\Desktop\Virus4.rar | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
| 1940 | cmd.exe | C:\Windows\System32\cmd.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
Total events
10 967
Read events
10 481
Write events
475
Delete events
11
Modification events
| (PID) Process: | (932) explorer.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Action Center\Checks\{C8E6F269-B90A-4053-A3BE-499AFCEC98C4}.check.0 |
| Operation: | write | Name: | CheckSetting |
Value: 01000000D08C9DDF0115D1118C7A00C04FC297EB01000000421EBB8D675C5B45B315A07138A133160000000002000000000010660000000100002000000040EBE5787A82BC45F45F69FF118604A87F0E9CD4E912FB43377672B473CD0F08000000000E8000000002000020000000B7DDCB48B0CF188A89C10B320252B79BDFC26B04C8824B977564C3750BF1863B30000000A3339EBE99343EC875EC879088B73F513FDA65B4C2145E7343C2F9BBBC1CA12DDF77E3A2322E4085139354505EE398E9400000000B0E55026EB9B809E75B23C2176AE54D593AEA6D75E79B57F48B495DEB017EE2F1612FB3B7186CA041CC1F840C1D799A94363C37E2EDEEC79667E602E803FBD4 | |||
| (PID) Process: | (932) explorer.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Explorer\FileExts\.rar\OpenWithList |
| Operation: | write | Name: | a |
Value: WinRAR.exe | |||
| (PID) Process: | (932) explorer.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Explorer\FileExts\.rar\OpenWithList |
| Operation: | write | Name: | MRUList |
Value: a | |||
| (PID) Process: | (932) explorer.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Explorer\FileExts\.rar\OpenWithProgids |
| Operation: | write | Name: | WinRAR |
Value: | |||
| (PID) Process: | (932) explorer.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Explorer\RecentDocs\.rar |
| Operation: | delete value | Name: | MRUList |
Value: | |||
| (PID) Process: | (932) explorer.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Explorer\RecentDocs |
| Operation: | write | Name: | 6 |
Value: 5600690072007500730034002E00720061007200000068003200000000000000000000005669727573342E7261722E6C6E6B00004A0008000400EFBE00000000000000002A000000000000000000000000000000000000000000000000005600690072007500730034002E007200610072002E006C006E006B0000001E000000 | |||
| (PID) Process: | (932) explorer.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Explorer\RecentDocs\.rar |
| Operation: | write | Name: | 0 |
Value: 5600690072007500730034002E00720061007200000068003200000000000000000000005669727573342E7261722E6C6E6B00004A0008000400EFBE00000000000000002A000000000000000000000000000000000000000000000000005600690072007500730034002E007200610072002E006C006E006B0000001E000000 | |||
| (PID) Process: | (932) explorer.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Explorer\RecentDocs\.rar |
| Operation: | write | Name: | MRUListEx |
Value: 00000000FFFFFFFF | |||
| (PID) Process: | (932) explorer.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (932) explorer.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
Executable files
4
Suspicious files
4
Text files
1
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 932 | explorer.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\AutomaticDestinations\1b4dd67f29cb1962.automaticDestinations-ms | binary | |
MD5:62B1DAA6ACC2EFA4CA8771F6D2887586 | SHA256:8395A743A7FA4A495C439435951FEEAF358D01EF94030EF5B427B2A2A08AD919 | |||
| 932 | explorer.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\AutomaticDestinations\290532160612e071.automaticDestinations-ms | binary | |
MD5:9607D1DBA0F0547CCE04066684849BC3 | SHA256:2C46403B5FA60069C71D7412BE7AC51E253225BF4DAA94E8F2339452082F6503 | |||
| 1824 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXb1824.27286\RECYCLER\f5399233.exe | executable | |
MD5:20B8D0698E3CA20D689820849923C553 | SHA256:0DA74DB7B75317200652EB317BB32029BBA74A1B3C09D2B00272CA2D9A697D5B | |||
| 932 | explorer.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\Virus4.rar.lnk | lnk | |
MD5:E9290EDF7A70303B47D2F4444DEA612E | SHA256:63C857742B84737A3812649BBE3D1411D17195FF1F85500DB2FF3CFA3EC12F0D | |||
| 1824 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXb1824.27286\ОС.lnk | lnk | |
MD5:BCAEE09C0BF995AB32E83F770908A579 | SHA256:1054B86F132B958381317AC4703E1D09E22EE206E4CB04A4D07B58C1ECAF9B3E | |||
| 932 | explorer.exe | C:\Users\admin\Desktop\f5399233.exe | executable | |
MD5:20B8D0698E3CA20D689820849923C553 | SHA256:0DA74DB7B75317200652EB317BB32029BBA74A1B3C09D2B00272CA2D9A697D5B | |||
| 1824 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXb1824.27286\RECYCLER\Desktop.ini | ini | |
MD5:E783BDD20A976EAEAAE1FF4624487420 | SHA256:2F65FA9C7ED712F493782ABF91467F869419A2F8B5ADF23B44019C08190FA3F3 | |||
| 932 | explorer.exe | C:\Users\admin\AppData\Roaming\Deeoer.exe | executable | |
MD5:20B8D0698E3CA20D689820849923C553 | SHA256:0DA74DB7B75317200652EB317BB32029BBA74A1B3C09D2B00272CA2D9A697D5B | |||
| 1824 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRb1824.28730\RECYCLER\f5399233.exe | executable | |
MD5:20B8D0698E3CA20D689820849923C553 | SHA256:0DA74DB7B75317200652EB317BB32029BBA74A1B3C09D2B00272CA2D9A697D5B | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
14
DNS requests
11
Threats
7
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 224.0.0.252:5355 | — | — | — | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
1108 | svchost.exe | 224.0.0.252:5355 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
932 | explorer.exe | 199.2.137.20:8080 | xD.0dayx.com | MICROSOFT-CORP-AS | US | malicious |
932 | explorer.exe | 199.2.137.20:80 | xD.0dayx.com | MICROSOFT-CORP-AS | US | malicious |
932 | explorer.exe | 208.100.26.242:8080 | xD.honeycat.org | STEADFAST | US | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
google.com |
| whitelisted |
api.wipmania.com |
| unknown |
xD.0dayx.com |
| malicious |
appupdate.org |
| malicious |
xD.0days.me |
| malicious |
appupdate02.info |
| malicious |
xD.a7aneek.net |
| malicious |
xD.honeycat.org |
| unknown |
xD.psybnc.c |
| unknown |
xD.masrawy.in |
| unknown |
Threats
PID | Process | Class | Message |
|---|---|---|---|
1108 | svchost.exe | A Network Trojan was detected | ET MALWARE DNS Reply Sinkhole - Microsoft - 199.2.137.0/24 |
1108 | svchost.exe | A Network Trojan was detected | ET MALWARE DNS Reply Sinkhole - Microsoft - 199.2.137.0/24 |
1108 | svchost.exe | A Network Trojan was detected | ET MALWARE DNS Reply Sinkhole - Microsoft - 199.2.137.0/24 |
1108 | svchost.exe | A Network Trojan was detected | ET MALWARE DNS Reply Sinkhole - Microsoft - 199.2.137.0/24 |
1108 | svchost.exe | A Network Trojan was detected | ET MALWARE DNS Reply Sinkhole - Microsoft - 199.2.137.0/24 |
1108 | svchost.exe | A Network Trojan was detected | ET MALWARE DNS Reply Sinkhole - Microsoft - 199.2.137.0/24 |
1108 | svchost.exe | A Network Trojan was detected | ET MALWARE DNS Reply Sinkhole - Microsoft - 199.2.137.0/24 |