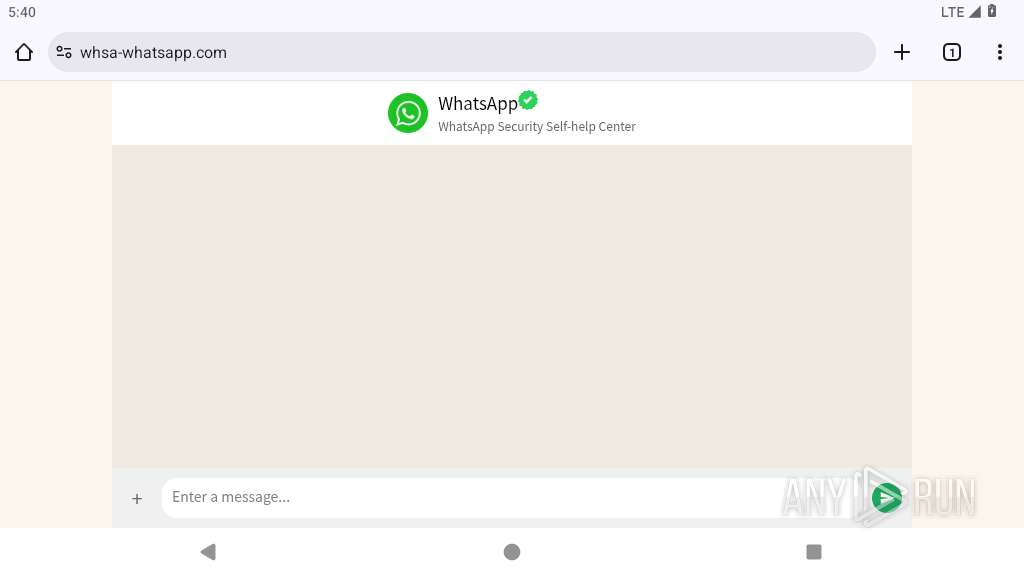
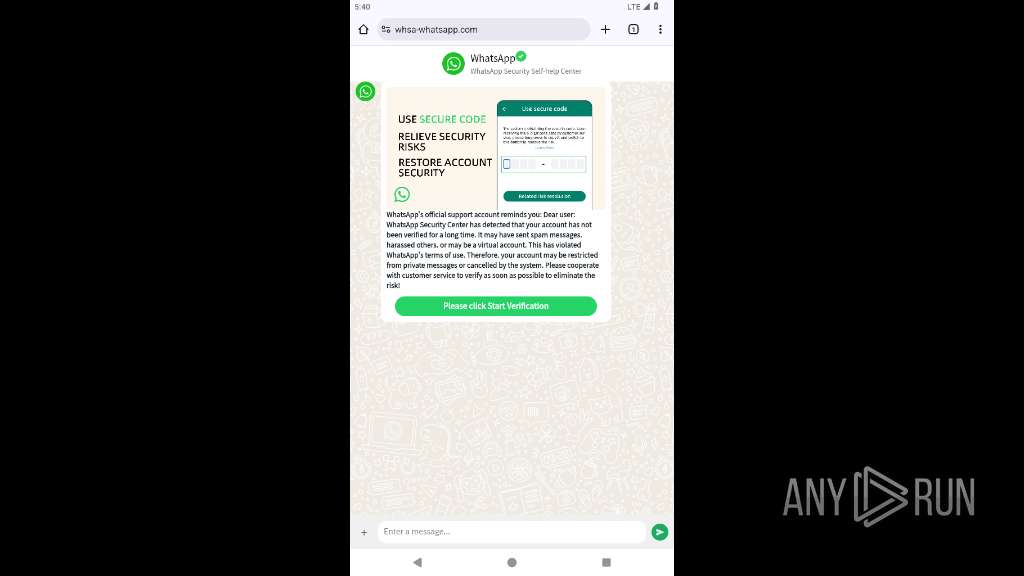
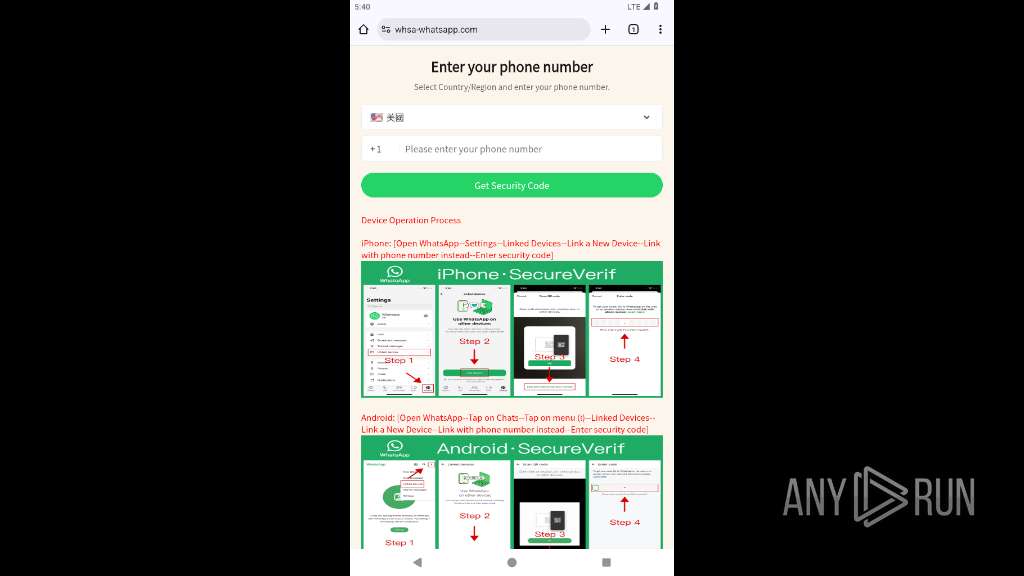
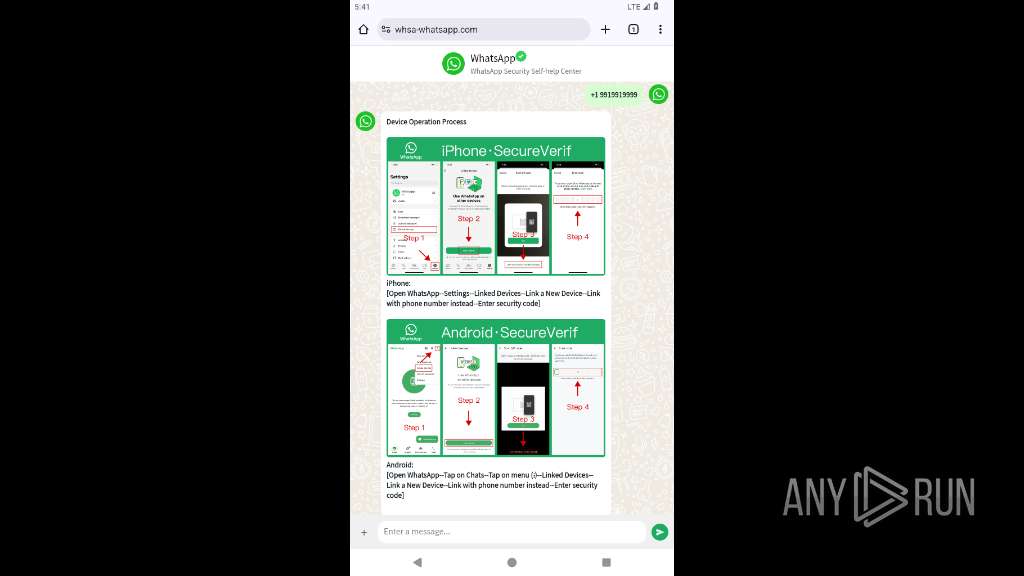
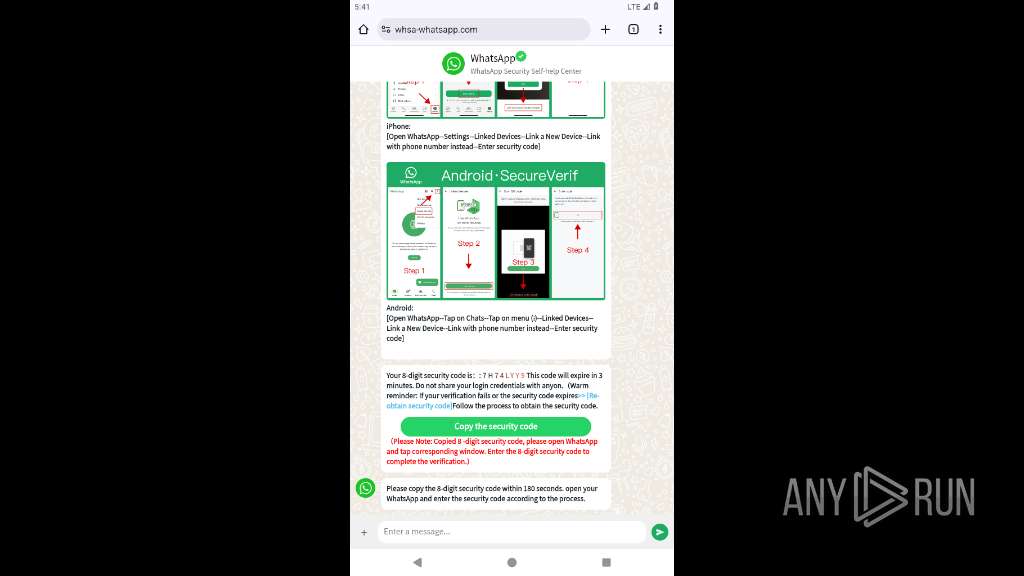
| URL: | https://whsa-whatsapp.com |
| Full analysis: | https://app.any.run/tasks/4c540d60-21fb-43ec-b33f-c84e3d69f0f2 |
| Verdict: | Malicious activity |
| Analysis date: | June 17, 2025, 05:40:14 |
| OS: | Android 14 |
| Tags: | |
| Indicators: | |
| MD5: | 19372212C2EB214F9EE06CFAC3C4E727 |
| SHA1: | 1AF3322F6FEE4D89C14404ACAC1D6D0EC55E9706 |
| SHA256: | 819520631F4E3EDC14DD93A74337C29173D3D40B37534B595F213D265F4CFD21 |
| SSDEEP: | 3:N8cWENbiK:2cMK |
MALICIOUS
PHISHING has been detected (SURICATA)
- app_process64 (PID: 2217)
SUSPICIOUS
Connects to unusual port
- app_process64 (PID: 2217)
INFO
No info indicators.
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
130
Monitored processes
7
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process |
|---|---|---|---|---|
| 2217 | org.chromium.chrome | /system/bin/app_process64 | app_process64 | |
User: root Integrity Level: UNKNOWN Exit code: 0 | ||||
| 2260 | org.chromium.chrome_zygote | /system/bin/app_process64 | — | app_process64 |
User: root Integrity Level: UNKNOWN Exit code: 0 | ||||
| 2275 | org.chromium.chrome_zygote | /system/bin/app_process64 | — | app_process64 |
User: u0_a73 Integrity Level: UNKNOWN Exit code: 0 | ||||
| 2312 | org.chromium.chrome:privileged_process0 | /system/bin/app_process64 | — | app_process64 |
User: root Integrity Level: UNKNOWN Exit code: 0 | ||||
| 2333 | com.android.adservices.api | /system/bin/app_process64 | — | app_process64 |
User: root Integrity Level: UNKNOWN Exit code: 0 | ||||
| 2396 | org.chromium.chrome_zygote | /system/bin/app_process64 | — | app_process64 |
User: u0_a73 Integrity Level: UNKNOWN Exit code: 0 | ||||
| 2425 | com.android.providers.partnerbookmarks | /system/bin/app_process64 | — | app_process64 |
User: root Integrity Level: UNKNOWN Exit code: 0 | ||||
Total events
0
Read events
0
Write events
0
Delete events
0
Modification events
Executable files
0
Suspicious files
0
Text files
0
Unknown types
0
Dropped files
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
2
TCP/UDP connections
24
DNS requests
31
Threats
11
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | GET | 204 | 142.250.186.131:80 | http://connectivitycheck.gstatic.com/generate_204 | unknown | — | — | whitelisted |
2217 | app_process64 | GET | 200 | 142.250.186.174:80 | http://clients2.google.com/time/1/current?cup2key=9:MAN_ADp6M5NZiIR_SdgURcNwBpEHP-w3_PDkgnXozhM&cup2hreq=e3b0c44298fc1c149afbf4c8996fb92427ae41e4649b934ca495991b7852b855 | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
446 | mdnsd | 224.0.0.251:5353 | — | — | — | unknown |
— | — | 216.239.35.12:123 | time.android.com | — | — | whitelisted |
— | — | 142.250.186.131:80 | connectivitycheck.gstatic.com | GOOGLE | US | whitelisted |
— | — | 142.250.185.68:443 | www.google.com | GOOGLE | US | whitelisted |
— | — | 142.250.27.81:443 | staging-remoteprovisioning.sandbox.googleapis.com | GOOGLE | US | whitelisted |
573 | app_process64 | 216.239.35.8:123 | time.android.com | — | — | whitelisted |
573 | app_process64 | 216.239.35.0:123 | time.android.com | — | — | whitelisted |
2217 | app_process64 | 142.250.186.174:80 | clients2.google.com | GOOGLE | US | whitelisted |
2217 | app_process64 | 142.250.27.84:443 | accounts.google.com | GOOGLE | US | whitelisted |
2217 | app_process64 | 8.210.160.184:443 | whsa-whatsapp.com | Alibaba US Technology Co., Ltd. | HK | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
www.google.com |
| whitelisted |
connectivitycheck.gstatic.com |
| whitelisted |
time.android.com |
| whitelisted |
staging-remoteprovisioning.sandbox.googleapis.com |
| whitelisted |
google.com |
| whitelisted |
clients2.google.com |
| whitelisted |
whsa-whatsapp.com |
| unknown |
accounts.google.com |
| whitelisted |
vip.kaso2p.vip |
| unknown |
api.vore.top |
| unknown |
Threats
PID | Process | Class | Message |
|---|---|---|---|
— | — | Misc activity | ET INFO Android Device Connectivity Check |
2217 | app_process64 | Possible Social Engineering Attempted | PHISHING [ANY.RUN] Suspected Phishing Domain (whsa-whatsapp .com) |
2217 | app_process64 | Generic Protocol Command Decode | SURICATA QUIC failed decrypt |
2217 | app_process64 | Generic Protocol Command Decode | SURICATA QUIC failed decrypt |
2217 | app_process64 | Generic Protocol Command Decode | SURICATA QUIC failed decrypt |
2217 | app_process64 | Generic Protocol Command Decode | SURICATA QUIC failed decrypt |
2217 | app_process64 | Generic Protocol Command Decode | SURICATA QUIC failed decrypt |
2217 | app_process64 | Generic Protocol Command Decode | SURICATA QUIC failed decrypt |
2217 | app_process64 | Generic Protocol Command Decode | SURICATA QUIC failed decrypt |
2217 | app_process64 | Generic Protocol Command Decode | SURICATA QUIC failed decrypt |