| File name: | WARZONE RAT 2.70 POISON - cortexnet.cc.7z |
| Full analysis: | https://app.any.run/tasks/757ee264-9a53-4897-890d-3784f9c68a07 |
| Verdict: | Malicious activity |
| Analysis date: | February 10, 2023, 05:38:16 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/x-7z-compressed |
| File info: | 7-zip archive data, version 0.4 |
| MD5: | C4C26FFD14CAD3AB6135155CA524B1B2 |
| SHA1: | 10C4E14B1C5922D0FDB10D307019F750DDD7ADD0 |
| SHA256: | 818F218F3D84F9CF715E548A0BC1906F206B81775761A73E06FAE07AD888770B |
| SSDEEP: | 393216:ZyrDURlHD+AGDhhjrGVtB+crh+Kzju5kgQSqMN/:Zy3U7HqAqjrGVKcA8u5kD4N/ |
MALICIOUS
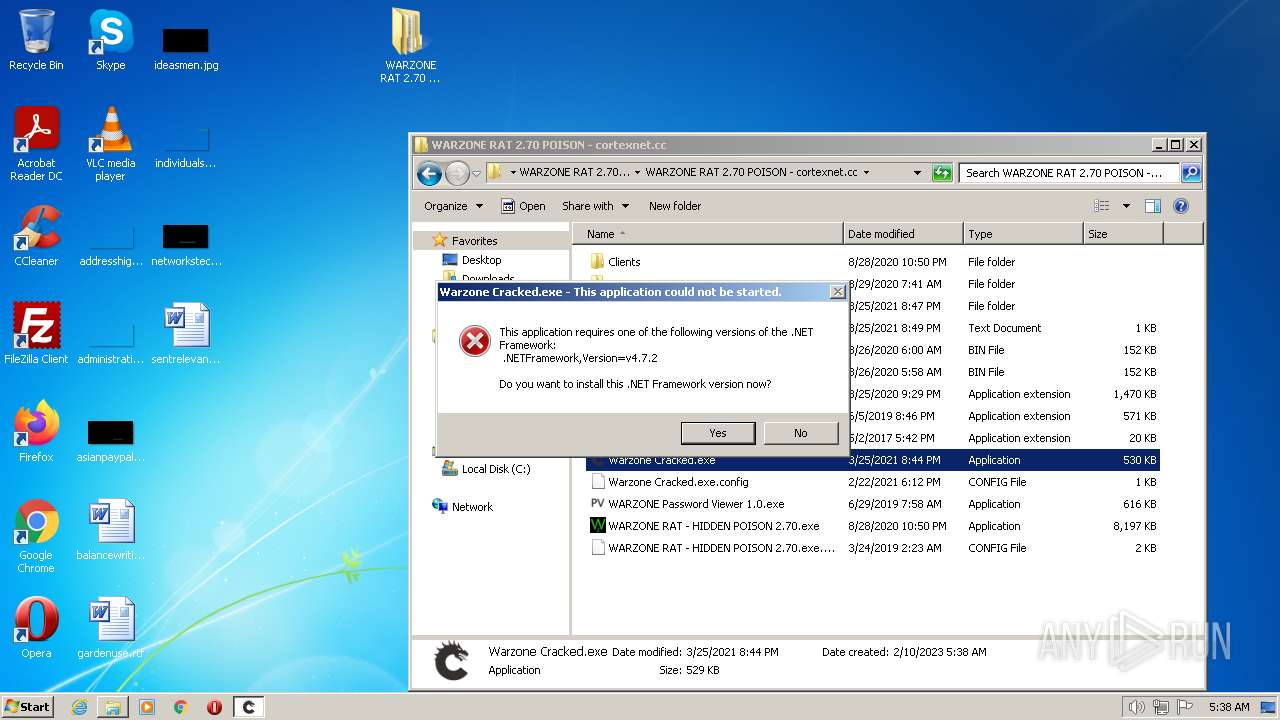
Application was dropped or rewritten from another process
- Warzone Cracked.exe (PID: 3688)
SUSPICIOUS
Reads the Internet Settings
- Warzone Cracked.exe (PID: 3688)
The process drops Mozilla's DLL files
- WinRAR.exe (PID: 3256)
INFO
Manual execution by a user
- wmpnscfg.exe (PID: 1760)
- Warzone Cracked.exe (PID: 3688)
Reads the machine GUID from the registry
- wmpnscfg.exe (PID: 1760)
Drops a file that was compiled in debug mode
- WinRAR.exe (PID: 3256)
Checks supported languages
- wmpnscfg.exe (PID: 1760)
- Warzone Cracked.exe (PID: 3688)
The process checks LSA protection
- wmpnscfg.exe (PID: 1760)
- iexplore.exe (PID: 2280)
- iexplore.exe (PID: 1388)
Create files in a temporary directory
- iexplore.exe (PID: 1388)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 3256)
Dropped object may contain Bitcoin addresses
- iexplore.exe (PID: 2280)
- iexplore.exe (PID: 1388)
Reads the computer name
- Warzone Cracked.exe (PID: 3688)
- wmpnscfg.exe (PID: 1760)
Application launched itself
- iexplore.exe (PID: 1388)
Drops the executable file immediately after the start
- WinRAR.exe (PID: 3256)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .7z | | | 7-Zip compressed archive (v0.4) (57.1) |
|---|---|---|
| .7z | | | 7-Zip compressed archive (gen) (42.8) |
Total processes
45
Monitored processes
5
Malicious processes
0
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1388 | "C:\Program Files\Internet Explorer\iexplore.exe" http://go.microsoft.com/fwlink/?prd=11324&pver=4.5&sbp=AppLaunch&plcid=0x409&o1=.NETFramework,Version=v4.7.2&processName=Warzone Cracked.exe&platform=0000&osver=5&isServer=0&shimver=4.0.30319.34209 | C:\Program Files\Internet Explorer\iexplore.exe | Warzone Cracked.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 1760 | "C:\Program Files\Windows Media Player\wmpnscfg.exe" | C:\Program Files\Windows Media Player\wmpnscfg.exe | — | Explorer.EXE | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Media Player Network Sharing Service Configuration Application Exit code: 0 Version: 12.0.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2280 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:1388 CREDAT:267521 /prefetch:2 | C:\Program Files\Internet Explorer\iexplore.exe | iexplore.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 3256 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Temp\WARZONE RAT 2.70 POISON - cortexnet.cc.7z" | C:\Program Files\WinRAR\WinRAR.exe | Explorer.EXE | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
| 3688 | "C:\Users\admin\Desktop\WARZONE RAT 2.70 POISON - cortexnet.cc\WARZONE RAT 2.70 POISON - cortexnet.cc\Warzone Cracked.exe" | C:\Users\admin\Desktop\WARZONE RAT 2.70 POISON - cortexnet.cc\WARZONE RAT 2.70 POISON - cortexnet.cc\Warzone Cracked.exe | — | Explorer.EXE | |||||||||||
User: admin Integrity Level: MEDIUM Description: Warzone Cracked Exit code: 2148734720 Version: 1.0.0.0 Modules
| |||||||||||||||
Total events
28 202
Read events
27 852
Write events
340
Delete events
10
Modification events
| (PID) Process: | (3256) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (3256) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (3256) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\16D\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (3256) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\virtio_ivshmem_master_build.zip | |||
| (PID) Process: | (3256) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\Win7-KB3191566-x86.zip | |||
| (PID) Process: | (3256) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\phacker.zip | |||
| (PID) Process: | (3256) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\WARZONE RAT 2.70 POISON - cortexnet.cc.7z | |||
| (PID) Process: | (3256) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (3256) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (3256) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
Executable files
40
Suspicious files
28
Text files
72
Unknown types
28
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3256 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3256.49559\WARZONE RAT 2.70 POISON - cortexnet.cc\WARZONE RAT 2.70 POISON - cortexnet.cc\cracked by cortexnet.cc.txt | text | |
MD5:D25DD3C924DB6DABF2DBA54F34298BC3 | SHA256:F464F28BC1357F5E5A1B917521D76D0350AD8B4109F15D43CD6EB7994E2B7D14 | |||
| 3256 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3256.49559\WARZONE RAT 2.70 POISON - cortexnet.cc\WARZONE RAT 2.70 POISON - cortexnet.cc\Datas\rdpwrap64.dll | executable | |
MD5:C4063372AFE486D5E9A11C5B68E0524F | SHA256:FC1F3FC182CEF9BCEF5192E4FA4569697E27852CBFFB7A55EA6118C603DDC420 | |||
| 3256 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3256.49559\WARZONE RAT 2.70 POISON - cortexnet.cc\WARZONE RAT 2.70 POISON - cortexnet.cc\Datas\rV2.bsp1 | binary | |
MD5:7DE0184ED564E0D2076D9B3520E7CCE6 | SHA256:4449673175412AACBAB5A485DEAE55DD11B2EFE67A06525DAD05C948542F7387 | |||
| 3256 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3256.49559\WARZONE RAT 2.70 POISON - cortexnet.cc\WARZONE RAT 2.70 POISON - cortexnet.cc\Warzone Cracked.exe.config | xml | |
MD5:159280C802BED8DE261D40FCF7130BC4 | SHA256:65F6FF8549E1F144AB78432F69A51168A7F1B3021D23C20BF9D51393D4C92368 | |||
| 3256 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3256.49559\WARZONE RAT 2.70 POISON - cortexnet.cc\WARZONE RAT 2.70 POISON - cortexnet.cc\Injector\Bootstrap.exp | exp | |
MD5:B813D59E0E8567435350927CA6957B1C | SHA256:88E1A3E9C0EC7E274B83EB1761782A6C68F6D21F59562E11CF444A33B7AC381C | |||
| 3256 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3256.49559\WARZONE RAT 2.70 POISON - cortexnet.cc\WARZONE RAT 2.70 POISON - cortexnet.cc\Datas\geoip\GeoIP.dat | binary | |
MD5:B64EA0C3E9617CCD2F22D8568676A325 | SHA256:432E12E688449C2CF1B184C94E2E964F9E09398C194888A7FE1A5B1F8CF3059B | |||
| 3256 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3256.49559\WARZONE RAT 2.70 POISON - cortexnet.cc\WARZONE RAT 2.70 POISON - cortexnet.cc\Datas\rdpwrap.ini | binary | |
MD5:6BC395161B04AA555D5A4E8EB8320020 | SHA256:23390DFCDA60F292BA1E52ABB5BA2F829335351F4F9B1D33A9A6AD7A9BF5E2BE | |||
| 3256 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3256.49559\WARZONE RAT 2.70 POISON - cortexnet.cc\WARZONE RAT 2.70 POISON - cortexnet.cc\Datas\firefox.dlls | executable | |
MD5:A26861558315278D5960FE1BF58B1950 | SHA256:B52720863EC78E0F7BFF98E6C809FDF50AB2D0EA361E95EB5341E870AAFB0354 | |||
| 3256 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3256.49559\WARZONE RAT 2.70 POISON - cortexnet.cc\WARZONE RAT 2.70 POISON - cortexnet.cc\Datas\rV.bsp1 | binary | |
MD5:A23A6C143732E1C83BF09FE71C78AA93 | SHA256:E48D338DD5FC668888EB89E6C35E8F4B4F61B4D4BC35574C548A1BC9DBF52054 | |||
| 3256 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3256.49559\WARZONE RAT 2.70 POISON - cortexnet.cc\WARZONE RAT 2.70 POISON - cortexnet.cc\Datas\rvncviewer.exe | executable | |
MD5:27561E722C736AB5A77110790402999B | SHA256:5E49A7FEC8C9F81B191E5FA69BDB1A627814631813FEDFC4136C71E55CD57C0F | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
8
TCP/UDP connections
32
DNS requests
18
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2280 | iexplore.exe | GET | — | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEA177el9ggmWelJjG4vdGL0%3D | US | — | — | whitelisted |
2280 | iexplore.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAqvpsXKY8RRQeo74ffHUxc%3D | US | der | 471 b | whitelisted |
2280 | iexplore.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEALnkXH7gCHpP%2BLZg4NMUMA%3D | US | der | 471 b | whitelisted |
2280 | iexplore.exe | GET | 200 | 8.253.246.254:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?9037ec57f11e85d4 | US | compressed | 4.70 Kb | whitelisted |
2280 | iexplore.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAbY2QTVWENG9oovp1QifsQ%3D | US | der | 471 b | whitelisted |
2280 | iexplore.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAxq6XzO1ZmDhpCgCp6lMhQ%3D | US | der | 471 b | whitelisted |
2280 | iexplore.exe | GET | 200 | 8.59.0.190:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?b637c2561c06c859 | US | compressed | 4.70 Kb | whitelisted |
1388 | iexplore.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTBL0V27RVZ7LBduom%2FnYB45SPUEwQU5Z1ZMIJHWMys%2BghUNoZ7OrUETfACEA%2BnRyLFPYjID1ie%2Bx%2BdSjo%3D | US | der | 1.47 Kb | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2280 | iexplore.exe | 93.184.220.29:80 | ocsp.digicert.com | EDGECAST | GB | whitelisted |
1388 | iexplore.exe | 13.107.21.200:443 | www.bing.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
1388 | iexplore.exe | 93.184.220.29:80 | ocsp.digicert.com | EDGECAST | GB | whitelisted |
2280 | iexplore.exe | 2.21.20.153:443 | statics-marketingsites-wcus-ms-com.akamaized.net | Akamai International B.V. | DE | suspicious |
— | — | 2.21.20.153:443 | statics-marketingsites-wcus-ms-com.akamaized.net | Akamai International B.V. | DE | suspicious |
2280 | iexplore.exe | 2.18.233.62:443 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
2280 | iexplore.exe | 8.59.0.190:80 | ctldl.windowsupdate.com | LEVEL3 | US | unknown |
— | — | 2.18.233.62:443 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
2280 | iexplore.exe | 2.21.20.144:443 | img-prod-cms-rt-microsoft-com.akamaized.net | Akamai International B.V. | DE | suspicious |
— | — | 13.107.237.45:443 | dotnet.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
go.microsoft.com |
| whitelisted |
ctldl.windowsupdate.com |
| whitelisted |
api.bing.com |
| whitelisted |
www.bing.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
dotnet.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
statics-marketingsites-wcus-ms-com.akamaized.net |
| whitelisted |
js.monitor.azure.com |
| whitelisted |
target.microsoft.com |
| whitelisted |