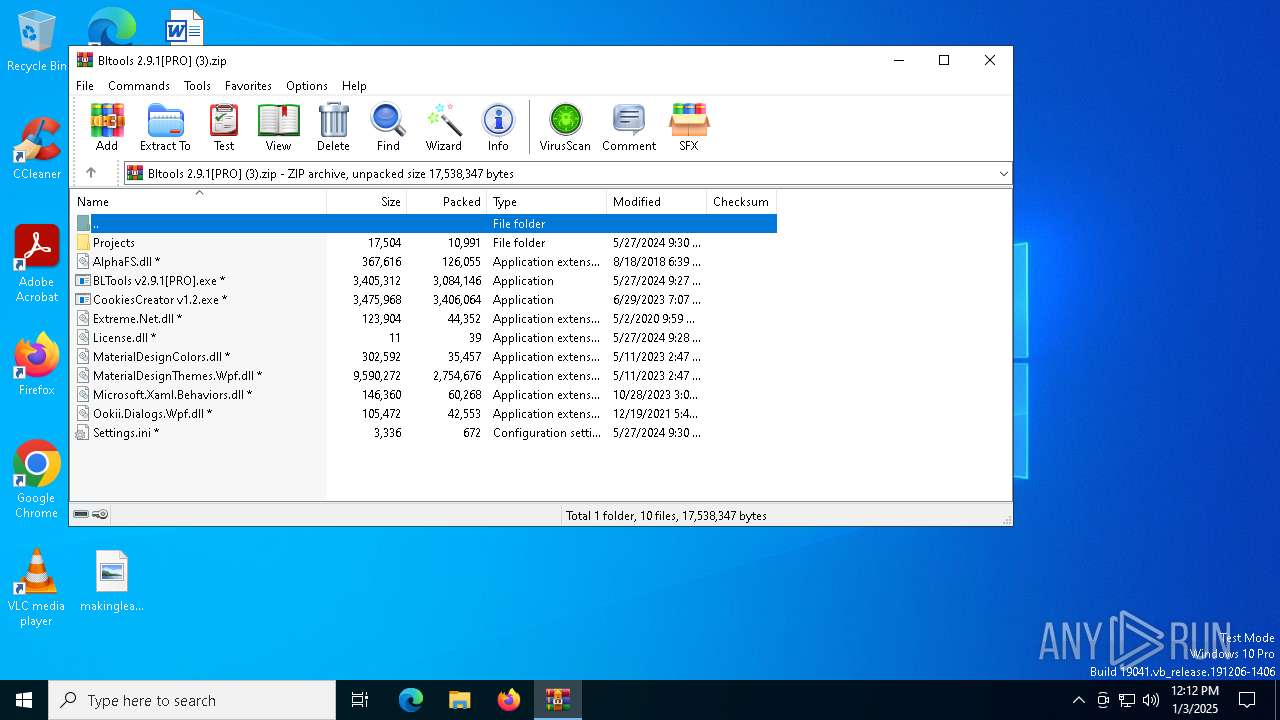
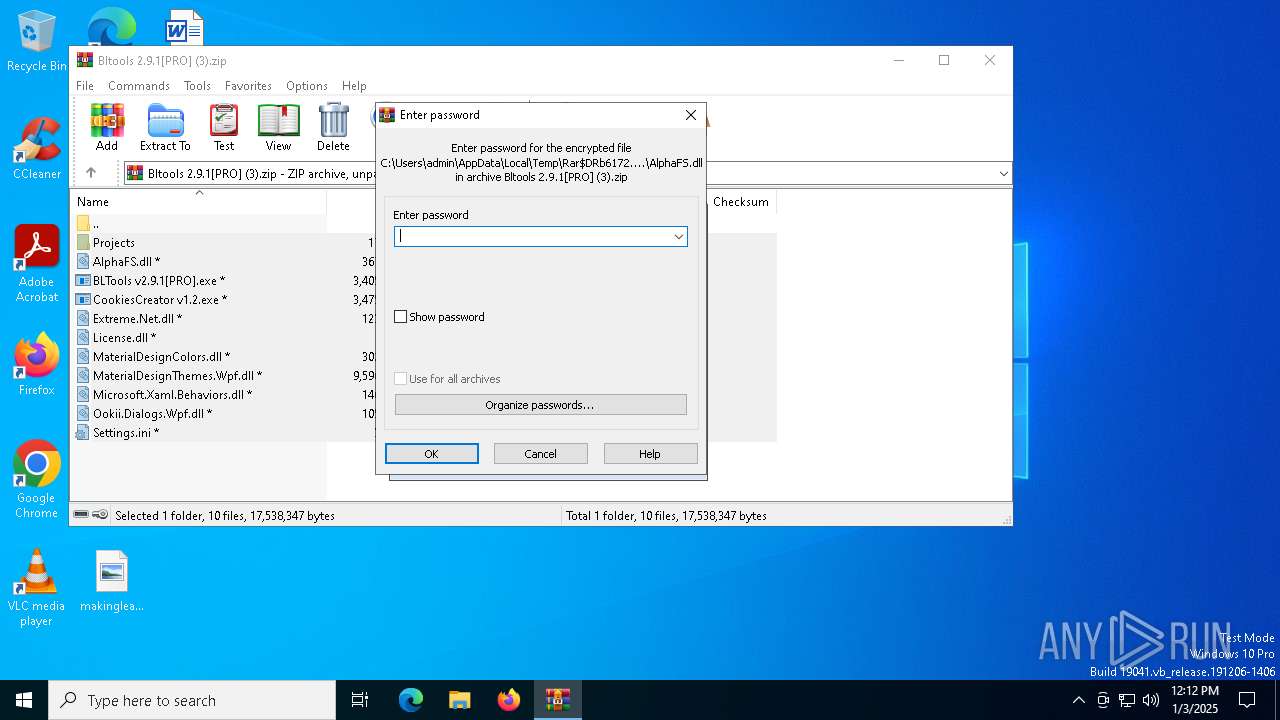
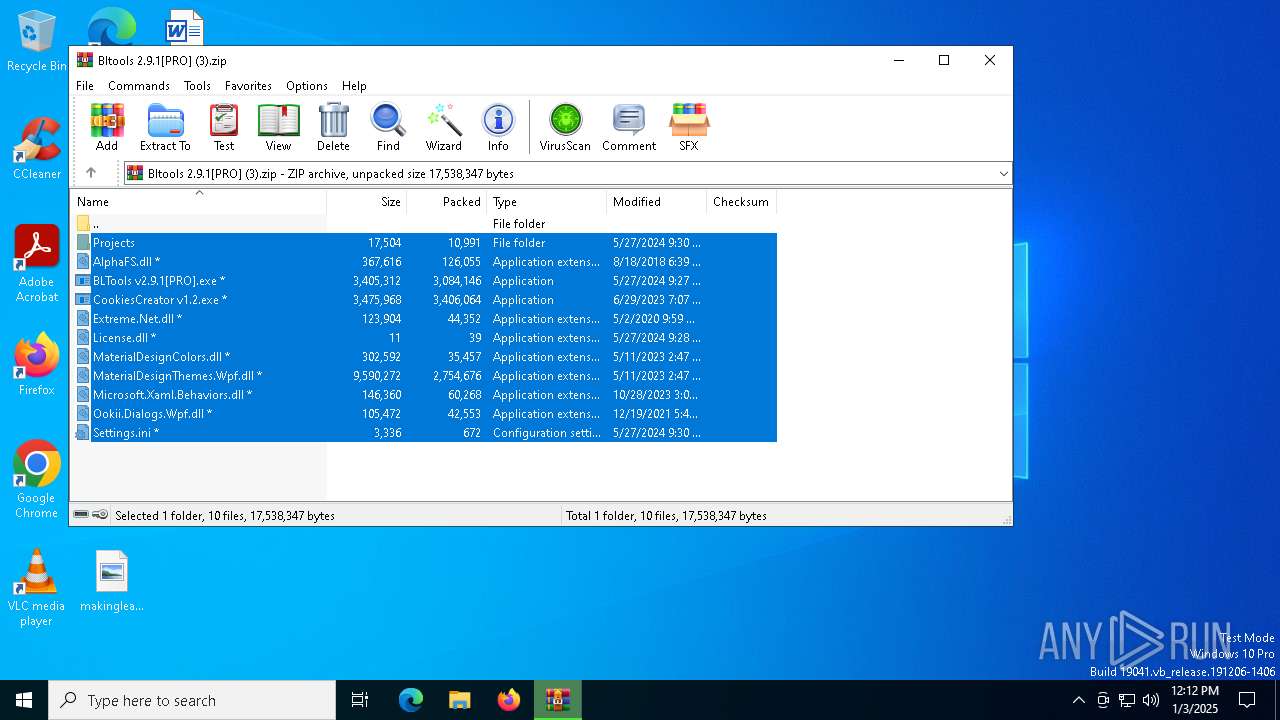
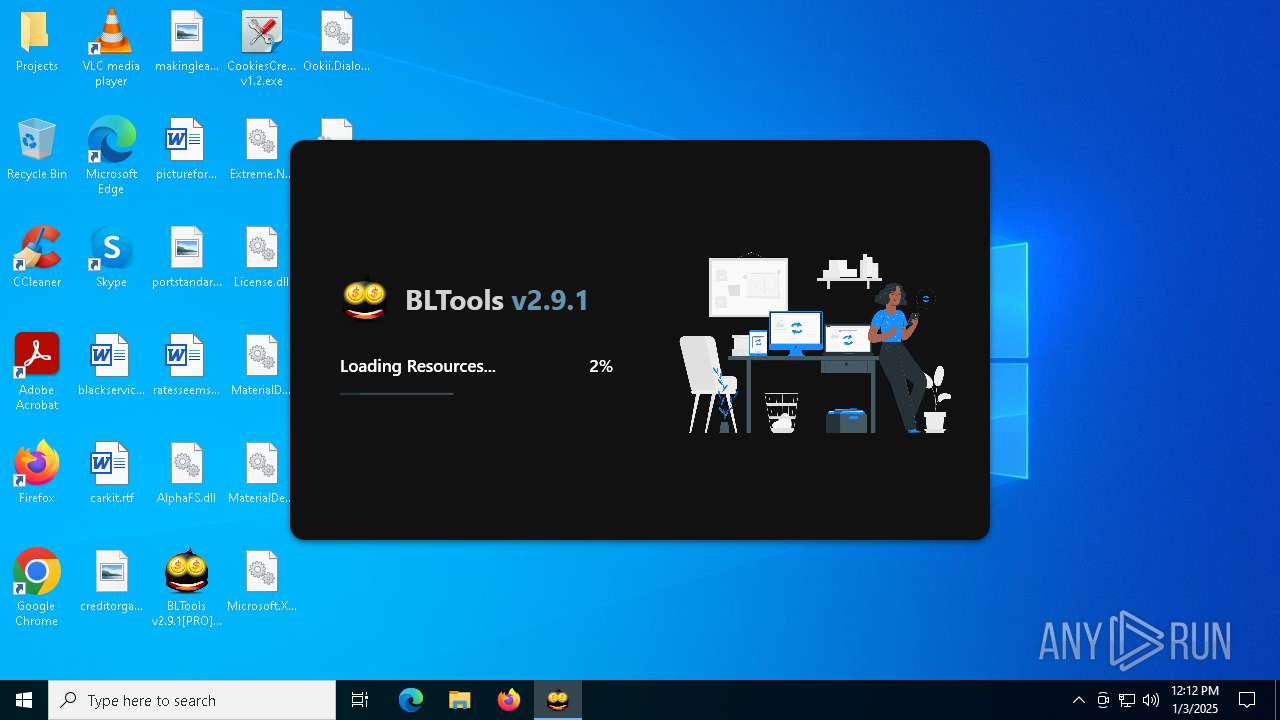
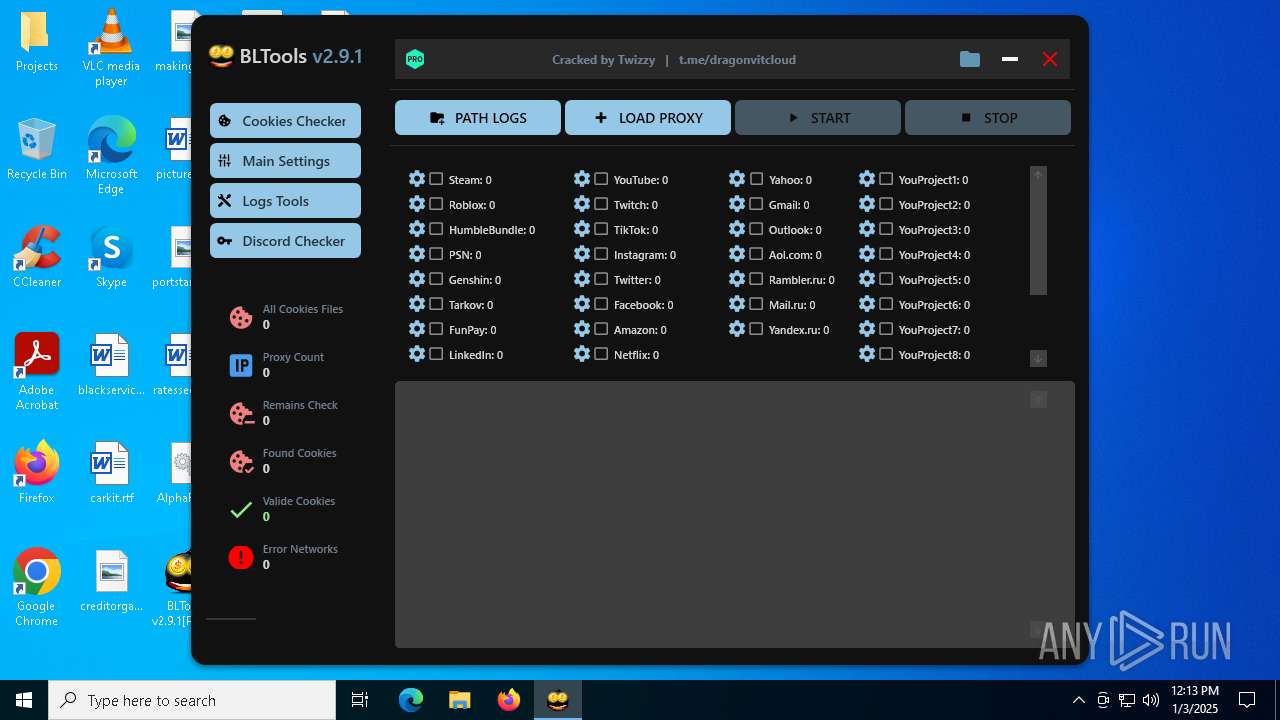
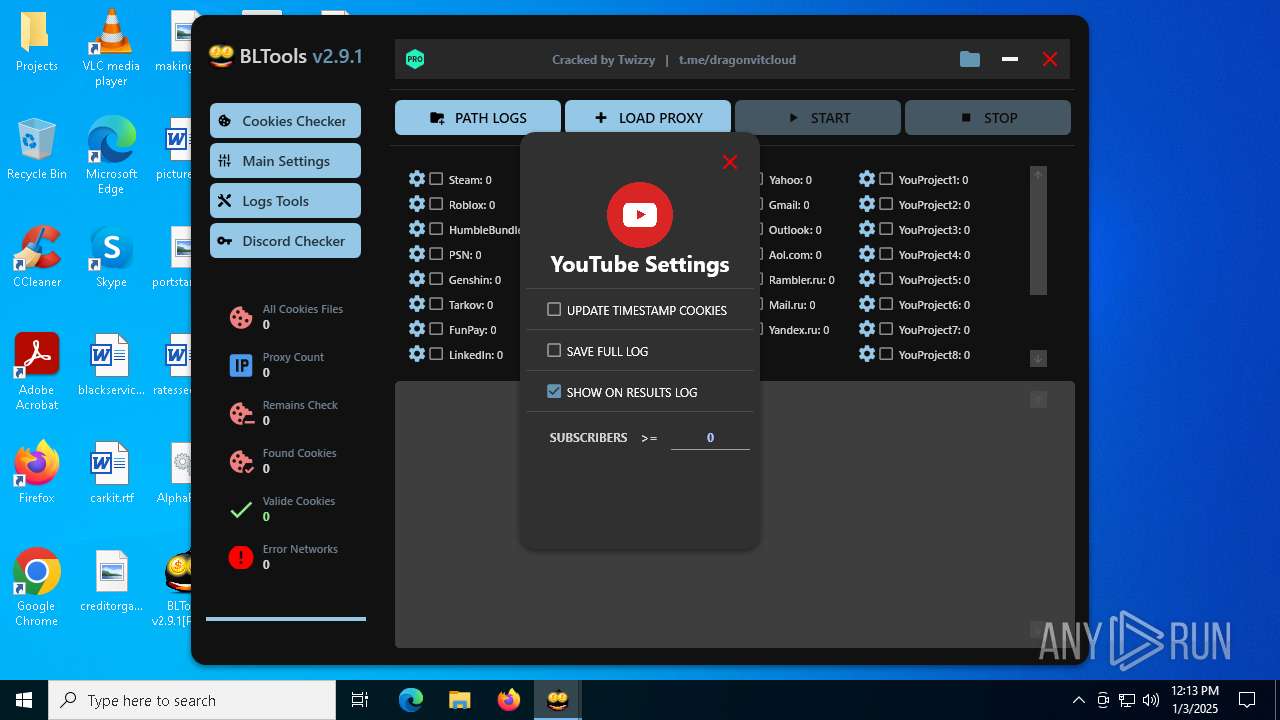
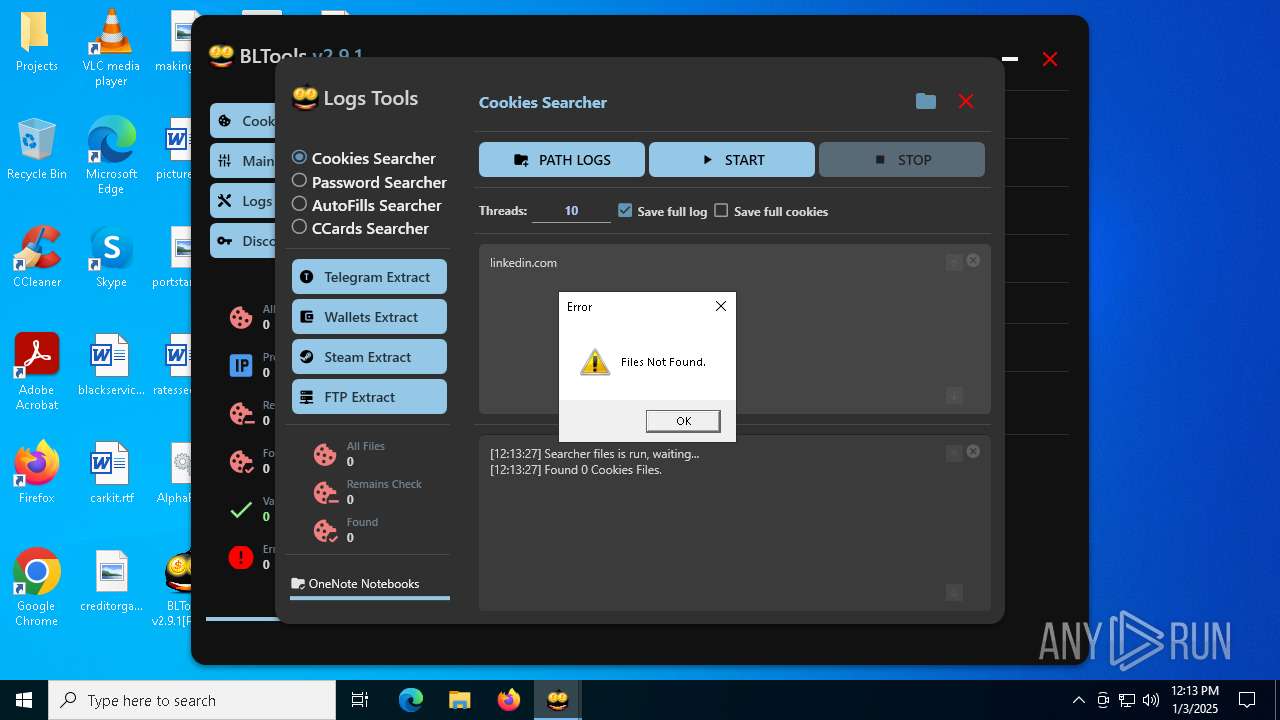
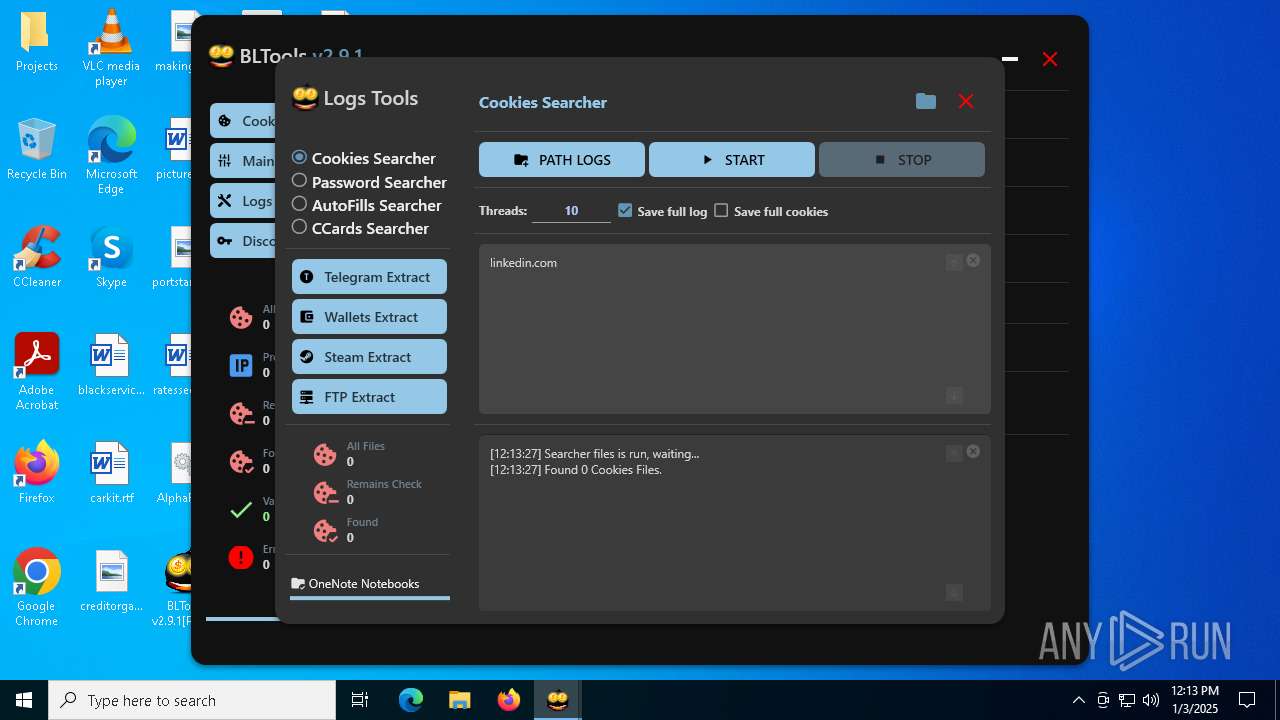
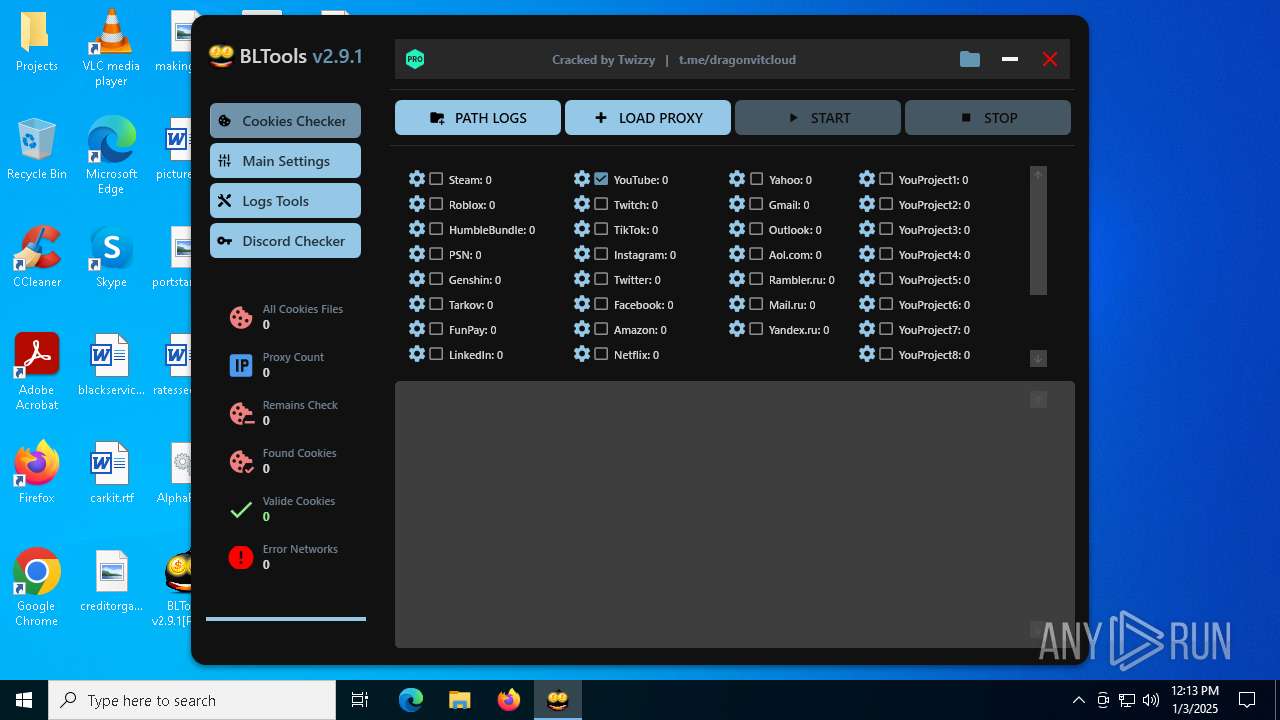
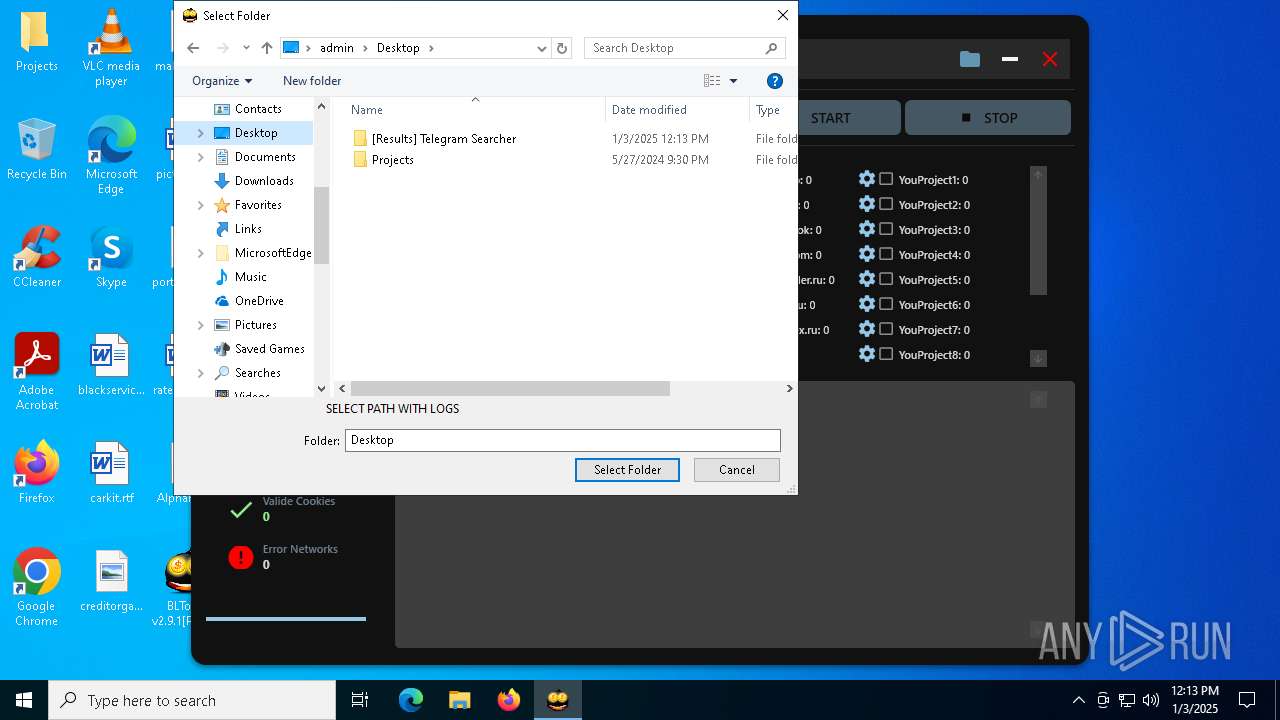
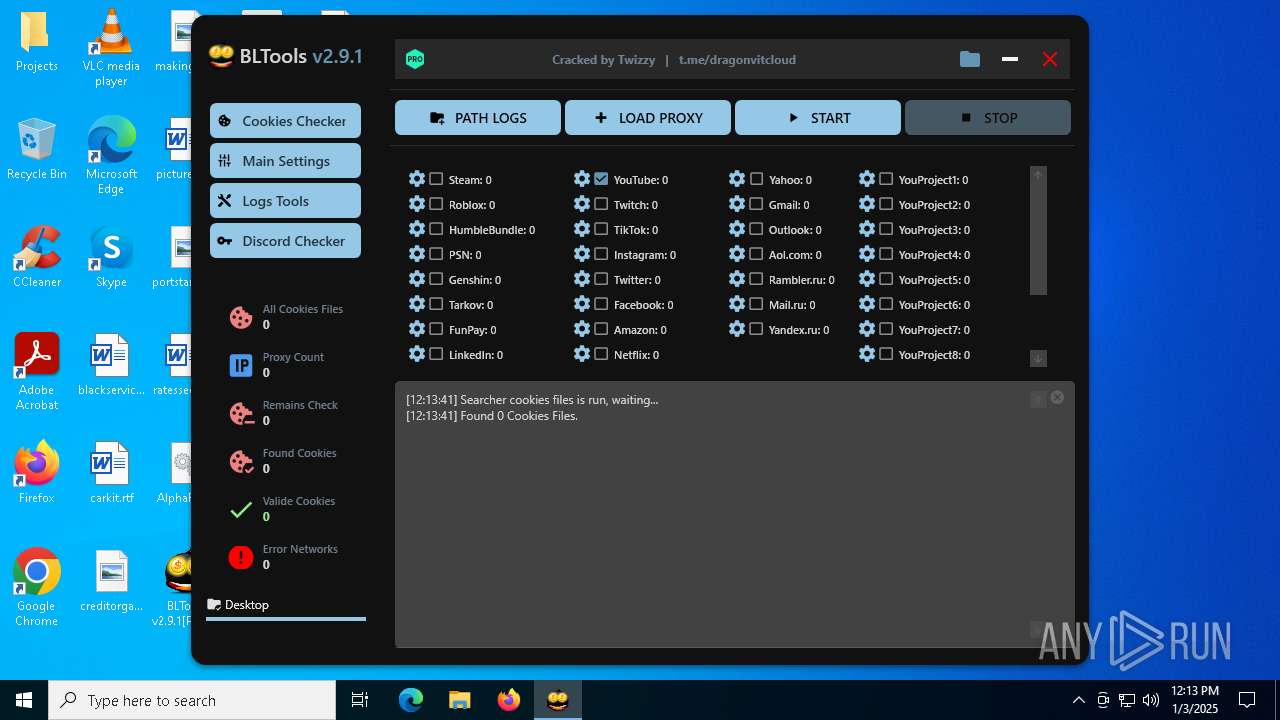
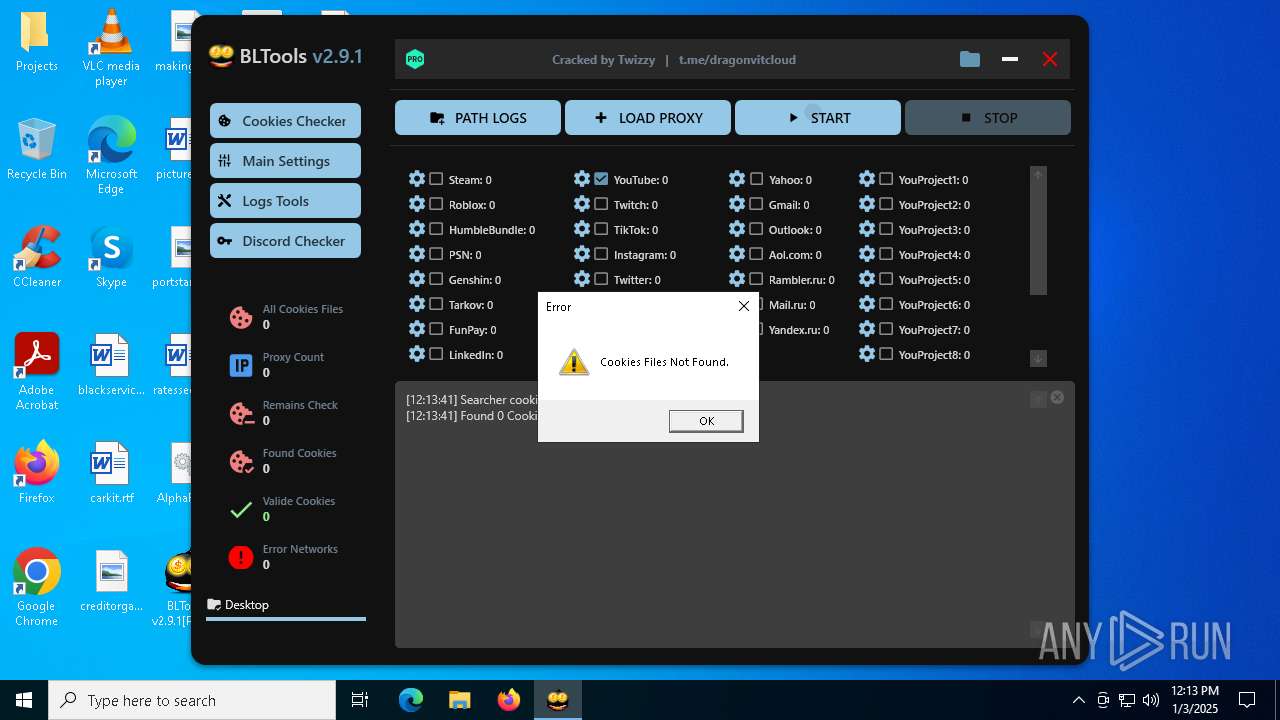
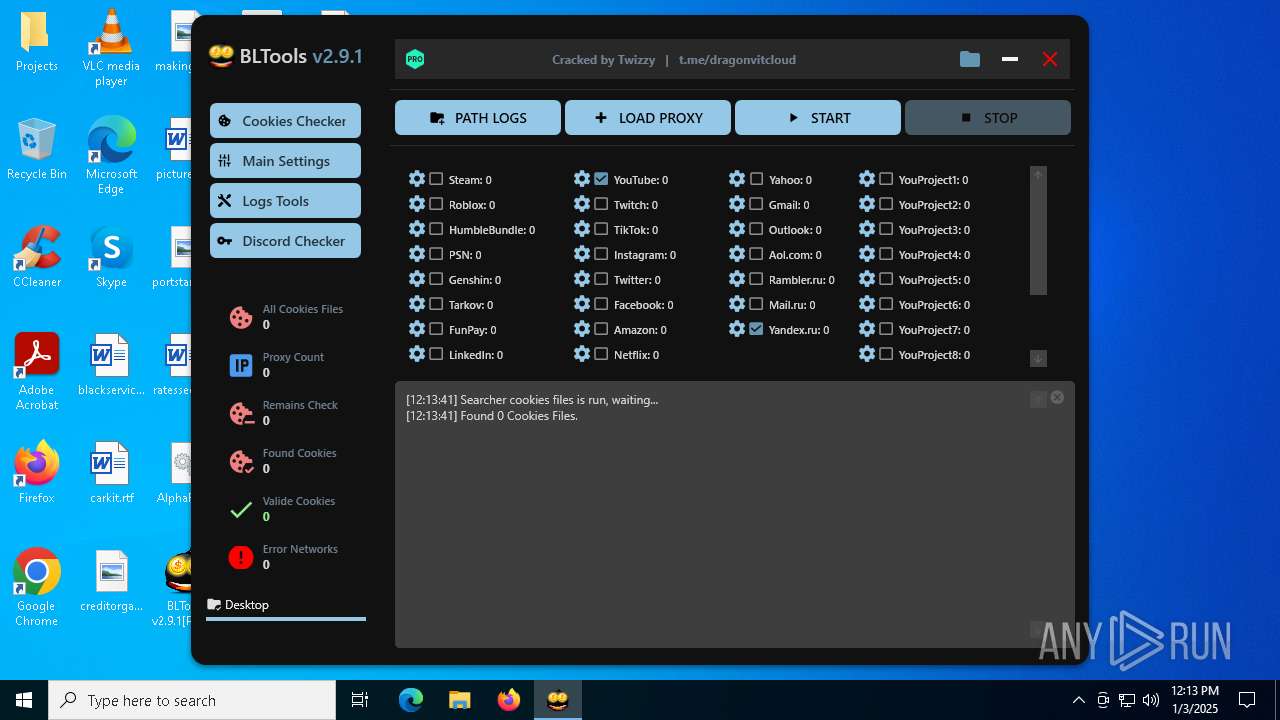
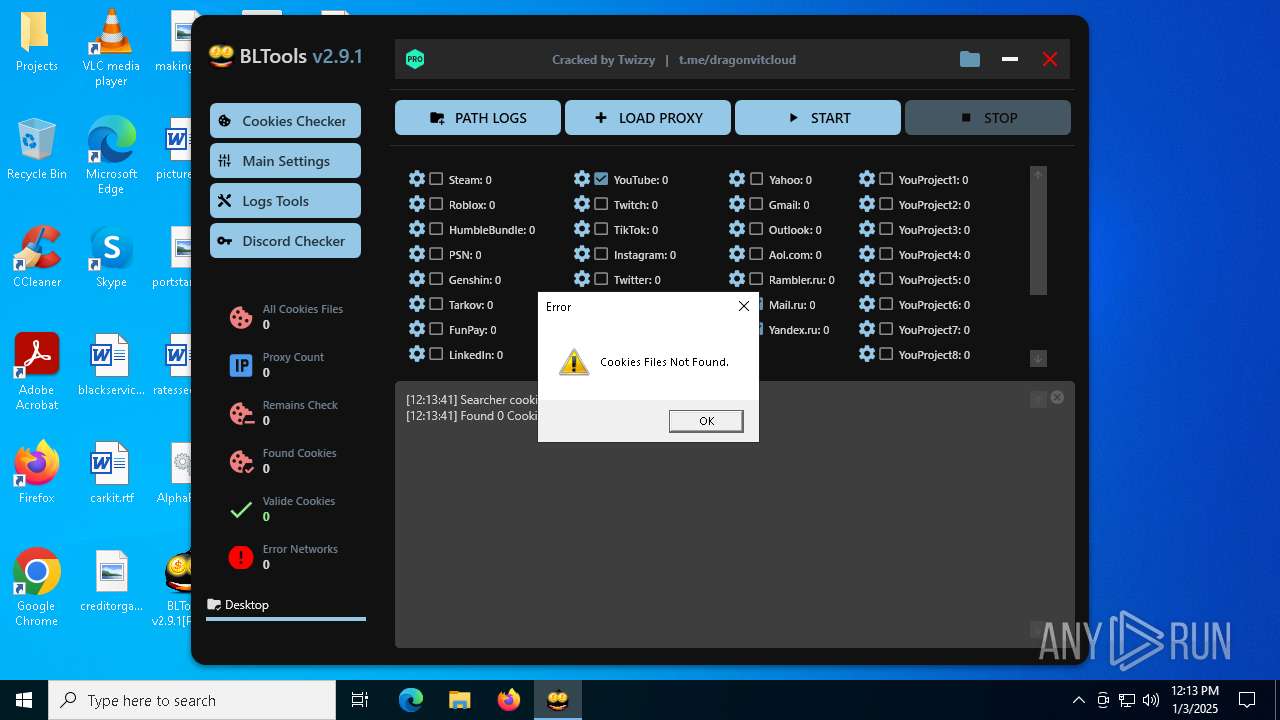
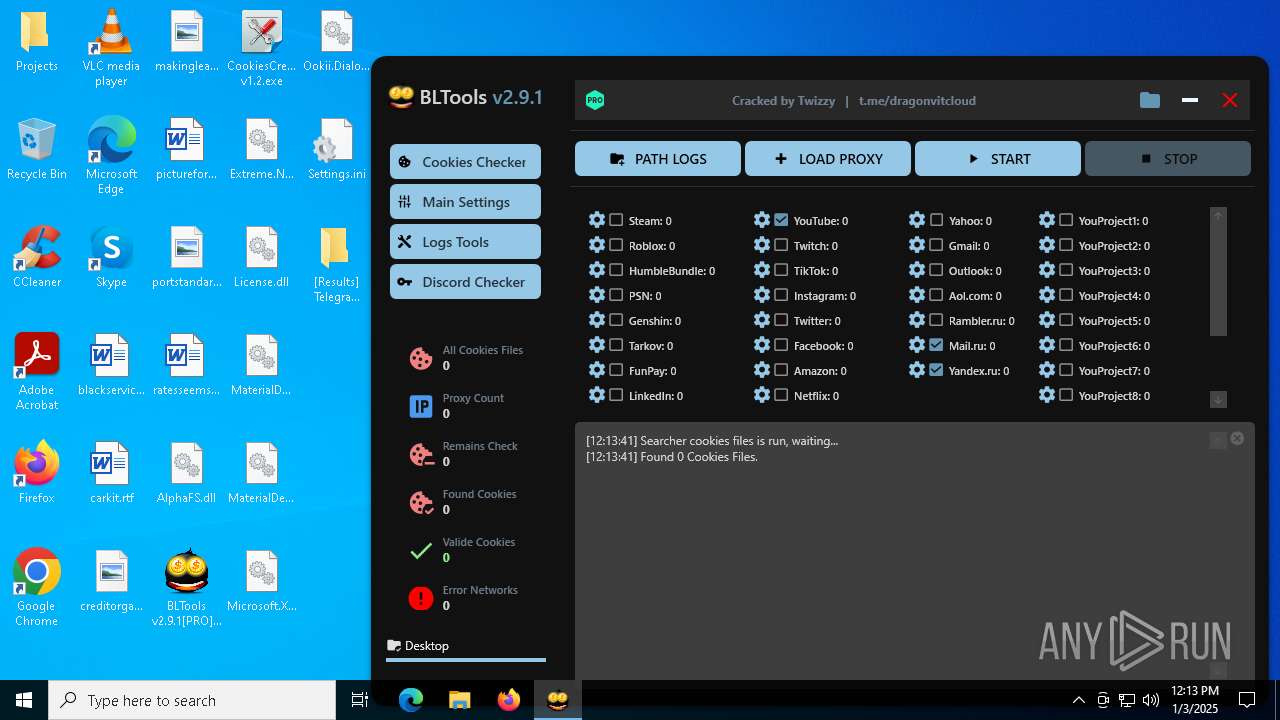
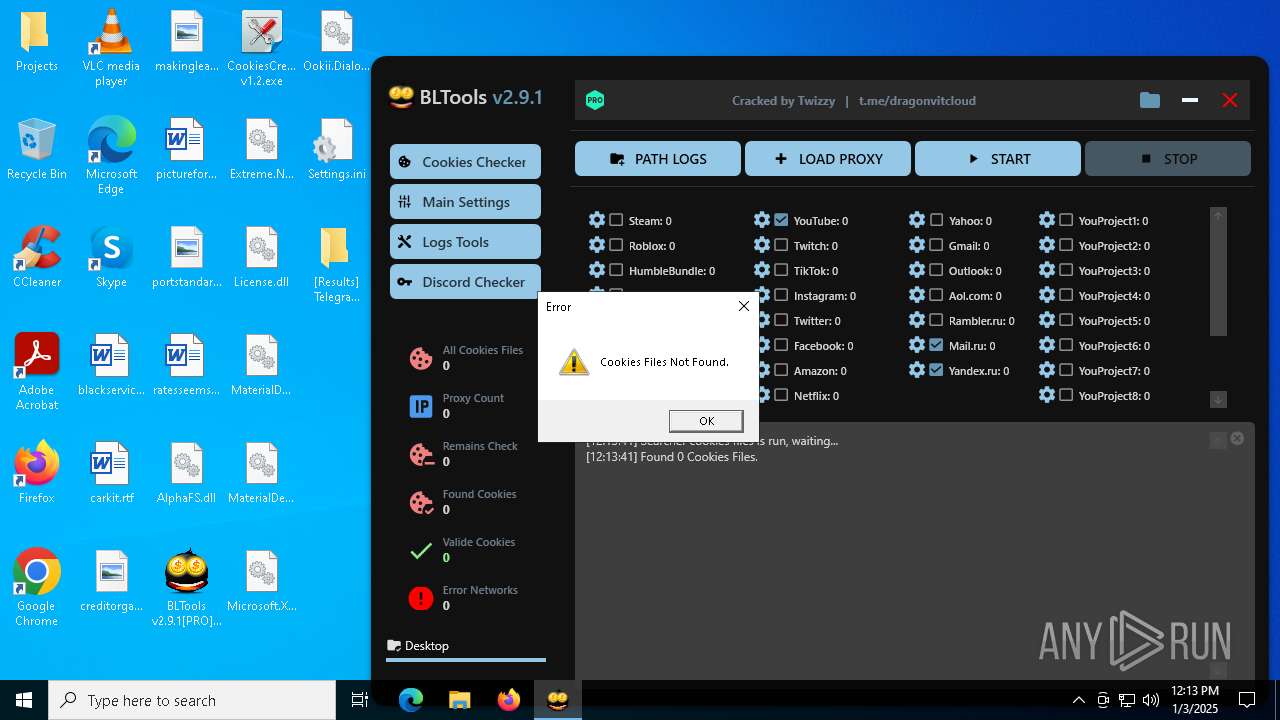
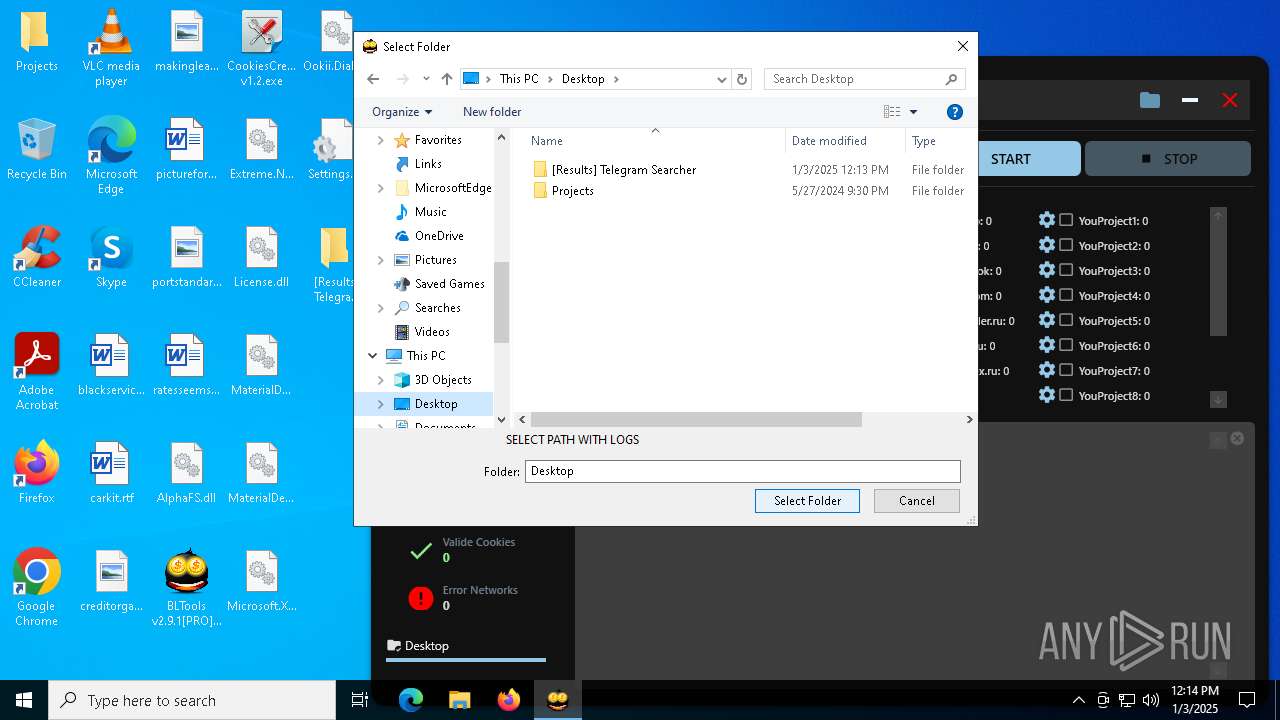
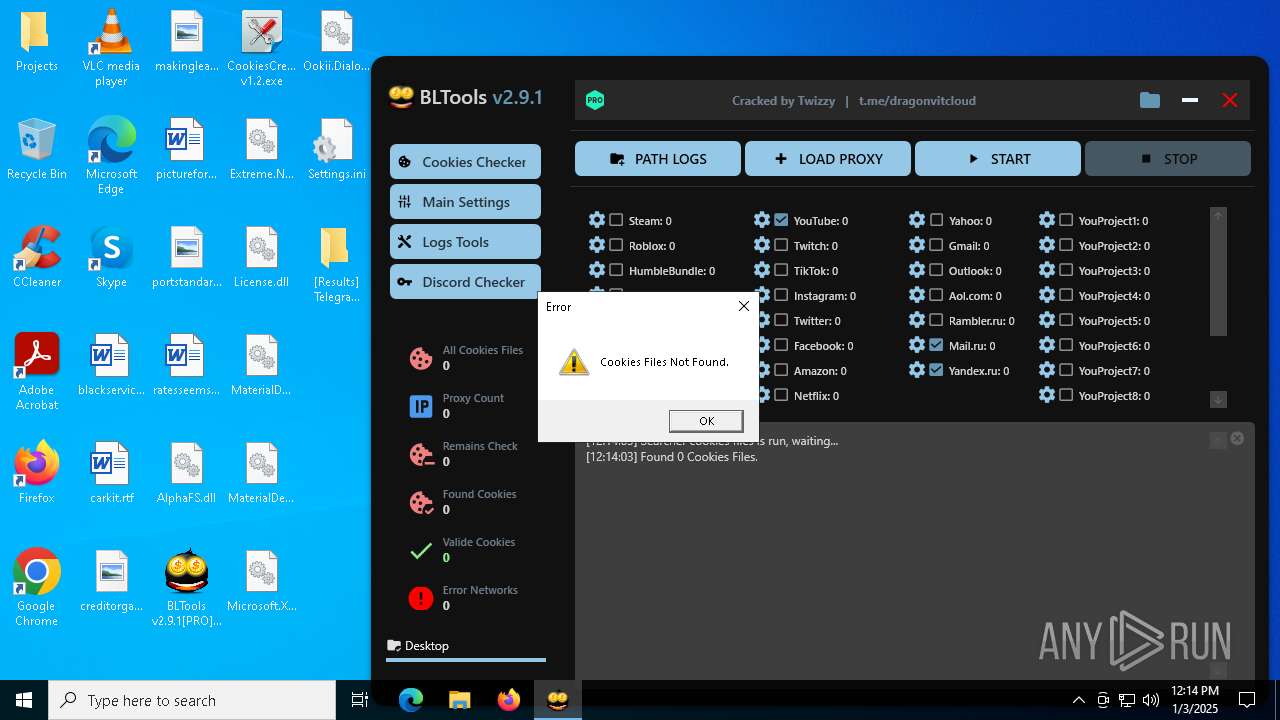
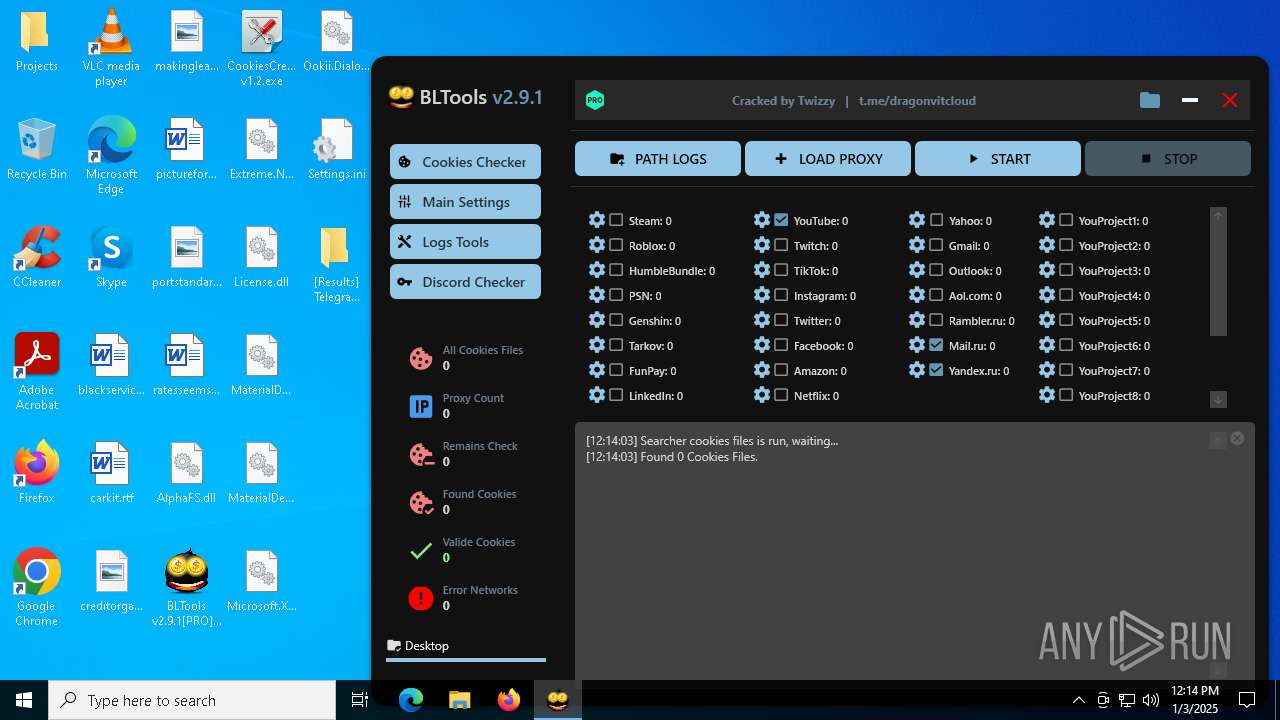
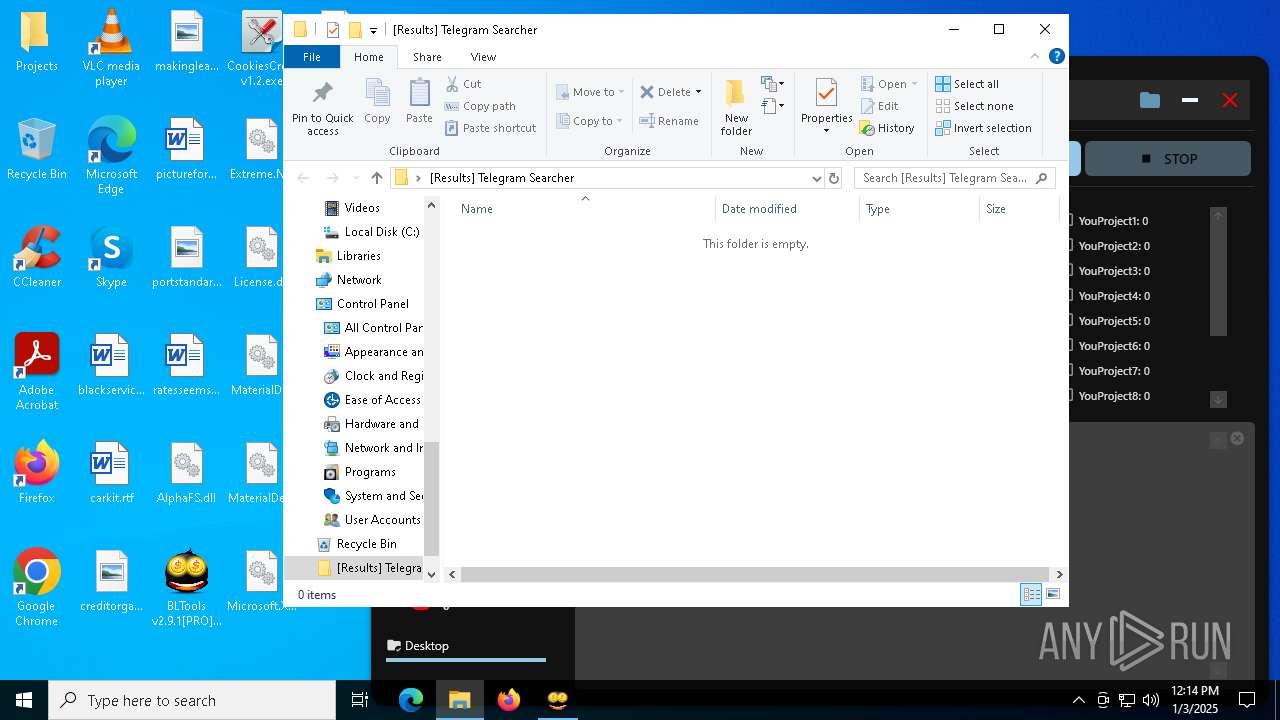
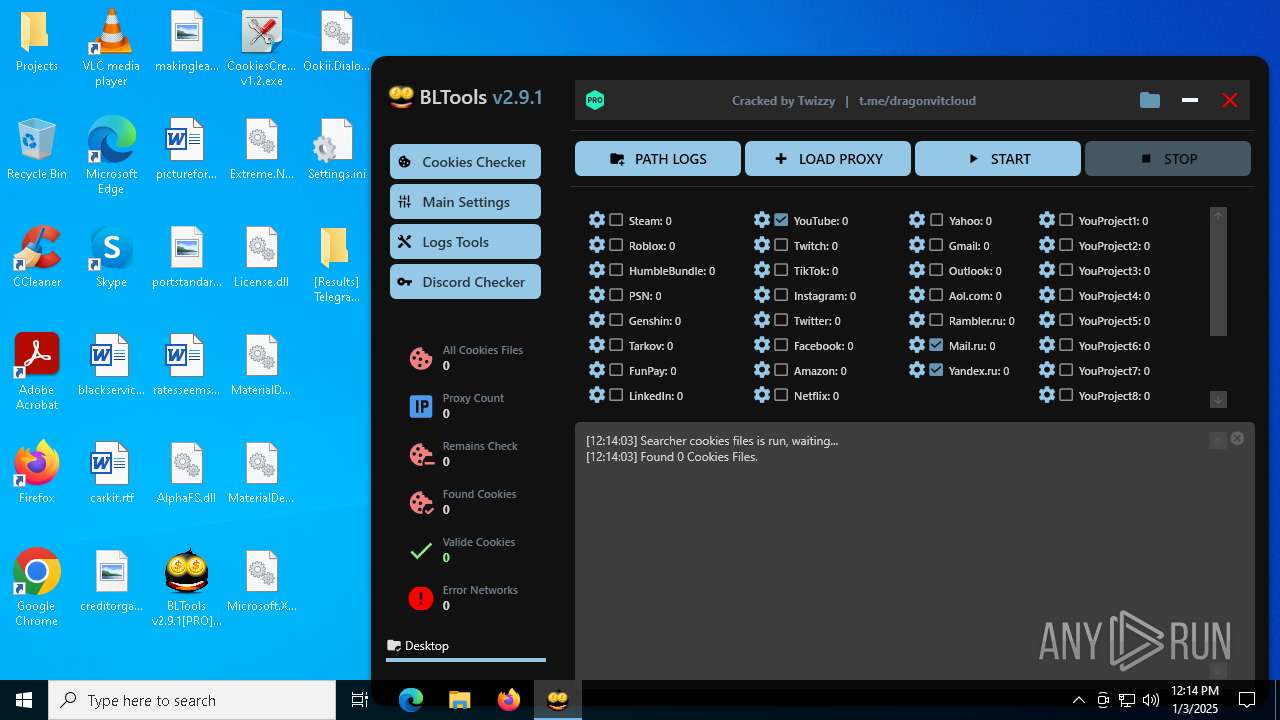
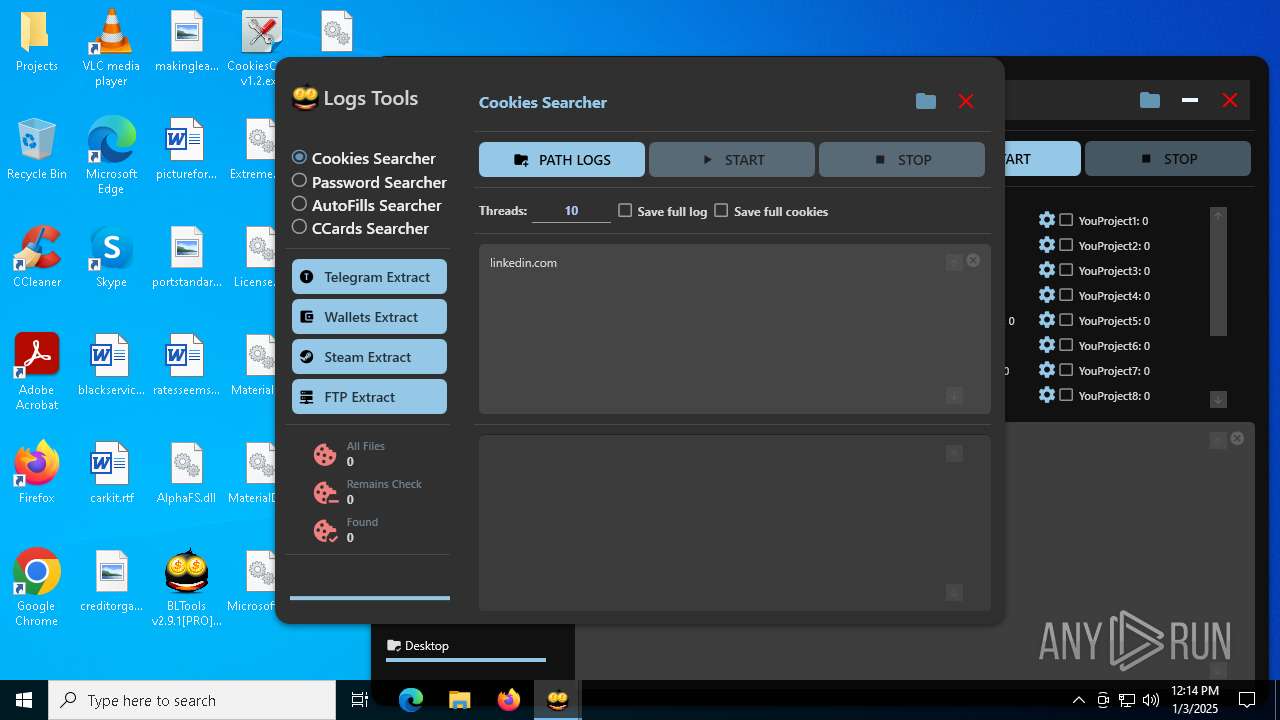
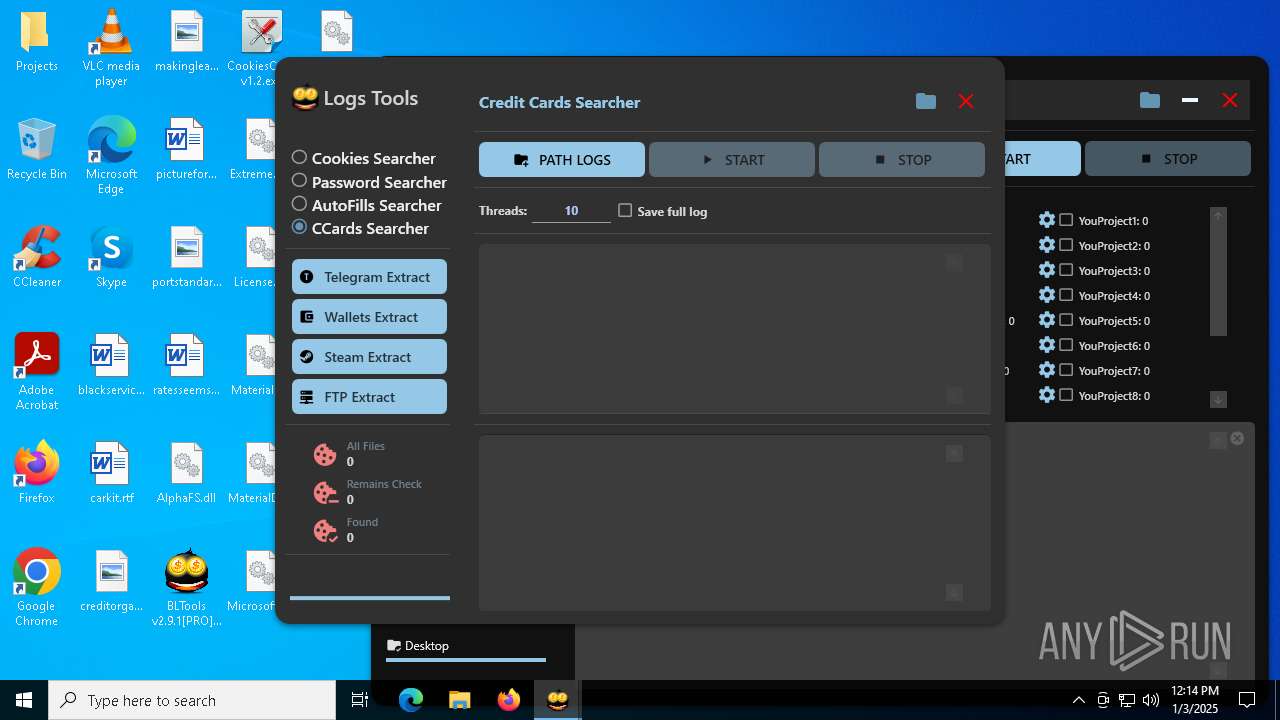
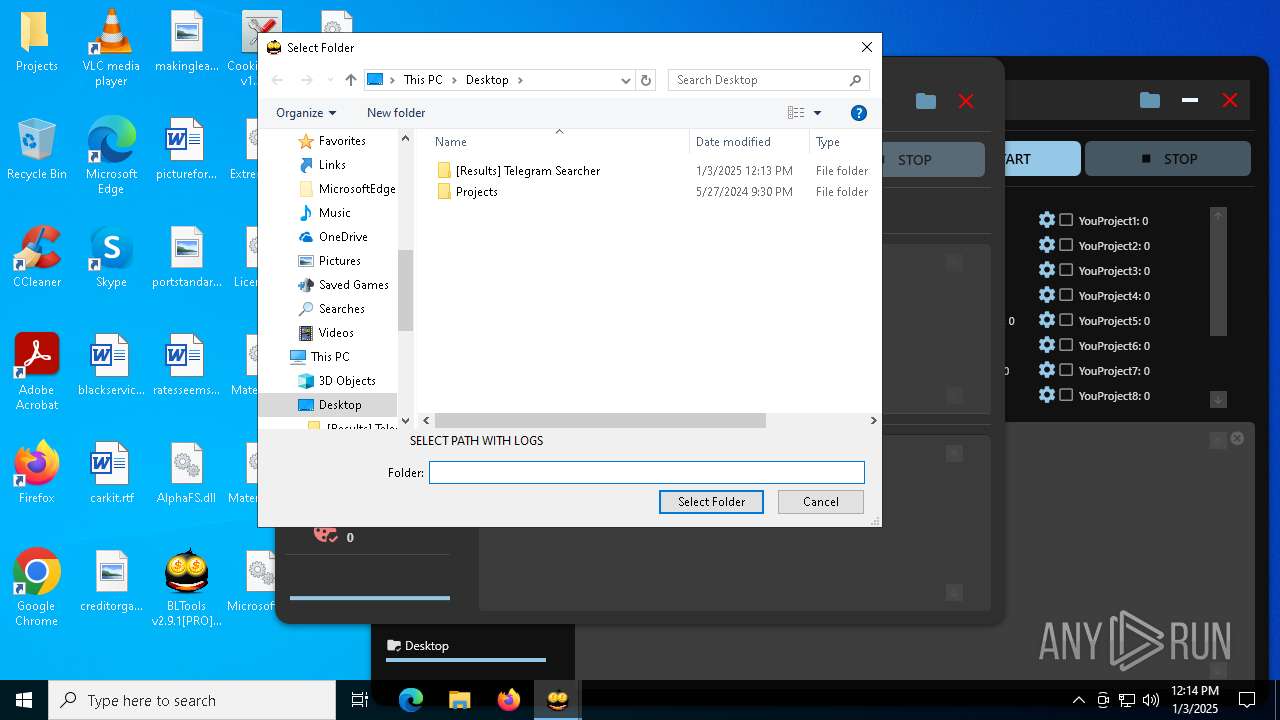
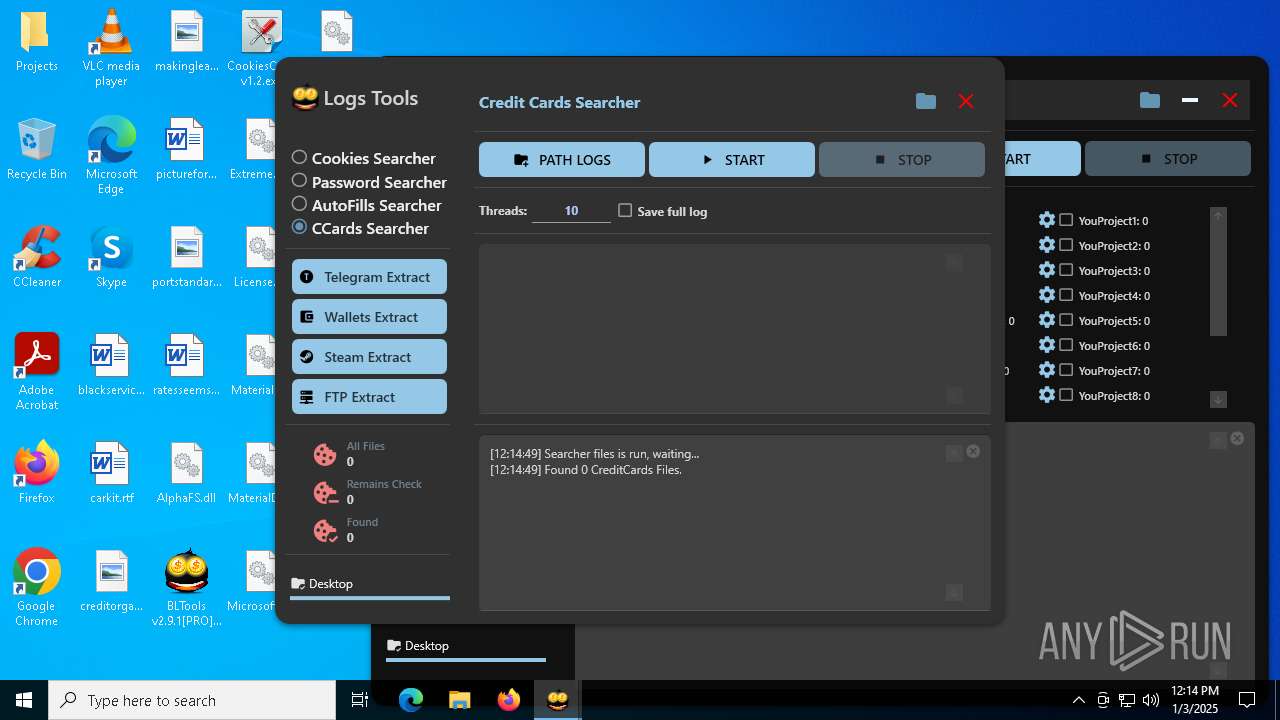
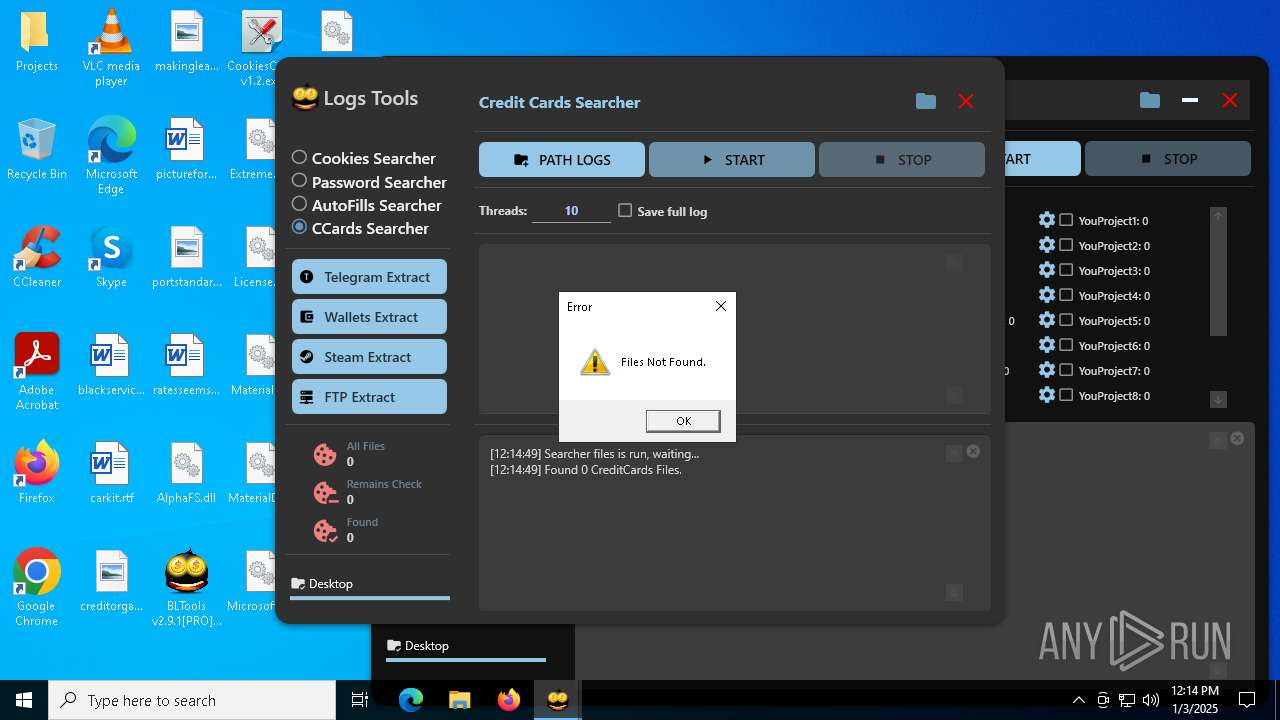
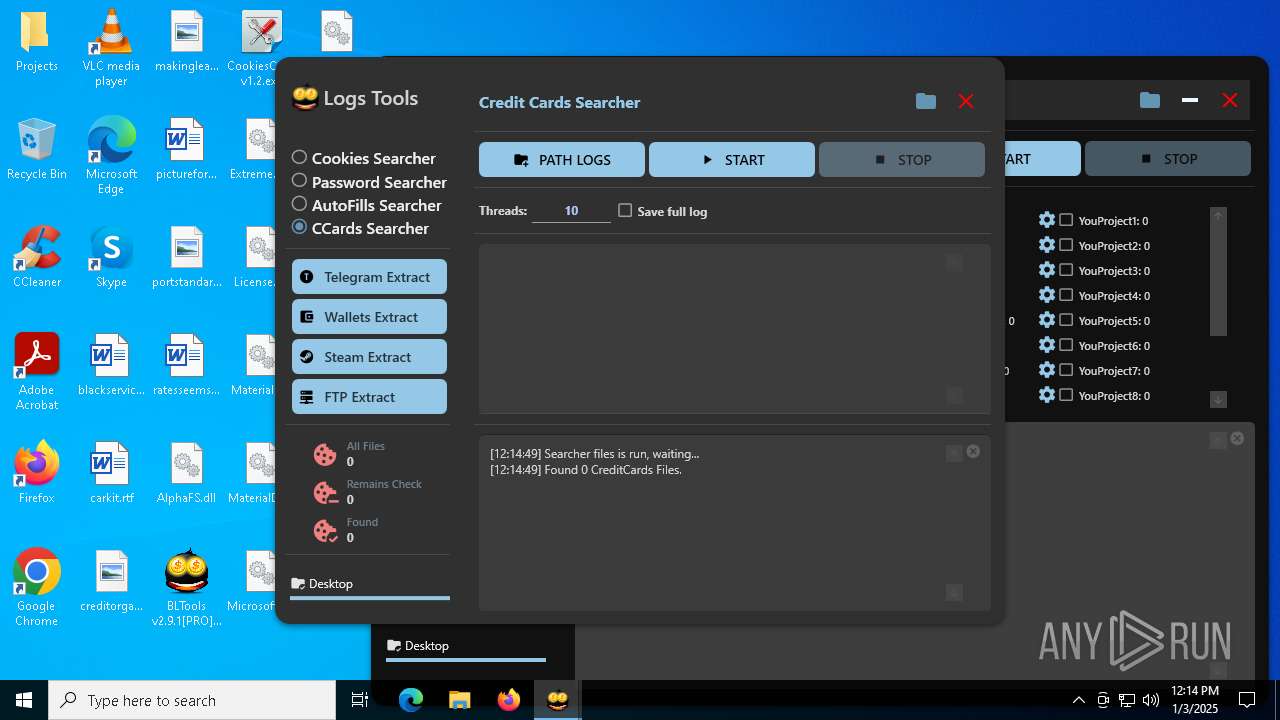
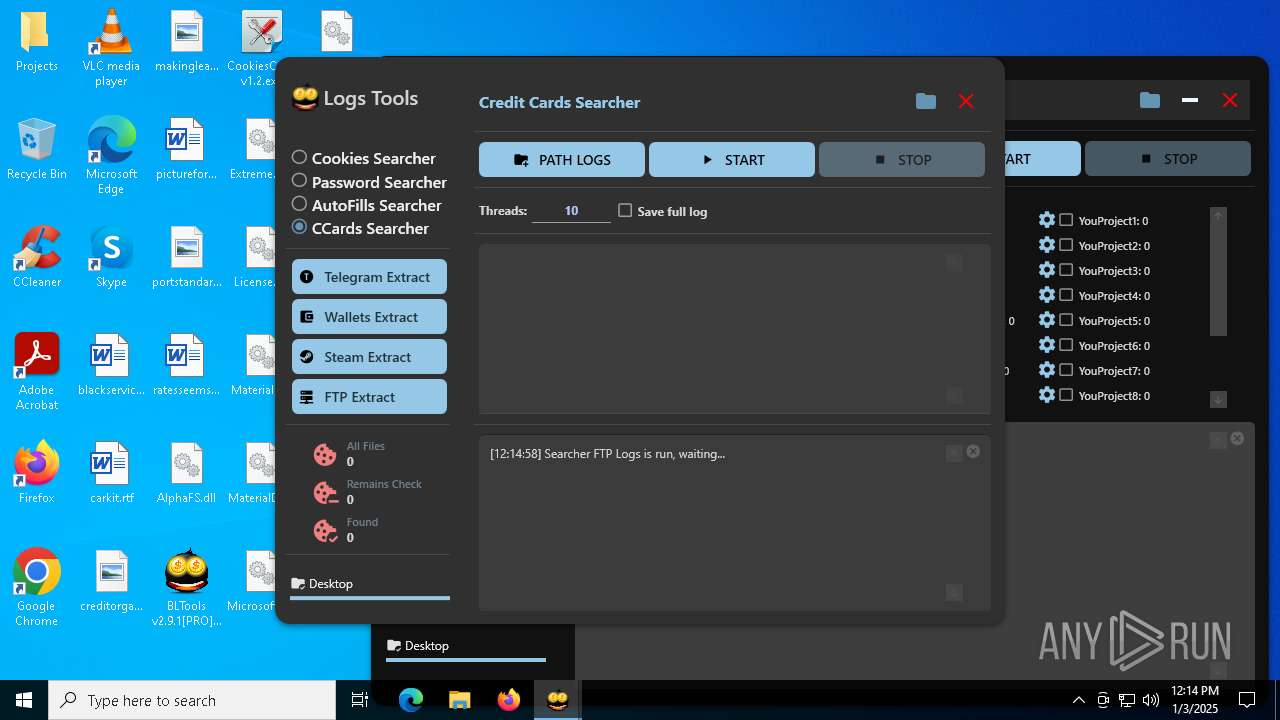
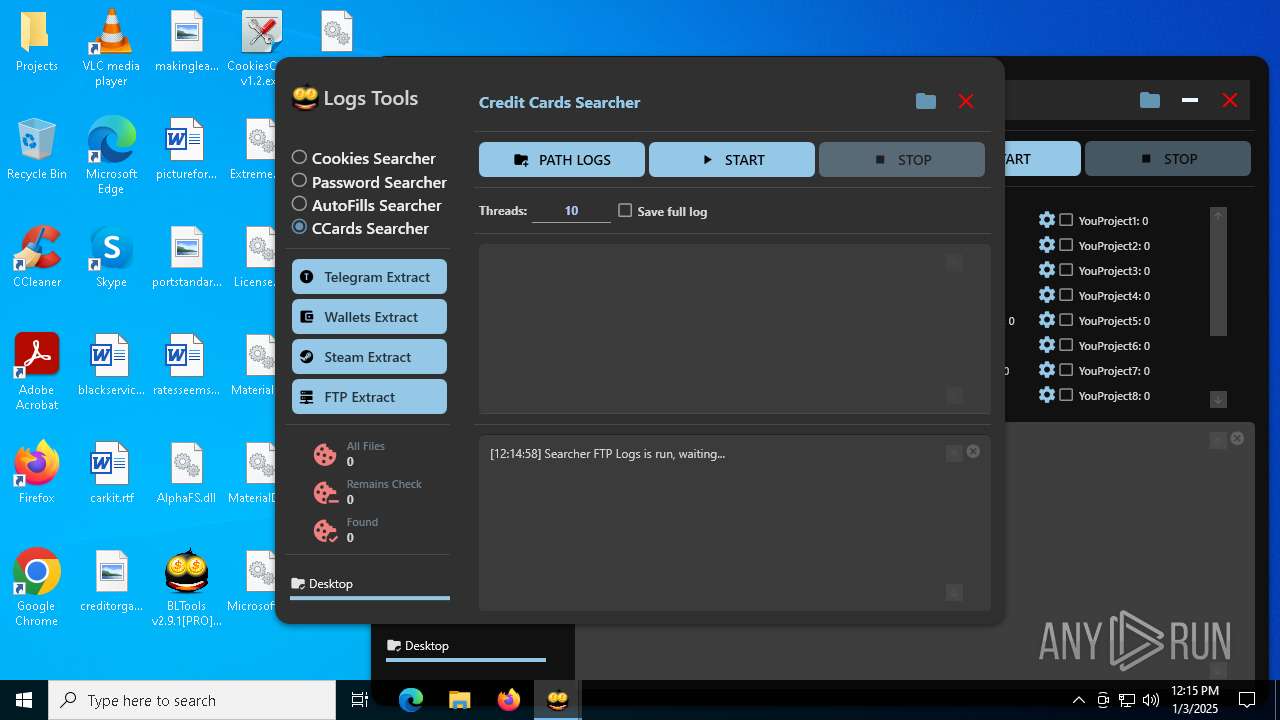
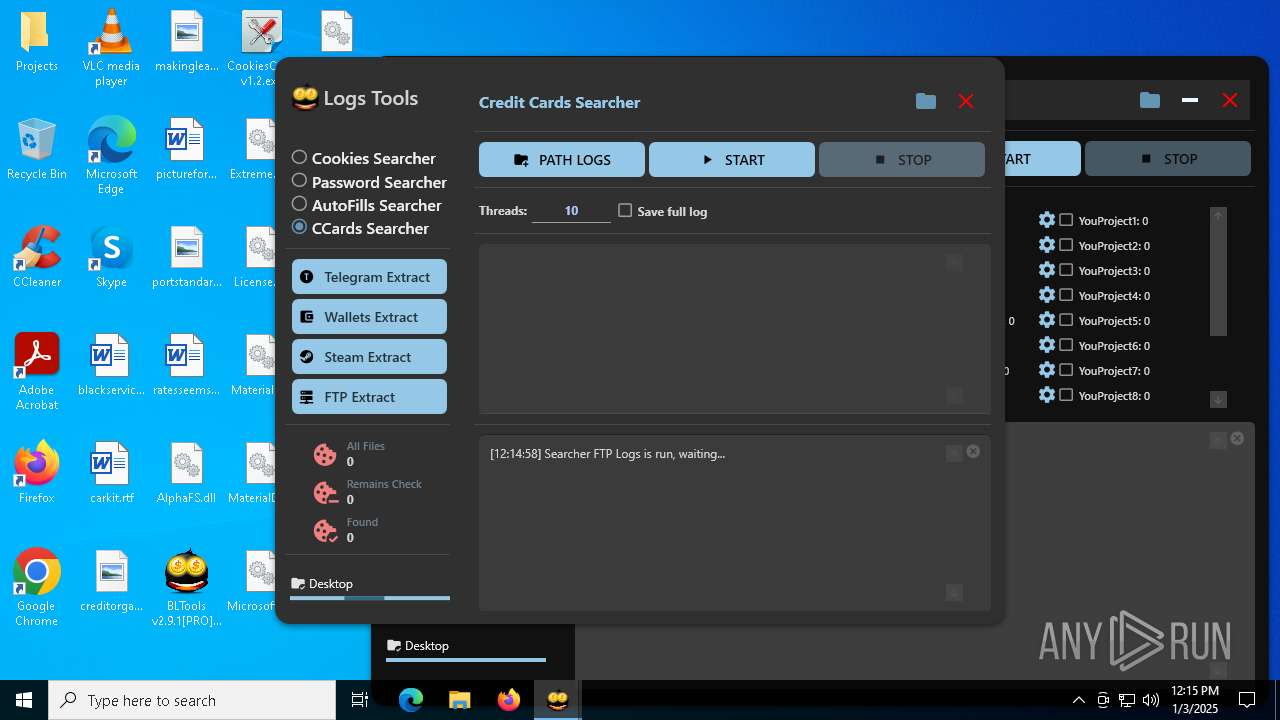
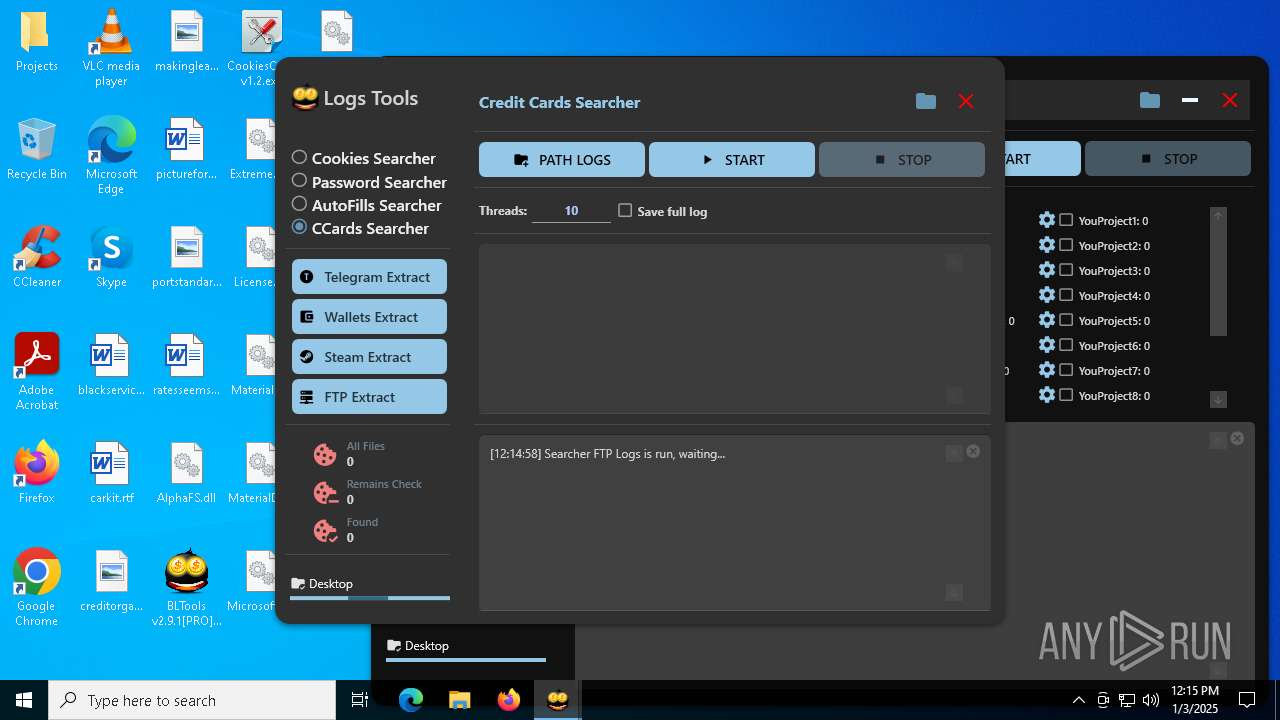
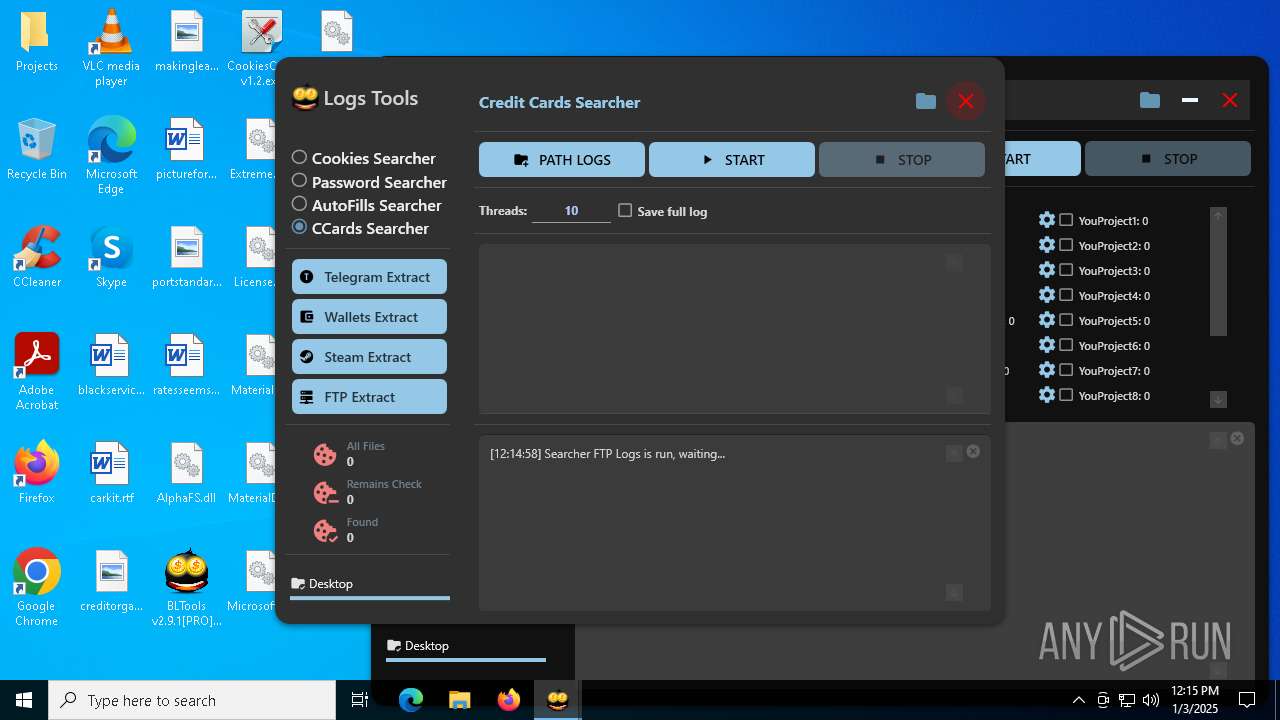
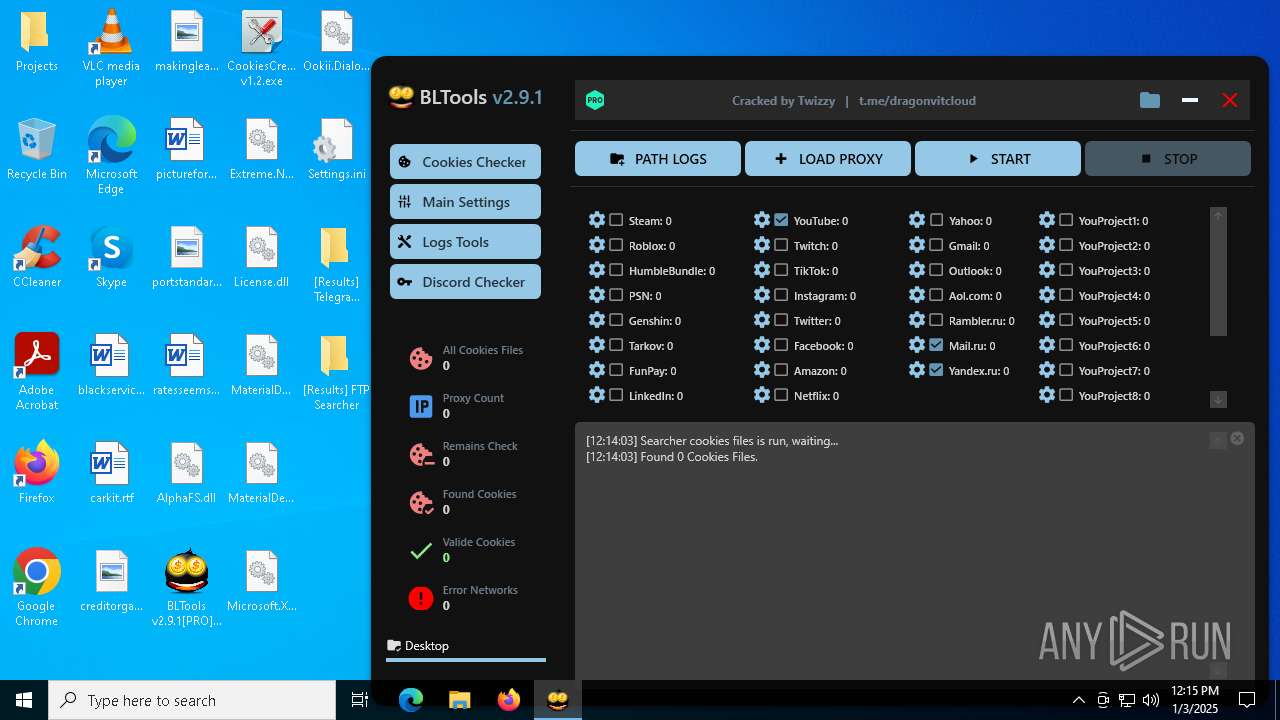
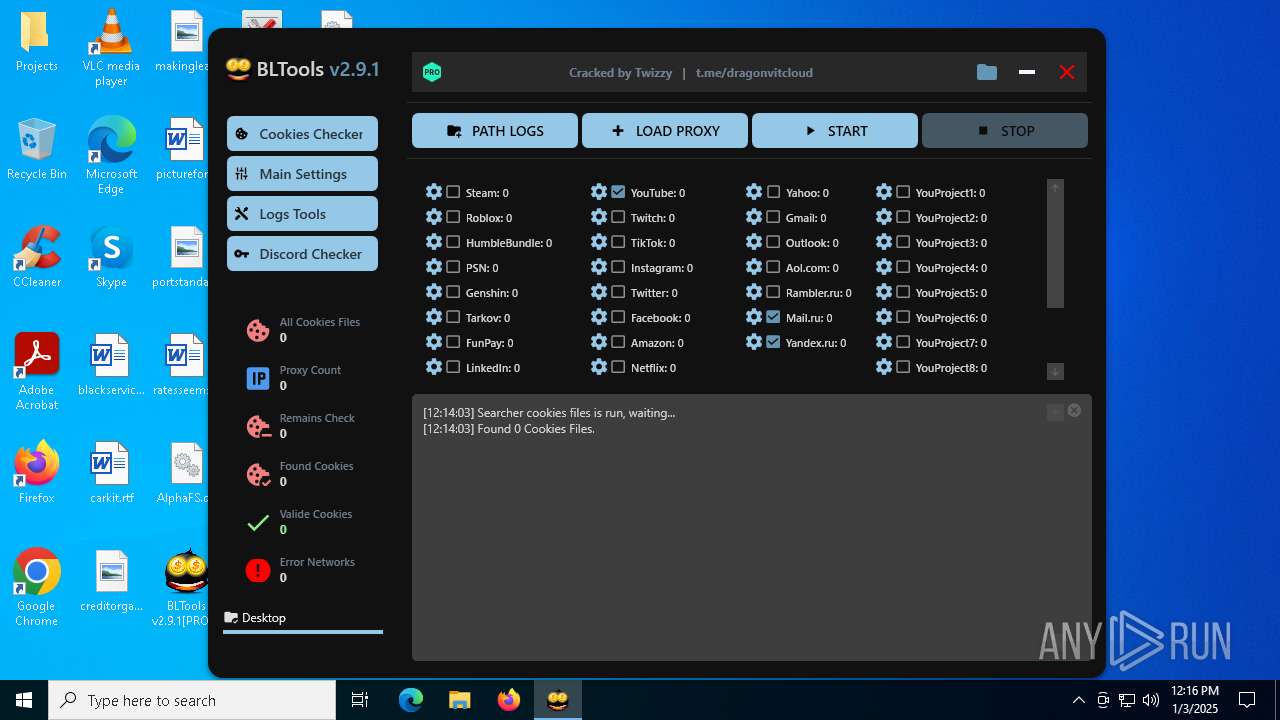
| File name: | Bltools 2.9.1[PRO] (3).zip |
| Full analysis: | https://app.any.run/tasks/7934496d-1313-420e-bde9-c6e6fe9e05a9 |
| Verdict: | Malicious activity |
| Analysis date: | January 03, 2025, 12:12:15 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v5.1 to extract, compression method=AES Encrypted |
| MD5: | 2DDC018733D5C2BECD04ADA9853D8E94 |
| SHA1: | D962F735F647C5EB12217D56D7CB873DE8D692F6 |
| SHA256: | 817731743684500DCAB3CAC6C0FCB3F39FCF8858BE13321079AAA334413DABC8 |
| SSDEEP: | 98304:AhNC4ZsRftiYctD8xmr72Z/8HwBExREZthv4NSmvksnborVnfJu4fiFxa0RslGWH:Ai7aA9RyQthpiKnqXUd |
MALICIOUS
No malicious indicators.SUSPICIOUS
Reads security settings of Internet Explorer
- BLTools v2.9.1[PRO].exe (PID: 2828)
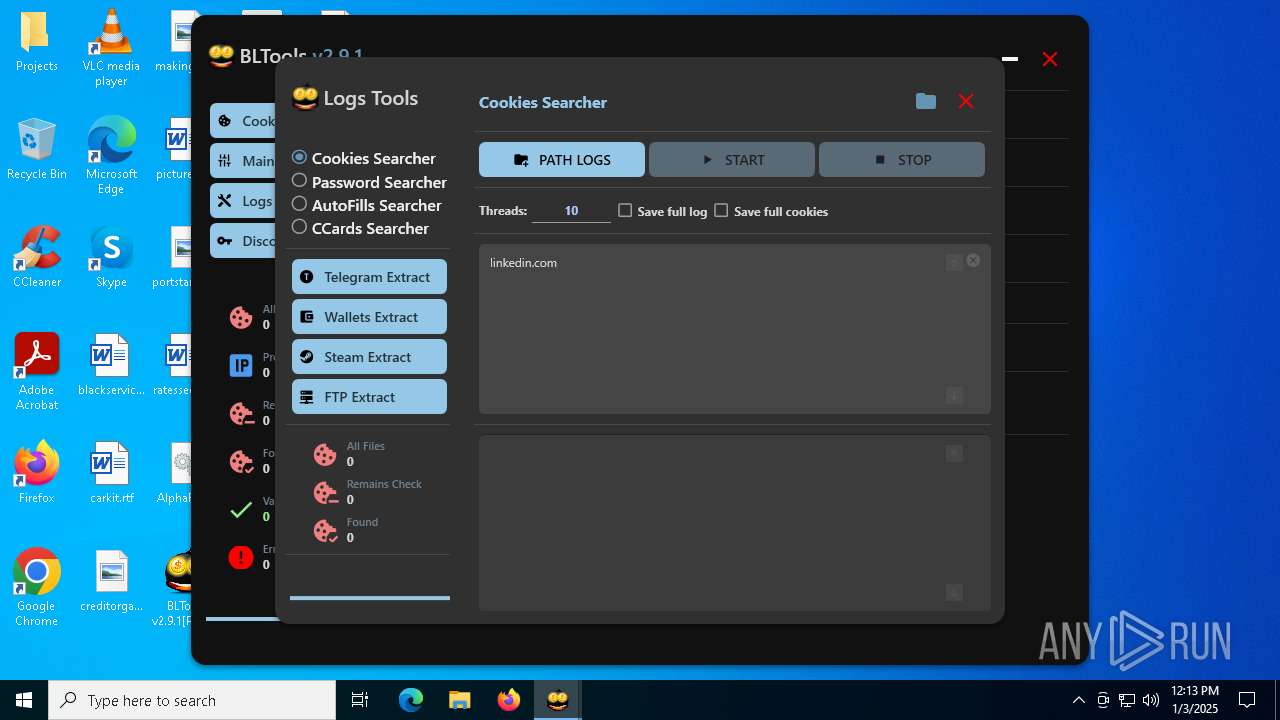
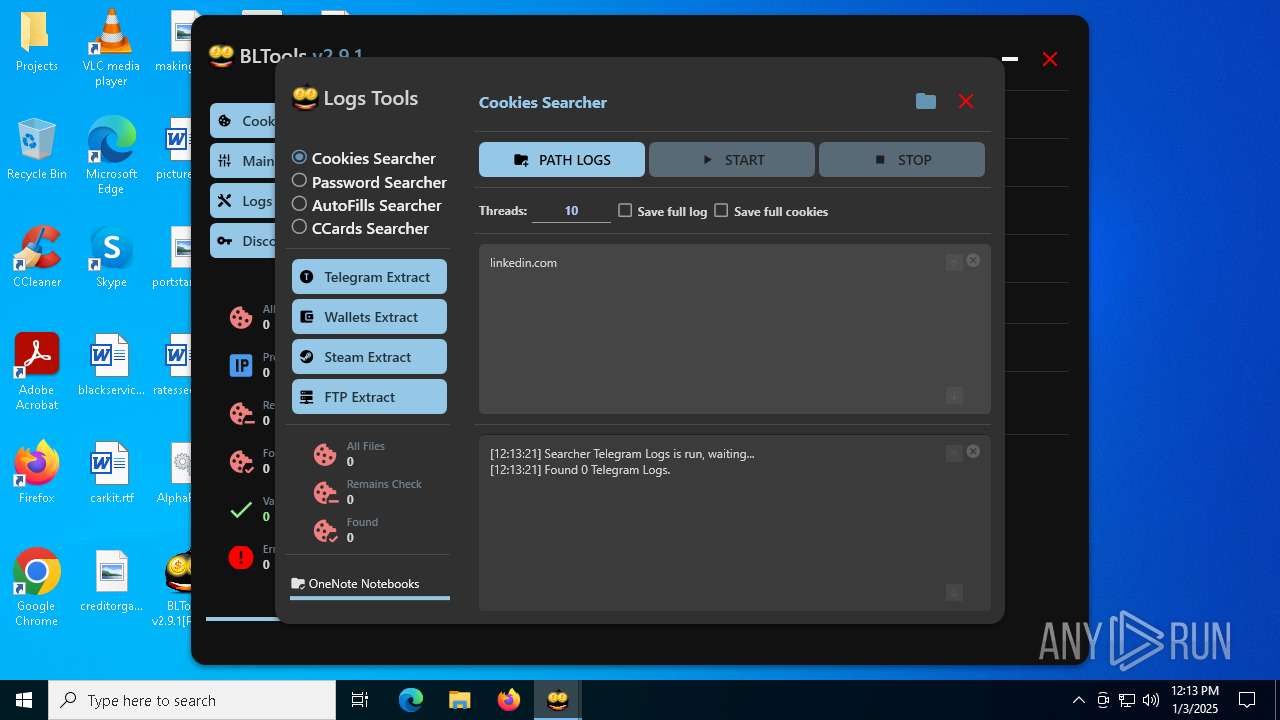
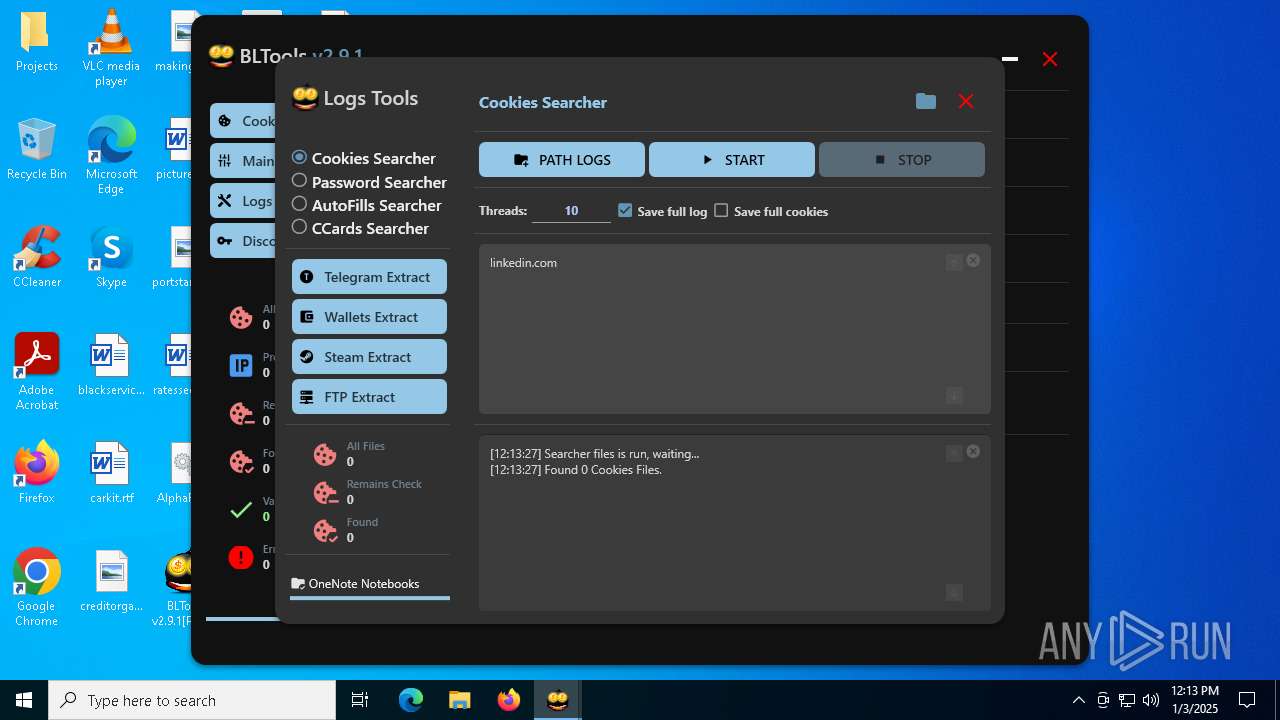
Possible usage of Discord/Telegram API has been detected (YARA)
- BLTools v2.9.1[PRO].exe (PID: 2828)
Write to the desktop.ini file (may be used to cloak folders)
- BLTools v2.9.1[PRO].exe (PID: 2828)
Process drops legitimate windows executable
- BLTools v2.9.1[PRO].exe (PID: 2828)
- WinRAR.exe (PID: 6172)
Executable content was dropped or overwritten
- BLTools v2.9.1[PRO].exe (PID: 2828)
INFO
Executable content was dropped or overwritten
- WinRAR.exe (PID: 6172)
The process uses the downloaded file
- WinRAR.exe (PID: 6172)
Reads the machine GUID from the registry
- BLTools v2.9.1[PRO].exe (PID: 2828)
Checks supported languages
- BLTools v2.9.1[PRO].exe (PID: 2828)
Manual execution by a user
- BLTools v2.9.1[PRO].exe (PID: 2828)
Reads the computer name
- BLTools v2.9.1[PRO].exe (PID: 2828)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
ims-api
(PID) Process(2828) BLTools v2.9.1[PRO].exe
Telegram-Tokens (1)6448011148:AAHcTB8GjoKK5nZce44buWa2oZ3D7kqBVPk
Telegram-Info-Links
6448011148:AAHcTB8GjoKK5nZce44buWa2oZ3D7kqBVPk
Get info about bothttps://api.telegram.org/bot6448011148:AAHcTB8GjoKK5nZce44buWa2oZ3D7kqBVPk/getMe
Get incoming updateshttps://api.telegram.org/bot6448011148:AAHcTB8GjoKK5nZce44buWa2oZ3D7kqBVPk/getUpdates
Get webhookhttps://api.telegram.org/bot6448011148:AAHcTB8GjoKK5nZce44buWa2oZ3D7kqBVPk/getWebhookInfo
Delete webhookhttps://api.telegram.org/bot6448011148:AAHcTB8GjoKK5nZce44buWa2oZ3D7kqBVPk/deleteWebhook
Drop incoming updateshttps://api.telegram.org/bot6448011148:AAHcTB8GjoKK5nZce44buWa2oZ3D7kqBVPk/deleteWebhook?drop_pending_updates=true
Telegram-Requests
Token6448011148:AAHcTB8GjoKK5nZce44buWa2oZ3D7kqBVPk
End-PointsendMessage
Args
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 51 |
|---|---|
| ZipBitFlag: | 0x0001 |
| ZipCompression: | Unknown (99) |
| ZipModifyDate: | 2018:08:18 21:39:52 |
| ZipCRC: | 0x00000000 |
| ZipCompressedSize: | 126055 |
| ZipUncompressedSize: | 367616 |
| ZipFileName: | AlphaFS.dll |
Total processes
128
Monitored processes
3
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 2828 | "C:\Users\admin\Desktop\BLTools v2.9.1[PRO].exe" | C:\Users\admin\Desktop\BLTools v2.9.1[PRO].exe | explorer.exe | ||||||||||||
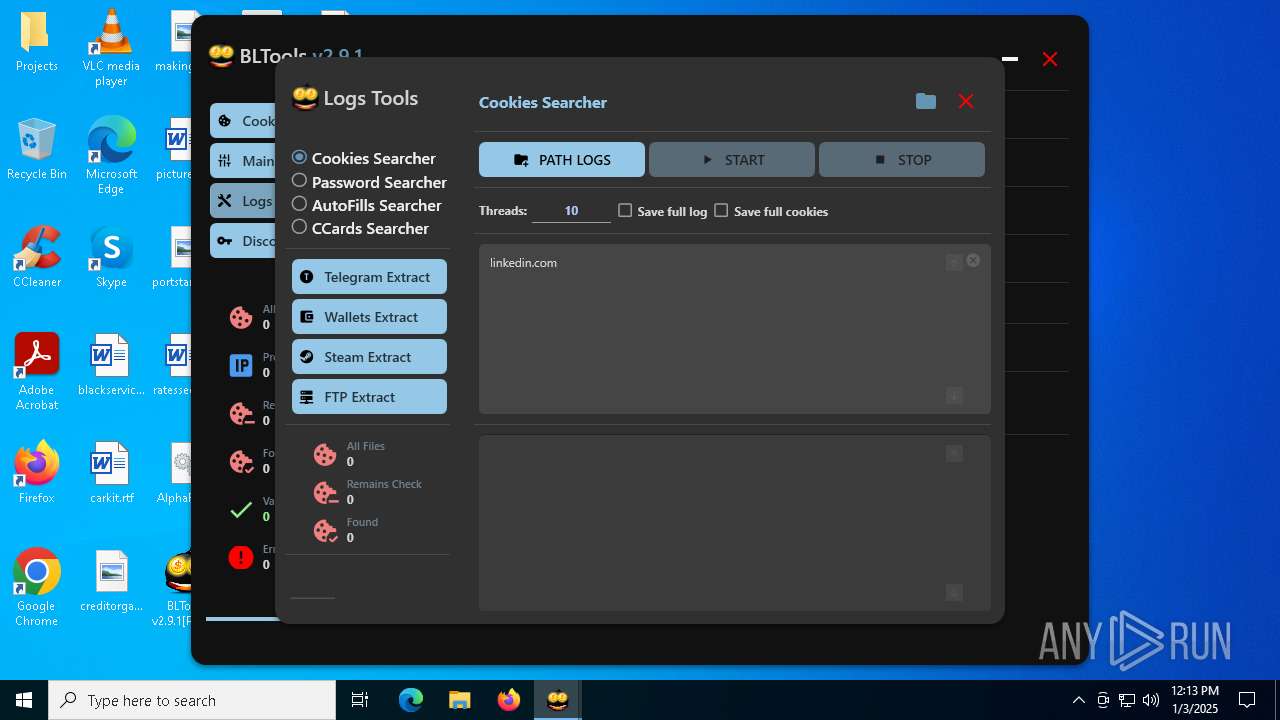
User: admin Integrity Level: MEDIUM Description: BLTools Cookies Checker Version: 2.9.1.0 Modules
ims-api(PID) Process(2828) BLTools v2.9.1[PRO].exe Telegram-Tokens (1)6448011148:AAHcTB8GjoKK5nZce44buWa2oZ3D7kqBVPk Telegram-Info-Links 6448011148:AAHcTB8GjoKK5nZce44buWa2oZ3D7kqBVPk Get info about bothttps://api.telegram.org/bot6448011148:AAHcTB8GjoKK5nZce44buWa2oZ3D7kqBVPk/getMe Get incoming updateshttps://api.telegram.org/bot6448011148:AAHcTB8GjoKK5nZce44buWa2oZ3D7kqBVPk/getUpdates Get webhookhttps://api.telegram.org/bot6448011148:AAHcTB8GjoKK5nZce44buWa2oZ3D7kqBVPk/getWebhookInfo Delete webhookhttps://api.telegram.org/bot6448011148:AAHcTB8GjoKK5nZce44buWa2oZ3D7kqBVPk/deleteWebhook Drop incoming updateshttps://api.telegram.org/bot6448011148:AAHcTB8GjoKK5nZce44buWa2oZ3D7kqBVPk/deleteWebhook?drop_pending_updates=true Telegram-Requests Token6448011148:AAHcTB8GjoKK5nZce44buWa2oZ3D7kqBVPk End-PointsendMessage Args | |||||||||||||||
| 5728 | C:\WINDOWS\System32\rundll32.exe C:\WINDOWS\System32\shell32.dll,SHCreateLocalServerRunDll {9aa46009-3ce0-458a-a354-715610a075e6} -Embedding | C:\Windows\System32\rundll32.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6172 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Temp\Bltools 2.9.1[PRO] (3).zip" | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
Total events
14 238
Read events
13 924
Write events
300
Delete events
14
Modification events
| (PID) Process: | (6172) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\preferences.zip | |||
| (PID) Process: | (6172) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\chromium_ext.zip | |||
| (PID) Process: | (6172) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
| (PID) Process: | (6172) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\Bltools 2.9.1[PRO] (3).zip | |||
| (PID) Process: | (6172) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (6172) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (6172) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (6172) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (6172) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface |
| Operation: | write | Name: | ShowPassword |
Value: 0 | |||
| (PID) Process: | (6172) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface\MainWin |
| Operation: | write | Name: | Placement |
Value: 2C0000000000000001000000FFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFF3D0000002D000000FD03000016020000 | |||
Executable files
410
Suspicious files
0
Text files
2 419
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6172 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRb6172.16999\License.dll | text | |
MD5:D76BF73F3D3768A4589E72A7B2B83088 | SHA256:EAAB53F4B23C3CC9E3C9D4D5D4689438146519E69C7063F4F15B0A43DD861F7B | |||
| 6172 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRb6172.16999\Projects\carousell_SG.proj | text | |
MD5:C9E038B00F09D559AE137ADAFFD1BA91 | SHA256:EBB25FBF252E0769D66447F885B2B047DFFCD3EEFD715300E5978F1BA13B4F17 | |||
| 6172 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRb6172.16999\CookiesCreator v1.2.exe | executable | |
MD5:30C33F45545B68BD1E0D7EC79A090883 | SHA256:4E95226CCE6E17FDC39F3A5F9050720D7848BB34CE2DF72E63C878235C5BE630 | |||
| 6172 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRb6172.16999\Extreme.Net.dll | executable | |
MD5:F79F0E3A0361CAC000E2D3553753CD68 | SHA256:8A6518AB7419FBEC3AC9875BAA3AFB410AD1398C7AA622A09CD9084EC6CADFCD | |||
| 6172 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRb6172.16999\MaterialDesignThemes.Wpf.dll | executable | |
MD5:824CBF63999F954AA1747F79586A4D3C | SHA256:344E2CEE979E979932F504DC76BD75E97AE1FF46CAA3FE2795ADFE0A866347F7 | |||
| 6172 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRb6172.16999\Microsoft.Xaml.Behaviors.dll | executable | |
MD5:95F46F34C099421D917D5FEADBB33EDB | SHA256:8E77A1DD5E2DF4D4AF801376CC3428B082EB49FCB6E647B933967FAE12AD9D5D | |||
| 6172 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRb6172.16999\Projects\Ebay.proj | text | |
MD5:A57E89250A50C010B2B6EDD2EFD0B39F | SHA256:51314174405FE1D723621C67C12C03550426F07A83DDCAB9E36E6D992498D899 | |||
| 6172 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRb6172.16999\BLTools v2.9.1[PRO].exe | executable | |
MD5:025D637741B1B326DED2E99E6B54ED77 | SHA256:D68B3CDCA20F0B871A653A3203E4292846E766B45FB989856A2DE0FB9E0C4860 | |||
| 6172 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRb6172.16999\Projects\GitHub.proj | text | |
MD5:B7126FF12E98449DAB0F633F4F67FD52 | SHA256:983FBD68350AF56C31CC6C39C8367D787D47954BCDCCDF665DFB80F73F2CB141 | |||
| 6172 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRb6172.16999\Projects\Godaddy.proj | text | |
MD5:35DC422A9D0CD1393E6899CC68C4138B | SHA256:0ED94DBFAD19CACED82F9BA48B171B1AAD9AC7E2BE4EBE3D5FDCBFAAB9CD3AEC | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
10
TCP/UDP connections
34
DNS requests
20
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
524 | svchost.exe | GET | 200 | 2.16.164.51:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
4712 | MoUsoCoreWorker.exe | GET | 200 | 2.16.164.51:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
4712 | MoUsoCoreWorker.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
524 | svchost.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
1176 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
6352 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAUZZSZEml49Gjh0j13P68w%3D | unknown | — | — | whitelisted |
7028 | SIHClient.exe | GET | 200 | 184.30.230.103:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
7028 | SIHClient.exe | GET | 200 | 184.30.230.103:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4712 | MoUsoCoreWorker.exe | 2.16.164.51:80 | crl.microsoft.com | Akamai International B.V. | NL | whitelisted |
524 | svchost.exe | 2.16.164.51:80 | crl.microsoft.com | Akamai International B.V. | NL | whitelisted |
4712 | MoUsoCoreWorker.exe | 95.101.149.131:80 | www.microsoft.com | Akamai International B.V. | NL | unknown |
524 | svchost.exe | 95.101.149.131:80 | www.microsoft.com | Akamai International B.V. | NL | whitelisted |
— | — | 95.101.149.131:80 | www.microsoft.com | Akamai International B.V. | NL | whitelisted |
5064 | SearchApp.exe | 2.23.227.215:443 | www.bing.com | Ooredoo Q.S.C. | QA | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1176 | svchost.exe | 20.190.159.4:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| unknown |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
www.bing.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
go.microsoft.com |
| whitelisted |
arc.msn.com |
| whitelisted |
fd.api.iris.microsoft.com |
| whitelisted |