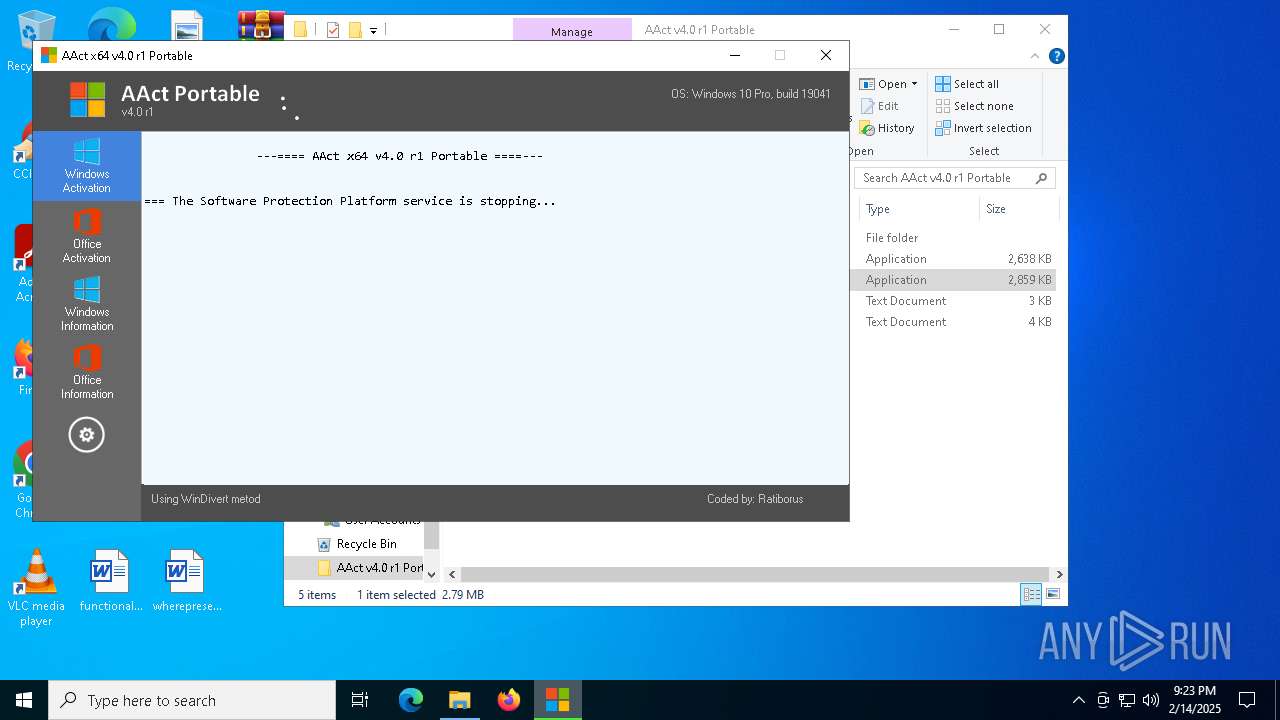
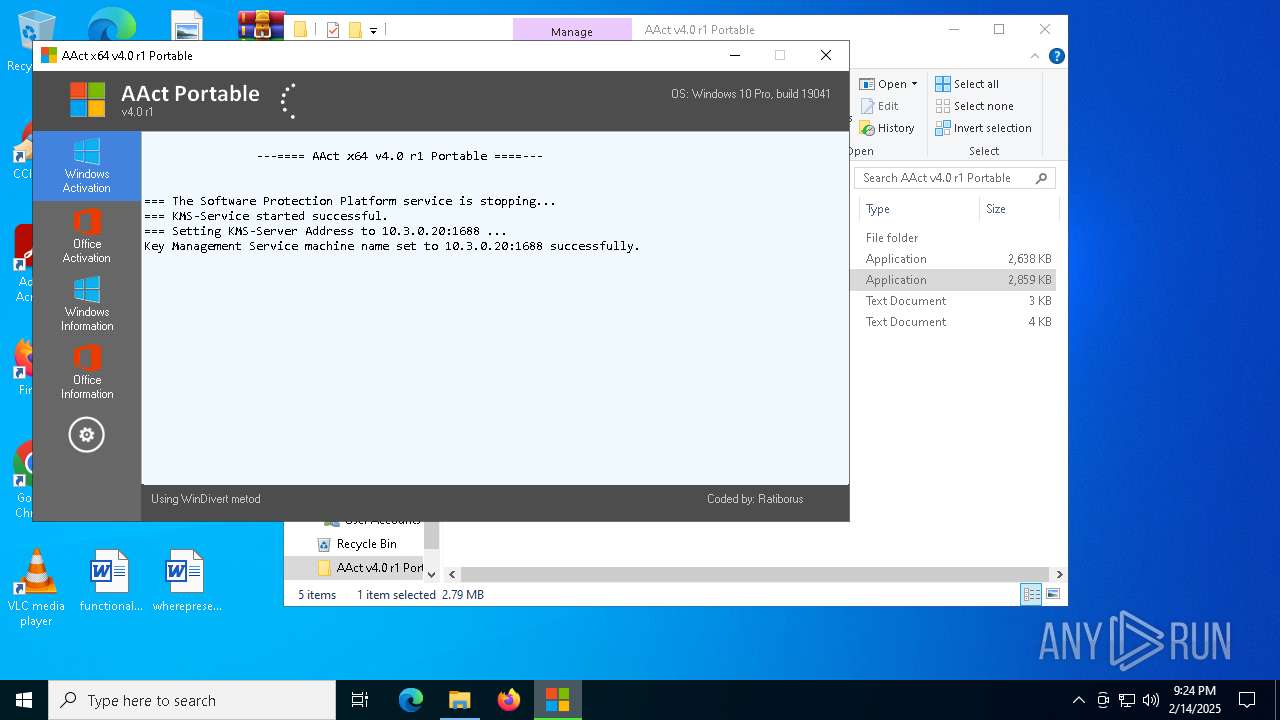
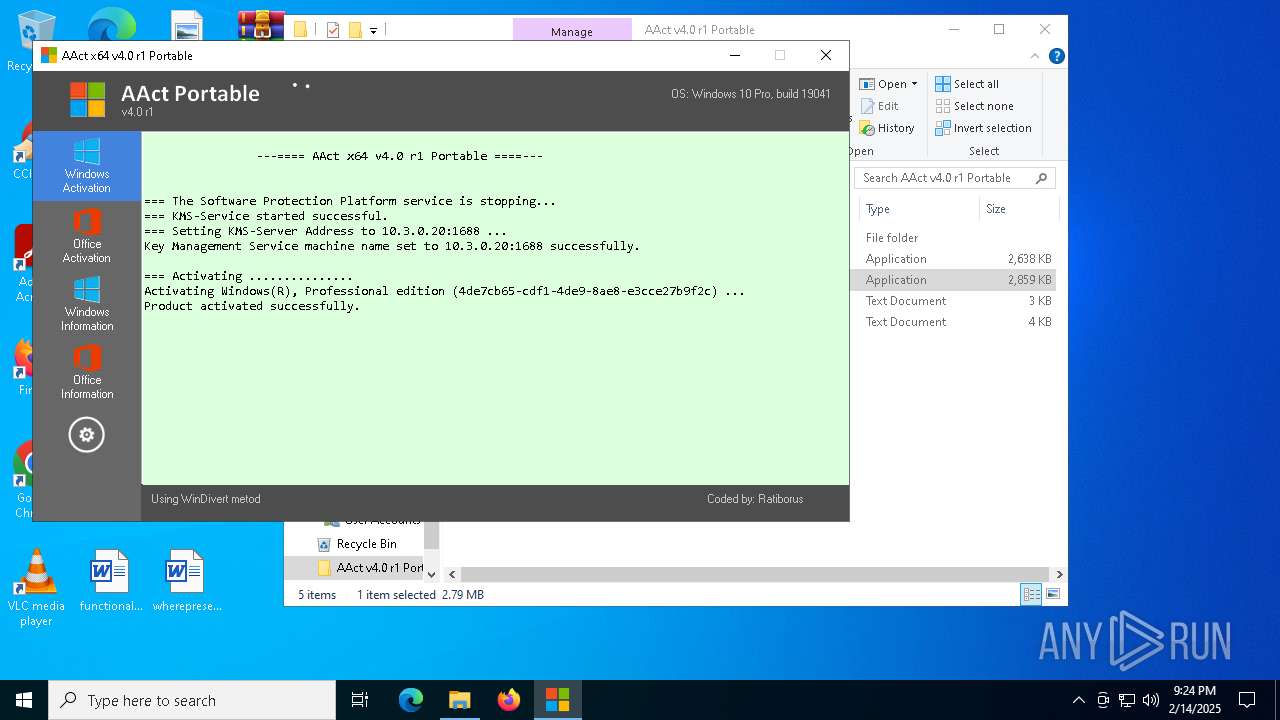
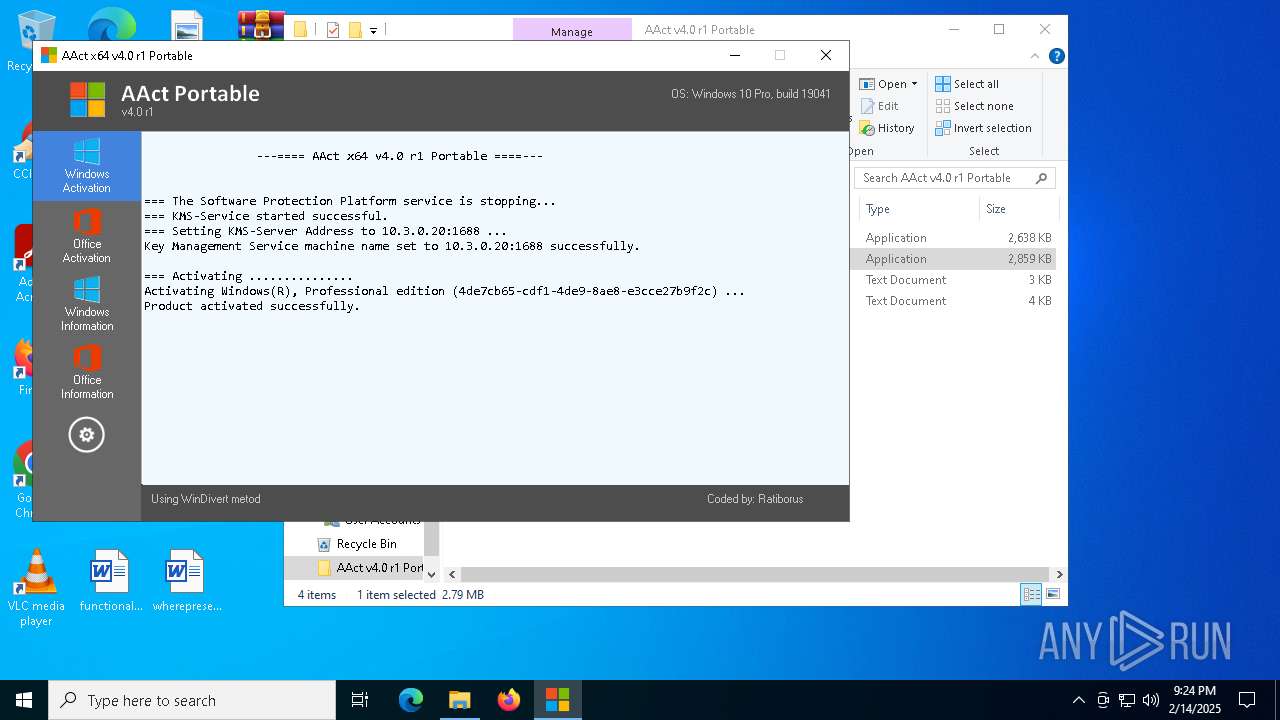
| File name: | AAct v4.0 r1 Portable.zip |
| Full analysis: | https://app.any.run/tasks/6dfbf273-8014-4d3f-9bc3-8fe85ec5c20e |
| Verdict: | Malicious activity |
| Analysis date: | February 14, 2025, 21:23:18 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v1.0 to extract, compression method=store |
| MD5: | B66EF901FB04D3E228F4C4F97C42760C |
| SHA1: | 994F44BBCD31B3444F7D0F44AC7B73ED2388045E |
| SHA256: | 81618A9D4F157E7AC4A7702C9334BD642B1A8519396FDCFE3FEE5A1255681857 |
| SSDEEP: | 98304:tBNMAULNx8spTeKSeo37atmP2vwf3PMl47Mmuo8xsxeMOZaqo6JUrFd0viSRENn3:W4 |
MALICIOUS
Generic archive extractor
- WinRAR.exe (PID: 6436)
Executing a file with an untrusted certificate
- AAct_x64.exe (PID: 6244)
- AAct_x64.exe (PID: 6276)
Uses WMIC.EXE to add exclusions to the Windows Defender
- cmd.exe (PID: 6328)
- cmd.exe (PID: 2356)
- cmd.exe (PID: 132)
- cmd.exe (PID: 396)
- cmd.exe (PID: 624)
Accesses name of the domain to which a computer belongs via WMI (SCRIPT)
- cscript.exe (PID: 6660)
- cscript.exe (PID: 644)
- cscript.exe (PID: 5592)
- cscript.exe (PID: 3188)
SUSPICIOUS
Starts CMD.EXE for commands execution
- AAct_x64.exe (PID: 6276)
Found strings related to reading or modifying Windows Defender settings
- AAct_x64.exe (PID: 6276)
Windows service management via SC.EXE
- sc.exe (PID: 3700)
- sc.exe (PID: 2164)
Uses TASKKILL.EXE to kill process
- cmd.exe (PID: 4952)
- cmd.exe (PID: 7124)
- cmd.exe (PID: 132)
- cmd.exe (PID: 2356)
- cmd.exe (PID: 1808)
- cmd.exe (PID: 6184)
Uses ROUTE.EXE to obtain the routing table information
- cmd.exe (PID: 2076)
- cmd.exe (PID: 6264)
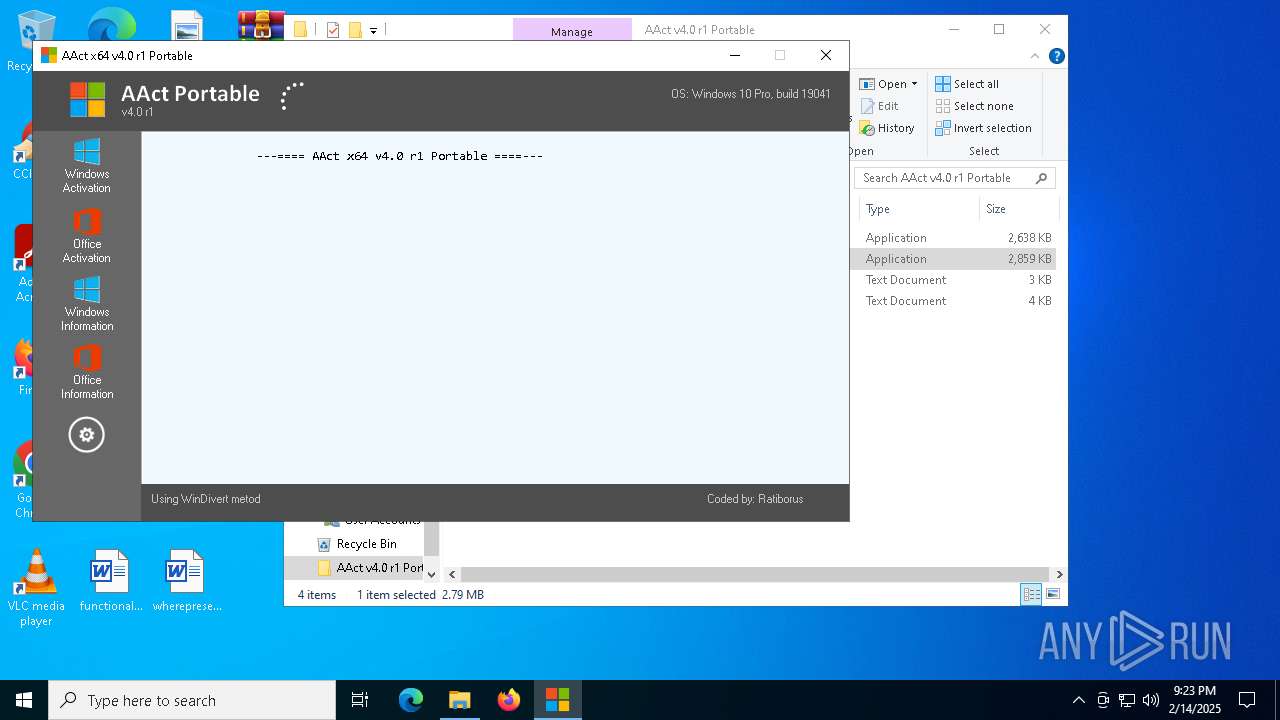
KMS tool has been detected
- cmd.exe (PID: 6268)
- AAct_x64.exe (PID: 6276)
- cmd.exe (PID: 5112)
- cmd.exe (PID: 6016)
Starts SC.EXE for service management
- cmd.exe (PID: 5400)
- cmd.exe (PID: 3060)
- cmd.exe (PID: 900)
- cmd.exe (PID: 6232)
- cmd.exe (PID: 6632)
Stops a currently running service
- sc.exe (PID: 5192)
- sc.exe (PID: 6632)
- sc.exe (PID: 6668)
Uses NETSH.EXE to delete a firewall rule or allowed programs
- cmd.exe (PID: 6268)
- cmd.exe (PID: 6016)
Hides command output
- cmd.exe (PID: 900)
Executable content was dropped or overwritten
- AAct_x64.exe (PID: 6276)
Drops a system driver (possible attempt to evade defenses)
- AAct_x64.exe (PID: 6276)
Uses ROUTE.EXE to modify routing table
- cmd.exe (PID: 5548)
Uses NETSH.EXE to add a firewall rule or allowed programs
- cmd.exe (PID: 5112)
The process executes VB scripts
- cmd.exe (PID: 2008)
- cmd.exe (PID: 3680)
- cmd.exe (PID: 6628)
- cmd.exe (PID: 900)
- cmd.exe (PID: 6408)
- cmd.exe (PID: 4840)
- cmd.exe (PID: 4536)
Uses WMI to retrieve WMI-managed resources (SCRIPT)
- cscript.exe (PID: 1480)
- cscript.exe (PID: 6660)
- cscript.exe (PID: 644)
- cscript.exe (PID: 6148)
- cscript.exe (PID: 3188)
- cscript.exe (PID: 5592)
- cscript.exe (PID: 2672)
Reads data from a binary Stream object (SCRIPT)
- cscript.exe (PID: 1480)
- cscript.exe (PID: 6660)
- cscript.exe (PID: 644)
- cscript.exe (PID: 6148)
- cscript.exe (PID: 2672)
- cscript.exe (PID: 5592)
- cscript.exe (PID: 3188)
Gets full path of the running script (SCRIPT)
- cscript.exe (PID: 1480)
- cscript.exe (PID: 6660)
- cscript.exe (PID: 644)
- cscript.exe (PID: 6148)
- cscript.exe (PID: 2672)
- cscript.exe (PID: 3188)
- cscript.exe (PID: 5592)
Uses REG/REGEDIT.EXE to modify registry
- AAct_x64.exe (PID: 6276)
The process downloads a VBScript from the remote host
- cmd.exe (PID: 900)
INFO
Executable content was dropped or overwritten
- WinRAR.exe (PID: 6436)
Manual execution by a user
- AAct_x64.exe (PID: 6276)
- AAct_x64.exe (PID: 6244)
Reads Environment values
- AAct_x64.exe (PID: 6276)
Reads product name
- AAct_x64.exe (PID: 6276)
Checks supported languages
- AAct_x64.exe (PID: 6276)
- FakeClient.exe (PID: 624)
- KMSSS.exe (PID: 5628)
Checks Windows version
- cmd.exe (PID: 6372)
Checks operating system version
- AAct_x64.exe (PID: 6276)
Reads security settings of Internet Explorer
- WMIC.exe (PID: 6312)
- WMIC.exe (PID: 1852)
- WMIC.exe (PID: 1704)
- WMIC.exe (PID: 1296)
- WMIC.exe (PID: 5572)
- cscript.exe (PID: 1480)
- cscript.exe (PID: 6148)
- cscript.exe (PID: 644)
- cscript.exe (PID: 6660)
- cscript.exe (PID: 2672)
- cscript.exe (PID: 3188)
- cscript.exe (PID: 5592)
Reads the computer name
- AAct_x64.exe (PID: 6276)
- FakeClient.exe (PID: 624)
- KMSSS.exe (PID: 5628)
Deletes a route via ROUTE.EXE
- ROUTE.EXE (PID: 7120)
- ROUTE.EXE (PID: 6152)
The sample compiled with english language support
- AAct_x64.exe (PID: 6276)
Adds a route via ROUTE.EXE
- ROUTE.EXE (PID: 2672)
Reads the machine GUID from the registry
- KMSSS.exe (PID: 5628)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 10 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | None |
| ZipModifyDate: | 2018:09:05 10:43:12 |
| ZipCRC: | 0x00000000 |
| ZipCompressedSize: | - |
| ZipUncompressedSize: | - |
| ZipFileName: | AAct v4.0 r1 Portable/ |
Total processes
231
Monitored processes
101
Malicious processes
9
Suspicious processes
7
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 132 | "C:\WINDOWS\System32\cmd.exe" /c WMIC /NAMESPACE:\\root\Microsoft\Windows\Defender PATH MSFT_MpPreference call Add ExclusionPath="C:\WINDOWS\System32\SppExtComObjPatcher.exe" | C:\Windows\System32\cmd.exe | — | AAct_x64.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 2147749889 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 132 | "C:\WINDOWS\System32\cmd.exe" /c taskkill.exe /t /f /IM SppExtComObj.Exe | C:\Windows\System32\cmd.exe | — | AAct_x64.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 128 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 396 | "C:\WINDOWS\System32\cmd.exe" /c WMIC /NAMESPACE:\\root\Microsoft\Windows\Defender PATH MSFT_MpPreference call Add ExclusionPath="C:\WINDOWS\System32\SppExtComObjHook.dll" | C:\Windows\System32\cmd.exe | — | AAct_x64.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 2147749889 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 524 | taskkill.exe /t /f /IM KMSSS.exe | C:\Windows\System32\taskkill.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Terminates Processes Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 624 | "C:\WINDOWS\System32\cmd.exe" /c WMIC /NAMESPACE:\\root\Microsoft\Windows\Defender PATH MSFT_MpPreference call Add ExclusionPath="C:\Users\admin\Desktop\AAct v4.0 r1 Portable\AAct_files\KMSSS.exe" | C:\Windows\System32\cmd.exe | — | AAct_x64.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 2147749889 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 624 | "FakeClient.exe" 10.3.0.20 | C:\Users\admin\Desktop\AAct v4.0 r1 Portable\AAct_files\x64WDV\FakeClient.exe | — | AAct_x64.exe | |||||||||||
User: admin Integrity Level: HIGH Exit code: 1 Modules
| |||||||||||||||
| 644 | cscript.exe C:\WINDOWS\System32\slmgr.vbs //NoLogo /ckms-domain | C:\Windows\System32\cscript.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft ® Console Based Script Host Exit code: 0 Version: 5.812.10240.16384 Modules
| |||||||||||||||
| 736 | taskkill.exe /t /f /IM SppExtComObj.Exe | C:\Windows\System32\taskkill.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Terminates Processes Exit code: 128 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 768 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 900 | "C:\WINDOWS\System32\cmd.exe" /c sc.exe stop sppsvc >nul 2>&1 | C:\Windows\System32\cmd.exe | — | AAct_x64.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
7 069
Read events
7 048
Write events
21
Delete events
0
Modification events
| (PID) Process: | (6436) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\preferences.zip | |||
| (PID) Process: | (6436) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\chromium_ext.zip | |||
| (PID) Process: | (6436) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
| (PID) Process: | (6436) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\AAct v4.0 r1 Portable.zip | |||
| (PID) Process: | (6436) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (6436) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (6436) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (6436) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (6436) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface\MainWin |
| Operation: | write | Name: | Placement |
Value: 2C0000000000000001000000FFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFF800000030000000B804000019020000 | |||
| (PID) Process: | (6436) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\ArcColumnWidths |
| Operation: | write | Name: | name |
Value: 256 | |||
Executable files
6
Suspicious files
0
Text files
2
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6436 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa6436.1953\AAct v4.0 r1 Portable\readme_en.txt | text | |
MD5:35DB3ACB89F704147901B83C9BDC0B5B | SHA256:C56E528E8E536B5D71033E190B6E5B4EA735D9E76C6EB46CE3AB5BC0C23EB03E | |||
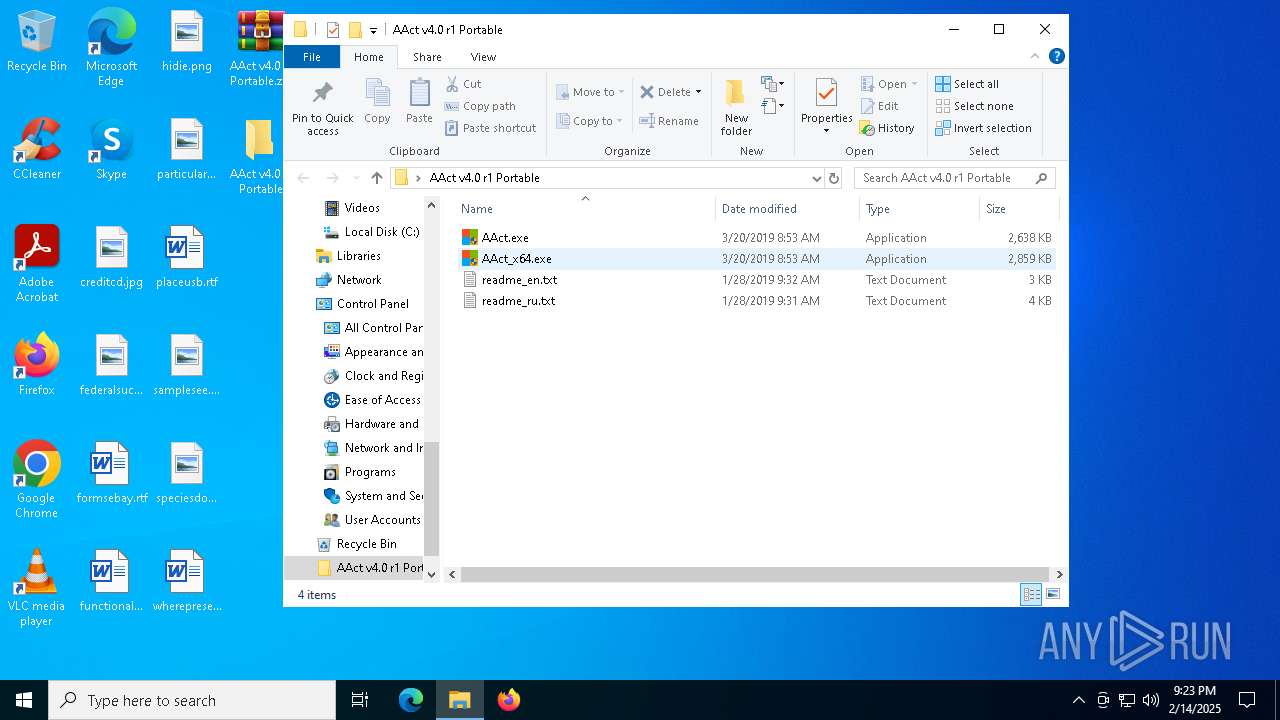
| 6436 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa6436.1953\AAct v4.0 r1 Portable\AAct.exe | executable | |
MD5:A087B2E6EC57B08C0D0750C60F96A74C | SHA256:E12B6641D7E7E4DA97A0FF8E1A0D4840C882569D47B8FAB8FB187AC2B475636C | |||
| 6276 | AAct_x64.exe | C:\Users\admin\Desktop\AAct v4.0 r1 Portable\AAct_files\x64WDV\WinDivert64.sys | executable | |
MD5:D6F42128C81965E12578FECA7DAC500F | SHA256:9026147943BD44A1EB5E2F0C89CC8F441C7D1F13C1571ABA54E262D2E7354798 | |||
| 6276 | AAct_x64.exe | C:\Users\admin\Desktop\AAct v4.0 r1 Portable\AAct_files\KMSSS.exe | executable | |
MD5:01A80AAD5DABED1C1580F7E00213CF9D | SHA256:FD7499214ABAA13BF56D006AB7DE78EB8D6ADF17926C24ACE024D067049BC81D | |||
| 6436 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa6436.1953\AAct v4.0 r1 Portable\readme_ru.txt | text | |
MD5:97CFC67D7774B3FAC626CF36A1456528 | SHA256:17FF3A22661B442DBE6437FAC5D276A152C7ADFFA65FDCC106BA60B5A3D583C0 | |||
| 6436 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa6436.1953\AAct v4.0 r1 Portable\AAct_x64.exe | executable | |
MD5:7F3DFE3836F04A1A4CAB8377FC572500 | SHA256:F53A0AC49FE1EB88C937F8829B93A24BBB0B332B955BB1374046FBCEAF663E54 | |||
| 6276 | AAct_x64.exe | C:\Users\admin\Desktop\AAct v4.0 r1 Portable\AAct_files\x64WDV\FakeClient.exe | executable | |
MD5:6241A145A6BC3511E7690DCF107CEFD8 | SHA256:2218293E4442DEB06E398AA0357AEF54DF377B95E46B6ED79B48B65B666C9405 | |||
| 6276 | AAct_x64.exe | C:\Users\admin\Desktop\AAct v4.0 r1 Portable\AAct_files\x64WDV\WinDivert.dll | executable | |
MD5:EE42F18F56E8AB20103D0EACC6CB3056 | SHA256:D0D8E5806952CE8F321D106551C680AFE5A074CB9366A54282FF83397C64C27F | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
9
TCP/UDP connections
33
DNS requests
16
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
4712 | MoUsoCoreWorker.exe | GET | 200 | 23.32.238.34:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
4712 | MoUsoCoreWorker.exe | GET | 200 | 2.16.253.202:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 23.32.238.34:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 2.16.253.202:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
1176 | svchost.exe | GET | 200 | 184.30.131.245:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
— | — | GET | 200 | 184.30.131.245:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
6756 | backgroundTaskHost.exe | GET | 200 | 2.23.77.188:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAUZZSZEml49Gjh0j13P68w%3D | unknown | — | — | whitelisted |
1580 | SIHClient.exe | GET | 200 | 23.219.150.101:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
1580 | SIHClient.exe | GET | 200 | 23.219.150.101:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 40.127.240.158:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | IE | unknown |
4712 | MoUsoCoreWorker.exe | 23.32.238.34:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
— | — | 23.32.238.34:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
4712 | MoUsoCoreWorker.exe | 2.16.253.202:80 | www.microsoft.com | Akamai International B.V. | NL | whitelisted |
— | — | 2.16.253.202:80 | www.microsoft.com | Akamai International B.V. | NL | whitelisted |
5064 | SearchApp.exe | 2.16.204.135:443 | www.bing.com | Akamai International B.V. | DE | whitelisted |
— | — | 184.30.131.245:80 | ocsp.digicert.com | AKAMAI-AS | US | whitelisted |
4328 | svchost.exe | 40.127.240.158:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | IE | unknown |
3976 | svchost.exe | 40.127.240.158:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | IE | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
www.bing.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
login.live.com |
| whitelisted |
go.microsoft.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
arc.msn.com |
| whitelisted |
fd.api.iris.microsoft.com |
| whitelisted |