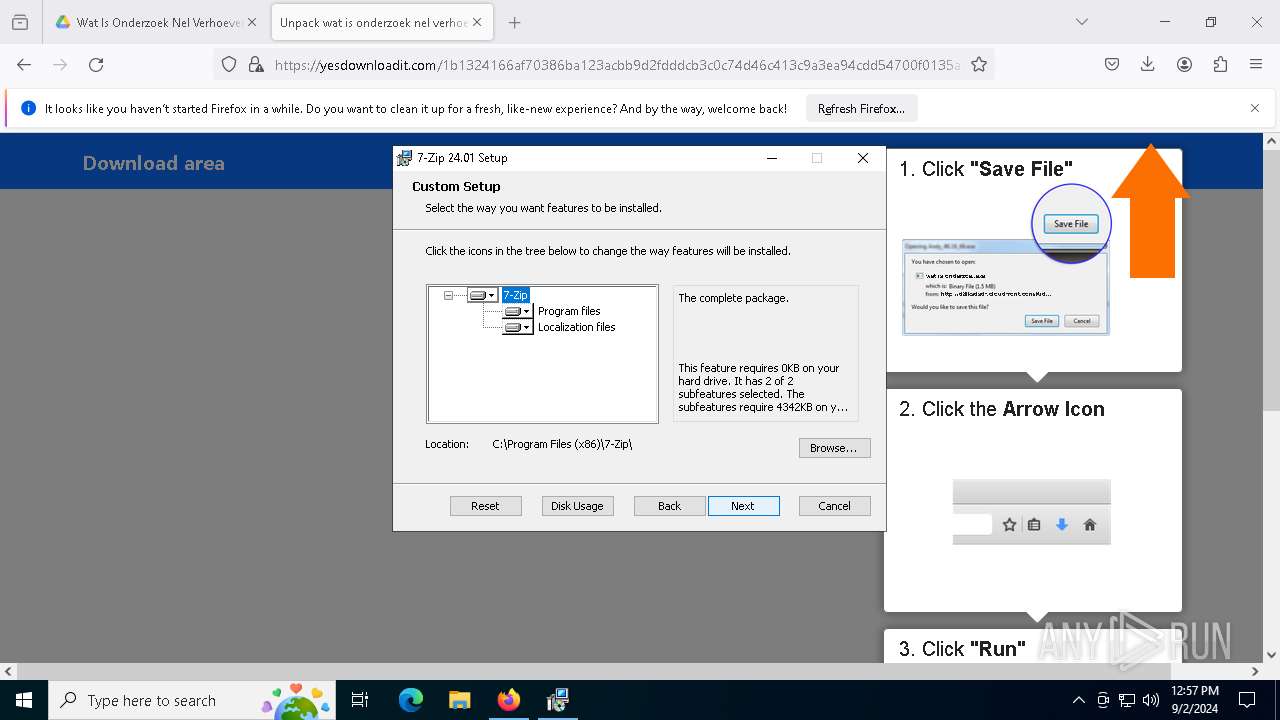
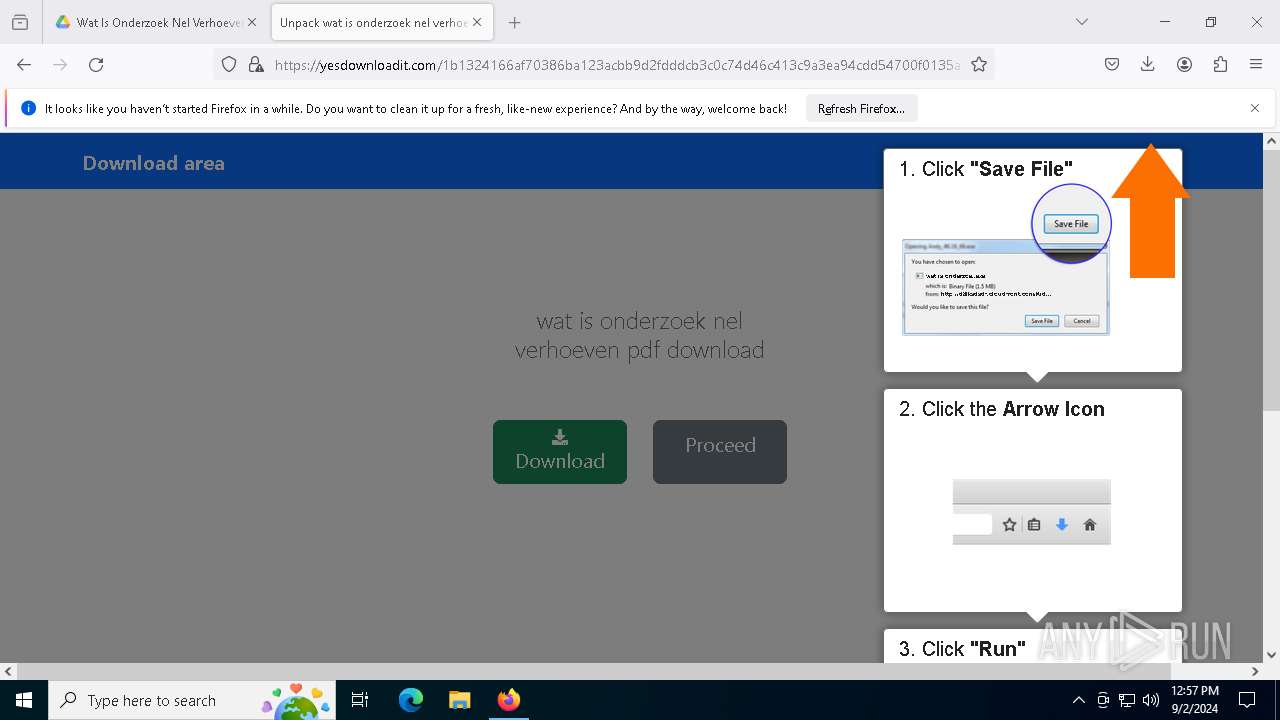
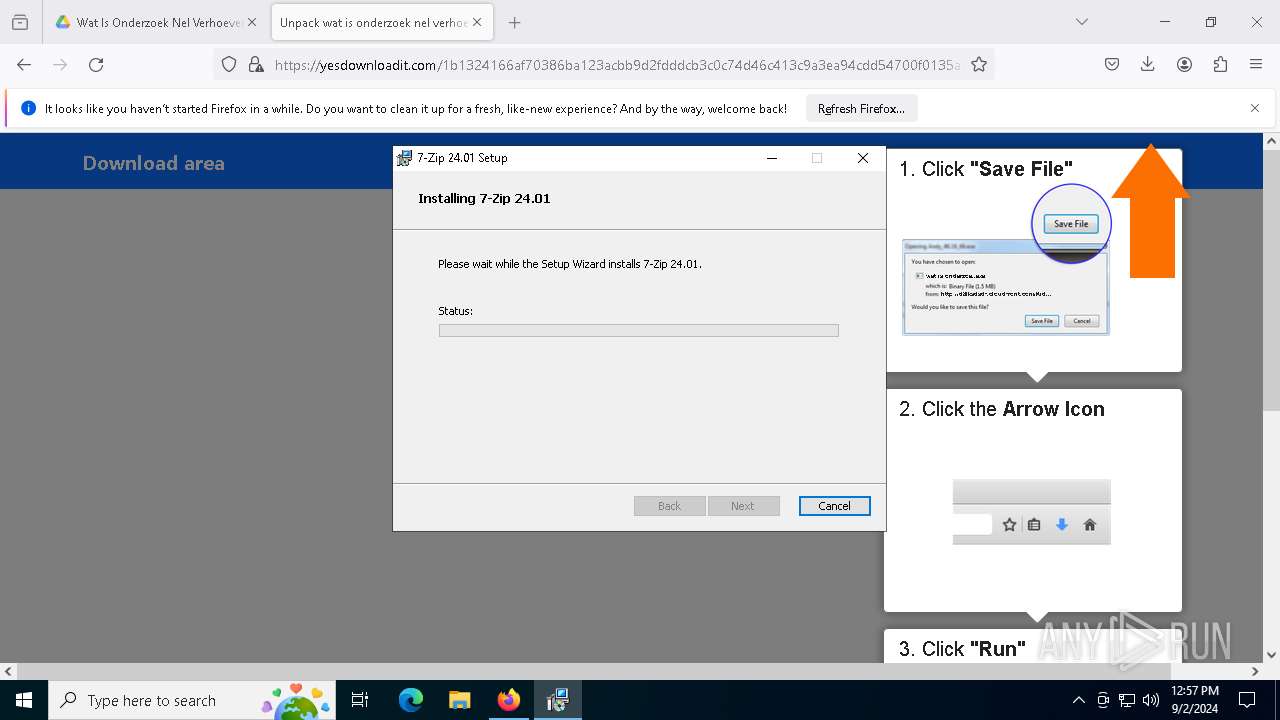
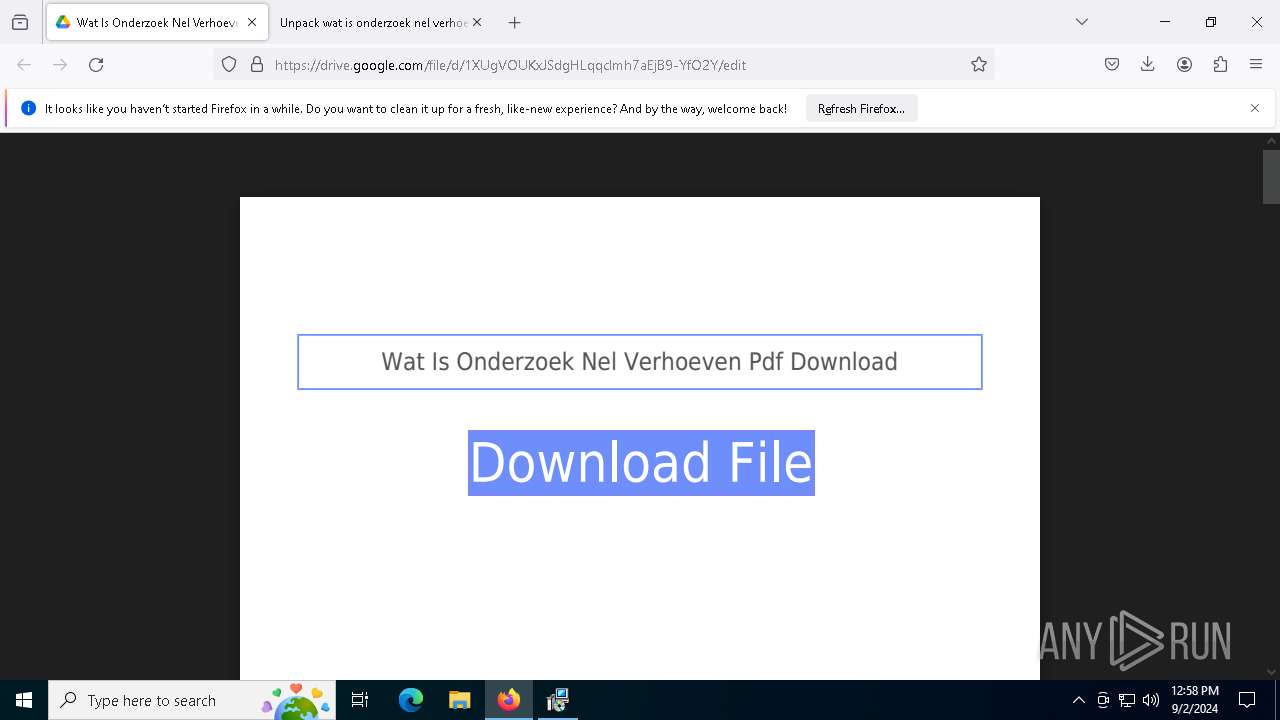
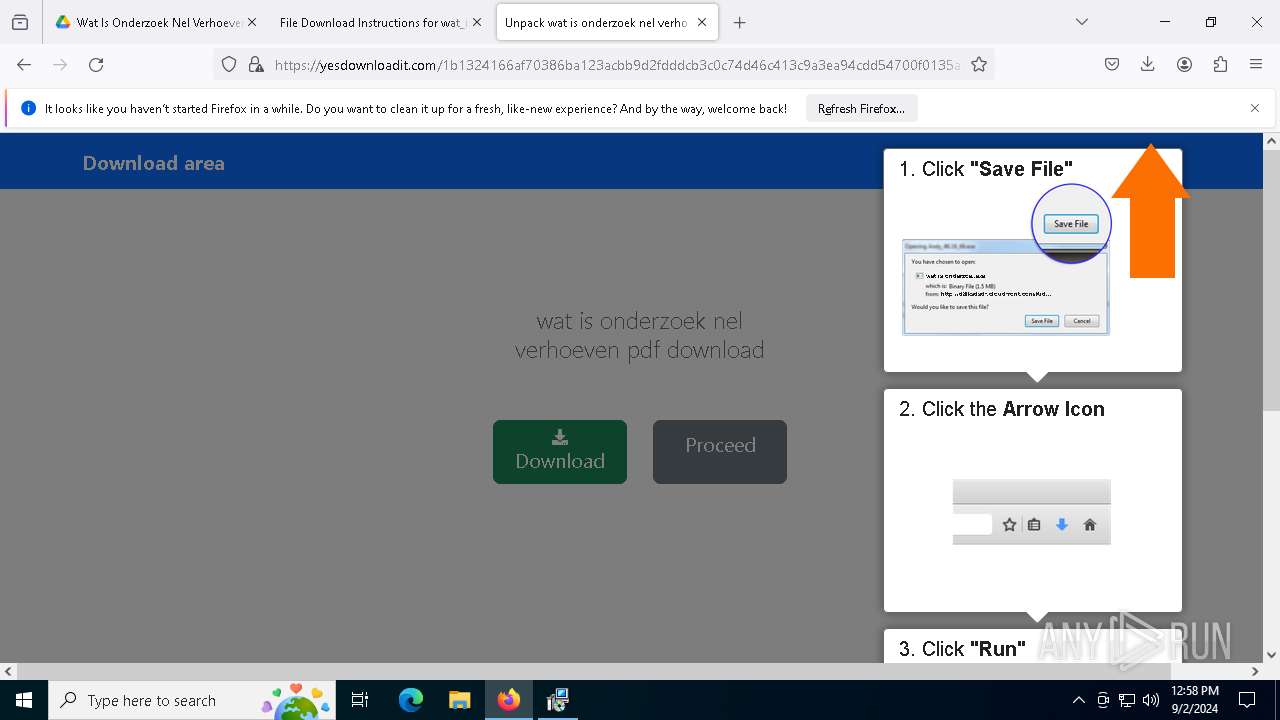
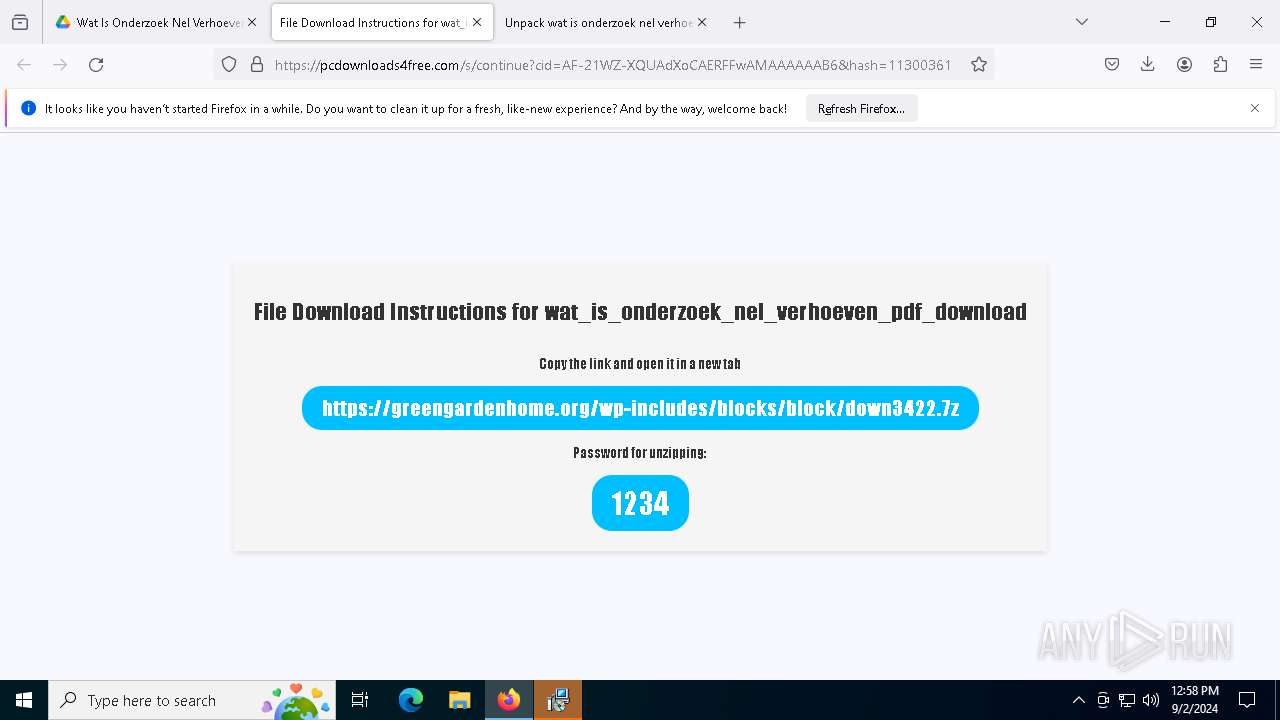
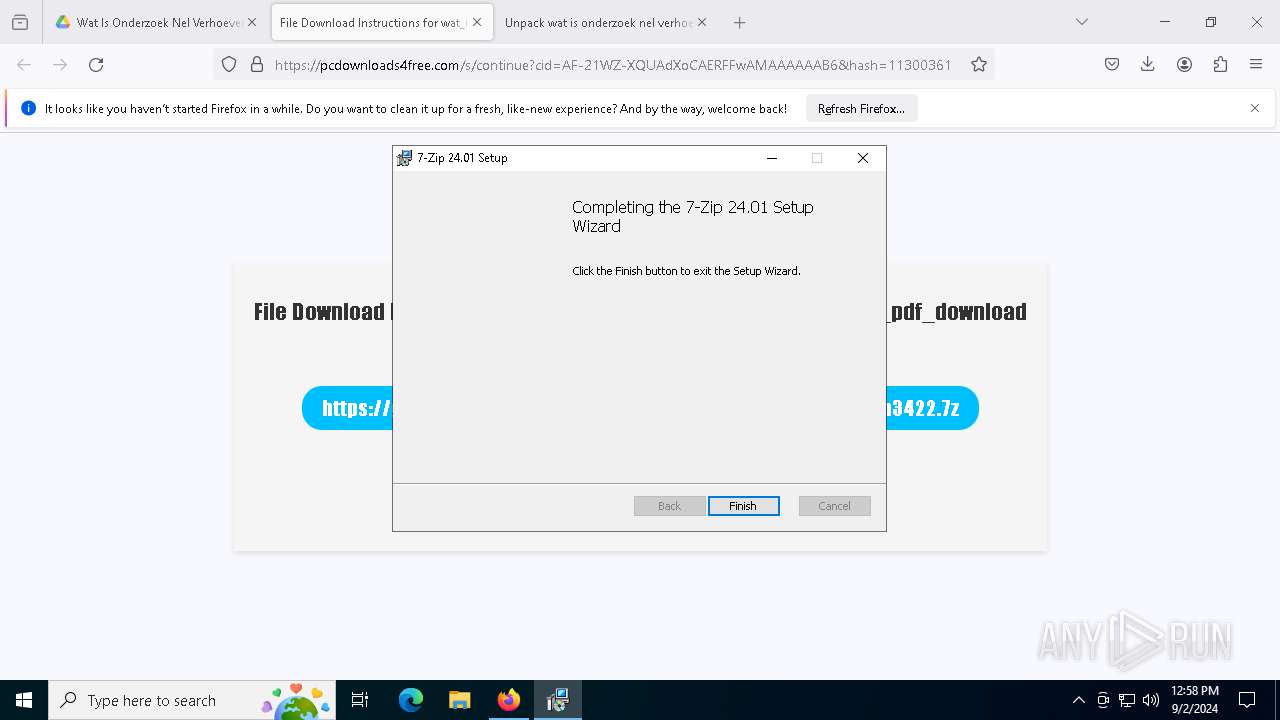
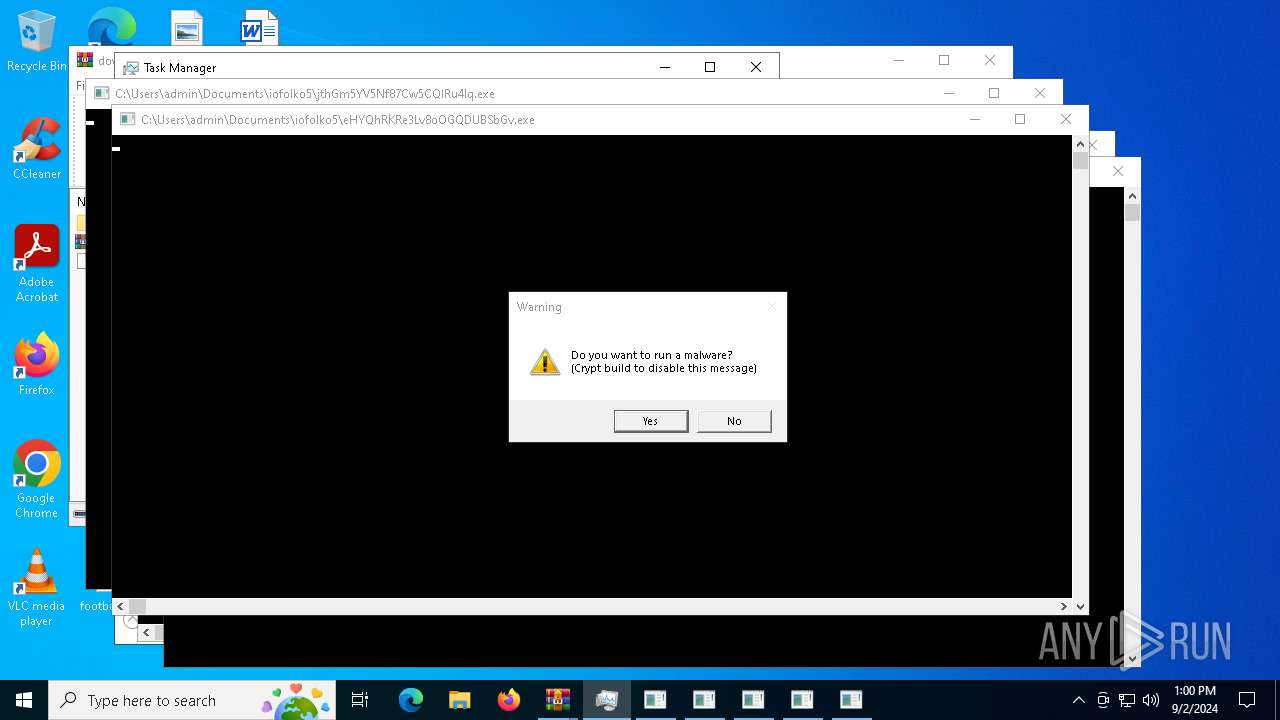
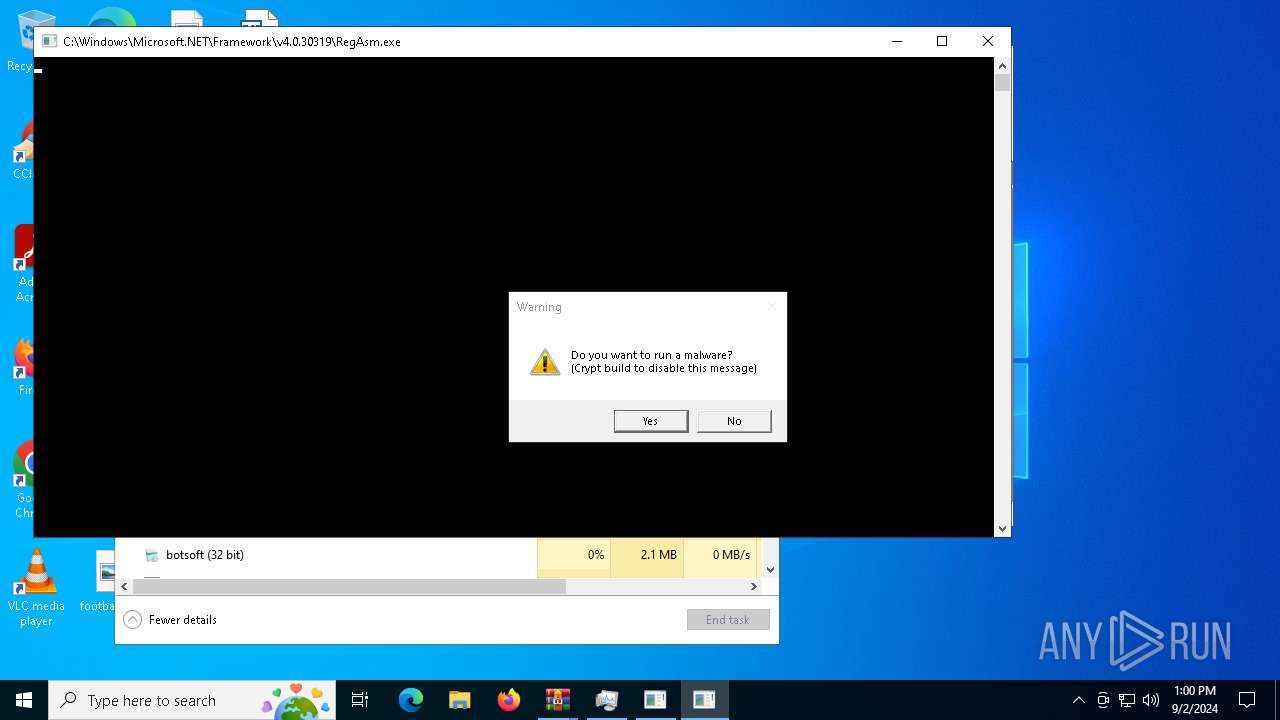
| URL: | https://drive.google.com/file/d/1XUgVOUKxJSdgHLqqclmh7aEjB9-YfO2Y/edit |
| Full analysis: | https://app.any.run/tasks/7822af07-1cc7-4674-9fe1-b5441987f9da |
| Verdict: | Malicious activity |
| Threats: | A loader is malicious software that infiltrates devices to deliver malicious payloads. This malware is capable of infecting victims’ computers, analyzing their system information, and installing other types of threats, such as trojans or stealers. Criminals usually deliver loaders through phishing emails and links by relying on social engineering to trick users into downloading and running their executables. Loaders employ advanced evasion and persistence tactics to avoid detection. |
| Analysis date: | September 02, 2024, 12:57:18 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MD5: | AC46A28FFC15B4F07BF5A5A587D1B410 |
| SHA1: | 054317BC93F8627B199BC273C720B4D75EF7CE76 |
| SHA256: | 81555C01DE3D6893A536EE3F3C4F6B114939C8F151B52E9541784E397431623D |
| SSDEEP: | 3:N8PMMtZJuloHwwo20QGAEGsW:2AnZ2FD |
MALICIOUS
PRIVATELOADER has been detected (SURICATA)
- Quantities.pif (PID: 7296)
- Quantities.pif (PID: 6124)
Actions looks like stealing of personal data
- Quantities.pif (PID: 7296)
- K77Fh1qxOWRMTQJYbZHAixag.exe (PID: 7216)
- RegAsm.exe (PID: 7292)
- RegAsm.exe (PID: 6532)
- Quantities.pif (PID: 6124)
- RegAsm.exe (PID: 7816)
Connects to the CnC server
- Quantities.pif (PID: 7296)
- K77Fh1qxOWRMTQJYbZHAixag.exe (PID: 7216)
- RegAsm.exe (PID: 6532)
- Quantities.pif (PID: 6124)
- RegAsm.exe (PID: 7816)
STEALC has been detected (SURICATA)
- K77Fh1qxOWRMTQJYbZHAixag.exe (PID: 7216)
- RegAsm.exe (PID: 7816)
Changes the autorun value in the registry
- Yup1erlzMpQriLXfQvqWA_8g.exe (PID: 8092)
- reg.exe (PID: 5548)
- reg.exe (PID: 4528)
Stealers network behavior
- K77Fh1qxOWRMTQJYbZHAixag.exe (PID: 7216)
- Yup1erlzMpQriLXfQvqWA_8g.exe (PID: 8092)
- RegAsm.exe (PID: 6532)
- RegAsm.exe (PID: 7292)
- RegAsm.exe (PID: 7816)
Create files in the Startup directory
- Yup1erlzMpQriLXfQvqWA_8g.exe (PID: 8092)
Uses Task Scheduler to run other applications
- Yup1erlzMpQriLXfQvqWA_8g.exe (PID: 8092)
Uses Task Scheduler to autorun other applications
- Yup1erlzMpQriLXfQvqWA_8g.exe (PID: 8092)
RISEPRO has been detected (SURICATA)
- Yup1erlzMpQriLXfQvqWA_8g.exe (PID: 8092)
REDLINE has been detected (SURICATA)
- RegAsm.exe (PID: 6532)
METASTEALER has been detected (SURICATA)
- RegAsm.exe (PID: 6532)
- RegAsm.exe (PID: 7292)
Steals credentials from Web Browsers
- RegAsm.exe (PID: 7292)
- RegAsm.exe (PID: 6532)
- K77Fh1qxOWRMTQJYbZHAixag.exe (PID: 7216)
- RegAsm.exe (PID: 7816)
STEALC has been detected (YARA)
- K77Fh1qxOWRMTQJYbZHAixag.exe (PID: 7216)
- RegAsm.exe (PID: 7816)
PHISHING has been detected (SURICATA)
- svchost.exe (PID: 2256)
MINER has been detected (SURICATA)
- svchost.exe (PID: 2256)
VIDAR has been detected (YARA)
- RegAsm.exe (PID: 4448)
LUMMA has been detected (YARA)
- Yup1erlzMpQriLXfQvqWA_8g.exe (PID: 8092)
- screenrecorderle32.exe (PID: 8152)
SUSPICIOUS
Executes as Windows Service
- VSSVC.exe (PID: 8184)
Creates/Modifies COM task schedule object
- msiexec.exe (PID: 7884)
Drops 7-zip archiver for unpacking
- msiexec.exe (PID: 7884)
Reads the Windows owner or organization settings
- msiexec.exe (PID: 7884)
- wdQecB0wVN0lwhaZwzoLuAti.tmp (PID: 8012)
- UIXzMT1oWhYdCWSZ4TivU04j.tmp (PID: 6204)
Reads security settings of Internet Explorer
- WinRAR.exe (PID: 2480)
- WinRAR.exe (PID: 7672)
- File.exe (PID: 7716)
- File.exe (PID: 6000)
- Quantities.pif (PID: 7296)
- K77Fh1qxOWRMTQJYbZHAixag.exe (PID: 7216)
- Yup1erlzMpQriLXfQvqWA_8g.exe (PID: 4672)
- Quantities.pif (PID: 6124)
- RegAsm.exe (PID: 7816)
Application launched itself
- WinRAR.exe (PID: 2480)
- cmd.exe (PID: 3692)
- cmd.exe (PID: 3648)
- Yup1erlzMpQriLXfQvqWA_8g.exe (PID: 2820)
- Yup1erlzMpQriLXfQvqWA_8g.exe (PID: 4672)
- Yup1erlzMpQriLXfQvqWA_8g.exe (PID: 4524)
- M2_wXb0vXnuBxHOr7rwwWhEP.exe (PID: 6684)
Executing commands from a ".bat" file
- File.exe (PID: 7716)
- File.exe (PID: 6000)
Reads the date of Windows installation
- File.exe (PID: 7716)
- File.exe (PID: 6000)
- Yup1erlzMpQriLXfQvqWA_8g.exe (PID: 4672)
- RegAsm.exe (PID: 7816)
Starts CMD.EXE for commands execution
- File.exe (PID: 7716)
- cmd.exe (PID: 3692)
- File.exe (PID: 6000)
- cmd.exe (PID: 3648)
- RegAsm.exe (PID: 7816)
Get information on the list of running processes
- cmd.exe (PID: 3692)
- cmd.exe (PID: 3648)
Using 'findstr.exe' to search for text patterns in files and output
- cmd.exe (PID: 3692)
- cmd.exe (PID: 3648)
Drops a file with a rarely used extension (PIF)
- cmd.exe (PID: 3692)
Executable content was dropped or overwritten
- cmd.exe (PID: 3692)
- Quantities.pif (PID: 7296)
- wdQecB0wVN0lwhaZwzoLuAti.exe (PID: 1280)
- wdQecB0wVN0lwhaZwzoLuAti.tmp (PID: 8012)
- screenrecorderle32.exe (PID: 8152)
- Yup1erlzMpQriLXfQvqWA_8g.exe (PID: 8092)
- K77Fh1qxOWRMTQJYbZHAixag.exe (PID: 7216)
- G2dX3FvDEyzA7uSCi9dzFYdG.exe (PID: 7880)
- Quantities.pif (PID: 6124)
- etzpikspwykg.exe (PID: 5144)
- RegAsm.exe (PID: 7816)
- UIXzMT1oWhYdCWSZ4TivU04j.tmp (PID: 6204)
- UIXzMT1oWhYdCWSZ4TivU04j.exe (PID: 7784)
The executable file from the user directory is run by the CMD process
- Quantities.pif (PID: 5140)
- Quantities.pif (PID: 4024)
Starts application with an unusual extension
- cmd.exe (PID: 3692)
- cmd.exe (PID: 3648)
Process drops legitimate windows executable
- WinRAR.exe (PID: 7672)
- wdQecB0wVN0lwhaZwzoLuAti.tmp (PID: 8012)
- K77Fh1qxOWRMTQJYbZHAixag.exe (PID: 7216)
- RegAsm.exe (PID: 7816)
- UIXzMT1oWhYdCWSZ4TivU04j.tmp (PID: 6204)
Checks for external IP
- svchost.exe (PID: 2256)
- Quantities.pif (PID: 7296)
- Quantities.pif (PID: 6124)
Checks Windows Trust Settings
- Quantities.pif (PID: 7296)
- Quantities.pif (PID: 6124)
Process requests binary or script from the Internet
- Quantities.pif (PID: 7296)
- K77Fh1qxOWRMTQJYbZHAixag.exe (PID: 7216)
- Quantities.pif (PID: 6124)
- RegAsm.exe (PID: 7816)
Connects to the server without a host name
- Quantities.pif (PID: 7296)
- Quantities.pif (PID: 6124)
- RegAsm.exe (PID: 7816)
- K77Fh1qxOWRMTQJYbZHAixag.exe (PID: 7216)
Potential Corporate Privacy Violation
- Quantities.pif (PID: 7296)
- svchost.exe (PID: 2256)
- K77Fh1qxOWRMTQJYbZHAixag.exe (PID: 7216)
- Quantities.pif (PID: 6124)
- RegAsm.exe (PID: 7816)
Windows Defender mutex has been found
- K77Fh1qxOWRMTQJYbZHAixag.exe (PID: 7216)
- RegAsm.exe (PID: 7816)
Reads the BIOS version
- K77Fh1qxOWRMTQJYbZHAixag.exe (PID: 7216)
- jT1wfVFaZRJ86jCrX2kWQgZR.exe (PID: 4284)
Searches for installed software
- K77Fh1qxOWRMTQJYbZHAixag.exe (PID: 7216)
- RegAsm.exe (PID: 7292)
- RegAsm.exe (PID: 6532)
- RegAsm.exe (PID: 7816)
Contacting a server suspected of hosting an CnC
- K77Fh1qxOWRMTQJYbZHAixag.exe (PID: 7216)
- Yup1erlzMpQriLXfQvqWA_8g.exe (PID: 8092)
- RegAsm.exe (PID: 7292)
- RegAsm.exe (PID: 7816)
Connects to unusual port
- Yup1erlzMpQriLXfQvqWA_8g.exe (PID: 8092)
- RegAsm.exe (PID: 6532)
- RegAsm.exe (PID: 7292)
The process drops Mozilla's DLL files
- K77Fh1qxOWRMTQJYbZHAixag.exe (PID: 7216)
- RegAsm.exe (PID: 7816)
The process drops C-runtime libraries
- K77Fh1qxOWRMTQJYbZHAixag.exe (PID: 7216)
- RegAsm.exe (PID: 7816)
Uses REG/REGEDIT.EXE to modify registry
- G2dX3FvDEyzA7uSCi9dzFYdG.exe (PID: 7880)
- etzpikspwykg.exe (PID: 5144)
Uses powercfg.exe to modify the power settings
- G2dX3FvDEyzA7uSCi9dzFYdG.exe (PID: 7880)
- etzpikspwykg.exe (PID: 5144)
Starts itself from another location
- G2dX3FvDEyzA7uSCi9dzFYdG.exe (PID: 7880)
Drops a system driver (possible attempt to evade defenses)
- etzpikspwykg.exe (PID: 5144)
Crypto Currency Mining Activity Detected
- svchost.exe (PID: 2256)
INFO
Connects to unusual port
- firefox.exe (PID: 1184)
Application launched itself
- firefox.exe (PID: 6960)
- firefox.exe (PID: 1184)
Reads Microsoft Office registry keys
- firefox.exe (PID: 1184)
Executable content was dropped or overwritten
- firefox.exe (PID: 1184)
- msiexec.exe (PID: 7884)
- WinRAR.exe (PID: 7672)
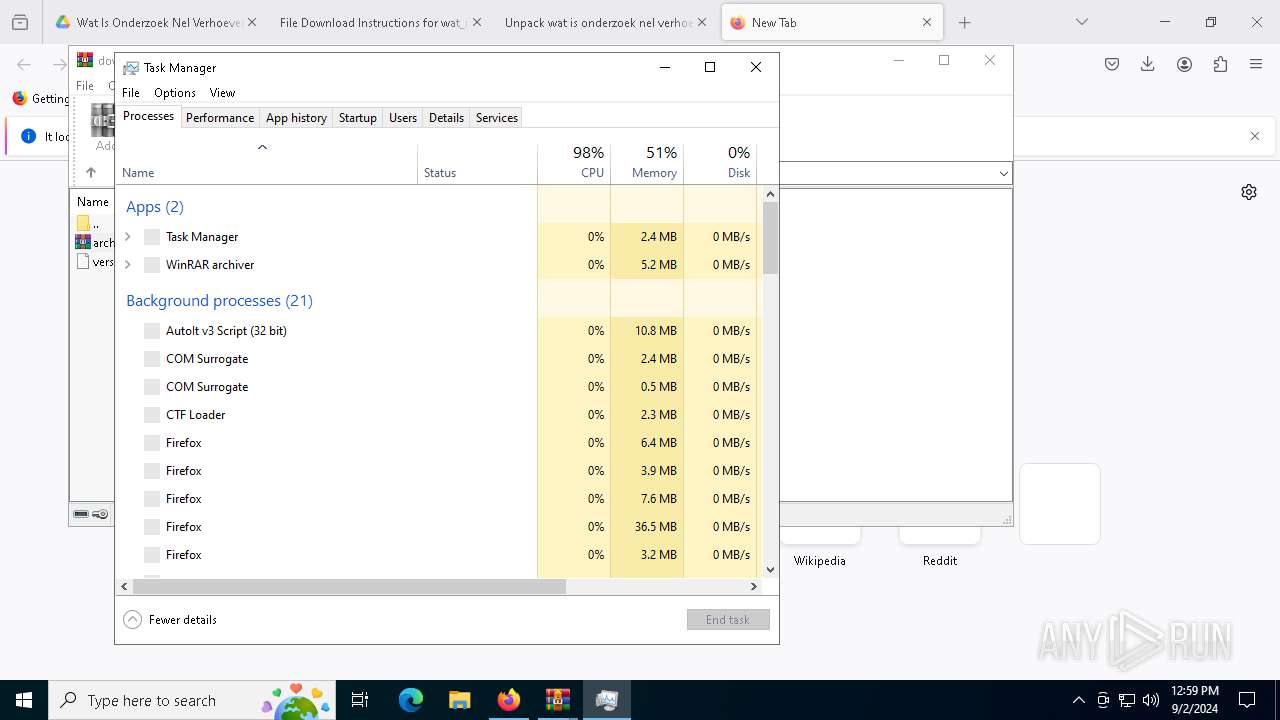
Manual execution by a user
- msiexec.exe (PID: 7796)
- WinRAR.exe (PID: 2480)
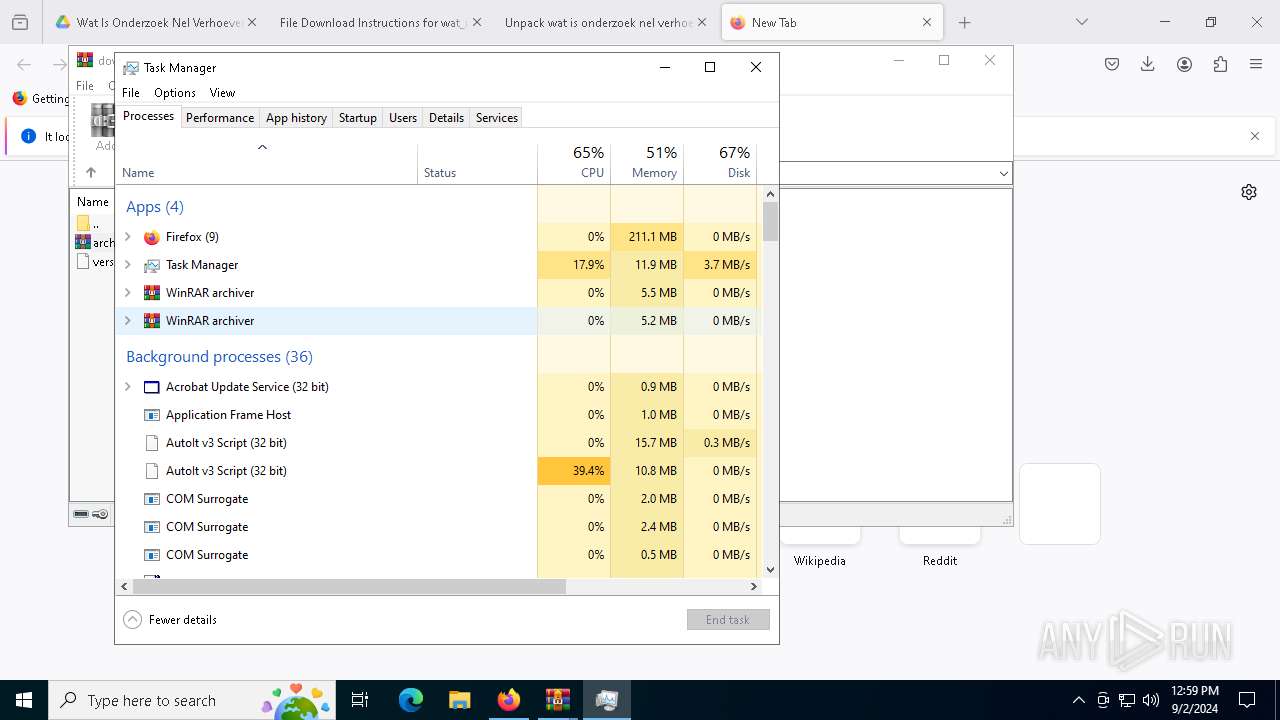
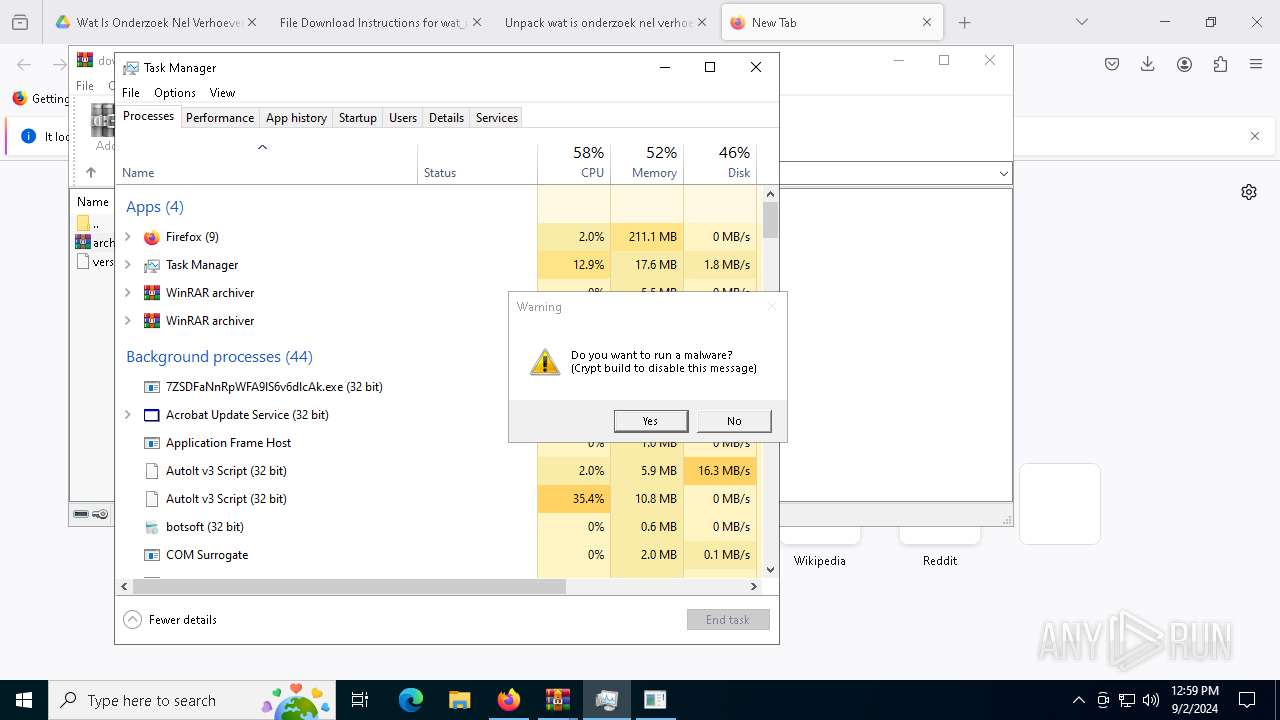
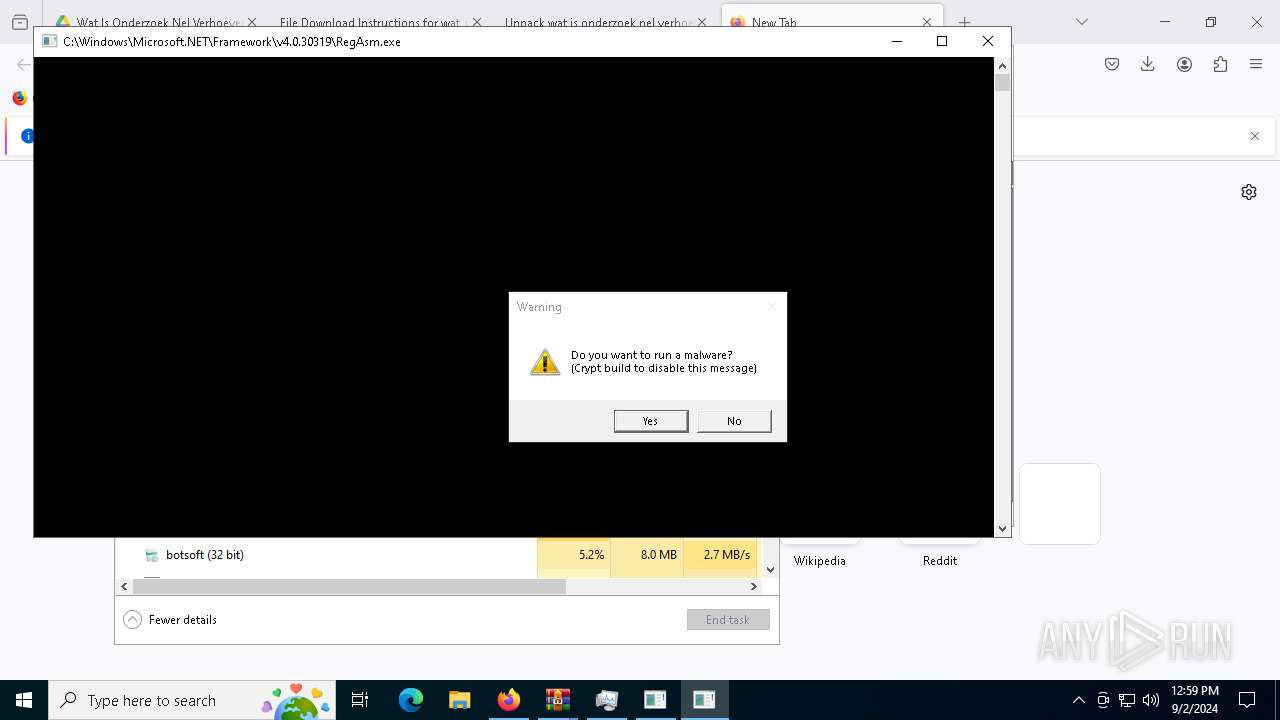
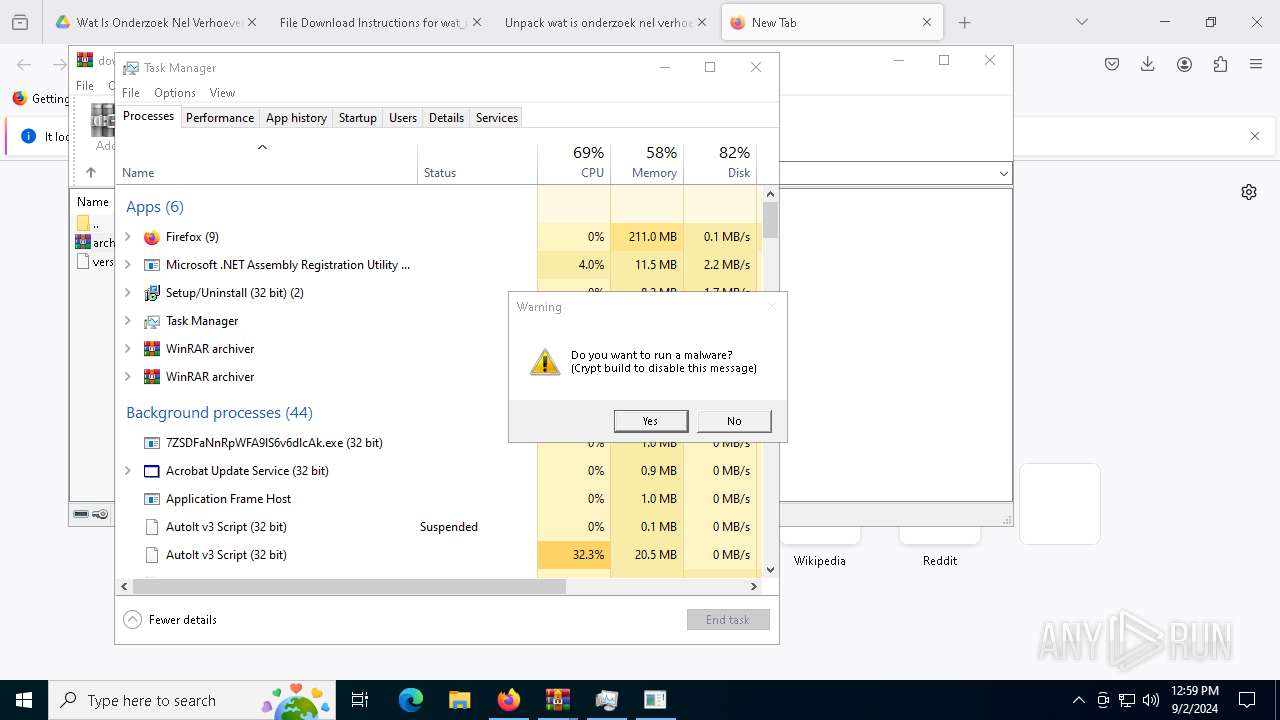
- Quantities.pif (PID: 7296)
- Taskmgr.exe (PID: 7248)
- Taskmgr.exe (PID: 7228)
- Quantities.pif (PID: 6124)
The process uses the downloaded file
- firefox.exe (PID: 1184)
- WinRAR.exe (PID: 2480)
- WinRAR.exe (PID: 7672)
- File.exe (PID: 7716)
- File.exe (PID: 6000)
- Yup1erlzMpQriLXfQvqWA_8g.exe (PID: 4672)
- RegAsm.exe (PID: 7816)
Checks supported languages
- msiexec.exe (PID: 7884)
- File.exe (PID: 7716)
- File.exe (PID: 6000)
- Quantities.pif (PID: 5140)
- Quantities.pif (PID: 4024)
- Quantities.pif (PID: 7296)
- Yup1erlzMpQriLXfQvqWA_8g.exe (PID: 2820)
- 7ZSDFaNnRpWFA9lS6v6dlcAk.exe (PID: 4708)
- wdQecB0wVN0lwhaZwzoLuAti.exe (PID: 1280)
- G2dX3FvDEyzA7uSCi9dzFYdG.exe (PID: 7880)
- wdQecB0wVN0lwhaZwzoLuAti.tmp (PID: 8012)
- K77Fh1qxOWRMTQJYbZHAixag.exe (PID: 7216)
- 5dkKQp0E5y7di_7LzDaFJLtS.exe (PID: 4524)
- Swc_1X0utb1zSBlRsCIrzgx_.exe (PID: 7080)
- JLqLqfMmASUhMk95b6SsvG1S.exe (PID: 8008)
- DE9UKvU4CPlcYNl6HFiJSfUc.exe (PID: 3112)
- RegAsm.exe (PID: 7816)
- RegAsm.exe (PID: 6532)
- RegAsm.exe (PID: 7292)
- screenrecorderle32.exe (PID: 8152)
- RegAsm.exe (PID: 4448)
- Yup1erlzMpQriLXfQvqWA_8g.exe (PID: 4672)
- Yup1erlzMpQriLXfQvqWA_8g.exe (PID: 4524)
- Yup1erlzMpQriLXfQvqWA_8g.exe (PID: 8092)
- Quantities.pif (PID: 6124)
- etzpikspwykg.exe (PID: 5144)
- M2_wXb0vXnuBxHOr7rwwWhEP.exe (PID: 6684)
- 9C9ogY2eDNKbFHQ9UzSObnJr.exe (PID: 5000)
- UIXzMT1oWhYdCWSZ4TivU04j.exe (PID: 7784)
- UIXzMT1oWhYdCWSZ4TivU04j.tmp (PID: 6204)
- jthGm5YV5Nf87Cw5CQlRu4Iq.exe (PID: 6312)
- 6qYAYXLeu5ehaFkjiF_q8dbg.exe (PID: 1712)
- jT1wfVFaZRJ86jCrX2kWQgZR.exe (PID: 4284)
Reads the computer name
- msiexec.exe (PID: 7884)
- File.exe (PID: 7716)
- Quantities.pif (PID: 5140)
- File.exe (PID: 6000)
- Quantities.pif (PID: 7296)
- Quantities.pif (PID: 4024)
- wdQecB0wVN0lwhaZwzoLuAti.tmp (PID: 8012)
- Yup1erlzMpQriLXfQvqWA_8g.exe (PID: 2820)
- JLqLqfMmASUhMk95b6SsvG1S.exe (PID: 8008)
- 5dkKQp0E5y7di_7LzDaFJLtS.exe (PID: 4524)
- DE9UKvU4CPlcYNl6HFiJSfUc.exe (PID: 3112)
- Swc_1X0utb1zSBlRsCIrzgx_.exe (PID: 7080)
- K77Fh1qxOWRMTQJYbZHAixag.exe (PID: 7216)
- RegAsm.exe (PID: 6532)
- RegAsm.exe (PID: 7292)
- RegAsm.exe (PID: 7816)
- screenrecorderle32.exe (PID: 8152)
- Yup1erlzMpQriLXfQvqWA_8g.exe (PID: 4672)
- Yup1erlzMpQriLXfQvqWA_8g.exe (PID: 4524)
- Yup1erlzMpQriLXfQvqWA_8g.exe (PID: 8092)
- Quantities.pif (PID: 6124)
- UIXzMT1oWhYdCWSZ4TivU04j.tmp (PID: 6204)
- M2_wXb0vXnuBxHOr7rwwWhEP.exe (PID: 6684)
Creates a software uninstall entry
- msiexec.exe (PID: 7884)
- wdQecB0wVN0lwhaZwzoLuAti.tmp (PID: 8012)
Create files in a temporary directory
- File.exe (PID: 7716)
- File.exe (PID: 6000)
- wdQecB0wVN0lwhaZwzoLuAti.exe (PID: 1280)
- wdQecB0wVN0lwhaZwzoLuAti.tmp (PID: 8012)
- RegAsm.exe (PID: 4448)
- Yup1erlzMpQriLXfQvqWA_8g.exe (PID: 8092)
- etzpikspwykg.exe (PID: 5144)
- UIXzMT1oWhYdCWSZ4TivU04j.exe (PID: 7784)
- UIXzMT1oWhYdCWSZ4TivU04j.tmp (PID: 6204)
Process checks computer location settings
- File.exe (PID: 7716)
- File.exe (PID: 6000)
- Quantities.pif (PID: 7296)
- Yup1erlzMpQriLXfQvqWA_8g.exe (PID: 4672)
- Quantities.pif (PID: 6124)
- RegAsm.exe (PID: 7816)
Reads the software policy settings
- slui.exe (PID: 6172)
- Quantities.pif (PID: 7296)
- RegAsm.exe (PID: 7292)
- Quantities.pif (PID: 6124)
- slui.exe (PID: 2640)
Reads mouse settings
- Quantities.pif (PID: 5140)
- Quantities.pif (PID: 4024)
Checks proxy server information
- Quantities.pif (PID: 7296)
- K77Fh1qxOWRMTQJYbZHAixag.exe (PID: 7216)
- Quantities.pif (PID: 6124)
- slui.exe (PID: 2640)
- RegAsm.exe (PID: 7816)
Creates files or folders in the user directory
- Quantities.pif (PID: 7296)
- wdQecB0wVN0lwhaZwzoLuAti.tmp (PID: 8012)
- K77Fh1qxOWRMTQJYbZHAixag.exe (PID: 7216)
- Yup1erlzMpQriLXfQvqWA_8g.exe (PID: 8092)
- RegAsm.exe (PID: 6532)
- Quantities.pif (PID: 6124)
- G2dX3FvDEyzA7uSCi9dzFYdG.exe (PID: 7880)
- RegAsm.exe (PID: 7816)
Reads security settings of Internet Explorer
- Taskmgr.exe (PID: 7228)
Reads the machine GUID from the registry
- Quantities.pif (PID: 7296)
- Yup1erlzMpQriLXfQvqWA_8g.exe (PID: 2820)
- RegAsm.exe (PID: 7292)
- RegAsm.exe (PID: 6532)
- Yup1erlzMpQriLXfQvqWA_8g.exe (PID: 4524)
- Quantities.pif (PID: 6124)
Creates files in the program directory
- screenrecorderle32.exe (PID: 8152)
- Yup1erlzMpQriLXfQvqWA_8g.exe (PID: 8092)
- K77Fh1qxOWRMTQJYbZHAixag.exe (PID: 7216)
- RegAsm.exe (PID: 7816)
Reads product name
- K77Fh1qxOWRMTQJYbZHAixag.exe (PID: 7216)
- RegAsm.exe (PID: 7816)
Reads CPU info
- K77Fh1qxOWRMTQJYbZHAixag.exe (PID: 7216)
- RegAsm.exe (PID: 7816)
Reads Environment values
- K77Fh1qxOWRMTQJYbZHAixag.exe (PID: 7216)
- RegAsm.exe (PID: 7292)
- RegAsm.exe (PID: 6532)
- RegAsm.exe (PID: 7816)
Themida protector has been detected
- K77Fh1qxOWRMTQJYbZHAixag.exe (PID: 7216)
.NET Reactor protector has been detected
- Yup1erlzMpQriLXfQvqWA_8g.exe (PID: 8092)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Vidar
(PID) Process(4448) RegAsm.exe
C2https://t.me/iyigunl
URLhttps://steamcommunity.com/profiles/76561199761128941
Strings (239)INSERT_KEY_HERE
lstrcpyA
GetEnvironmentVariableA
GdipSaveImageToStream
History
runas
ssfn*
GetProcAddress
lstrcatA
OpenEventA
CloseHandle
Sleep
GetUserDefaultLangID
VirtualAllocExNuma
VirtualFree
GetSystemInfo
HeapAlloc
GetComputerNameA
GetProcessHeap
GetCurrentProcess
lstrlenA
ExitProcess
GlobalMemoryStatusEx
GetSystemTime
SystemTimeToFileTime
gdi32.dll
user32.dll
crypt32.dll
ntdll.dll
CreateDCA
GetDeviceCaps
ReleaseDC
CryptStringToBinaryA
sscanf
NtQueryInformationProcess
HAL9TH
JohnDoe
DISPLAY
%hu/%hu/%hu
GetFileAttributesA
GlobalLock
GlobalSize
CreateToolhelp32Snapshot
IsWow64Process
Process32Next
GetLocalTime
GetTimeZoneInformation
GetSystemPowerStatus
GetVolumeInformationA
Process32First
GetLocaleInfoA
GetUserDefaultLocaleName
GetModuleFileNameA
FindNextFileA
SetEnvironmentVariableA
LocalAlloc
GetFileSizeEx
SetFilePointer
FindFirstFileA
VirtualProtect
GetLogicalProcessorInformationEx
GetLastError
MultiByteToWideChar
GlobalFree
WideCharToMultiByte
TerminateProcess
GetCurrentProcessId
rstrtmgr.dll
CreateCompatibleBitmap
SelectObject
BitBlt
DeleteObject
CreateCompatibleDC
GdipGetImageEncodersSize
GdipGetImageEncoders
GdipCreateBitmapFromHBITMA
GdiplusStartup
GdiplusShutdown
GdipDisposeImage
GetHGlobalFromStream
CreateStreamOnHGlobal
CoUninitialize
CoInitialize
CoCreateInstance
BCryptGenerateSymmetricKey
BCryptCloseAlgorithmProvider
BCryptDecrypt
BCryptSetProperty
BCryptDestroyKey
BCryptOpenAlgorithmProvider
GetWindowRect
GetDesktopWindow
GetDC
EnumDisplayDevicesA
GetKeyboardLayoutList
CharToOemW
RegQueryValueExA
RegEnumKeyExA
RegOpenKeyExA
RegEnumValueA
CryptBinaryToStringA
CryptUnprotectData
SHGetFolderPathA
InternetOpenUrlA
InternetConnectA
InternetCloseHandle
InternetOpenA
HttpSendRequestA
HttpOpenRequestA
InternetReadFile
InternetCrackUrlA
StrStrA
PathMatchSpecA
GetModuleFileNameExA
RmStartSession
RmRegisterResources
RmEndSession
sqlite3_open
sqlite3_prepare_v2
sqlite3_step
sqlite3_column_text
sqlite3_finalize
sqlite3_close
sqlite3_column_bytes
sqlite3_column_blob
encrypted_key
PATH
C:\ProgramData\nss3.dll
NSS_Shutdown
PK11_GetInternalKeySlot
PK11_FreeSlot
PK11_Authenticate
PK11SDR_Decrypt
C:\ProgramData\
SELECT origin_url, username_value, password_value FROM logins
Soft:
Host:
Login:
Password:
Opera
OperaGX
Network
Cookies
.txt
TRUE
FALSE
SELECT name, value FROM autofill
History
SELECT url FROM urls LIMIT 1000
CC
SELECT name_on_card, expiration_month, expiration_year, card_number_encrypted FROM credit_cards
Name:
Month:
Year:
Card:
Cookies
Login Data
formSubmitURL
usernameField
encryptedUsername
encryptedPassword
guid
SELECT host, isHttpOnly, path, isSecure, expiry, name, value FROM moz_cookies
SELECT fieldname, value FROM moz_formhistory
SELECT url FROM moz_places LIMIT 1000
cookies.sqlite
formhistory.sqlite
places.sqlite
Plugins
Local Extension Settings
Sync Extension Settings
Opera Stable
Opera GX Stable
CURRENT
chrome-extension_
_0.indexeddb.leveldb
profiles.ini
chrome
opera
firefox
Wallets
%08lX%04lX%lu
SOFTWARE\Microsoft\Windows NT\CurrentVersion
x64
%d/%d/%d %d:%d:%d
HARDWARE\DESCRIPTION\System\CentralProcessor\0
ProcessorNameString
SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall
DisplayVersion
msvcp140.dll
softokn3.dll
vcruntime140.dll
\Temp\
.exe
open
%LOCALAPPDATA%
%USERPROFILE%
%PROGRAMFILES%
%PROGRAMFILES_86%
*.lnk
Files
\Local Storage\leveldb\CURRENT
\Local Storage\leveldb
\Telegram Desktop\
D877F783D5D3EF8C*
map*
A7FDF864FBC10B77*
A92DAA6EA6F891F2*
F8806DD0C461824F*
Tox
*.tox
*.ini
Software\Microsoft\Windows NT\CurrentVersion\Windows Messaging Subsystem\Profiles\Outlook\9375
Software\Microsoft\Office\13.0\Outlook\Profiles\Outlook\9375CFF0413111d3B88A00104B2A6676\
Software\Microsoft\Office\14.0\Outlook\Profiles\Outlook\9375CFF0413111d3B88A00104B2A6676\
Software\Microsoft\Office.0\Outlook\Profiles\Outlook\9375CFF0413111d3B88A00104B2A6676\
Software\Microsoft\Windows Messaging Subsystem\Profiles\9375CFF0413111d3B88A00104B2A6676\
\Outlook\accounts.txt
Pidgin
accounts.xml
token:
Software\Valve\Steam
config.vdf
DialogConfig.vdf
DialogConfigOverlay*.vdf
libraryfolders.vdf
loginusers.vdf
\Steam\
\Discord\tokens.txt
/c timeout /t 5 & del /f /q "
" & del "C:\ProgramData\*.dll"" & exit
C:\Windows\system32\cmd.exe
Content-Type: multipart/form-data; boundary=----
Content-Disposition: form-data; name="
build
token
message
ABCDEFGHIJKLMNOPQRSTUVWXYZ1234567890
screenshot.jpg
Stealc
(PID) Process(7816) RegAsm.exe
C246.8.231.109
Strings (353)INSERT_KEY_HERE
09
09
20
24
GetProcAddress
LoadLibraryA
lstrcatA
OpenEventA
CreateEventA
CloseHandle
Sleep
GetUserDefaultLangID
VirtualAllocExNuma
VirtualFree
GetSystemInfo
VirtualAlloc
HeapAlloc
GetComputerNameA
lstrcpyA
GetProcessHeap
GetCurrentProcess
lstrlenA
ExitProcess
GlobalMemoryStatusEx
GetSystemTime
SystemTimeToFileTime
advapi32.dll
gdi32.dll
user32.dll
crypt32.dll
ntdll.dll
GetUserNameA
CreateDCA
GetDeviceCaps
ReleaseDC
CryptStringToBinaryA
sscanf
VMwareVMware
HAL9TH
JohnDoe
DISPLAY
%hu/%hu/%hu
http://46.8.231.109
george
|
/c4754d4f680ead72.php
/1309cdeb8f4c8736/
default
GetEnvironmentVariableA
GetFileAttributesA
GlobalLock
HeapFree
GetFileSize
GlobalSize
CreateToolhelp32Snapshot
IsWow64Process
Process32Next
GetLocalTime
FreeLibrary
GetTimeZoneInformation
GetSystemPowerStatus
GetVolumeInformationA
GetWindowsDirectoryA
Process32First
GetLocaleInfoA
GetUserDefaultLocaleName
GetModuleFileNameA
DeleteFileA
FindNextFileA
LocalFree
FindClose
SetEnvironmentVariableA
LocalAlloc
GetFileSizeEx
ReadFile
SetFilePointer
WriteFile
CreateFileA
FindFirstFileA
CopyFileA
VirtualProtect
GetLogicalProcessorInformationEx
GetLastError
lstrcpynA
MultiByteToWideChar
GlobalFree
WideCharToMultiByte
GlobalAlloc
OpenProcess
TerminateProcess
GetCurrentProcessId
gdiplus.dll
ole32.dll
bcrypt.dll
wininet.dll
shlwapi.dll
shell32.dll
psapi.dll
rstrtmgr.dll
CreateCompatibleBitmap
SelectObject
BitBlt
DeleteObject
CreateCompatibleDC
GdipGetImageEncodersSize
GdipGetImageEncoders
GdipCreateBitmapFromHBITMAP
GdiplusStartup
GdiplusShutdown
GdipSaveImageToStream
GdipDisposeImage
GdipFree
GetHGlobalFromStream
CreateStreamOnHGlobal
CoUninitialize
CoInitialize
CoCreateInstance
BCryptGenerateSymmetricKey
BCryptCloseAlgorithmProvider
BCryptDecrypt
BCryptSetProperty
BCryptDestroyKey
BCryptOpenAlgorithmProvider
GetWindowRect
GetDesktopWindow
GetDC
CloseWindow
wsprintfA
EnumDisplayDevicesA
GetKeyboardLayoutList
CharToOemW
wsprintfW
RegQueryValueExA
RegEnumKeyExA
RegOpenKeyExA
RegCloseKey
RegEnumValueA
CryptBinaryToStringA
CryptUnprotectData
SHGetFolderPathA
ShellExecuteExA
InternetOpenUrlA
InternetConnectA
InternetCloseHandle
InternetOpenA
HttpSendRequestA
HttpOpenRequestA
InternetReadFile
InternetCrackUrlA
StrCmpCA
StrStrA
StrCmpCW
PathMatchSpecA
GetModuleFileNameExA
RmStartSession
RmRegisterResources
RmGetList
RmEndSession
sqlite3_open
sqlite3_prepare_v2
sqlite3_step
sqlite3_column_text
sqlite3_finalize
sqlite3_close
sqlite3_column_bytes
sqlite3_column_blob
encrypted_key
PATH
C:\ProgramData\nss3.dll
NSS_Init
NSS_Shutdown
PK11_GetInternalKeySlot
PK11_FreeSlot
PK11_Authenticate
PK11SDR_Decrypt
C:\ProgramData\
SELECT origin_url, username_value, password_value FROM logins
browser:
profile:
url:
login:
password:
Opera
OperaGX
Network
cookies
.txt
SELECT HOST_KEY, is_httponly, path, is_secure, (expires_utc/1000000)-11644480800, name, encrypted_value from cookies
TRUE
FALSE
autofill
SELECT name, value FROM autofill
history
SELECT url FROM urls LIMIT 1000
cc
SELECT name_on_card, expiration_month, expiration_year, card_number_encrypted FROM credit_cards
name:
month:
year:
card:
Cookies
Login Data
Web Data
History
logins.json
formSubmitURL
usernameField
encryptedUsername
encryptedPassword
guid
SELECT host, isHttpOnly, path, isSecure, expiry, name, value FROM moz_cookies
SELECT fieldname, value FROM moz_formhistory
SELECT url FROM moz_places LIMIT 1000
cookies.sqlite
formhistory.sqlite
places.sqlite
plugins
Local Extension Settings
Sync Extension Settings
IndexedDB
Opera Stable
Opera GX Stable
CURRENT
chrome-extension_
_0.indexeddb.leveldb
Local State
profiles.ini
chrome
opera
firefox
wallets
%08lX%04lX%lu
SOFTWARE\Microsoft\Windows NT\CurrentVersion
ProductName
x32
x64
%d/%d/%d %d:%d:%d
HARDWARE\DESCRIPTION\System\CentralProcessor\0
ProcessorNameString
SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall
DisplayName
DisplayVersion
Network Info:
- IP: IP?
- Country: ISO?
System Summary:
- HWID:
- OS:
- Architecture:
- UserName:
- Computer Name:
- Local Time:
- UTC:
- Language:
- Keyboards:
- Laptop:
- Running Path:
- CPU:
- Threads:
- Cores:
- RAM:
- Display Resolution:
- GPU:
User Agents:
Installed Apps:
All Users:
Current User:
Process List:
system_info.txt
freebl3.dll
mozglue.dll
msvcp140.dll
nss3.dll
softokn3.dll
vcruntime140.dll
\Temp\
.exe
runas
open
/c start
%DESKTOP%
%APPDATA%
%LOCALAPPDATA%
%USERPROFILE%
%DOCUMENTS%
%PROGRAMFILES%
%PROGRAMFILES_86%
%RECENT%
*.lnk
files
\discord\
\Local Storage\leveldb\CURRENT
\Local Storage\leveldb
\Telegram Desktop\
key_datas
D877F783D5D3EF8C*
map*
A7FDF864FBC10B77*
A92DAA6EA6F891F2*
F8806DD0C461824F*
Telegram
Tox
*.tox
*.ini
Password
Software\Microsoft\Windows NT\CurrentVersion\Windows Messaging Subsystem\Profiles\Outlook\9375CFF0413111d3B88A00104B2A6676\
Software\Microsoft\Office\13.0\Outlook\Profiles\Outlook\9375CFF0413111d3B88A00104B2A6676\
Software\Microsoft\Office\14.0\Outlook\Profiles\Outlook\9375CFF0413111d3B88A00104B2A6676\
Software\Microsoft\Office\15.0\Outlook\Profiles\Outlook\9375CFF0413111d3B88A00104B2A6676\
Software\Microsoft\Office\16.0\Outlook\Profiles\Outlook\9375CFF0413111d3B88A00104B2A6676\
oftware\Microsoft\Windows Messaging Subsystem\Profiles\9375CFF0413111d3B88A00104B2A6676\
00000001
00000002
00000003
00000004
\Outlook\accounts.txt
Pidgin
\.purple\
accounts.xml
dQw4w9WgXcQ
token:
Software\Valve\Steam
SteamPath
\config\
ssfn*
config.vdf
DialogConfig.vdf
DialogConfigOverlay*.vdf
libraryfolders.vdf
loginusers.vdf
\Steam\
sqlite3.dll
browsers
done
soft
\Discord\tokens.txt
/c timeout /t 5 & del /f /q "
" & del "C:\ProgramData\*.dll"" & exit
C:\Windows\system32\cmd.exe
https
Content-Type: multipart/form-data; boundary=----
POST
HTTP/1.1
Content-Disposition: form-data; name="
hwid
build
token
file_name
file
message
ABCDEFGHIJKLMNOPQRSTUVWXYZ1234567890
screenshot.jpg
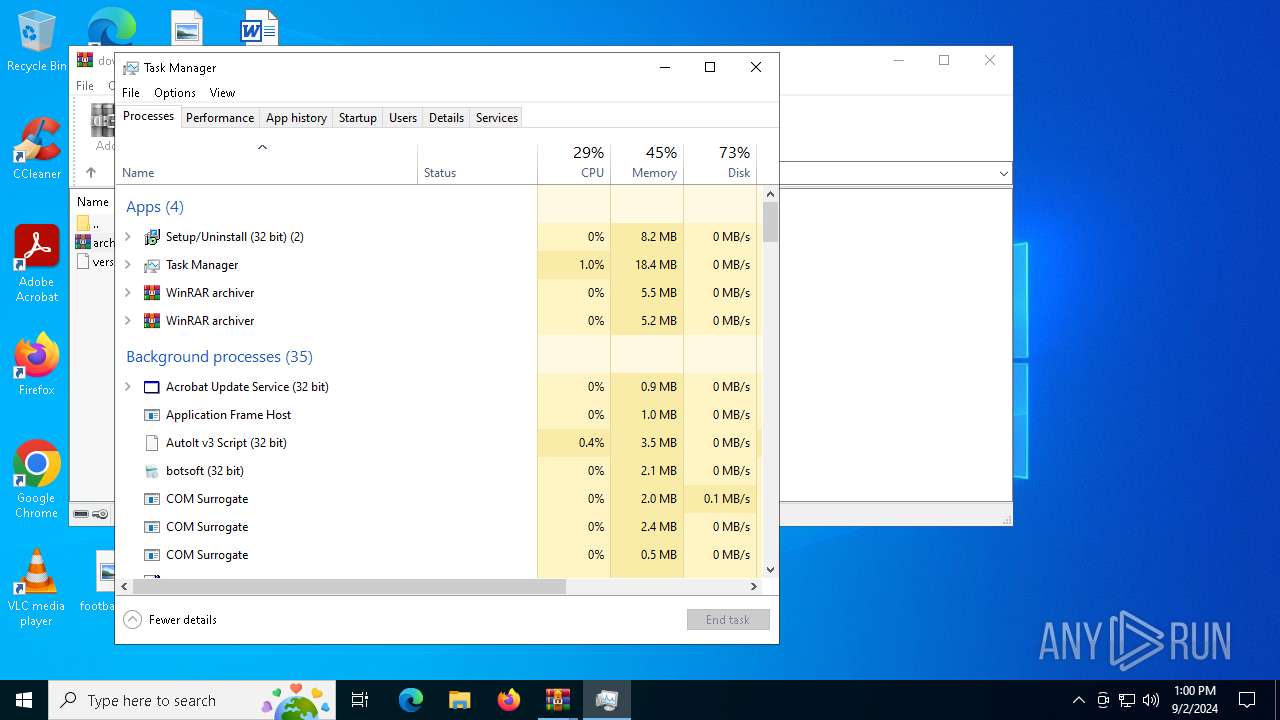
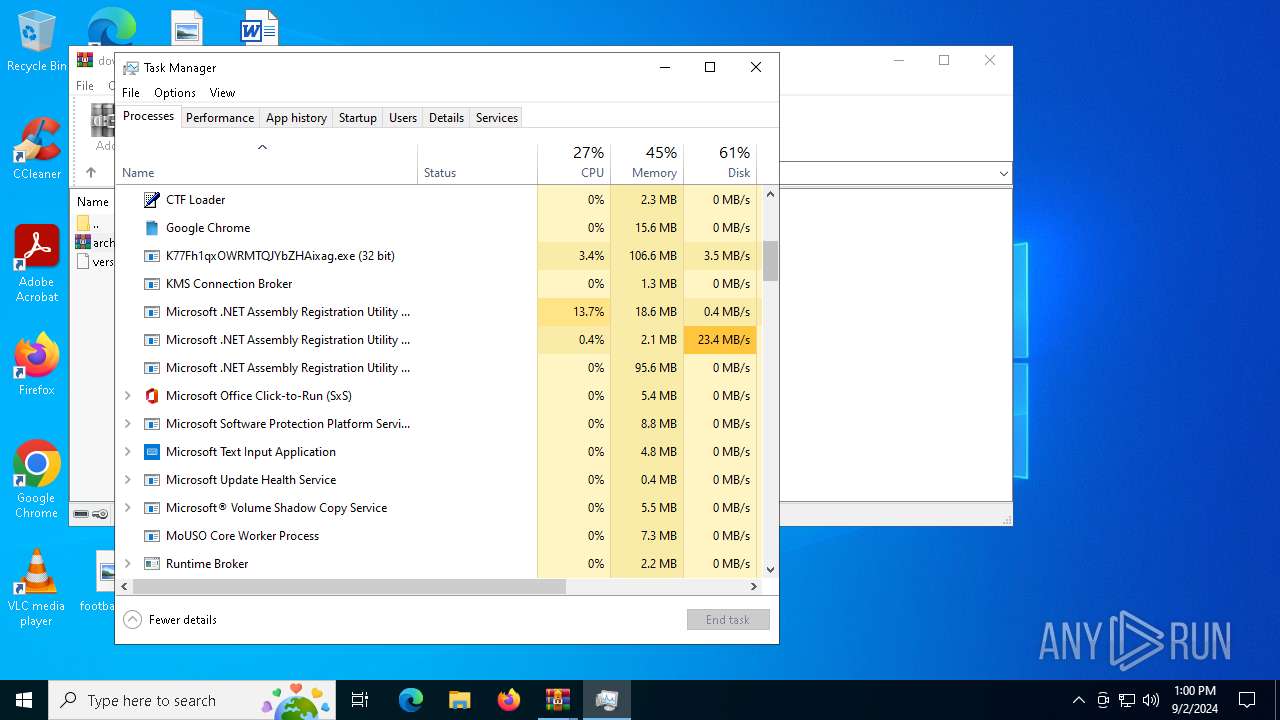
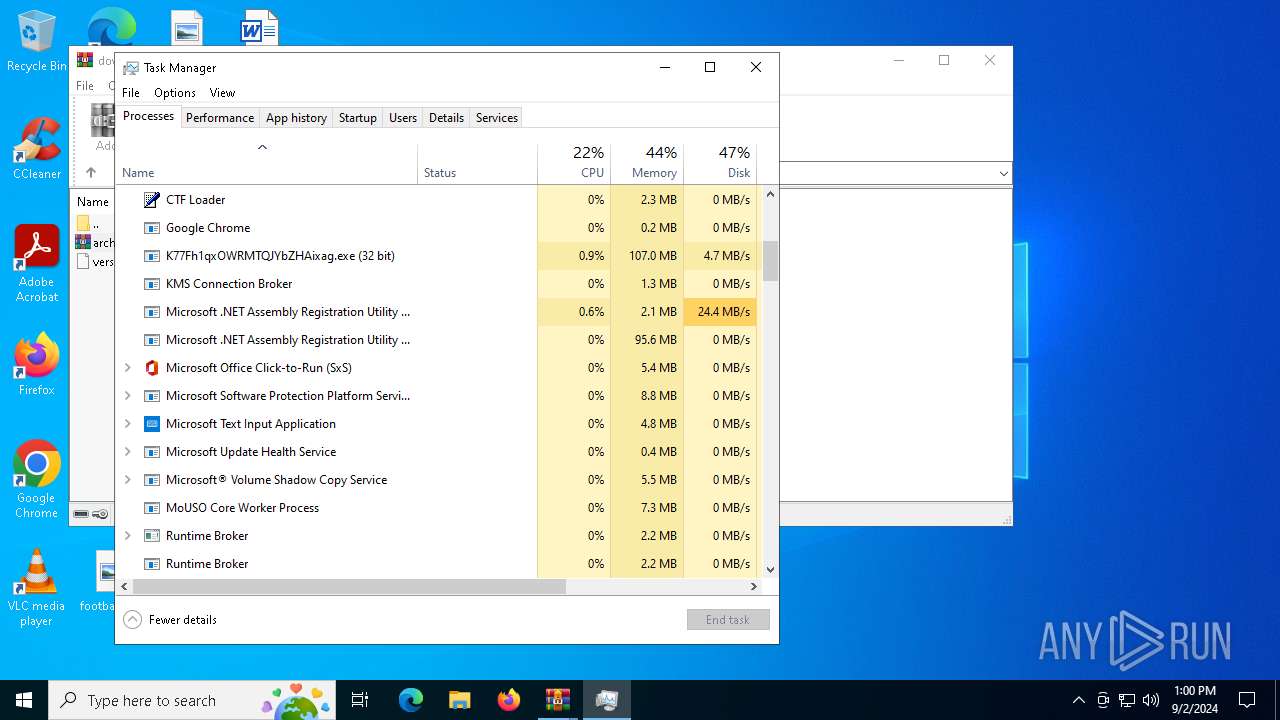
Total processes
278
Monitored processes
138
Malicious processes
24
Suspicious processes
5
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 736 | tasklist | C:\Windows\SysWOW64\tasklist.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Lists the current running tasks Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 892 | findstr /I "avastui avgui bdservicehost nswscsvc sophoshealth" | C:\Windows\SysWOW64\findstr.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Find String (QGREP) Utility Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 940 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | powercfg.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1184 | "C:\Program Files\Mozilla Firefox\firefox.exe" https://drive.google.com/file/d/1XUgVOUKxJSdgHLqqclmh7aEjB9-YfO2Y/edit | C:\Program Files\Mozilla Firefox\firefox.exe | firefox.exe | ||||||||||||
User: admin Company: Mozilla Corporation Integrity Level: MEDIUM Description: Firefox Exit code: 4294967295 Version: 123.0 Modules
| |||||||||||||||
| 1280 | C:\Users\admin\Documents\iofolko5\wdQecB0wVN0lwhaZwzoLuAti.exe | C:\Users\admin\Documents\iofolko5\wdQecB0wVN0lwhaZwzoLuAti.exe | Quantities.pif | ||||||||||||
User: admin Company: Integrity Level: MEDIUM Description: Screen Recorder Lite Edition Setup Version: Modules
| |||||||||||||||
| 1360 | svchost.exe | C:\Windows\System32\svchost.exe | etzpikspwykg.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Host Process for Windows Services Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1436 | "C:\Program Files\Mozilla Firefox\firefox.exe" -contentproc --channel=7084 -parentBuildID 20240213221259 -prefsHandle 6964 -prefMapHandle 6976 -prefsLen 34713 -prefMapSize 244343 -appDir "C:\Program Files\Mozilla Firefox\browser" - {ae911d89-e750-4121-b42d-6e0bc3565ea2} 1184 "\\.\pipe\gecko-crash-server-pipe.1184" 223d72f8810 rdd | C:\Program Files\Mozilla Firefox\firefox.exe | — | firefox.exe | |||||||||||
User: admin Company: Mozilla Corporation Integrity Level: LOW Description: Firefox Exit code: 4294967295 Version: 123.0 Modules
| |||||||||||||||
| 1556 | "C:\Users\admin\Documents\iofolko5\M2_wXb0vXnuBxHOr7rwwWhEP.exe" | C:\Users\admin\Documents\iofolko5\M2_wXb0vXnuBxHOr7rwwWhEP.exe | — | M2_wXb0vXnuBxHOr7rwwWhEP.exe | |||||||||||
User: admin Company: Hr9NiFu08oD2 Integrity Level: MEDIUM Description: botsoft Exit code: 0 Version: 4.8.3.9 | |||||||||||||||
| 1692 | C:\WINDOWS\system32\conhost.exe | C:\Windows\System32\conhost.exe | — | etzpikspwykg.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1712 | C:\Users\admin\Documents\iofolko5\6qYAYXLeu5ehaFkjiF_q8dbg.exe | C:\Users\admin\Documents\iofolko5\6qYAYXLeu5ehaFkjiF_q8dbg.exe | — | Quantities.pif | |||||||||||
User: admin Integrity Level: MEDIUM Modules
| |||||||||||||||
Total events
80 939
Read events
80 409
Write events
503
Delete events
27
Modification events
| (PID) Process: | (6960) firefox.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Mozilla\Firefox\Launcher |
| Operation: | write | Name: | C:\Program Files\Mozilla Firefox\firefox.exe|Launcher |
Value: B75EC70401000000 | |||
| (PID) Process: | (1184) firefox.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Mozilla\Firefox\Launcher |
| Operation: | write | Name: | C:\Program Files\Mozilla Firefox\firefox.exe|Browser |
Value: 15DFC80401000000 | |||
| (PID) Process: | (1184) firefox.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Mozilla\Firefox\PreXULSkeletonUISettings |
| Operation: | write | Name: | C:\Program Files\Mozilla Firefox\firefox.exe|Progress |
Value: 0 | |||
| (PID) Process: | (1184) firefox.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Mozilla\Firefox\PreXULSkeletonUISettings |
| Operation: | write | Name: | C:\Program Files\Mozilla Firefox\firefox.exe|Progress |
Value: 1 | |||
| (PID) Process: | (1184) firefox.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Mozilla\Firefox\Installer\308046B0AF4A39CB |
| Operation: | delete value | Name: | installer.taskbarpin.win10.enabled |
Value: | |||
| (PID) Process: | (1184) firefox.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Mozilla\Firefox\Launcher |
| Operation: | write | Name: | C:\Program Files\Mozilla Firefox\firefox.exe|Telemetry |
Value: 0 | |||
| (PID) Process: | (1184) firefox.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Mozilla\Firefox\DllPrefetchExperiment |
| Operation: | write | Name: | C:\Program Files\Mozilla Firefox\firefox.exe |
Value: 0 | |||
| (PID) Process: | (1184) firefox.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Mozilla\Firefox\PreXULSkeletonUISettings |
| Operation: | write | Name: | C:\Program Files\Mozilla Firefox\firefox.exe|Theme |
Value: 1 | |||
| (PID) Process: | (1184) firefox.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Mozilla\Firefox\PreXULSkeletonUISettings |
| Operation: | write | Name: | C:\Program Files\Mozilla Firefox\firefox.exe|Enabled |
Value: 1 | |||
| (PID) Process: | (1184) firefox.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Mozilla\Firefox\Default Browser Agent |
| Operation: | write | Name: | C:\Program Files\Mozilla Firefox|DisableTelemetry |
Value: 1 | |||
Executable files
99
Suspicious files
260
Text files
170
Unknown types
37
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 1184 | firefox.exe | C:\Users\admin\AppData\Local\Mozilla\Firefox\Profiles\9kie7cg6.default-release\startupCache\urlCache-current.bin | binary | |
MD5:297E88D7CEB26E549254EC875649F4EB | SHA256:8B75D4FB1845BAA06122888D11F6B65E6A36B140C54A72CC13DF390FD7C95702 | |||
| 1184 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\9kie7cg6.default-release\storage\permanent\chrome\idb\2823318777ntouromlalnodry--naod.sqlite-shm | binary | |
MD5:B7C14EC6110FA820CA6B65F5AEC85911 | SHA256:FD4C9FDA9CD3F9AE7C962B0DDF37232294D55580E1AA165AA06129B8549389EB | |||
| 1184 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\9kie7cg6.default-release\storage\permanent\chrome\idb\3870112724rsegmnoittet-es.sqlite-shm | binary | |
MD5:B7C14EC6110FA820CA6B65F5AEC85911 | SHA256:FD4C9FDA9CD3F9AE7C962B0DDF37232294D55580E1AA165AA06129B8549389EB | |||
| 1184 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\9kie7cg6.default-release\storage\permanent\chrome\idb\3870112724rsegmnoittet-es.sqlite | — | |
MD5:— | SHA256:— | |||
| 1184 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\9kie7cg6.default-release\sessionCheckpoints.json.tmp | binary | |
MD5:EA8B62857DFDBD3D0BE7D7E4A954EC9A | SHA256:792955295AE9C382986222C6731C5870BD0E921E7F7E34CC4615F5CD67F225DA | |||
| 1184 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\9kie7cg6.default-release\cookies.sqlite-shm | binary | |
MD5:B7C14EC6110FA820CA6B65F5AEC85911 | SHA256:FD4C9FDA9CD3F9AE7C962B0DDF37232294D55580E1AA165AA06129B8549389EB | |||
| 1184 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\9kie7cg6.default-release\prefs-1.js | text | |
MD5:513682DCFD8B2A20FE88F3FDDD293073 | SHA256:8923B088CB62E836559E88F7379CD376CD34AD8943080F534A51DA8AB7786E42 | |||
| 1184 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\9kie7cg6.default-release\sessionCheckpoints.json | binary | |
MD5:EA8B62857DFDBD3D0BE7D7E4A954EC9A | SHA256:792955295AE9C382986222C6731C5870BD0E921E7F7E34CC4615F5CD67F225DA | |||
| 1184 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\9kie7cg6.default-release\storage\permanent\chrome\idb\3561288849sdhlie.sqlite-shm | binary | |
MD5:B7C14EC6110FA820CA6B65F5AEC85911 | SHA256:FD4C9FDA9CD3F9AE7C962B0DDF37232294D55580E1AA165AA06129B8549389EB | |||
| 1184 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\9kie7cg6.default-release\SiteSecurityServiceState.bin | binary | |
MD5:7826EB89504CCEA360EE9F43F723B1D1 | SHA256:72ED85BA3E6C41013544A122D7F191EEBD12EDF14AECFBD393F7623247772B7B | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
145
TCP/UDP connections
191
DNS requests
245
Threats
181
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
1184 | firefox.exe | POST | 200 | 2.16.202.115:80 | http://r10.o.lencr.org/ | unknown | — | — | unknown |
1184 | firefox.exe | POST | 200 | 142.250.181.227:80 | http://o.pki.goog/wr2 | unknown | — | — | unknown |
1184 | firefox.exe | POST | 200 | 142.250.181.227:80 | http://o.pki.goog/wr2 | unknown | — | — | unknown |
1184 | firefox.exe | POST | — | 142.250.181.227:80 | http://o.pki.goog/wr2 | unknown | — | — | unknown |
1184 | firefox.exe | POST | 200 | 142.250.181.227:80 | http://o.pki.goog/wr2 | unknown | — | — | unknown |
1184 | firefox.exe | POST | 200 | 142.250.181.227:80 | http://o.pki.goog/wr2 | unknown | — | — | unknown |
1184 | firefox.exe | POST | 200 | 142.250.181.227:80 | http://o.pki.goog/wr2 | unknown | — | — | unknown |
1184 | firefox.exe | GET | 200 | 34.107.221.82:80 | http://detectportal.firefox.com/canonical.html | unknown | — | — | whitelisted |
1184 | firefox.exe | GET | 200 | 34.107.221.82:80 | http://detectportal.firefox.com/success.txt?ipv4 | unknown | — | — | whitelisted |
1184 | firefox.exe | POST | 200 | 142.250.181.227:80 | http://o.pki.goog/wr2 | unknown | — | — | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
2120 | MoUsoCoreWorker.exe | 20.73.194.208:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
1280 | RUXIMICS.exe | 20.73.194.208:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
6320 | svchost.exe | 20.73.194.208:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
1184 | firefox.exe | 142.250.186.170:443 | safebrowsing.googleapis.com | — | — | whitelisted |
1184 | firefox.exe | 142.250.74.206:443 | drive.google.com | GOOGLE | US | shared |
1184 | firefox.exe | 34.117.188.166:443 | contile.services.mozilla.com | — | — | whitelisted |
1184 | firefox.exe | 34.107.221.82:80 | detectportal.firefox.com | GOOGLE | US | whitelisted |
1184 | firefox.exe | 34.107.243.93:443 | push.services.mozilla.com | — | — | whitelisted |
1184 | firefox.exe | 142.250.181.227:80 | o.pki.goog | GOOGLE | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
google.com |
| whitelisted |
drive.google.com |
| shared |
detectportal.firefox.com |
| whitelisted |
prod.detectportal.prod.cloudops.mozgcp.net |
| whitelisted |
contile.services.mozilla.com |
| whitelisted |
example.org |
| whitelisted |
ipv4only.arpa |
| whitelisted |
spocs.getpocket.com |
| whitelisted |
prod.ads.prod.webservices.mozgcp.net |
| unknown |
o.pki.goog |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2256 | svchost.exe | Not Suspicious Traffic | INFO [ANY.RUN] Requests to a free CDN for open source projects (jsdelivr .net) |
2256 | svchost.exe | Not Suspicious Traffic | INFO [ANY.RUN] jQuery JavaScript Library Code Loaded (code .jquery .com) |
2256 | svchost.exe | Not Suspicious Traffic | INFO [ANY.RUN] Requests to a free CDN for open source projects (jsdelivr .net) |
2256 | svchost.exe | Not Suspicious Traffic | INFO [ANY.RUN] jQuery JavaScript Library Code Loaded (code .jquery .com) |
2256 | svchost.exe | Not Suspicious Traffic | INFO [ANY.RUN] jQuery JavaScript Library Code Loaded (code .jquery .com) |
2256 | svchost.exe | Not Suspicious Traffic | INFO [ANY.RUN] Requests to a free CDN for open source projects (jsdelivr .net) |
2256 | svchost.exe | Not Suspicious Traffic | INFO [ANY.RUN] Cloudflare content delivery network (cdnjs .cloudflare .com) |
2256 | svchost.exe | Not Suspicious Traffic | INFO [ANY.RUN] Cloudflare content delivery network (cdnjs .cloudflare .com) |
2256 | svchost.exe | Not Suspicious Traffic | INFO [ANY.RUN] Cloudflare content delivery network (cdnjs .cloudflare .com) |
5000 | firefox.exe | Misc activity | ET INFO Session Traversal Utilities for NAT (STUN Binding Request On Non-Standard High Port) |
6 ETPRO signatures available at the full report
Process | Message |
|---|---|
K77Fh1qxOWRMTQJYbZHAixag.exe |
%s------------------------------------------------
--- Themida Professional ---
--- (c)2012 Oreans Technologies ---
------------------------------------------------
|
jT1wfVFaZRJ86jCrX2kWQgZR.exe |
%s------------------------------------------------
--- Themida Professional ---
--- (c)2012 Oreans Technologies ---
------------------------------------------------
|