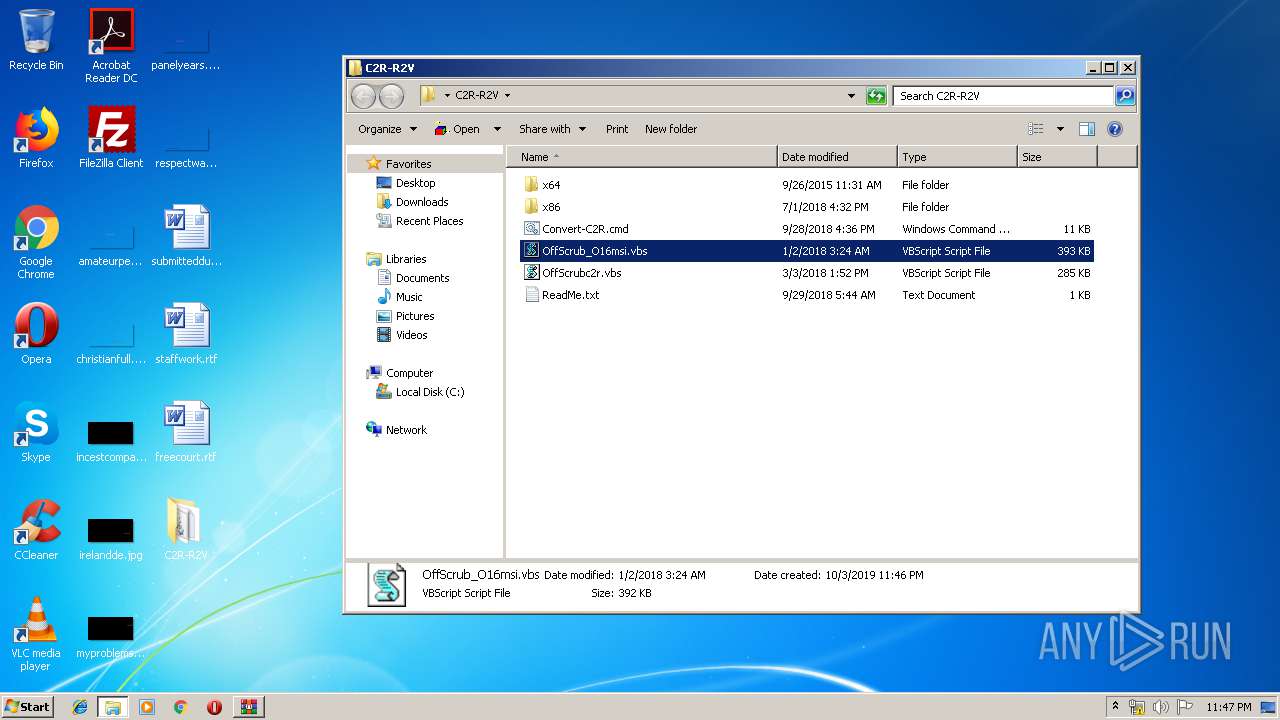
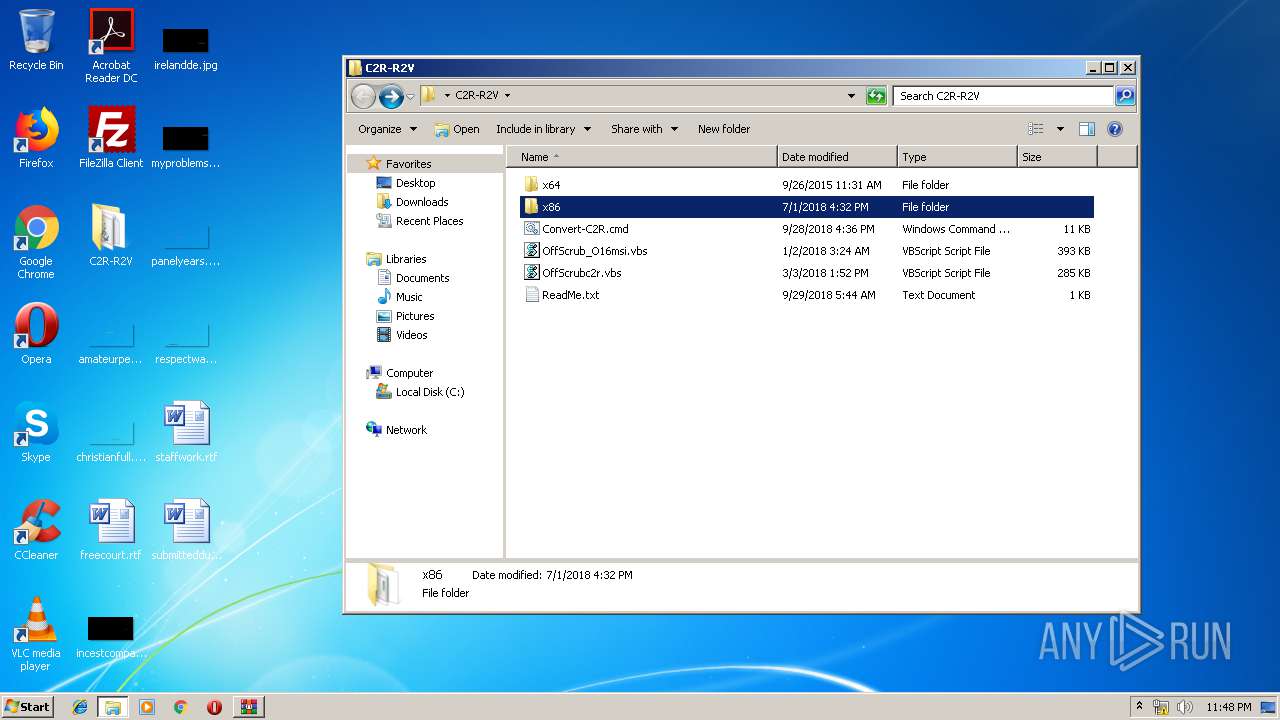
| File name: | C2R-R2V_5.7z |
| Full analysis: | https://app.any.run/tasks/07eeb633-f93b-482f-aa86-5f8eb34ad1fd |
| Verdict: | Malicious activity |
| Analysis date: | October 03, 2019, 22:45:42 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/x-7z-compressed |
| File info: | 7-zip archive data, version 0.4 |
| MD5: | 85086648BE3F3280581115BE82AB369D |
| SHA1: | 8365F5F61B64B8269708C5463FFB2AA712B7EB9B |
| SHA256: | 811E6F82B41E4263FC3F676C57DED8ECD1FB789C2A51B4D17273886370B6FB32 |
| SSDEEP: | 12288:uV3+4umF/ztkUjPkS8I8Gy+jnQaXeJyWYouPHc/E4xg8eZ:m3+4X/z/kS8PgjhektogyTuFZ |
MALICIOUS
Actions looks like stealing of personal data
- cscript.exe (PID: 2316)
Application was dropped or rewritten from another process
- CleanOSPP.exe (PID: 2116)
- cleanospp.exe (PID: 3228)
Loads dropped or rewritten executable
- cleanospp.exe (PID: 3228)
- CleanOSPP.exe (PID: 2116)
SUSPICIOUS
Executable content was dropped or overwritten
- WinRAR.exe (PID: 2920)
Application launched itself
- cmd.exe (PID: 2744)
Starts CMD.EXE for commands execution
- cmd.exe (PID: 2744)
Uses REG.EXE to modify Windows registry
- cmd.exe (PID: 2744)
Starts SC.EXE for service management
- cmd.exe (PID: 2744)
Executes scripts
- WScript.exe (PID: 3896)
- WScript.exe (PID: 2448)
INFO
Manual execution by user
- cmd.exe (PID: 2744)
- WScript.exe (PID: 3896)
- WScript.exe (PID: 2448)
- WScript.exe (PID: 3128)
- cleanospp.exe (PID: 3228)
- NOTEPAD.EXE (PID: 3608)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .7z | | | 7-Zip compressed archive (v0.4) (57.1) |
|---|---|---|
| .7z | | | 7-Zip compressed archive (gen) (42.8) |
Total processes
76
Monitored processes
16
Malicious processes
2
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1200 | sc query ClickToRunSvc | C:\Windows\system32\sc.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: A tool to aid in developing services for WindowsNT Exit code: 1060 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
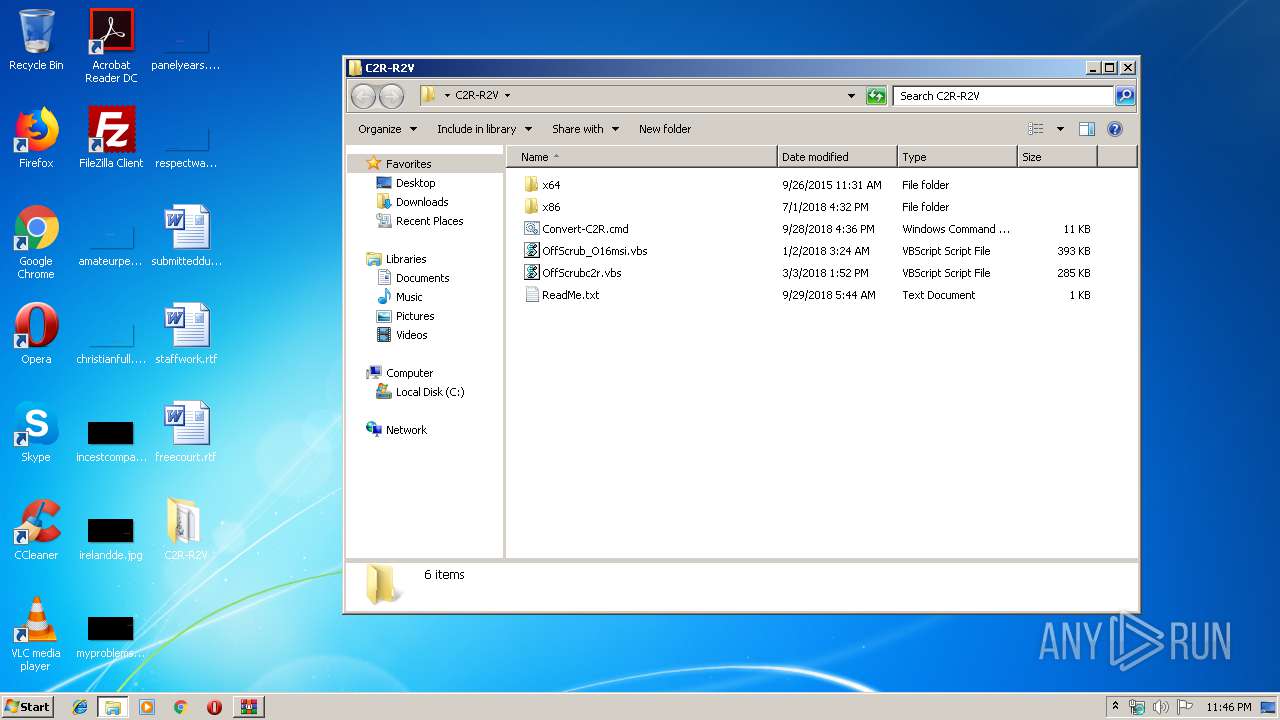
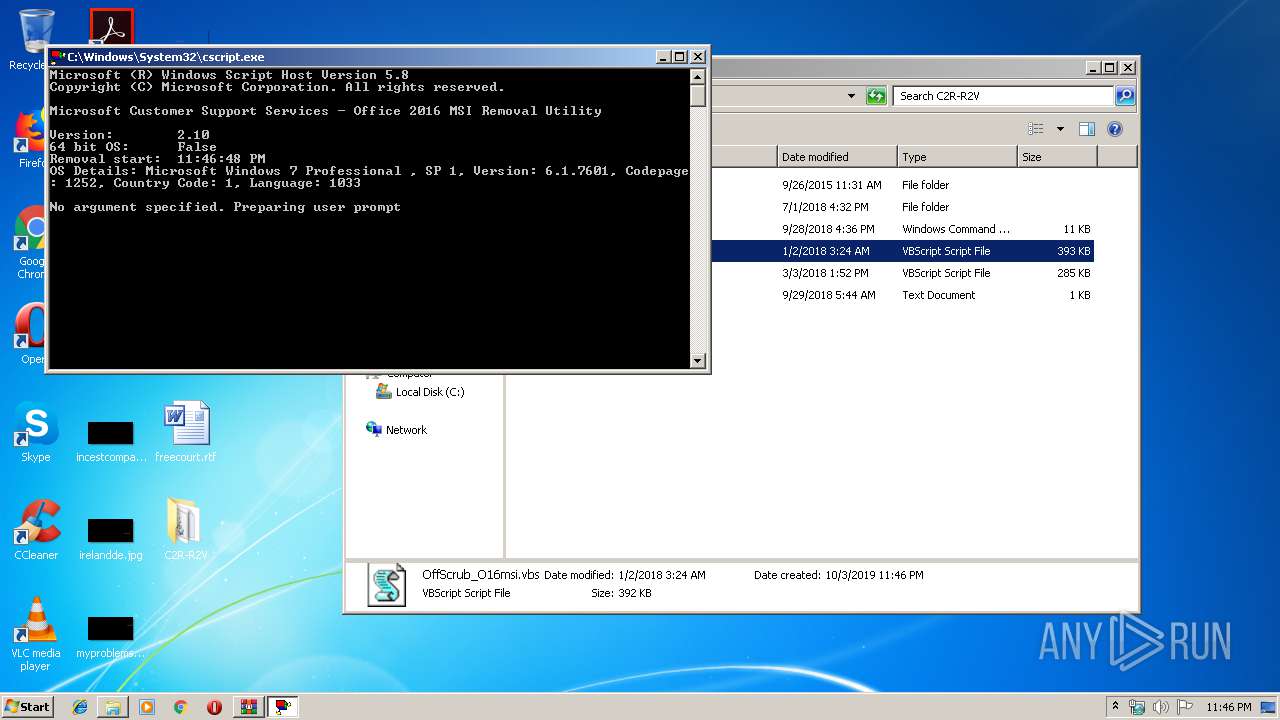
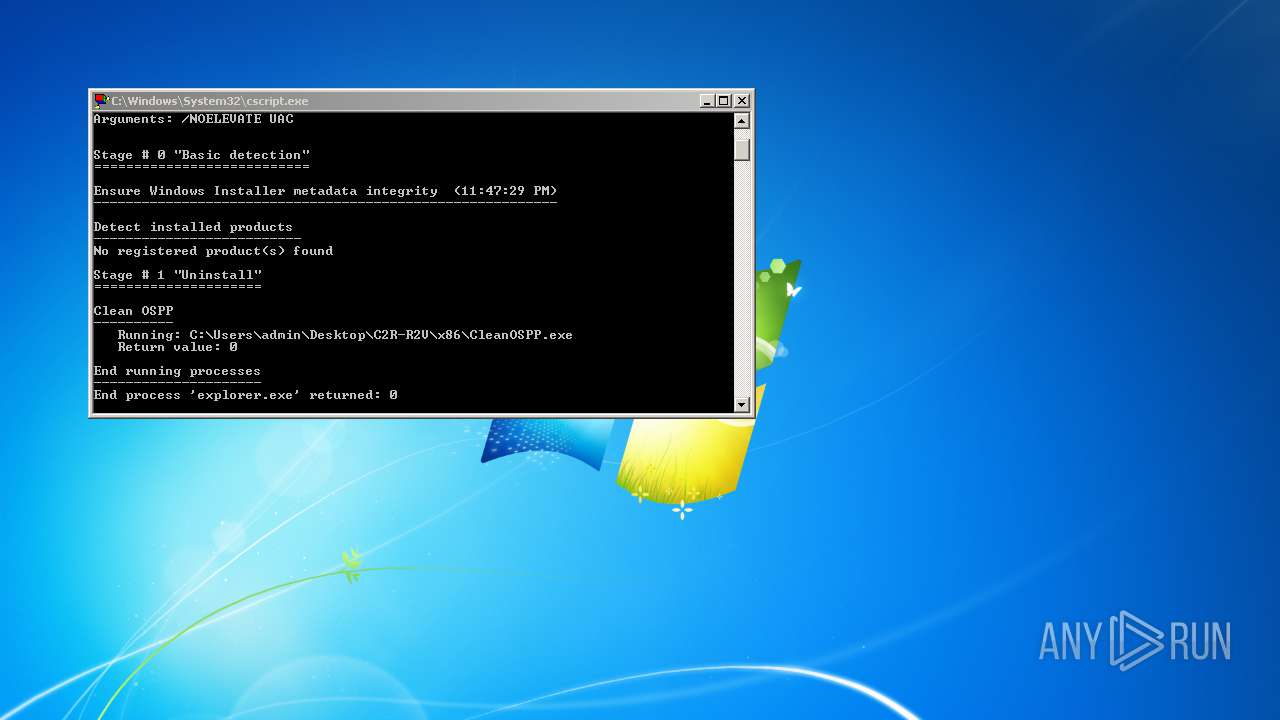
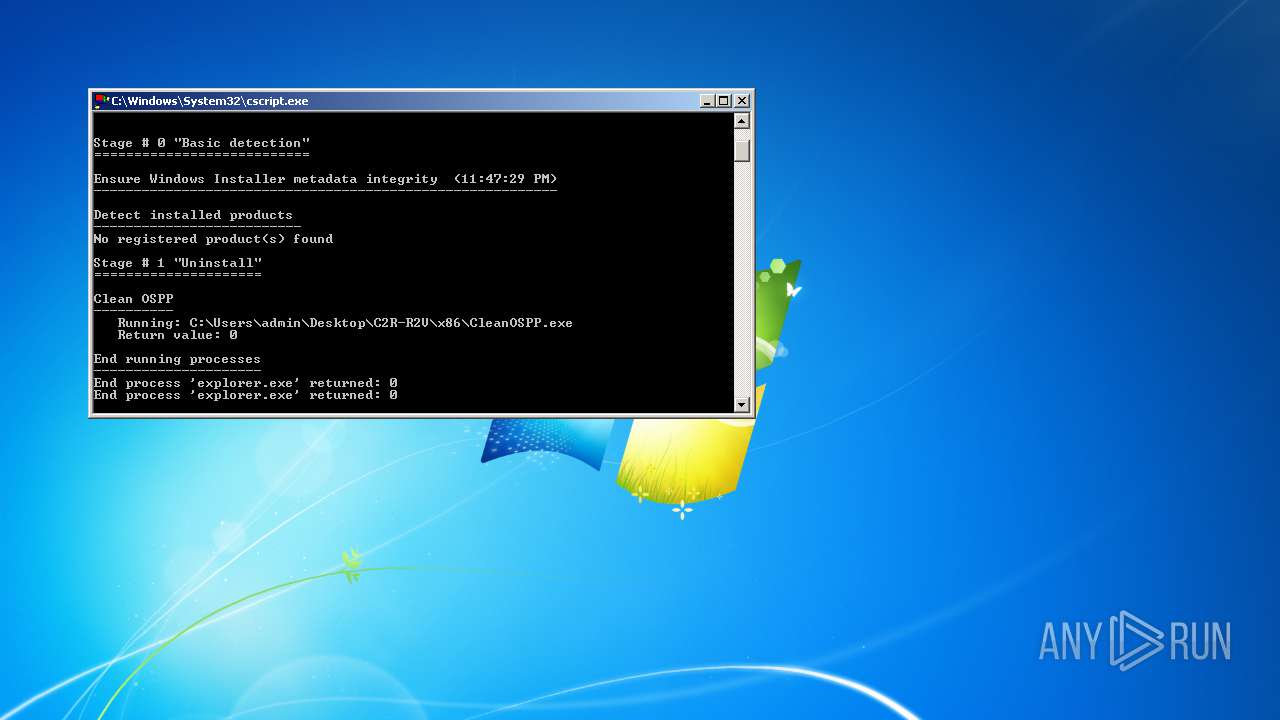
| 2116 | "C:\Users\admin\Desktop\C2R-R2V\x86\CleanOSPP.exe" | C:\Users\admin\Desktop\C2R-R2V\x86\CleanOSPP.exe | — | cscript.exe | |||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 2240 | sc query OfficeSvc | C:\Windows\system32\sc.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: A tool to aid in developing services for WindowsNT Exit code: 1060 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2292 | cscript.exe | C:\Windows\System32\cscript.exe | — | WScript.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft ® Console Based Script Host Exit code: 0 Version: 5.8.7600.16385 Modules
| |||||||||||||||
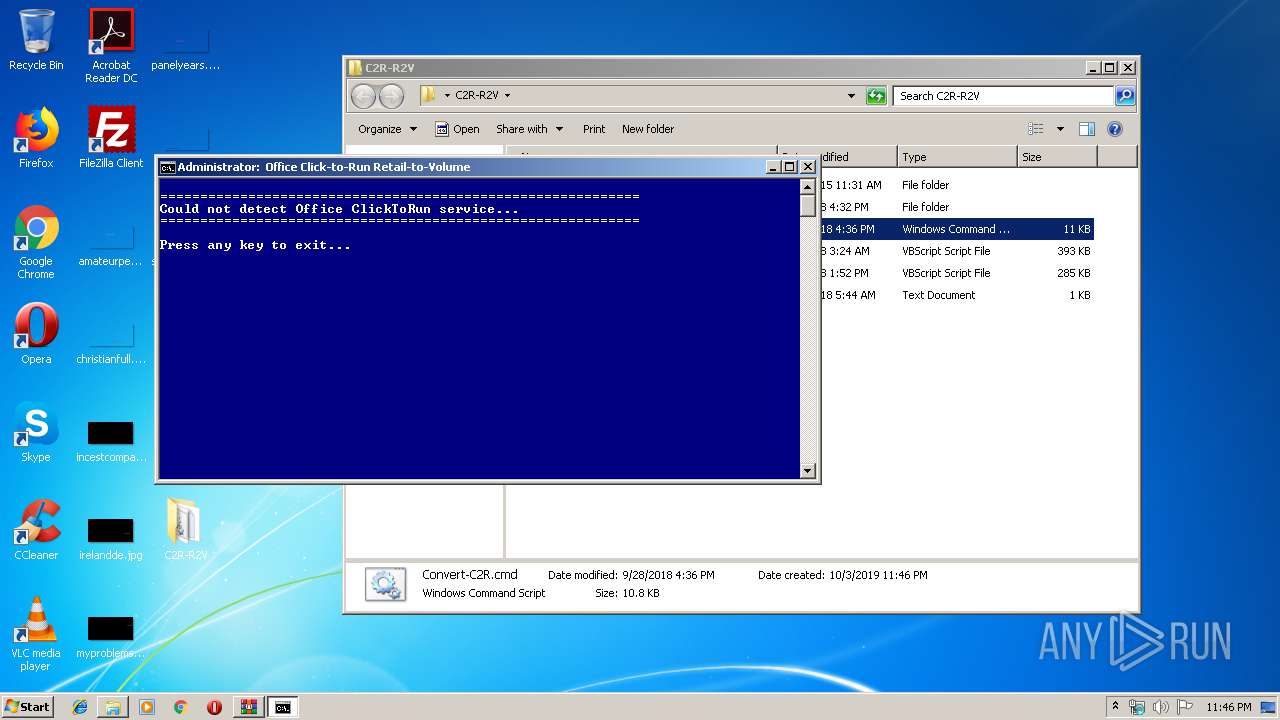
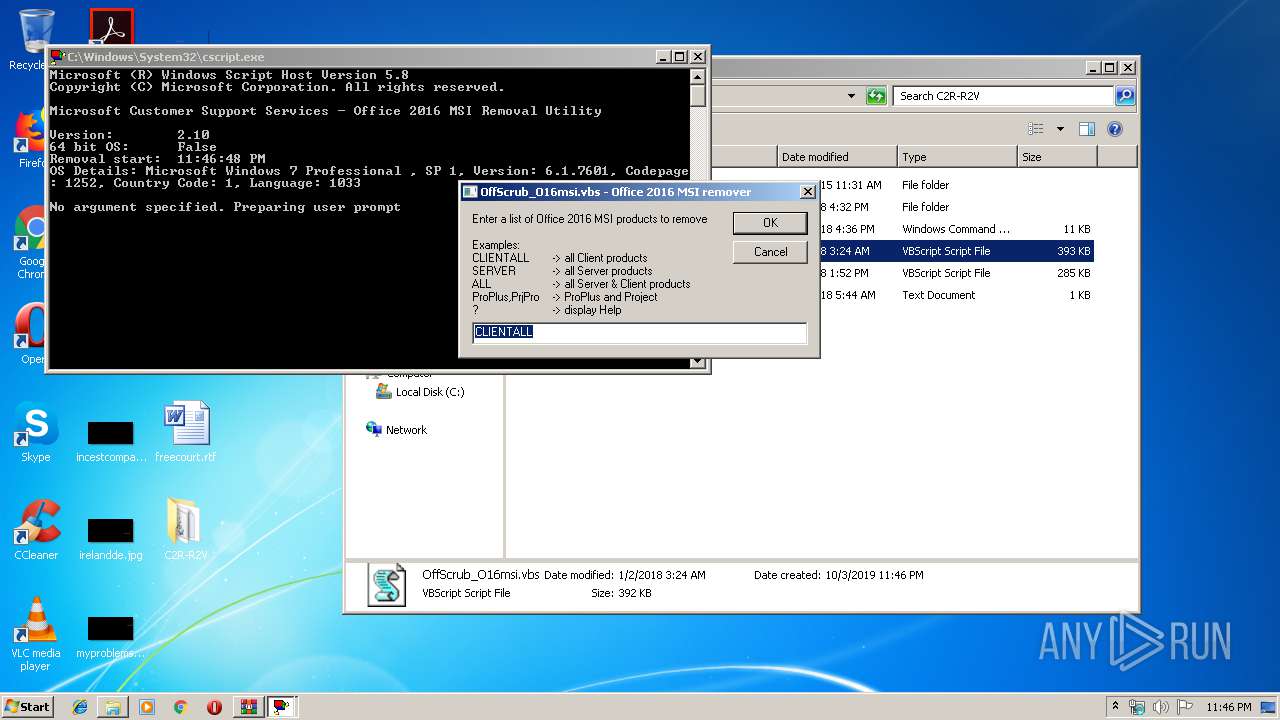
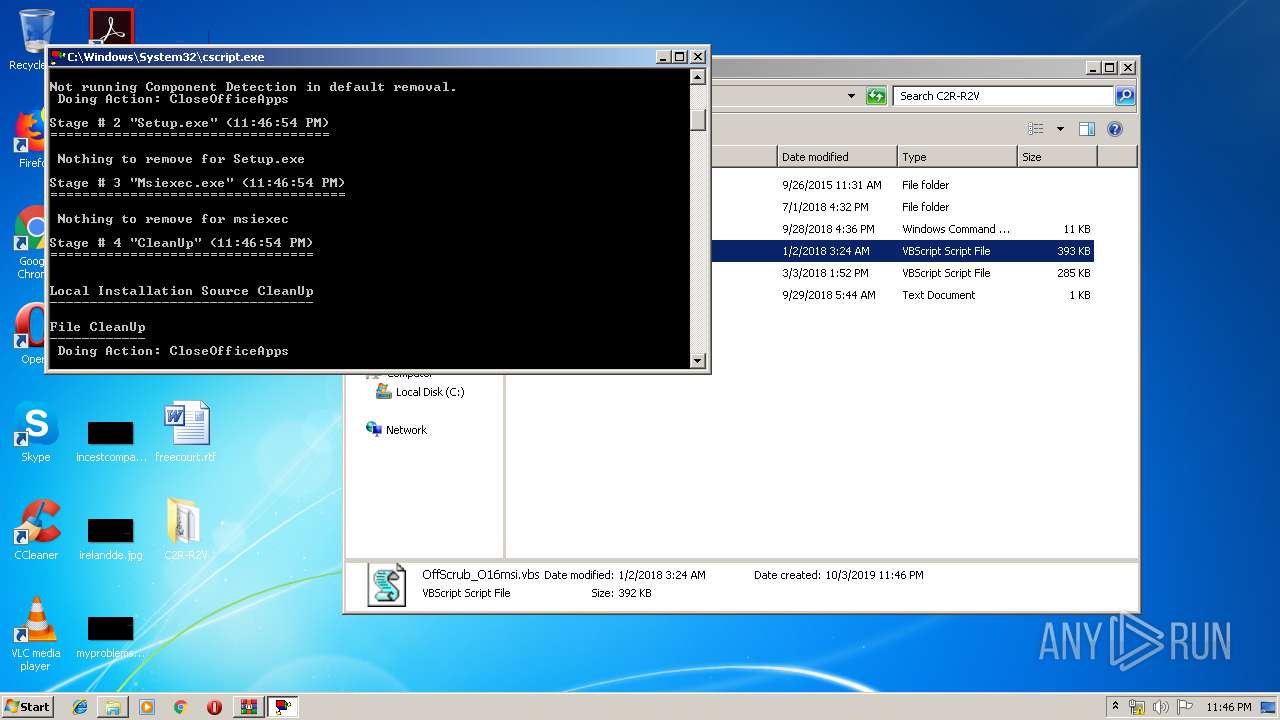
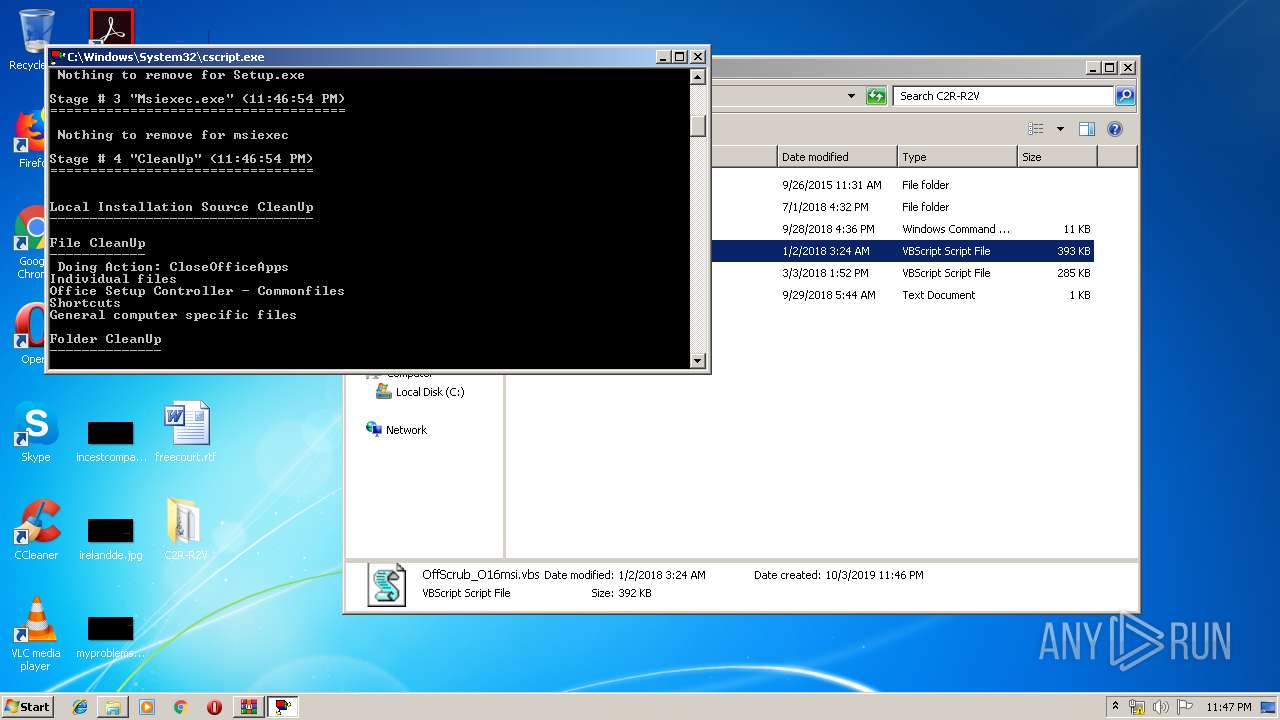
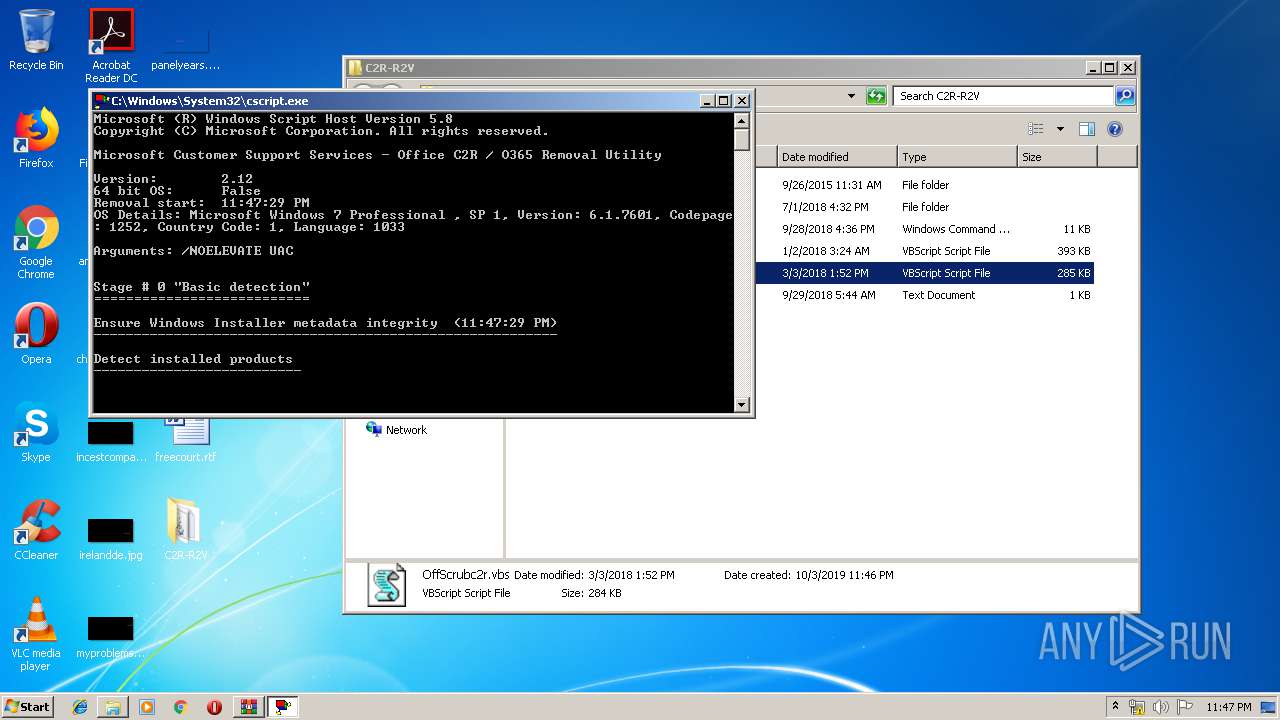
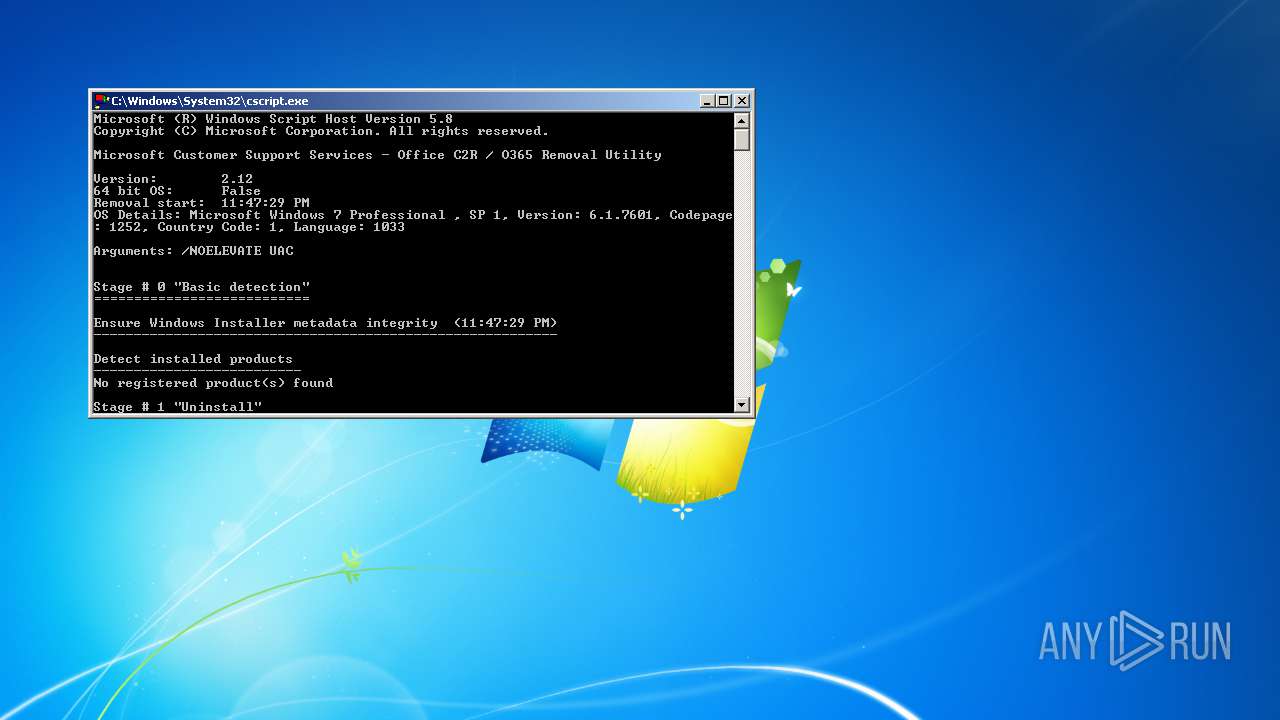
| 2316 | "C:\Windows\System32\cscript.exe" "C:\Users\admin\Desktop\C2R-R2V\OffScrub_O16msi.vbs" /NoElevate UAC | C:\Windows\System32\cscript.exe | WScript.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft ® Console Based Script Host Exit code: 3221225786 Version: 5.8.7600.16385 Modules
| |||||||||||||||
| 2448 | "C:\Windows\System32\WScript.exe" "C:\Users\admin\Desktop\C2R-R2V\OffScrubc2r.vbs" | C:\Windows\System32\WScript.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft ® Windows Based Script Host Exit code: 3221225786 Version: 5.8.7600.16385 Modules
| |||||||||||||||
| 2744 | "C:\Windows\System32\cmd.exe" /C "C:\Users\admin\Desktop\C2R-R2V\Convert-C2R.cmd" | C:\Windows\System32\cmd.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
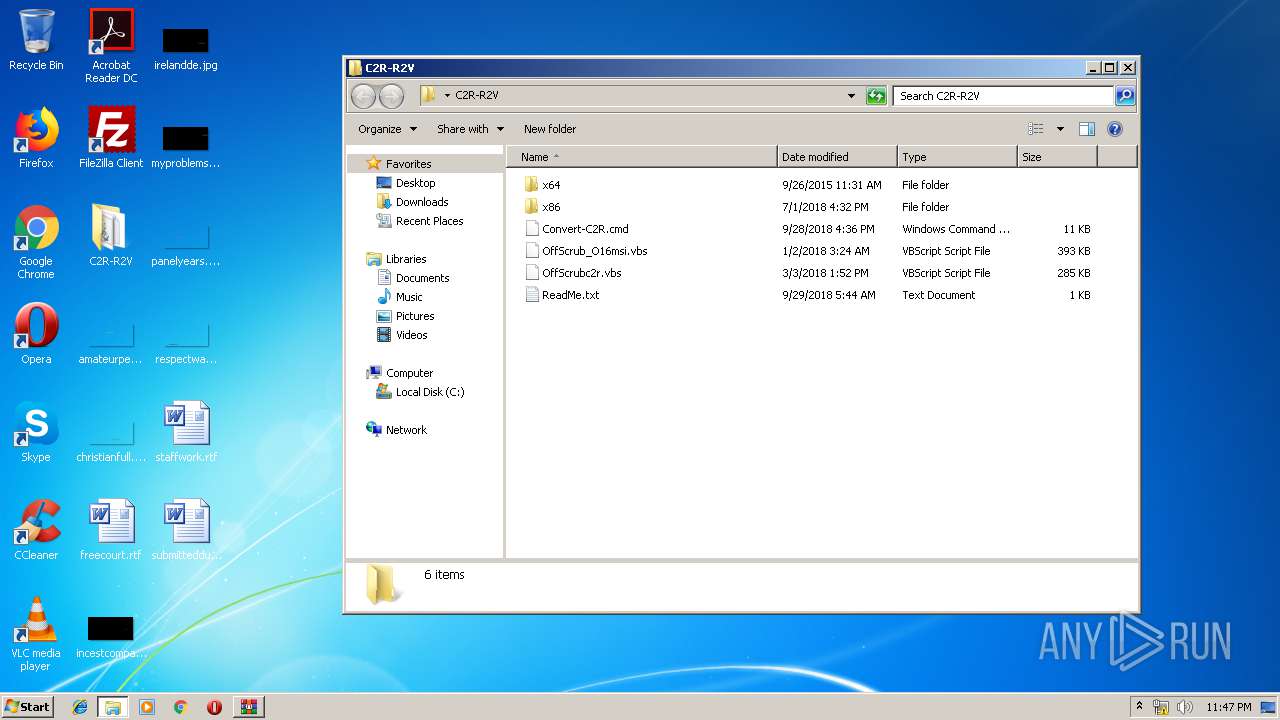
| 2920 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Temp\C2R-R2V_5.7z" | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.60.0 Modules
| |||||||||||||||
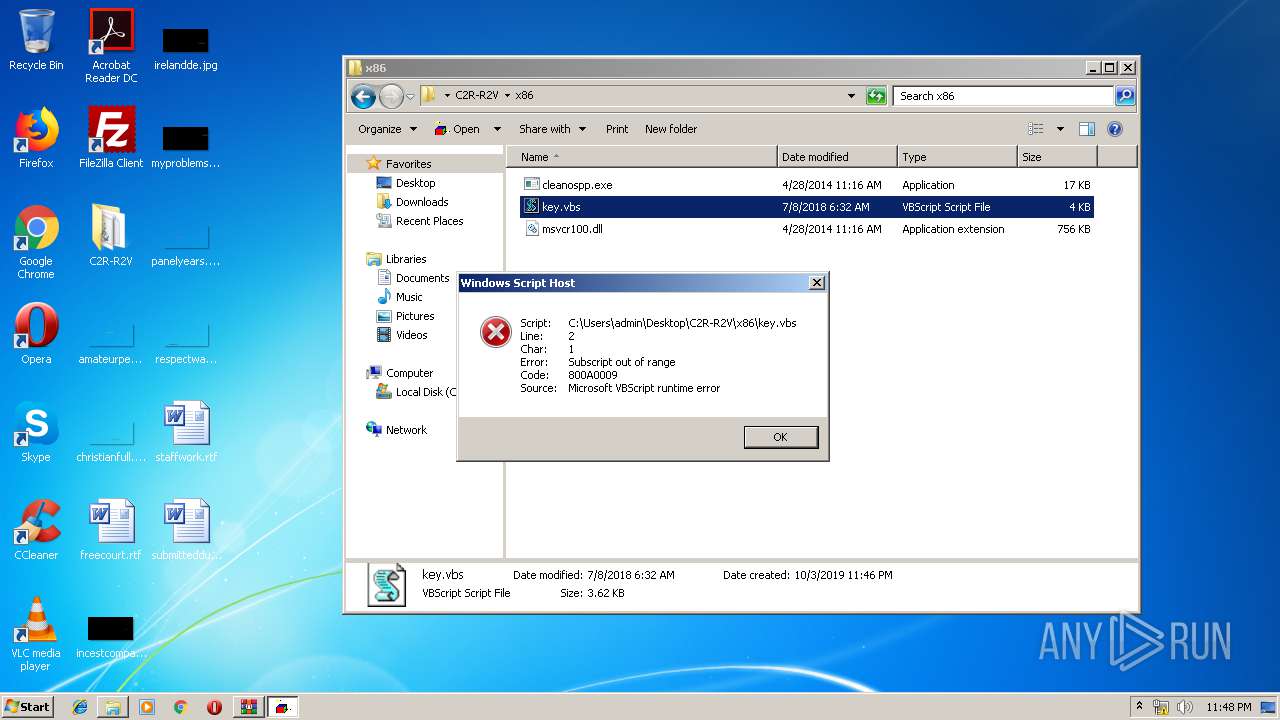
| 3128 | "C:\Windows\System32\WScript.exe" "C:\Users\admin\Desktop\C2R-R2V\x86\key.vbs" | C:\Windows\System32\WScript.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft ® Windows Based Script Host Exit code: 0 Version: 5.8.7600.16385 Modules
| |||||||||||||||
| 3216 | "C:\Windows\System32\cscript.exe" "C:\Users\admin\Desktop\C2R-R2V\OffScrubc2r.vbs" /NoElevate UAC | C:\Windows\System32\cscript.exe | WScript.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft ® Console Based Script Host Exit code: 3221225786 Version: 5.8.7600.16385 Modules
| |||||||||||||||
Total events
879
Read events
843
Write events
36
Delete events
0
Modification events
| (PID) Process: | (2920) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (2920) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (2920) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\72\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (2920) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\C2R-R2V_5.7z | |||
| (PID) Process: | (2920) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (2920) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (2920) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (2920) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (2920) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\DialogEditHistory\ExtrPath |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop | |||
| (PID) Process: | (3896) WScript.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 0 | |||
Executable files
4
Suspicious files
0
Text files
10
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2920 | WinRAR.exe | C:\Users\admin\Desktop\C2R-R2V\Convert-C2R.cmd | text | |
MD5:353CDE65B538019CA139E3E790ABD8CD | SHA256:D450D67F57F2B28EDEB22044D1107E35AF8AC3CC940E79F78B59601A3718B1FB | |||
| 2920 | WinRAR.exe | C:\Users\admin\Desktop\C2R-R2V\OffScrubc2r.vbs | text | |
MD5:930DC88EDCDDE90F7449CA55AA616928 | SHA256:570F82344AD7300DD4A2993AD6C3A1ABE1987F37254BFF708DBA1801BFEF392C | |||
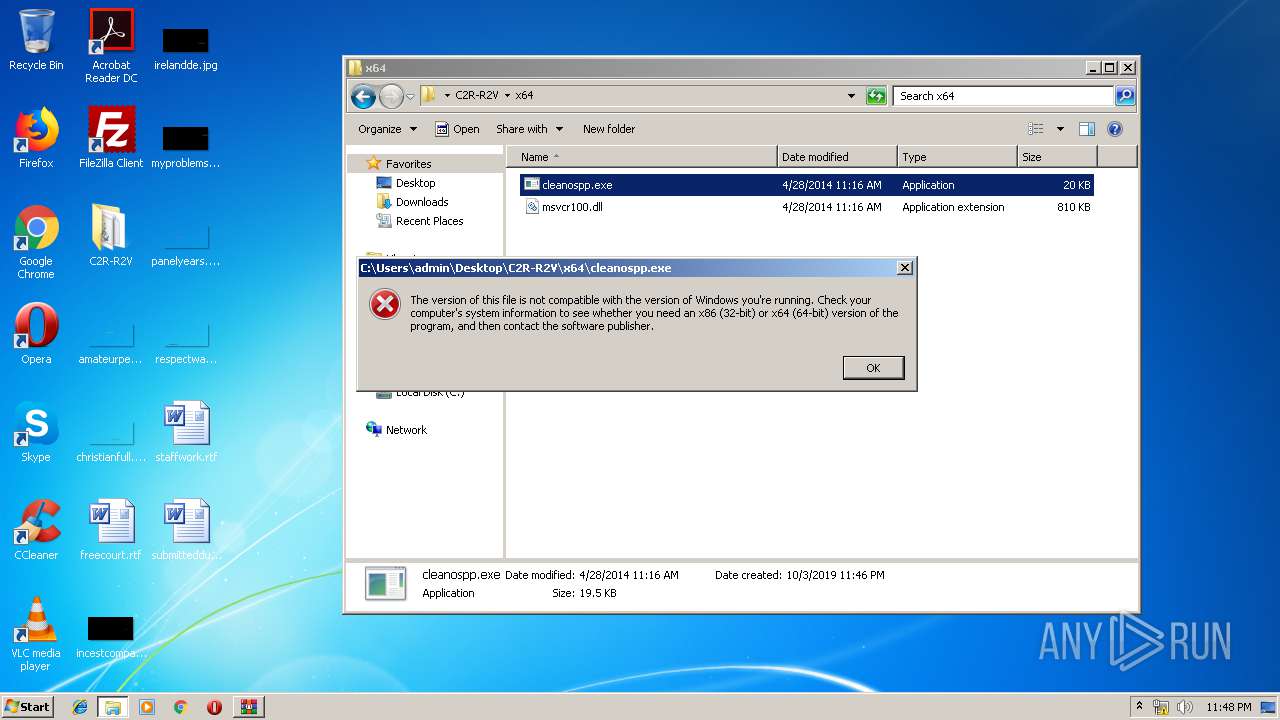
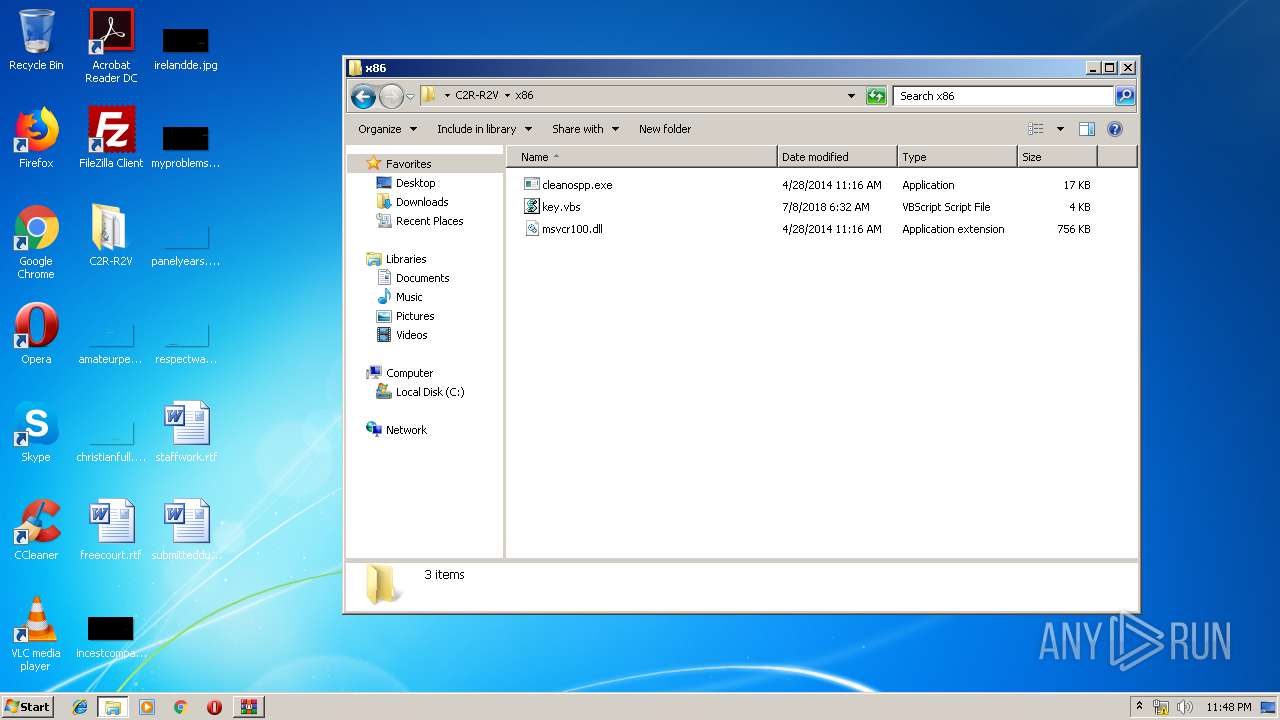
| 2920 | WinRAR.exe | C:\Users\admin\Desktop\C2R-R2V\x86\cleanospp.exe | executable | |
MD5:5FD363D52D04AC200CD24F3BCC903200 | SHA256:3FDEFE2AD092A9A7FE0EDF0AC4DC2DE7E5B9CE6A0804F6511C06564194966CF9 | |||
| 2920 | WinRAR.exe | C:\Users\admin\Desktop\C2R-R2V\x64\cleanospp.exe | executable | |
MD5:162AB955CB2F002A73C1530AA796477F | SHA256:5CE462E5F34065FC878362BA58617FAB28C22D631B9D836DDDCF43FB1AD4DE6E | |||
| 2920 | WinRAR.exe | C:\Users\admin\Desktop\C2R-R2V\OffScrub_O16msi.vbs | text | |
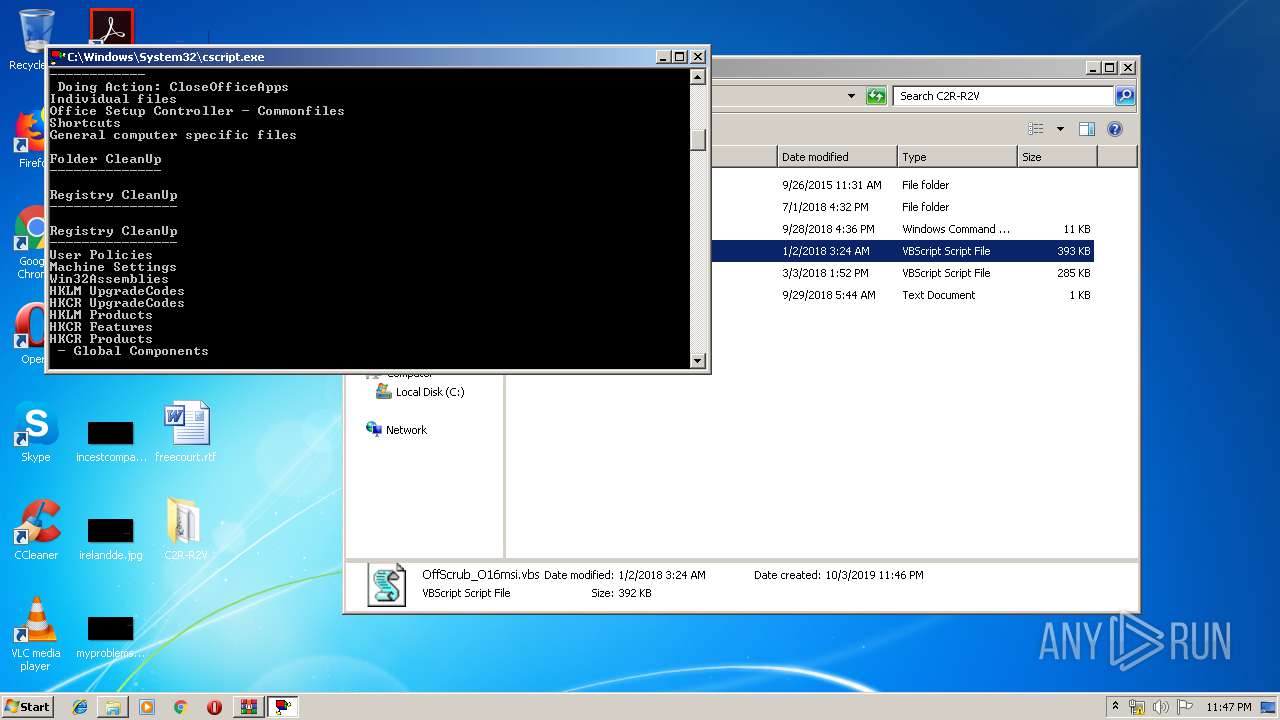
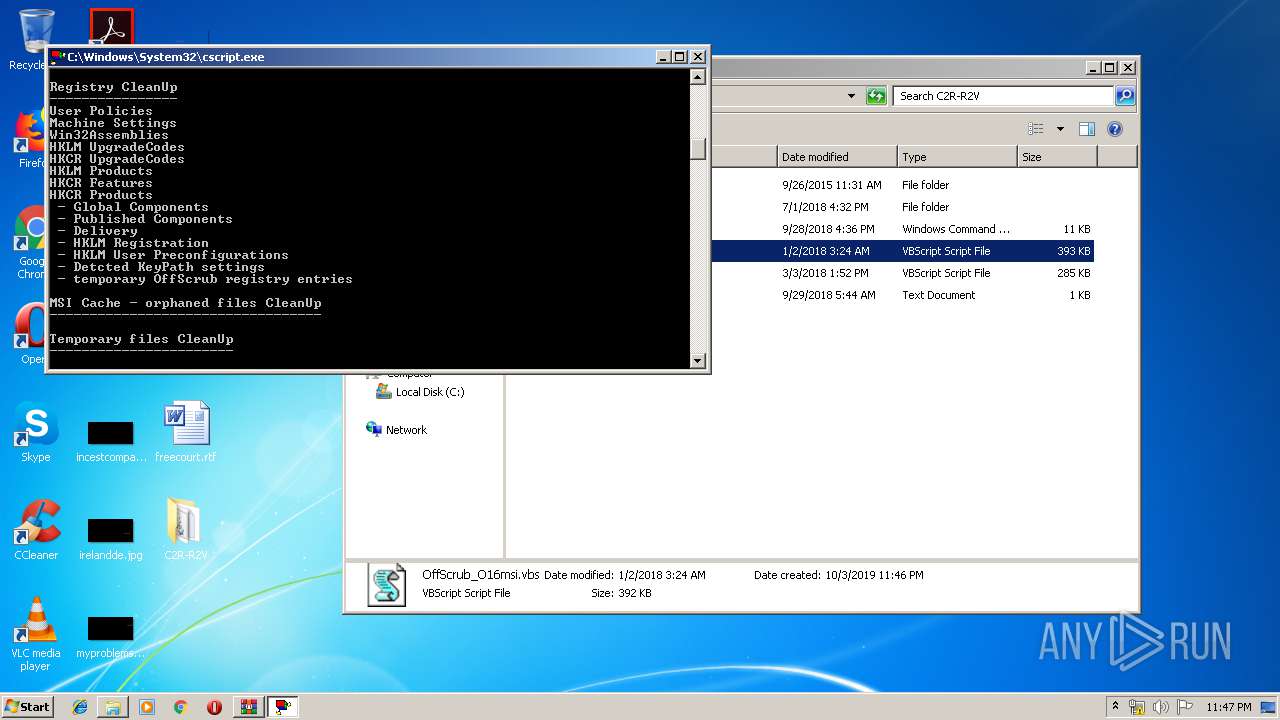
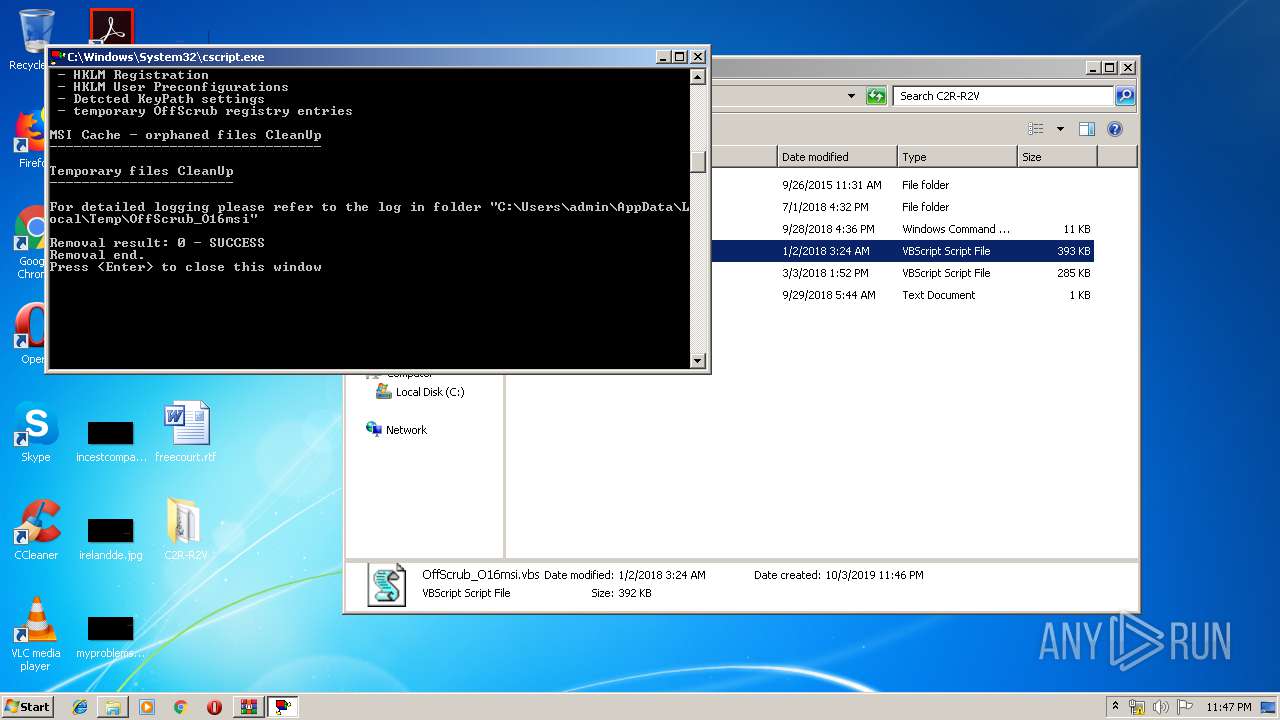
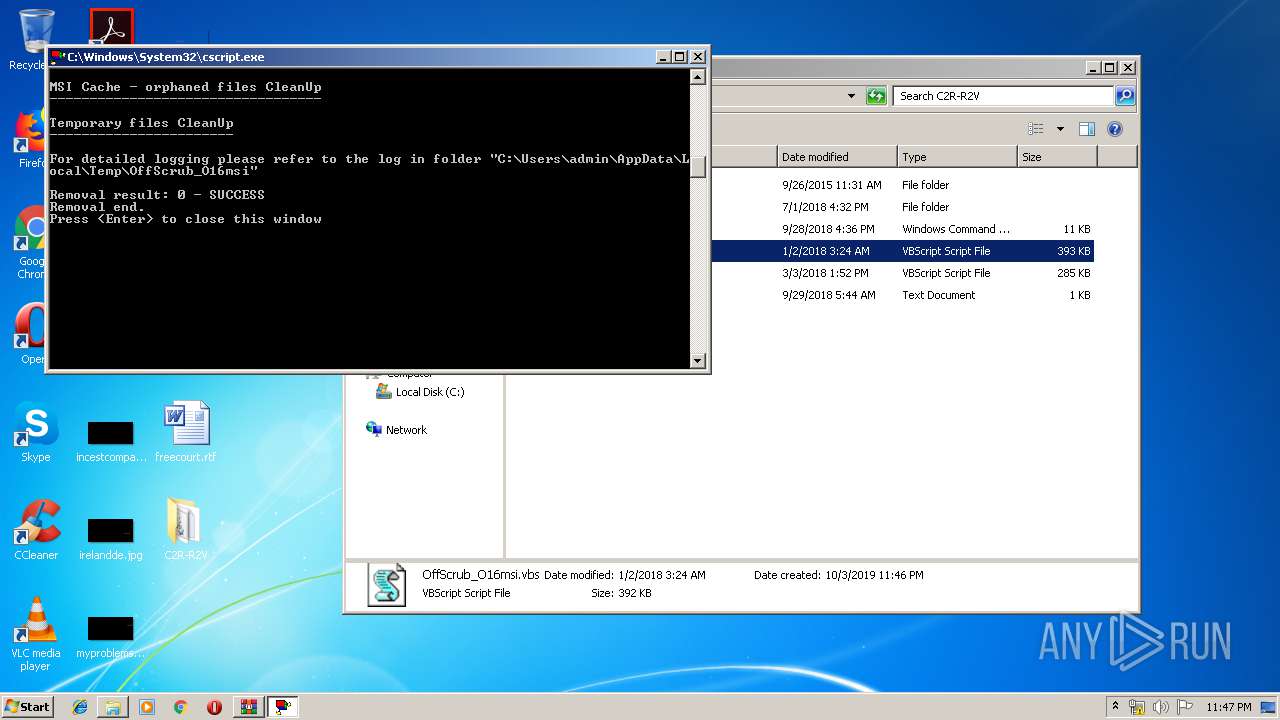
MD5:67885A2865E9B277EA5A623B5217782C | SHA256:C5903CD58467DE9BBA3614D03D637D002C2A24C6706729E105699B1214F938D1 | |||
| 2316 | cscript.exe | C:\Users\admin\AppData\Local\Temp\OffScrub_O16msi\USER-PC_20191003234648_ScrubLog.txt | text | |
MD5:— | SHA256:— | |||
| 3216 | cscript.exe | C:\Users\admin\AppData\Local\Temp\OffScrubC2R\USER-PC_20191003234729_ScrubLog.txt | text | |
MD5:— | SHA256:— | |||
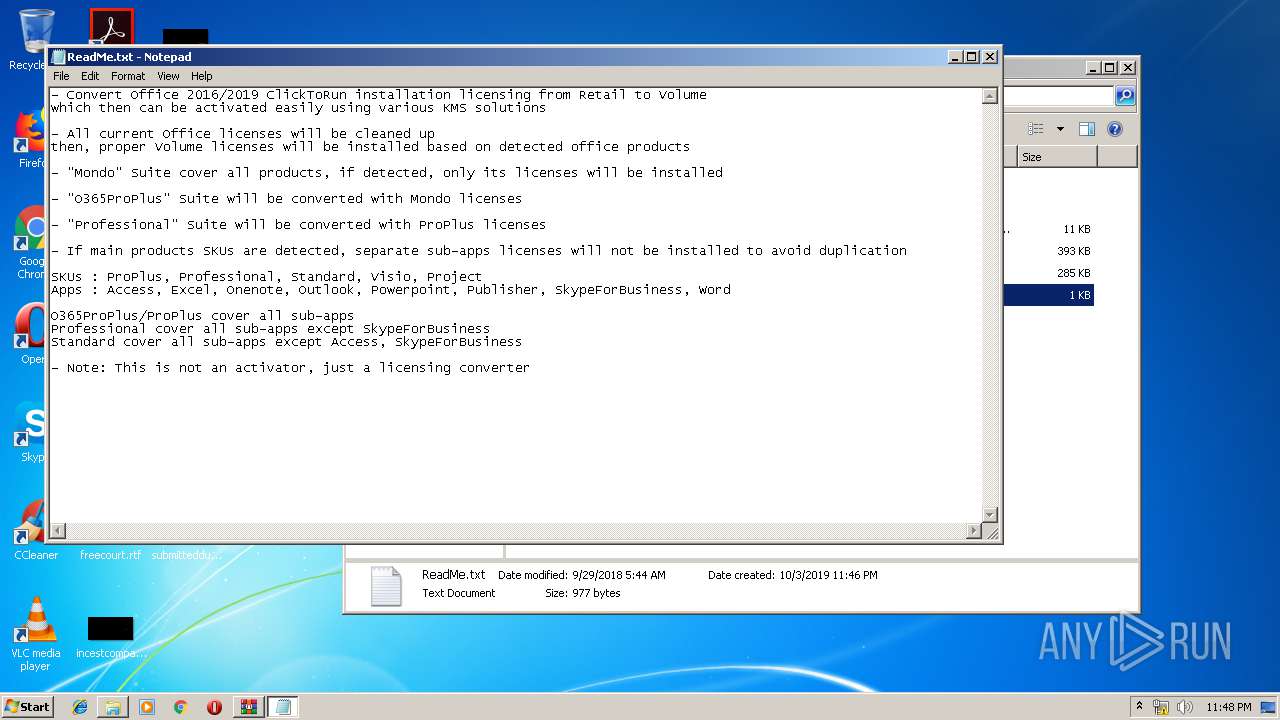
| 2920 | WinRAR.exe | C:\Users\admin\Desktop\C2R-R2V\ReadMe.txt | text | |
MD5:133FAC2255E749C176DBC1C8BF34D50E | SHA256:5822348EF723FB6AE37054B8B21976DEEAB82896BBA566EE6879F13F29488111 | |||
| 2920 | WinRAR.exe | C:\Users\admin\Desktop\C2R-R2V\x86\key.vbs | text | |
MD5:C264487F146AF23BE8B8C65E32D8A211 | SHA256:CE647840ADAB3A9B403DF557CA993A42032EB57F768B5992B022839787C2D0CE | |||
| 2920 | WinRAR.exe | C:\Users\admin\Desktop\C2R-R2V\x86\msvcr100.dll | executable | |
MD5:BF38660A9125935658CFA3E53FDC7D65 | SHA256:60C06E0FA4449314DA3A0A87C1A9D9577DF99226F943637E06F61188E5862EFA | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
0
DNS requests
0
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report